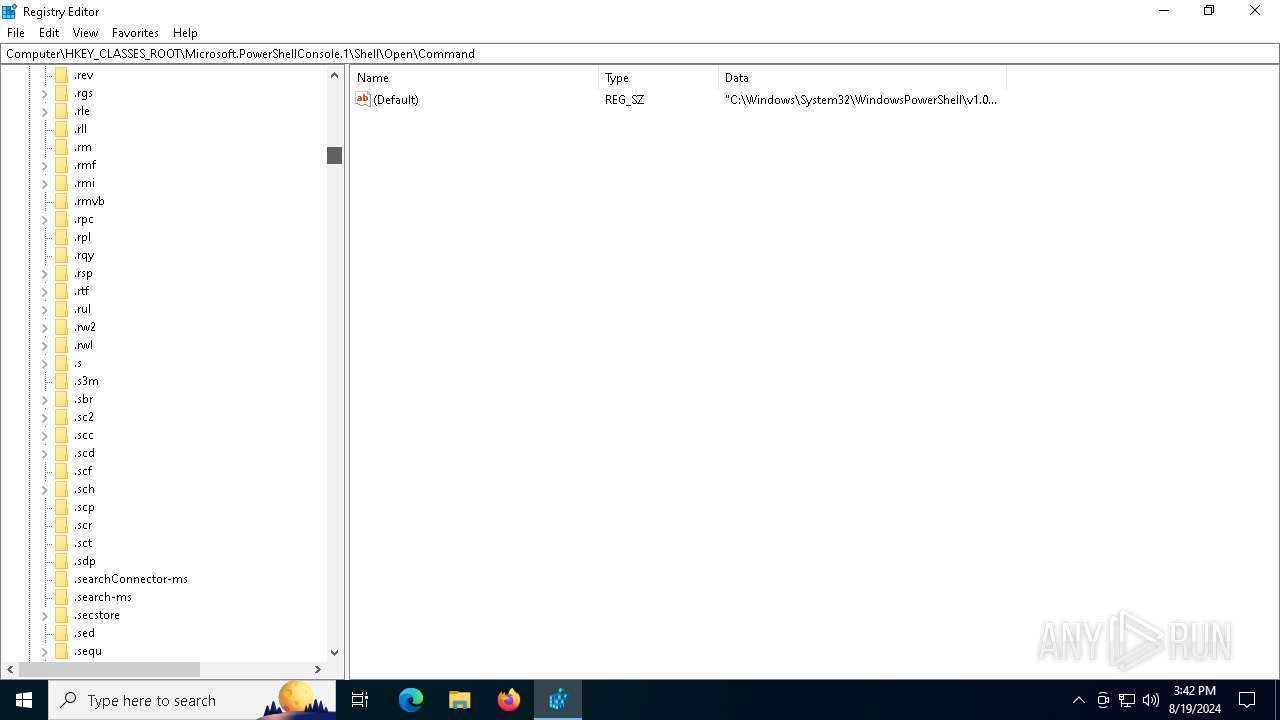
| File name: | MEGAvpnSetup64.exe |
| Full analysis: | https://app.any.run/tasks/133023ed-0286-4682-ac5e-e875f313dec9 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | August 19, 2024, 15:41:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | 1001507ADDB65D5708D79CC0C8E672D6 |
| SHA1: | 665B6120A02D9FD7EF09BCB1A80B023B7163E620 |
| SHA256: | 0C7D2BA6ABC70DBF020E9A626D0E076F177660A59A7F1131DE7212FF745316AD |
| SSDEEP: | 6144:51HC5XfBlCDl8nnnnn1TbFEUNR7CIghdOClEajW:51HC5XfBlCDl8nnnnnRbF57CIghdO9 |
MALICIOUS
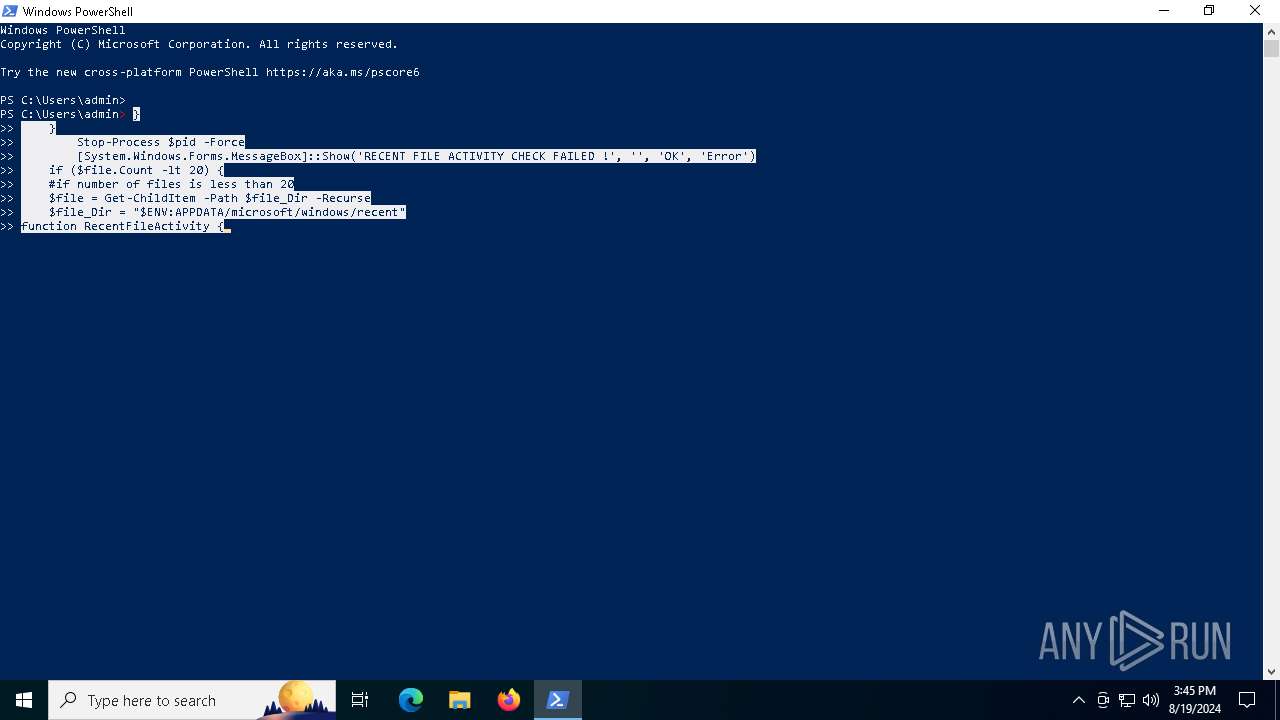
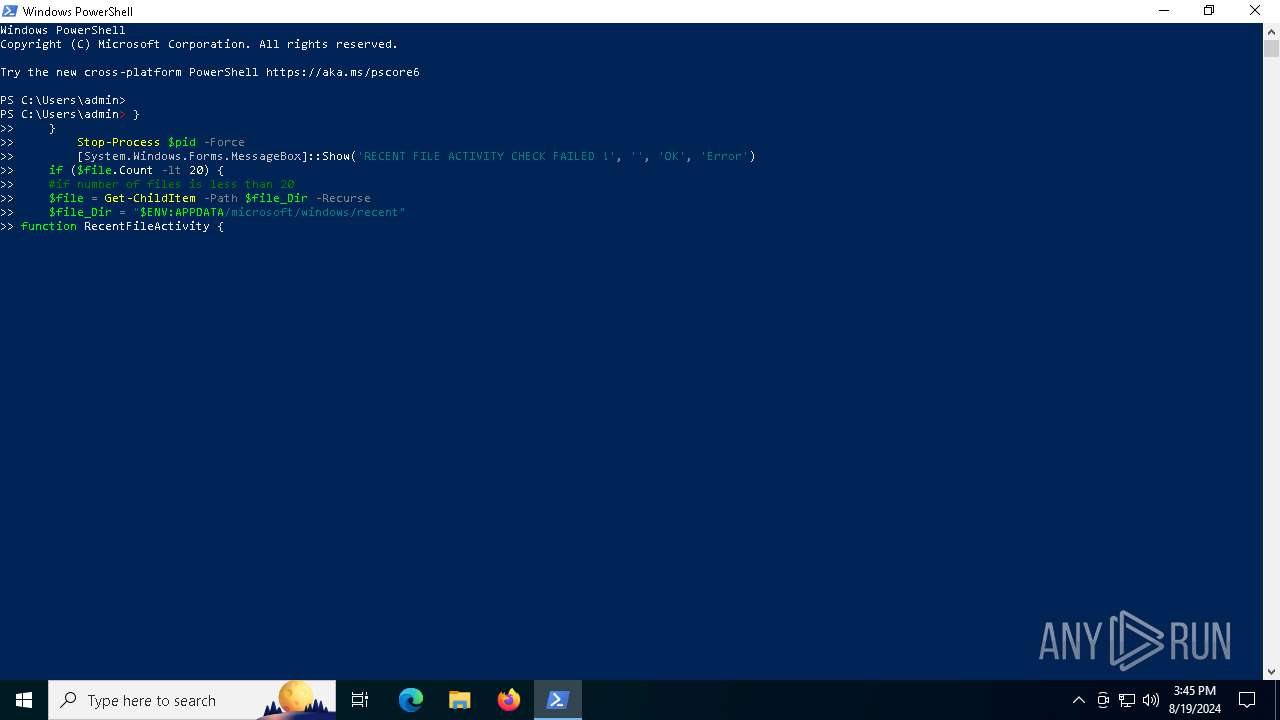
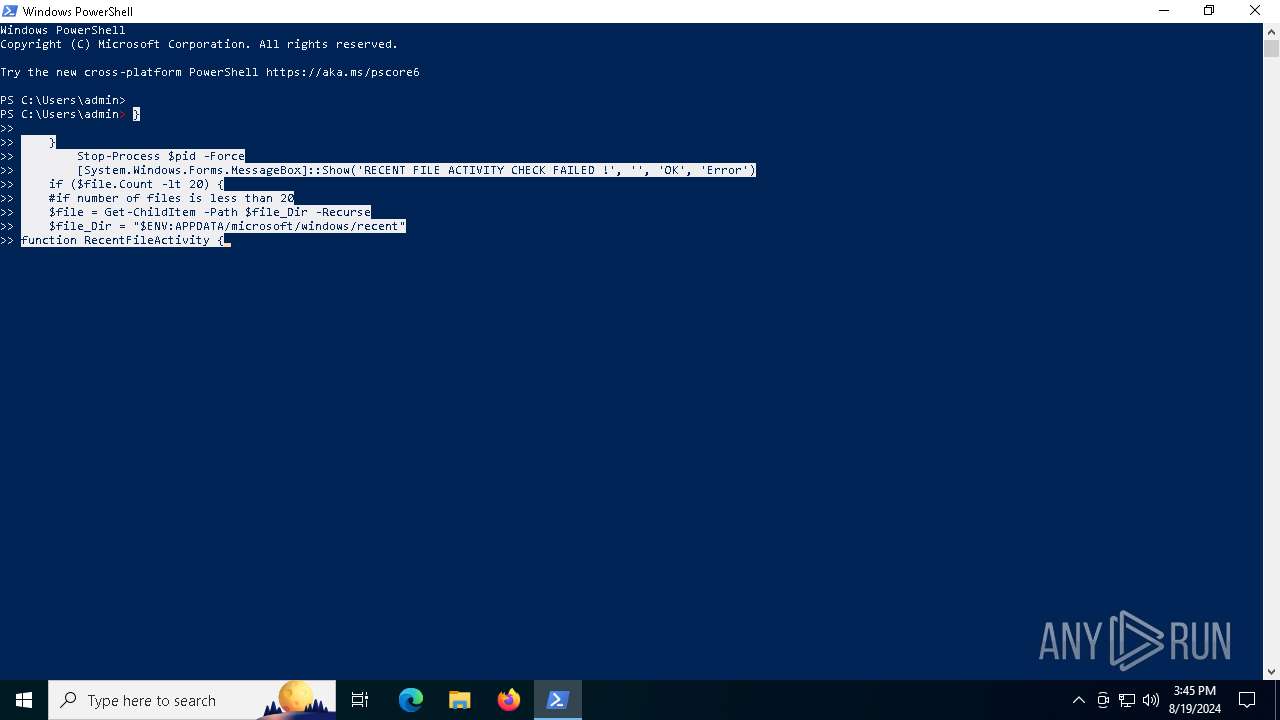
Adds path to the Windows Defender exclusion list
- MEGAvpnSetup64.exe (PID: 6900)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2256)
XORed URL has been found (YARA)
- conhost.exe (PID: 6272)
SUSPICIOUS
Drops the executable file immediately after the start
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
Reads the date of Windows installation
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
Reads security settings of Internet Explorer
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
Starts POWERSHELL.EXE for commands execution
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
The process checks if it is being run in the virtual environment
- MEGAvpnSetup64.exe (PID: 6900)
Powershell scripting: start process
- MEGAvpnSetup64.exe (PID: 6596)
Script adds exclusion path to Windows Defender
- MEGAvpnSetup64.exe (PID: 6900)
Checks Windows Trust Settings
- MEGAvpnSetup64.exe (PID: 6900)
Uses powercfg.exe to modify the power settings
- WmiPrvSE.exe (PID: 6160)
Starts CMD.EXE for commands execution
- MEGAvpnSetup64.exe (PID: 6900)
Executable content was dropped or overwritten
- WmiPrvSE.exe (PID: 6160)
- MEGAvpnSetup64.exe (PID: 6900)
Drops a system driver (possible attempt to evade defenses)
- WmiPrvSE.exe (PID: 6160)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2256)
Connects to unusual port
- conhost.exe (PID: 6272)
INFO
Process checks computer location settings
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
Checks supported languages
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
The executable file from the user directory is run by the Powershell process
- MEGAvpnSetup64.exe (PID: 6900)
Reads the computer name
- MEGAvpnSetup64.exe (PID: 6596)
- MEGAvpnSetup64.exe (PID: 6900)
Creates files in the program directory
- MEGAvpnSetup64.exe (PID: 6900)
Checks proxy server information
- MEGAvpnSetup64.exe (PID: 6900)
Reads the software policy settings
- MEGAvpnSetup64.exe (PID: 6900)
Creates files or folders in the user directory
- MEGAvpnSetup64.exe (PID: 6900)
Reads the machine GUID from the registry
- MEGAvpnSetup64.exe (PID: 6900)
Create files in a temporary directory
- WmiPrvSE.exe (PID: 6160)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7160)
- powershell.exe (PID: 6468)
Manual execution by a user
- regedit.exe (PID: 6884)
- powershell.exe (PID: 400)
- regedit.exe (PID: 6664)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7160)
- powershell.exe (PID: 400)
UPX packer has been detected
- conhost.exe (PID: 6272)
Checks current location (POWERSHELL)
- powershell.exe (PID: 400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6272) conhost.exe
Decrypted-URLs (1)https://206.12
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.42 |
| CodeSize: | 150528 |
| InitializedDataSize: | 496128 |
| UninitializedDataSize: | 3584 |
| EntryPoint: | 0x12fd |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | MEGA Limited |
| FileDescription: | MEGA VPN |
| FileVersion: | 1.0.0.0 |
| LegalCopyright: | MEGA Limited 2024 |
| ProductName: | MEGA VPN |
| ProductVersion: | 1.0.0.0 |
Total processes
165
Monitored processes
26
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6160 | "C:\Windows\System32\wbem\wmiprvse.exe" | C:\Windows\System32\wbem\WmiPrvSE.exe | MEGAvpnSetup64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Provider Host Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6172 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6200 | "C:\Windows\System32\cmd.exe" /C choice /C Y /N /D Y /T 3 & Del "C:\Users\admin\Downloads\MEGAvpnSetup64.exe" | C:\Windows\System32\cmd.exe | — | MEGAvpnSetup64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6216 | C:\WINDOWS\system32\powercfg.exe /x -hibernate-timeout-dc 0 | C:\Windows\System32\powercfg.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | conhost.exe | C:\Windows\System32\conhost.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
xor-url(PID) Process(6272) conhost.exe Decrypted-URLs (1)https://206.12 | |||||||||||||||
| 6284 | C:\WINDOWS\system32\powercfg.exe /x -hibernate-timeout-ac 0 | C:\Windows\System32\powercfg.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 125
Read events
37 087
Write events
38
Delete events
0
Modification events
| (PID) Process: | (6596) MEGAvpnSetup64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6596) MEGAvpnSetup64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6596) MEGAvpnSetup64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6596) MEGAvpnSetup64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6688) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6688) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6688) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6688) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6900) MEGAvpnSetup64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6900) MEGAvpnSetup64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
2
Suspicious files
10
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pv51twfq.thj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7160 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ht2hoe0j.p2s.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6688 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:58AA4968775D0260D7296ED61E59205D | SHA256:E9E1C3F0E024154BFCA8270F945E8891783AEC44B2CD5365B4E27AD1F3AEEC9E | |||
| 6900 | MEGAvpnSetup64.exe | C:\ProgramData\HK4ascBK6XOWTw\091tWWvcNt8c3Q.exe | executable | |
MD5:1001507ADDB65D5708D79CC0C8E672D6 | SHA256:0C7D2BA6ABC70DBF020E9A626D0E076F177660A59A7F1131DE7212FF745316AD | |||
| 6688 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_npmqmyz1.alj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6468 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_j2euhfj2.jc4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6900 | MEGAvpnSetup64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\xor[1].bin | binary | |
MD5:6494CD4717F83BB10046F7336024D22D | SHA256:B0A7C0AF1E7C36D5FBF2F8D1699A226DDA8729A5E075448ECF30DD68CE243C0A | |||
| 6160 | WmiPrvSE.exe | C:\Users\admin\AppData\Local\Temp\honnresalcnl.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
| 400 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:6348B0F88F5783D64CF74A4EC670ADA9 | SHA256:FCE3A10C6722916D50C52FC0AD8AD553EE65D099AC974687B892D99DC6ED454A | |||
| 400 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\Q75JDRSZGXNSJJ31F4CT.temp | binary | |
MD5:6348B0F88F5783D64CF74A4EC670ADA9 | SHA256:FCE3A10C6722916D50C52FC0AD8AD553EE65D099AC974687B892D99DC6ED454A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
60
DNS requests
32
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6900 | MEGAvpnSetup64.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
6900 | MEGAvpnSetup64.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4292 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
4100 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6400 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
240 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1432 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6900 | MEGAvpnSetup64.exe | 172.67.157.59:443 | tempfiles.ninja | CLOUDFLARENET | US | unknown |
6900 | MEGAvpnSetup64.exe | 142.250.184.227:80 | c.pki.goog | GOOGLE | US | whitelisted |
6272 | conhost.exe | 51.222.12.201:10343 | xmr-us-east1.nanopool.org | OVH SAS | CA | unknown |
6272 | conhost.exe | 104.20.4.235:443 | pastebin.com | CLOUDFLARENET | — | unknown |
6272 | conhost.exe | 51.79.71.77:10343 | xmr-us-east1.nanopool.org | OVH SAS | CA | unknown |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
tempfiles.ninja |
| unknown |
c.pki.goog |
| whitelisted |
xmr-us-east1.nanopool.org |
| whitelisted |
pastebin.com |
| shared |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY Observed DNS Query to Coin Mining Domain (nanopool .org) |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |