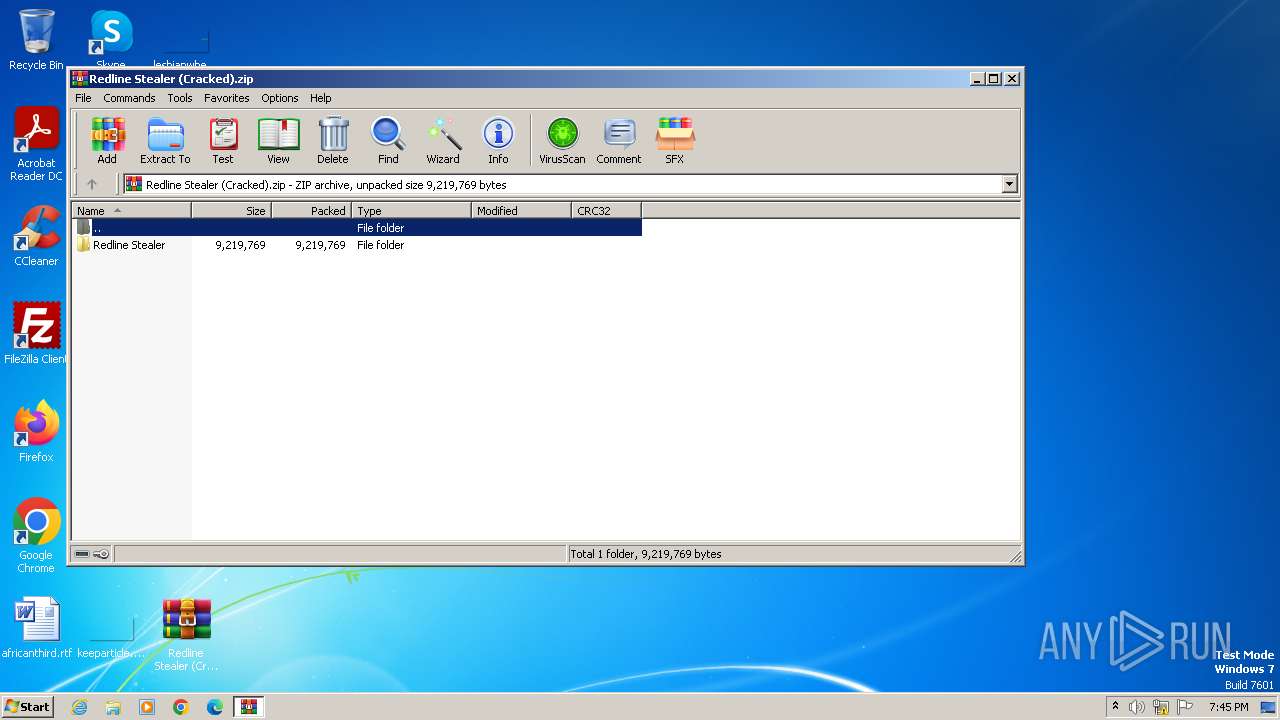
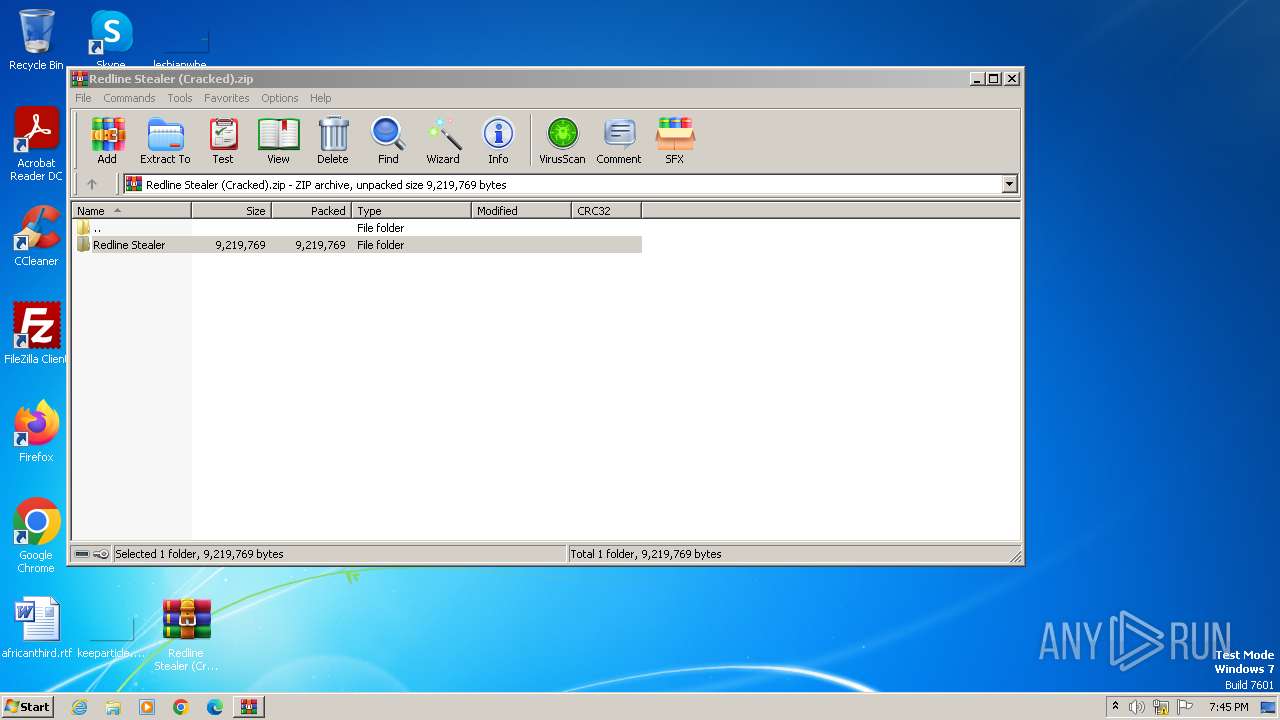
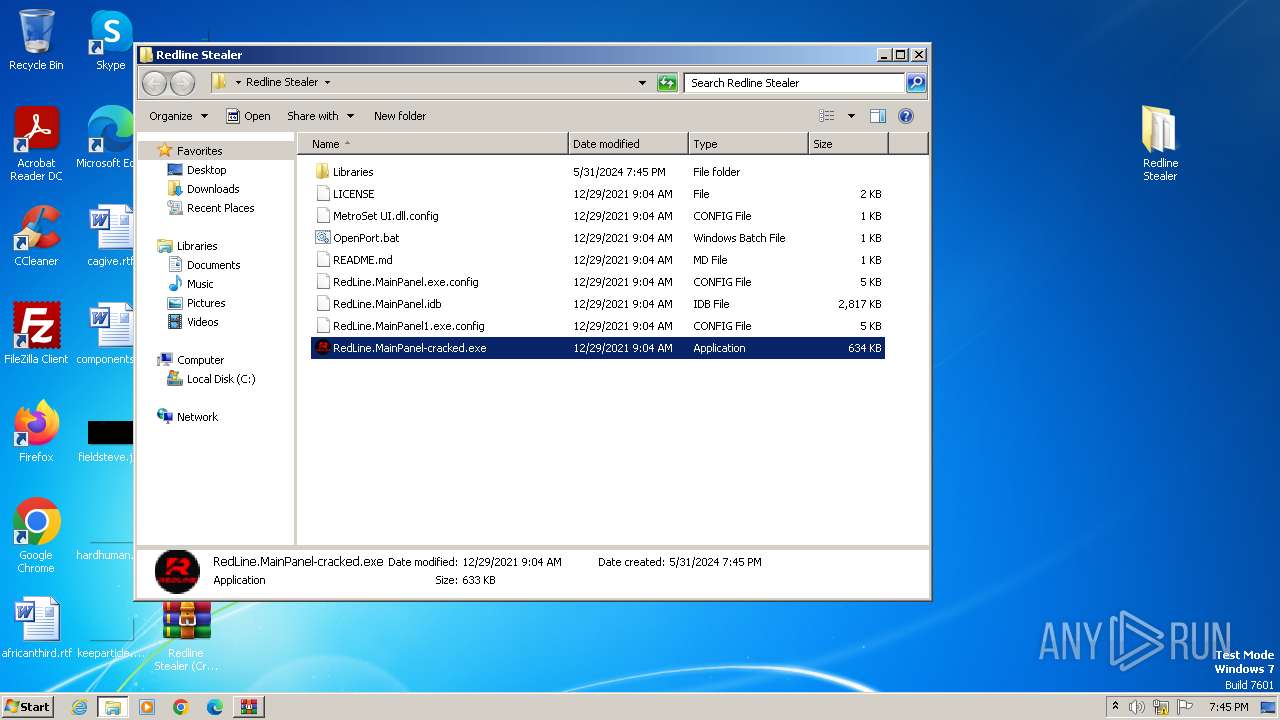
| File name: | Redline Stealer (Cracked).zip |
| Full analysis: | https://app.any.run/tasks/84b357fb-e8e7-4626-b35a-412f471cefa3 |
| Verdict: | Malicious activity |
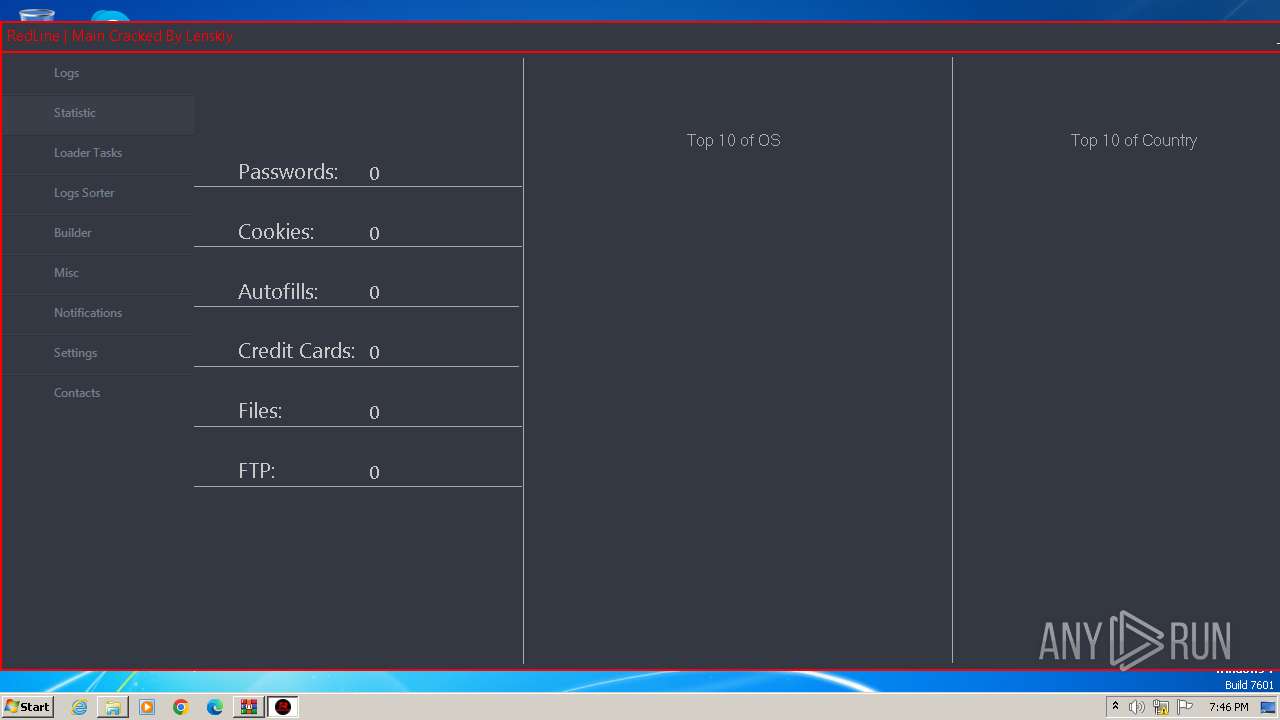
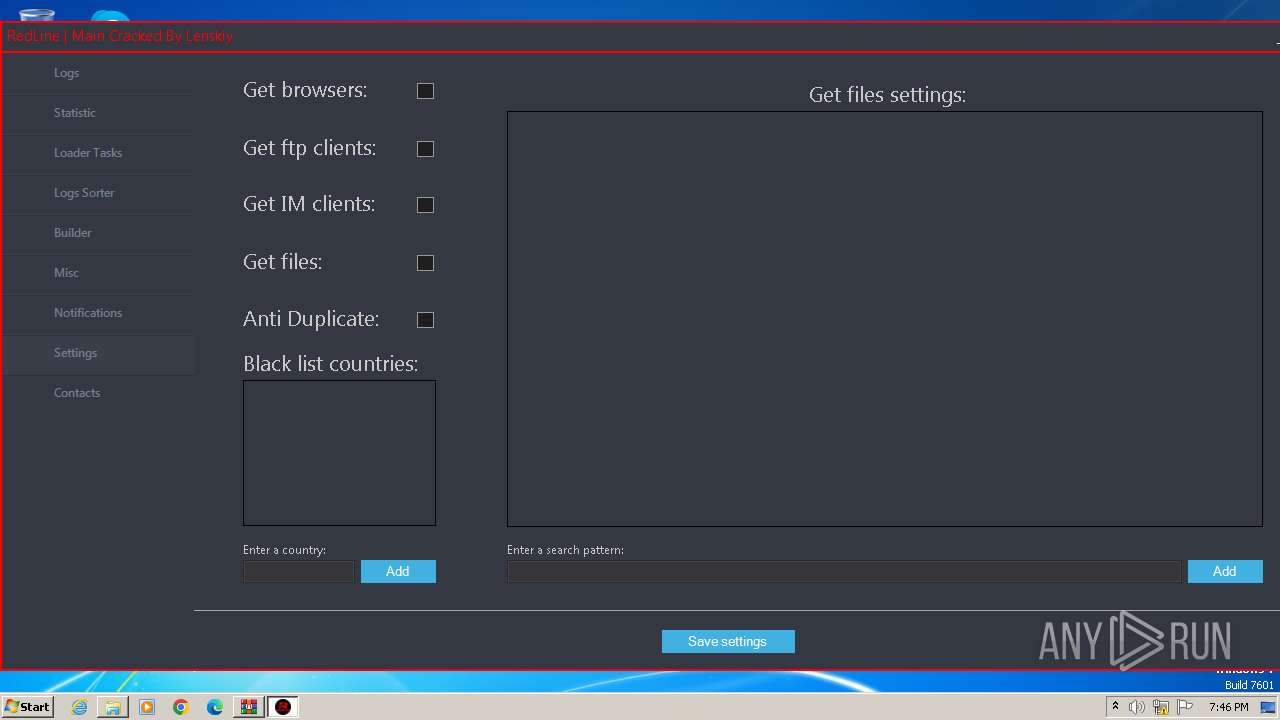
| Threats: | RedLine Stealer is a malicious program that collects users’ confidential data from browsers, systems, and installed software. It also infects operating systems with other malware. |
| Analysis date: | May 31, 2024, 18:45:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 45A6FE57C6337CC0610B2A8DC4F1528F |
| SHA1: | 6856D0C9CBE9A4EE0E249F4B020B8D280F5DCAAB |
| SHA256: | 0A8AA823B88D22FFDCDBC8F5F1B3C4A97B030885ED5AA2CFD8E46B89806AF7D9 |
| SSDEEP: | 98304:WJx39hUrFqNL9Ckdm4IIxYFdrkonHjgDJvLyX5FKCFBN42wjFCC44IgZI6GrKZQX:0el6JC |
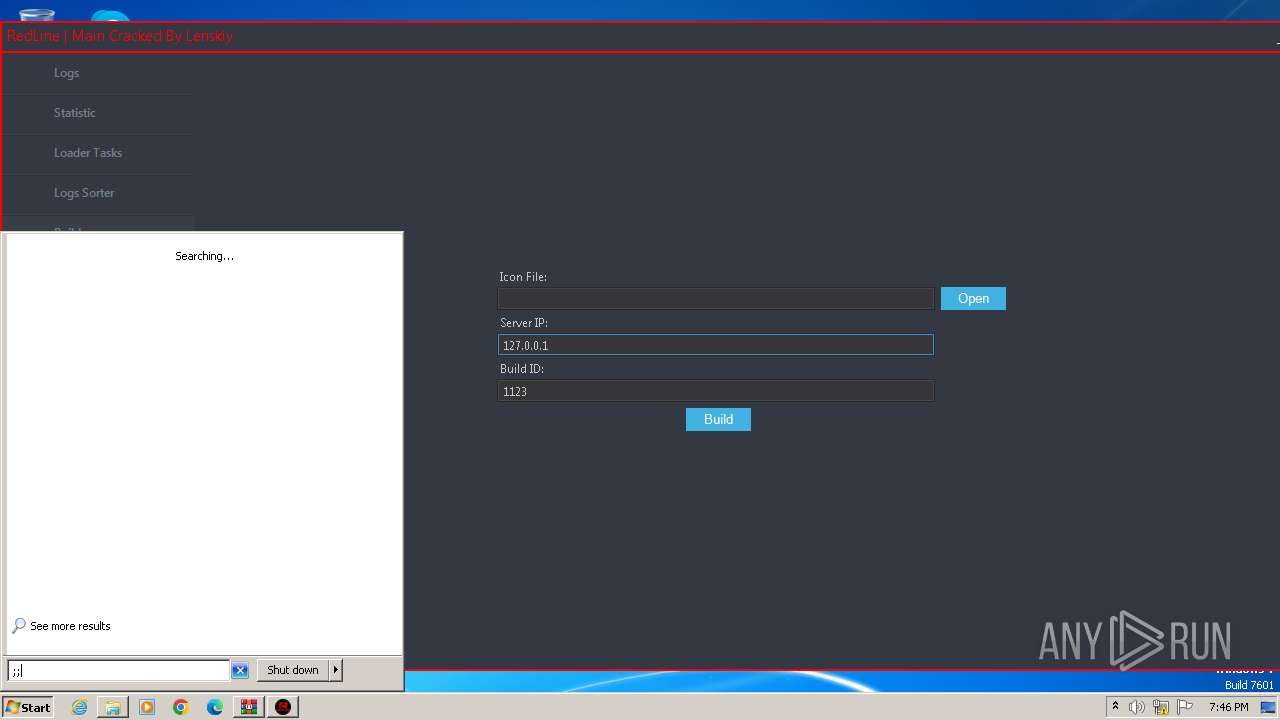
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
REDLINE has been detected (YARA)
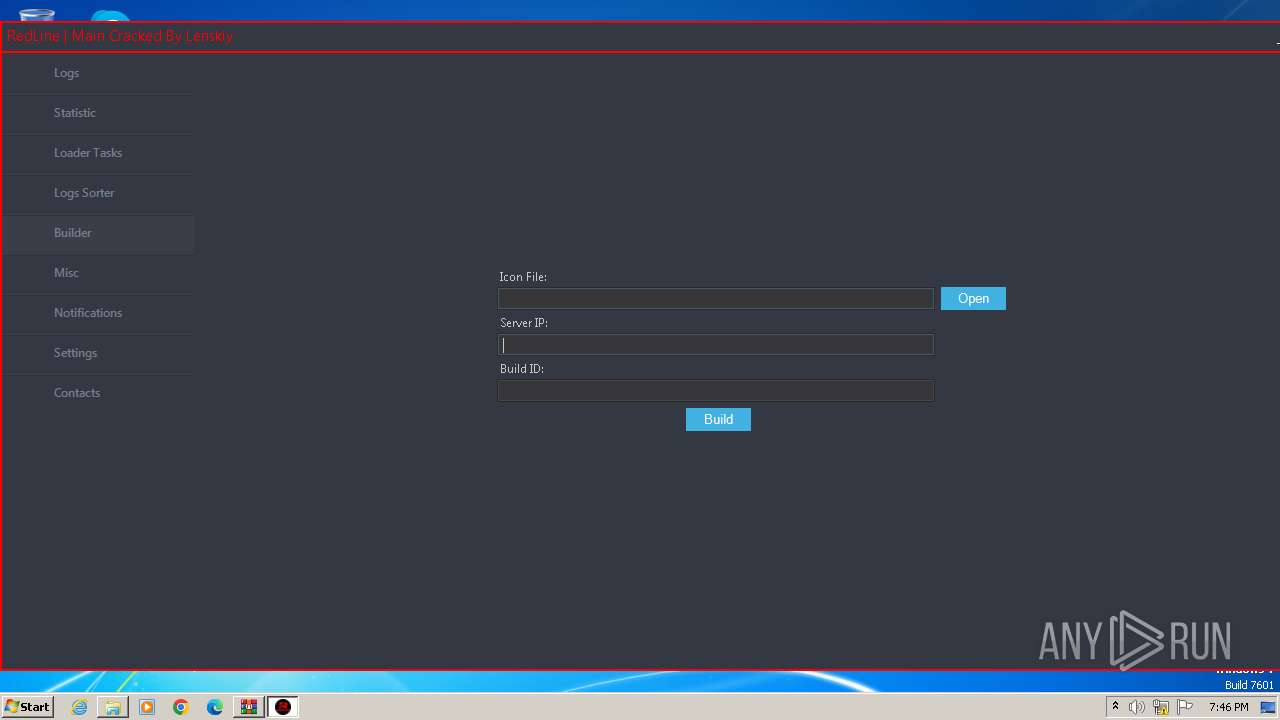
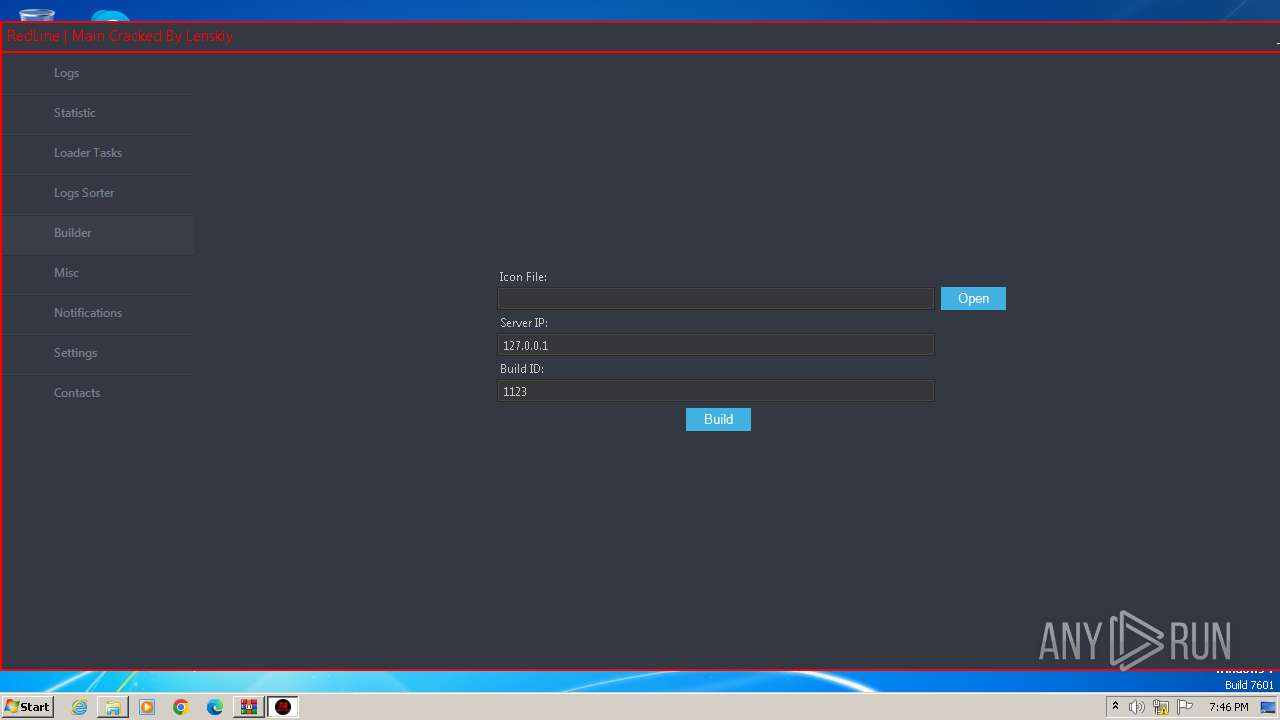
- RedLine.MainPanel-cracked.exe (PID: 752)
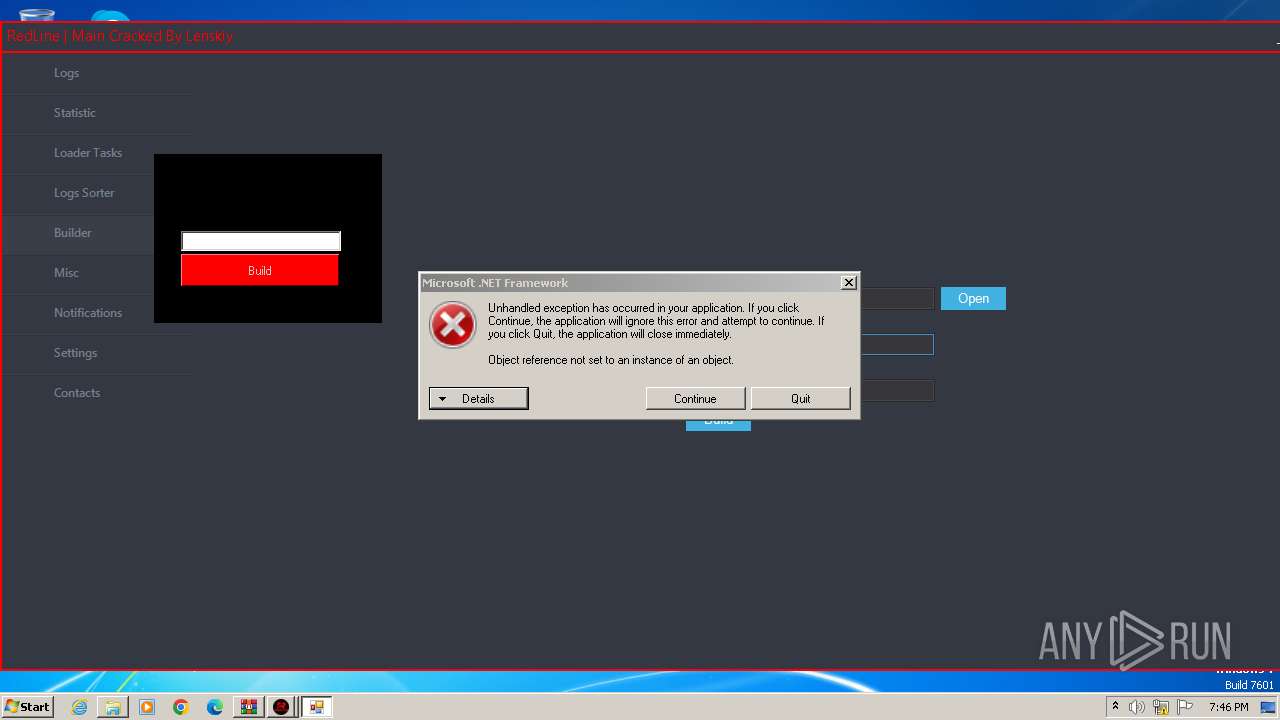
SUSPICIOUS
Reads security settings of Internet Explorer
- RedLine.MainPanel-cracked.exe (PID: 752)
Reads the Internet Settings
- RedLine.MainPanel-cracked.exe (PID: 752)
INFO
Checks supported languages
- RedLine.MainPanel-cracked.exe (PID: 752)
- builder.exe (PID: 728)
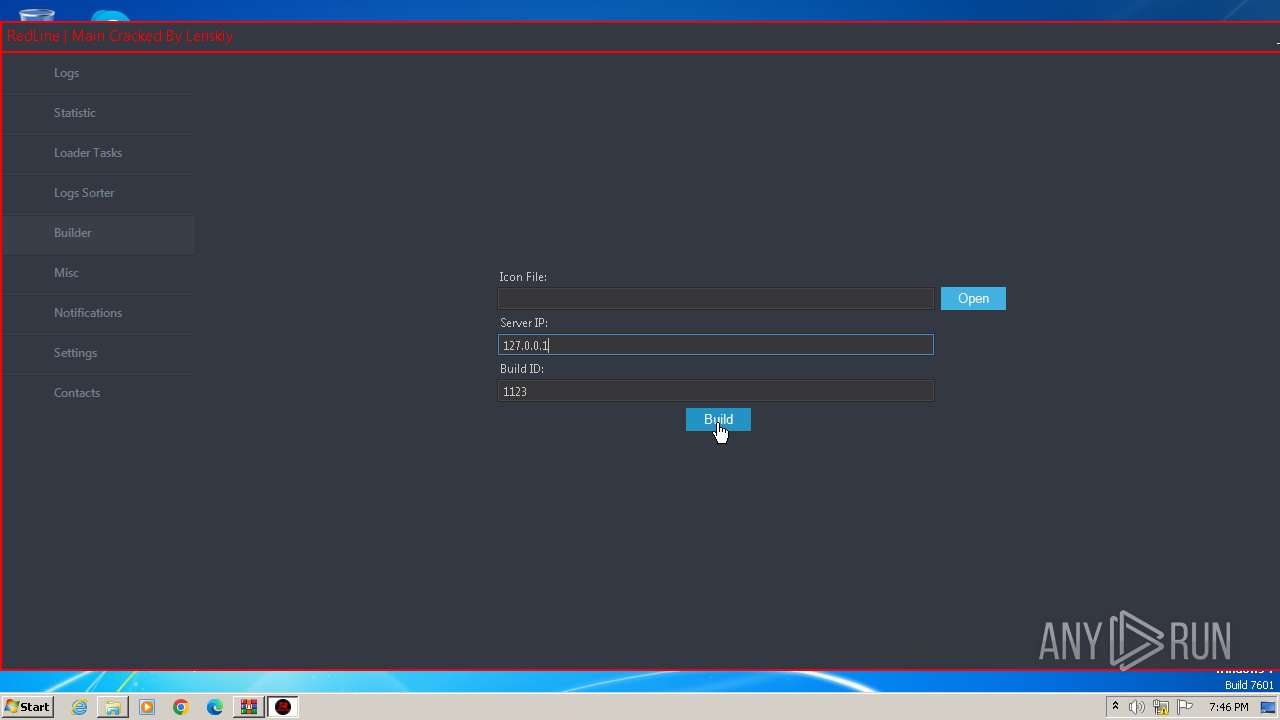
Manual execution by a user
- RedLine.MainPanel-cracked.exe (PID: 752)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Reads the computer name
- builder.exe (PID: 728)
- RedLine.MainPanel-cracked.exe (PID: 752)
Reads the machine GUID from the registry
- builder.exe (PID: 728)
- RedLine.MainPanel-cracked.exe (PID: 752)
Reads Environment values
- RedLine.MainPanel-cracked.exe (PID: 752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (36.3) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | None |
| ZipModifyDate: | 2021:12:29 09:04:16 |
| ZipCRC: | 0x3b3d61c6 |
| ZipCompressedSize: | 446 |
| ZipUncompressedSize: | 446 |
| ZipFileName: | Redline Stealer/README.md |
Total processes
36
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Users\admin\Desktop\Redline Stealer\Libraries\builder.exe" | C:\Users\admin\Desktop\Redline Stealer\Libraries\builder.exe | — | RedLine.MainPanel-cracked.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: builder Version: 1.0.0.0 Modules
| |||||||||||||||
| 752 | "C:\Users\admin\Desktop\Redline Stealer\RedLine.MainPanel-cracked.exe" | C:\Users\admin\Desktop\Redline Stealer\RedLine.MainPanel-cracked.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: RedLinePanel Version: 1.0.0.0 Modules
| |||||||||||||||
| 3972 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Redline Stealer (Cracked).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 925
Read events
4 906
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Redline Stealer (Cracked).zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
15
Suspicious files
6
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\RedLine.MainPanel.exe.config | xml | |
MD5:6EBC9B76090C8C4BF6B65C02503C6CD6 | SHA256:EF9352989527D16CF5BE708B0D8E6D384618746A3999230F477CF50F34FF67C9 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\LICENSE | text | |
MD5:624DABF940FEB6357C70AFB0E1769DD9 | SHA256:F70F862F10B5E832A87D98B159294B68CCF58D4188D7EFB323C053EECED58D82 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\RedLine.MainPanel1.exe.config | xml | |
MD5:6EBC9B76090C8C4BF6B65C02503C6CD6 | SHA256:EF9352989527D16CF5BE708B0D8E6D384618746A3999230F477CF50F34FF67C9 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\RedLine.MainPanel-cracked.exe | executable | |
MD5:BAF102927947289E4D589028620CE291 | SHA256:A6D2D1BA6765E5245B0F62E37D9298E20C913C5A33912B98BD65A76FC5AB28AE | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\Libraries\Mono.Cecil.Rocks.pdb | binary | |
MD5:17E3CCB3A96BE6D93CA3C286CA3B93DC | SHA256:CA54D2395697EFC3163016BBC2BB1E91B13D454B9A5A3EE9A4304012F012E5EB | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\OpenPort.bat | text | |
MD5:CF1CC90281E28CEE22DCE7ED013C2678 | SHA256:84399F8BCCEFA404E156A5351B1DE75A2D5290B4FDDD1754EFB16401ED7218EF | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\MetroSet UI.dll.config | xml | |
MD5:9A25AE6E4FBE956CC33A232AC97D3B16 | SHA256:A407B110C78C0077B651FCBD05CCE073541B61E3E8B4747608069AC5CE686A8C | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\Libraries\stub.exe | executable | |
MD5:9C44CE0CC507F539A3B6AA9C3671F092 | SHA256:7B6C6588D3BDDB06A0EFBBF237CF501C027DAC8BD2B82C6835E0A2C8BDFAE842 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\RedLine.MainPanel.idb | binary | |
MD5:3DA6C975E08BF1A134B25EE33D0288B1 | SHA256:16FEEF35E1C0B52A51E898A04D98034ABBC413E483DEB9C410469427035778C8 | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3972.44627\Redline Stealer\Libraries\Newtonsoft.Json.dll | executable | |
MD5:6815034209687816D8CF401877EC8133 | SHA256:7F912B28A07C226E0BE3ACFB2F57F050538ABA0100FA1F0BF2C39F1A1F1DA814 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |