| URL: | https://c.yfhost.com/trkXWH |
| Full analysis: | https://app.any.run/tasks/d828b718-1027-49eb-9c22-944aaee6a7b7 |
| Verdict: | Malicious activity |
| Threats: | Rhadamanthys is a C++ information-stealing malware that extracts sensitive data from infiltrated machines. Its layered operational chain and advanced evasion tactics make it a major risk in cybersecurity landscapes. |
| Analysis date: | July 18, 2025, 10:43:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 968756049E8DD8069A9BEED99A8B2E5C |
| SHA1: | A1B8DB98E184D0B1AA72049273B61D5DF2FEE378 |
| SHA256: | 0FE4E03C9CF89F127BADD4DBB62827AA2BB189BA9FF15DF94D01F1608068DBFB |
| SSDEEP: | 3:N8bhZIMOQt:2fIP4 |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 5764)
- reg.exe (PID: 6856)
Actions looks like stealing of personal data
- OOBE-Maintenance.exe (PID: 1872)
RHADAMANTHYS has been detected (YARA)
- OOBE-Maintenance.exe (PID: 1872)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
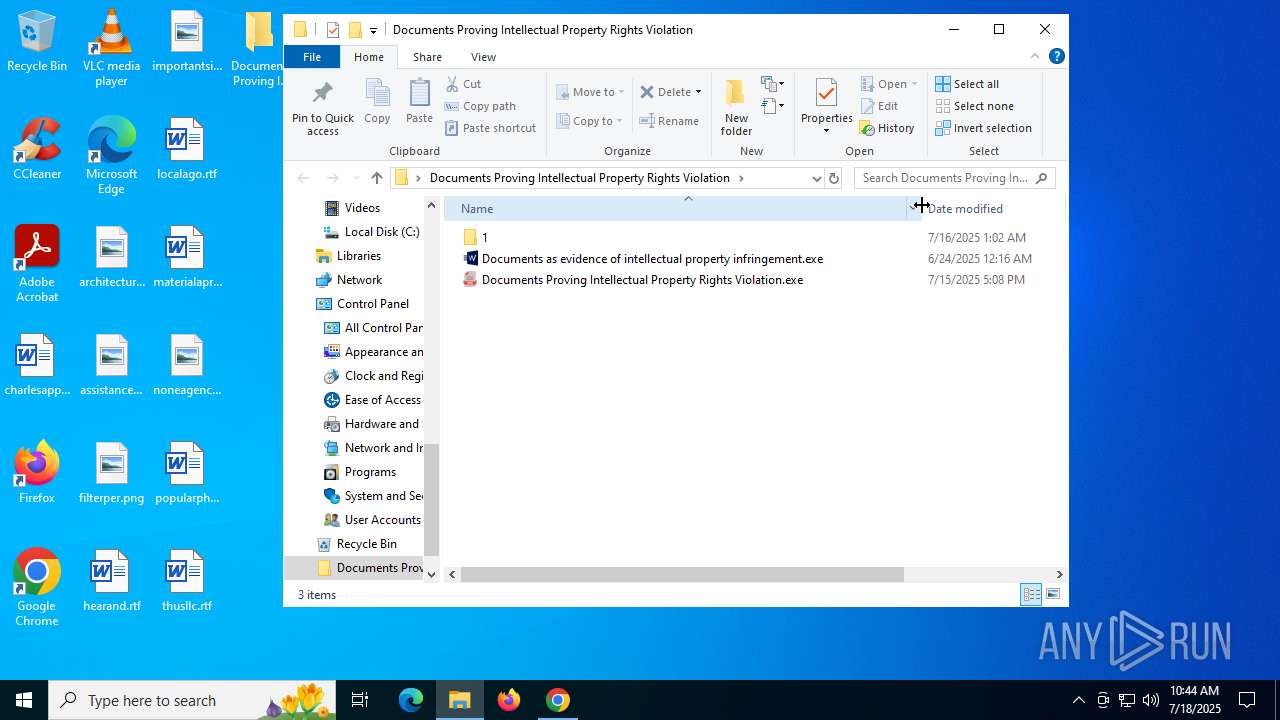
- Documents as evidence of intellectual property infringement.exe (PID: 6876)
- Documents as evidence of intellectual property infringement.exe (PID: 5416)
Application launched itself
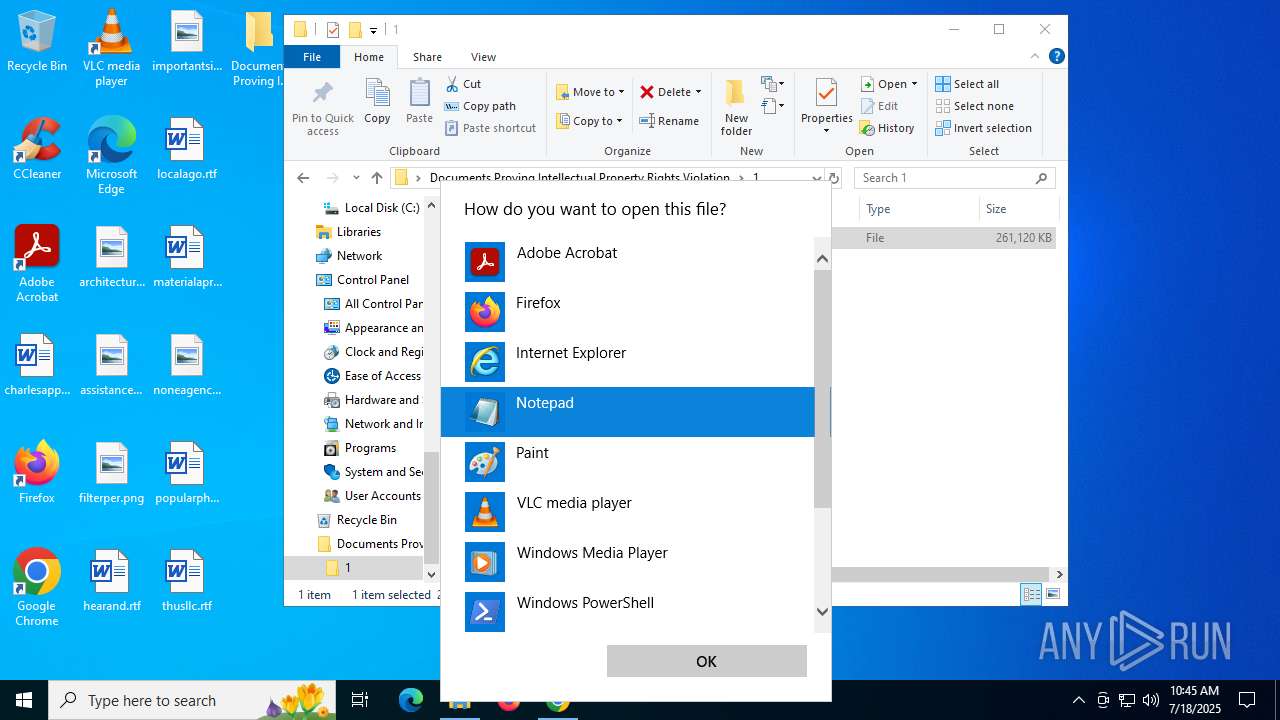
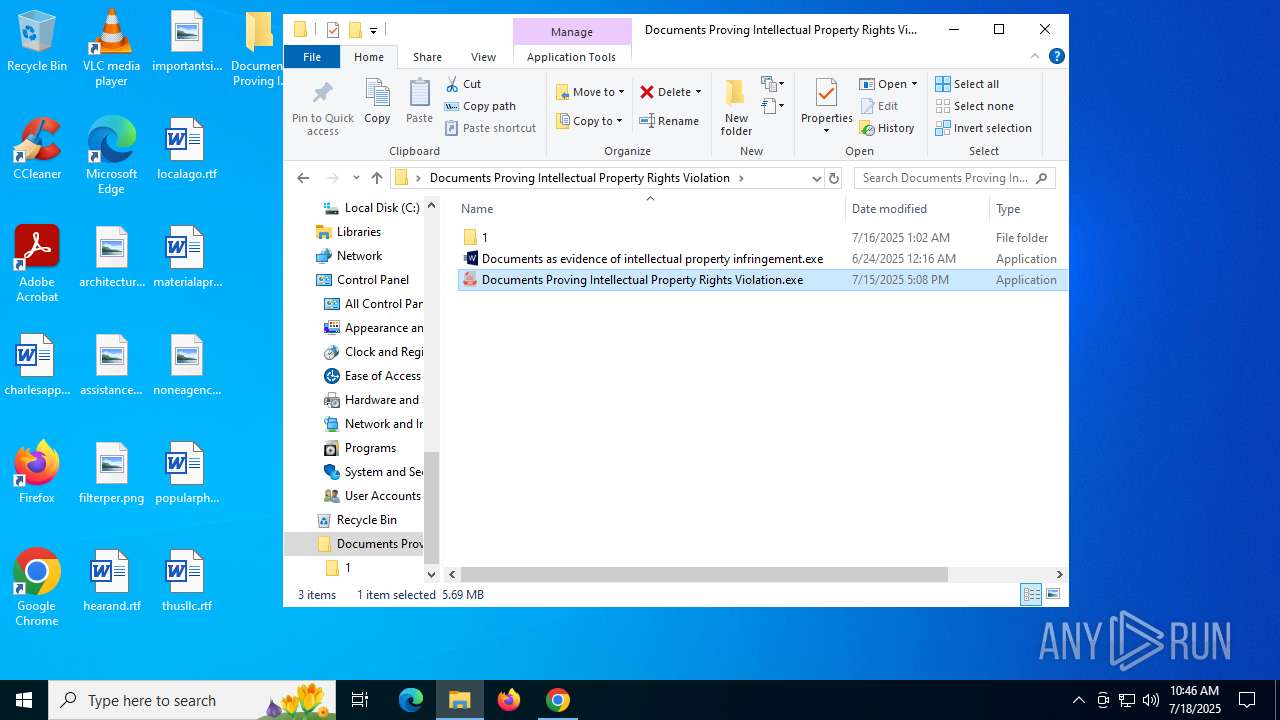
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7460)
- Documents as evidence of intellectual property infringement.exe (PID: 6876)
Starts CMD.EXE for commands execution
- Documents as evidence of intellectual property infringement.exe (PID: 6876)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7460)
Executes application which crashes
- Documents as evidence of intellectual property infringement.exe (PID: 5416)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7812)
- OOBE-Maintenance.exe (PID: 1872)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7928)
- cmd.exe (PID: 5496)
The process checks if it is being run in the virtual environment
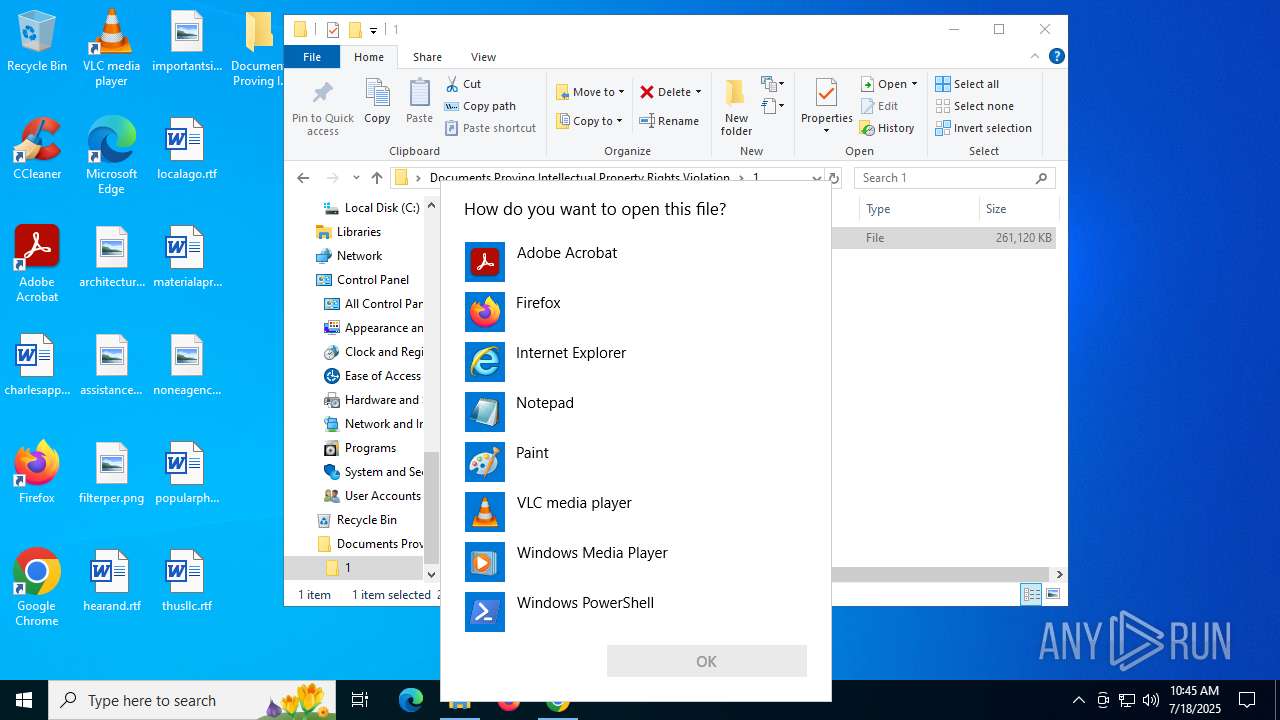
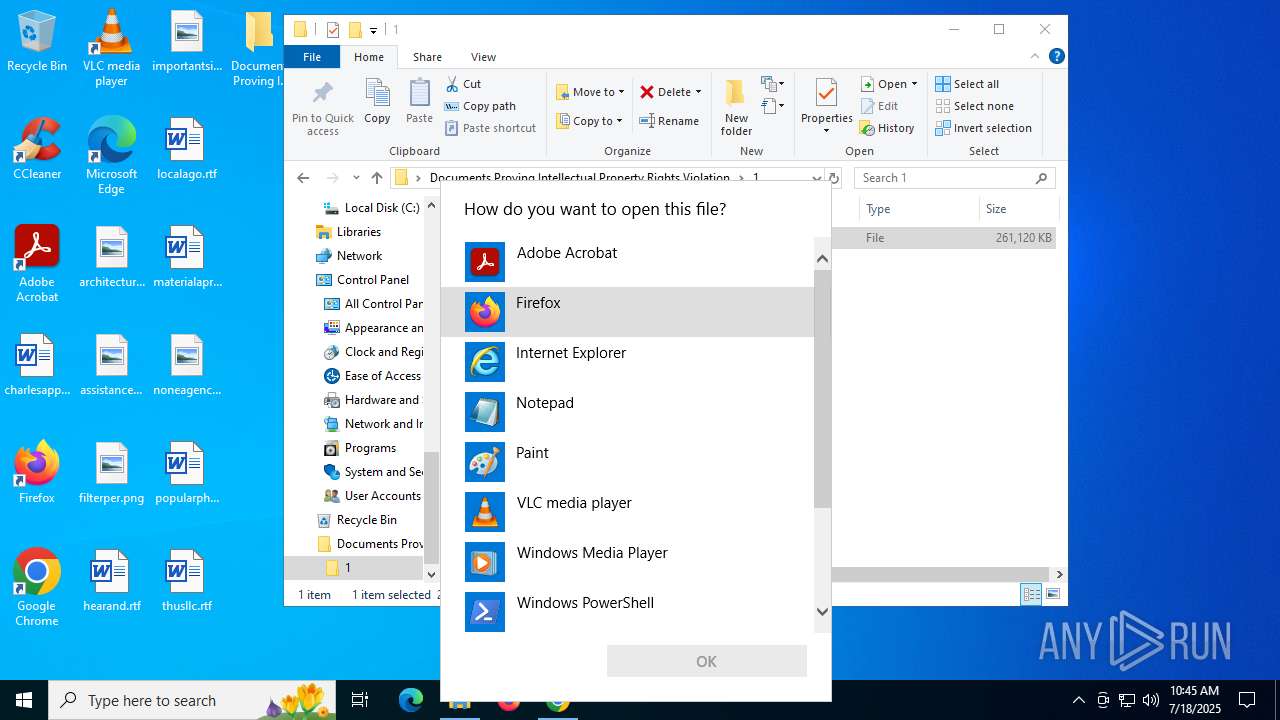
- OpenWith.exe (PID: 5628)
Reads security settings of Internet Explorer
- msedge.exe (PID: 7768)
Connects to unusual port
- OpenWith.exe (PID: 5628)
- wmpnscfg.exe (PID: 2528)
- OOBE-Maintenance.exe (PID: 1872)
- dllhost.exe (PID: 4048)
Reads Mozilla Firefox installation path
- msedge.exe (PID: 7768)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 1872)
Searches for installed software
- OOBE-Maintenance.exe (PID: 1872)
Executable content was dropped or overwritten
- OOBE-Maintenance.exe (PID: 1872)
INFO
Application launched itself
- chrome.exe (PID: 5532)
- msedge.exe (PID: 7768)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 3740)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8080)
- chrome.exe (PID: 7772)
Reads Microsoft Office registry keys
- chrome.exe (PID: 5532)
- OpenWith.exe (PID: 7292)
Checks supported languages
- Documents as evidence of intellectual property infringement.exe (PID: 6876)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7460)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7812)
- Documents as evidence of intellectual property infringement.exe (PID: 5416)
- chrome.exe (PID: 2076)
- msedge.exe (PID: 7768)
- chrome.exe (PID: 3740)
- wmpnscfg.exe (PID: 2528)
- z2@2Uk.exe (PID: 4060)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 7292)
- notepad.exe (PID: 5576)
Manual execution by a user
- Documents as evidence of intellectual property infringement.exe (PID: 6876)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7460)
- notepad++.exe (PID: 3820)
- OpenWith.exe (PID: 5628)
- OOBE-Maintenance.exe (PID: 1872)
- rundll32.exe (PID: 4456)
The sample compiled with english language support
- WinRAR.exe (PID: 8080)
- chrome.exe (PID: 7772)
Compiled with Borland Delphi (YARA)
- Documents as evidence of intellectual property infringement.exe (PID: 6876)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7460)
- Documents as evidence of intellectual property infringement.exe (PID: 5416)
- Documents Proving Intellectual Property Rights Violation.exe (PID: 7812)
Checks proxy server information
- slui.exe (PID: 2580)
- chrome.exe (PID: 2076)
- msedge.exe (PID: 7768)
- chrome.exe (PID: 3740)
Launching a file from a Registry key
- reg.exe (PID: 5764)
- reg.exe (PID: 6856)
Reads the software policy settings
- slui.exe (PID: 2580)
Reads Environment values
- chrome.exe (PID: 2076)
- msedge.exe (PID: 7768)
- chrome.exe (PID: 3740)
Process checks computer location settings
- chrome.exe (PID: 2076)
- msedge.exe (PID: 7768)
- chrome.exe (PID: 3740)
Reads the machine GUID from the registry
- chrome.exe (PID: 2076)
- msedge.exe (PID: 7768)
- wmpnscfg.exe (PID: 2528)
- chrome.exe (PID: 3740)
Create files in a temporary directory
- chrome.exe (PID: 2076)
- OOBE-Maintenance.exe (PID: 1872)
- msedge.exe (PID: 7768)
- chrome.exe (PID: 3740)
Reads the computer name
- msedge.exe (PID: 7768)
- chrome.exe (PID: 2076)
- chrome.exe (PID: 3740)
Process checks whether UAC notifications are on
- msedge.exe (PID: 7768)
Creates files or folders in the user directory
- msedge.exe (PID: 7768)
- OOBE-Maintenance.exe (PID: 1872)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Rhadamanthys
(PID) Process(1872) OOBE-Maintenance.exe
C2 (1)https://ahgjd3y4-siterees.xyz:5656/gateway/o3biw4x7.2b7u1
Total processes
254
Monitored processes
100
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 27768 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1040 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 27768 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --string-annotations --field-trial-handle=4356,i,2199810634724994567,2813057214012064636,262144 --variations-seed-version --mojo-platform-channel-handle=4736 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3088,i,17311723522588887777,657201155573568023,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3108 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=5224,i,17311723522588887777,657201155573568023,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --field-trial-handle=3744,i,426139635190840013,8877907697232500526,262144 --variations-seed-version --mojo-platform-channel-handle=3812 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Local\Temp\chrF75E.tmp /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Local\Temp\chrF75E.tmp\Crashpad --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc438ffff8,0x7ffc43900004,0x7ffc43900010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --extension-process --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --field-trial-handle=3672,i,2199810634724994567,2813057214012064636,262144 --variations-seed-version --mojo-platform-channel-handle=3732 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --string-annotations --field-trial-handle=1864,i,426139635190840013,8877907697232500526,262144 --variations-seed-version --mojo-platform-channel-handle=2424 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1872 | "C:\WINDOWS\system32\OOBE-Maintenance.exe" | C:\Windows\System32\OOBE-Maintenance.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: OOBE-Maintenance Exit code: 3221226356 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
Rhadamanthys(PID) Process(1872) OOBE-Maintenance.exe C2 (1)https://ahgjd3y4-siterees.xyz:5656/gateway/o3biw4x7.2b7u1 | |||||||||||||||
Total events
17 956
Read events
17 872
Write events
64
Delete events
20
Modification events
| (PID) Process: | (5532) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5532) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5532) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5532) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5532) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5532) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (8080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (8080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\Documents Proving Intellectual Property Rights Violation.zip | |||
Executable files
15
Suspicious files
638
Text files
130
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF18d0e7.TMP | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF18d0e7.TMP | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF18d107.TMP | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RF18d116.TMP | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SignalDB\LOG.old~RF18d126.TMP | — | |
MD5:— | SHA256:— | |||
| 5532 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SignalDB\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
93
DNS requests
102
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4172 | chrome.exe | GET | 200 | 142.250.186.110:80 | http://clients2.google.com/time/1/current?cup2key=8:B0ZieeFQFD7LTwXuNi1Czt_EoFjz7cknZOBOC-x2Lk4&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6860 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7876 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7876 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7276 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
7276 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
7276 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
7276 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4700 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4172 | chrome.exe | 142.250.186.74:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5532 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
4172 | chrome.exe | 142.250.186.110:80 | clients2.google.com | GOOGLE | US | whitelisted |
4172 | chrome.exe | 172.67.205.107:443 | c.yfhost.com | CLOUDFLARENET | US | unknown |
4172 | chrome.exe | 142.251.168.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
c.yfhost.com |
| unknown |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5628 | OpenWith.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
5628 | OpenWith.exe | Misc activity | ET INFO Cloudflare DNS Over HTTPS Certificate Inbound |
1872 | OOBE-Maintenance.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
1872 | OOBE-Maintenance.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2528 | wmpnscfg.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrD51F.tmp directory exists )
|
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrE0A9.tmp directory exists )
|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrF75E.tmp directory exists )
|