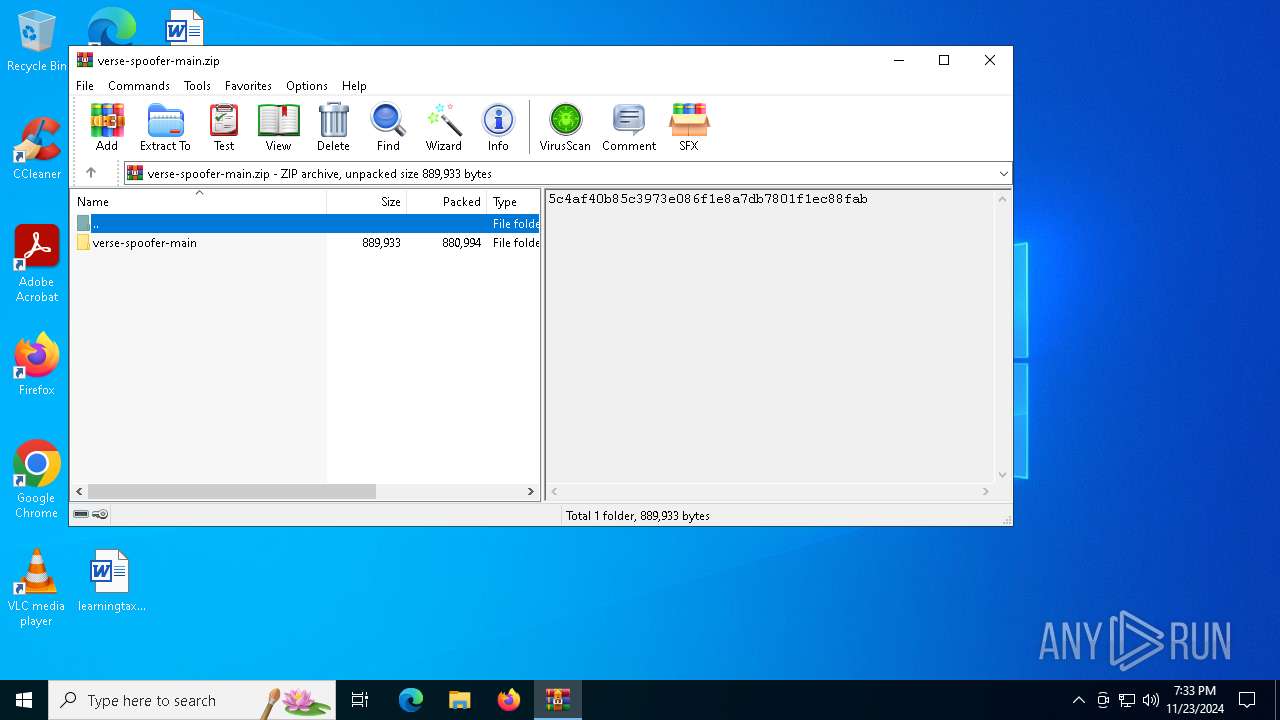
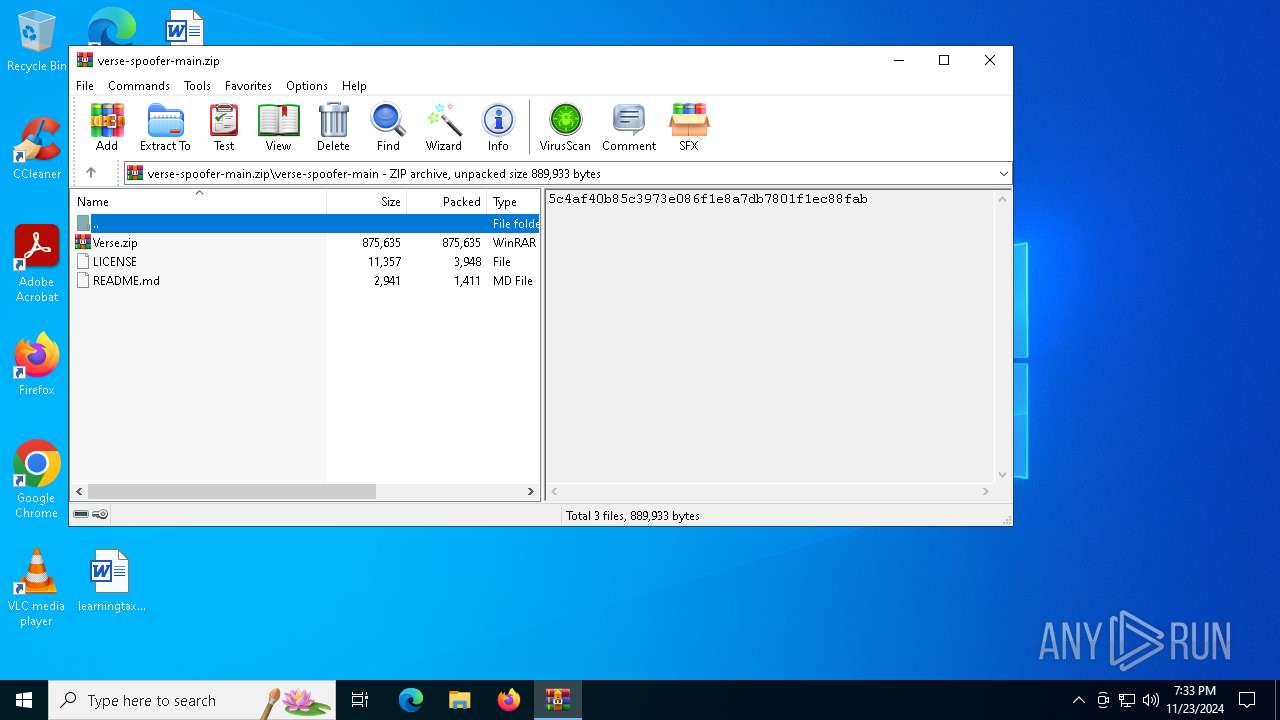
| File name: | verse-spoofer-main.zip |
| Full analysis: | https://app.any.run/tasks/75de5d95-5b1a-4b9e-8603-4ba2d3017bc9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | November 23, 2024, 19:33:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 144A4DCD19EDD75C77E4EE2826AA4A10 |
| SHA1: | 8C13D31383966CD6B985F8C9F16CF30A102A895B |
| SHA256: | 0ACC50DF80E99BAB480967768048653F81C0164DD2B076D618C609D3B6461F17 |
| SSDEEP: | 49152:X3/uTq17xuNq7lksNRQ0hPn55PE0x3tlELuR9SuNRZQ0VPG5dE0R3tlEruv9H/:X3GTqSNqBtNRPPn5G03t7jZ/PG5W0XNh |
MALICIOUS
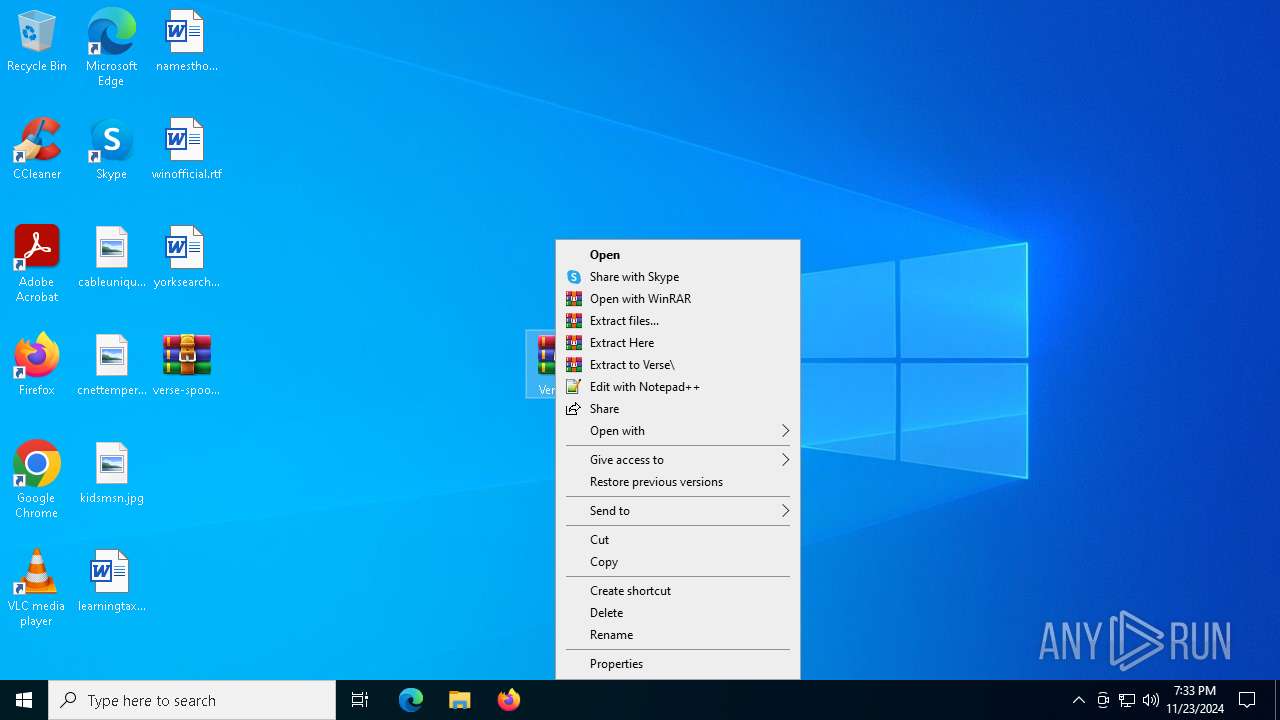
Generic archive extractor
- WinRAR.exe (PID: 3808)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
- Verse.exe (PID: 1520)
Connects to the CnC server
- svchost.exe (PID: 2192)
SUSPICIOUS
Executes application which crashes
- Verse.exe (PID: 5032)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
- Verse.exe (PID: 1520)
Application launched itself
- Verse.exe (PID: 5032)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 3808)
Manual execution by a user
- WinRAR.exe (PID: 1684)
- Verse.exe (PID: 5032)
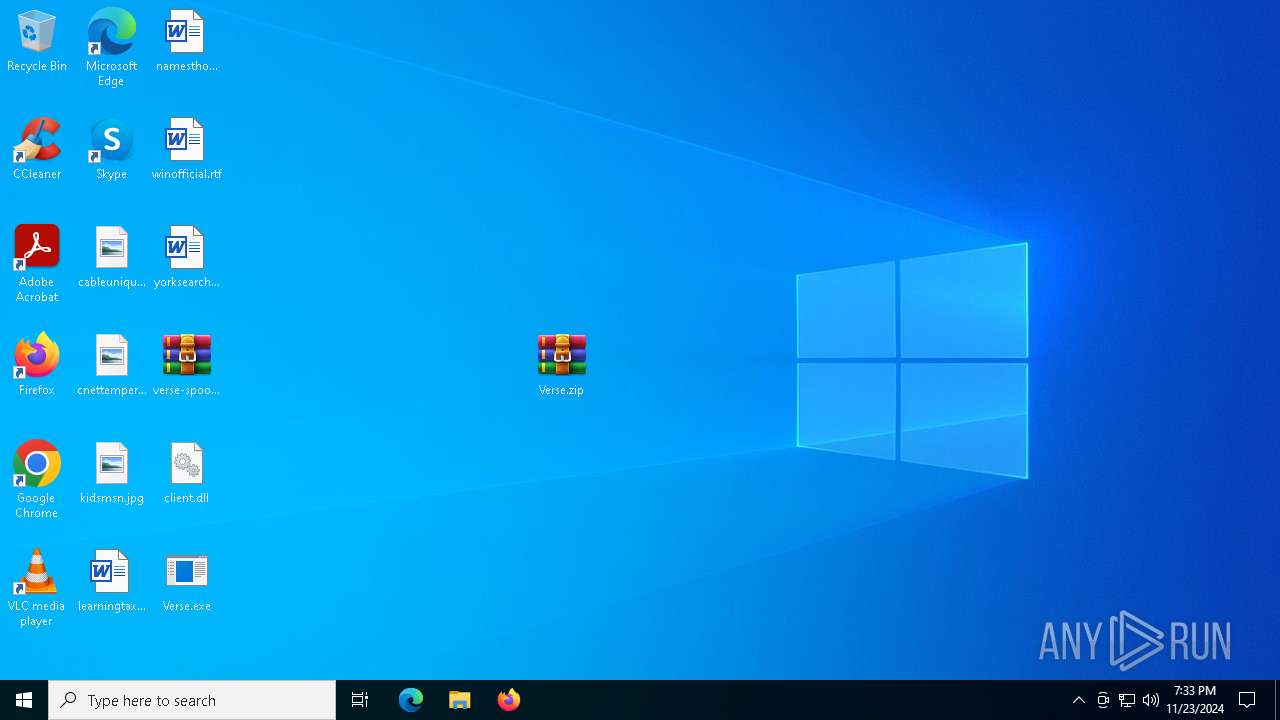
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:11:19 06:04:40 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | verse-spoofer-main/ |
Total processes
135
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1520 | "C:\Users\admin\Desktop\Verse.exe" | C:\Users\admin\Desktop\Verse.exe | Verse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1684 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Verse.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3808 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\verse-spoofer-main.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3984 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5032 -s 276 | C:\Windows\SysWOW64\WerFault.exe | Verse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Verse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | "C:\Users\admin\Desktop\Verse.exe" | C:\Users\admin\Desktop\Verse.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
Total events
4 978
Read events
4 955
Write events
23
Delete events
0
Modification events
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\verse-spoofer-main.zip | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (3808) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
1
Suspicious files
7
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_Verse.exe_915e1967f37a6385e7075f80cd3ad9c91d6fb8_f18a64ef_c47ae0ca-9144-4190-a359-90041792aa58\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1684 | WinRAR.exe | C:\Users\admin\Desktop\Verse.exe | executable | |
MD5:1B14CA85C235E35E80113854029BD38A | SHA256:D809E69A4B66D6C694E2892BB07E83BEA22E4996A441A5277C69116CC23FEEAB | |||
| 3984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC632.tmp.WERInternalMetadata.xml | xml | |
MD5:EF6B6D680EE083996ED22458E31F7FFD | SHA256:B04637F89888B7AB49A642A7D6AC9E28145896E0F03F6CF8AF9CF24C021DE8F6 | |||
| 3984 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:1EC57BC48B213E7172487C7A314E7EC2 | SHA256:03AFE299FDEC9D35334D438F09EC447DB94589AC35B90BA753858A6592AEF27E | |||
| 3984 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\21253908F3CB05D51B1C2DA8B681A785 | der | |
MD5:F6F53CD09A41E968C363419B279D3112 | SHA256:6D2BB01CC7A9BADE2113B219CAC1BDA86B2733196B7E1BD0C807CE1E396B1892 | |||
| 1684 | WinRAR.exe | C:\Users\admin\Desktop\client.dll | text | |
MD5:702348A3919A13F056AB52A8085C5B5B | SHA256:8C5F289D8817F1FF725DCCA44B93A0A9BEBDBB933750EBE81E91C33C561C875C | |||
| 3984 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:F0CF5B1794ECA7CD73F9C020DAAB8EF2 | SHA256:2AF00EDCE7EF3266897E52DC81E8DE3B7A079028C0F1F96EAFF9E38AD342F617 | |||
| 3984 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERC662.tmp.xml | xml | |
MD5:4BB9A6CFDB3F56B4B5F2C4810E462446 | SHA256:3A7B547C988AD001152D305767D637A6904431D98C2A09C2AA69276D0B66AF39 | |||
| 3984 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:363ED020182048C2F037AA935A573601 | SHA256:89DD2B3AAB1F8F2FF6678D3DBF53D7046BA60B8DCBD46E1D65F6DD41EC44C3CC | |||
| 3984 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\Verse.exe.5032.dmp | binary | |
MD5:F95381ABC43DC2AEA578812BAE9A7D24 | SHA256:6F0D04C0B4CD76EC10D3F64D716087EFAF78773B6C06FE864329E9906AE7334D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
22
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5880 | svchost.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5880 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5964 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5964 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3984 | WerFault.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3984 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4804 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5880 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5880 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5880 | svchost.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5880 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
cook-rain.sbs |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cook-rain .sbs) |
1520 | Verse.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cook-rain .sbs in TLS SNI) |
1520 | Verse.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cook-rain .sbs in TLS SNI) |
1520 | Verse.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cook-rain .sbs in TLS SNI) |
1520 | Verse.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cook-rain .sbs in TLS SNI) |
1520 | Verse.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cook-rain .sbs in TLS SNI) |
1520 | Verse.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cook-rain .sbs in TLS SNI) |