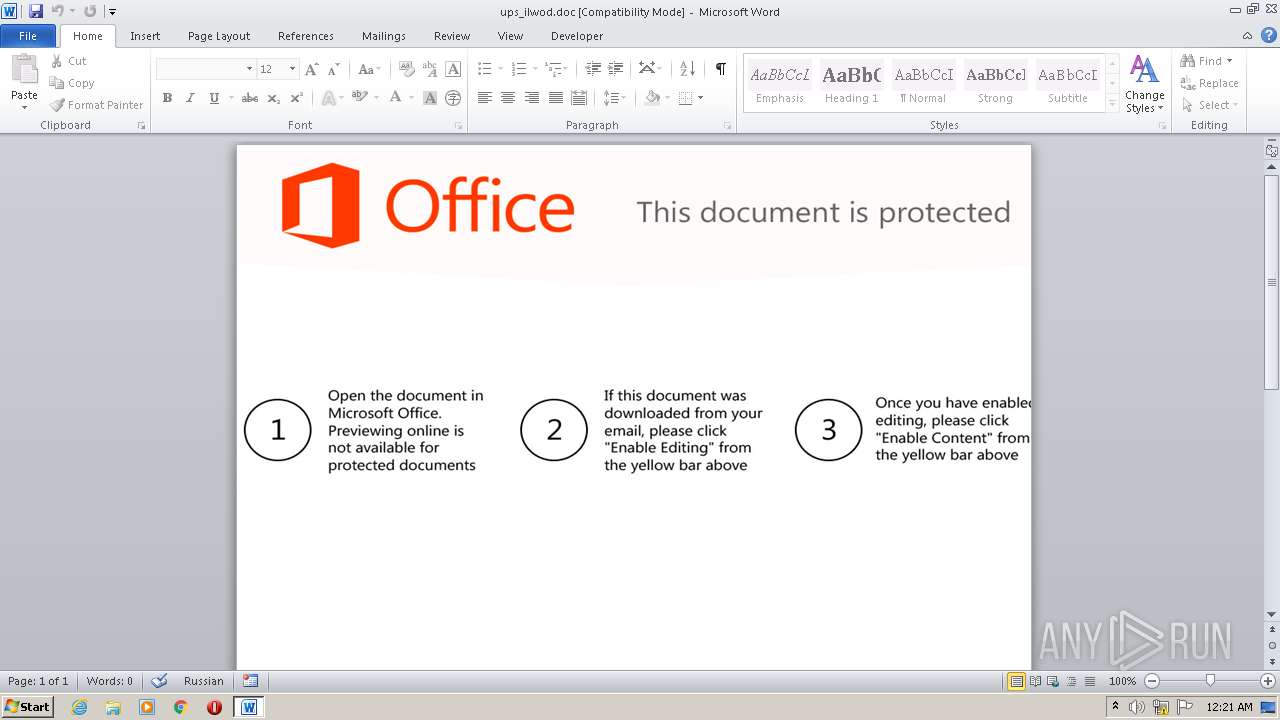
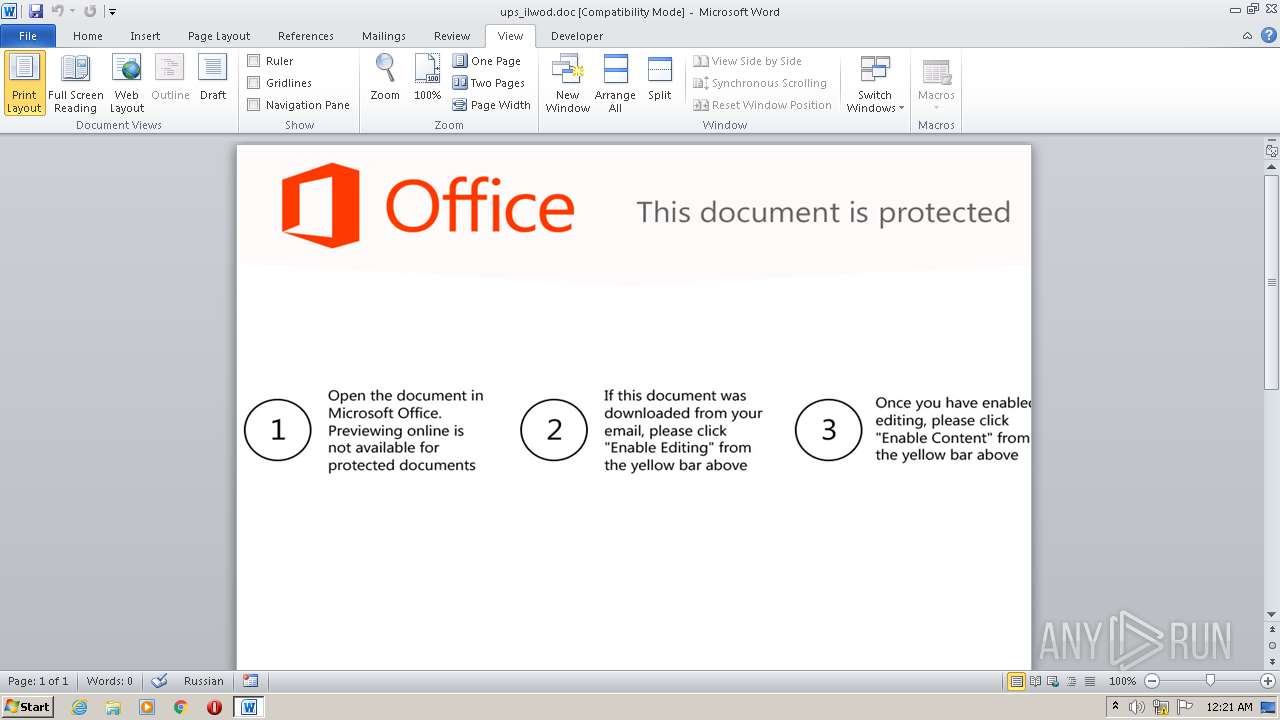
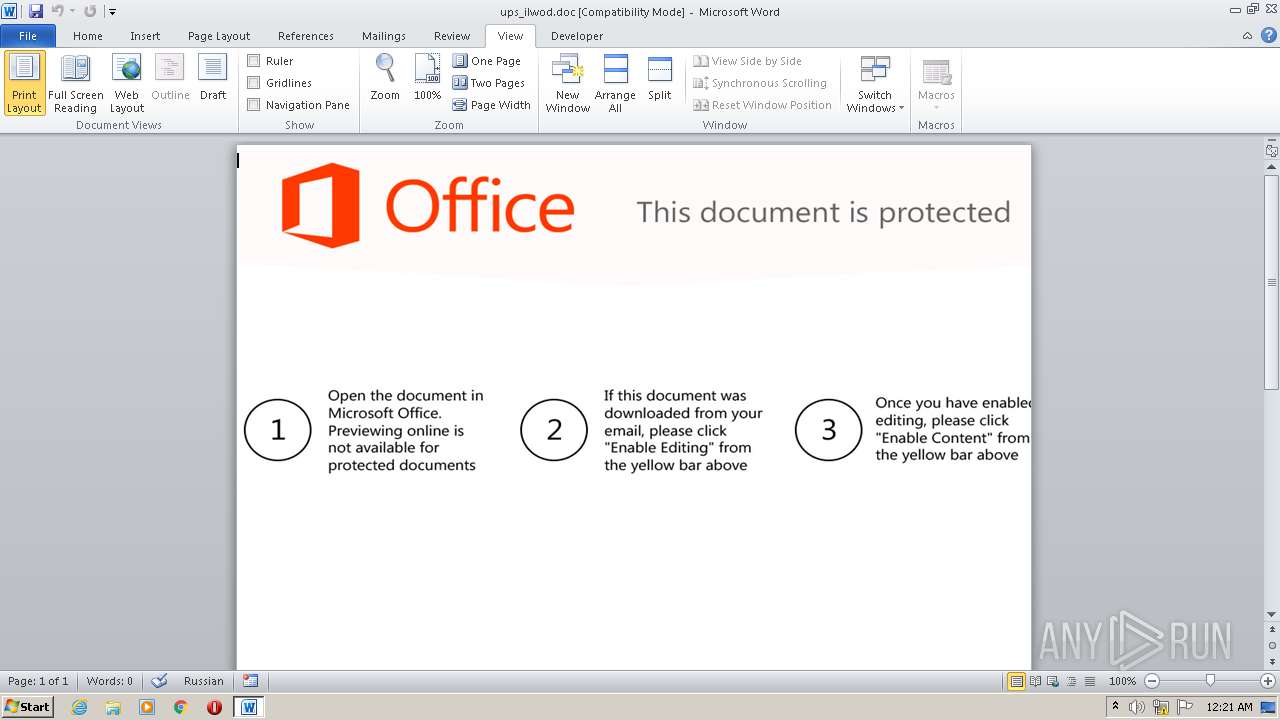
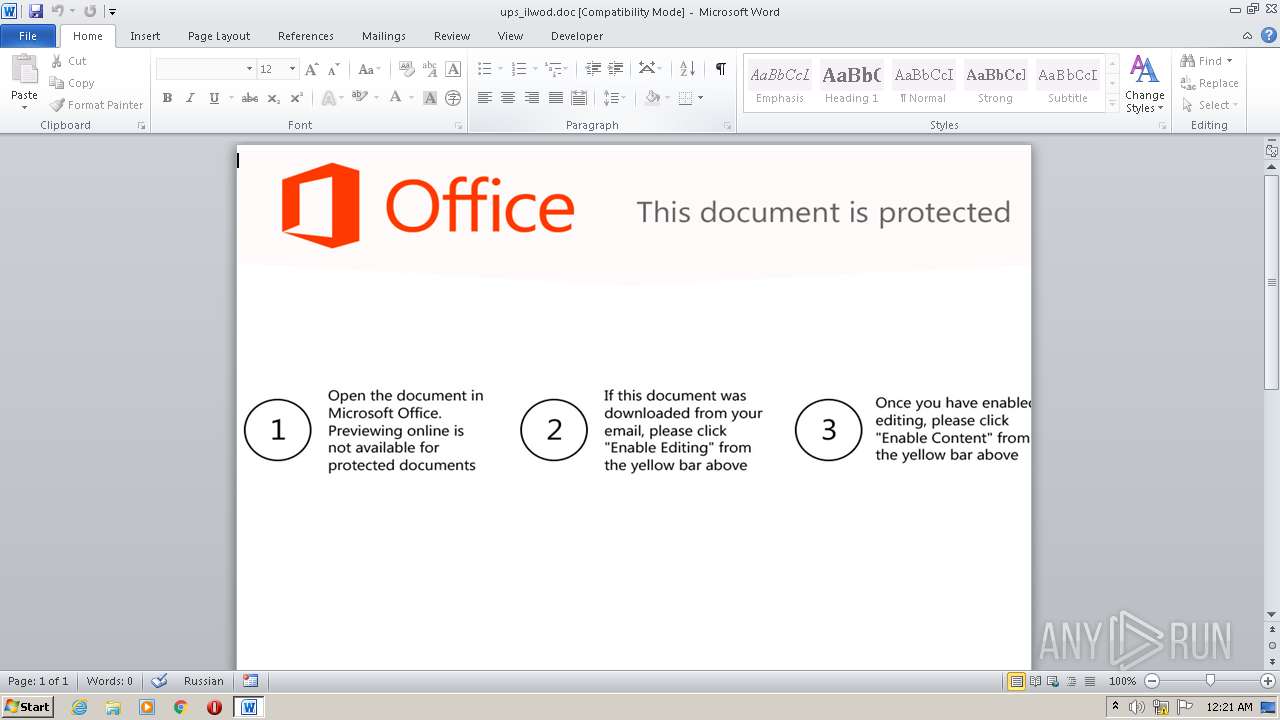
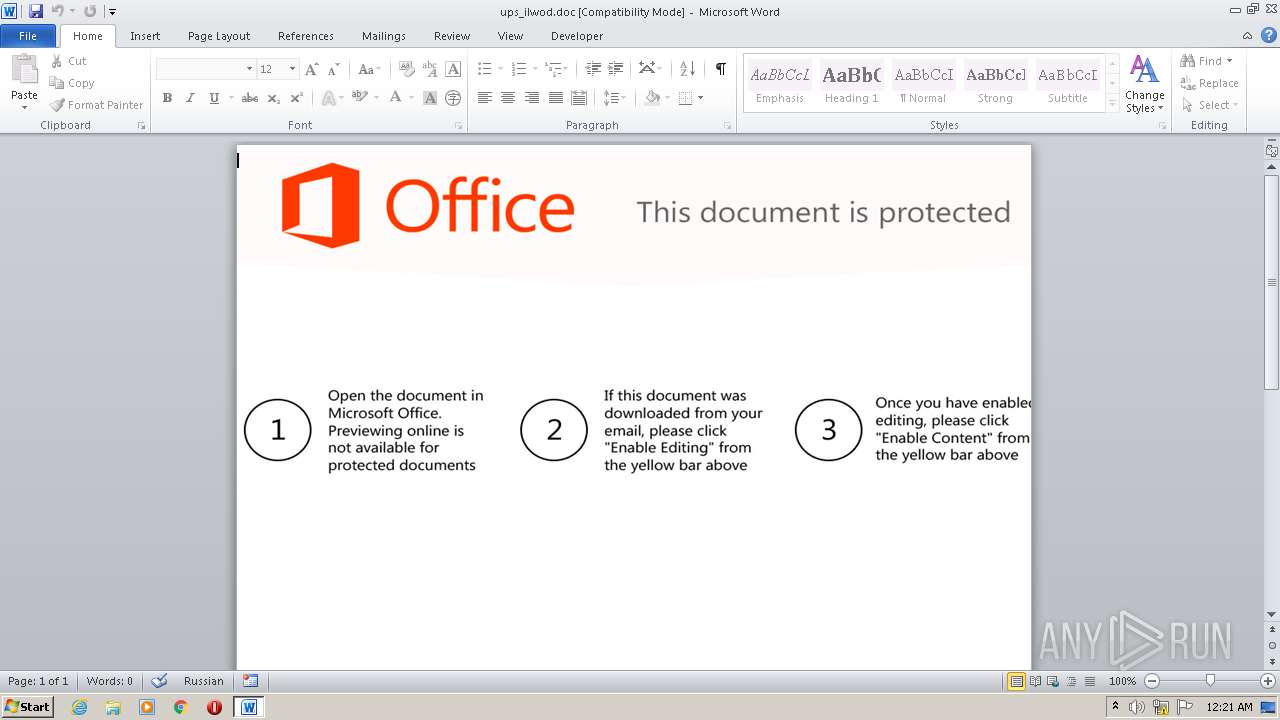
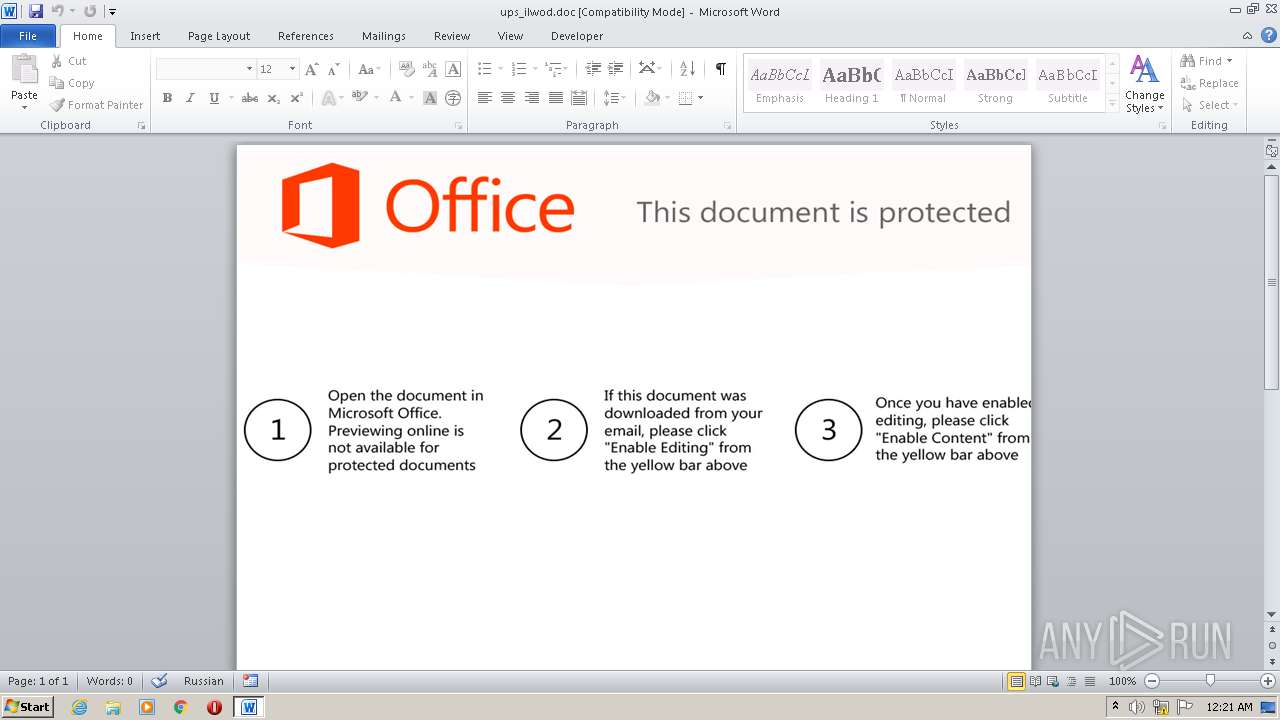
| File name: | ups_ilwod.doc |
| Full analysis: | https://app.any.run/tasks/8536731c-fbce-49be-9a09-689778b8e47b |
| Verdict: | Malicious activity |
| Threats: | Hancitor was created in 2014 to drop other malware on infected machines. It is also known as Tordal and Chanitor. This malware is available as a service which makes it accessible tools to criminals and contributes to the popularity of this virus. |
| Analysis date: | August 12, 2022, 23:21:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Title: , Author: Isabel, Template: Normal.dot, Last Saved By: Windows, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Thu Jan 12 13:32:00 2017, Last Saved Time/Date: Thu Jan 12 13:32:00 2017, Number of Pages: 1, Number of Words: 0, Number of Characters: 2, Security: 0 |
| MD5: | 38DB1BCF8EC66CA66B2936A48725144A |
| SHA1: | 5F8BCAE7410A194182ACB429605439DEA5BFDE61 |
| SHA256: | 1079376DD36788D51AB3385811484A7B0DB50F5926FFB4E2590DDD0DDA31E71B |
| SSDEEP: | 3072:3wjEWJXAOFkR2emjr27braMglbBDvjIrM:3wjZZHrKv69AM |
MALICIOUS
HANCITOR detected by memory dumps
- WINWORD.EXE (PID: 3160)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- WINWORD.EXE (PID: 3160)
Checks supported languages
- WINWORD.EXE (PID: 3160)
Searches for installed software
- WINWORD.EXE (PID: 3160)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| CompObjUserType: | ???????? Microsoft Office Word |
|---|---|
| CompObjUserTypeLen: | 31 |
| HeadingPairs: |
|
| TitleOfParts: | |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 11.5606 |
| CharCountWithSpaces: | 2 |
| Paragraphs: | 1 |
| Lines: | 1 |
| Bytes: | 11000 |
| Company: | |
| CodePage: | Windows Cyrillic |
| Security: | None |
| Characters: | 2 |
| Words: | - |
| Pages: | 1 |
| ModifyDate: | 2017:01:12 13:32:00 |
| CreateDate: | 2017:01:12 13:32:00 |
| TotalEditTime: | - |
| Software: | Microsoft Office Word |
| RevisionNumber: | 1 |
| LastModifiedBy: | Windows |
| Template: | Normal.dot |
| Comments: | - |
| Keywords: | - |
| Author: | Isabel |
| Subject: | - |
| Title: |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3160 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\ups_ilwod.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3596 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 259
Read events
2 761
Write events
270
Delete events
228
Modification events
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 649 |
Value: 36343900580C0000010000000000000000000000 | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR98B6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$s_ilwod.doc | pgc | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report