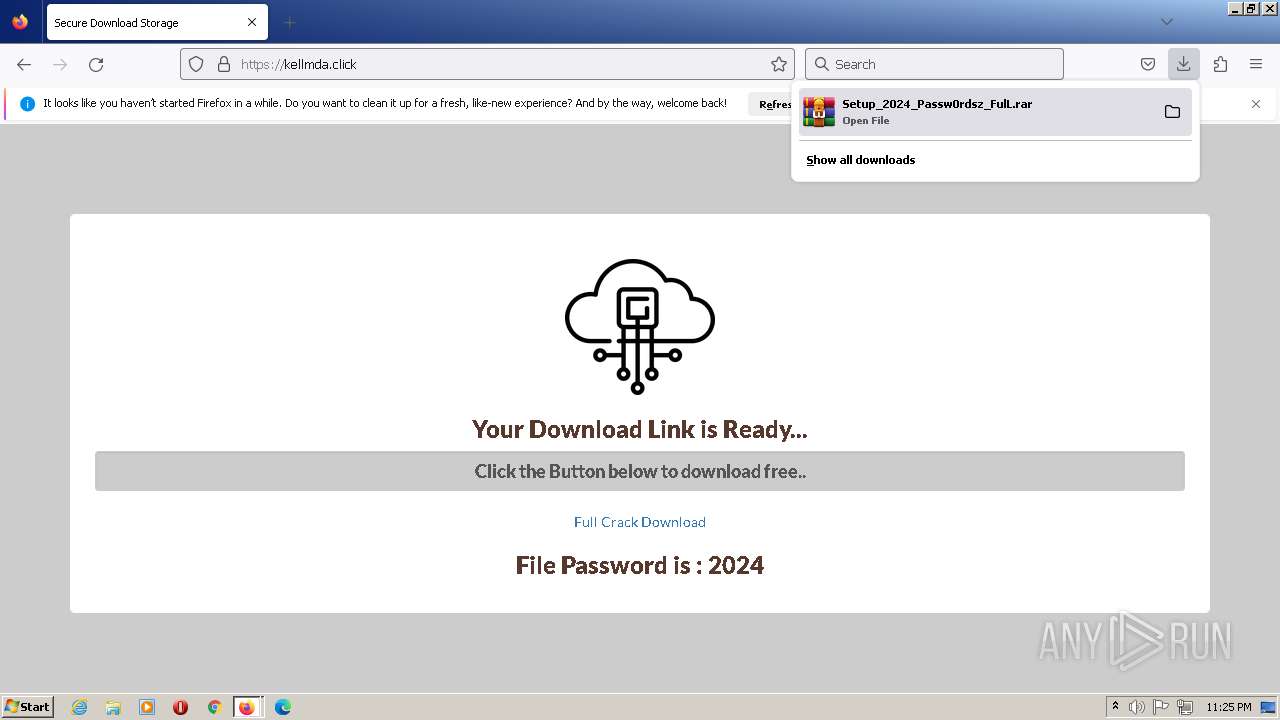
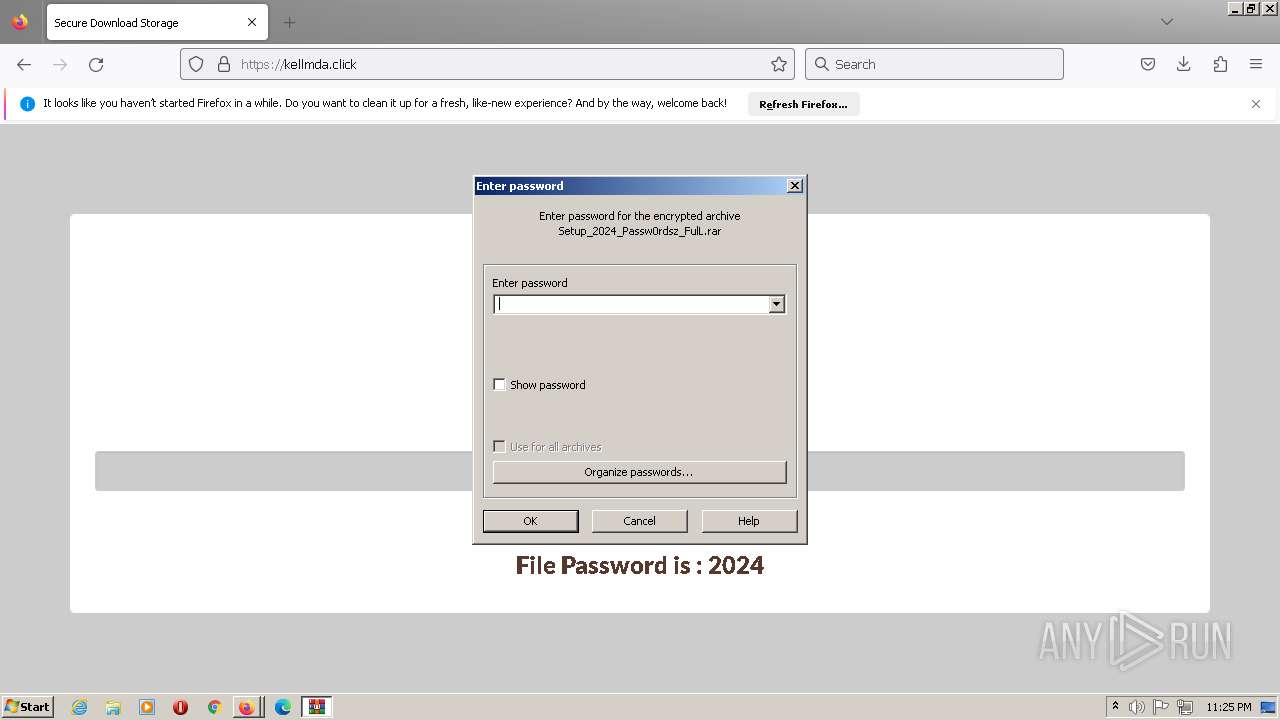
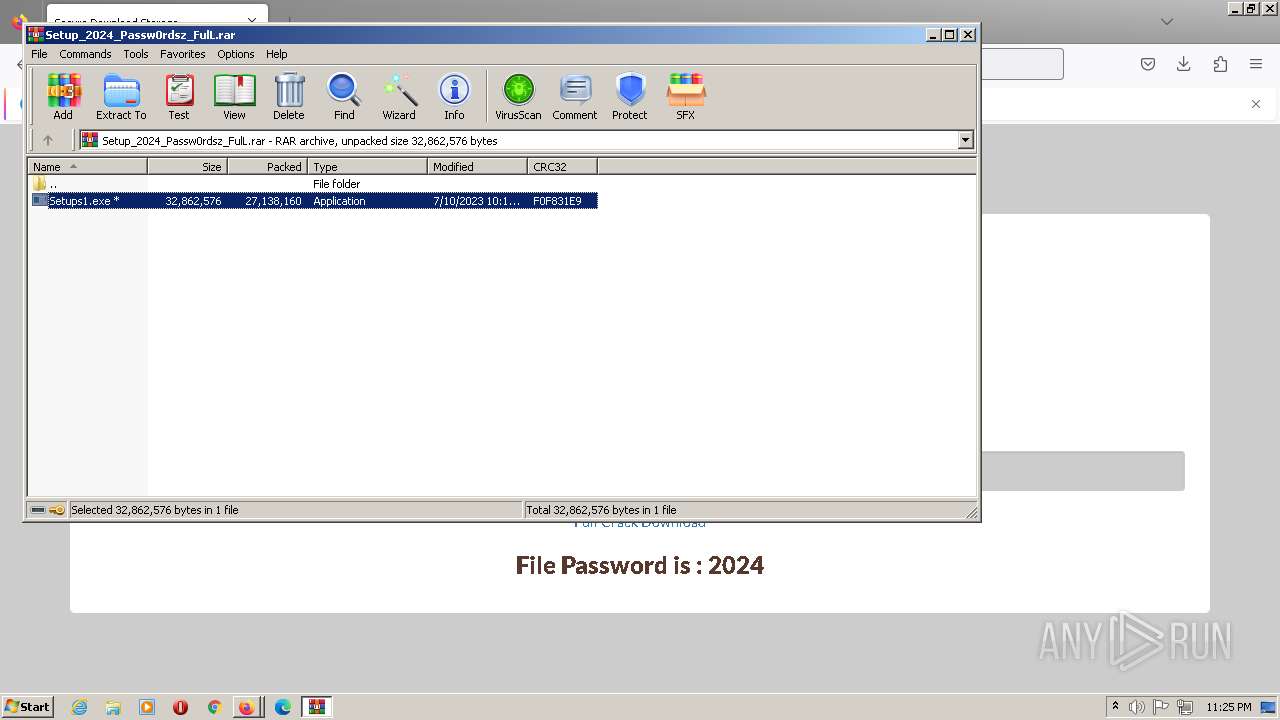
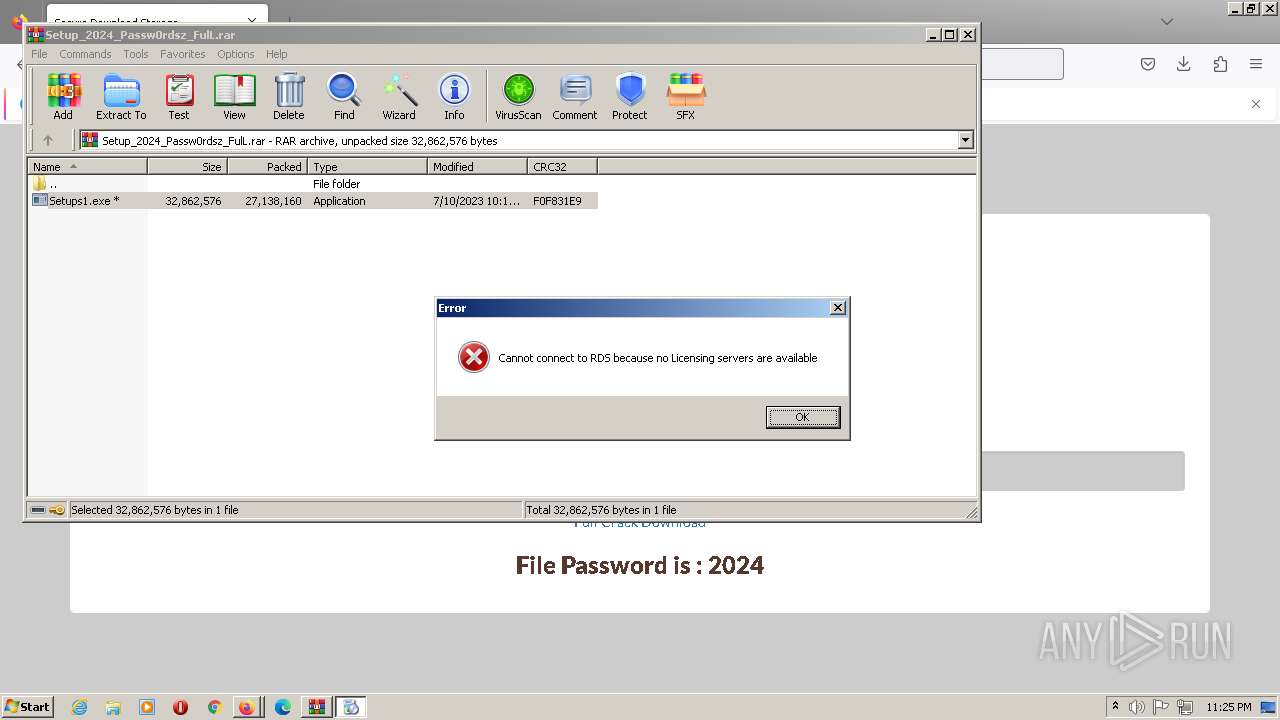
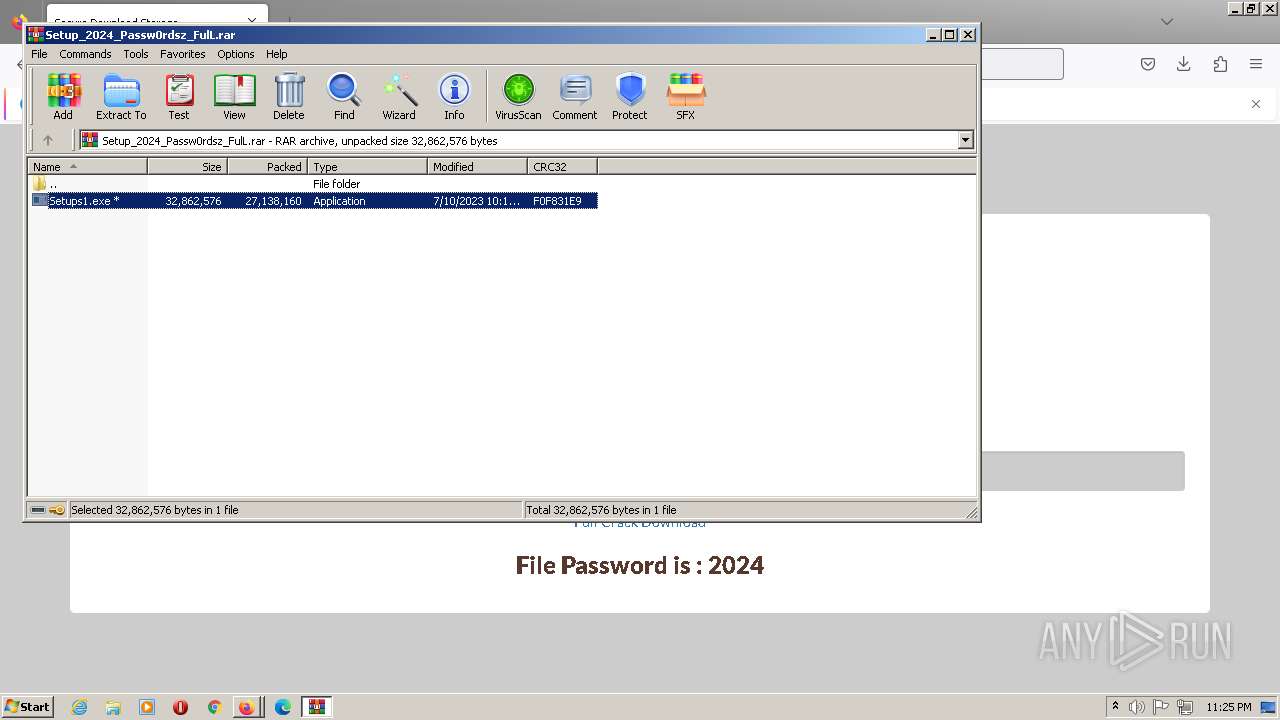
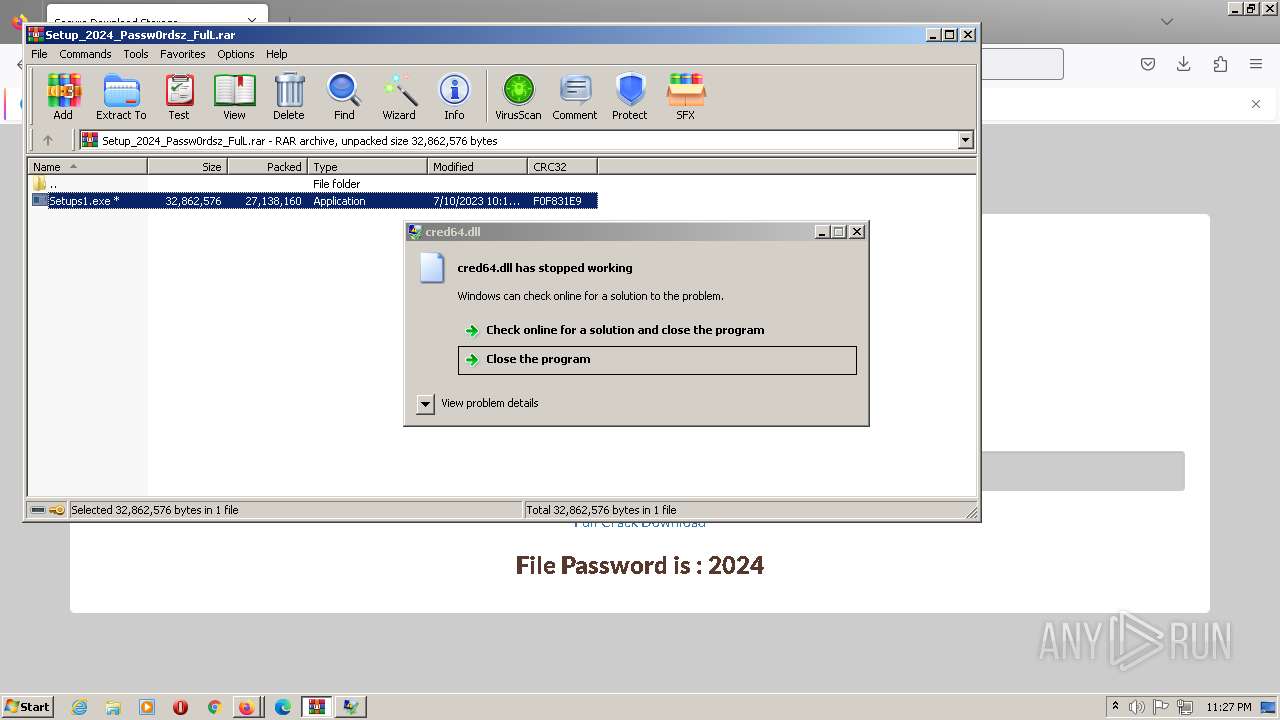
| URL: | https://boraflow.click |
| Full analysis: | https://app.any.run/tasks/32a6e71e-beff-4c72-a4d5-fadf9cc24ce6 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | July 14, 2023, 23:24:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 2F17E2573EAAAC5AD05DD98AA1DDC688 |
| SHA1: | E6522EDB1834C345E33105994EEC2537C83E1068 |
| SHA256: | 104B3CD96A1A45EC98B1A9BC98E2A39E8B4EB9F60FE9535A89F4A1D91C66103C |
| SSDEEP: | 3:N87au:29 |
MALICIOUS
Application was dropped or rewritten from another process
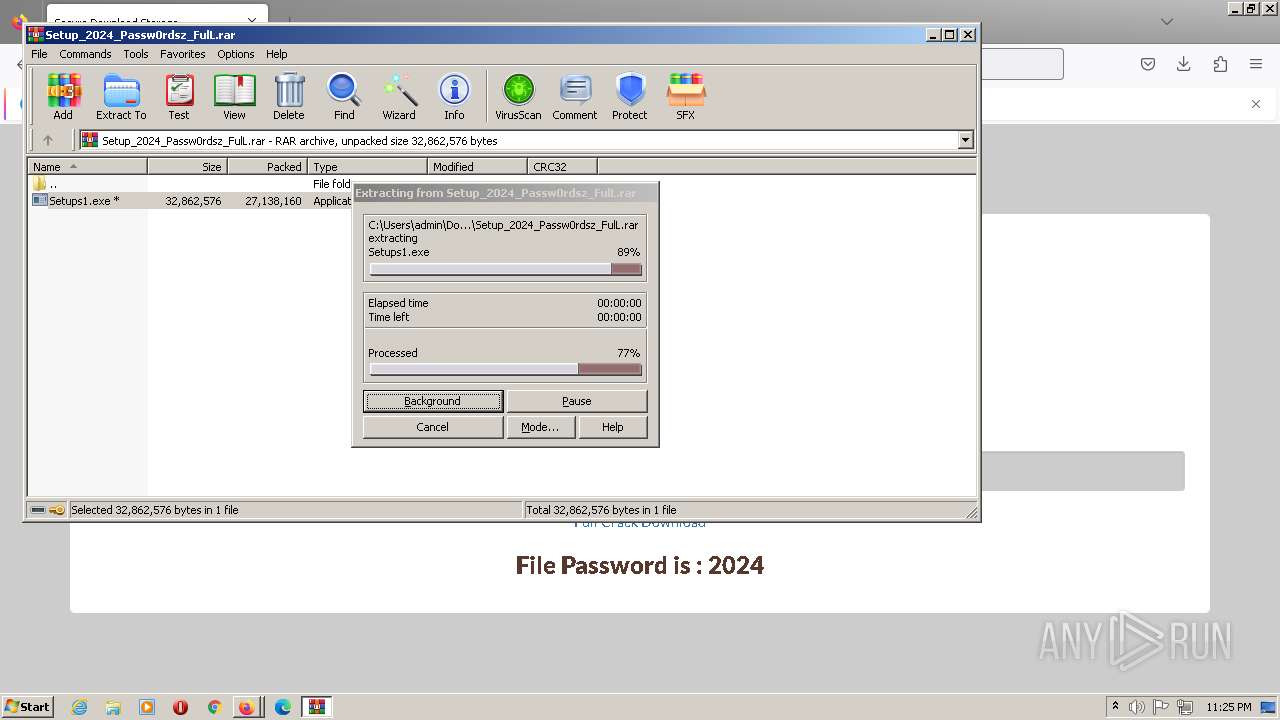
- Setups1.exe (PID: 3460)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
- jbruyer.exe (PID: 3848)
VIDAR was detected
- AddInProcess32.exe (PID: 668)
Loads dropped or rewritten executable
- AddInProcess32.exe (PID: 668)
- rundll32.exe (PID: 3128)
- rundll32.exe (PID: 4016)
- WerFault.exe (PID: 3956)
- rundll32.exe (PID: 3144)
Steals credentials from Web Browsers
- AddInProcess32.exe (PID: 668)
Connects to the CnC server
- AddInProcess32.exe (PID: 668)
- jbruyer.exe (PID: 572)
ARKEI detected by memory dumps
- AddInProcess32.exe (PID: 668)
Steals credentials
- AddInProcess32.exe (PID: 668)
ARKEI was detected
- AddInProcess32.exe (PID: 668)
Uses Task Scheduler to run other applications
- jbruyer.exe (PID: 572)
AMADEY was detected
- jbruyer.exe (PID: 572)
Actions looks like stealing of personal data
- rundll32.exe (PID: 4016)
- AddInProcess32.exe (PID: 668)
Changes the autorun value in the registry
- jbruyer.exe (PID: 572)
SUSPICIOUS
Reads the Internet Settings
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
Starts POWERSHELL.EXE for commands execution
- Setups1.exe (PID: 3460)
BASE64 encoded PowerShell command has been detected
- Setups1.exe (PID: 3460)
The process bypasses the loading of PowerShell profile settings
- Setups1.exe (PID: 3460)
Reads settings of System Certificates
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
Executes as Windows Service
- VSSVC.exe (PID: 2936)
Connects to the server without a host name
- AddInProcess32.exe (PID: 668)
- jbruyer.exe (PID: 572)
Checks Windows Trust Settings
- AddInProcess32.exe (PID: 668)
Reads browser cookies
- AddInProcess32.exe (PID: 668)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- AddInProcess32.exe (PID: 668)
Executable content was dropped or overwritten
- AddInProcess32.exe (PID: 668)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
Searches for installed software
- AddInProcess32.exe (PID: 668)
Reads security settings of Internet Explorer
- AddInProcess32.exe (PID: 668)
Starts itself from another location
- 33485718709684821295.exe (PID: 3104)
Starts CMD.EXE for commands execution
- jbruyer.exe (PID: 572)
- cmd.exe (PID: 2268)
Application launched itself
- cmd.exe (PID: 2268)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 2268)
The process executes via Task Scheduler
- jbruyer.exe (PID: 3848)
Process requests binary or script from the Internet
