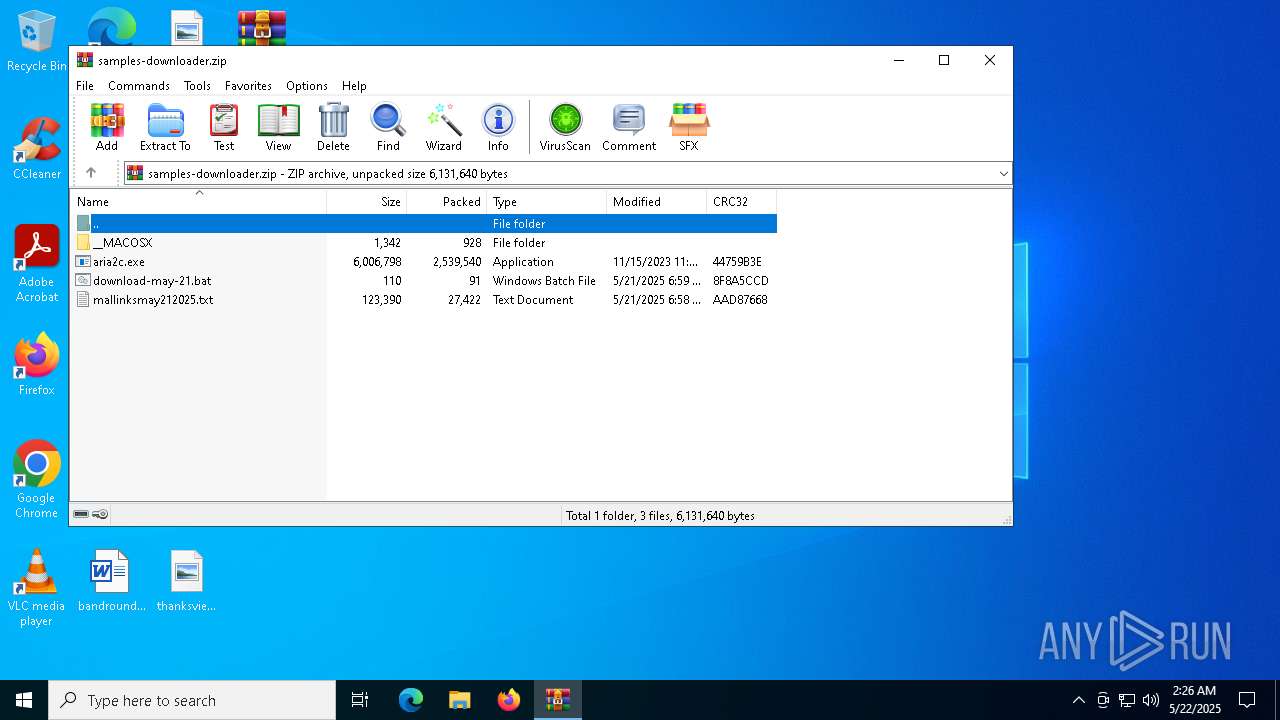
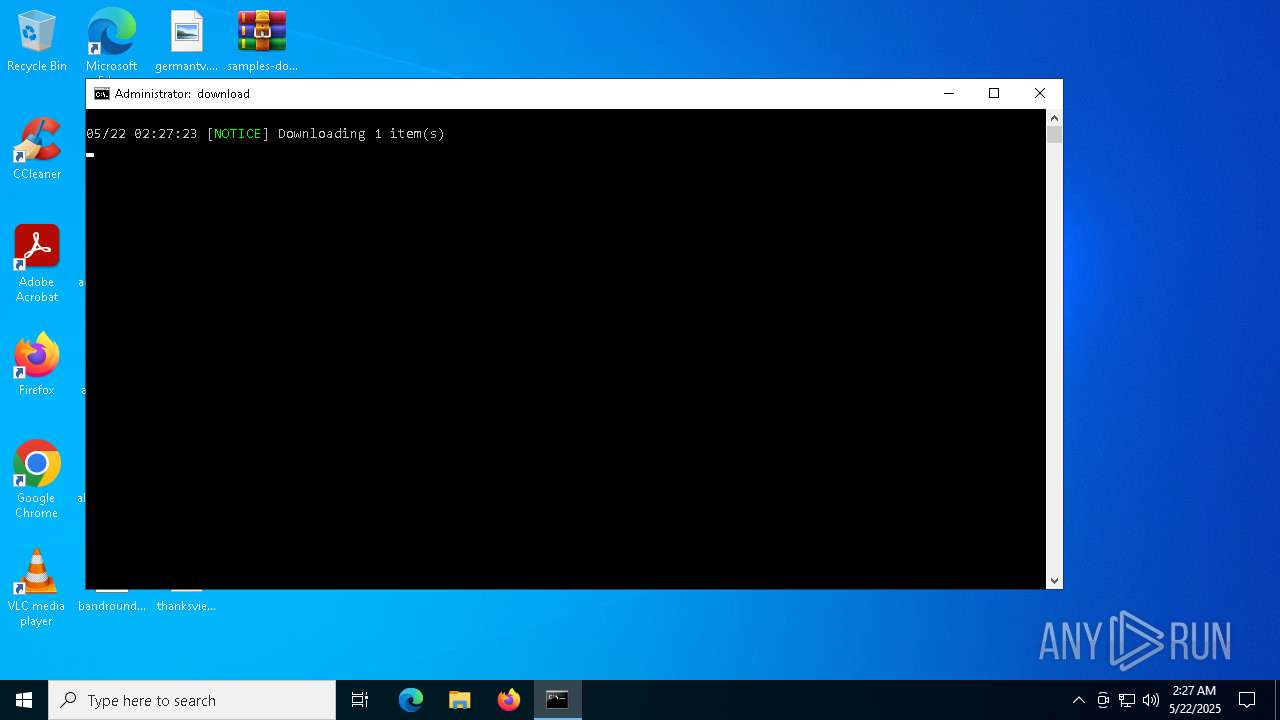
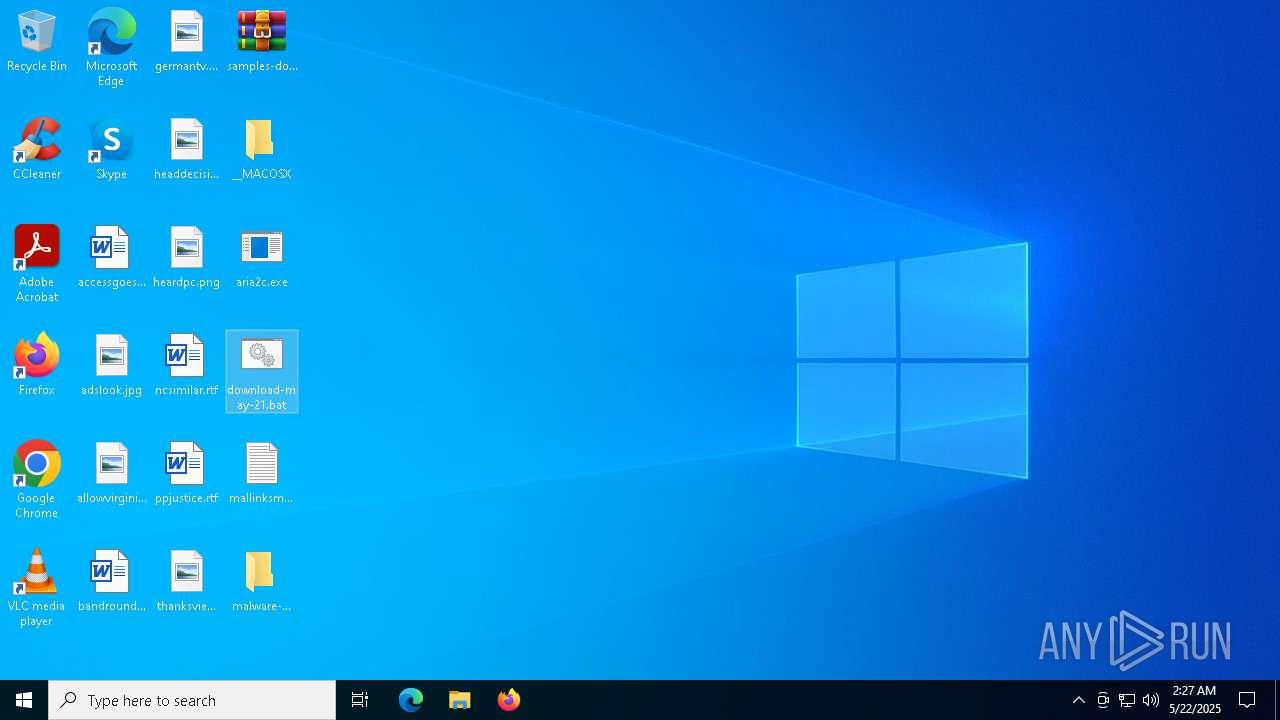
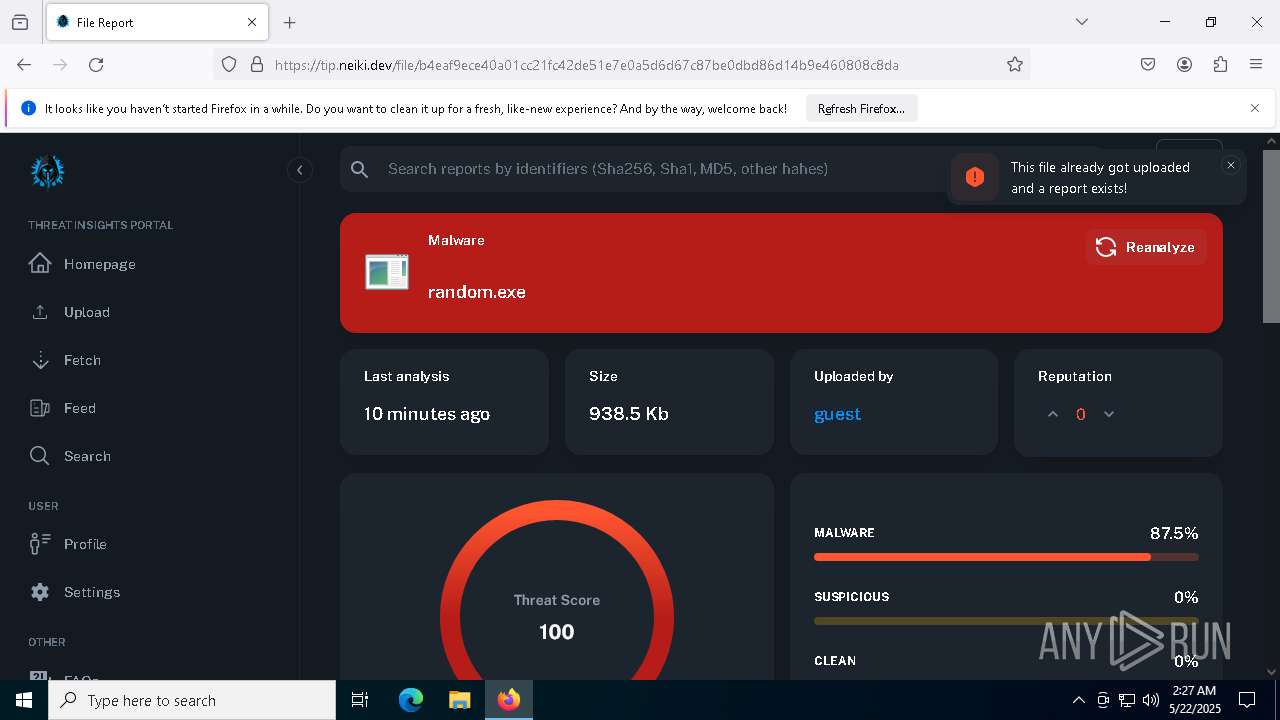
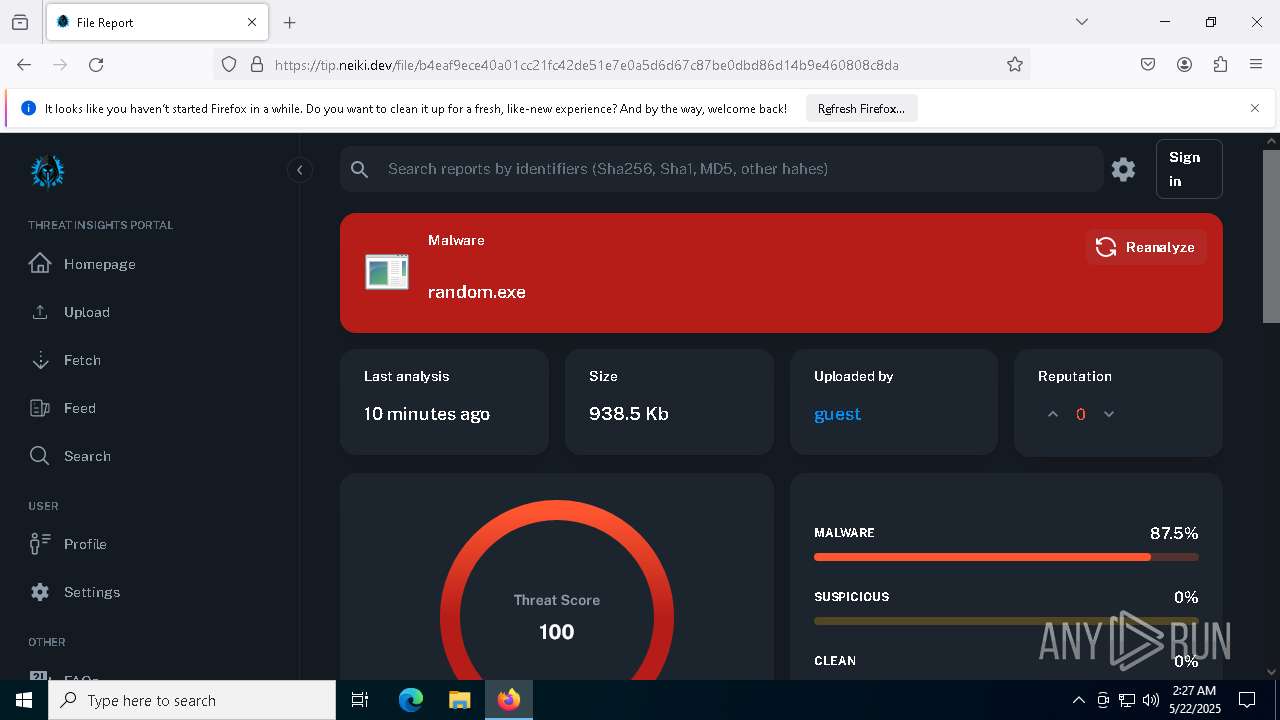
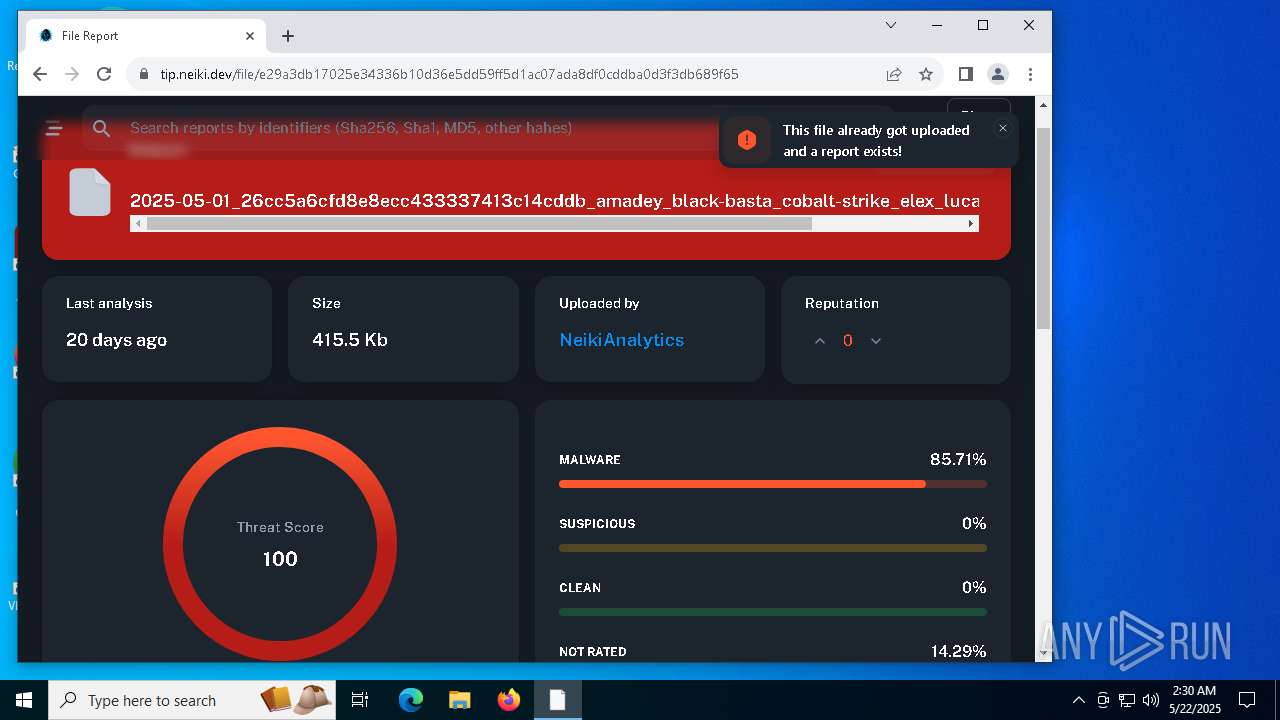
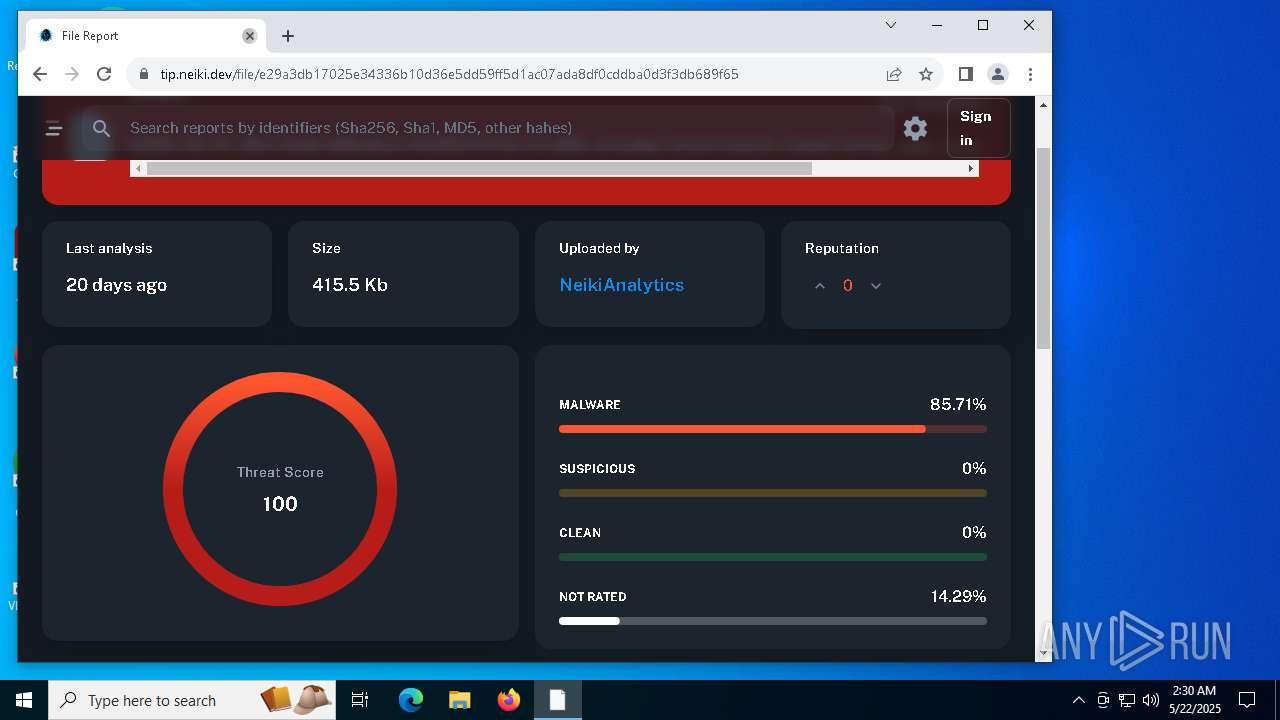
| File name: | samples-downloader.zip |
| Full analysis: | https://app.any.run/tasks/a7a11f32-10b8-42e9-a9ae-412d95881692 |
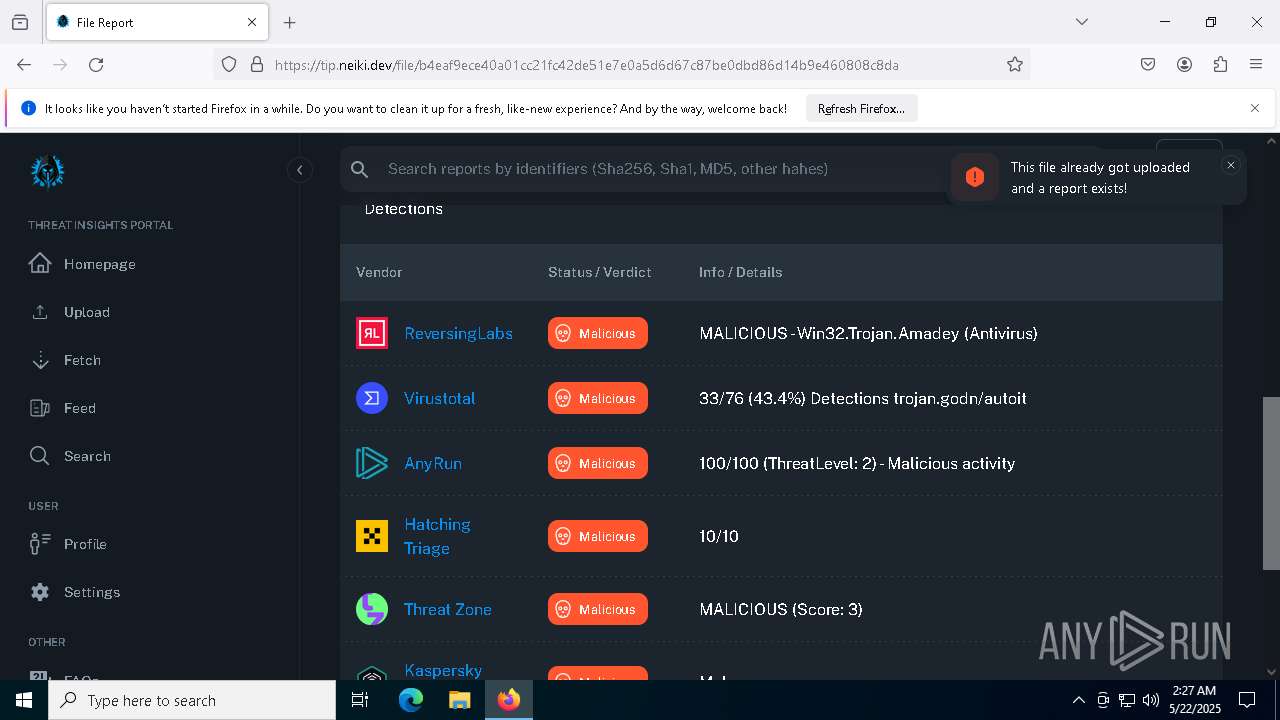
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 22, 2025, 02:26:37 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F58686141EB7738CFCC9A5664623D78A |
| SHA1: | BFCB6A5F3C72D151F653BD5CB7657052699D8119 |
| SHA256: | 0CDB7E138B0CB45BB651C3BE720FF172CD88FCAEADCF685D6549BB0EC4C118A9 |
| SSDEEP: | 98304:rTz0G8Sus6HRNAdvvtSppO6D5fBJWys8AGzBaOaRr9H953PDN43MF0q8338exMP+:OD8d8 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4776)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3156)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 6124)
- cmd.exe (PID: 8404)
Run PowerShell with an invisible window
- powershell.exe (PID: 7724)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 8556)
- powershell.exe (PID: 4120)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 7724)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 4120)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 208)
Connects to the CnC server
- ramez.exe (PID: 208)
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- bc6b73b926.exe (PID: 7608)
AMADEY has been detected (YARA)
- ramez.exe (PID: 208)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 5008)
- NSudoLG.exe (PID: 1020)
Changes Windows Defender settings
- NSudoLG.exe (PID: 1020)
LUMMA has been detected (YARA)
- bc6b73b926.exe (PID: 7608)
Starts SC.EXE for service management
- cmd.exe (PID: 5008)
SUSPICIOUS
Process requests binary or script from the Internet
- aria2c.exe (PID: 8172)
- powershell.exe (PID: 7724)
- ramez.exe (PID: 208)
- powershell.exe (PID: 3020)
- bc6b73b926.exe (PID: 7608)
- powershell.exe (PID: 4120)
Potential Corporate Privacy Violation
