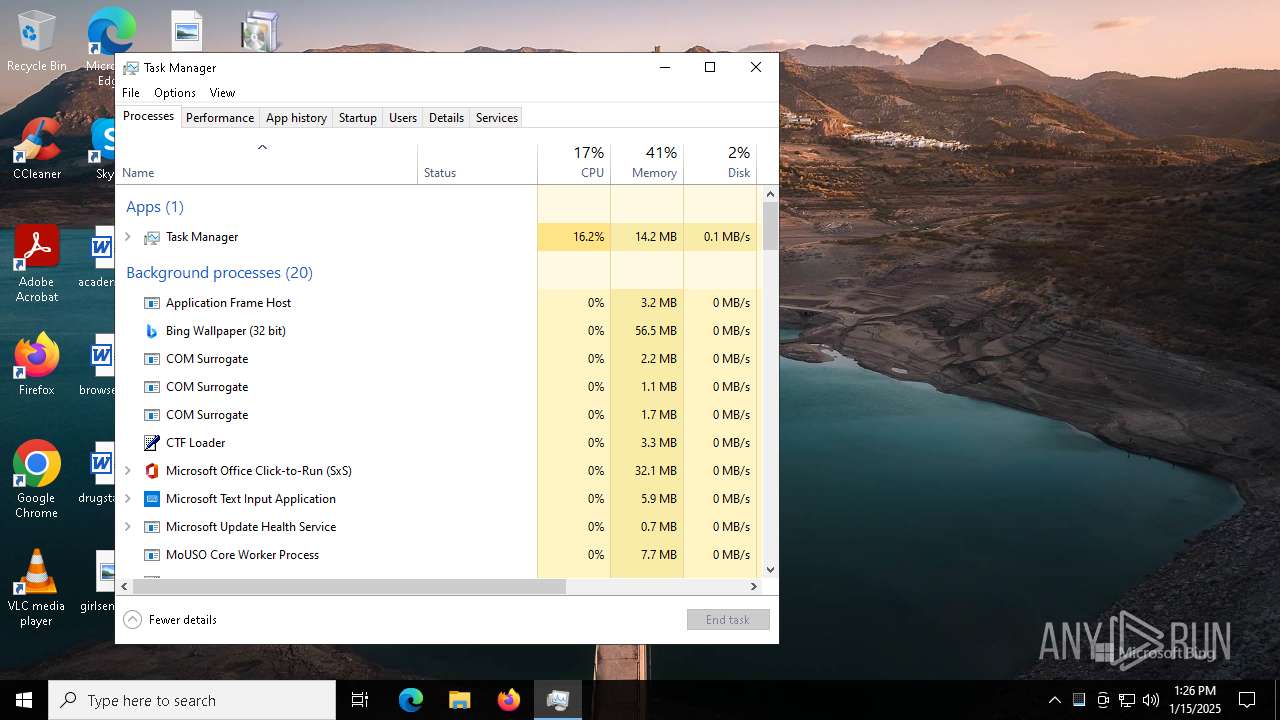
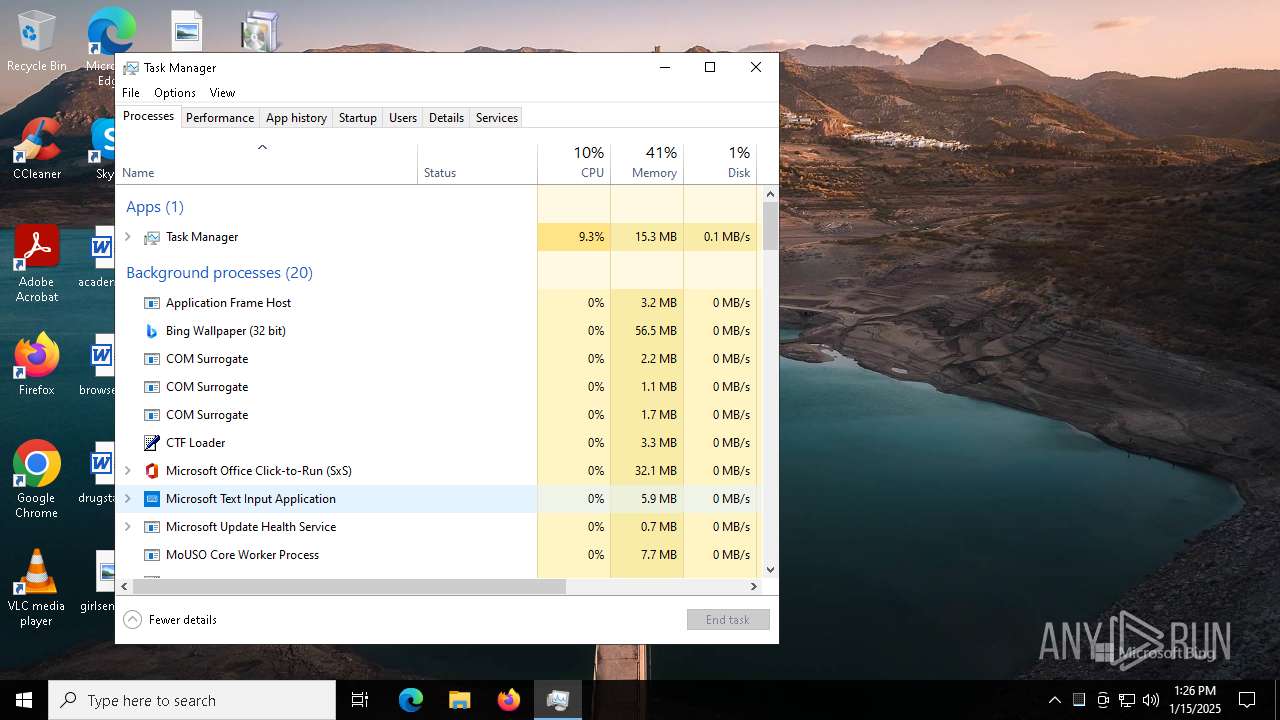
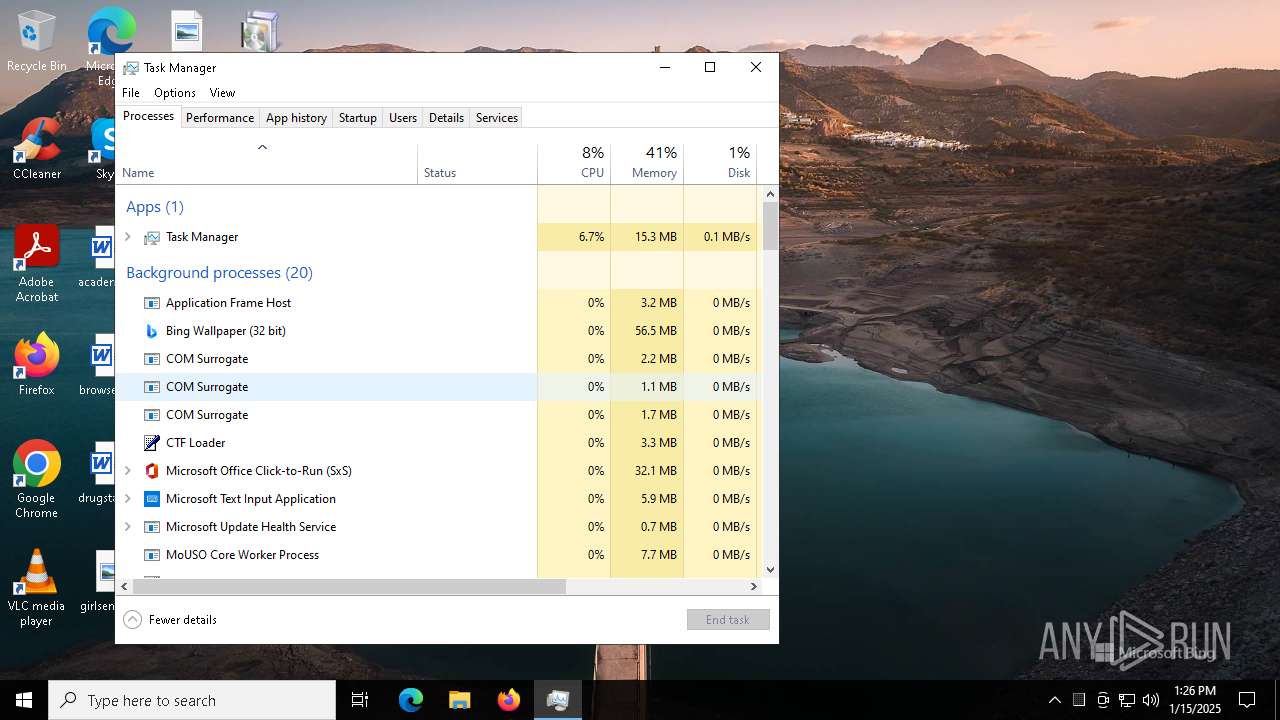
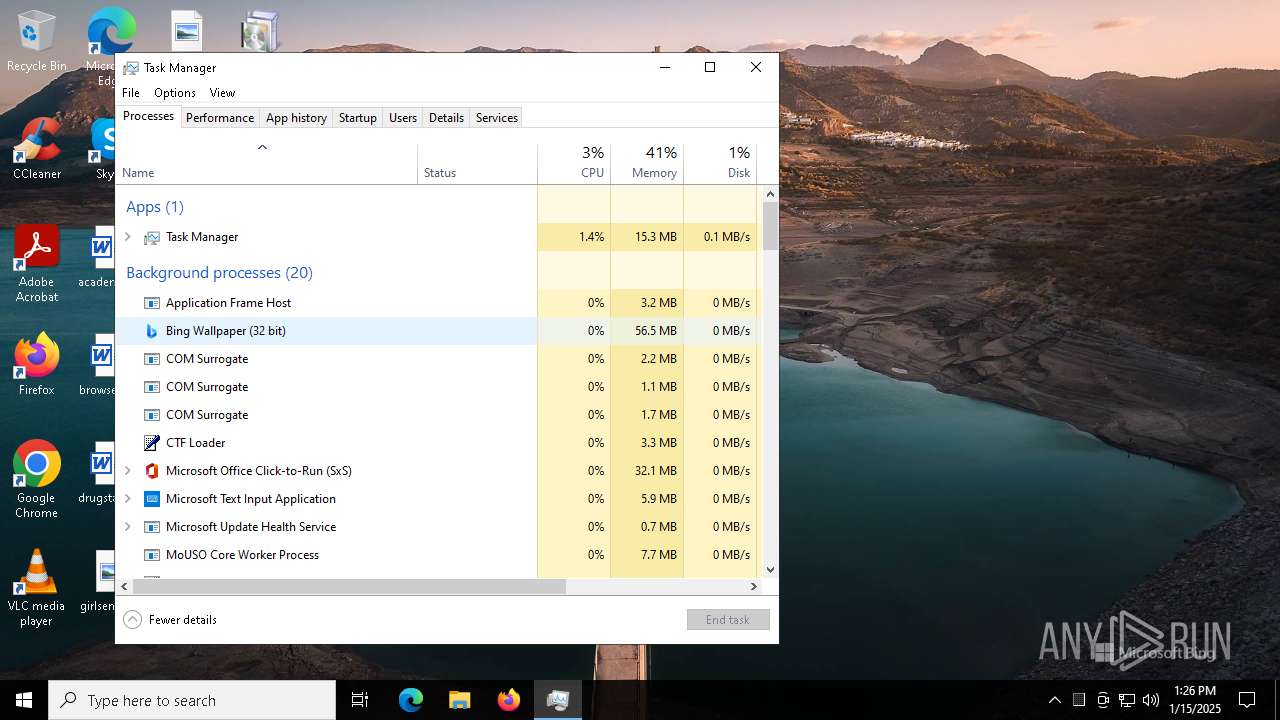
| download: | /BingWallPaperClientTest/2.0.1.4/BWCStartMSI.exe |
| Full analysis: | https://app.any.run/tasks/a1252ffb-3853-475d-89d3-b2777f975737 |
| Verdict: | Malicious activity |
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | January 15, 2025, 13:21:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 89D75B7846DB98111BE948830F9CF7C2 |
| SHA1: | 3771CBE04980AF3CDCA295DF79346456D1207051 |
| SHA256: | 1077F5FF5FC1C7B7CE347323D14BA387F43E9CFAB9808FA31A1CD3144FA05EF4 |
| SSDEEP: | 98304:An2E9XCwijxb+tbaIAXde7t2baQ7W/6wZZQE0gy2rUEEiQsfCnIZ+04WUmcduzJa:StK06s3fyMba6rirohmVQIgG |
MALICIOUS
REDLINE has been found (auto)
- BWCStartMSI.exe (PID: 6656)
Changes the autorun value in the registry
- msiexec.exe (PID: 6788)
Actions looks like stealing of personal data
- BingWallpaperApp.exe (PID: 6648)
SUSPICIOUS
Process drops legitimate windows executable
- BWCStartMSI.exe (PID: 6656)
- msiexec.exe (PID: 6788)
Starts a Microsoft application from unusual location
- BWCStartMSI.exe (PID: 6656)
- BWCStartMSI.exe (PID: 6688)
Executable content was dropped or overwritten
- BWCStartMSI.exe (PID: 6656)
- rundll32.exe (PID: 6336)
- rundll32.exe (PID: 6300)
- BingWallpaperApp.exe (PID: 6648)
Reads security settings of Internet Explorer
- BWCStartMSI.exe (PID: 6688)
Checks Windows Trust Settings
- msiexec.exe (PID: 6788)
Changes the desktop background image
- BingWallpaperApp.exe (PID: 6648)
Reads Mozilla Firefox installation path
- BingWallpaperApp.exe (PID: 6648)
INFO
Checks supported languages
- BWCStartMSI.exe (PID: 6656)
- BWCStartMSI.exe (PID: 6688)
- msiexec.exe (PID: 6788)
- msiexec.exe (PID: 2484)
- BingWallpaperApp.exe (PID: 6648)
The sample compiled with english language support
- BWCStartMSI.exe (PID: 6656)
- rundll32.exe (PID: 6336)
- rundll32.exe (PID: 6300)
- BingWallpaperApp.exe (PID: 6648)
Reads the computer name
- BWCStartMSI.exe (PID: 6688)
- msiexec.exe (PID: 6788)
- msiexec.exe (PID: 2484)
- BingWallpaperApp.exe (PID: 6648)
Create files in a temporary directory
- BWCStartMSI.exe (PID: 6656)
- rundll32.exe (PID: 6336)
- BingWallpaperApp.exe (PID: 6648)
- rundll32.exe (PID: 6300)
Creates files or folders in the user directory
- msiexec.exe (PID: 6788)
- BingWallpaperApp.exe (PID: 6648)
- rundll32.exe (PID: 6300)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6788)
- BingWallpaperApp.exe (PID: 6648)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6788)
The process uses the downloaded file
- rundll32.exe (PID: 6336)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 6336)
- rundll32.exe (PID: 6300)
Creates a software uninstall entry
- msiexec.exe (PID: 6788)
Reads the software policy settings
- msiexec.exe (PID: 6788)
Process checks computer location settings
- BingWallpaperApp.exe (PID: 6648)
- BWCStartMSI.exe (PID: 6688)
Disables trace logs
- BingWallpaperApp.exe (PID: 6648)
Manual execution by a user
- Taskmgr.exe (PID: 236)
- Taskmgr.exe (PID: 1580)
Checks proxy server information
- BingWallpaperApp.exe (PID: 6648)
- rundll32.exe (PID: 6300)
Confuser has been detected (YARA)
- BingWallpaperApp.exe (PID: 6648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2000:11:24 11:50:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.2 |
| CodeSize: | 25600 |
| InitializedDataSize: | 8506880 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a00 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.1.4 |
| ProductVersionNumber: | 2.0.1.4 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | BWCStartMSI |
| FileVersion: | 2.0.1.4 |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | BWCStartMSI |
| ProductVersion: | 2.0.1.4 |
Total processes
139
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1580 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | C:\Windows\syswow64\MsiExec.exe -Embedding 1AD751D242DC5D186152BAE0E6D26289 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6300 | rundll32.exe "C:\WINDOWS\Installer\MSI795C.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1276281 8 CustomActions!CustomActions.CustomActions.InstallPing | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6336 | rundll32.exe "C:\WINDOWS\Installer\MSI76AB.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1275640 2 CustomActions!CustomActions.CustomActions.StartApp | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6648 | "C:\Users\admin\AppData\Local\Microsoft\BingWallpaperApp\BingWallpaperApp.exe" | C:\Users\admin\AppData\Local\Microsoft\BingWallpaperApp\BingWallpaperApp.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Bing Wallpaper Version: 2.0.1.4 Modules
| |||||||||||||||
| 6656 | "C:\Users\admin\Desktop\BWCStartMSI.exe" | C:\Users\admin\Desktop\BWCStartMSI.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BWCStartMSI Exit code: 0 Version: 2.0.1.4 Modules
| |||||||||||||||
| 6688 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\BWCStartMSI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\BWCStartMSI.exe | — | BWCStartMSI.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BWCStartMSI Exit code: 0 Version: 2.0.1.4 Modules
| |||||||||||||||
| 6756 | "C:\Windows\System32\msiexec.exe" /q /i BWCInstaller.msi /norestart | C:\Windows\SysWOW64\msiexec.exe | — | BWCStartMSI.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6788 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 620
Read events
13 481
Write events
129
Delete events
10
Modification events
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 841A0000F5DF646C5067DB01 | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 51278E0F6AA7CE343250A37DFC21235FD9EE2E91A890882E7B72B570A3CB64AF | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\136e40.rbs |
Value: 31156048 | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\136e40.rbsLow |
Value: | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\E75EB4F5223116D48A5EDF60E49565E9 |
| Operation: | write | Name: | 1499D042364BC9B44B38179247B0A91C |
Value: 01:\Software\Microsoft\BingWallpaperApp\isMSIInstalled | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\810C749B0985F6E428196CE616BCA73E |
| Operation: | write | Name: | 1499D042364BC9B44B38179247B0A91C |
Value: 01:\Software\Microsoft\BingWallpaperApp\isMSIInstalled | |||
| (PID) Process: | (6788) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\9BC0DD7D0D606B5438AEAEB5EB52DB88 |
| Operation: | write | Name: | 1499D042364BC9B44B38179247B0A91C |
Value: 01:\Software\Microsoft\BingWallpaperApp\isMSIInstalled | |||
Executable files
13
Suspicious files
25
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6656 | BWCStartMSI.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\BWCInstaller.msi | — | |
MD5:— | SHA256:— | |||
| 6788 | msiexec.exe | C:\Windows\Installer\136e3e.msi | — | |
MD5:— | SHA256:— | |||
| 6788 | msiexec.exe | C:\Windows\Installer\136e41.msi | — | |
MD5:— | SHA256:— | |||
| 6788 | msiexec.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Bing Wallpaper.lnk | binary | |
MD5:8F922CE99BEA7083B2E4DAC555BE31B3 | SHA256:EA5CD56C9AB551606A39DB5F8E6243BDFC1901CAE13440C56E8FBCB0F8CBF7F8 | |||
| 6788 | msiexec.exe | C:\Windows\Installer\MSI7497.tmp | binary | |
MD5:681D7B2C4B3DFD928F80AC40D609BEA0 | SHA256:A6ECAEE8EA8E96D81F34A7E6EF18472CB3C5E1B6119E8E0E85ED5FFC9DD283AE | |||
| 6788 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:D74F937FF9E54249A4647AB5C44EED1B | SHA256:C98DE8B42D20F4EEFB4499A9D587F73761DDA80F940B2E58F9A404AEA3F0369A | |||
| 6788 | msiexec.exe | C:\Users\admin\AppData\Local\Microsoft\BingWallpaperApp\BingWallpaperApp.exe | executable | |
MD5:5DDF6C0675019C3A758236D0DB069D15 | SHA256:D9395E5D508E683DAEBFBC485B45249BD20C46A596AEFAE839F508C4A8C05F3F | |||
| 6788 | msiexec.exe | C:\Windows\Temp\~DF69B9E2BA6E4FBE6B.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6788 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0018BB1B5834735BFA60CD063B31956 | binary | |
MD5:1EA27366E034EB9447A33CE639C01489 | SHA256:788D210EF206A4D11B6B506BF52124EE03FCA4E8A9389FAD43772202A7E29452 | |||
| 6788 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:ACF70A82BEB5B4B18E6092B77926F22F | SHA256:C495FEEFBB2E2D126BECE0AED210D3379A408B4206D3BB1531DAA446F515EE72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
40
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.74:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6300 | rundll32.exe | GET | 200 | 20.41.62.11:80 | http://g.ceipmsn.com/8SE/44?MI=A2B1304A099FCC44AA1F7189599853B6&LV=10.0.19041.3636&OS=10.0.19045.1&TE=40&TV=isW000%7cpkBingWallpaper%7ctmen-us%7cvr2.0.1.4%7cat1%7crt1%7cpt2 | unknown | — | — | unknown |
6788 | msiexec.exe | GET | 200 | 2.16.164.58:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6788 | msiexec.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6648 | BingWallpaperApp.exe | GET | 200 | 20.41.62.11:80 | http://g.ceipmsn.com/8SE/44?MI=A2B1304A099FCC44AA1F7189599853B6&LV=2.0.1.4&OS=10.0.19045.1&TE=40&TV=isW000%7cpkBingWallpaper%7ctmen-us%7cmo%3dMCwxMjgweDcyMA%253D%253D%7cvr2.0.1.4%7cpt6 | unknown | — | — | unknown |
6488 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6924 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.23.227.199:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.74:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3220 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
g.ceipmsn.com |
| unknown |
bingwallpaper.microsoft.com |
| whitelisted |
bingwallpaperimages.azureedge.net |
| whitelisted |