| File name: | Virus.Win32.Pioneer.cz-1149019445bb47d59dabe8bd4b1941ce5fd212b5cbf3f647291affdaf56e2911.exe |
| Full analysis: | https://app.any.run/tasks/d6501093-517c-4bb7-8843-3f0062e08872 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | May 27, 2024, 21:57:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
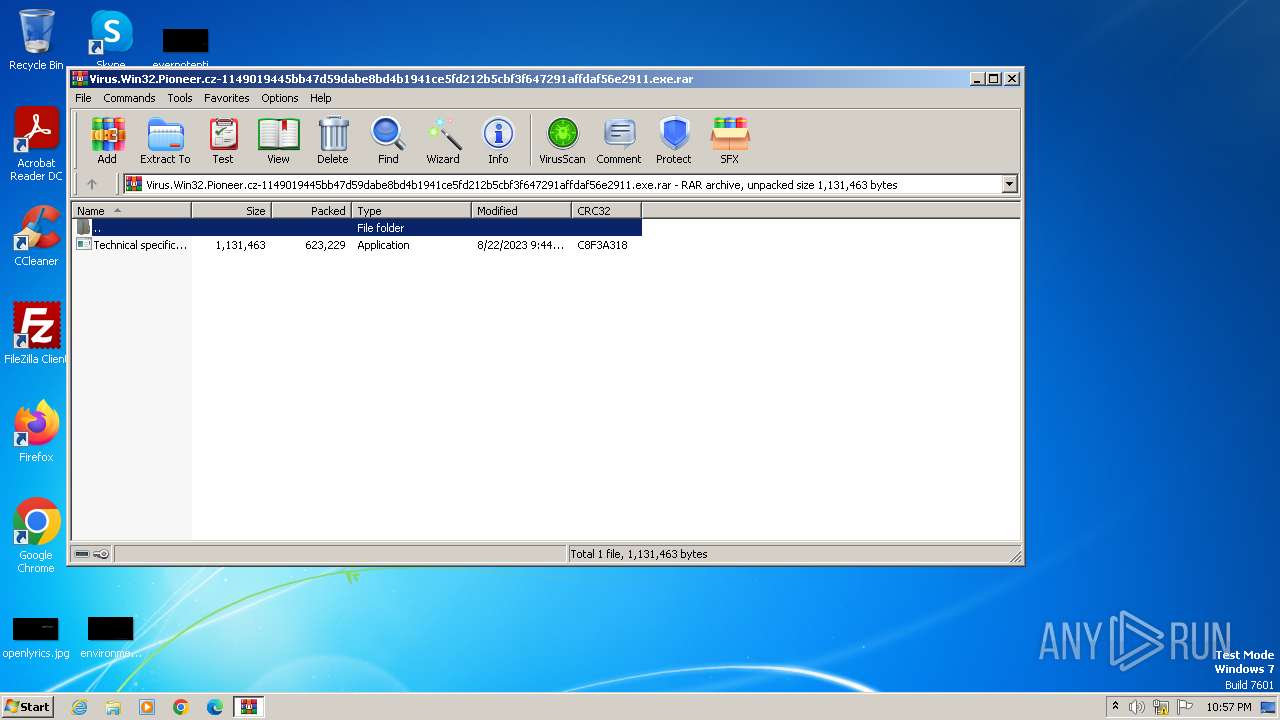
| File info: | RAR archive data, v5 |
| MD5: | C41F9CC04934AE12C91A902507D7307A |
| SHA1: | C42E84DD849588C45912E0185B1FAE01065EA6CF |
| SHA256: | 1149019445BB47D59DABE8BD4B1941CE5FD212B5CBF3F647291AFFDAF56E2911 |
| SSDEEP: | 24576:vVE4Rmj3XBNpqaFknZ9bCXDSXK/FvAvKBLcMJBGRiFE1K3lg7zKSOz:vVEImj3XBNcaFKbCXDSXK/FvAvKBLcM5 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3968)
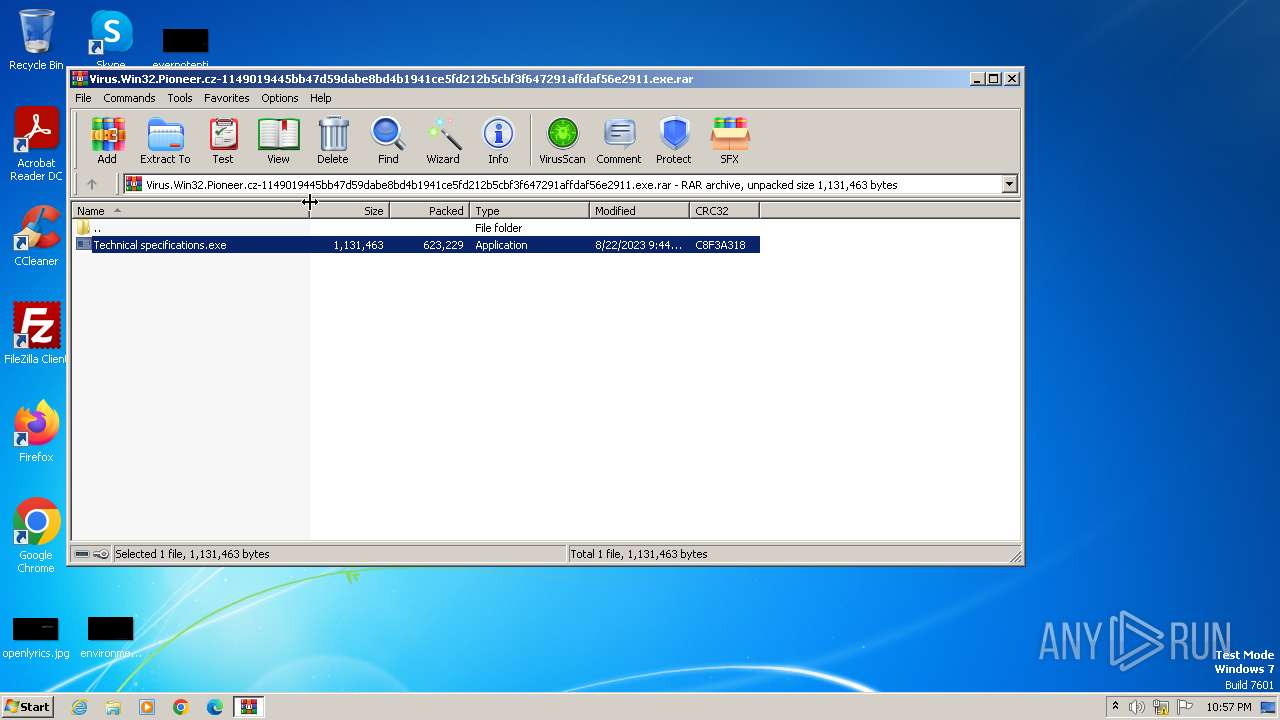
- Technical specifications.exe (PID: 4076)
DBATLOADER has been detected (YARA)
- Technical specifications.exe (PID: 4076)
SUSPICIOUS
Reads security settings of Internet Explorer
- Technical specifications.exe (PID: 4076)
Reads the Internet Settings
- Technical specifications.exe (PID: 4076)
Executable content was dropped or overwritten
- Technical specifications.exe (PID: 4076)
Process drops legitimate windows executable
- Technical specifications.exe (PID: 4076)
INFO
Manual execution by a user
- Technical specifications.exe (PID: 4076)
- wmpnscfg.exe (PID: 1292)
Checks supported languages
- Technical specifications.exe (PID: 4076)
- wmpnscfg.exe (PID: 1292)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3968)
Reads the machine GUID from the registry
- Technical specifications.exe (PID: 4076)
Reads the computer name
- Technical specifications.exe (PID: 4076)
- wmpnscfg.exe (PID: 1292)
Checks proxy server information
- Technical specifications.exe (PID: 4076)
Create files in a temporary directory
- Technical specifications.exe (PID: 4076)
Creates files or folders in the user directory
- Technical specifications.exe (PID: 4076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DBatLoader
(PID) Process(4076) Technical specifications.exe
C2 (1)https://balkancelikdovme.com/work/Elpuxpkilck
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1292 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Virus.Win32.Pioneer.cz-1149019445bb47d59dabe8bd4b1941ce5fd212b5cbf3f647291affdaf56e2911.exe.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\Desktop\Technical specifications.exe" | C:\Users\admin\Desktop\Technical specifications.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 250477278 Modules
DBatLoader(PID) Process(4076) Technical specifications.exe C2 (1)https://balkancelikdovme.com/work/Elpuxpkilck | |||||||||||||||
Total events
4 615
Read events
4 578
Write events
31
Delete events
6
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Virus.Win32.Pioneer.cz-1149019445bb47d59dabe8bd4b1941ce5fd212b5cbf3f647291affdaf56e2911.exe.rar | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4076 | Technical specifications.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\WinRAR\rarext.dll.tmp | executable | |
MD5:D4BE6E3B2AE52F1EFE3477FCE21C21C6 | SHA256:3143567621E84D92FCBFDCBB0B3E6D7E8A6DA1D190E9E4712D6C483F62F201CF | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3968.38716\Technical specifications.exe | executable | |
MD5:533B3DF0E597C50E1129EC807FD6BBCF | SHA256:8BF8B980381FD607EC9065BFBCD572973770EE77C815354A35455C10651516D5 | |||
| 4076 | Technical specifications.exe | C:\users\admin\appdata\local\temp\conres.dll.000 | text | |
MD5:1130C911BF5DB4B8F7CF9B6F4B457623 | SHA256:EBA08CC8182F379392A97F542B350EA0DBBE5E4009472F35AF20E3D857EAFDF1 | |||
| 4076 | Technical specifications.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\WinRAR\WinRAR.exe.tmp | executable | |
MD5:D625FF9198B367756C16A1B2C3D5146D | SHA256:99B0665C2A2EF19978C4CC81ECE53E8645478352E33455A217C86AB5D2EC3EEC | |||
| 4076 | Technical specifications.exe | C:\Users\admin\AppData\Local\Temp\conres.dll | executable | |
MD5:7574CF2C64F35161AB1292E2F532AABF | SHA256:DE055A89DE246E629A8694BDE18AF2B1605E4B9B493C7E4AEF669DD67ACF5085 | |||
| 4076 | Technical specifications.exe | C:\Users\admin\AppData\Local\VirtualStore\Program Files\FileZilla FTP Client\libgcc_s_dw2-1.dll.tmp | executable | |
MD5:E633478CA42462EE464B80F63E1B193C | SHA256:5315EAD7C29F28D9A2582139800EE64384CE844C8FD111831CA7096B0B782BF9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4076 | Technical specifications.exe | GET | 403 | 96.126.123.244:80 | http://www.aieov.com/logo.gif | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4076 | Technical specifications.exe | 96.126.123.244:80 | www.aieov.com | Linode, LLC | US | unknown |
4076 | Technical specifications.exe | 185.181.116.217:443 | balkancelikdovme.com | NTT Global Data Centers EMEA UK Ltd. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
5isohu.com |
| unknown |
www.aieov.com |
| unknown |
balkancelikdovme.com |
| unknown |
Threats
1 ETPRO signatures available at the full report