- jbruyer.exe (PID: 572)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 4016)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 3128)
INFO
The process checks LSA protection
- VSSVC.exe (PID: 2936)
- slui.exe (PID: 3716)
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
Manual execution by a user
- WinRAR.exe (PID: 3796)
- firefox.exe (PID: 2576)
The process uses the downloaded file
- WinRAR.exe (PID: 3796)
- firefox.exe (PID: 2456)
Executable content was dropped or overwritten
- firefox.exe (PID: 2456)
- WinRAR.exe (PID: 3796)
Checks supported languages
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
- jbruyer.exe (PID: 3848)
Reads the computer name
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
Reads the machine GUID from the registry
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
Creates files or folders in the user directory
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- jbruyer.exe (PID: 572)
Checks proxy server information
- Setups1.exe (PID: 3460)
- AddInProcess32.exe (PID: 668)
- jbruyer.exe (PID: 572)
Create files in a temporary directory
- Setups1.exe (PID: 3460)
- 33485718709684821295.exe (PID: 3104)
- jbruyer.exe (PID: 572)
Application launched itself
- firefox.exe (PID: 2456)
Creates files in the program directory
- AddInProcess32.exe (PID: 668)
Reads Environment values
- AddInProcess32.exe (PID: 668)
Reads product name
- AddInProcess32.exe (PID: 668)
Reads CPU info
- AddInProcess32.exe (PID: 668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
84
Monitored processes
37
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | CACLS "..\c2868ed41c" /P "admin:R" /E | C:\Windows\SysWOW64\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | "C:\Users\admin\AppData\Local\Temp\c2868ed41c\jbruyer.exe" | C:\Users\admin\AppData\Local\Temp\c2868ed41c\jbruyer.exe | 33485718709684821295.exe | ||||||||||||
User: admin Company: NortonLifeLock Inc. Integrity Level: MEDIUM Description: Norton Remove and Reinstall Exit code: 0 Version: 4.5.0.157 Modules
| |||||||||||||||
| 668 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | Setups1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 0 Version: 4.7.2558.0 built by: NET471REL1 Modules
| |||||||||||||||
| 2120 | CACLS "jbruyer.exe" /P "admin:R" /E | C:\Windows\SysWOW64\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2208 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2456.6.1759457091\782632702" -parentBuildID 20230710165010 -prefsHandle 2908 -prefMapHandle 2912 -prefsLen 25927 -prefMapSize 242647 -appDir "C:\Program Files\Mozilla Firefox\browser" - {596a9ab1-f236-4590-8b68-c186925f3f01} 2456 "\\.\pipe\gecko-crash-server-pipe.2456" 2892 1d0e1f58 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2268 | "C:\Windows\System32\cmd.exe" /k echo Y|CACLS "jbruyer.exe" /P "admin:N"&&CACLS "jbruyer.exe" /P "admin:R" /E&&echo Y|CACLS "..\c2868ed41c" /P "admin:N"&&CACLS "..\c2868ed41c" /P "admin:R" /E&&Exit | C:\Windows\SysWOW64\cmd.exe | — | jbruyer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2312 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2456.4.1609688618\136042366" -childID 3 -isForBrowser -prefsHandle 2672 -prefMapHandle 2676 -prefsLen 23517 -prefMapSize 242647 -jsInitHandle 908 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {9872fc59-eb63-467b-99f4-3bcde320b20c} 2456 "\\.\pipe\gecko-crash-server-pipe.2456" 2660 1973e858 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2456.0.1997569638\2052684237" -parentBuildID 20230710165010 -prefsHandle 1260 -prefMapHandle 1264 -prefsLen 24055 -prefMapSize 242647 -appDir "C:\Program Files\Mozilla Firefox\browser" - {25840ebb-8115-446b-aa01-0816ee76f589} 2456 "\\.\pipe\gecko-crash-server-pipe.2456" 1180 13851258 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2456 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://boraflow.click" | C:\Program Files\Mozilla Firefox\firefox.exe | explorer.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2456.3.2076233146\481971839" -childID 2 -isForBrowser -prefsHandle 1936 -prefMapHandle 2264 -prefsLen 25822 -prefMapSize 242647 -jsInitHandle 908 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {7916fbb9-7e3a-486f-b8b8-3f1e685d7dc3} 2456 "\\.\pipe\gecko-crash-server-pipe.2456" 1564 d77c58 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
16 665
Read events
16 511
Write events
154
Delete events
0
Modification events
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (2576) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 0000000000000000 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000008F000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\155\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3716) slui.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\Activation |
| Operation: | write | Name: | LastAction |
Value: B2CBB71A03000000 | |||
| (PID) Process: | (3716) slui.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\Activation |
| Operation: | write | Name: | ActionId |
Value: 7 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|ScreenX |
Value: 144 | |||
| (PID) Process: | (2456) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|ScreenY |
Value: 354 | |||
Executable files
19
Suspicious files
610
Text files
156
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\webappsstore.sqlite-wal | — | |
MD5:— | SHA256:— | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\compatibility.ini | text | |
MD5:C6998EF9E767E571FE74299C971B9C98 | SHA256:69C387E1BE9E3C5A5BE3B767F5734E7E31755B67C3F6F409D175FB9265D53F2E | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\permissions.sqlite-journal | binary | |
MD5:EB1091337B6DB79E11438CD4F8EB7B06 | SHA256:E95B70CF1C5D3011CD70F1089F99A1CEAB3B0BA63907FB4FFE94BBB86EDD4E11 | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cookies.sqlite-shm | binary | |
MD5:0E57A98A1B758C757880D0750D77FE11 | SHA256:11D47954B63164FAE7FA41899C8EACAA36015E667EFCC6EEFB0B7915B8214D87 | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\ls-archive-tmp.sqlite-journal | binary | |
MD5:6F935B390969A4CF42F99B00B3B22DA0 | SHA256:59B6BC774C25052A0B399B26E0C5B70663C3768FD5E54D3BF30C90412B8E8027 | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage\ls-archive-tmp.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\storage.sqlite-journal | binary | |
MD5:0D3332474212596D16A58860F61CD4BB | SHA256:1C77099021F16E6F7E098C4306D36A8862E6ED0CCD7817C4383EB821AAED8B1B | |||
| 2456 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\nltxvmn2.default\cookies.sqlite-wal | binary | |
MD5:CB337C69FEF6735FEC8C0DD0786AEDB6 | SHA256:F363475D9B8768312413365091FC909AEAAD79465C58B49D8A0881705AE47267 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
112
DNS requests
190
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2456 | firefox.exe | GET | 301 | 104.21.90.243:80 | http://boraflow.click/ | US | — | — | malicious |
2456 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | US | text | 90 b | whitelisted |
2456 | firefox.exe | POST | 200 | 104.86.110.200:80 | http://r3.o.lencr.org/ | GB | binary | 503 b | shared |
2456 | firefox.exe | POST | 200 | 104.86.110.200:80 | http://r3.o.lencr.org/ | GB | binary | 503 b | shared |
2456 | firefox.exe | POST | 200 | 104.86.110.200:80 | http://r3.o.lencr.org/ | GB | binary | 503 b | shared |
2456 | firefox.exe | POST | 200 | 104.86.110.200:80 | http://r3.o.lencr.org/ | GB | binary | 503 b | shared |
2456 | firefox.exe | POST | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3 | US | binary | 471 b | whitelisted |
2456 | firefox.exe | POST | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gts1c3 | US | binary | 472 b | whitelisted |
2456 | firefox.exe | POST | 200 | 104.86.110.200:80 | http://r3.o.lencr.org/ | GB | der | 503 b | shared |
— | — | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | binary | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2456 | firefox.exe | 104.21.90.243:443 | boraflow.click | CLOUDFLARENET | — | unknown |
2456 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2456 | firefox.exe | 104.86.110.200:80 | r3.o.lencr.org | Akamai International B.V. | GB | unknown |
2456 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | suspicious |
2456 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | suspicious |
2456 | firefox.exe | 54.185.202.81:443 | shavar.services.mozilla.com | AMAZON-02 | US | unknown |
2456 | firefox.exe | 52.55.246.60:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
2456 | firefox.exe | 52.222.226.205:80 | ocsp.r2m02.amazontrust.com | AMAZON-02 | US | unknown |
2456 | firefox.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
boraflow.click |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
r3.o.lencr.org |
| shared |
a1887.dscq.akamai.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
668 | AddInProcess32.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
668 | AddInProcess32.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host ZIP Request |
572 | jbruyer.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Check-In |
572 | jbruyer.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Bot Activity (POST) M2 |
572 | jbruyer.exe | A Network Trojan was detected | AV TROJAN Agent.DHOA System Info Exfiltration |
572 | jbruyer.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Attempt to send e-mail as POST request |
572 | jbruyer.exe | A Network Trojan was detected | ET MALWARE Amadey Bot Activity (POST) M1 |
572 | jbruyer.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
572 | jbruyer.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .dll file with no User-Agent |
572 | jbruyer.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3 ETPRO signatures available at the full report