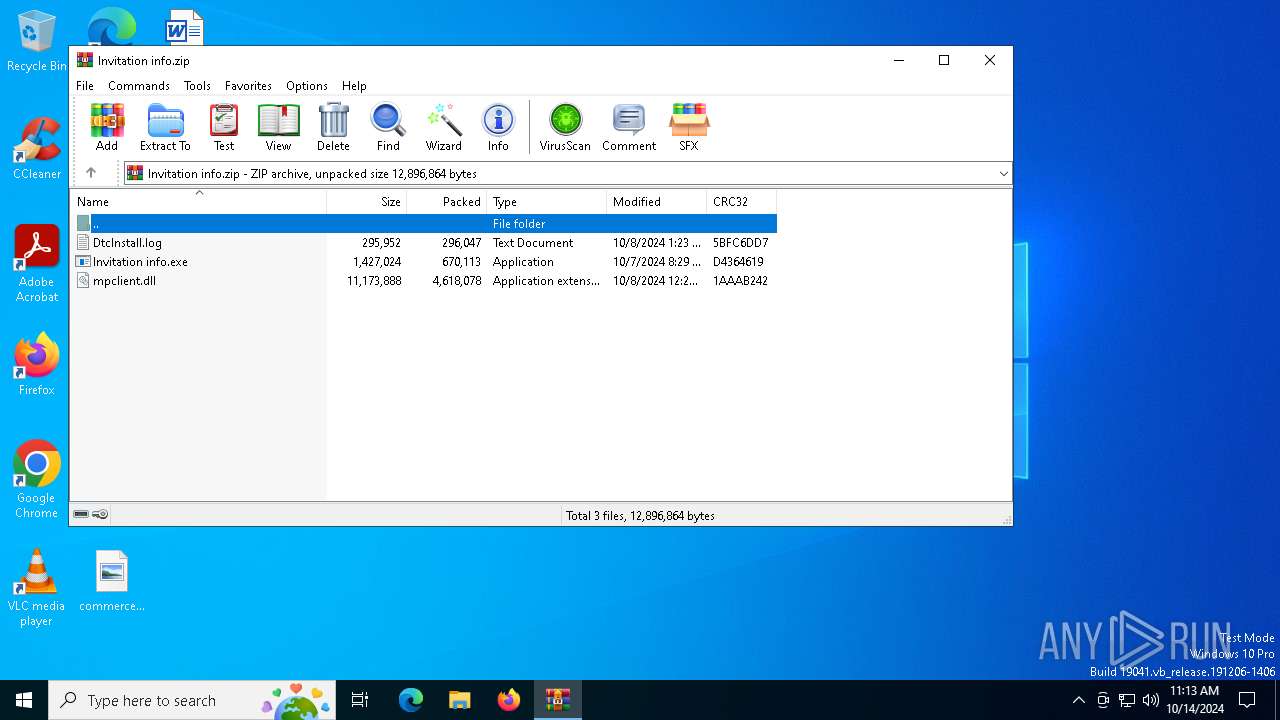
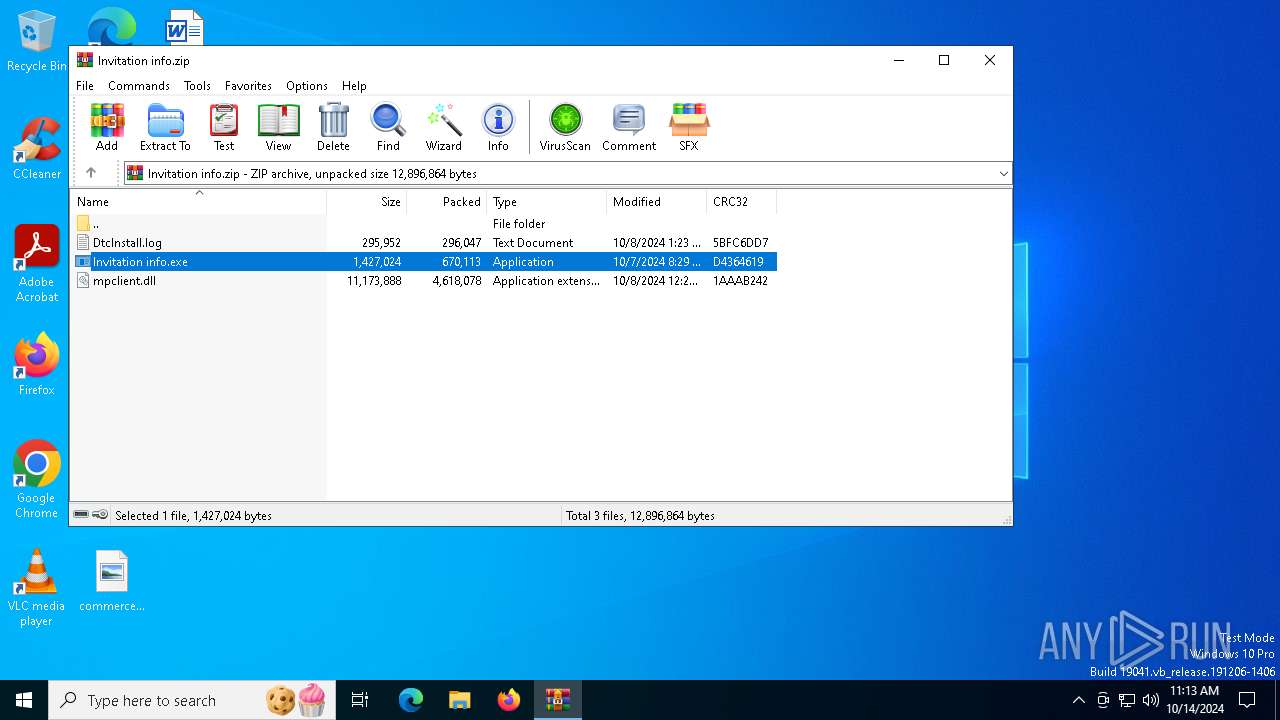
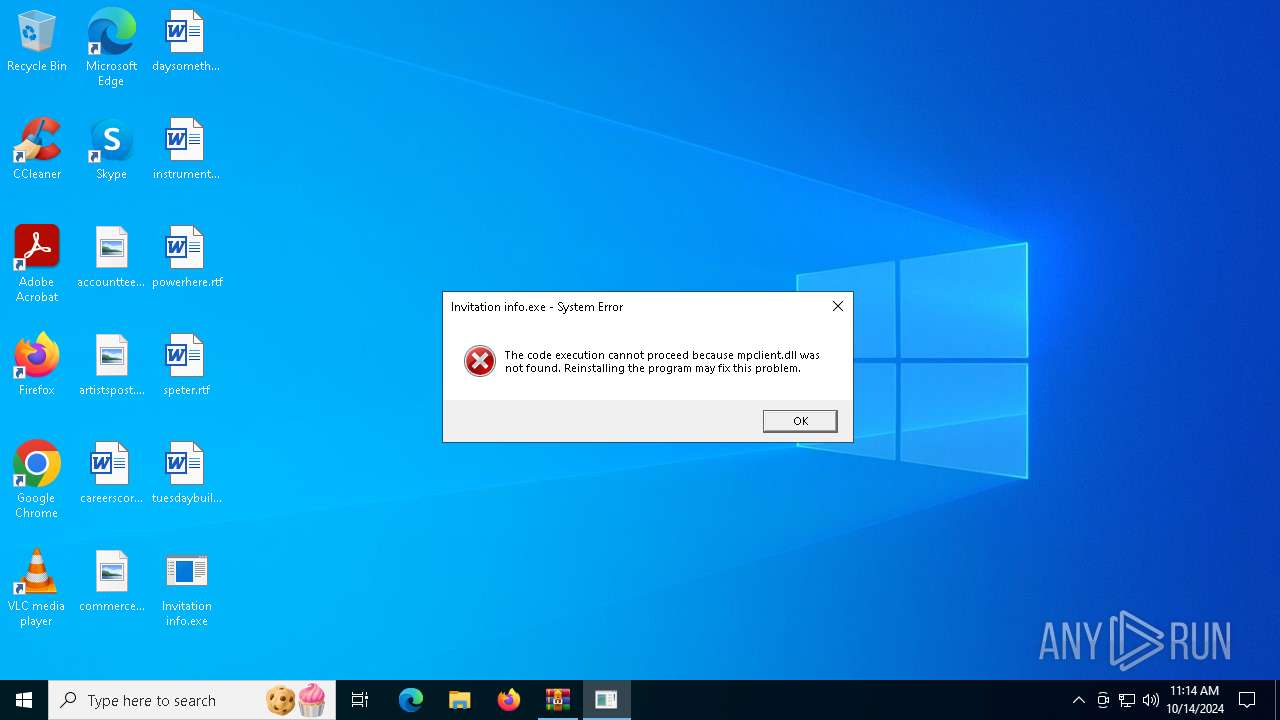
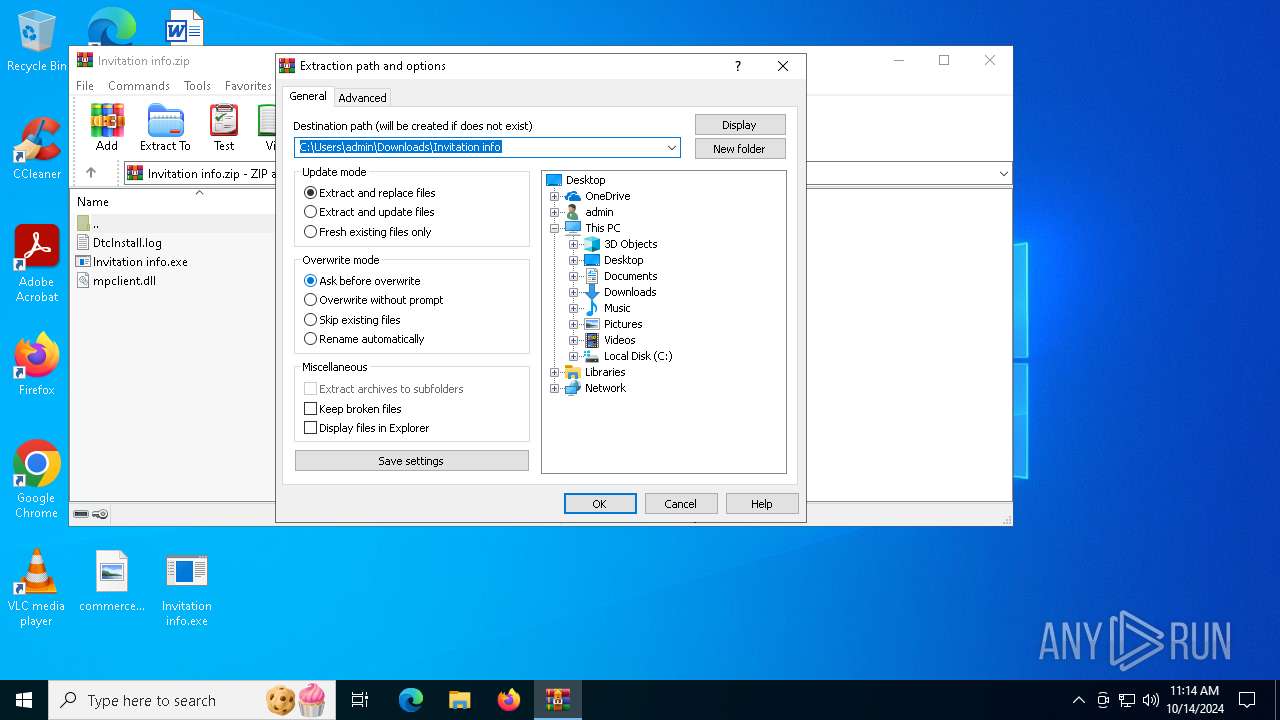
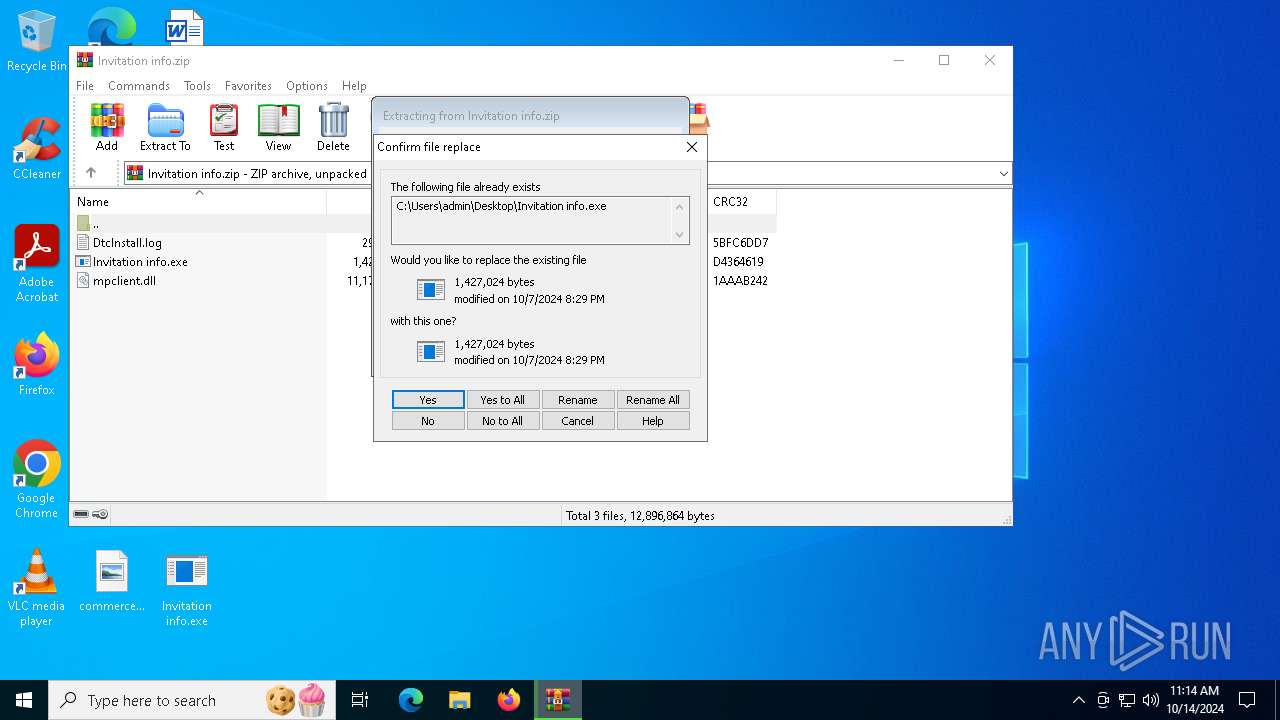
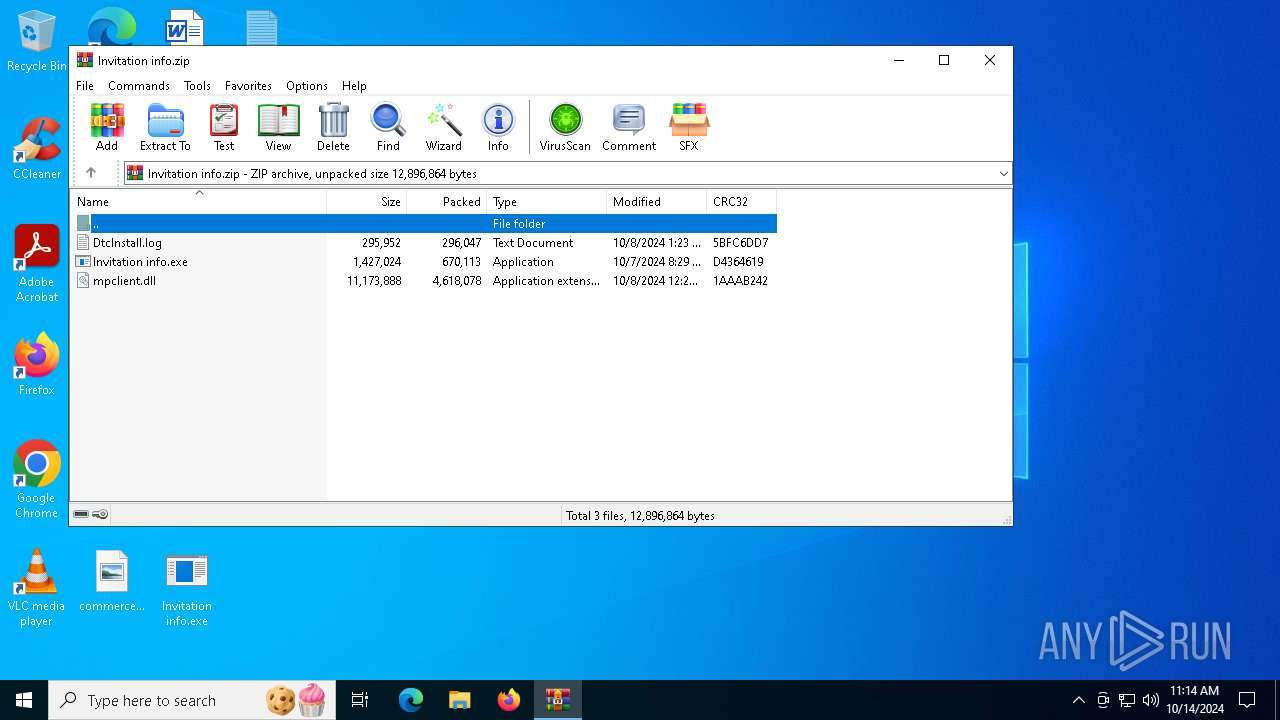
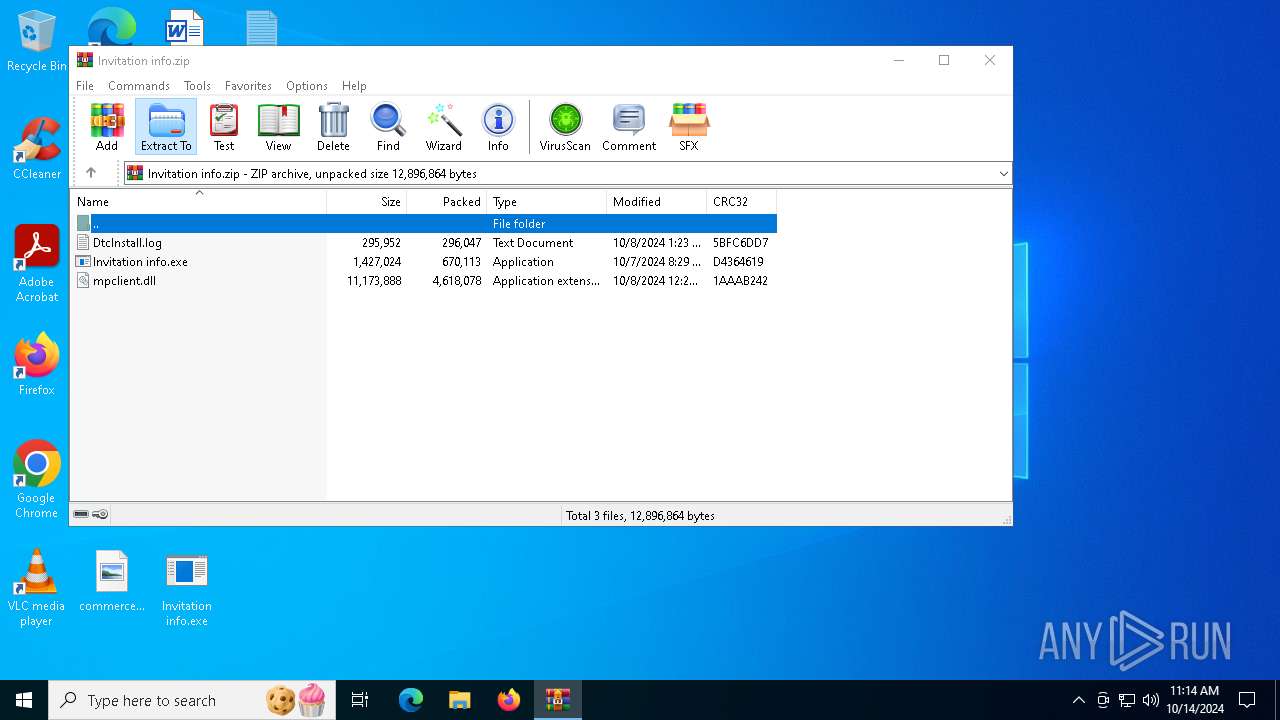
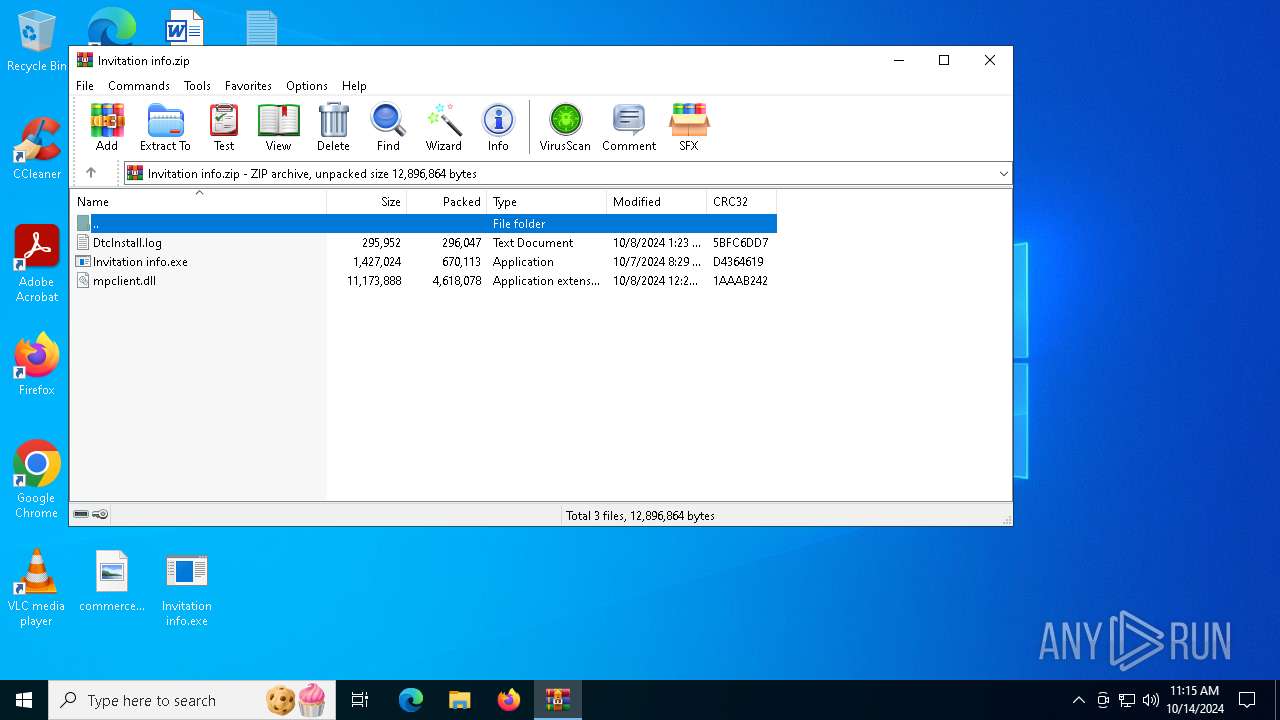
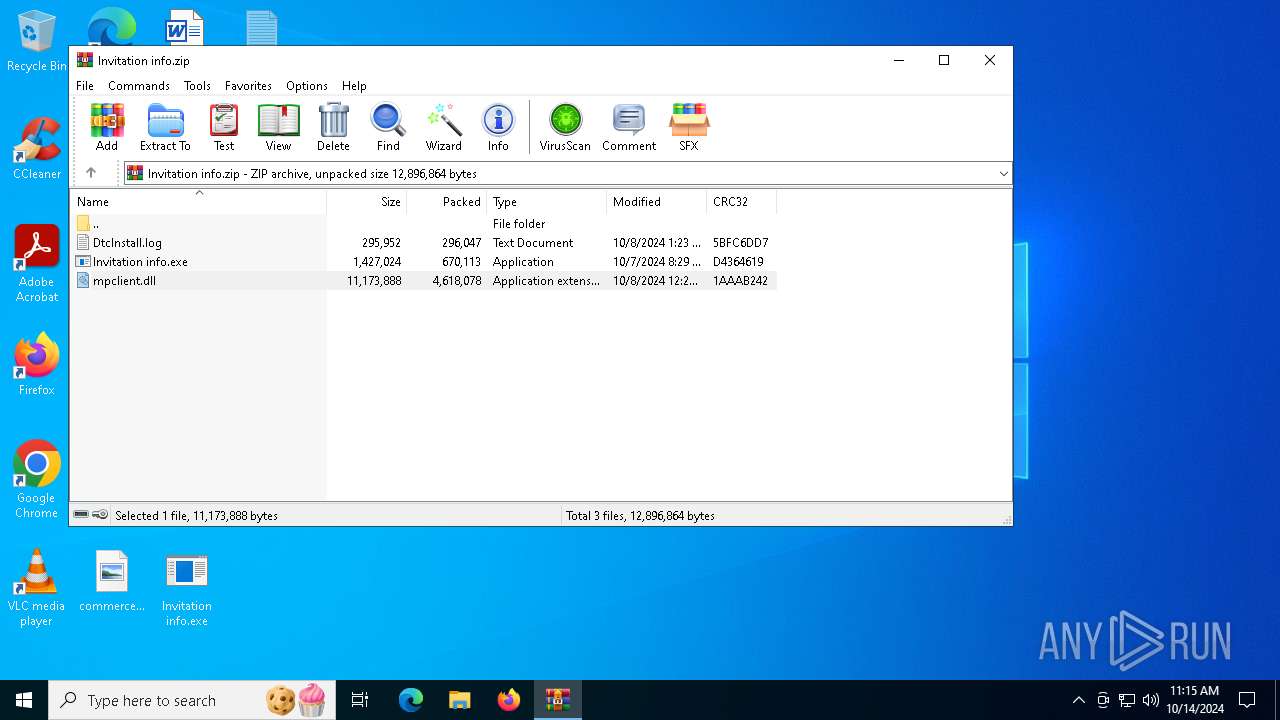
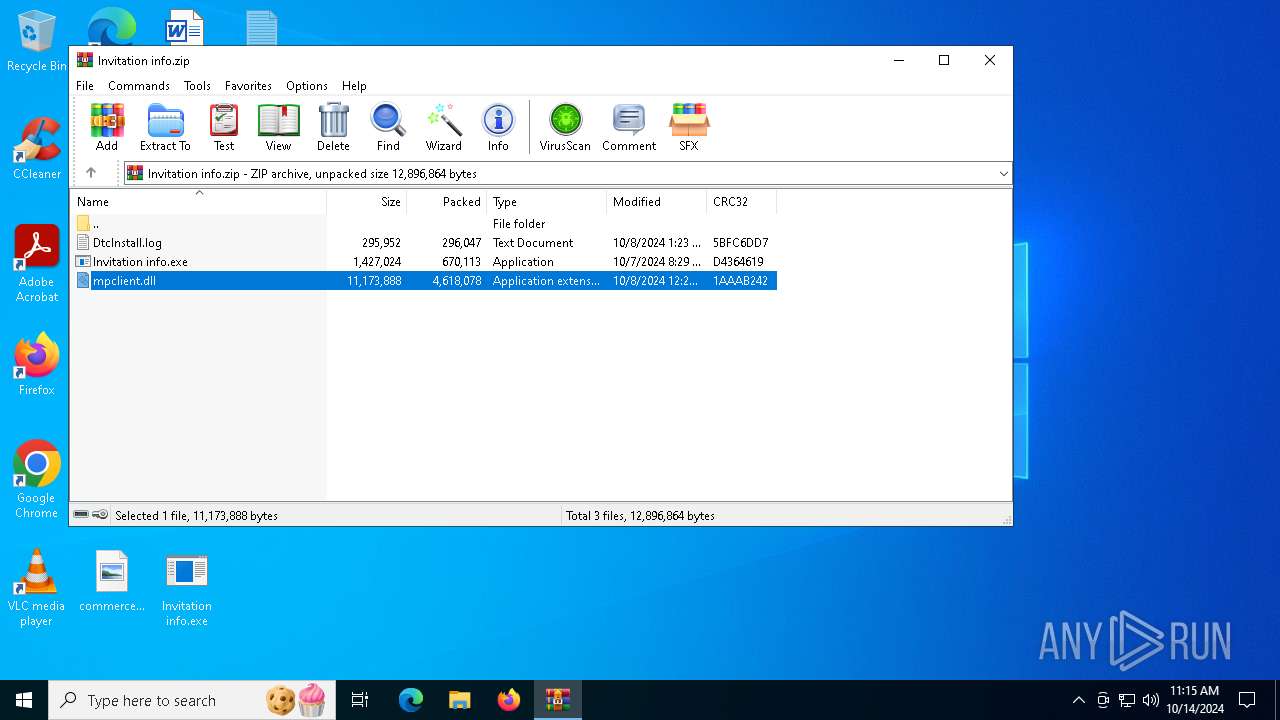
| File name: | Invitation info.zip |
| Full analysis: | https://app.any.run/tasks/1f88f3d7-41dd-47cf-b0d1-b706f31e4761 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | October 14, 2024, 11:13:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
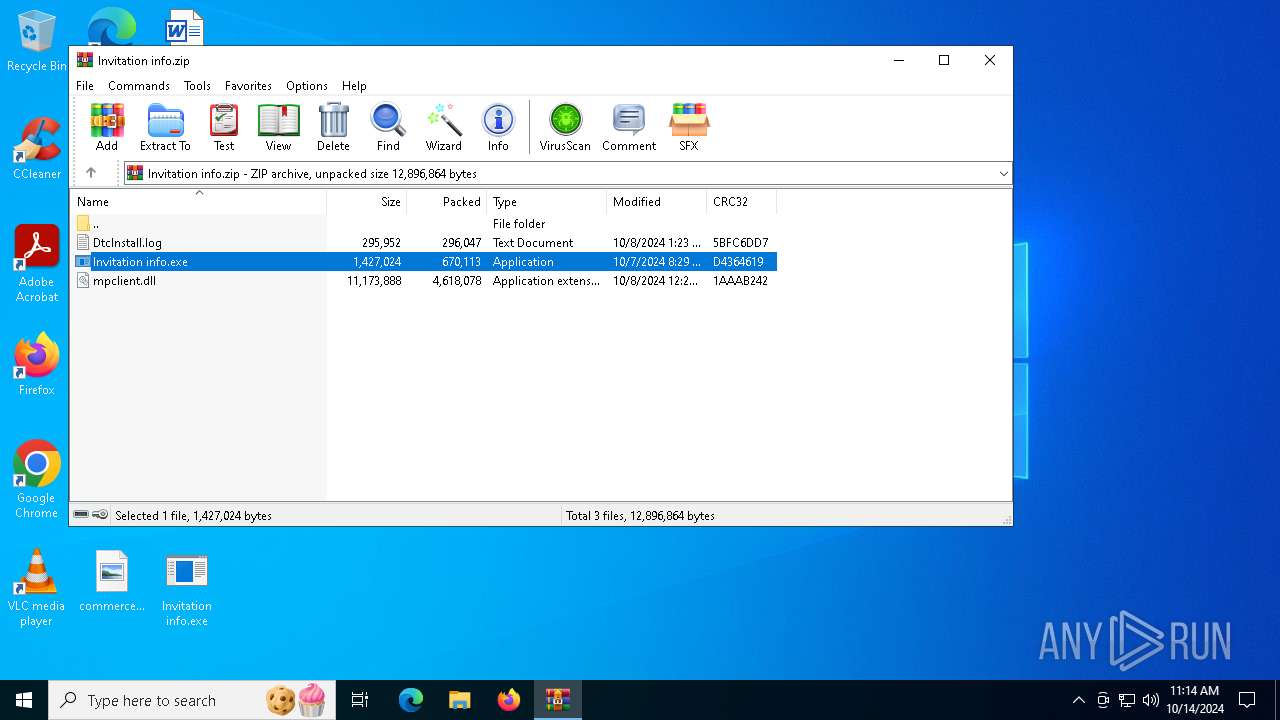
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 85EC534649A5EF894B9232CB11A211D3 |
| SHA1: | F48F82963FC2628CA693BC2A7D91903207AB3799 |
| SHA256: | 11E6B9F73916FC7D6ECE63305B659DEA5F6C0A295B607E009A067CCEC5D736BA |
