| URL: | https://app.box.com/s/qulsz9aubfz07k4rz85i7ld4jz6nr4i0 |
| Full analysis: | https://app.any.run/tasks/5faadbf2-9cdd-4819-89e7-89caffe722ec |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | November 17, 2024, 17:53:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 7E6C2F5CA6708C63C953A52CD17BD8F5 |
| SHA1: | 6AAF657CD64912189FACF348687F16BA8B005EF4 |
| SHA256: | 0FB9FD874460D8561E6C731158B6AB75F2ACEF5408532EB7879065DCE1D30675 |
| SSDEEP: | 3:N8aqLdmPfqZaJP7tU:2aqkPf+8W |
MALICIOUS
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 3600)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1712)
- wscript.exe (PID: 7156)
Executing a file with an untrusted certificate
- EHttpSrv.exe (PID: 7872)
- EHttpSrv.exe (PID: 7472)
REMCOS has been detected (SURICATA)
- EHttpSrv.exe (PID: 7472)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7096)
- msiexec.exe (PID: 8076)
- msiexec.exe (PID: 7324)
Executing commands from a ".bat" file
- msiexec.exe (PID: 8076)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7052)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 8076)
- wscript.exe (PID: 1712)
- EHttpSrv.exe (PID: 7872)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 7084)
- wscript.exe (PID: 1712)
Starts application with an unusual extension
- cmd.exe (PID: 7052)
Starts process via Powershell
- powershell.exe (PID: 6280)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7084)
- wscript.exe (PID: 1712)
Runs shell command (SCRIPT)
- cscript.exe (PID: 7084)
- wscript.exe (PID: 7156)
- wscript.exe (PID: 1712)
The process executes VB scripts
- cmd.exe (PID: 7052)
- powershell.exe (PID: 6280)
- wscript.exe (PID: 1712)
Starts POWERSHELL.EXE for commands execution
- cscript.exe (PID: 7084)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 1712)
Found strings related to reading or modifying Windows Defender settings
- wscript.exe (PID: 1712)
Gets the drive type (SCRIPT)
- wscript.exe (PID: 1712)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6112)
- cmd.exe (PID: 2796)
Application launched itself
- wscript.exe (PID: 1712)
The process drops C-runtime libraries
- msiexec.exe (PID: 7324)
Contacting a server suspected of hosting an CnC
- EHttpSrv.exe (PID: 7472)
Connects to unusual port
- EHttpSrv.exe (PID: 7472)
The executable file from the user directory is run by the CMD process
- EHttpSrv.exe (PID: 7472)
INFO
Manual execution by a user
- WinRAR.exe (PID: 7096)
- msiexec.exe (PID: 6000)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7096)
- msiexec.exe (PID: 8076)
- msiexec.exe (PID: 7324)
- firefox.exe (PID: 6676)
Application launched itself
- firefox.exe (PID: 6676)
- firefox.exe (PID: 6216)
Changes the display of characters in the console
- cmd.exe (PID: 7052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
184
Monitored processes
48
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 692 | timeout /t 60 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2908 -childID 1 -isForBrowser -prefsHandle 2900 -prefMapHandle 2896 -prefsLen 26798 -prefMapSize 244343 -jsInitHandle 1164 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {9a9c7797-2f06-494a-ad67-7a5ed5fcf5f6} 6676 "\\.\pipe\gecko-crash-server-pipe.6676" 17902095f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1332 | "C:\Windows\System32\cmd.exe" /c echo Script started >> "C:\Users\root\Desktop\wix\log.txt" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
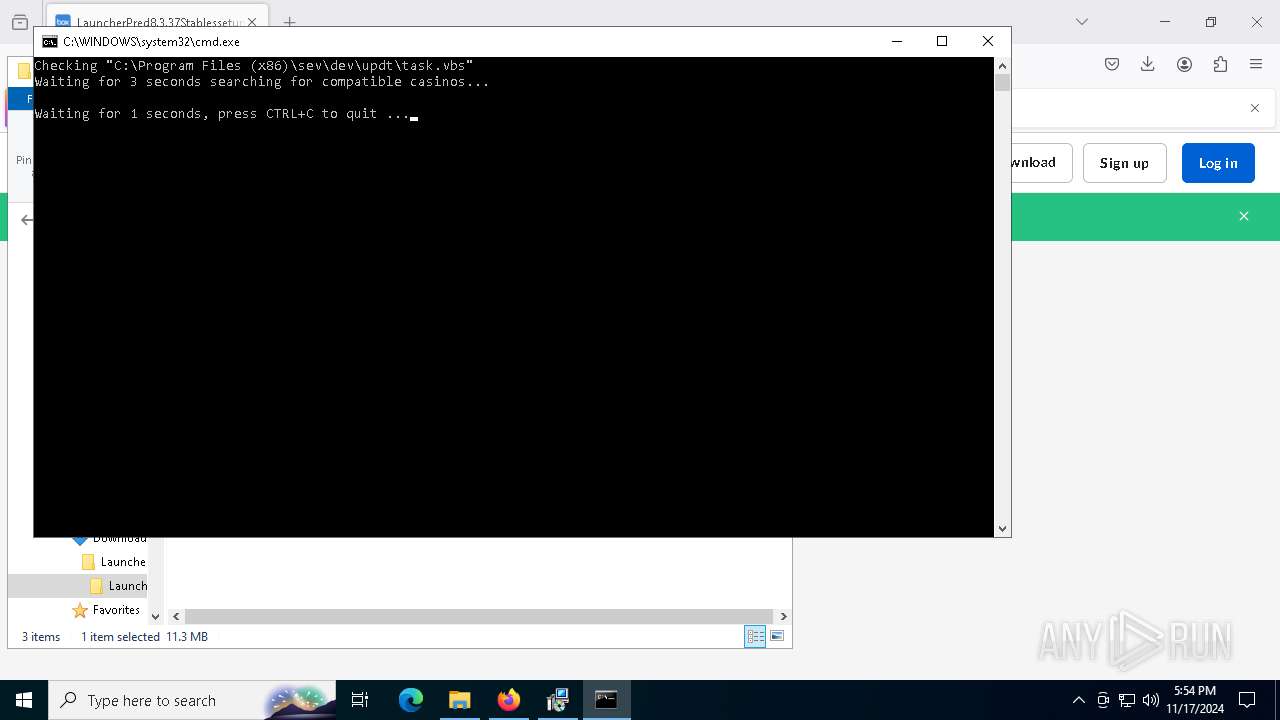
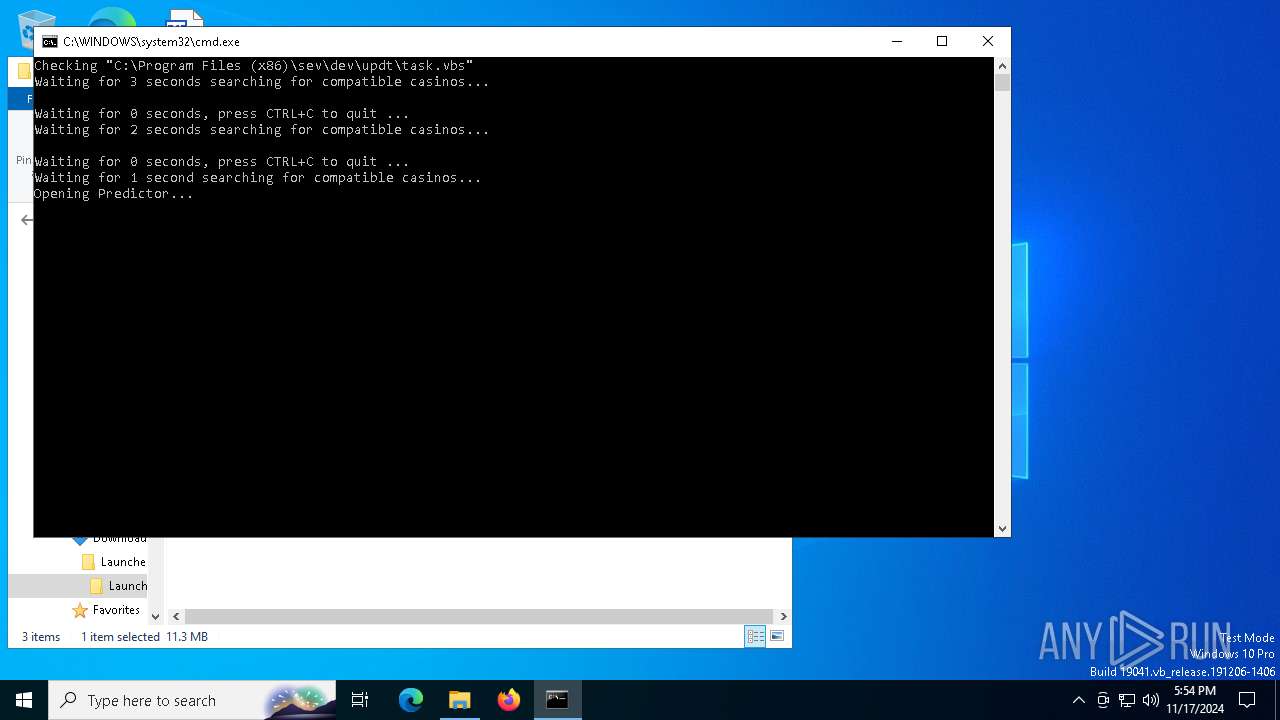
| 1712 | "C:\WINDOWS\system32\wscript.exe" "C:\Program Files (x86)\sev\dev\updt\task.vbs | C:\Windows\System32\wscript.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2620 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1812 -parentBuildID 20240213221259 -prefsHandle 1740 -prefMapHandle 1732 -prefsLen 30705 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {c84ec10d-bbef-45a3-957e-005b619f06d0} 6676 "\\.\pipe\gecko-crash-server-pipe.6676" 178fd4c2110 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 2660 | Wmic.exe /Namespace:\\root\Microsoft\Windows\Defender class MSFT_MpPreference call Add ExclusionPath="C:\" | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | "C:\Windows\System32\cmd.exe" /c taskkill /f /im msiexec.exe | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3600 | "C:\Windows\System32\cmd.exe" /c Wmic.exe /Namespace:\\root\Microsoft\Windows\Defender class MSFT_MpPreference call Add ExclusionPath="C:\" | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 142
Read events
27 040
Write events
72
Delete events
30
Modification events
| (PID) Process: | (6676) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 11 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 10 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 9 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 8 |
Value: | |||
| (PID) Process: | (7096) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 7 |
Value: | |||
Executable files
27
Suspicious files
224
Text files
46
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6676 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:9E9C9F5EC397392BEBDE3AA2BFD75AF5 | SHA256:EC916BCBB68A771F47F5A506B8DE778059B1B0ED01439ADA9121FDB8C30FF73D | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\protections.sqlite-journal | binary | |
MD5:213C20CD5934B916923EE48DB0048830 | SHA256:75402021FE68D3DEB7A6381CD256114CE932D99F49148276AD737386DE2E8BAF | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:9E9C9F5EC397392BEBDE3AA2BFD75AF5 | SHA256:EC916BCBB68A771F47F5A506B8DE778059B1B0ED01439ADA9121FDB8C30FF73D | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6676 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:51B9F340301E8F1BBE2A011E1A63E5AB | SHA256:AFA499117FAA37034903A7EF48EFB9C78FF6A4ACCBD3C4CB50E861122BB1A529 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
111
DNS requests
133
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6676 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6676 | firefox.exe | POST | 200 | 23.32.238.27:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6676 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
6676 | firefox.exe | POST | 200 | 23.32.238.27:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
6676 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6676 | firefox.exe | POST | 200 | 142.250.185.99:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
4700 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6676 | firefox.exe | POST | 200 | 23.32.238.27:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
6676 | firefox.exe | POST | 200 | 23.32.238.27:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2464 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.161:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6676 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
6676 | firefox.exe | 74.112.186.157:443 | app.box.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
6676 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
app.box.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7472 | EHttpSrv.exe | A Network Trojan was detected | REMOTE [ANY.RUN] REMCOS TLS Connection JA3 Hash |
7472 | EHttpSrv.exe | Malware Command and Control Activity Detected | ET JA3 Hash - Remcos 3.x/4.x TLS Connection |