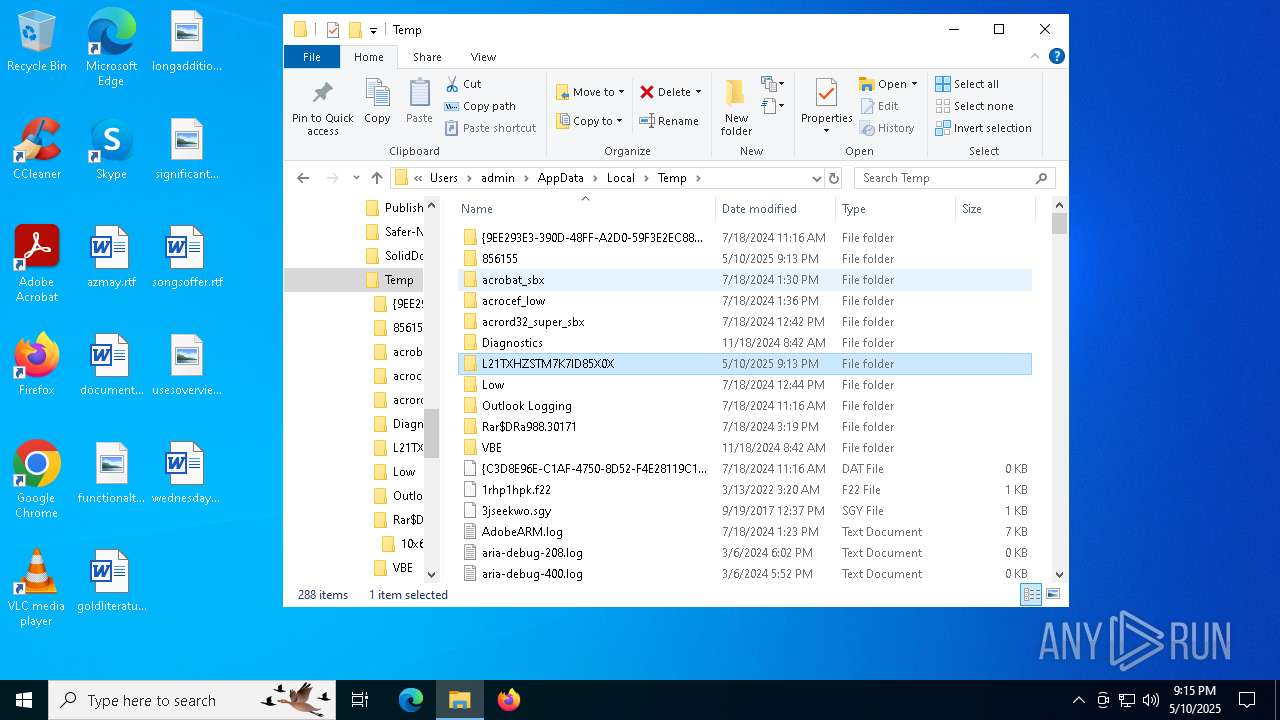
| File name: | 𝗦𝗲𝘁𝘂𝗽.exe |
| Full analysis: | https://app.any.run/tasks/b9d7d820-fbfd-42f0-993c-cc2dd8eff5b6 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 10, 2025, 21:12:32 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 2231C70DC26CF6E38ED6633CADBCA0DA |
| SHA1: | F63BAAB14E5901E1295B300F7B90FB1F6E97D128 |
| SHA256: | 0D5E1C904BFC8D4060D2D36B838E2D711BC0A7AB32DF7C9757EBE867618E6EE4 |
| SSDEEP: | 98304:njYYun+dxa96pXCcskNxlcIgRkJs7f746QWiM6HyC9iTGYsl96lrGB4gVNig62bE:7FqR |
MALICIOUS
Executing a file with an untrusted certificate
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- TransactorSmart.exe (PID: 4228)
- TransactorSmart.exe (PID: 4220)
- TransactorSmart.exe (PID: 6660)
GENERIC has been found (auto)
- TransactorSmart.exe (PID: 4228)
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
Known privilege escalation attack
- dllhost.exe (PID: 2980)
LUMMA mutex has been found
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
Steals credentials from Web Browsers
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
Actions looks like stealing of personal data
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
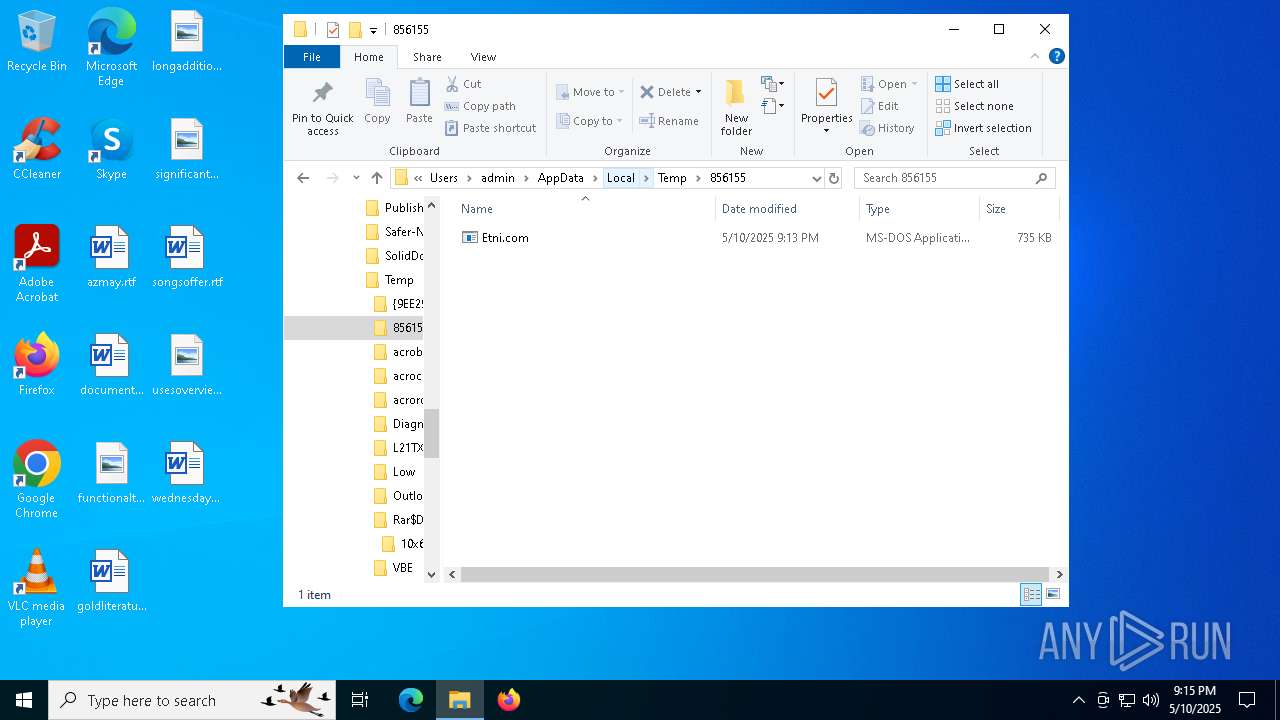
- Etni.com (PID: 812)
SUSPICIOUS
Process drops legitimate windows executable
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- TransactorSmart.exe (PID: 4228)
- Etni.com (PID: 812)
- MicrosoftEdgeWebview2Setup.exe (PID: 4200)
- MicrosoftEdgeUpdate.exe (PID: 1300)
There is functionality for taking screenshot (YARA)
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- Etni.com (PID: 812)
Executable content was dropped or overwritten
- TransactorSmart.exe (PID: 4228)
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- TransactorSmart.exe (PID: 4220)
- TransactorSmart.exe (PID: 6660)
- Etni.com (PID: 812)
- MicrosoftEdgeWebview2Setup.exe (PID: 4200)
The process drops C-runtime libraries
- TransactorSmart.exe (PID: 4228)
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
Starts itself from another location
- TransactorSmart.exe (PID: 4228)
Starts application with an unusual extension
- TransactorSmart.exe (PID: 6660)
Reads security settings of Internet Explorer
- Etni.com (PID: 812)
- MicrosoftEdgeUpdate.exe (PID: 1300)
Connects to unusual port
- Etni.com (PID: 812)
Starts POWERSHELL.EXE for commands execution
- Etni.com (PID: 812)
Starts a Microsoft application from unusual location
- MicrosoftEdgeUpdate.exe (PID: 1300)
Searches for installed software
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
Starts process via Powershell
- powershell.exe (PID: 5232)
Disables SEHOP
- MicrosoftEdgeUpdate.exe (PID: 1300)
INFO
Checks supported languages
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- TransactorSmart.exe (PID: 4228)
- TransactorSmart.exe (PID: 4220)
- tcpvcon.exe (PID: 920)
- TransactorSmart.exe (PID: 6660)
- Etni.com (PID: 812)
- MicrosoftEdgeWebview2Setup.exe (PID: 4200)
- MicrosoftEdgeUpdate.exe (PID: 1300)
- tcpvcon.exe (PID: 1912)
The sample compiled with english language support
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- TransactorSmart.exe (PID: 4228)
- TransactorSmart.exe (PID: 4220)
- MicrosoftEdgeWebview2Setup.exe (PID: 4200)
- MicrosoftEdgeUpdate.exe (PID: 1300)
- Etni.com (PID: 812)
Reads the software policy settings
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- slui.exe (PID: 5204)
- Etni.com (PID: 812)
- wermgr.exe (PID: 6740)
- MicrosoftEdgeUpdate.exe (PID: 1300)
Reads the computer name
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
- TransactorSmart.exe (PID: 4228)
- TransactorSmart.exe (PID: 4220)
- tcpvcon.exe (PID: 920)
- TransactorSmart.exe (PID: 6660)
- Etni.com (PID: 812)
- MicrosoftEdgeUpdate.exe (PID: 1300)
- tcpvcon.exe (PID: 1912)
Creates files in the program directory
- TransactorSmart.exe (PID: 4228)
- TransactorSmart.exe (PID: 4220)
- Etni.com (PID: 812)
- MicrosoftEdgeWebview2Setup.exe (PID: 4200)
Creates files or folders in the user directory
- TransactorSmart.exe (PID: 4228)
- Etni.com (PID: 812)
- wermgr.exe (PID: 6740)
Reads the machine GUID from the registry
- tcpvcon.exe (PID: 920)
- Etni.com (PID: 812)
Create files in a temporary directory
- TransactorSmart.exe (PID: 4220)
- TransactorSmart.exe (PID: 6660)
- 𝗦𝗲𝘁𝘂𝗽.exe (PID: 2656)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 2980)
Checks proxy server information
- Etni.com (PID: 812)
- wermgr.exe (PID: 6740)
- MicrosoftEdgeUpdate.exe (PID: 1300)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 1300)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 1300)
Manual execution by a user
- notepad.exe (PID: 6964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:07:04 09:14:22+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 1362944 |
| InitializedDataSize: | 2613248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x123349 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.20.0.1 |
| ProductVersionNumber: | 1.20.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | ExpressCenter |
| FileVersion: | 1, 20, 0, 1 |
| InternalName: | ExpressCenter |
| LegalCopyright: | Copyright (c) 2012 - 2014 by OpenCloner Inc. |
| OriginalFileName: | ExpressCenter.exe |
| ProductName: | OpenCloner Express Center |
| ProductVersion: | 1, 20, 0, 1 |
Total processes
154
Monitored processes
21
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\Users\admin\AppData\Local\Temp\856155\Etni.com | C:\Users\admin\AppData\Local\Temp\856155\Etni.com | TransactorSmart.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 900 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | "C:\ProgramData\asus\tcpvcon.exe" "C:\ProgramData\asus\tcpvcon.exe" /accepteula | C:\ProgramData\asus\tcpvcon.exe | — | TransactorSmart.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals TcpVcon Exit code: 0 Version: 4.18 Modules
| |||||||||||||||
| 1300 | "C:\Program Files (x86)\Microsoft\Temp\EU39D5.tmp\MicrosoftEdgeUpdate.exe" /silent /install "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=prefers" | C:\Program Files (x86)\Microsoft\Temp\EU39D5.tmp\MicrosoftEdgeUpdate.exe | MicrosoftEdgeWebview2Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Update Exit code: 2147747592 Version: 1.3.195.25 Modules
| |||||||||||||||
| 1912 | "C:\ProgramData\asus\tcpvcon.exe" "C:\ProgramData\asus\tcpvcon.exe" /accepteula | C:\ProgramData\asus\tcpvcon.exe | — | TransactorSmart.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Sysinternals TcpVcon Exit code: 0 Version: 4.18 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | "C:\Users\admin\AppData\Local\Temp\𝗦𝗲𝘁𝘂𝗽.exe" | C:\Users\admin\AppData\Local\Temp\𝗦𝗲𝘁𝘂𝗽.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ExpressCenter Exit code: 0 Version: 1, 20, 0, 1 Modules
| |||||||||||||||
| 2664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 203
Read events
11 165
Write events
36
Delete events
2
Modification events
| (PID) Process: | (2980) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (812) Etni.com | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (812) Etni.com | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (812) Etni.com | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1300) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MicrosoftEdgeUpdate.exe |
| Operation: | write | Name: | DisableExceptionChainValidation |
Value: 0 | |||
| (PID) Process: | (1300) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\PersistedPings\{75FE4386-E24E-47C7-B241-EA3B81B4C535} |
| Operation: | write | Name: | PersistedPingString |
Value: <?xml version="1.0" encoding="UTF-8"?><request protocol="3.0" updater="Omaha" updaterversion="1.3.195.25" shell_version="1.3.147.37" ismachine="1" sessionid="{072429D2-E3B4-427C-B516-CC21943E1D34}" userid="{FD984739-A122-4DB0-BE5B-46E3E09D84E4}" installsource="otherinstallcmd" requestid="{75FE4386-E24E-47C7-B241-EA3B81B4C535}" dedup="cr" domainjoined="0"><hw logical_cpus="4" physmemory="4" disk_type="2" sse="1" sse2="1" sse3="1" ssse3="1" sse41="1" sse42="1" avx="1"/><os platform="win" version="10.0.19045.4046" sp="" arch="x64" product_type="48" is_wip="0" is_in_lockdown_mode="0"/><oem product_manufacturer="DELL" product_name="DELL"/><exp etag=""r452t1+k2Tgq/HXzjvFNBRhopBWR9sbjXxqeUDH9uX0=""/><app appid="{F3C4FE00-EFD5-403B-9569-398A20F1BA4A}" version="1.3.185.17" nextversion="1.3.195.25" lang="" brand="" client=""><event eventtype="2" eventresult="1" errorcode="0" extracode1="0" system_uptime_ticks="10642356634" install_time_ms="359"/></app></request> | |||
| (PID) Process: | (1300) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\PersistedPings\{75FE4386-E24E-47C7-B241-EA3B81B4C535} |
| Operation: | write | Name: | PersistedPingTime |
Value: 133913852600360301 | |||
| (PID) Process: | (1300) MicrosoftEdgeUpdate.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\proxy |
| Operation: | write | Name: | source |
Value: auto | |||
| (PID) Process: | (1300) MicrosoftEdgeUpdate.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\PersistedPings\{75FE4386-E24E-47C7-B241-EA3B81B4C535} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1300) MicrosoftEdgeUpdate.exe | Key: | \REGISTRY\A\{9e87d65a-a1c9-b0f4-0bdb-aca84154d54a}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
Executable files
211
Suspicious files
21
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
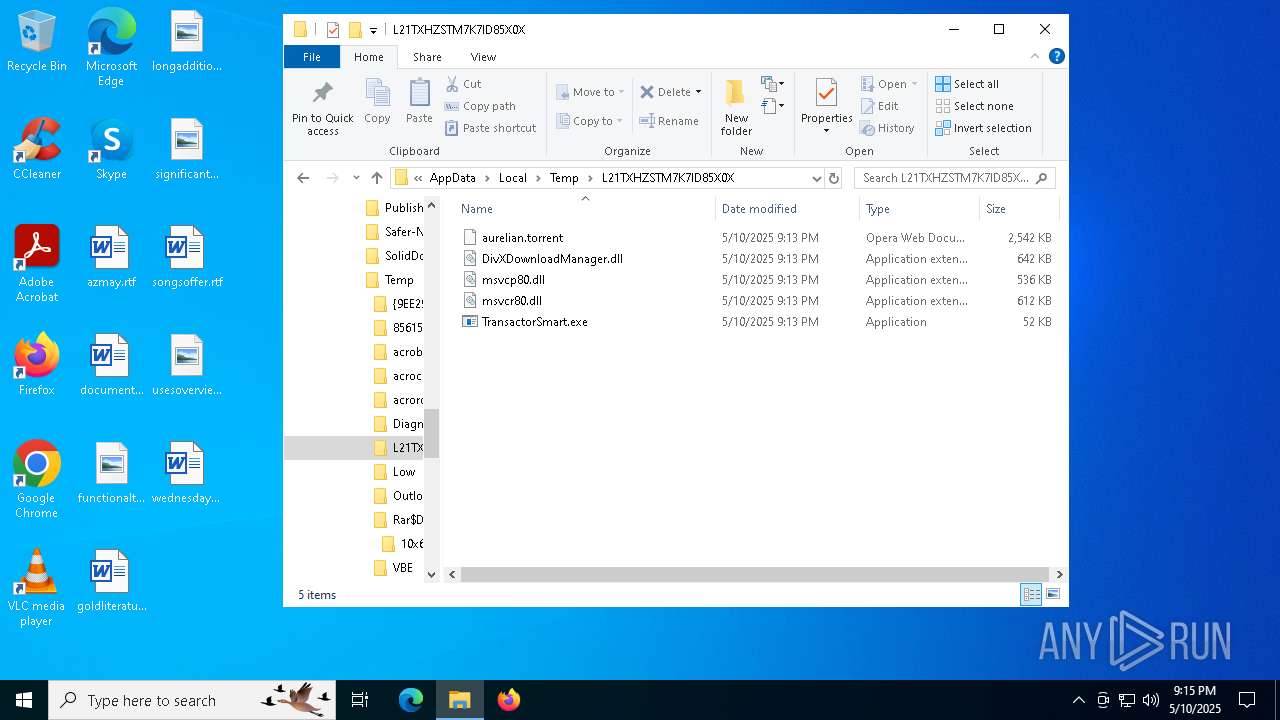
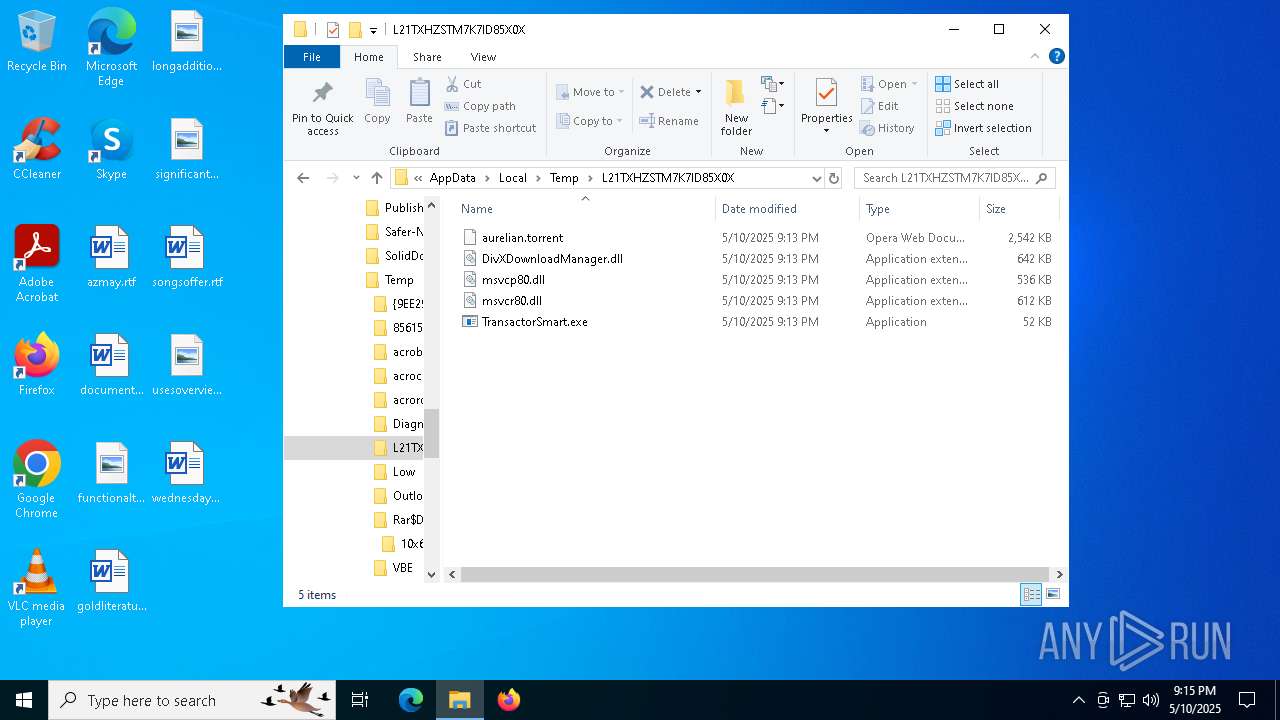
| 2656 | 𝗦𝗲𝘁𝘂𝗽.exe | C:\Users\admin\AppData\Local\Temp\L21TXHZSTM7K7ID85X0X\DivXDownloadManager.dll | executable | |
MD5:E1146619FC1DB71A1E3668371342E626 | SHA256:A39E5A8204F10AD32C0156569439624D744A4D504CBEF9925E94BCC7439FEC0E | |||
| 2656 | 𝗦𝗲𝘁𝘂𝗽.exe | C:\Users\admin\AppData\Local\Temp\L21TXHZSTM7K7ID85X0X\msvcr80.dll | executable | |
MD5:43143ABB001D4211FAB627C136124A44 | SHA256:CB8928FF2FAF2921B1EDDC267DCE1BB64E6FEE4D15B68CD32588E0F3BE116B03 | |||
| 2656 | 𝗦𝗲𝘁𝘂𝗽.exe | C:\Users\admin\AppData\Local\Temp\L21TXHZSTM7K7ID85X0X\TransactorSmart.exe | executable | |
MD5:FF254C1778AEFE5AF06889F1F999DEE3 | SHA256:94BC0C01641801F258E207ECA8227845F3F1C686E7394CE3864A6B2538B8EADB | |||
| 4228 | TransactorSmart.exe | C:\ProgramData\asus\DivXDownloadManager.dll | executable | |
MD5:E1146619FC1DB71A1E3668371342E626 | SHA256:A39E5A8204F10AD32C0156569439624D744A4D504CBEF9925E94BCC7439FEC0E | |||
| 4228 | TransactorSmart.exe | C:\ProgramData\asus\msvcr80.dll | executable | |
MD5:43143ABB001D4211FAB627C136124A44 | SHA256:CB8928FF2FAF2921B1EDDC267DCE1BB64E6FEE4D15B68CD32588E0F3BE116B03 | |||
| 4228 | TransactorSmart.exe | C:\ProgramData\asus\msvcp80.dll | executable | |
MD5:272A9E637ADCAF30B34EA184F4852836 | SHA256:35B15B78C31111DB4FA11D9C9CAD3A6F22C92DAA5E6F069DC455E72073266CC4 | |||
| 4220 | TransactorSmart.exe | C:\Users\admin\AppData\Local\Temp\F0F2B05.tmp | binary | |
MD5:1B42E08B129890AA56223E27777FD01B | SHA256:9A2F7B3AAE23D0EE42E9DDF65BC3776E8DB3F1B0010113D226862D5055DC3889 | |||
| 4228 | TransactorSmart.exe | C:\ProgramData\asus\TransactorSmart.exe | executable | |
MD5:FF254C1778AEFE5AF06889F1F999DEE3 | SHA256:94BC0C01641801F258E207ECA8227845F3F1C686E7394CE3864A6B2538B8EADB | |||
| 4220 | TransactorSmart.exe | C:\ProgramData\asus\tcpvcon.exe | executable | |
MD5:1CF39530D557CE880D7F71984928384F | SHA256:198995FECC0E38A2749B7E48C54112A959B77878683B726EE36430C4BACEC196 | |||
| 4228 | TransactorSmart.exe | C:\ProgramData\asus\aurelian.torrent | binary | |
MD5:73051F1FED9D7F0B21D4CDC48224A32B | SHA256:C050D48792242351FD33A0375F262B8743EB61164D250D27758286C9083FE3FD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
51
DNS requests
33
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1660 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1660 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
812 | Etni.com | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEk8qlS4%2B0YpYvbhdG8DOXyc%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6740 | wermgr.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
812 | Etni.com | GET | 200 | 143.204.99.128:80 | http://ocsp.r2m04.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTihuFvpmFDw5hOcIp918Jm5B3CQgQUH1KSYVaCVH%2BBZtgdPQqqMlyH3QgCEAqlOECbKpghQnC3N5zkTKU%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
serldp.digital |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
unitech.x10.mx |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | MALWARE [ANY.RUN] Suspected Domain Associated with Malware Distribution (postedtipped .top) |
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES DNS Query to Commonly Actor Abused Online Service (data-seed-prebsc-1-s1 .binance .org) |
812 | Etni.com | Misc activity | ET TA_ABUSED_SERVICES Observed Commonly Actor Abused Online Service Domain (data-seed-prebsc-1-s1 .binance .org in TLS SNI) |