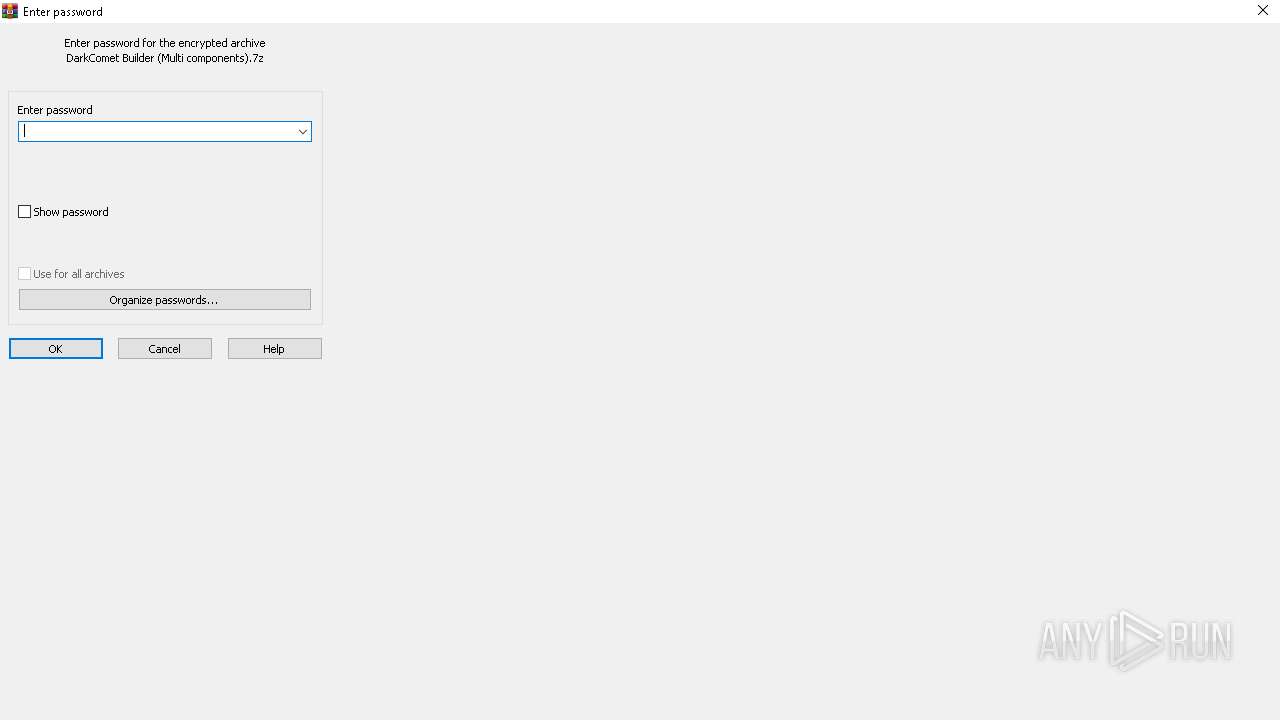
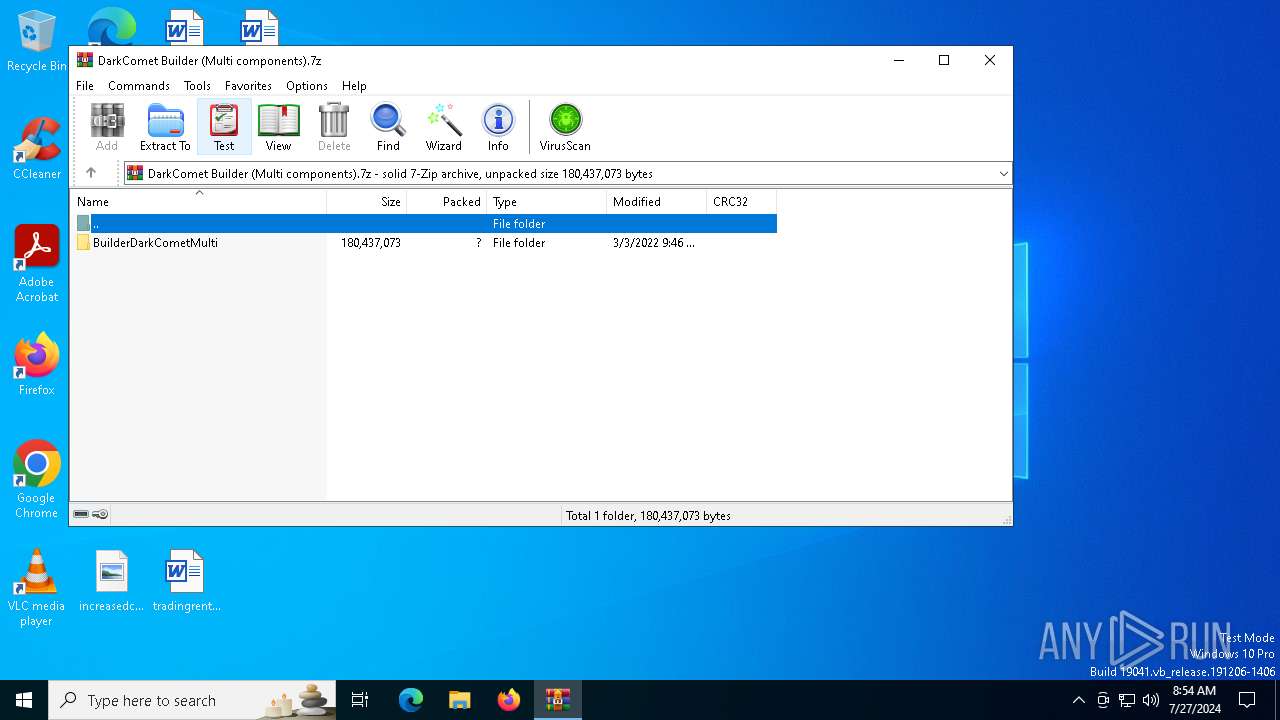
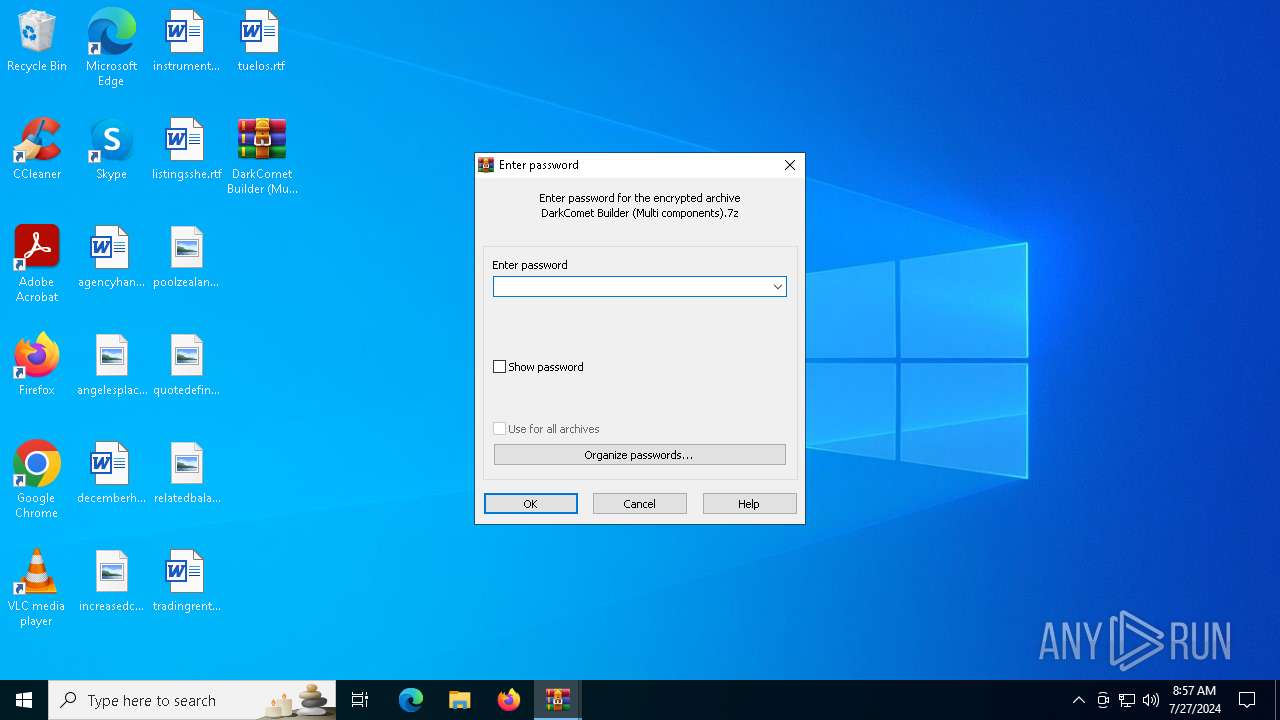
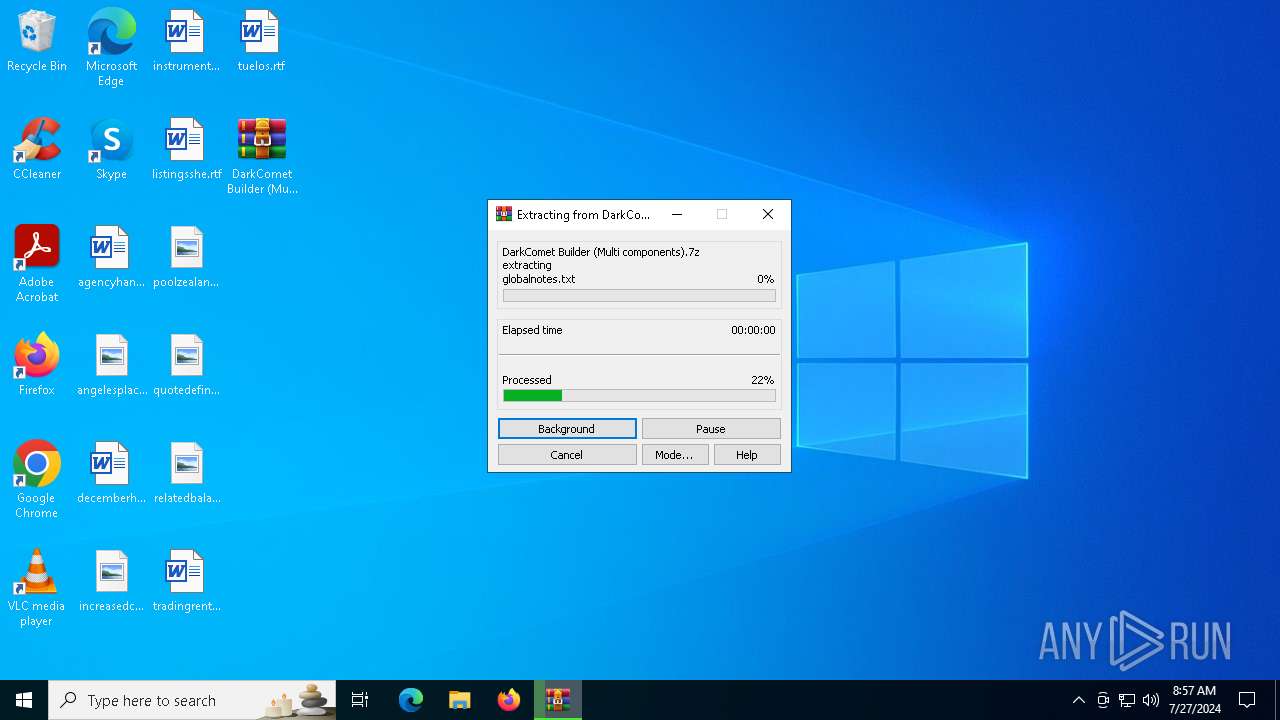
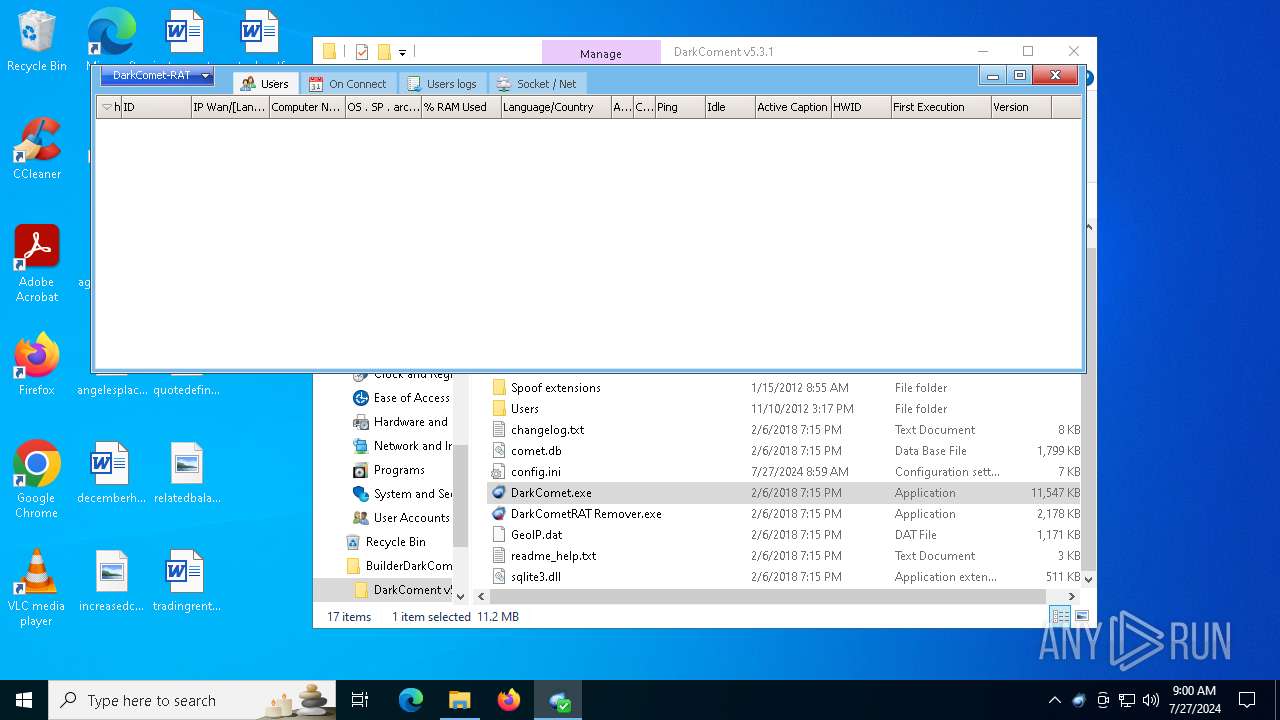
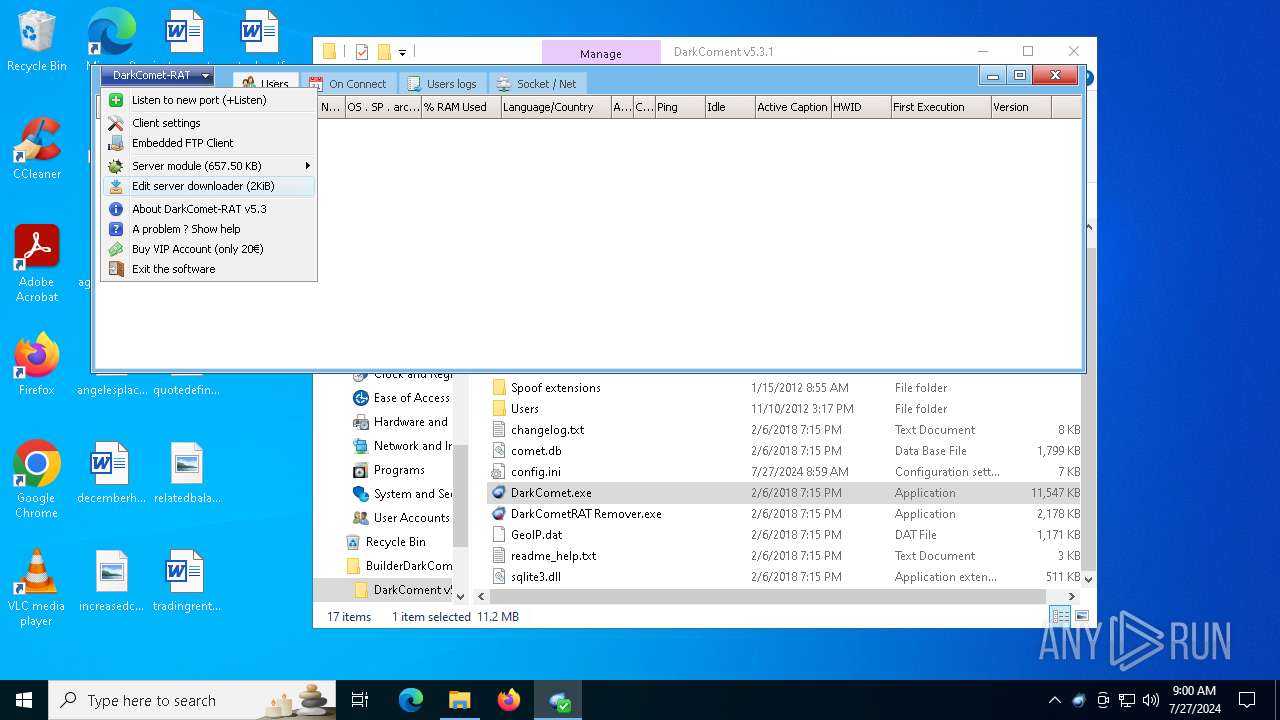
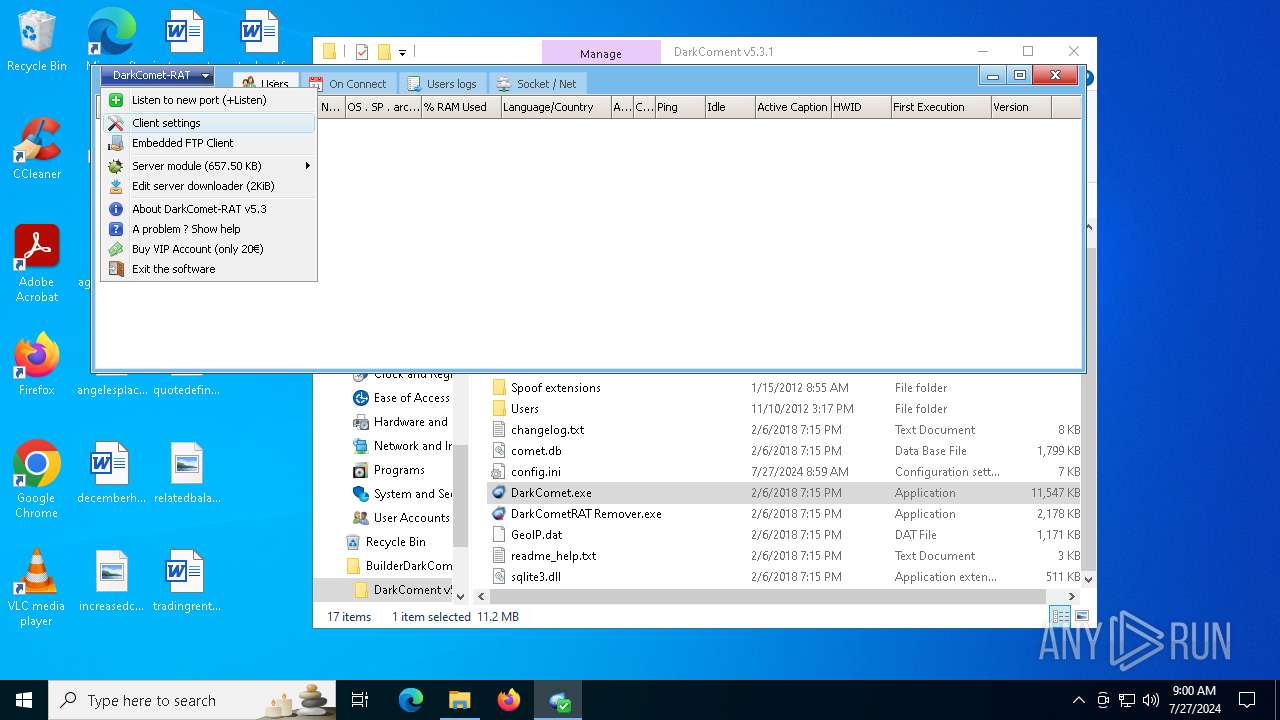
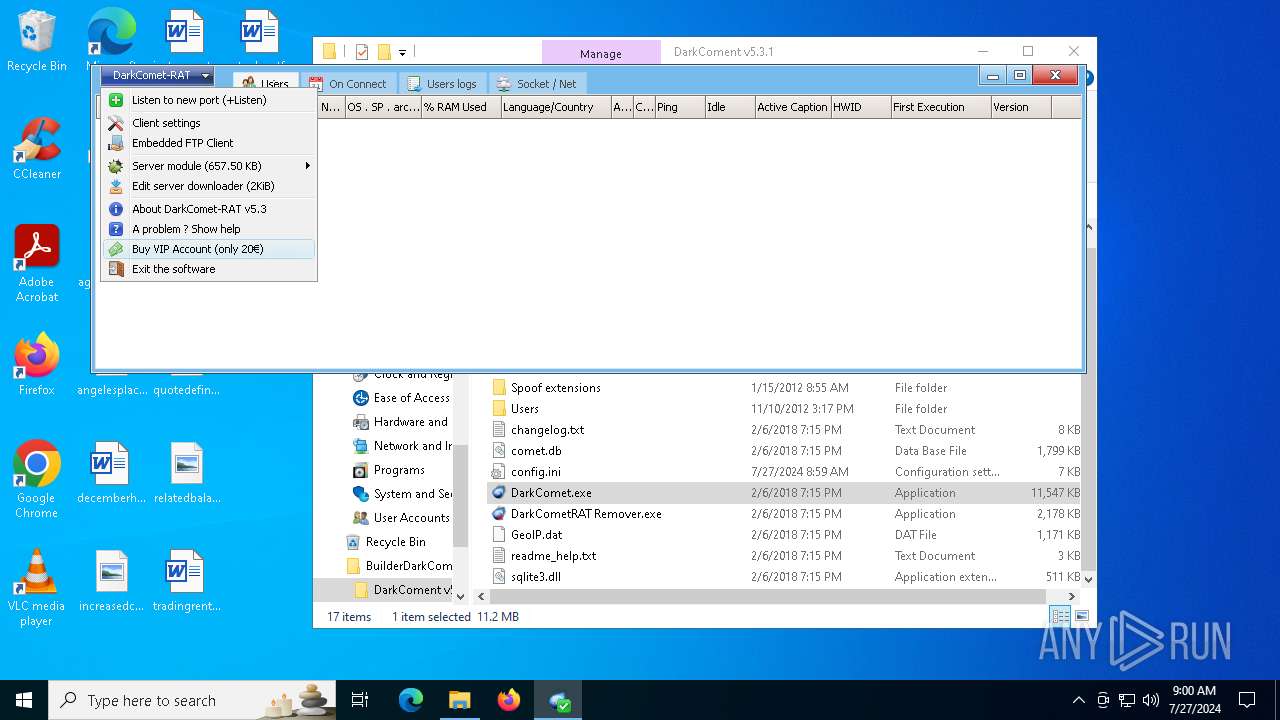
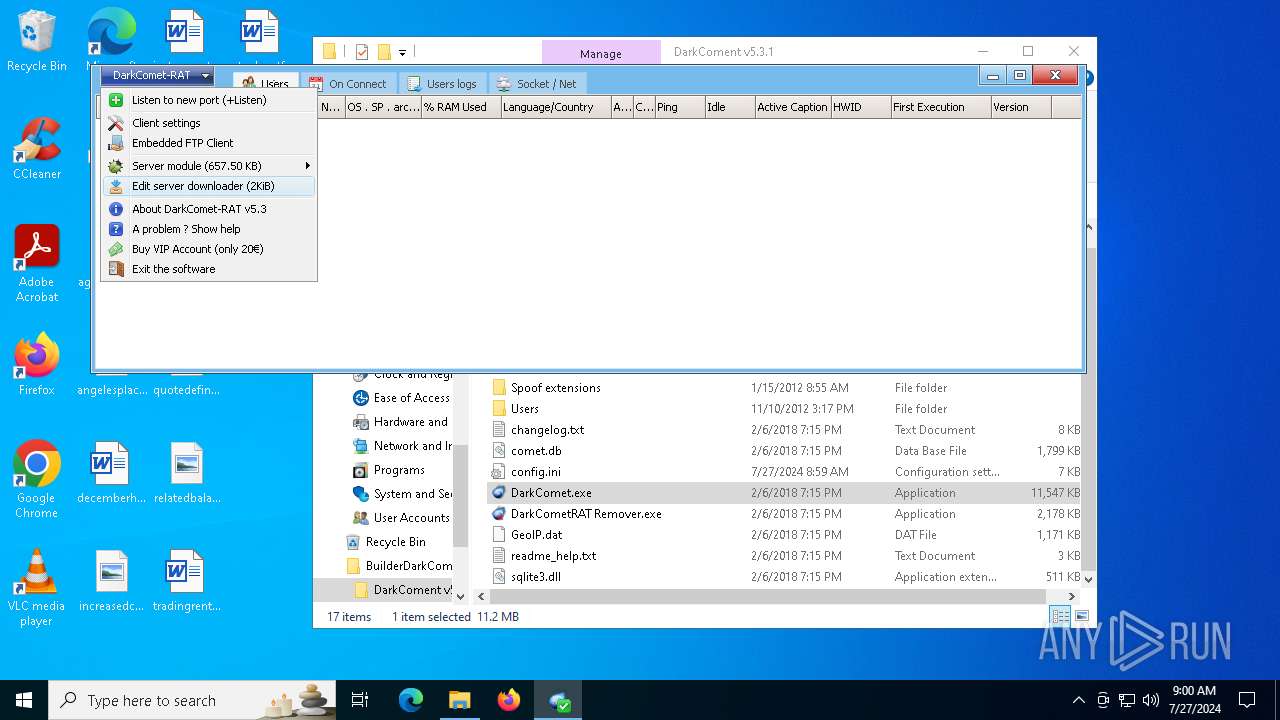
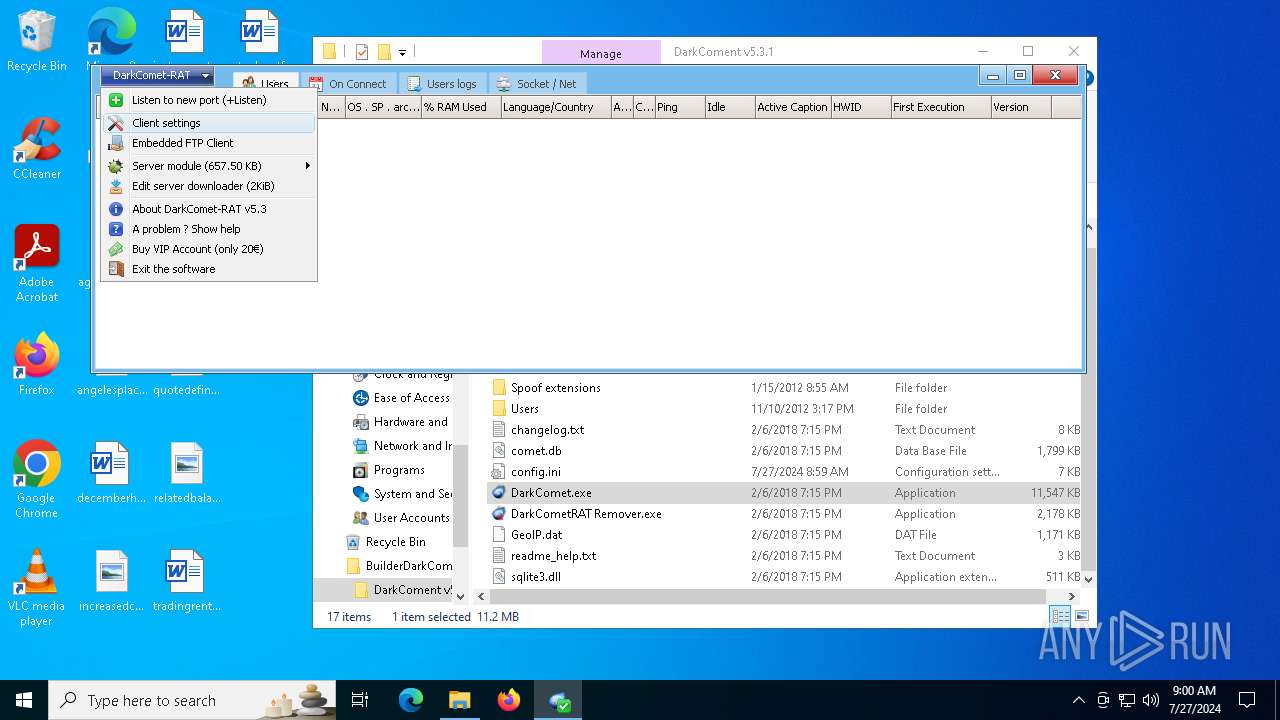
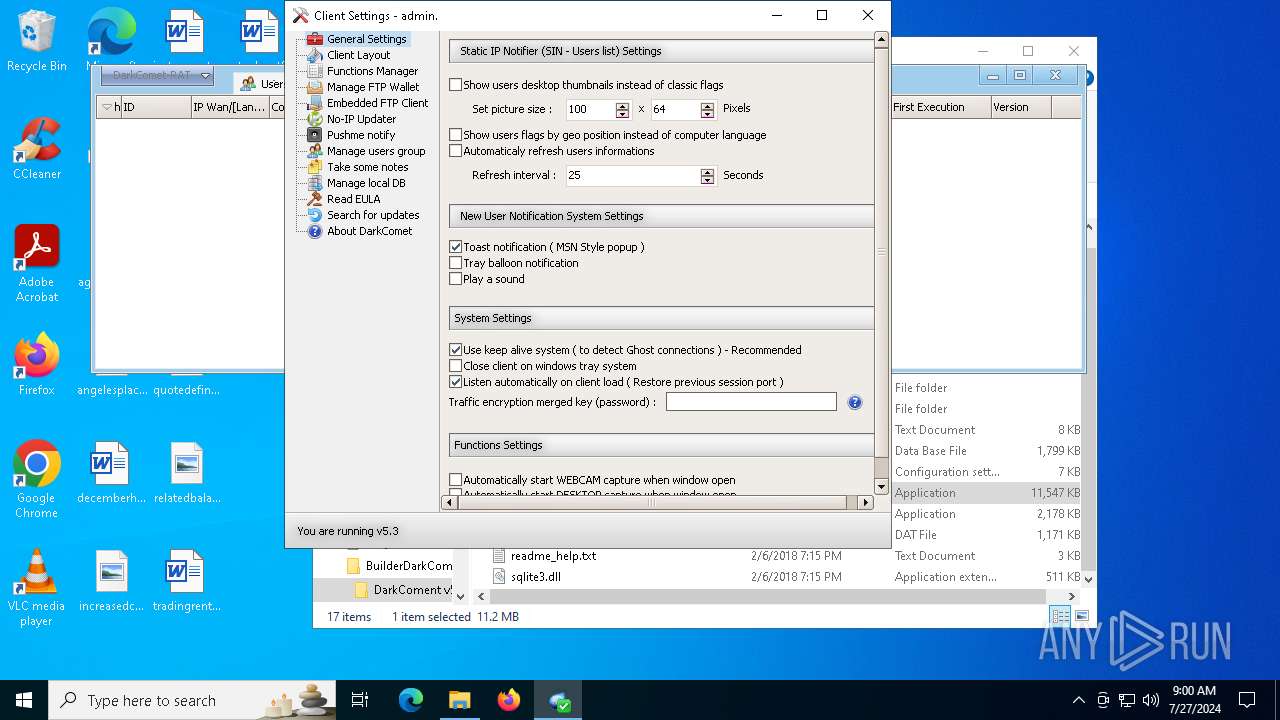
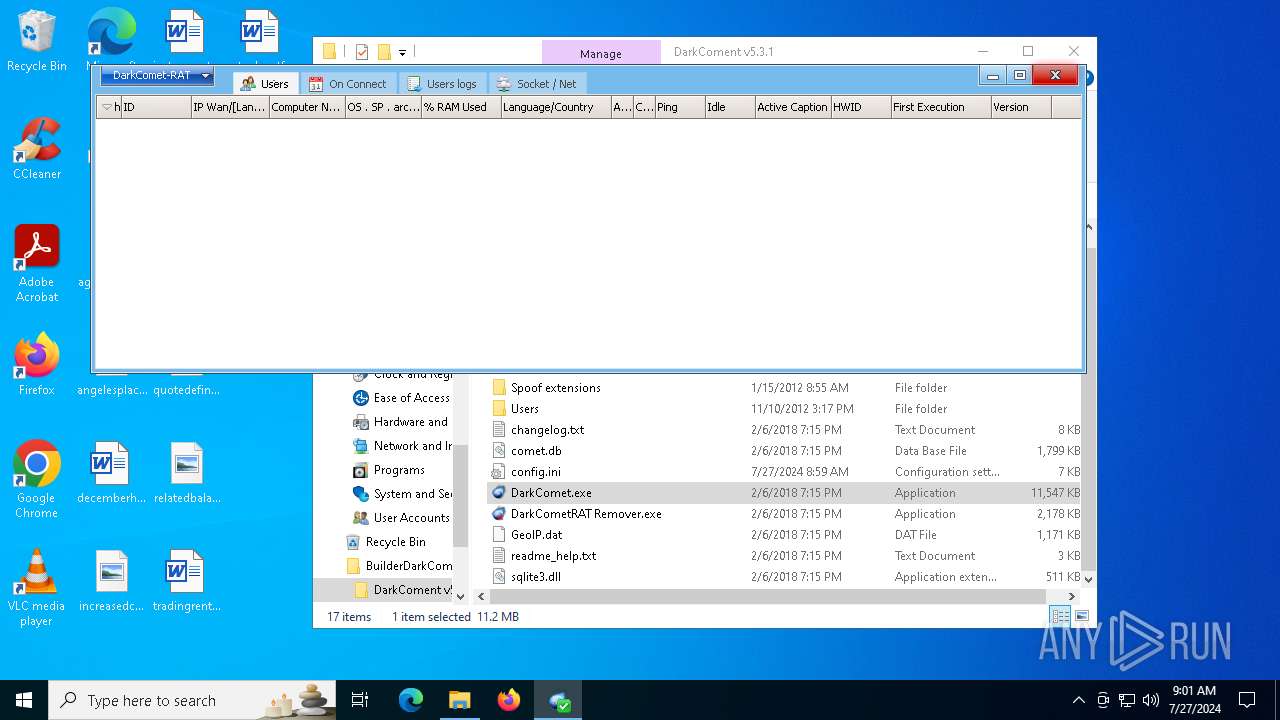
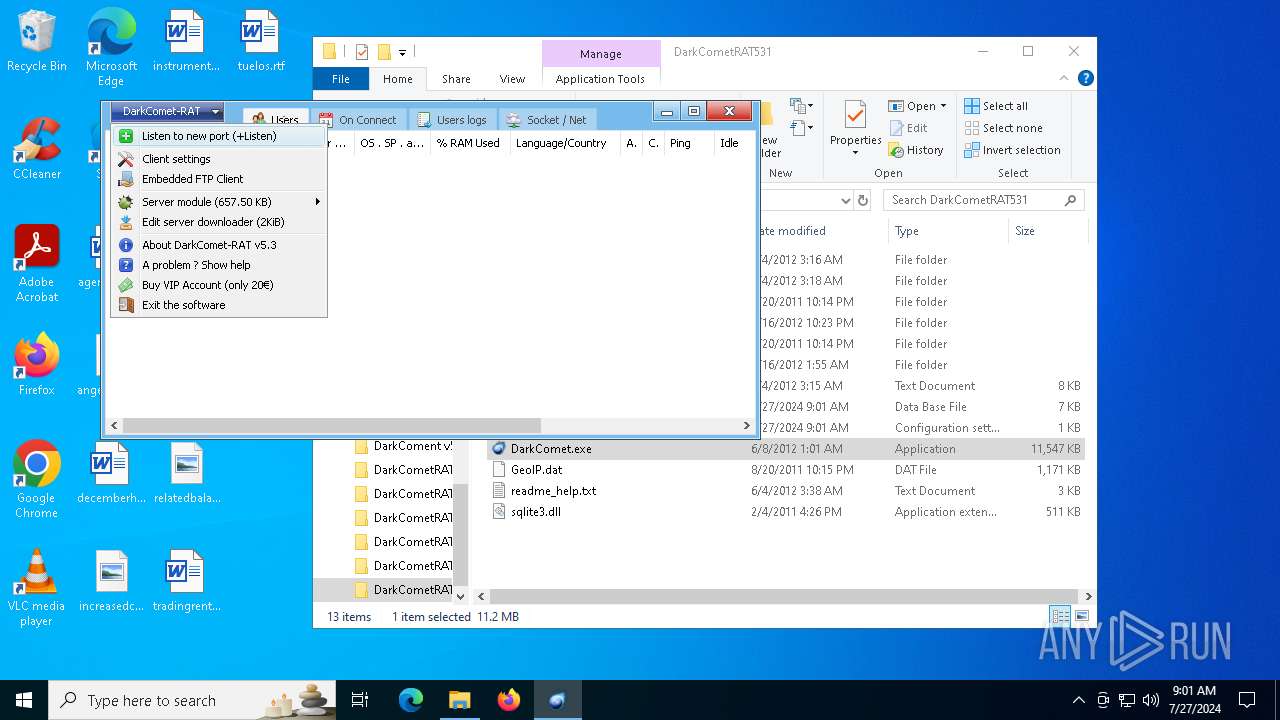
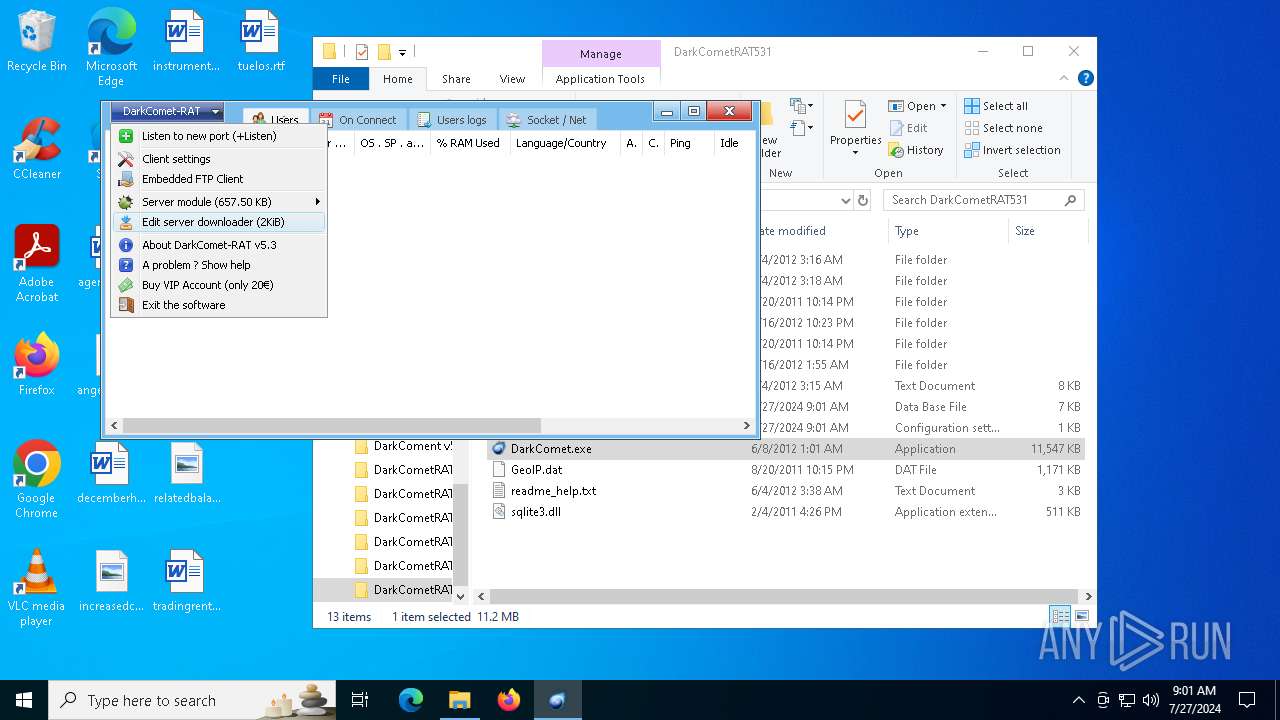
| File name: | DarkComet Builder (Multi components).7z |
| Full analysis: | https://app.any.run/tasks/3646d02b-c39d-44f1-b8d6-ad9cc7a989d8 |
| Verdict: | Malicious activity |
| Threats: | DarkComet RAT is a malicious program designed to remotely control or administer a victim's computer, steal private data and spy on the victim. |
| Analysis date: | July 27, 2024, 08:54:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 016F5A1A5073B93F9A4A164AF1447C0F |
| SHA1: | F8A97B51B2D04F78C8F94A6FF94C6128849A9A61 |
| SHA256: | 0CB70432A70E01759916831C350F6059E8E262FC9403C94E9D87BDB68F5076AD |
| SSDEEP: | 196608:C/HB4Tx5VlmzvV/bc8NFgjTcuygIam97GhA3sw9:eBs+LV/bKDnIyAsy |
MALICIOUS
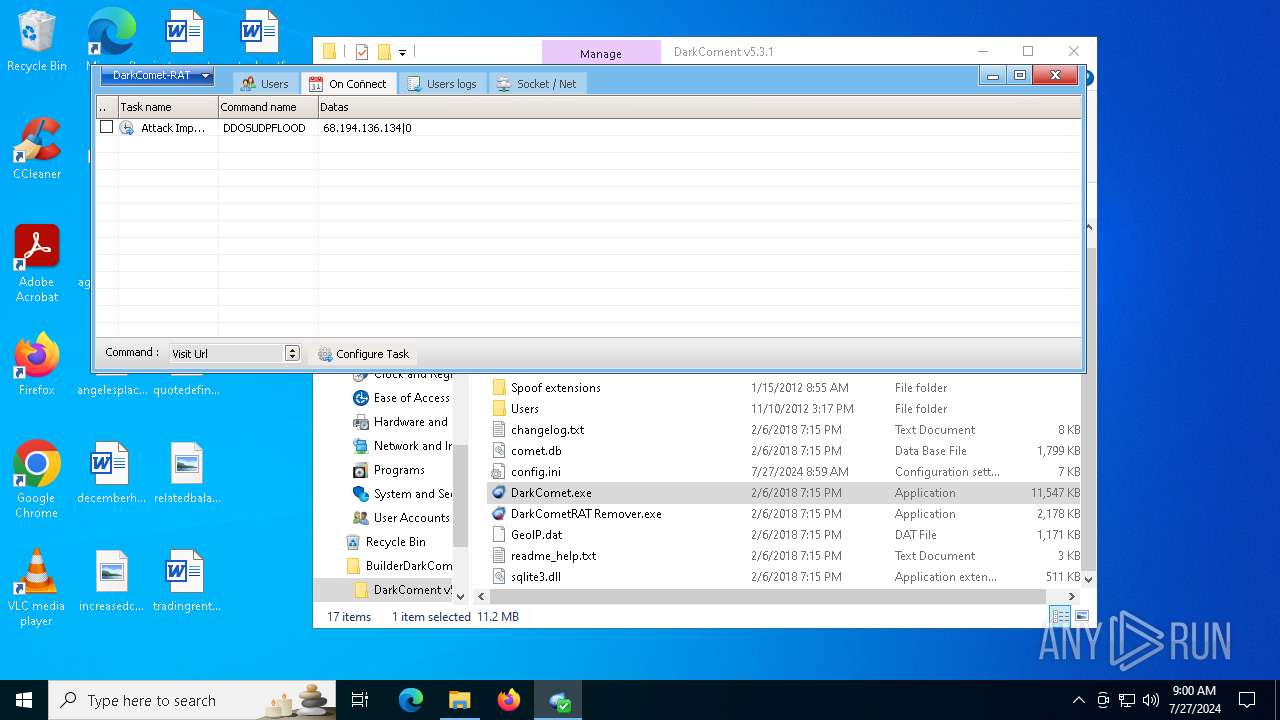
Drops the executable file immediately after the start
- DarkComet.exe (PID: 524)
- DarkComet.exe (PID: 3600)
DARKCOMET has been detected (YARA)
- DarkComet.exe (PID: 3600)
- DarkComet.exe (PID: 524)
Scans artifacts that could help determine the target
- fun.exe.exe (PID: 4660)
SUSPICIOUS
Executable content was dropped or overwritten
- DarkComet.exe (PID: 524)
- DarkComet.exe (PID: 3600)
Reads security settings of Internet Explorer
- DarkComet.exe (PID: 524)
- DarkComet.exe (PID: 3600)
- fun.exe.exe (PID: 4660)
Reads the date of Windows installation
- DarkComet.exe (PID: 524)
There is functionality for communication dyndns network (YARA)
- DarkComet.exe (PID: 524)
- DarkComet.exe (PID: 3600)
INFO
Checks proxy server information
- slui.exe (PID: 1996)
- fun.exe.exe (PID: 4660)
Drops a (possible) Coronavirus decoy
- WinRAR.exe (PID: 6044)
- WinRAR.exe (PID: 7164)
- WinRAR.exe (PID: 2976)
Reads the software policy settings
- slui.exe (PID: 1996)
Manual execution by a user
- WinRAR.exe (PID: 7164)
- WinRAR.exe (PID: 2976)
- DarkComet.exe (PID: 524)
- fun.exe.exe (PID: 4660)
- DarkComet.exe (PID: 3600)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7164)
- WinRAR.exe (PID: 6044)
- WinRAR.exe (PID: 2976)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2976)
Create files in a temporary directory
- DarkComet.exe (PID: 524)
Checks supported languages
- DarkComet.exe (PID: 524)
- upnp.exe (PID: 3616)
- upnp.exe (PID: 6564)
- DarkComet.exe (PID: 3600)
- fun.exe.exe (PID: 4660)
Reads the computer name
- DarkComet.exe (PID: 524)
- upnp.exe (PID: 3616)
- upnp.exe (PID: 6564)
- DarkComet.exe (PID: 3600)
- fun.exe.exe (PID: 4660)
Process checks computer location settings
- DarkComet.exe (PID: 524)
UPX packer has been detected
- DarkComet.exe (PID: 524)
- DarkComet.exe (PID: 3600)
Mpress packer has been detected
- DarkComet.exe (PID: 3600)
- DarkComet.exe (PID: 524)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
153
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | "C:\Users\admin\Desktop\BuilderDarkCometMulti\DarkComent v5.3.1\DarkComet.exe" | C:\Users\admin\Desktop\BuilderDarkCometMulti\DarkComent v5.3.1\DarkComet.exe | explorer.exe | ||||||||||||
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: A remote administration tool from the cosmos Exit code: 0 Version: 4.2.0.28 Modules
| |||||||||||||||
| 1996 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2976 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\DarkComet Builder (Multi components).7z" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3600 | "C:\Users\admin\Desktop\BuilderDarkCometMulti\DarkCometRAT531\DarkComet.exe" | C:\Users\admin\Desktop\BuilderDarkCometMulti\DarkCometRAT531\DarkComet.exe | explorer.exe | ||||||||||||
User: admin Company: Unremote.org Integrity Level: MEDIUM Description: A remote administration tool from the cosmos Exit code: 0 Version: 4.2.0.28 Modules
| |||||||||||||||
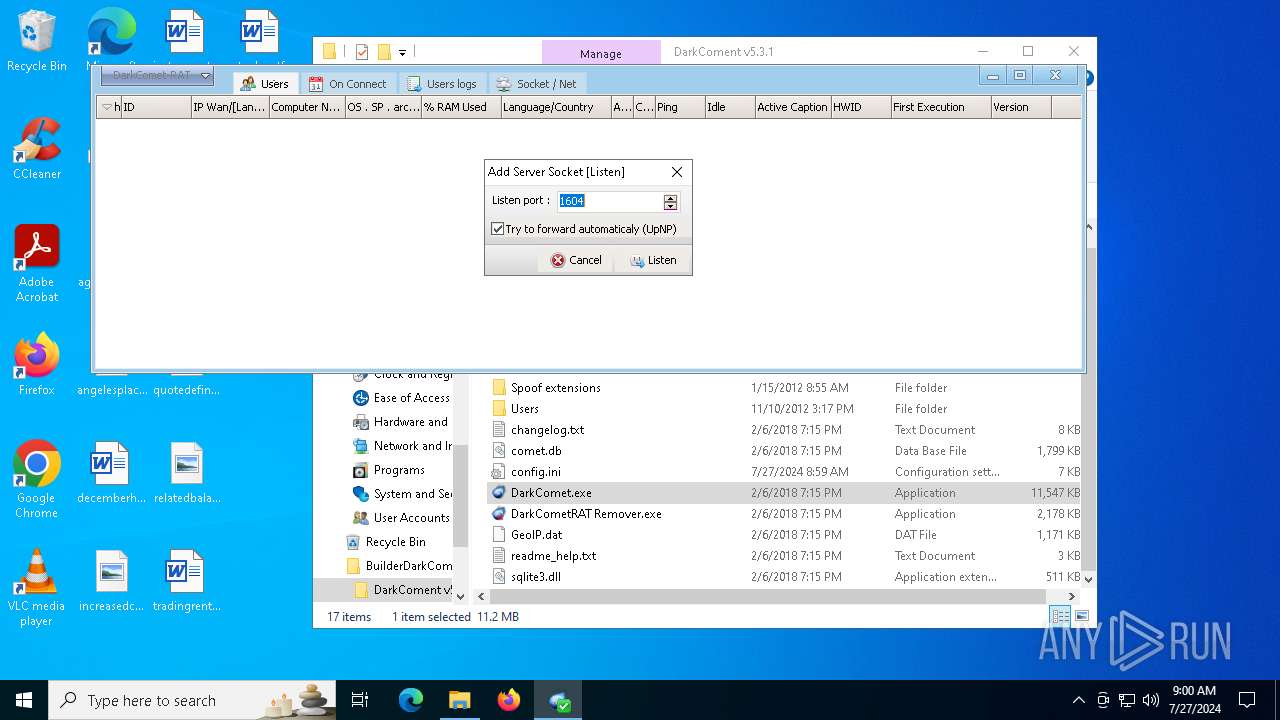
| 3616 | "C:\Users\admin\AppData\Local\Temp\upnp.exe" -a 192.168.100.22 1604 1604 TCP | C:\Users\admin\AppData\Local\Temp\upnp.exe | DarkComet.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3820 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | upnp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4660 | "C:\Users\admin\Desktop\fun.exe.exe" | C:\Users\admin\Desktop\fun.exe.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\DarkComet Builder (Multi components).7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6284 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | upnp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6564 | "C:\Users\admin\AppData\Local\Temp\upnp.exe" -a 192.168.100.22 1604 1604 TCP | C:\Users\admin\AppData\Local\Temp\upnp.exe | DarkComet.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
21 992
Read events
21 851
Write events
137
Delete events
4
Modification events
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\DarkComet Builder (Multi components).7z | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF560100003B0000001605000024020000 | |||
Executable files
28
Suspicious files
1 940
Text files
763
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\AR.ini | text | |
MD5:4276808F92D3EFE8359CB03F9C45C9E1 | SHA256:C4E0CD4D29594C9CB188DEAB7BB5F73FC6B3ED832468322ABC05B4E981C306C4 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\EN.ini | text | |
MD5:D5B95D8DBCDCC5BE0290067BE9043009 | SHA256:48A43817F513A7DE5F033F842EA71DCEC7CFE45E2EDC87BE844E461D99E2572E | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\SR.ini | text | |
MD5:FDFC0EE3AD0F395E3078F600ED9BA689 | SHA256:37DCDA2CD0682A3EDFE354111E0DD637BE6581A71E6C240AE5729CE9F6A05EF9 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\VN.ini | text | |
MD5:24874C298B575AE2AC496765AA5F3F6B | SHA256:B0B6AD746697E54CC76DCE834D963885D0284CCEEEB24DE62BE9EAF4BEE47EDD | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\changelog.txt | text | |
MD5:7A23E5B811DD52E99CBDB72A7FE4CE12 | SHA256:7CF268D2FBBC3BB3E1CE2019D53F7C88B42F3BBCD4833AC69798D34FBD809DFE | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Goodies\wallpaper_1.jpg | image | |
MD5:F72131120657B33655E6EC741FC2C407 | SHA256:9C53C010DB6E61ED6CA7A484D3FFB23BA1BD8B6EEE6CFA652F1C5647ADDC2280 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\ES.ini | text | |
MD5:4745B84E71D23454D2535CC608DE57D0 | SHA256:EB0553309ACD121B01566C1CA297ED46E896E3AD11C486971E8FA7275A1FF061 | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\GR.ini | text | |
MD5:8B35CDF90F3D89D2502E1F61B2BBF631 | SHA256:FCA01673CB23ABD479B6D54D19A40A87E9D72B90ECC7F5D59AF14D192CC07C7C | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\IT.ini | binary | |
MD5:1CB447996787264785C83D110C67AB13 | SHA256:840DB2223BC47B37C44393BCE4CA8583D373EF6D70B6BC9143561190AA16CDCB | |||
| 6044 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6044.29693\BuilderDarkCometMulti\DarkComent v5.3.1\Celesty Binder\Lang\FR.ini | text | |
MD5:A8568B41DF3F0A47F875964E8FEEFA70 | SHA256:F515EE7D43CF301FE771599C60E2771DB6F27E614AF6A4403771A0D99CB19BC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
29
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 13.85.23.206:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
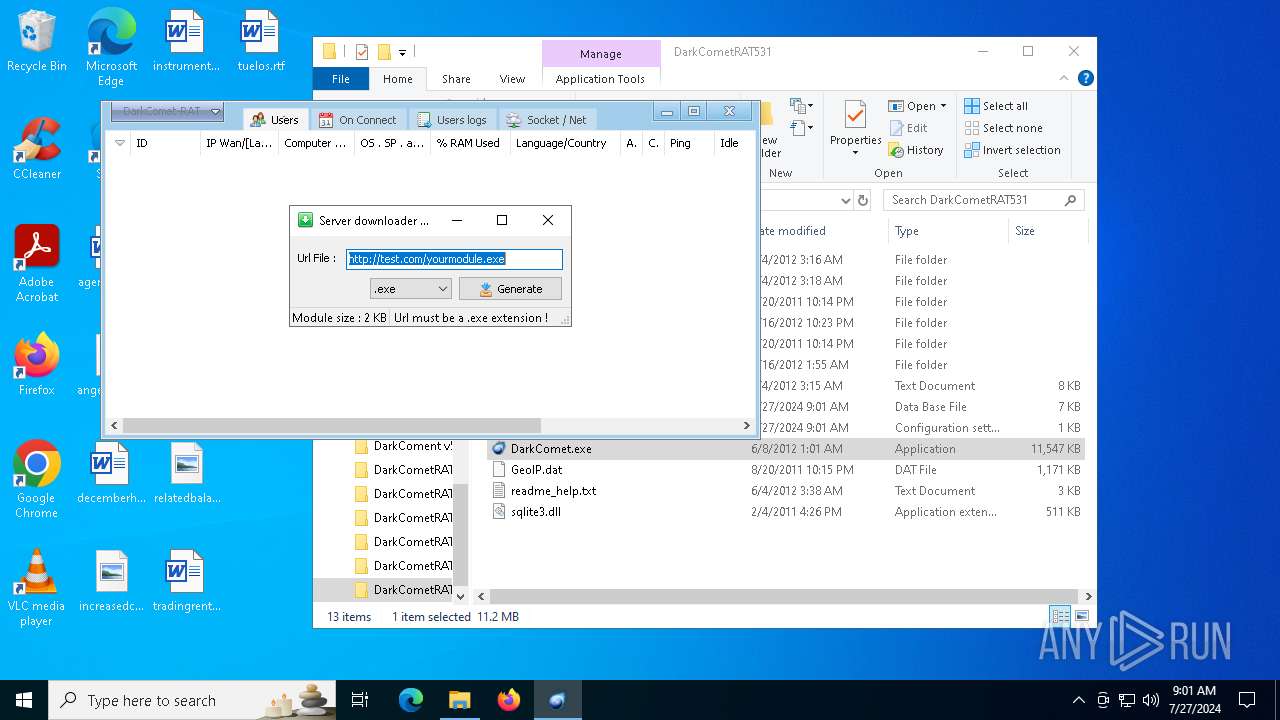
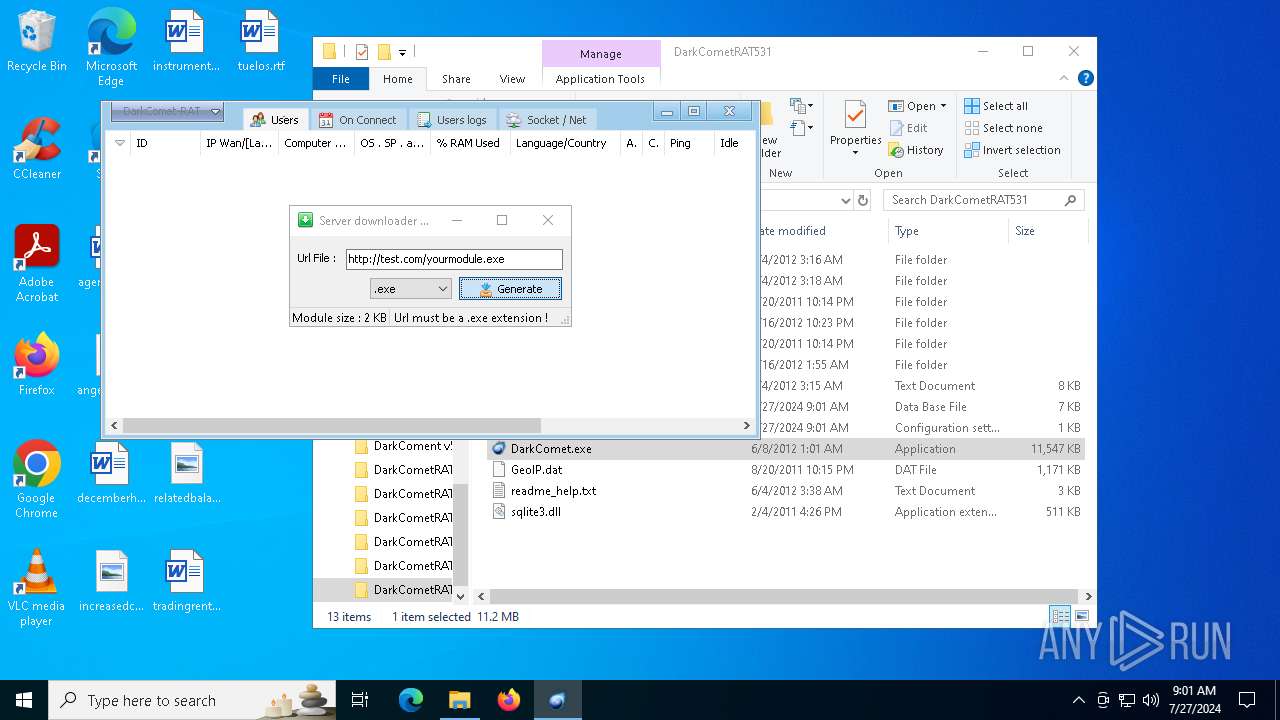
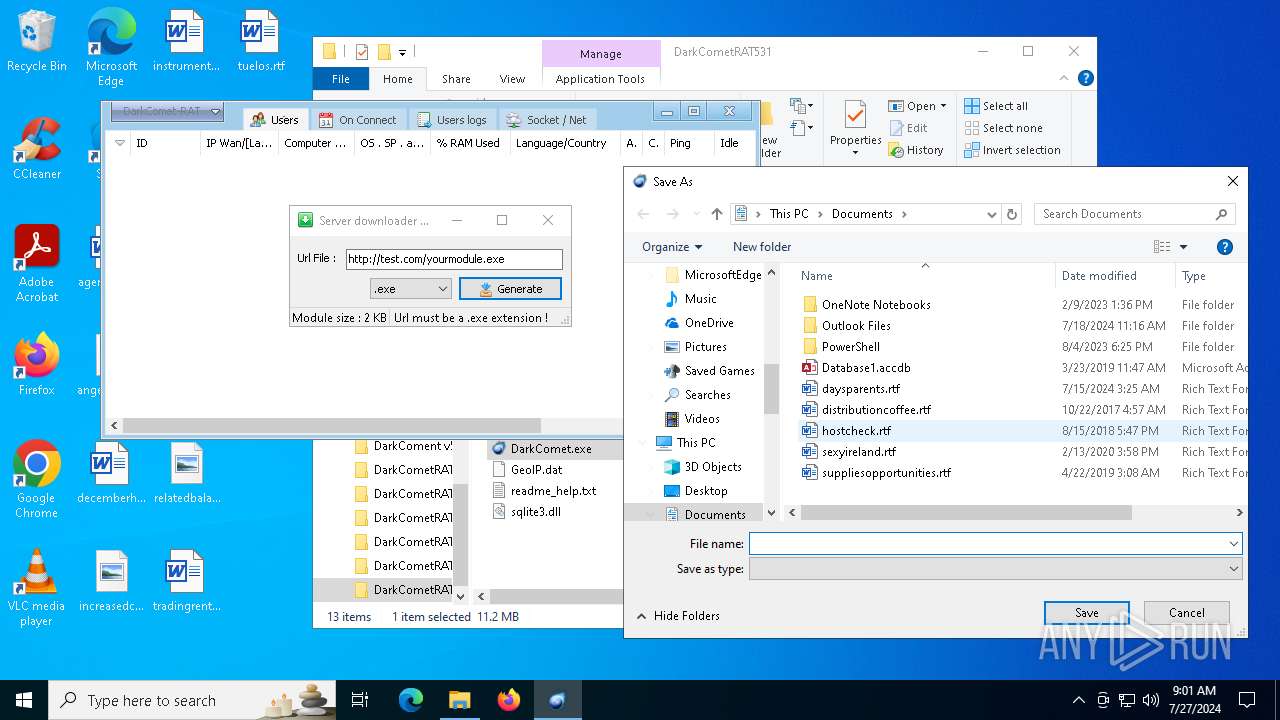
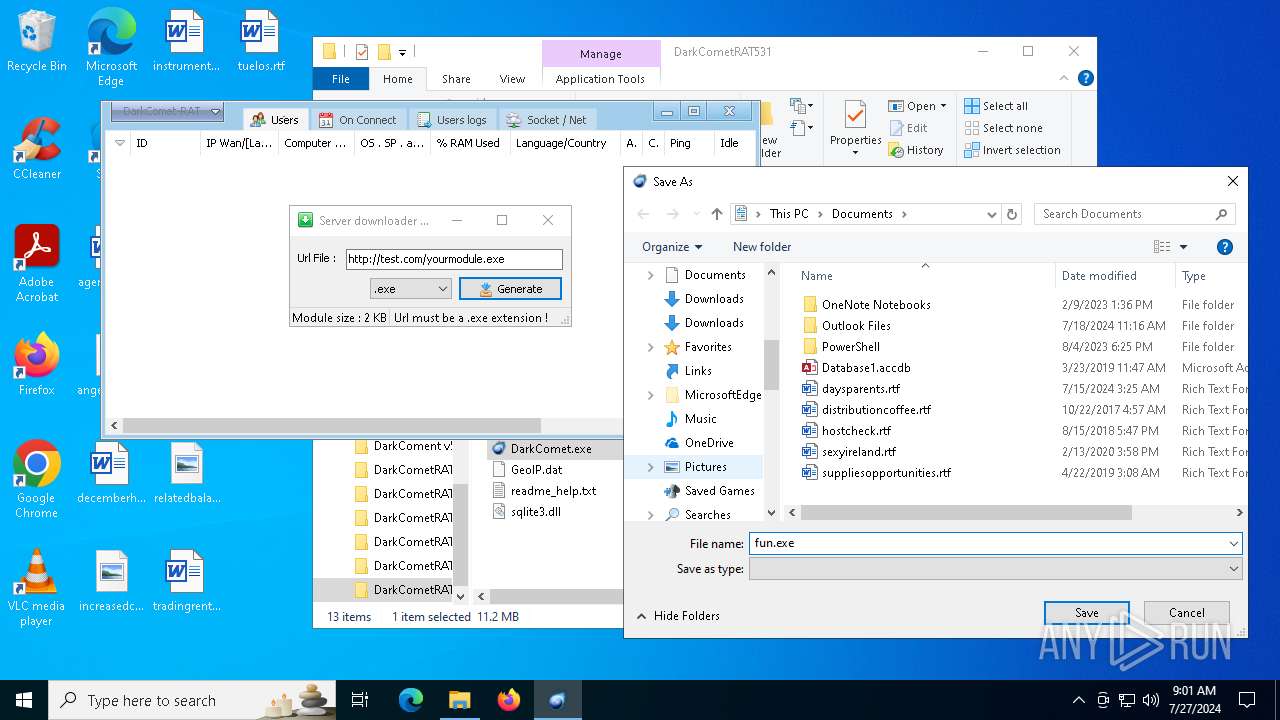
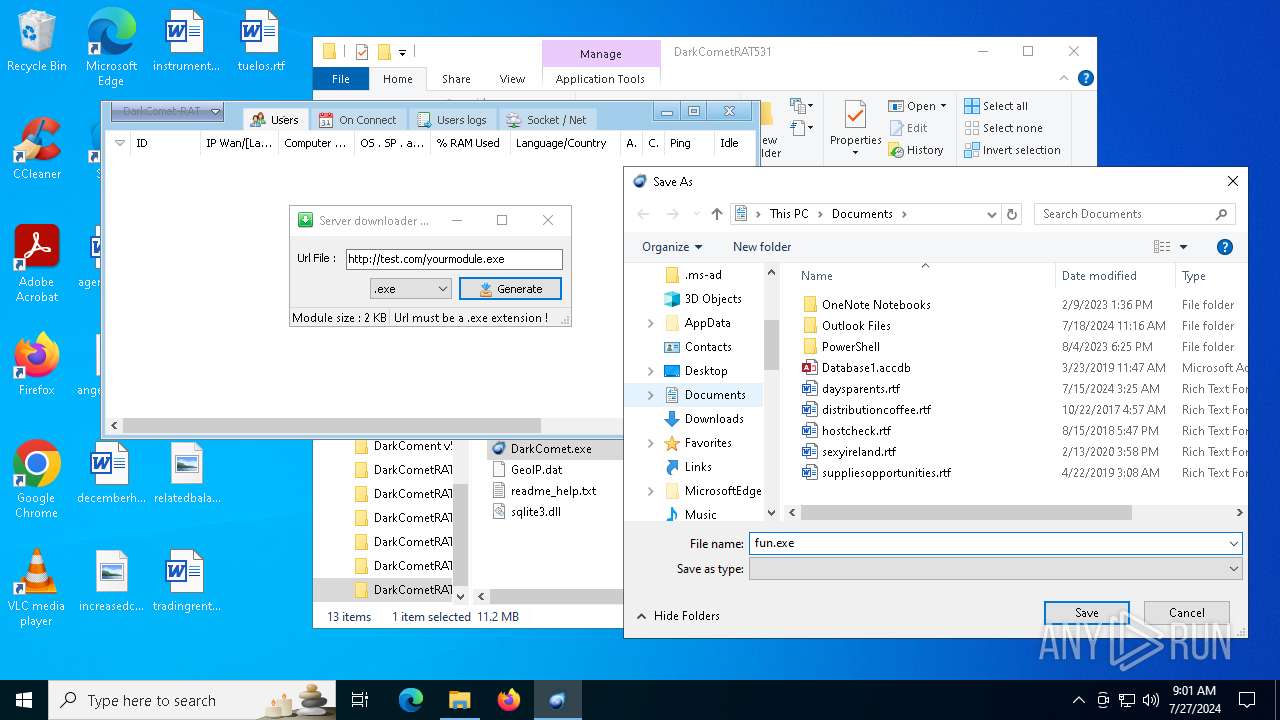
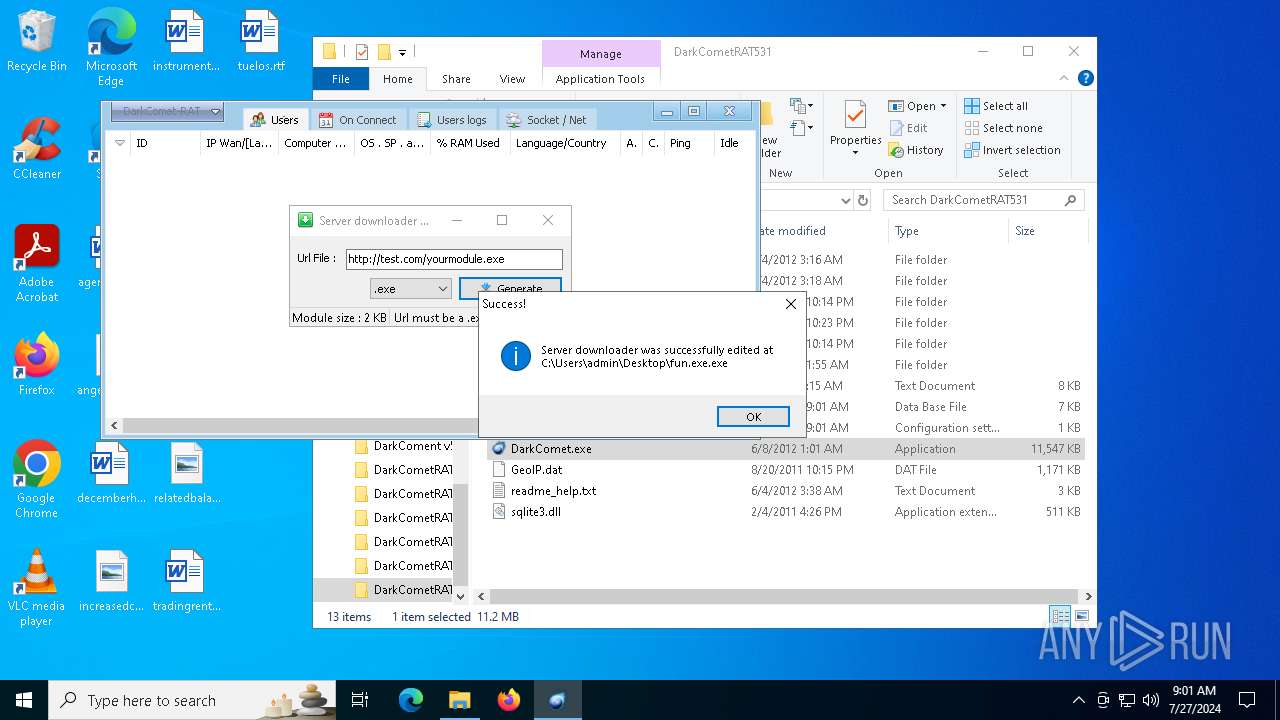
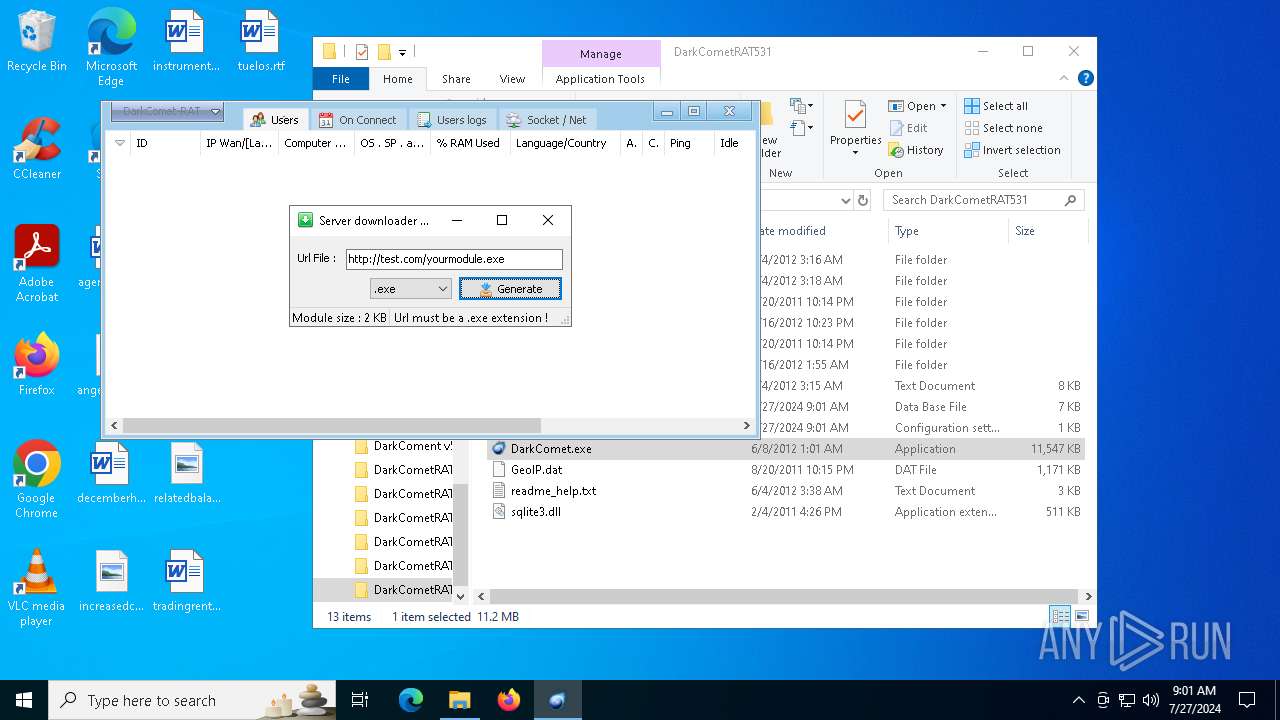
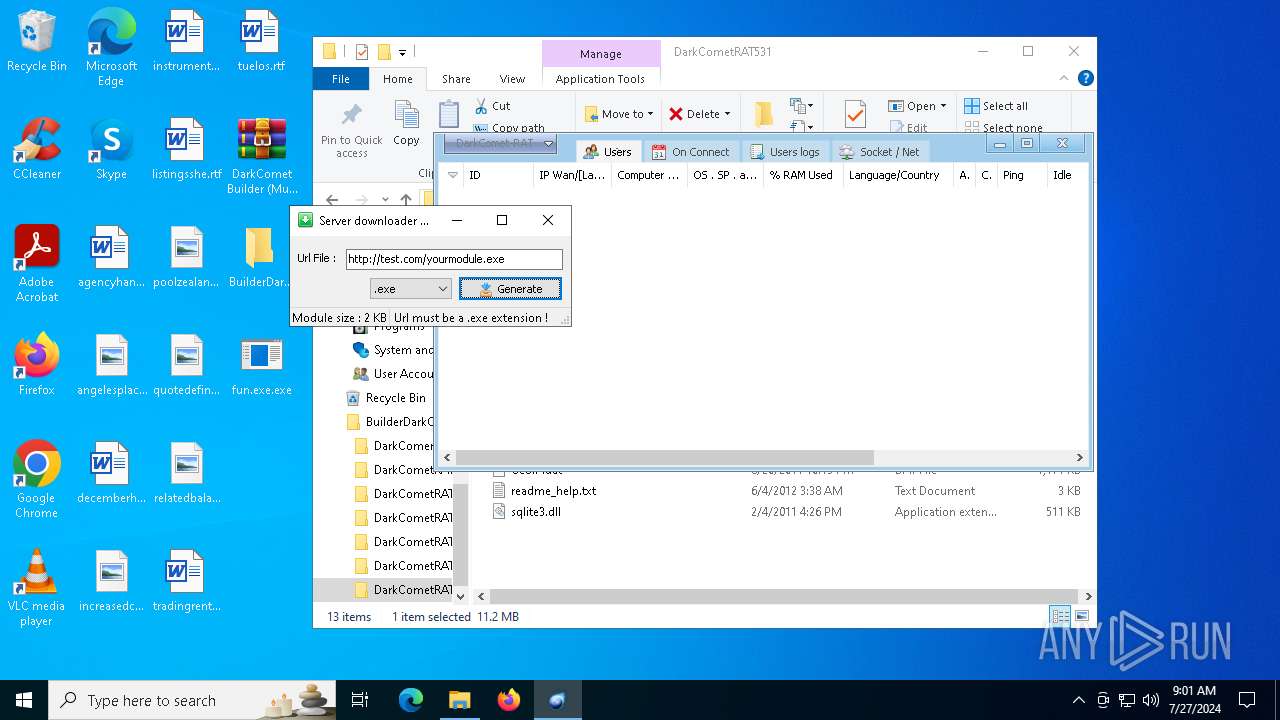
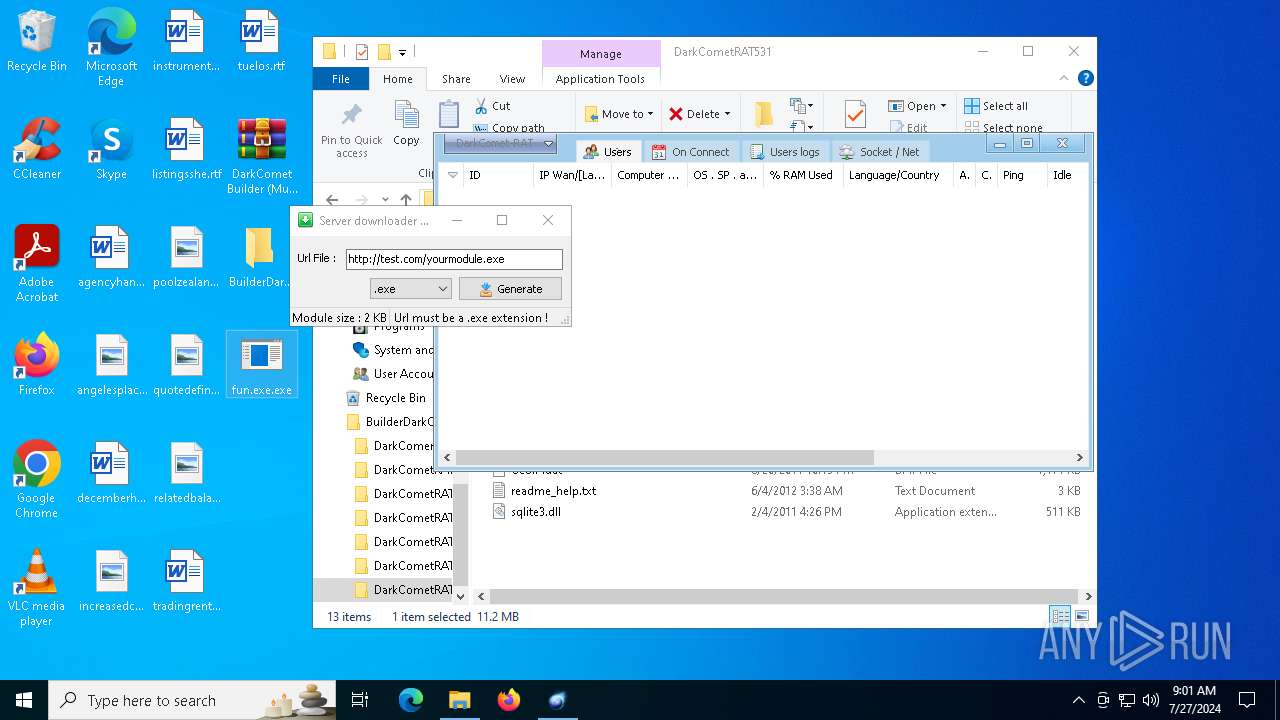
4660 | fun.exe.exe | GET | — | 3.18.255.247:80 | http://test.com/yourmodule.exe | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | unknown |
— | — | POST | 200 | 104.208.16.88:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
— | — | POST | 200 | 20.189.173.17:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.16.110.171:443 | www.bing.com | Akamai International B.V. | DE | unknown |
6412 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4340 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2668 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
t-ring-fdv2.msedge.net |
| unknown |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
test.com |
| whitelisted |