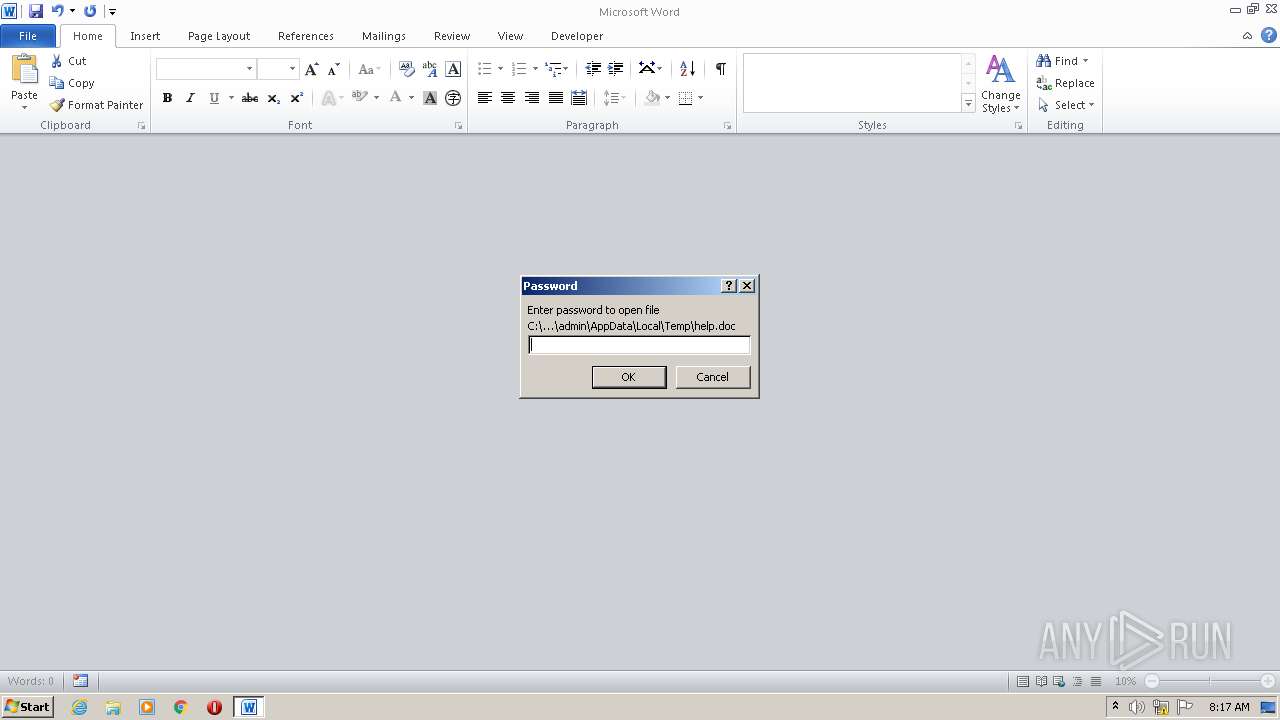
| File name: | help.doc |
| Full analysis: | https://app.any.run/tasks/c9e51f6a-4e3c-462f-9305-e8ea6ee6595b |
| Verdict: | Malicious activity |
| Threats: | Hancitor was created in 2014 to drop other malware on infected machines. It is also known as Tordal and Chanitor. This malware is available as a service which makes it accessible tools to criminals and contributes to the popularity of this virus. |
| Analysis date: | August 02, 2022, 07:17:00 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | B259E7D25E95EE65052D6DB146BCFE24 |
| SHA1: | B788506181233087E4AFF0CAFF8755E2C32733EF |
| SHA256: | 106A02E6E6452320F7F5425DBFBC8B126AC331D3C758417B08AB80B8AAA91846 |
| SSDEEP: | 1536:lePhCq5vJl18xTGz9MGMd+w3YwRxU+0gB0U/ymYomGgekV5f6Rfy6YP9+bnLMQ4E:gZvVMTGZMLLxNztymYLek+j08bLMQAd |
MALICIOUS
Drops executable file immediately after starts
- WINWORD.EXE (PID: 3160)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 3160)
Loads dropped or rewritten executable
- rundll32.exe (PID: 3888)
HANCITOR detected by memory dumps
- rundll32.exe (PID: 3888)
SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 968)
- cmd.exe (PID: 1716)
Drops a file with a compile date too recent
- WINWORD.EXE (PID: 3160)
Application launched itself
- cmd.exe (PID: 968)
Checks for external IP
- rundll32.exe (PID: 3888)
INFO
Checks supported languages
- WINWORD.EXE (PID: 3160)
- PING.EXE (PID: 2332)
- PING.EXE (PID: 1572)
- rundll32.exe (PID: 3888)
Reads the computer name
- WINWORD.EXE (PID: 3160)
- PING.EXE (PID: 2332)
- PING.EXE (PID: 1572)
- rundll32.exe (PID: 3888)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Hancitor
(PID) Process(3888) rundll32.exe
Hosts (3)http://hiltustra.com/9/forum.php
http://corelince.ru/9/forum.php
http://mernwel.ru/9/forum.php
Hosts (3)http://hiltustra.com/9/forum.php
http://corelince.ru/9/forum.php
http://mernwel.ru/9/forum.php
Total processes
41
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 968 | cmd.exe /c cd c:\users\admin\appdata\roaming\microsoft\templates && ping localhost -n 10 && c:\users\admin\appdata\roaming\microsoft\templates/1.bat | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1572 | ping localhost -n 10 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1716 | cmd.exe /c ping localhost -n 10 | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2332 | ping localhost -n 10 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3160 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\help.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3888 | rundll32.exe iff.bin,WCWGVXGWTDGAWLW | C:\Windows\system32\rundll32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Hancitor(PID) Process(3888) rundll32.exe Hosts (3)http://hiltustra.com/9/forum.php http://corelince.ru/9/forum.php http://mernwel.ru/9/forum.php (PID) Process(3888) rundll32.exe Hosts (3)http://hiltustra.com/9/forum.php http://corelince.ru/9/forum.php http://mernwel.ru/9/forum.php | |||||||||||||||
Total events
3 173
Read events
3 056
Write events
91
Delete events
26
Modification events
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | >"> |
Value: 3E223E00580C0000010000000000000000000000 | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3160) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
5
Text files
2
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR42BE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFB8E17B4D58F24700.TMP | binary | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DFD1640731C2C8F0B0.TMP | binary | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF7EA3B2954B6AA735.TMP | binary | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6BE8D99C.emf | emf | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\if.bin | executable | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\users\admin\appdata\roaming\microsoft\templates\1.bat | text | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$help.doc | pgc | |
MD5:— | SHA256:— | |||
| 3160 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF96161EE0821B3D7F.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
13
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3888 | rundll32.exe | GET | 200 | 3.232.242.170:80 | http://api.ipify.org/ | US | text | 13 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 3.232.242.170:80 | api.ipify.org | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.ipify.org |
| shared |
hiltustra.com |
| malicious |
dns.msftncsi.com |
| shared |
corelince.ru |
| unknown |
mernwel.ru |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3888 | rundll32.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup api.ipify.org |