| SSDEEP: | 98304:1SIGxity5v93NYLGD9vDOFwYP5a6rwi8FUN2j+gvEGaWz2vWTXRktbHgc48kM9Rf:4L9PZhl5FMmE |
MALICIOUS
COBALTSTRIKE has been detected (YARA)
- Invitation info.exe (PID: 7956)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 5832)
Starts a Microsoft application from unusual location
- Invitation info.exe (PID: 7956)
- Invitation info.exe (PID: 7736)
INFO
Manual execution by a user
- Invitation info.exe (PID: 7956)
- Invitation info.exe (PID: 7736)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
CobalStrike
(PID) Process(7956) Invitation info.exe
C2 (1)istockstrade.com/content/AAGaKjAdXwQxZOFTXPWLFbgS
BeaconTypeHTTPS
Port443
SleepTime48000
MaxGetSize6931528
Jitter29
PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCHBnzhpPnO7SsrNPrQuk/MJwJm
T/AOYittw02f8+yVoT/eGKkjCnIi3Wyi4iB/6GDkJBQH1mLoUdJgeoefP7ss006H
KZyHKff7BwHiNiI9+6HWyYKeaKvZJSFlM1Vm6NHSLjohDFDmE+4zMMOnr58YZDIQ
7dedARGfSMXb7Psh2wIDAQAB
-----END PUBLIC KEY-----
DNS_strategyrandom
DNS_strategy_rotate_seconds-1
DNS_strategy_fail_x-1
DNS_strategy_fail_seconds-1
SpawnTo00000000000000000000000000000000
Spawnto_x86%windir%\syswow64\WerFault.exe
Spawnto_x64%windir%\sysnative\WerFault.exe
CryptoScheme0
HttpGet_VerbGET
HttpPost_VerbGET
HttpPostChunk96
Watermark987654321
bStageCleanupTrue
bCFGCautionFalse
UserAgentMozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36 Edg/129.0.2792.79
HttpPostUri/received/36735adf456-65fadfa55-a7d67f5ad7a
Malleable_C2_InstructionsNetBIOS Encode 'a'
HttpGet_Metadata
ConstHeaders (2)Accept: */*
Cookie: MicrosoftApplicationsTelemetryDeviceId=95c18d8-4dce9854;ClientId=1C0F6C5D910F9;MSPAuth=3EkAjDKjI;xid=730bf7;wla42=MgRMqgT
ConstParams (1)path=/calendar
SessionId (2)netbios
parameter: wa
HttpPost_Metadata
ConstHeaders (1)Accept: */*
SessionId (7)netbios
prepend: wla42=
prepend: xid=730bf7;
prepend: MSPAuth=3EkAjDKjI;
prepend: ClientId=1C0F6C5D910F9;
prepend: MicrosoftApplicationsTelemetryDeviceId=95c18d8-4dce9854;
header: Cookie
Output (2)netbios
parameter: cx
bUsesCookies0001
Proxy_BehaviorUse IE settings
tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000
KillDate0-0-0
bProcInject_StartRWXTrue
bProcInject_UseRWXFalse
bProcInject_MinAllocSize8192
ProcInject_PrependAppend_x86909090909090909090..
ProcInject_PrependAppend_x64909090909090909090..
ProcInject_Stube43a1b63f09794f74d90a9889f7acb77
ProcInject_AllocationMethodNtMapViewOfSection
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:08 01:23:52 |
| ZipCRC: | 0x5bfc6dd7 |
| ZipCompressedSize: | 296047 |
| ZipUncompressedSize: | 295952 |
| ZipFileName: | DtcInstall.log |
Total processes
136
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5832 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Invitation info.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7736 | "C:\Users\admin\Desktop\Invitation info.exe" | C:\Users\admin\Desktop\Invitation info.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Antimalware Core Service Exit code: 3221225781 Version: 4.18.24070.5 (e798126f926dd886b32c6c109a80cc3baf14090c) Modules
| |||||||||||||||
| 7956 | "C:\Users\admin\Desktop\Invitation info.exe" | C:\Users\admin\Desktop\Invitation info.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Antimalware Core Service Version: 4.18.24070.5 (e798126f926dd886b32c6c109a80cc3baf14090c) Modules
CobalStrike(PID) Process(7956) Invitation info.exe C2 (1)istockstrade.com/content/AAGaKjAdXwQxZOFTXPWLFbgS BeaconTypeHTTPS Port443 SleepTime48000 MaxGetSize6931528 Jitter29 PublicKey-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCHBnzhpPnO7SsrNPrQuk/MJwJm
T/AOYittw02f8+yVoT/eGKkjCnIi3Wyi4iB/6GDkJBQH1mLoUdJgeoefP7ss006H
KZyHKff7BwHiNiI9+6HWyYKeaKvZJSFlM1Vm6NHSLjohDFDmE+4zMMOnr58YZDIQ
7dedARGfSMXb7Psh2wIDAQAB
-----END PUBLIC KEY----- DNS_strategyrandom DNS_strategy_rotate_seconds-1 DNS_strategy_fail_x-1 DNS_strategy_fail_seconds-1 SpawnTo00000000000000000000000000000000 Spawnto_x86%windir%\syswow64\WerFault.exe Spawnto_x64%windir%\sysnative\WerFault.exe CryptoScheme0 HttpGet_VerbGET HttpPost_VerbGET HttpPostChunk96 Watermark987654321 bStageCleanupTrue bCFGCautionFalse UserAgentMozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36 Edg/129.0.2792.79 HttpPostUri/received/36735adf456-65fadfa55-a7d67f5ad7a Malleable_C2_InstructionsNetBIOS Encode 'a' HttpGet_Metadata ConstHeaders (2)Accept: */* Cookie: MicrosoftApplicationsTelemetryDeviceId=95c18d8-4dce9854;ClientId=1C0F6C5D910F9;MSPAuth=3EkAjDKjI;xid=730bf7;wla42=MgRMqgT ConstParams (1)path=/calendar SessionId (2)netbios parameter: wa HttpPost_Metadata ConstHeaders (1)Accept: */* SessionId (7)netbios prepend: wla42= prepend: xid=730bf7; prepend: MSPAuth=3EkAjDKjI; prepend: ClientId=1C0F6C5D910F9; prepend: MicrosoftApplicationsTelemetryDeviceId=95c18d8-4dce9854; header: Cookie Output (2)netbios parameter: cx bUsesCookies0001 Proxy_BehaviorUse IE settings tcpFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 smbFrameHeader0004000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 KillDate0-0-0 bProcInject_StartRWXTrue bProcInject_UseRWXFalse bProcInject_MinAllocSize8192 ProcInject_PrependAppend_x86909090909090909090.. ProcInject_PrependAppend_x64909090909090909090.. ProcInject_Stube43a1b63f09794f74d90a9889f7acb77 ProcInject_AllocationMethodNtMapViewOfSection | |||||||||||||||
Total events
3 186
Read events
3 145
Write events
16
Delete events
25
Modification events
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Invitation info.zip | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (5832) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
4
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5832 | WinRAR.exe | C:\Users\admin\Desktop\DtcInstall.log | binary | |
MD5:B528999ADCCFE513BEFED18B7FD21E8F | SHA256:8D1CBEDB4468E2D1E8B0E5DEA1A87568E98F03B0F25E63D1BA91EBC86B15E2FB | |||
| 5832 | WinRAR.exe | C:\Users\admin\Desktop\Invitation info.exe | executable | |
MD5:02748A839DA6F702EA42DEC8EB32B648 | SHA256:B341D1EBB1413D5985E4B2E87BDBA4A4AAE7C1FFF85EC2CCB6EA948F40FFFA9D | |||
| 5832 | WinRAR.exe | C:\Users\admin\Downloads\Invitation info\Invitation info.exe | executable | |
MD5:02748A839DA6F702EA42DEC8EB32B648 | SHA256:B341D1EBB1413D5985E4B2E87BDBA4A4AAE7C1FFF85EC2CCB6EA948F40FFFA9D | |||
| 5832 | WinRAR.exe | C:\Users\admin\Downloads\Invitation info\DtcInstall.log | binary | |
MD5:B528999ADCCFE513BEFED18B7FD21E8F | SHA256:8D1CBEDB4468E2D1E8B0E5DEA1A87568E98F03B0F25E63D1BA91EBC86B15E2FB | |||
| 5832 | WinRAR.exe | C:\Users\admin\Downloads\Invitation info\mpclient.dll | executable | |
MD5:91549DF6F018A6F8BE3A92E83867BD82 | SHA256:C2FEF100A739E22F7E422819590700515410D41D8A173934035F5942D8ADF8BA | |||
| 5832 | WinRAR.exe | C:\Users\admin\Desktop\mpclient.dll | executable | |
MD5:91549DF6F018A6F8BE3A92E83867BD82 | SHA256:C2FEF100A739E22F7E422819590700515410D41D8A173934035F5942D8ADF8BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
69
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.81:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
632 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1168 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7472 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7472 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2444 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.81:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.186:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |