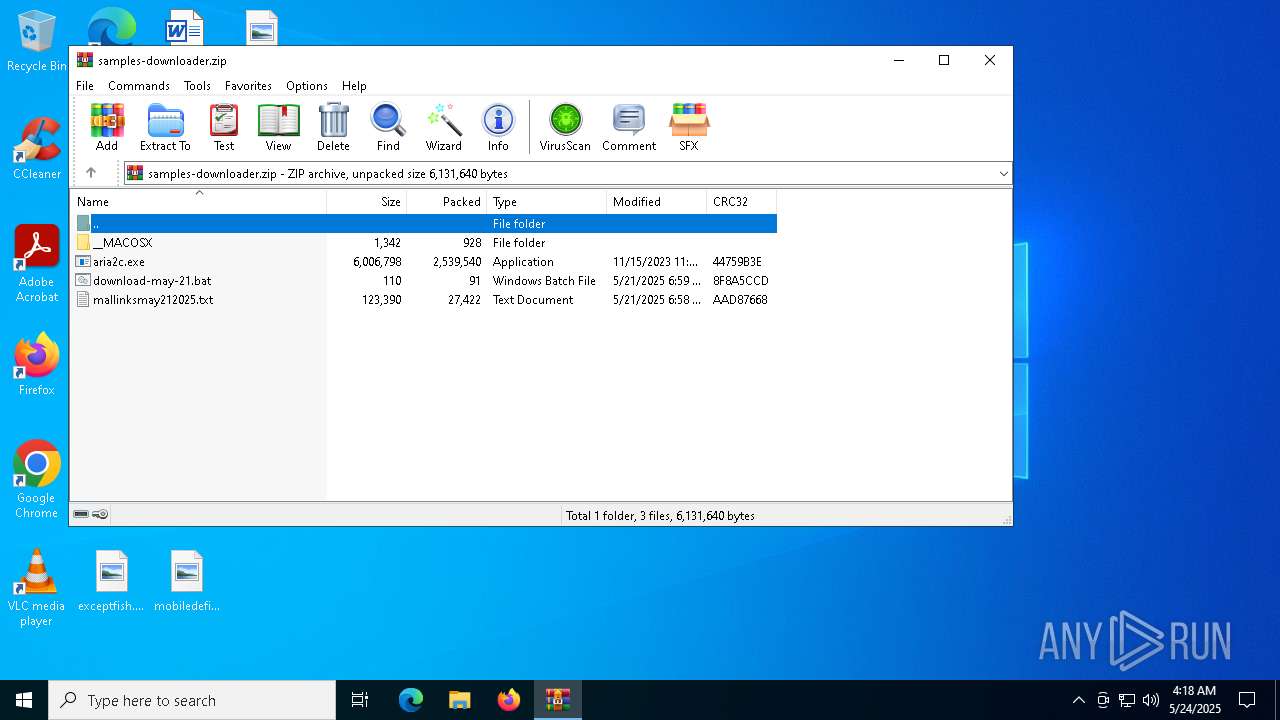
| File name: | samples-downloader.zip |
| Full analysis: | https://app.any.run/tasks/35415228-aabd-4a3e-86b4-4b03e1b26dcb |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 24, 2025, 04:18:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F58686141EB7738CFCC9A5664623D78A |
| SHA1: | BFCB6A5F3C72D151F653BD5CB7657052699D8119 |
| SHA256: | 0CDB7E138B0CB45BB651C3BE720FF172CD88FCAEADCF685D6549BB0EC4C118A9 |
| SSDEEP: | 98304:rTz0G8Sus6HRNAdvvtSppO6D5fBJWys8AGzBaOaRr9H953PDN43MF0q8338exMP+:OD8d8 |
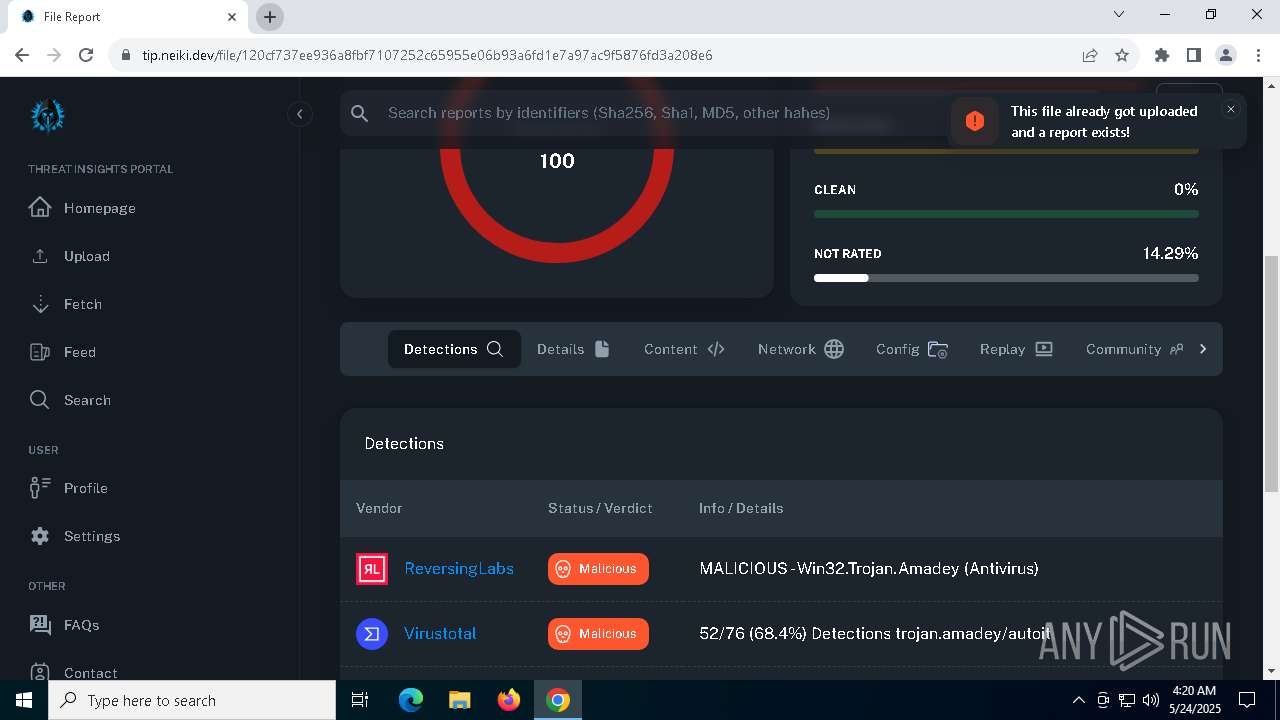
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7532)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1128)
- cmd.exe (PID: 5044)
- cmd.exe (PID: 8148)
- cmd.exe (PID: 132)
- cmd.exe (PID: 6972)
Run PowerShell with an invisible window
- powershell.exe (PID: 1196)
- powershell.exe (PID: 4740)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 7244)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3100)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 1132)
Connects to the CnC server
- ramez.exe (PID: 1132)
AMADEY has been detected (YARA)
- ramez.exe (PID: 1132)
SUSPICIOUS
Connects to the server without a host name
- aria2c.exe (PID: 2552)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 3100)
- ramez.exe (PID: 1132)
Potential Corporate Privacy Violation
- aria2c.exe (PID: 2552)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 7244)
Executable content was dropped or overwritten
- aria2c.exe (PID: 2552)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 1196)
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 7524)
Process requests binary or script from the Internet
- aria2c.exe (PID: 2552)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 7244)
Starts CMD.EXE for commands execution
- random.exe (PID: 2772)
- random.exe (PID: 1088)
- random.exe (PID: 5164)
- random.exe (PID: 7312)
- random.exe (PID: 5332)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 8172)
- mshta.exe (PID: 5172)
- mshta.exe (PID: 8112)
- mshta.exe (PID: 232)
- mshta.exe (PID: 7968)
Manipulates environment variables
- powershell.exe (PID: 1196)
- powershell.exe (PID: 4740)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 3100)
Starts process via Powershell
- powershell.exe (PID: 1196)
- powershell.exe (PID: 4740)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 7244)
- powershell.exe (PID: 3100)
Probably download files using WebClient
- mshta.exe (PID: 8172)
- mshta.exe (PID: 5172)
- mshta.exe (PID: 8112)
- mshta.exe (PID: 232)
- mshta.exe (PID: 7968)
Found IP address in command line
- powershell.exe (PID: 4740)
- powershell.exe (PID: 1196)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 6136)
- powershell.exe (PID: 4380)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 7244)
Starts itself from another location
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 7524)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 1132)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 1132)
There is functionality for taking screenshot (YARA)
- ramez.exe (PID: 1132)
The process executes via Task Scheduler
- ramez.exe (PID: 8104)
- ramez.exe (PID: 3032)
INFO
Manual execution by a user
- chrome.exe (PID: 864)
- WinRAR.exe (PID: 8120)
- notepad.exe (PID: 8184)
- cmd.exe (PID: 2240)
- random.exe (PID: 2772)
- random.exe (PID: 5164)
- random.exe (PID: 1088)
- random.exe (PID: 7312)
- random.exe (PID: 5332)
- ramez.exe (PID: 516)
- ramez.exe (PID: 5936)
- ramez.exe (PID: 684)
- ramez.exe (PID: 7288)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8120)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8184)
Application launched itself
- chrome.exe (PID: 864)
Reads the machine GUID from the registry
- aria2c.exe (PID: 2552)
Checks supported languages
- aria2c.exe (PID: 2552)
Reads the computer name
- aria2c.exe (PID: 2552)
The sample compiled with english language support
- aria2c.exe (PID: 2552)
Reads the software policy settings
- slui.exe (PID: 7708)
The executable file from the user directory is run by the Powershell process
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 7524)
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 2064)
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 6576)
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 4976)
- TempFHBXRDPWNCM0WW4J9JWHWSYYDFPYJMXU.EXE (PID: 7304)
- TempCHV2X7APEIVTC7A1JOY6NQL4CKYIJFLB.EXE (PID: 5260)
- TempELC1JU2127OL28DDY86CJQWH3DMHWDXC.EXE (PID: 2192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(1132) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
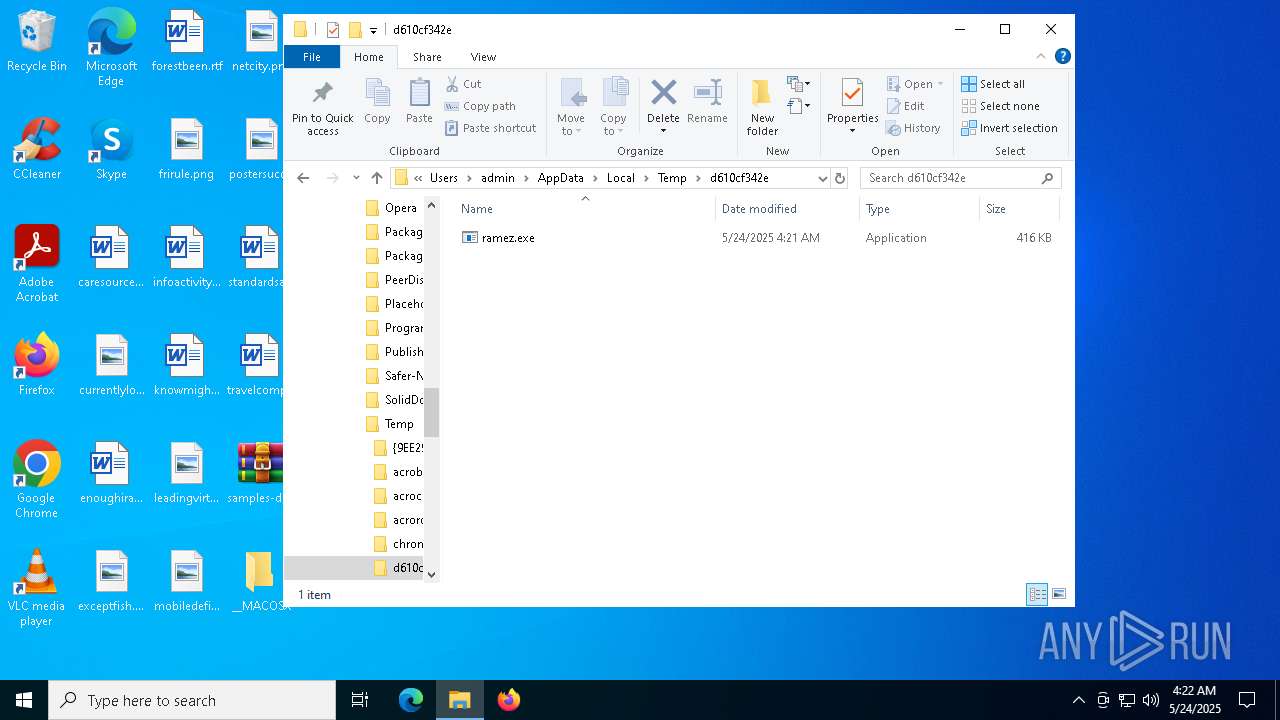
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
d610cf342e
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
/te4h2nus/index.php
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
ramez.exe
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
185.156.72.96
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
TRiD
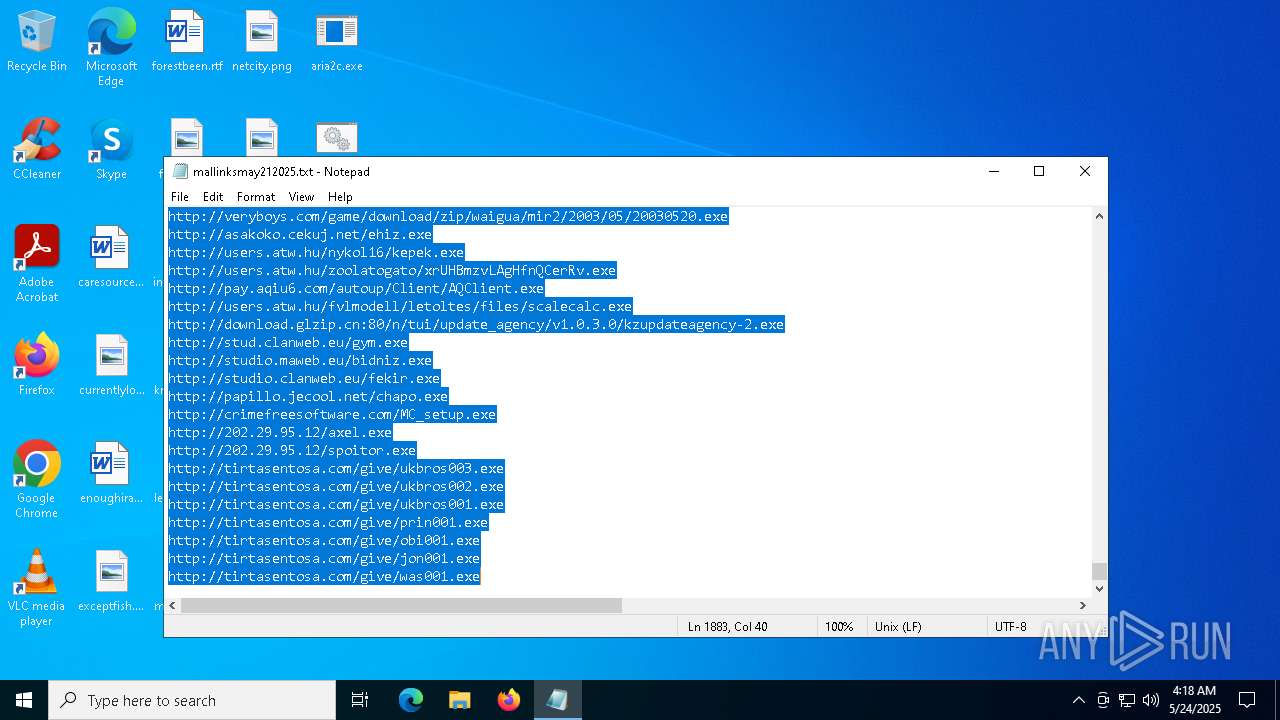
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:21 20:58:48 |
| ZipCRC: | 0xaad87668 |
| ZipCompressedSize: | 27422 |
| ZipUncompressedSize: | 123390 |
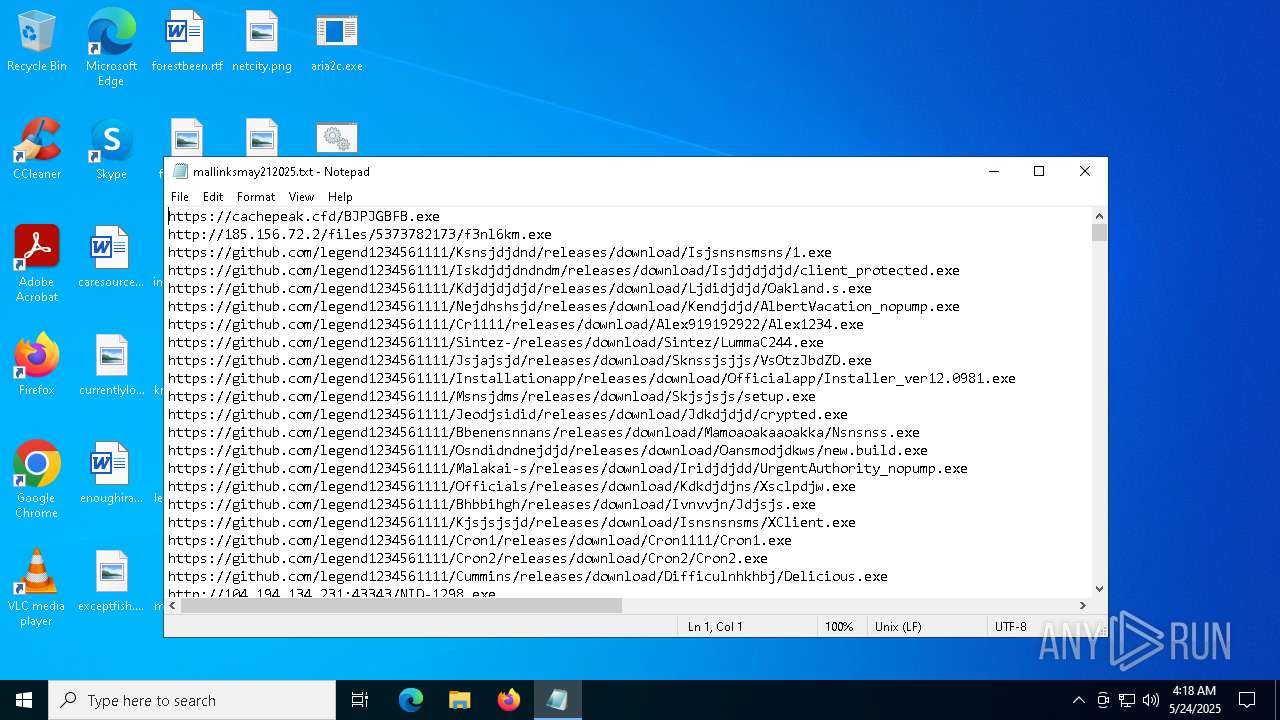
| ZipFileName: | mallinksmay212025.txt |
Total processes
216
Monitored processes
79
Malicious processes
12
Suspicious processes
9
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | C:\WINDOWS\system32\cmd.exe /c schtasks /create /tn Kbp9GmaUql6 /tr "mshta C:\Users\admin\AppData\Local\Temp\3YSrcoFIT.hta" /sc minute /mo 25 /ru "admin" /f | C:\Windows\SysWOW64\cmd.exe | — | random.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | mshta C:\Users\admin\AppData\Local\Temp\3YSrcoFIT.hta | C:\Windows\SysWOW64\mshta.exe | — | random.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7ffc89f8dc40,0x7ffc89f8dc4c,0x7ffc89f8dc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe" | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 976 | schtasks /create /tn Kbp9GmaUql6 /tr "mshta C:\Users\admin\AppData\Local\Temp\3YSrcoFIT.hta" /sc minute /mo 25 /ru "admin" /f | C:\Windows\SysWOW64\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | "C:\Users\admin\Desktop\malware-samples\random.exe" | C:\Users\admin\Desktop\malware-samples\random.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\cmd.exe /c schtasks /create /tn vXY85maa0bX /tr "mshta C:\Users\admin\AppData\Local\Temp\nXVkHeLcs.hta" /sc minute /mo 25 /ru "admin" /f | C:\Windows\SysWOW64\cmd.exe | — | random.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
53 003
Read events
52 765
Write events
230
Delete events
8
Modification events
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\samples-downloader.zip | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
7
Suspicious files
165
Text files
54
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1152e0.TMP | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1152e0.TMP | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF1152e0.TMP | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1152ef.TMP | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1152ef.TMP | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 864 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
63
DNS requests
60
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.20.245.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6300 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6300 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2552 | aria2c.exe | GET | 200 | 185.156.72.121:80 | http://185.156.72.121/test/exe/random.exe | unknown | — | — | malicious |
2552 | aria2c.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/test/exe/random.exe | unknown | — | — | malicious |
5136 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5136 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
5136 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.20.245.139:80 | crl.microsoft.com | Akamai International B.V. | SE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5008 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
5008 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] hCaptcha Enterprise Challenge |
2552 | aria2c.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2552 | aria2c.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2552 | aria2c.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2552 | aria2c.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
2552 | aria2c.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
2552 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |
2552 | aria2c.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 35 |
2552 | aria2c.exe | A Network Trojan was detected | ET USER_AGENTS Aria2 User-Agent |