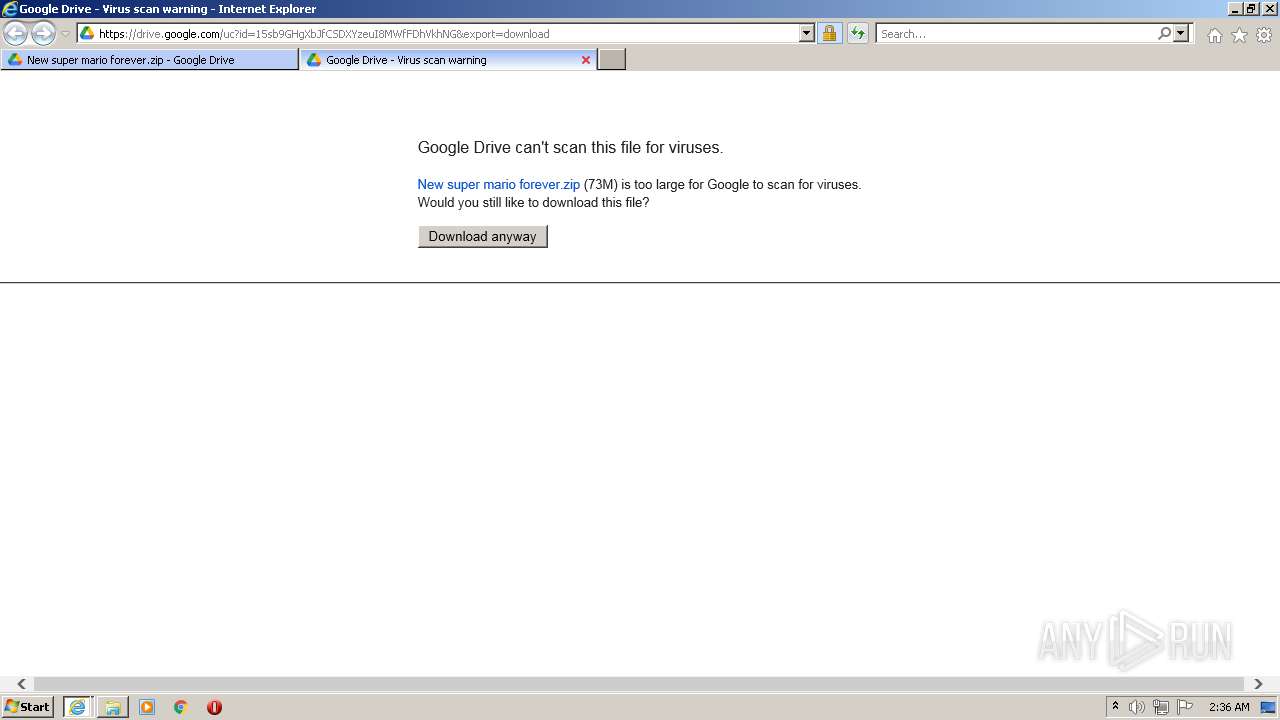
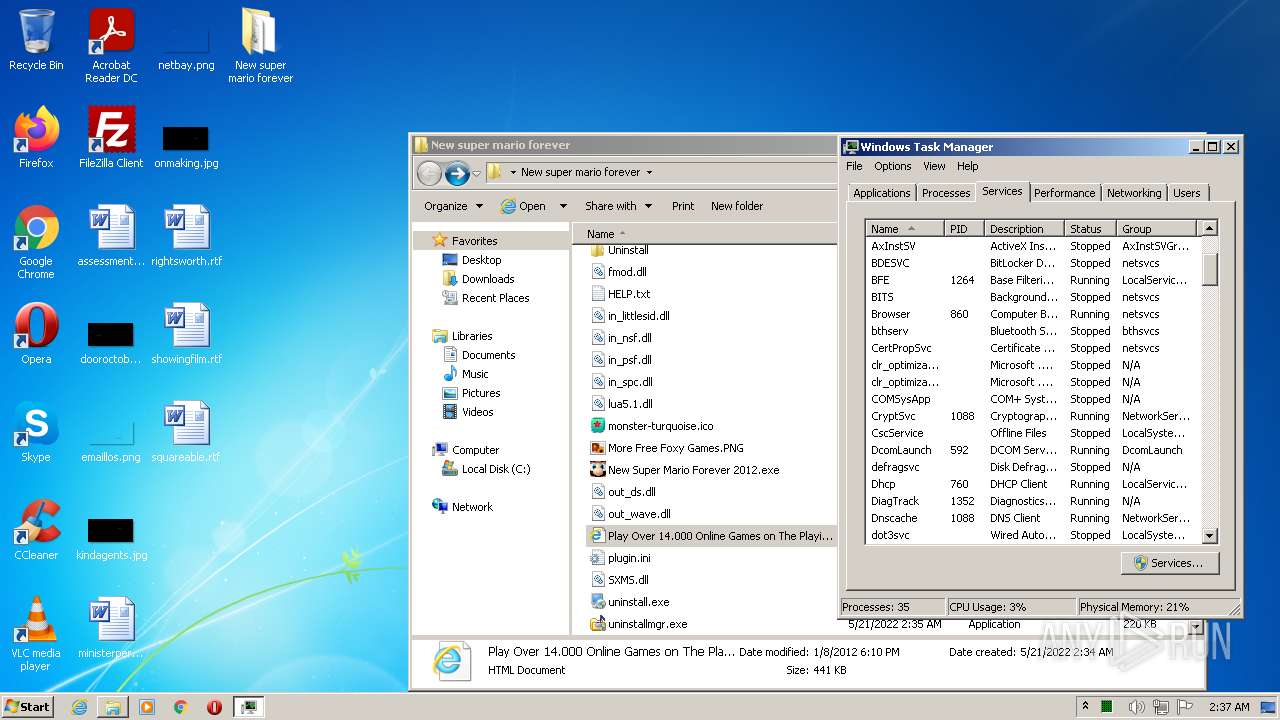
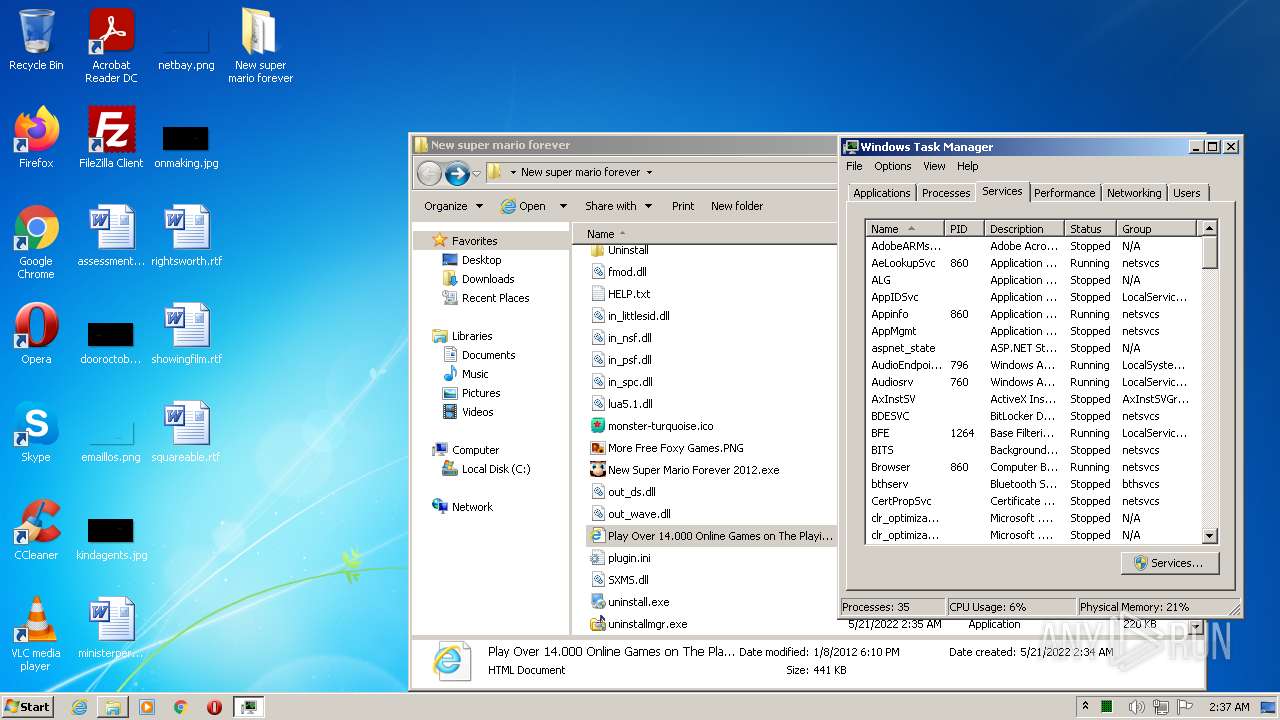
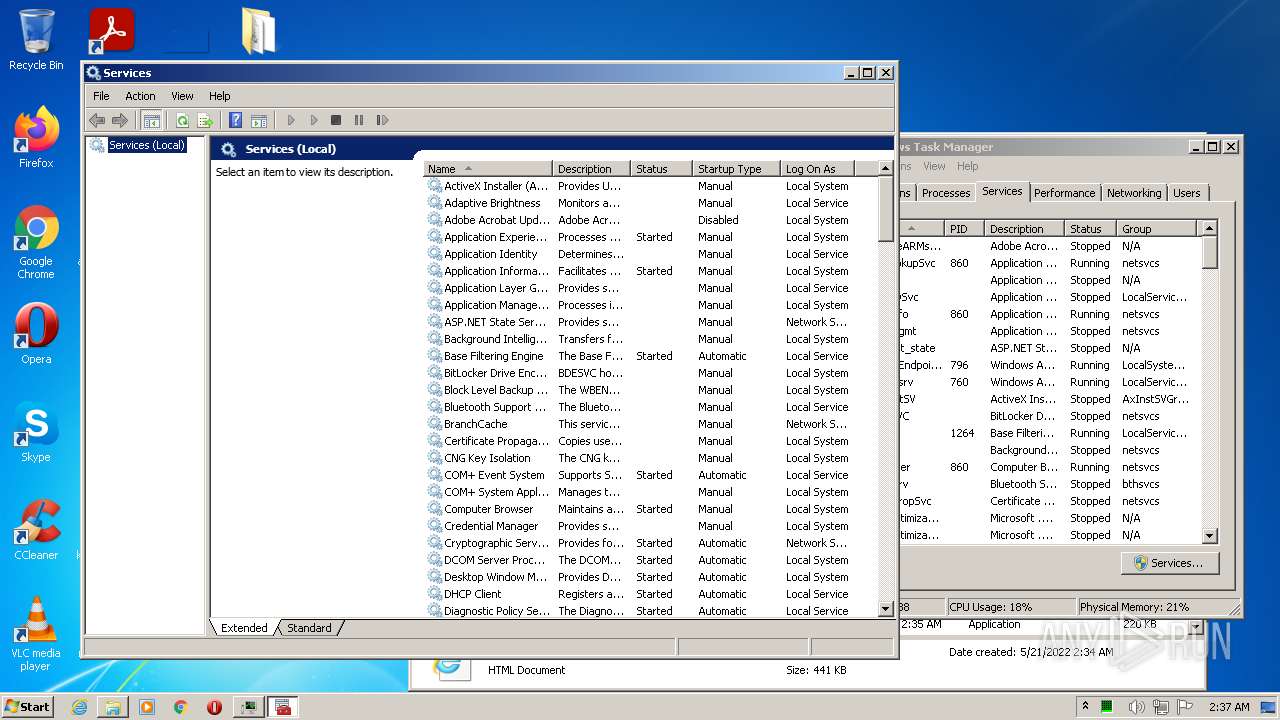
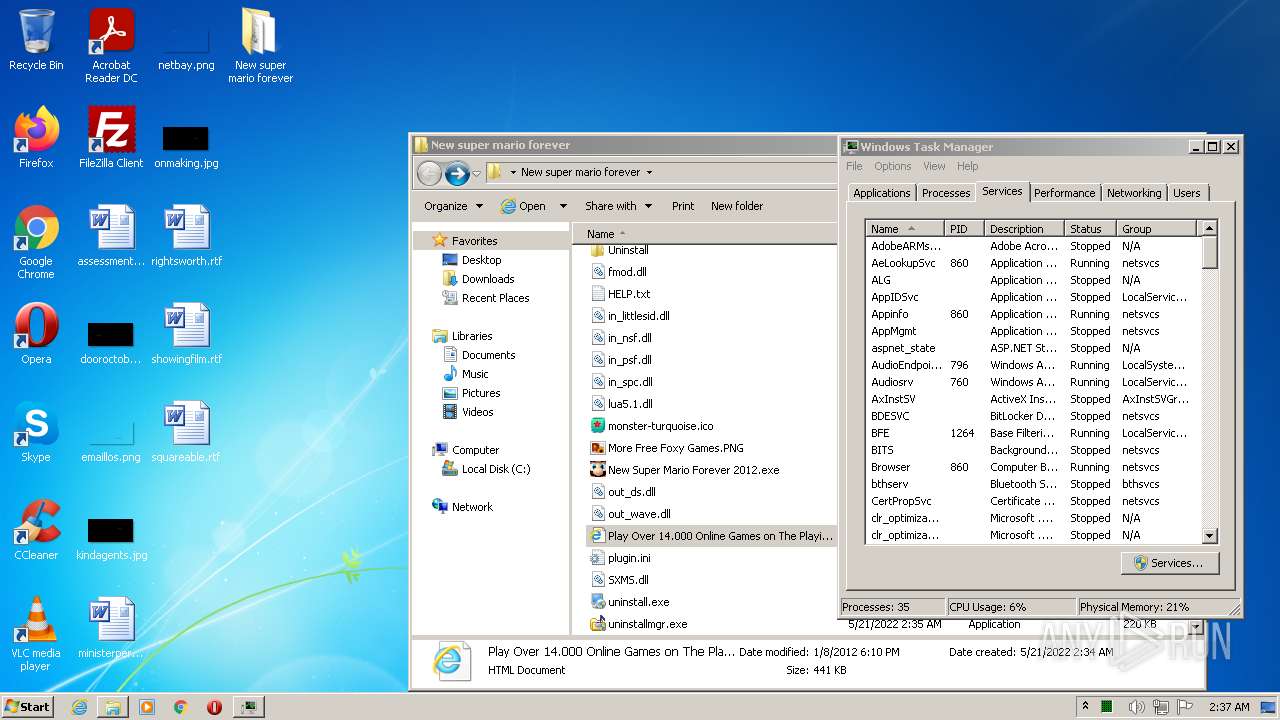
| URL: | https://www.youtube.com/redirect?event=video_description&redir_token=QUFFLUhqa082UXpHN1RuZTQ4b0hqUWM5dm5ldDVRajBnZ3xBQ3Jtc0ttQ2djczVuYzJoTFJWV29EOFE5clNzY29DdTg2bnZ4SERaLXJMNUl1NjB3QkY1ODlKOFMwbGxqcXZIdlplRnk4cHRVSUpQQjNfdTV0NF90am9tR01NdklDZE9EQU9XSmRPb21RR3FEa3RGcXBCR0JWVQ&q=https%3A%2F%2Fdrive.google.com%2Ffile%2Fd%2F15sb9GHgXbJfCSDXYzeuI8MWfFDhVkhNG%2Fview%3Fusp%3Dsharing&v=4X77gAlJcfg |
| Full analysis: | https://app.any.run/tasks/af91cafe-51f3-467e-85b8-c92719b5a9a1 |
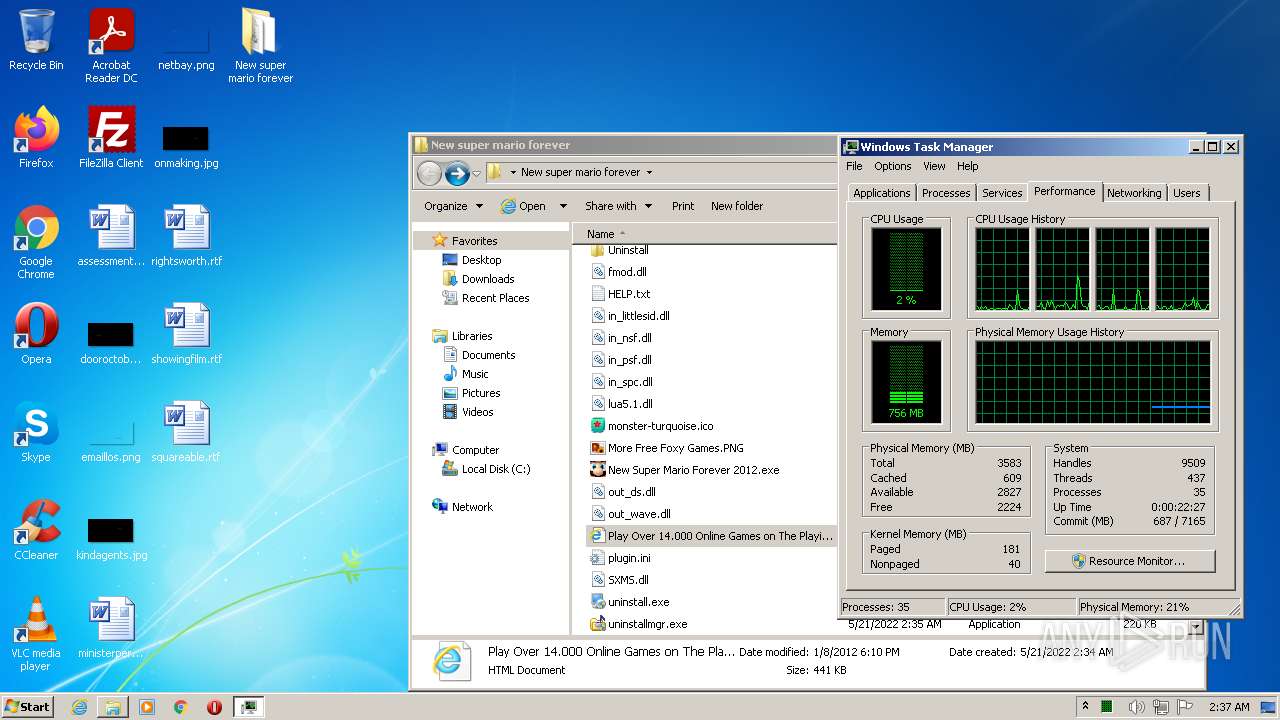
| Verdict: | Malicious activity |
| Threats: | Ramnit is a highly modular banking trojan and worm that evolved from a file-infecting virus into a powerful cybercrime tool. It specializes in financial fraud, credential theft, remote access, and malware delivery, being a serious threat to businesses and individuals. First spotted in 2010, Ramnit became popular after the 2014 takedown of the GameOver Zeus botnet, as cybercriminals sought alternatives for banking fraud. |
| Analysis date: | May 21, 2022, 01:32:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B80FD5B42E31A0DE38BC8EF976C26114 |
| SHA1: | 2B06194C343974AB3D68DE7AABFEF6A4C58A545C |
| SHA256: | 0F12ADBA412A92F92928FDBE075B3858717BEACFBA4E9A1D64D9B1F00DE181D2 |
| SSDEEP: | 6:2OLUxGKmKLqZG7GmLkG5WZ2urUq6gUVeprxeaww13zieLQ3izaeQKme:2jGRfGfLkGcPAEUVe1kaw8ueKizanK7 |
MALICIOUS
Changes settings of System certificates
- svchost.exe (PID: 1088)
Drops executable file immediately after starts
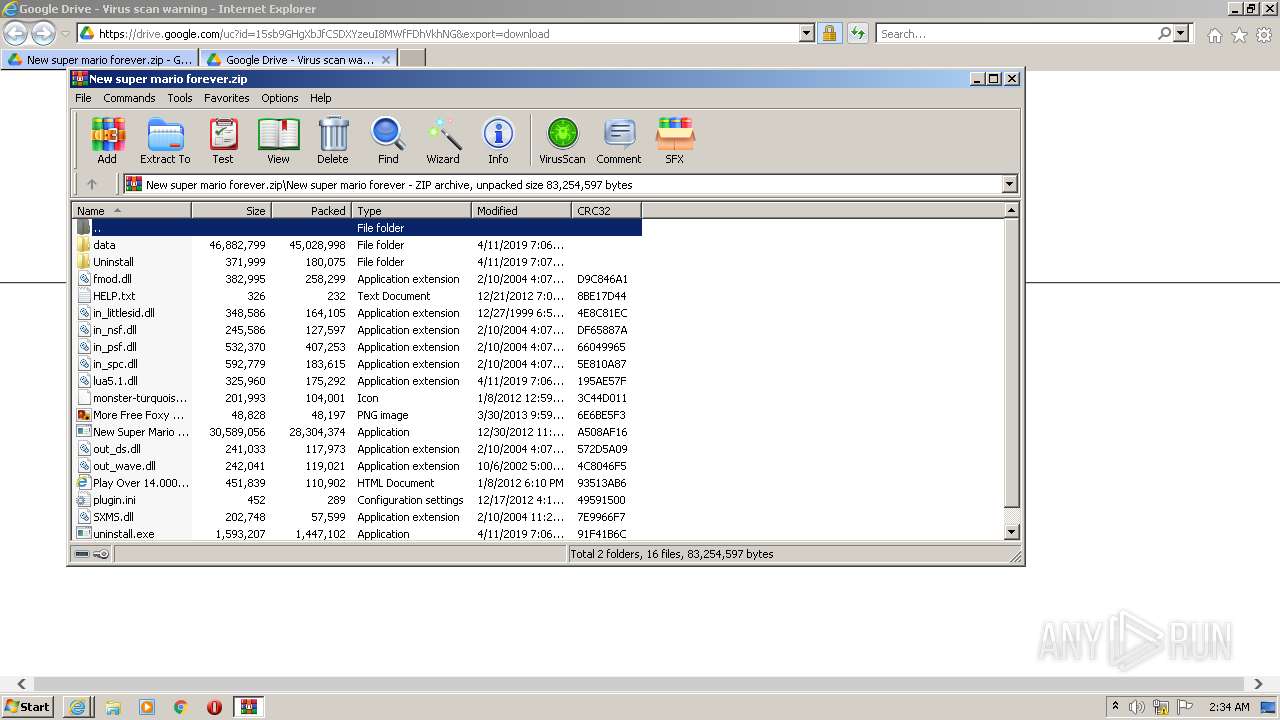
- WinRAR.exe (PID: 556)
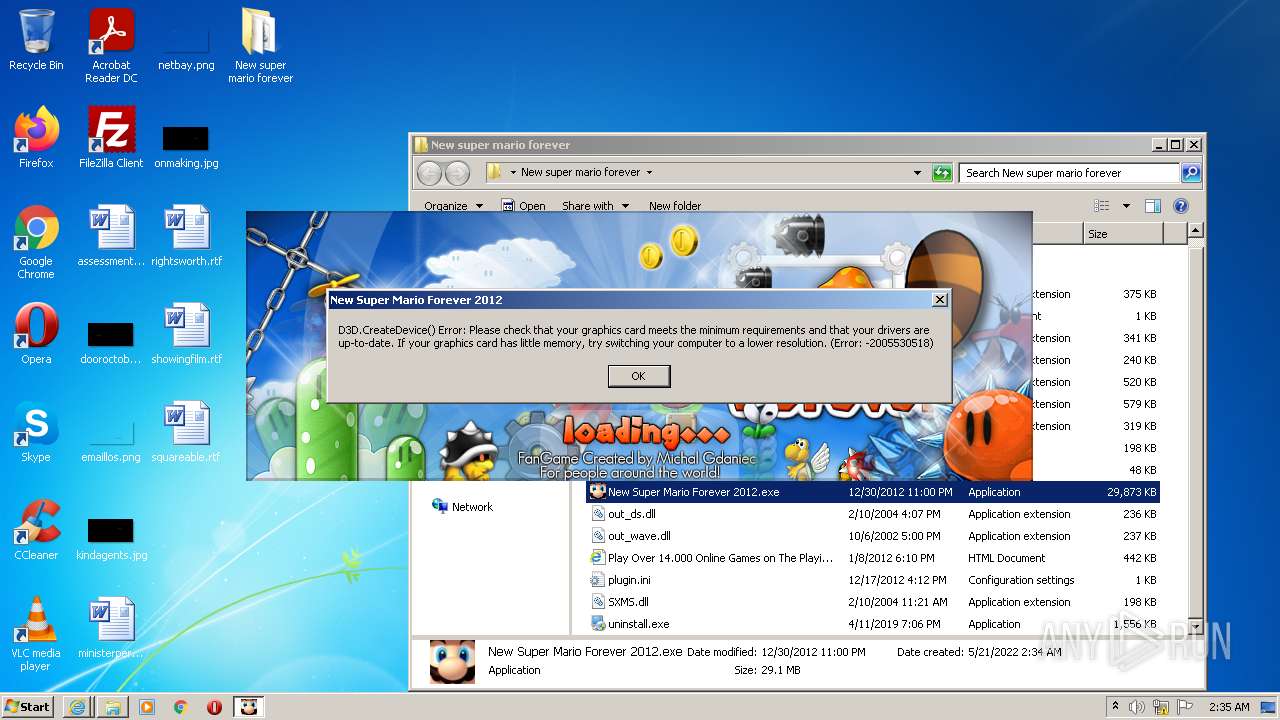
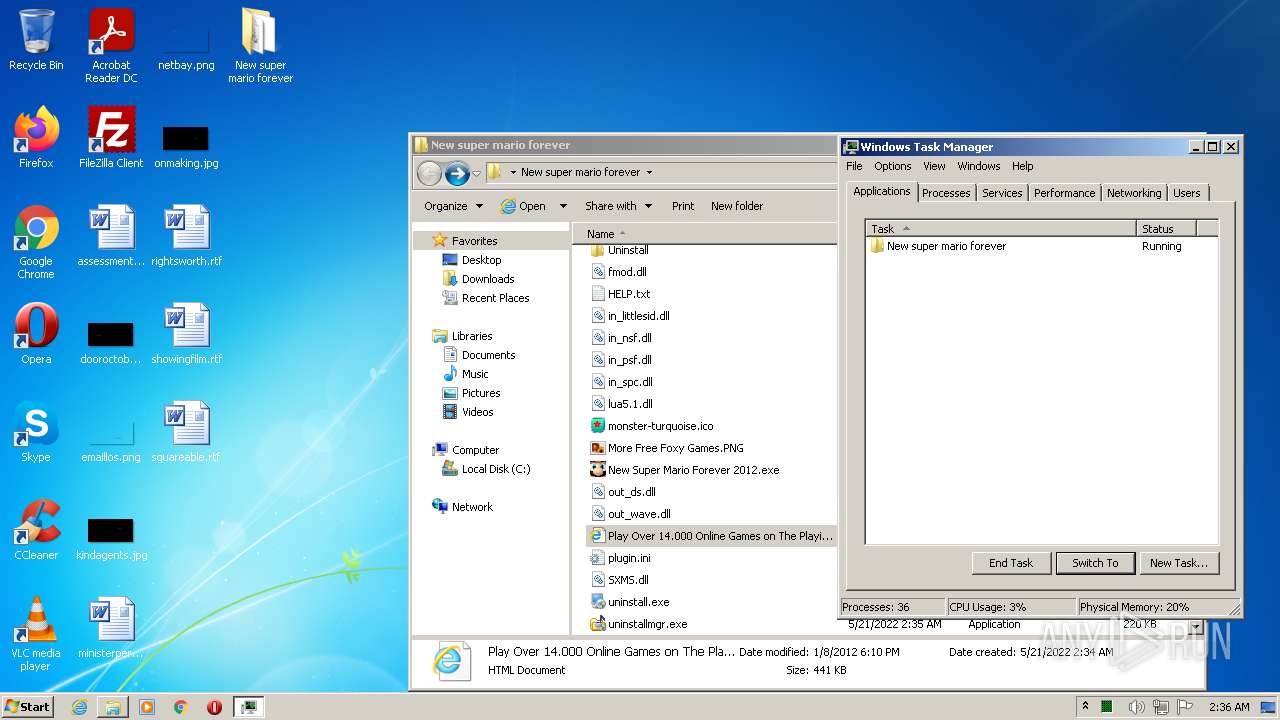
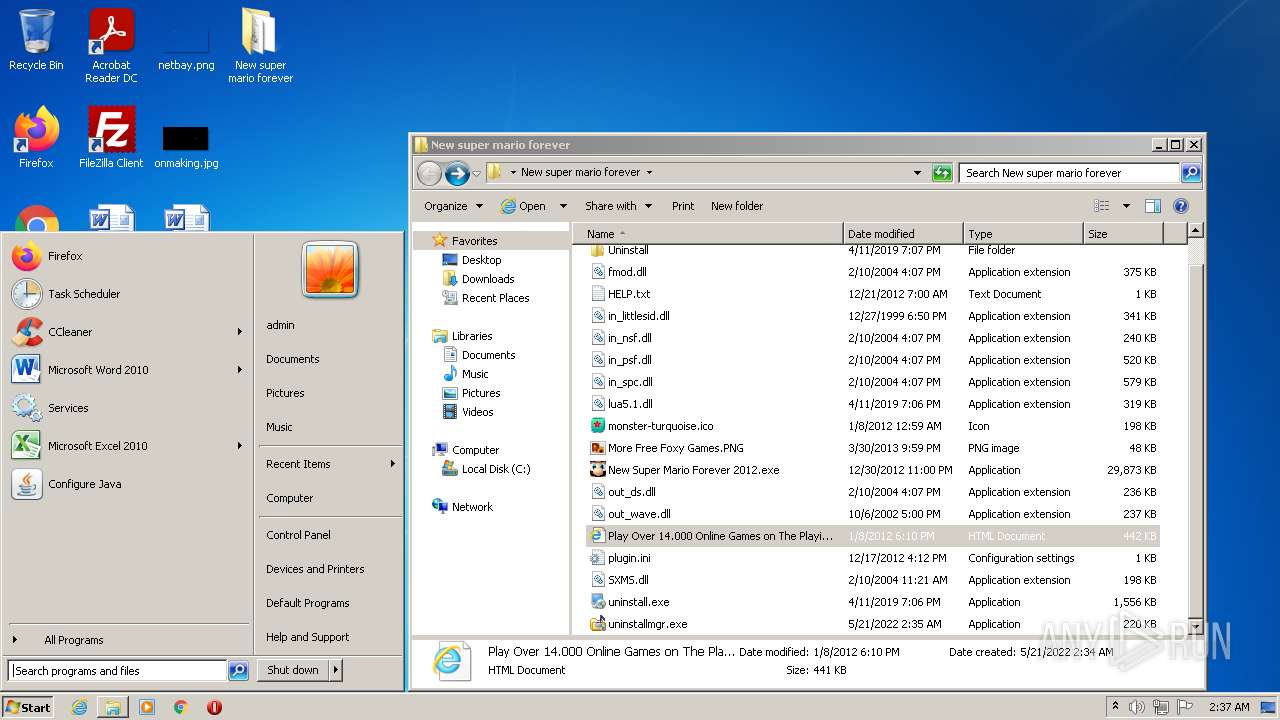
- New Super Mario Forever 2012.exe (PID: 1920)
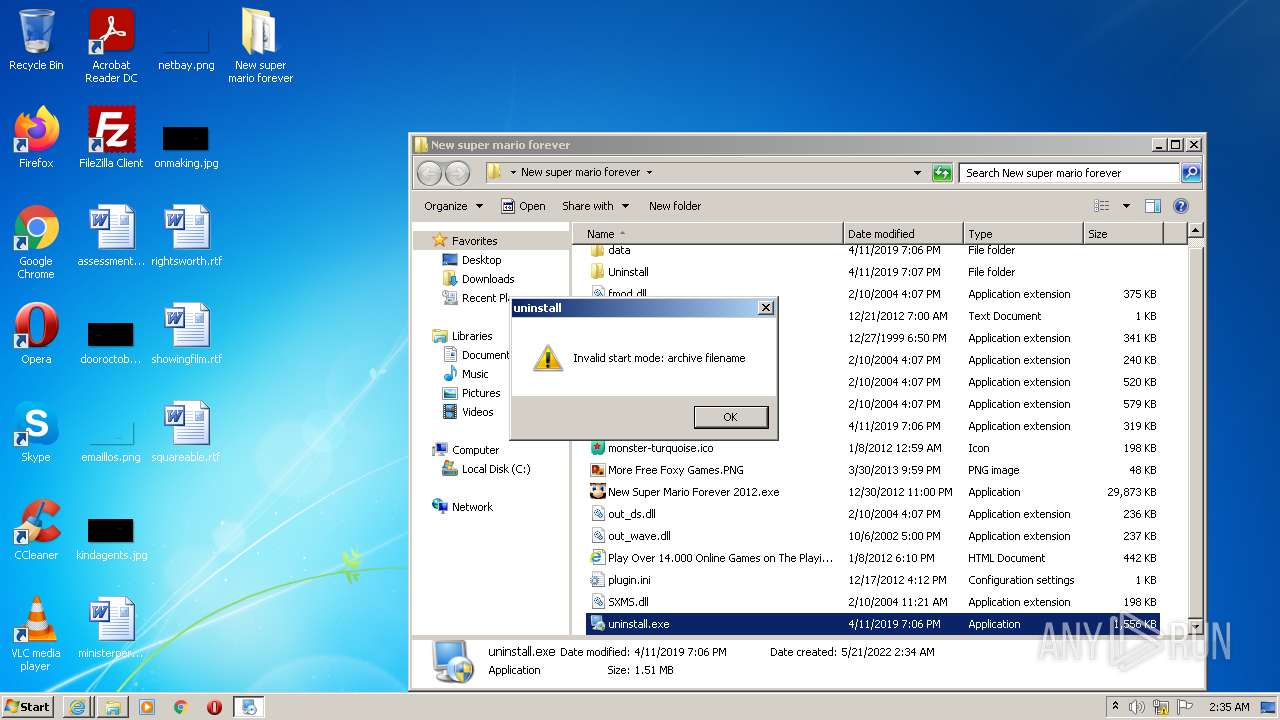
- uninstall.exe (PID: 280)
- iexplore.exe (PID: 1128)
Application was dropped or rewritten from another process
- New Super Mario Forever 2012.exe (PID: 1920)
- uninstall.exe (PID: 3236)
- uninstall.exe (PID: 280)
- uninstallmgr.exe (PID: 1620)
Loads dropped or rewritten executable
- New Super Mario Forever 2012.exe (PID: 1920)
- SearchProtocolHost.exe (PID: 2284)
- Explorer.EXE (PID: 1464)
- uninstall.exe (PID: 280)
Writes to a start menu file
- iexplore.exe (PID: 1128)
Application was injected by another process
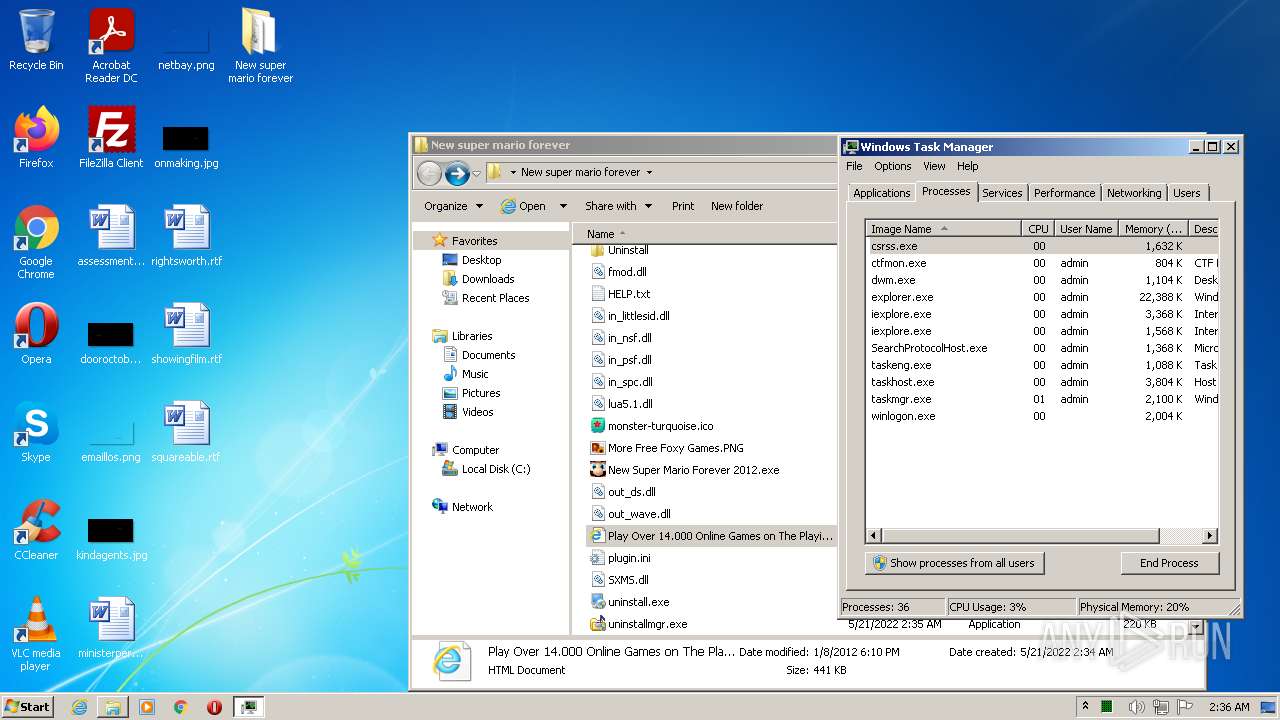
- csrss.exe (PID: 340)
- smss.exe (PID: 260)
- taskeng.exe (PID: 288)
- Dwm.exe (PID: 936)
- wininit.exe (PID: 376)
- IMEDICTUPDATE.EXE (PID: 1424)
- svchost.exe (PID: 860)
- spoolsv.exe (PID: 1236)
- svchost.exe (PID: 824)
- svchost.exe (PID: 1264)
- svchost.exe (PID: 1352)
- svchost.exe (PID: 592)
- svchost.exe (PID: 672)
- services.exe (PID: 468)
- svchost.exe (PID: 1936)
- svchost.exe (PID: 796)
- lsass.exe (PID: 484)
- svchost.exe (PID: 1088)
- svchost.exe (PID: 968)
- winlogon.exe (PID: 432)
- lsm.exe (PID: 492)
- svchost.exe (PID: 760)
- SearchIndexer.exe (PID: 2544)
- csrss.exe (PID: 384)
- DllHost.exe (PID: 984)
- SearchFilterHost.exe (PID: 2356)
- ctfmon.exe (PID: 1396)
- DllHost.exe (PID: 3544)
- DllHost.exe (PID: 2872)
- DllHost.exe (PID: 2928)
- DllHost.exe (PID: 2952)
- DllHost.exe (PID: 4080)
- SearchProtocolHost.exe (PID: 580)
- SearchFilterHost.exe (PID: 3688)
- DllHost.exe (PID: 3360)
- DllHost.exe (PID: 1328)
- LogonUI.exe (PID: 3972)
Runs injected code in another process
- iexplore.exe (PID: 3604)
RAMNIT was detected
- iexplore.exe (PID: 1128)
Connects to CnC server
- iexplore.exe (PID: 1128)
SUSPICIOUS
Creates files in the Windows directory
- svchost.exe (PID: 1088)
- svchost.exe (PID: 824)
Removes files from Windows directory
- svchost.exe (PID: 1088)
Starts Internet Explorer
- Explorer.EXE (PID: 1464)
- uninstallmgr.exe (PID: 1620)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2152)
- iexplore.exe (PID: 2584)
- mmc.exe (PID: 752)
Creates files in the program directory
- SearchIndexer.exe (PID: 2544)
Checks supported languages
- WinRAR.exe (PID: 556)
- New Super Mario Forever 2012.exe (PID: 1920)
- uninstall.exe (PID: 280)
- uninstallmgr.exe (PID: 1620)
- svchost.exe (PID: 592)
- svchost.exe (PID: 796)
- SearchIndexer.exe (PID: 2544)
Reads the computer name
- WinRAR.exe (PID: 556)
- New Super Mario Forever 2012.exe (PID: 1920)
- uninstallmgr.exe (PID: 1620)
- csrss.exe (PID: 384)
- uninstall.exe (PID: 280)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 556)
- New Super Mario Forever 2012.exe (PID: 1920)
- uninstall.exe (PID: 280)
- iexplore.exe (PID: 1128)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 556)
- New Super Mario Forever 2012.exe (PID: 1920)
- uninstall.exe (PID: 280)
- iexplore.exe (PID: 1128)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1464)
Searches for installed software
- svchost.exe (PID: 796)
Creates files in the user directory
- Explorer.EXE (PID: 1464)
Executed via COM
- DllHost.exe (PID: 3184)
Reads internet explorer settings
- mmc.exe (PID: 752)
INFO
Application launched itself
- iexplore.exe (PID: 2832)
Changes internet zones settings
- iexplore.exe (PID: 2832)
Checks supported languages
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 2152)
- csrss.exe (PID: 384)
- SearchProtocolHost.exe (PID: 2284)
- SearchFilterHost.exe (PID: 2356)
- DllHost.exe (PID: 2872)
- DllHost.exe (PID: 984)
- iexplore.exe (PID: 1128)
- iexplore.exe (PID: 3604)
- DllHost.exe (PID: 3184)
- DllHost.exe (PID: 2952)
- DllHost.exe (PID: 3544)
- DllHost.exe (PID: 2928)
- DllHost.exe (PID: 4080)
- iexplore.exe (PID: 2584)
- SearchProtocolHost.exe (PID: 580)
- SearchFilterHost.exe (PID: 3688)
- taskmgr.exe (PID: 2964)
- DllHost.exe (PID: 1328)
- DllHost.exe (PID: 3360)
- mmc.exe (PID: 752)
- LogonUI.exe (PID: 3972)
Checks Windows Trust Settings
- iexplore.exe (PID: 2152)
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 2584)
Reads settings of System Certificates
- svchost.exe (PID: 1088)
- lsass.exe (PID: 484)
- iexplore.exe (PID: 2152)
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 2584)
Creates files in the user directory
- iexplore.exe (PID: 2152)
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 1128)
- iexplore.exe (PID: 2584)
Reads internet explorer settings
- iexplore.exe (PID: 2152)
- iexplore.exe (PID: 2584)
Reads the computer name
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 2152)
- SearchFilterHost.exe (PID: 2356)
- SearchProtocolHost.exe (PID: 2284)
- DllHost.exe (PID: 2872)
- DllHost.exe (PID: 984)
- iexplore.exe (PID: 3604)
- iexplore.exe (PID: 1128)
- DllHost.exe (PID: 2952)
- DllHost.exe (PID: 2928)
- DllHost.exe (PID: 3544)
- DllHost.exe (PID: 3184)
- DllHost.exe (PID: 4080)
- iexplore.exe (PID: 2584)
- SearchProtocolHost.exe (PID: 580)
- SearchFilterHost.exe (PID: 3688)
- taskmgr.exe (PID: 2964)
- DllHost.exe (PID: 1328)
- DllHost.exe (PID: 3360)
- mmc.exe (PID: 752)
- LogonUI.exe (PID: 3972)
Changes settings of System certificates
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 2584)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2832)
- iexplore.exe (PID: 2584)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2832)
Manual execution by user
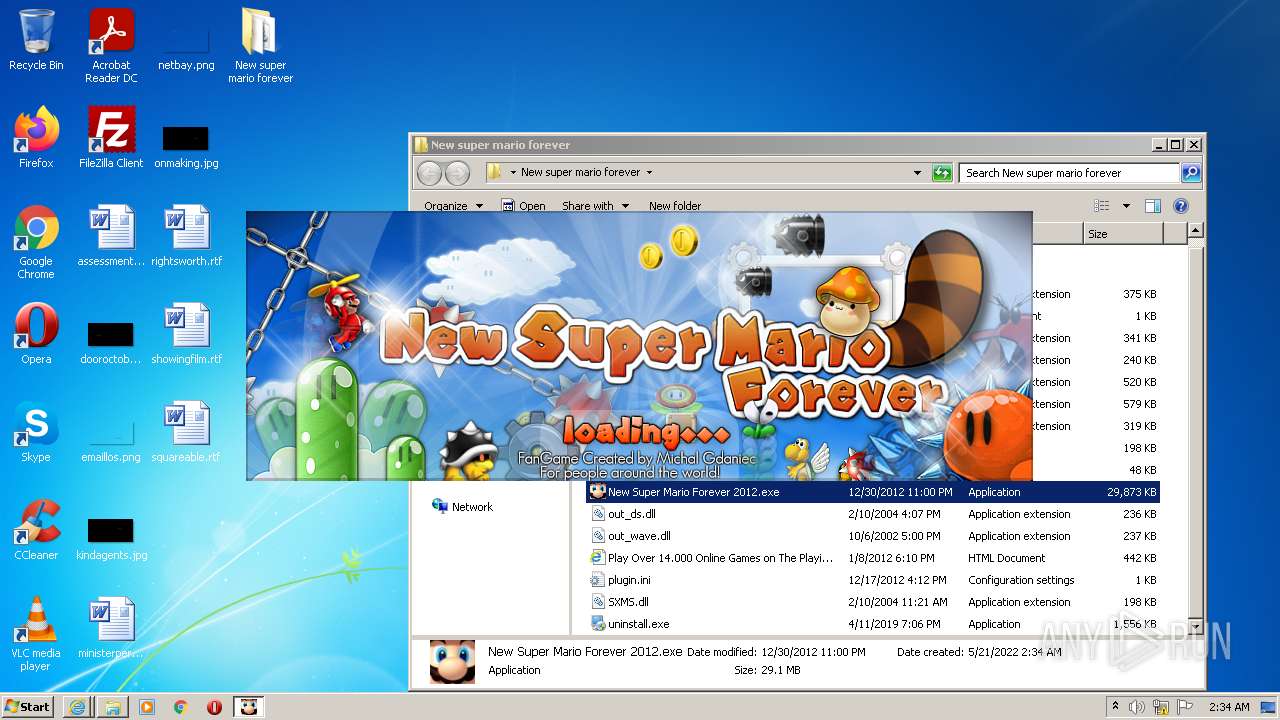
- New Super Mario Forever 2012.exe (PID: 1920)
Creates files in the program directory
- iexplore.exe (PID: 1128)
Reads CPU info
- iexplore.exe (PID: 2584)
Reads the date of Windows installation
- iexplore.exe (PID: 2832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
66
Monitored processes
53
Malicious processes
10
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 260 | \SystemRoot\System32\smss.exe | \SystemRoot\System32\smss.exe | System | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 280 | "C:\Users\admin\Desktop\New super mario forever\uninstall.exe" | C:\Users\admin\Desktop\New super mario forever\uninstall.exe | Explorer.EXE | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: Setup Application Exit code: 12 Version: 9.0.4.0 Modules
| |||||||||||||||
| 288 | taskeng.exe {BB154EF7-42D4-42F2-B57F-9CBB745DE3E3} | C:\Windows\system32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 340 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\system32\csrss.exe | taskhost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 376 | wininit.exe | C:\Windows\system32\wininit.exe | taskhost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 384 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\system32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 432 | winlogon.exe | C:\Windows\system32\winlogon.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 468 | C:\Windows\system32\services.exe | C:\Windows\system32\services.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Services and Controller app Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 484 | C:\Windows\system32\lsass.exe | C:\Windows\system32\lsass.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Security Authority Process Exit code: 0 Version: 6.1.7601.24545 (win7sp1_ldr_escrow.200102-1707) Modules
| |||||||||||||||
| 492 | C:\Windows\system32\lsm.exe | C:\Windows\system32\lsm.exe | wininit.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Local Session Manager Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
58 512
Read events
57 479
Write events
1 019
Delete events
14
Modification events
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960818 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960818 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2832) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
19
Suspicious files
438
Text files
270
Unknown types
426
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\646C991C2A28825F3CC56E0A1D1E3FA9 | der | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\646C991C2A28825F3CC56E0A1D1E3FA9 | binary | |
MD5:— | SHA256:— | |||
| 2832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F07644E38ED7C9F37D11EEC6D4335E02_7172467AE25B54F1B9D87A9343356E9B | der | |
MD5:— | SHA256:— | |||
| 2152 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_7172467AE25B54F1B9D87A9343356E9B | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
181
TCP/UDP connections
176
DNS requests
74
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2584 | iexplore.exe | GET | — | 217.160.0.45:80 | http://original.theplayingbay.com/img/1-_thumb_100x100Christmas-2011-Hidden-Objects.jpg | DE | — | — | malicious |
2584 | iexplore.exe | GET | — | 217.160.0.45:80 | http://original.theplayingbay.com/img/1-moos2012_thumb_200x200.jpg | DE | — | — | malicious |
2152 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2152 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCdUrA%2FwvrytArhIvu6cF3d | US | der | 472 b | whitelisted |
2152 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEG3aTvFLTYzNCmxS2fUJutw%3D | US | der | 471 b | whitelisted |
2584 | iexplore.exe | GET | — | 217.160.0.45:80 | http://original.theplayingbay.com/img/1-nightofvampire_thumb_200x200.png | DE | — | — | malicious |
2832 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFsL8ccV6MRJElibH7RYju4%3D | US | der | 471 b | whitelisted |
2152 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2152 | iexplore.exe | GET | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBYnd%2Bve3wCNElLpX24g2gY%3D | US | der | 471 b | whitelisted |
2832 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2152 | iexplore.exe | 142.250.185.174:443 | www.youtube.com | Google Inc. | US | whitelisted |
2152 | iexplore.exe | 23.216.77.80:80 | ctldl.windowsupdate.com | NTT DOCOMO, INC. | US | suspicious |
2832 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2832 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2152 | iexplore.exe | 172.217.18.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2832 | iexplore.exe | 142.250.185.174:443 | www.youtube.com | Google Inc. | US | whitelisted |
2152 | iexplore.exe | 142.250.185.142:443 | drive.google.com | Google Inc. | US | whitelisted |
2152 | iexplore.exe | 142.250.185.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2152 | iexplore.exe | 142.250.185.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2152 | iexplore.exe | 142.250.184.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.youtube.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.pki.goog |
| whitelisted |
crl3.digicert.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
drive.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2584 | iexplore.exe | Potential Corporate Privacy Violation | ET INFO Observed Interesting Content-Type Inbound (application/x-sh) |
1128 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
1128 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |
1128 | iexplore.exe | A Network Trojan was detected | ET TROJAN Win32/Ramnit Checkin |