- aria2c.exe (PID: 8172)
- powershell.exe (PID: 7724)
- ramez.exe (PID: 208)
- bc6b73b926.exe (PID: 7608)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 4120)
Connects to the server without a host name
- aria2c.exe (PID: 8172)
- powershell.exe (PID: 7724)
- ramez.exe (PID: 208)
- powershell.exe (PID: 3020)
- bc6b73b926.exe (PID: 7608)
- powershell.exe (PID: 4120)
Starts CMD.EXE for commands execution
- random.exe (PID: 7496)
- fa517635b3.exe (PID: 2644)
- cmd.exe (PID: 4112)
- NSudoLG.exe (PID: 7436)
- cmd.exe (PID: 2192)
- cmd.exe (PID: 5008)
- dc734431a4.exe (PID: 7912)
- Unlocker.exe (PID: 7572)
- Unlocker.exe (PID: 8076)
- Unlocker.exe (PID: 8176)
- random.exe (PID: 4408)
- random.exe (PID: 6476)
Executable content was dropped or overwritten
- aria2c.exe (PID: 8172)
- powershell.exe (PID: 7724)
- TempTIVJ3W20YZKRC2DBUFW5MPXHKJI9UJO6.EXE (PID: 5164)
- ramez.exe (PID: 208)
- bc6b73b926.exe (PID: 7608)
- powershell.exe (PID: 3020)
- fa517635b3.exe (PID: 2644)
- 7z.exe (PID: 6824)
- Unlocker.exe (PID: 8076)
- cmd.exe (PID: 5008)
- powershell.exe (PID: 4120)
Manipulates environment variables
- powershell.exe (PID: 7724)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 8556)
- powershell.exe (PID: 4120)
Probably download files using WebClient
- mshta.exe (PID: 3396)
- mshta.exe (PID: 6240)
- mshta.exe (PID: 4376)
- mshta.exe (PID: 6644)
Found IP address in command line
- powershell.exe (PID: 7724)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 8556)
- powershell.exe (PID: 4120)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 3396)
- NSudoLG.exe (PID: 1020)
- mshta.exe (PID: 6240)
- mshta.exe (PID: 4376)
- mshta.exe (PID: 6644)
Starts process via Powershell
- powershell.exe (PID: 7724)
- powershell.exe (PID: 3020)
- powershell.exe (PID: 4120)
- powershell.exe (PID: 8556)
Starts itself from another location
- TempTIVJ3W20YZKRC2DBUFW5MPXHKJI9UJO6.EXE (PID: 5164)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 208)
- bc6b73b926.exe (PID: 7608)
- svchost.exe (PID: 2196)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 208)
Application launched itself
- cmd.exe (PID: 4112)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 2192)
- ie4uinit.exe (PID: 6264)
- setup.exe (PID: 8036)
- setup.exe (PID: 7448)
- setup.exe (PID: 3800)
Executing commands from a ".bat" file
- fa517635b3.exe (PID: 2644)
- cmd.exe (PID: 4112)
- cmd.exe (PID: 2192)
- NSudoLG.exe (PID: 7436)
Starts application with an unusual extension
- cmd.exe (PID: 4688)
- cmd.exe (PID: 5008)
The executable file from the user directory is run by the CMD process
- NSudoLG.exe (PID: 7436)
- NSudoLG.exe (PID: 1020)
- 7z.exe (PID: 6824)
- Unlocker.exe (PID: 7572)
- Unlocker.exe (PID: 8076)
- Unlocker.exe (PID: 8176)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4688)
- cmd.exe (PID: 5008)
Get information on the list of running processes
- cmd.exe (PID: 8076)
- cmd.exe (PID: 5008)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 8164)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 1020)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5008)
There is functionality for taking screenshot (YARA)
- ramez.exe (PID: 208)
Drops 7-zip archiver for unpacking
- fa517635b3.exe (PID: 2644)
Windows service management via SC.EXE
- sc.exe (PID: 7796)
- sc.exe (PID: 7400)
- sc.exe (PID: 7408)
- sc.exe (PID: 8088)
- sc.exe (PID: 7240)
- sc.exe (PID: 7468)
- sc.exe (PID: 4804)
- sc.exe (PID: 6624)
- sc.exe (PID: 3836)
- sc.exe (PID: 4624)
- sc.exe (PID: 4420)
- sc.exe (PID: 4716)
- sc.exe (PID: 4460)
- sc.exe (PID: 8064)
- sc.exe (PID: 6712)
- sc.exe (PID: 5300)
- sc.exe (PID: 7324)
- sc.exe (PID: 776)
- sc.exe (PID: 7140)
- sc.exe (PID: 6844)
- sc.exe (PID: 2336)
- sc.exe (PID: 6756)
- sc.exe (PID: 8184)
- sc.exe (PID: 2096)
- sc.exe (PID: 8056)
- sc.exe (PID: 240)
- sc.exe (PID: 2504)
- sc.exe (PID: 7936)
- sc.exe (PID: 7972)
- sc.exe (PID: 2740)
- sc.exe (PID: 6820)
- sc.exe (PID: 7608)
- sc.exe (PID: 2896)
- sc.exe (PID: 4056)
- sc.exe (PID: 5988)
- sc.exe (PID: 6708)
- sc.exe (PID: 6652)
- sc.exe (PID: 7952)
- sc.exe (PID: 7060)
- sc.exe (PID: 7736)
- sc.exe (PID: 7380)
Starts SC.EXE for service management
- cmd.exe (PID: 7568)
- cmd.exe (PID: 5008)
- cmd.exe (PID: 4652)
- cmd.exe (PID: 6824)
- cmd.exe (PID: 5240)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6676)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 6976)
Drops a system driver (possible attempt to evade defenses)
- Unlocker.exe (PID: 8076)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 8032)
Stops a currently running service
- sc.exe (PID: 3676)
- sc.exe (PID: 3144)
- sc.exe (PID: 5696)
- sc.exe (PID: 4692)
- sc.exe (PID: 5896)
- sc.exe (PID: 2316)
- sc.exe (PID: 7708)
- sc.exe (PID: 1708)
- sc.exe (PID: 7120)
- sc.exe (PID: 7620)
- sc.exe (PID: 4464)
- sc.exe (PID: 7780)
- sc.exe (PID: 5504)
- sc.exe (PID: 4608)
- sc.exe (PID: 5364)
- sc.exe (PID: 7940)
- sc.exe (PID: 7748)
Process drops legitimate windows executable
- cmd.exe (PID: 5008)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 7012)
- schtasks.exe (PID: 5576)
- schtasks.exe (PID: 4812)
- schtasks.exe (PID: 720)
- schtasks.exe (PID: 7776)
Executes application which crashes
- explorer.exe (PID: 7336)
The process executes via Task Scheduler
- ramez.exe (PID: 9172)
- ramez.exe (PID: 10136)
- ramez.exe (PID: 3796)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 9320)
INFO
Manual execution by a user
- WinRAR.exe (PID: 7684)
- cmd.exe (PID: 8108)
- notepad.exe (PID: 7728)
- firefox.exe (PID: 1452)
- random.exe (PID: 7496)
- random.exe (PID: 6476)
- random.exe (PID: 4408)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7684)
Checks supported languages
- aria2c.exe (PID: 8172)
Reads security settings of Internet Explorer
- notepad.exe (PID: 7728)
Reads the computer name
- aria2c.exe (PID: 8172)
Reads the machine GUID from the registry
- aria2c.exe (PID: 8172)
Application launched itself
- firefox.exe (PID: 5736)
- firefox.exe (PID: 1452)
- chrmstp.exe (PID: 6800)
- chrmstp.exe (PID: 6768)
- chrome.exe (PID: 516)
- chrmstp.exe (PID: 8572)
- chrmstp.exe (PID: 8672)
The sample compiled with english language support
- aria2c.exe (PID: 8172)
- ramez.exe (PID: 208)
- fa517635b3.exe (PID: 2644)
- Unlocker.exe (PID: 8076)
- cmd.exe (PID: 5008)
Reads the software policy settings
- slui.exe (PID: 7276)
The executable file from the user directory is run by the Powershell process
- TempTIVJ3W20YZKRC2DBUFW5MPXHKJI9UJO6.EXE (PID: 5164)
- TempZBH81QHAKUMLJ3PNXFQXZKZRUBRSF6SG.EXE (PID: 1912)
- TempXZ9VWWHSRIEMBWJN9BKL4QLVSBQVJLQJ.EXE (PID: 8276)
- TempXZ9VWWHSRIEMBWJN9BKL4QLVSBQVJLQJ.EXE (PID: 9952)
Changes the display of characters in the console
- cmd.exe (PID: 4688)
- cmd.exe (PID: 5008)
Checks operating system version
- cmd.exe (PID: 5008)
Starts MODE.COM to configure console settings
- mode.com (PID: 7012)
Themida protector has been detected
- bc6b73b926.exe (PID: 7608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(208) ramez.exe
C2185.156.72.96
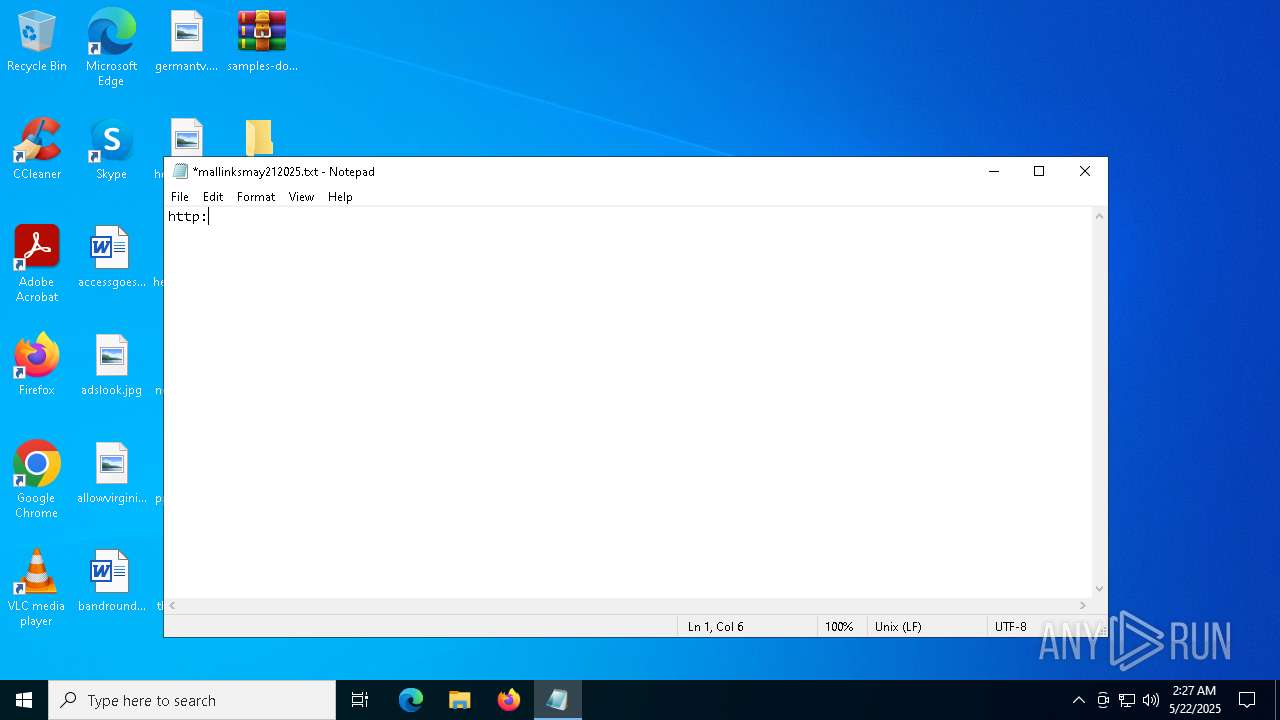
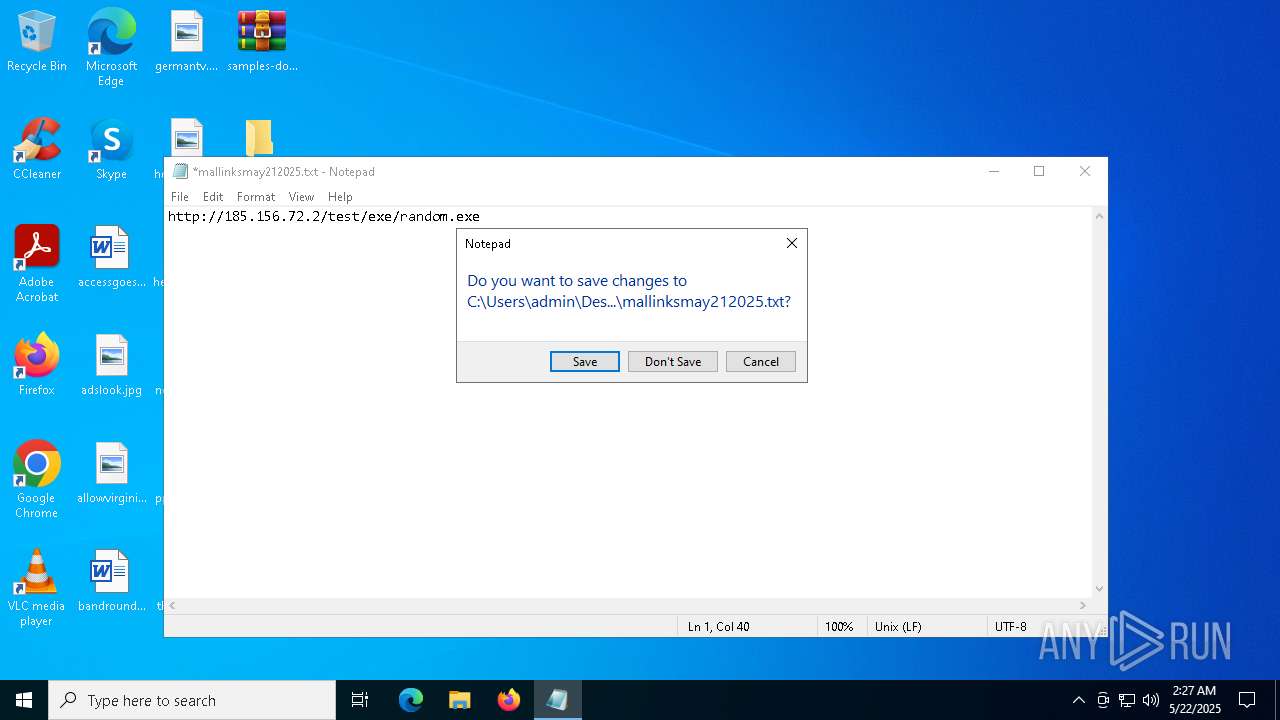
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
d610cf342e
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
/te4h2nus/index.php
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
ramez.exe
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
185.156.72.96
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
Lumma
(PID) Process(7608) bc6b73b926.exe
C2 (9)escczlv.top/bufi
korxddl.top/qidz
cornerdurv.top/adwq
localixbiw.top/zlpa
diecam.top/laur
citellcagt.top/gjtu
bogtkr.top/zhyk
narrathfpt.top/tekq
ordntx.top/pxla
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:21 20:58:48 |
| ZipCRC: | 0xaad87668 |
| ZipCompressedSize: | 27422 |
| ZipUncompressedSize: | 123390 |
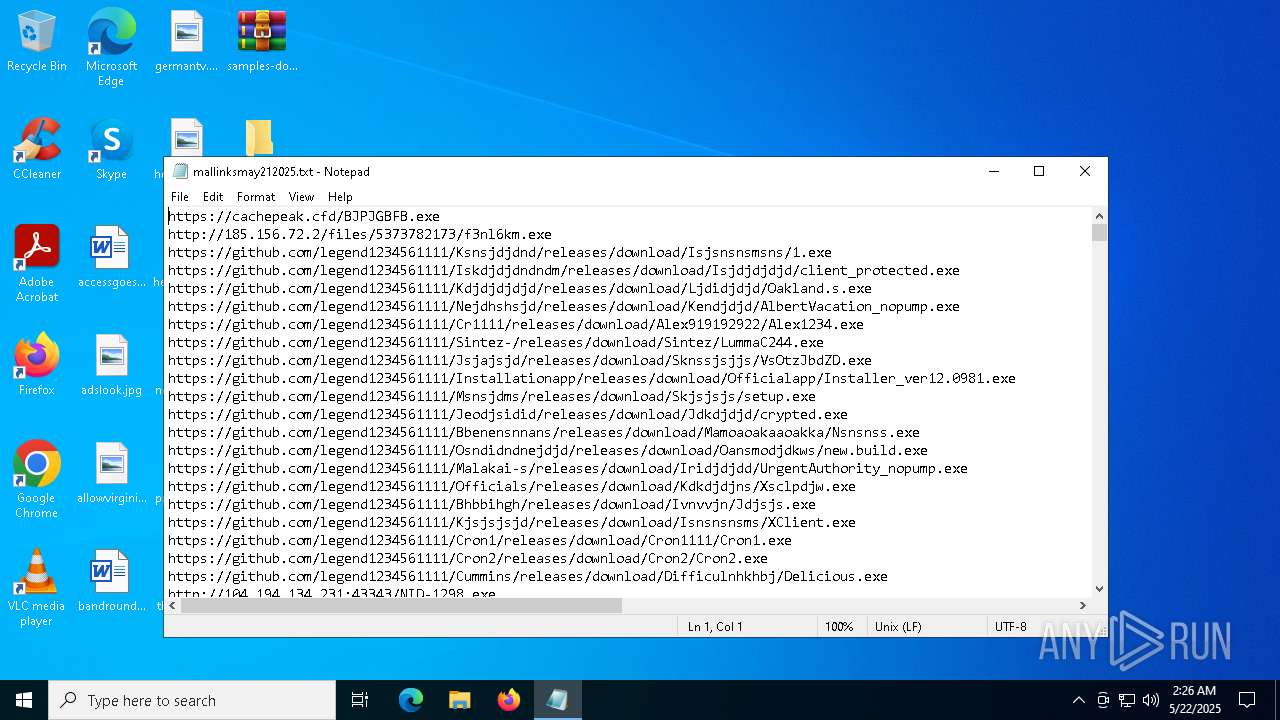
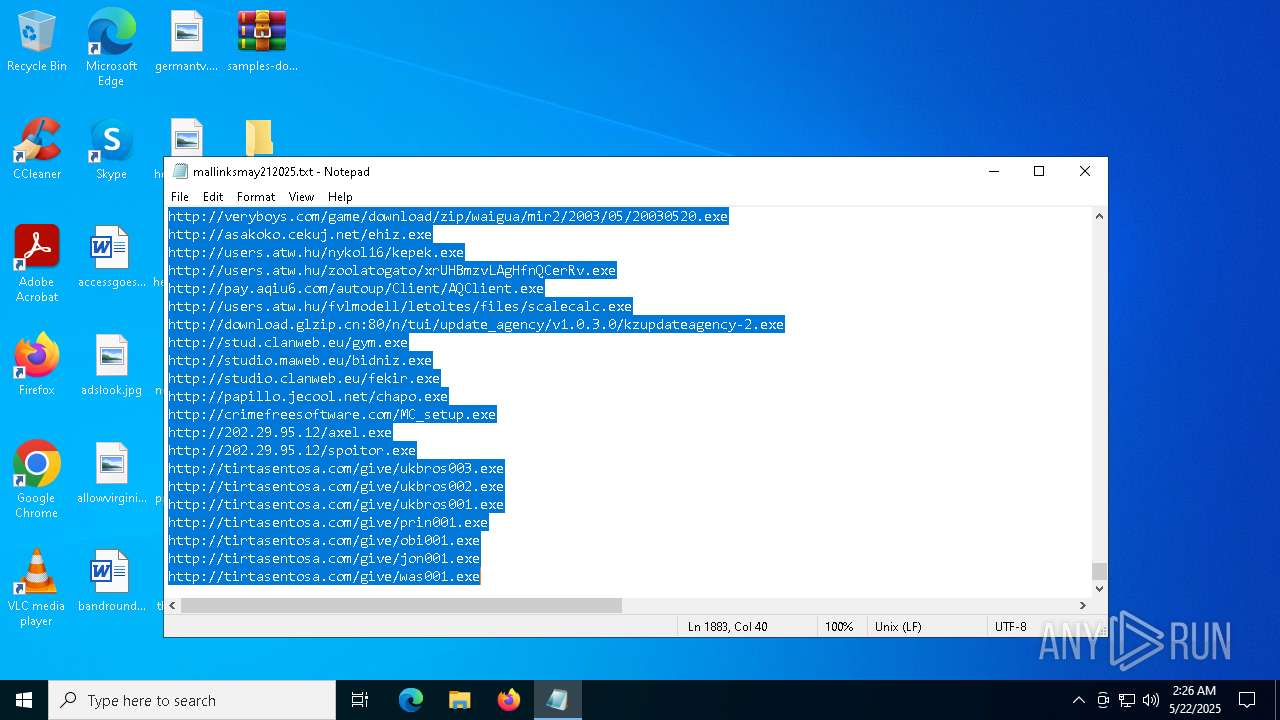
| ZipFileName: | mallinksmay212025.txt |
Total processes
475
Monitored processes
311
Malicious processes
23
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5348 -childID 4 -isForBrowser -prefsHandle 5356 -prefMapHandle 5200 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {642df636-4eec-44f4-8312-9d732f71bca6} 5736 "\\.\pipe\gecko-crash-server-pipe.5736" 224cb2dc4d0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 208 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | TempTIVJ3W20YZKRC2DBUFW5MPXHKJI9UJO6.EXE | ||||||||||||
User: admin Integrity Level: HIGH Modules
Amadey(PID) Process(208) ramez.exe C2185.156.72.96 URLhttp://185.156.72.96/te4h2nus/index.php Version5.34 Options Drop directoryd610cf342e Drop nameramez.exe Strings (125)lv: msi Kaspersky Lab av: | # " \App 00000422 dm: Powershell.exe ProgramData\ ps1 rundll32 http:// Content-Disposition: form-data; name="data"; filename=" SOFTWARE\Microsoft\Windows NT\CurrentVersion dll SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders id: VideoID cred.dll|clip.dll| 0000043f cmd 00000423 SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName -executionpolicy remotesigned -File " 2022 ------ 2016 og: \0000 CurrentBuild 2019 ::: S-%lu- " && timeout 1 && del ProductName Panda Security ESET SOFTWARE\Microsoft\Windows\CurrentVersion\Run /k +++ ?scr=1 Doctor Web GET SYSTEM\ControlSet001\Services\BasicDisplay\Video /quiet .jpg d610cf342e vs: sd: rundll32.exe "taskkill /f /im " pc: random = 360TotalSecurity <d> wb Content-Type: multipart/form-data; boundary=---- Startup Norton && Exit" os: https:// SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce 2025 Avira %-lu zip POST "
Content-Type: application/octet-stream Rem /te4h2nus/index.php ------ 5.34 <c> clip.dll AVAST Software \ shell32.dll " && ren e3 ramez.exe kernel32.dll DefaultSettings.XResolution d1 DefaultSettings.YResolution 185.156.72.96 r= cred.dll -- GetNativeSystemInfo -%lu ComputerName &unit= Keyboard Layout\Preload SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders ar: Sophos %USERPROFILE% exe e1 e2 st=s Programs 0123456789 un: rb bi: abcdefghijklmnopqrstuvwxyz0123456789-_ SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\ cmd /C RMDIR /s/q Bitdefender -unicode- AVG WinDefender && shutdown -s -t 0 Comodo 00000419 Content-Type: application/x-www-form-urlencoded /Plugins/ Main | |||||||||||||||
| 240 | sc config "WdBoot" start= disabled | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Service Control Manager Configuration Tool Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=1972 --field-trial-handle=1976,i,12655325639753308215,3419553263359017474,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 456 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2720 -childID 1 -isForBrowser -prefsHandle 2808 -prefMapHandle 2804 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1536 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {740c5b7a-296a-4871-a50f-774ff1e9992b} 5736 "\\.\pipe\gecko-crash-server-pipe.5736" 224c8ea2f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 456 | reg add "HKU\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize" /v "AppsUseLightTheme" /t reg_dword /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | taskkill /f /pid "8076" | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 672 | C:\WINDOWS\system32\RunDll32.exe C:\WINDOWS\system32\migration\WininetPlugin.dll,MigrateCacheForUser /m /0 | C:\Windows\System32\rundll32.exe | — | ie4uinit.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | reg query "HKLM\System\CurrentControlSet\Services\MsSecCore" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
146 506
Read events
144 580
Write events
1 719
Delete events
207
Modification events
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\samples-downloader.zip | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (4776) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
40
Suspicious files
774
Text files
353
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5736 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7684 | WinRAR.exe | C:\Users\admin\Desktop\mallinksmay212025.txt | text | |
MD5:FDD847CCD4F083FC18A204B85BA1B4FD | SHA256:76237DA3E136EE92F686DC310C59D8361DCDD51C114FE15E983E82BF4CB0388B | |||
| 5736 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 8172 | aria2c.exe | C:\Users\admin\Desktop\malware-samples\random.exe.aria2__temp | binary | |
MD5:5E4A0CD6BB2A4CE7FC776EDB4D3718A5 | SHA256:25C4BADCFC289AFF4E247EB3ABB293DDB1919ADDE93A4D7F6B40FE6C5A406C32 | |||
| 7684 | WinRAR.exe | C:\Users\admin\Desktop\__MACOSX\._mallinksmay212025.txt | binary | |
MD5:1886F36505D613B45C22F6C579CD87DF | SHA256:7F5F135B8046962AD4800489D921810BB6169E29C1ADC4F31BFA491D8F3AF29C | |||
| 7684 | WinRAR.exe | C:\Users\admin\Desktop\__MACOSX\._download-may-21.bat | binary | |
MD5:6289D0F52DC014A8A0DD2C474BFA6C29 | SHA256:BC4EE076EFA7EF86EFB000D83C4D932A89C4AFDA4E9A9089B0DDE1214F75EBC4 | |||
| 5736 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 5736 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:B472EEFAE8133B2F56FE41528BF96DE9 | SHA256:50B89DCA6E2980959E7291C19CE564CEDE1F9F236102F214D00F9AF56EF0B93E | |||
| 5736 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7684 | WinRAR.exe | C:\Users\admin\Desktop\__MACOSX\._aria2c.exe | binary | |
MD5:96B648177E7071D0D762076839547706 | SHA256:3B056E59C231DED8CF301CC76EE6A493E7559D23817F9982E27FDF350766E84F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
200
DNS requests
183
Threats
58
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7916 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7916 | SIHClient.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5736 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
8172 | aria2c.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/test/exe/random.exe | unknown | — | — | malicious |
5736 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5736 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5736 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
5736 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5216 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7916 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7916 | SIHClient.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
8172 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
8172 | aria2c.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
8172 | aria2c.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
8172 | aria2c.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
7724 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |