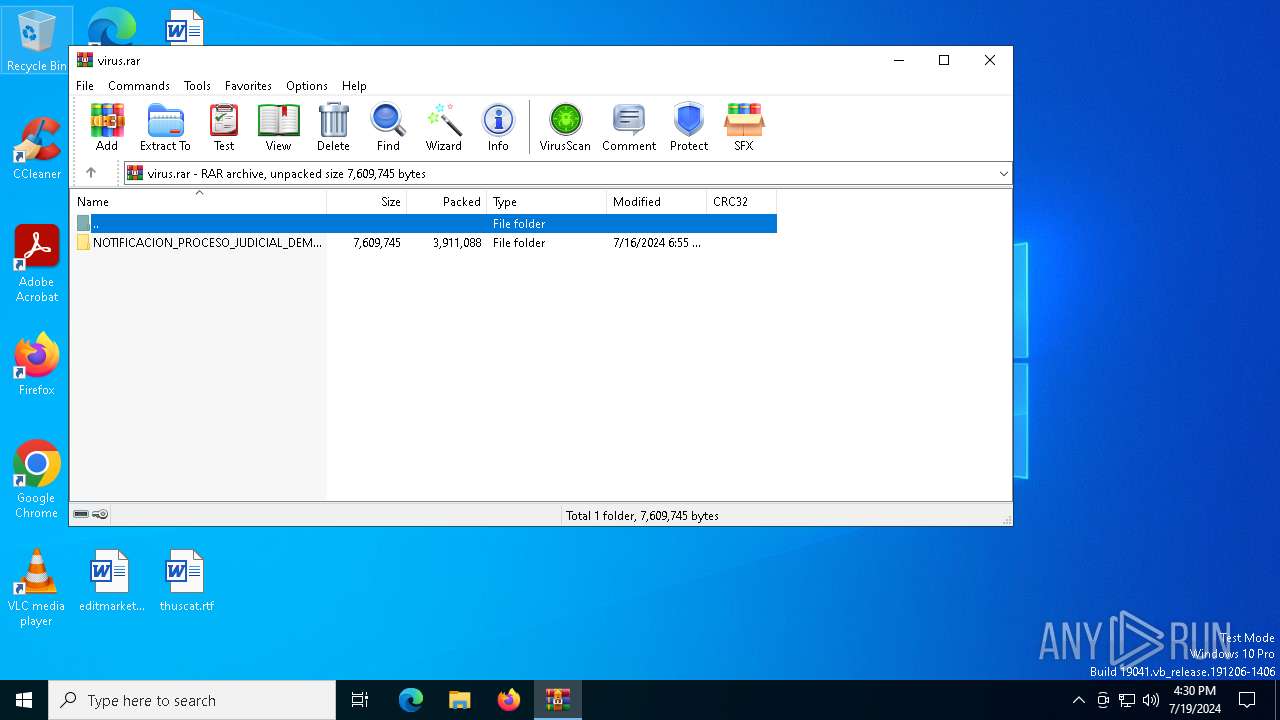
| File name: | virus.rar |
| Full analysis: | https://app.any.run/tasks/7388b0a5-3bf5-4c1e-8cb8-f12691b95068 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 19, 2024, 16:30:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DA913E56C16EFFDDC6C3B9041146FFA4 |
| SHA1: | A1AD230984C72E23D82CEC7893A3ABB3DF033D33 |
| SHA256: | 11CF35CA10BA07F602329C7ACBDCD76D5530DB731782038FE8931A8A78F4692F |
| SSDEEP: | 98304:m6ihjw2ZzjQlZ9xQO2t7J3un3vwdr7WzpTNyQgLHn8rNqOf3ke5aUEcrgdwY5fO8:Fvrq20s4 |
MALICIOUS
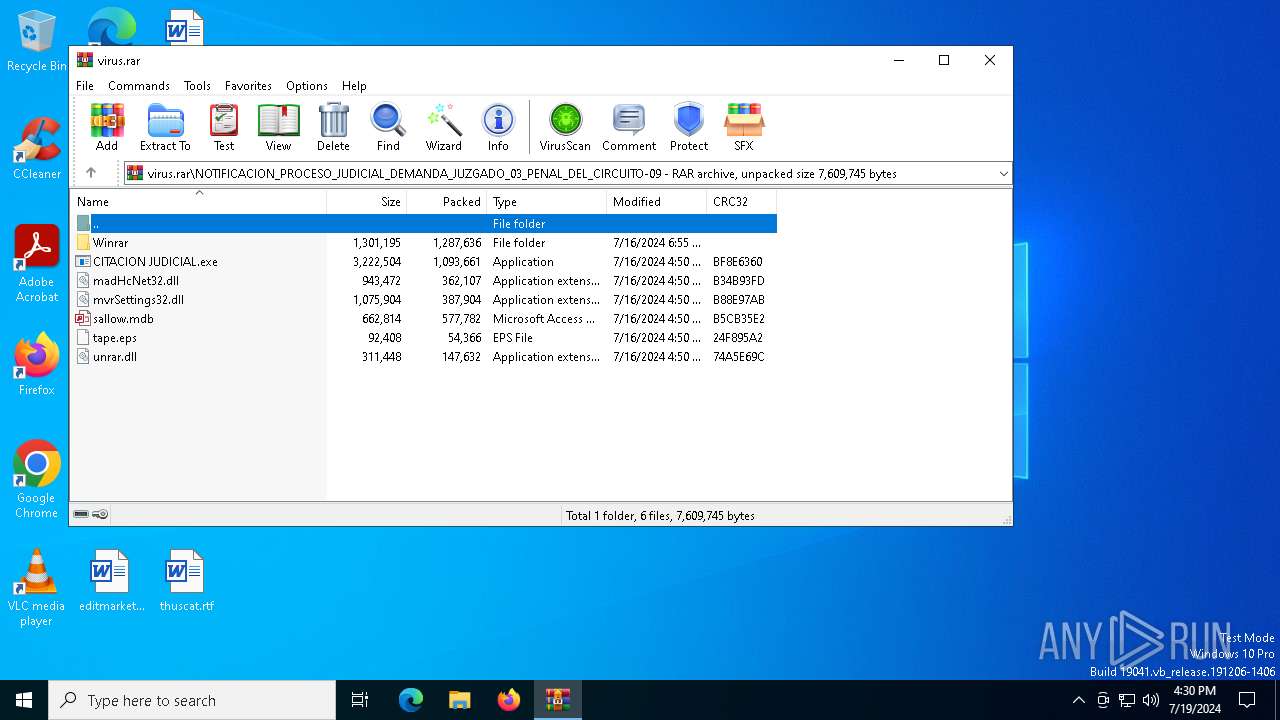
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1032)
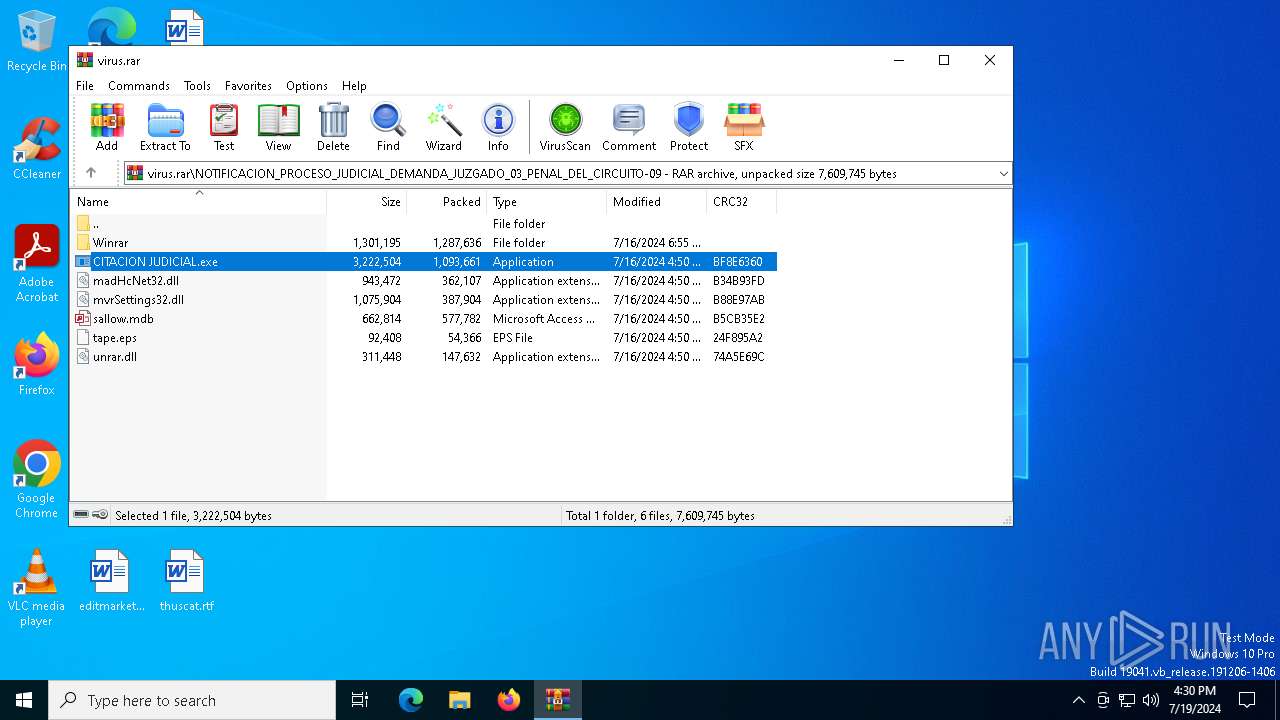
- CITACION JUDICIAL.exe (PID: 7244)
HIJACKLOADER has been detected (YARA)
- cmd.exe (PID: 5936)
ASYNCRAT has been detected (MUTEX)
- MSBuild.exe (PID: 5716)
ASYNCRAT has been detected (SURICATA)
- MSBuild.exe (PID: 5716)
ASYNCRAT has been detected (YARA)
- MSBuild.exe (PID: 5716)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 5716)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 1032)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1032)
Executable content was dropped or overwritten
- CITACION JUDICIAL.exe (PID: 7244)
Starts CMD.EXE for commands execution
- CITACION JUDICIAL.exe (PID: 7244)
Connects to unusual port
- MSBuild.exe (PID: 5716)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 5716)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1032)
Checks supported languages
- CITACION JUDICIAL.exe (PID: 7244)
- MSBuild.exe (PID: 5716)
Reads the computer name
- CITACION JUDICIAL.exe (PID: 7244)
- MSBuild.exe (PID: 5716)
Creates files or folders in the user directory
- CITACION JUDICIAL.exe (PID: 7244)
Create files in a temporary directory
- CITACION JUDICIAL.exe (PID: 7244)
Reads the machine GUID from the registry
- MSBuild.exe (PID: 5716)
Reads Environment values
- MSBuild.exe (PID: 5716)
Reads the software policy settings
- MSBuild.exe (PID: 5716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(5716) MSBuild.exe
C2 (1)enviofinal.kozow.com
Ports (1)5051
Version| CRACKED BY https://t.me/xworm_v2
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz...
Server_SignatureH6CC69VFwMAeB1cvASWt6n66/K+g9J9WhTbw+OrBeCfv67skFd/CgT2QnjYsCUql0QIxTmCtG3tsuNetF0yVkv3Cwyfv/JwuEIXyyNW5ci5YatXq+T4ZhhUYhDdslTs9jBvwwvmIT6IsmdCuIQrcaKV62atj42oUEx58oydjFtMdlTcsls7eduiXagYuIyjPzk2hMthfGPT/QI9GuaQdOgo6P9bPSQAod0ieGoaHZ+0rI04u2JFlYxJkxWi8S0ZYf+bj9zggBzI7cwsgxUYvTM9Jr/1xh/lZSNp/oKZtejOr...
Keys
AESb4ef162c5c2b8858870784bad86f90094ed07701ead952ef99d12b829999f7e8
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
145
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1032 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\virus.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2252 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5340 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5716 | C:\WINDOWS\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
AsyncRat(PID) Process(5716) MSBuild.exe C2 (1)enviofinal.kozow.com Ports (1)5051 Version| CRACKED BY https://t.me/xworm_v2 Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% Certificates Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz... Server_SignatureH6CC69VFwMAeB1cvASWt6n66/K+g9J9WhTbw+OrBeCfv67skFd/CgT2QnjYsCUql0QIxTmCtG3tsuNetF0yVkv3Cwyfv/JwuEIXyyNW5ci5YatXq+T4ZhhUYhDdslTs9jBvwwvmIT6IsmdCuIQrcaKV62atj42oUEx58oydjFtMdlTcsls7eduiXagYuIyjPzk2hMthfGPT/QI9GuaQdOgo6P9bPSQAod0ieGoaHZ+0rI04u2JFlYxJkxWi8S0ZYf+bj9zggBzI7cwsgxUYvTM9Jr/1xh/lZSNp/oKZtejOr... Keys AESb4ef162c5c2b8858870784bad86f90094ed07701ead952ef99d12b829999f7e8 Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 5936 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | CITACION JUDICIAL.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7244 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\CITACION JUDICIAL.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\CITACION JUDICIAL.exe | WinRAR.exe | ||||||||||||
User: admin Company: madshi.net Integrity Level: MEDIUM Description: mad* home cinema control Exit code: 1 Version: 1.1.21.0 Modules
| |||||||||||||||
Total events
12 989
Read events
12 973
Write events
16
Delete events
0
Modification events
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\virus.rar | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1032) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
8
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5936 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rlemqbdetih | — | |
MD5:— | SHA256:— | |||
| 1032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\CITACION JUDICIAL.exe | executable | |
MD5:B841D408448F2A07F308CED1589E7673 | SHA256:69A90665113BD73B30360D87F7F6ED2C789A90A67F3B6E86474E21273A64F699 | |||
| 1032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\mvrSettings32.dll | executable | |
MD5:D168F18B79F9F33690F011D1DEB1E7CF | SHA256:B7D3BC460A17E1B43C9FF09786E44EA4033710538BDB539400B55E5B80D0B338 | |||
| 7244 | CITACION JUDICIAL.exe | C:\Users\admin\AppData\Roaming\ScanExplore\unrar.dll | executable | |
MD5:851C9E8CE9F94457CC36B66678F52494 | SHA256:0891EDB0CC1C0208AF2E4BC65D6B5A7160642F89FD4B4DC321F79D2B5DFC2DCC | |||
| 1032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\sallow.mdb | binary | |
MD5:2556ACA0B94D623367029C5D5F89E98E | SHA256:B45A92A00018F7F4FE2C2C9FCC863292E232FC99CAA991D936ECF858692F69BF | |||
| 1032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\tape.eps | binary | |
MD5:10D8E1CB3CC0836EE187C96073C19DEA | SHA256:DF5BD65B747646A7CFD95DBD4F67C27F668E1023AFCB311CAF24C9A0FF2057C1 | |||
| 5936 | cmd.exe | C:\Users\admin\AppData\Local\Temp\kppenvrfdmq | binary | |
MD5:F68009F536C03818FC85A7992BEC21C6 | SHA256:51E2E3DDDD5EA1D13F536C3B062E0225485188363FC3E3AFD7FBA3745F485F66 | |||
| 7244 | CITACION JUDICIAL.exe | C:\Users\admin\AppData\Local\Temp\a410d7fe | binary | |
MD5:1C816B42D9D2F56BCA65552427ACC1FF | SHA256:767F88548656901934704220095DCBD2CC2C0EDA3AA71DA51F3E64DA16028E7A | |||
| 1032 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1032.43641\NOTIFICACION_PROCESO_JUDICIAL_DEMANDA_JUZGADO_03_PENAL_DEL_CIRCUITO-09\madHcNet32.dll | executable | |
MD5:2BA4099EB6FBAC4EAAE2D6DFE71B4E18 | SHA256:8BD3EDBF027972636BDB4CBB46037F0BE98CA233E19B003E860AF0BD7526A0AC | |||
| 7244 | CITACION JUDICIAL.exe | C:\Users\admin\AppData\Roaming\ScanExplore\madHcNet32.dll | executable | |
MD5:2BA4099EB6FBAC4EAAE2D6DFE71B4E18 | SHA256:8BD3EDBF027972636BDB4CBB46037F0BE98CA233E19B003E860AF0BD7526A0AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
33
DNS requests
15
Threats
6
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4716 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5620 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7856 | svchost.exe | 52.230.59.222:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | SG | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2760 | svchost.exe | 40.113.110.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6120 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6032 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
enviofinal.kozow.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.kozow .com Domain |
5716 | MSBuild.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
5716 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
5716 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
5716 | MSBuild.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report