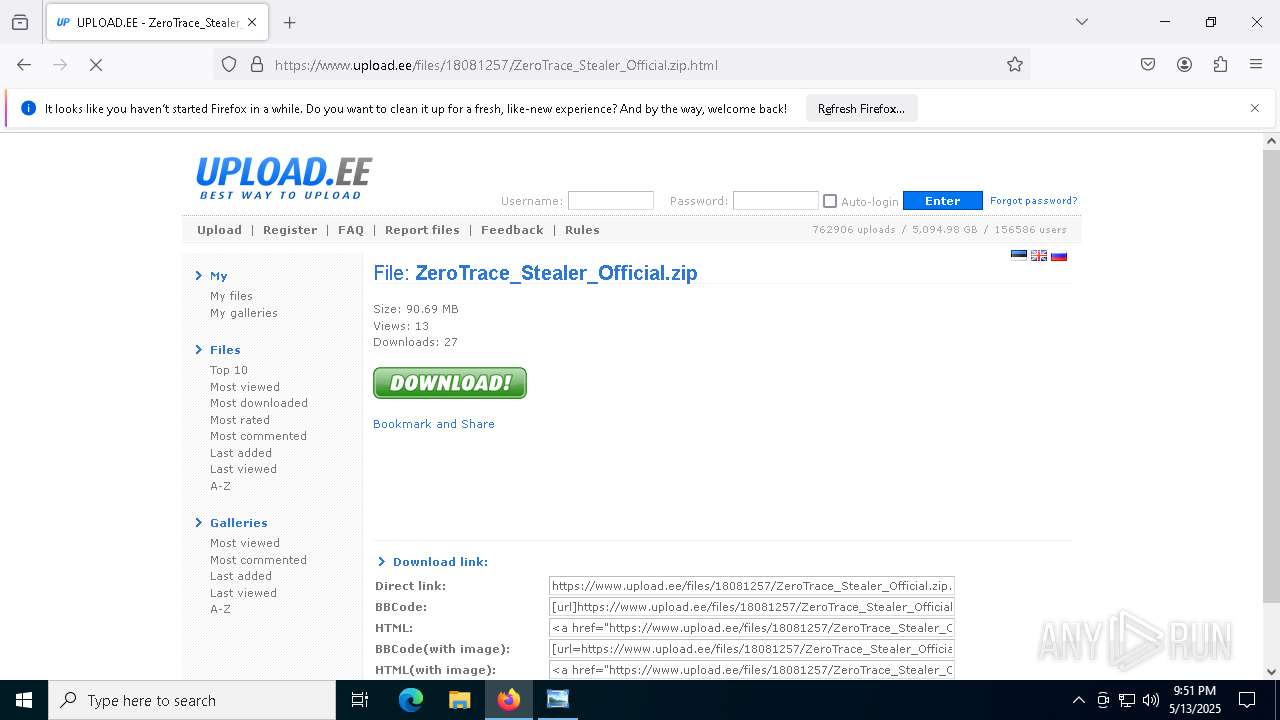
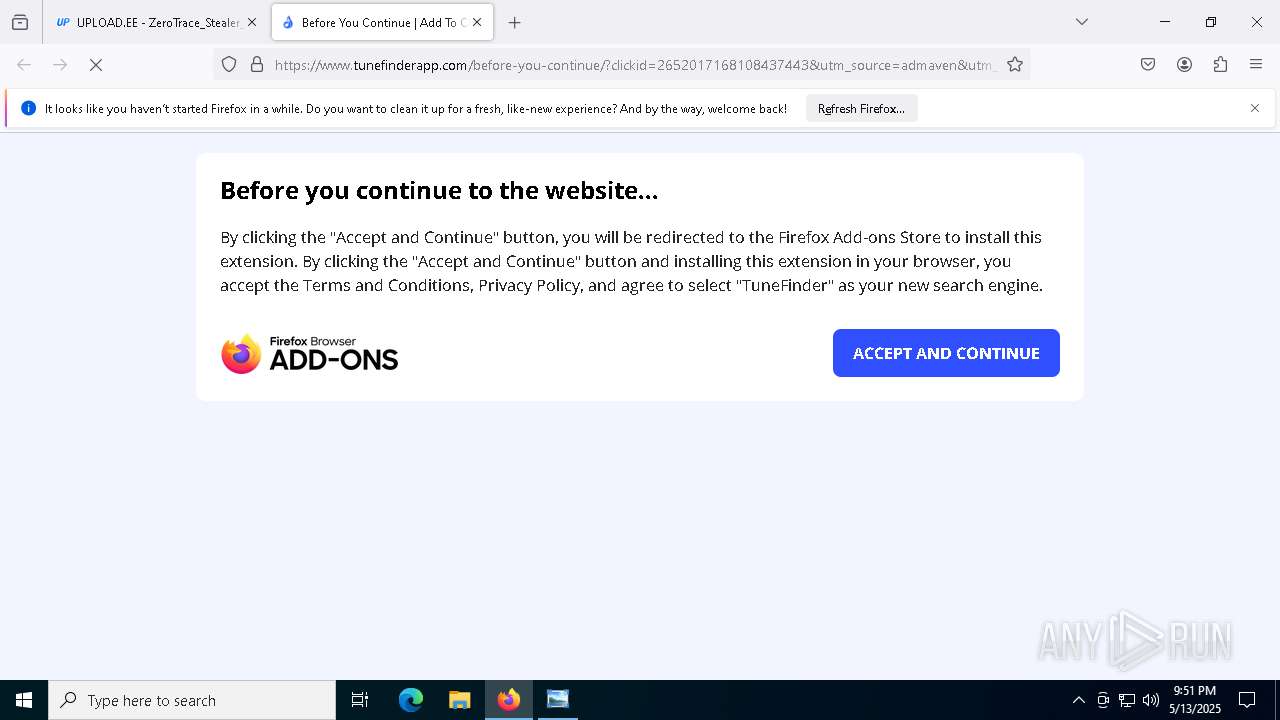
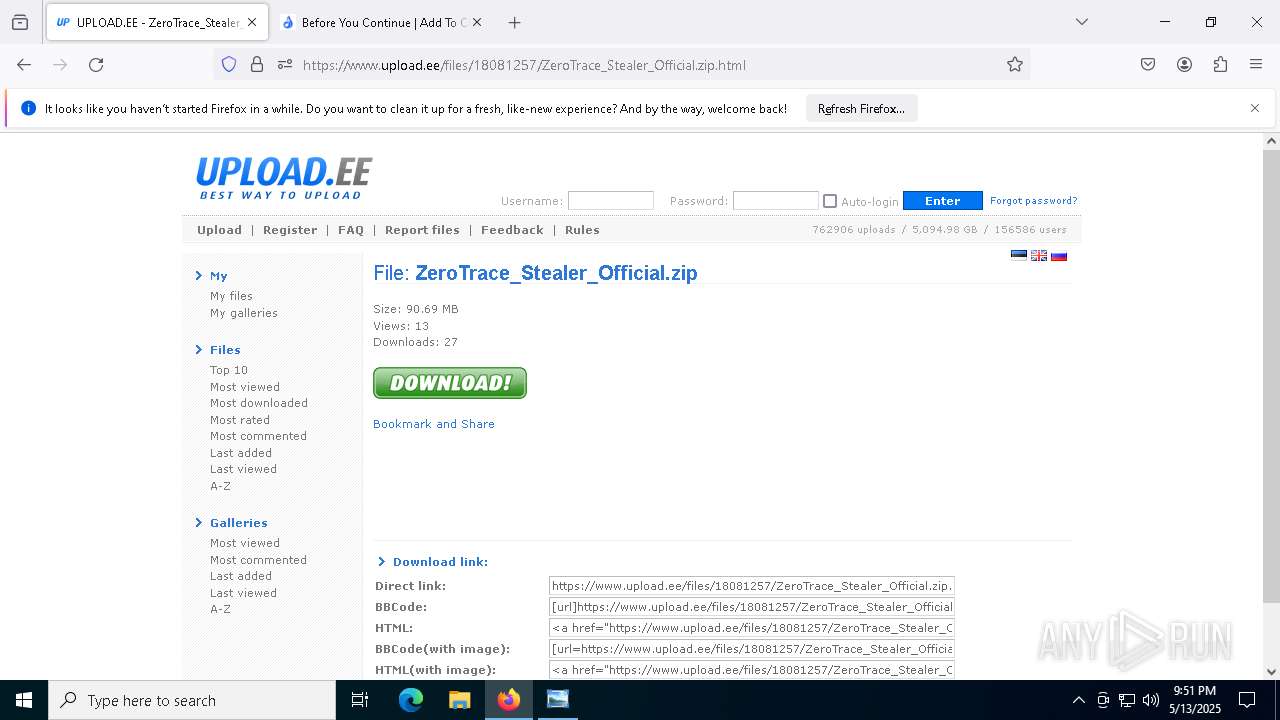
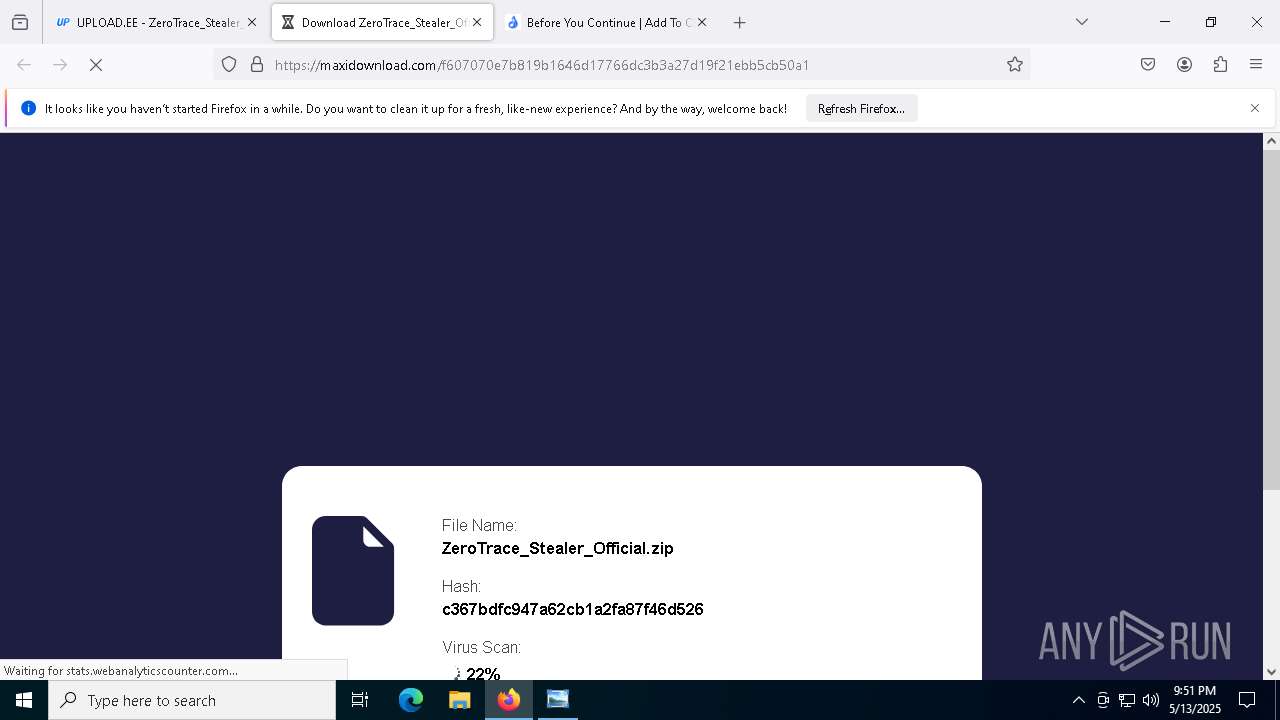
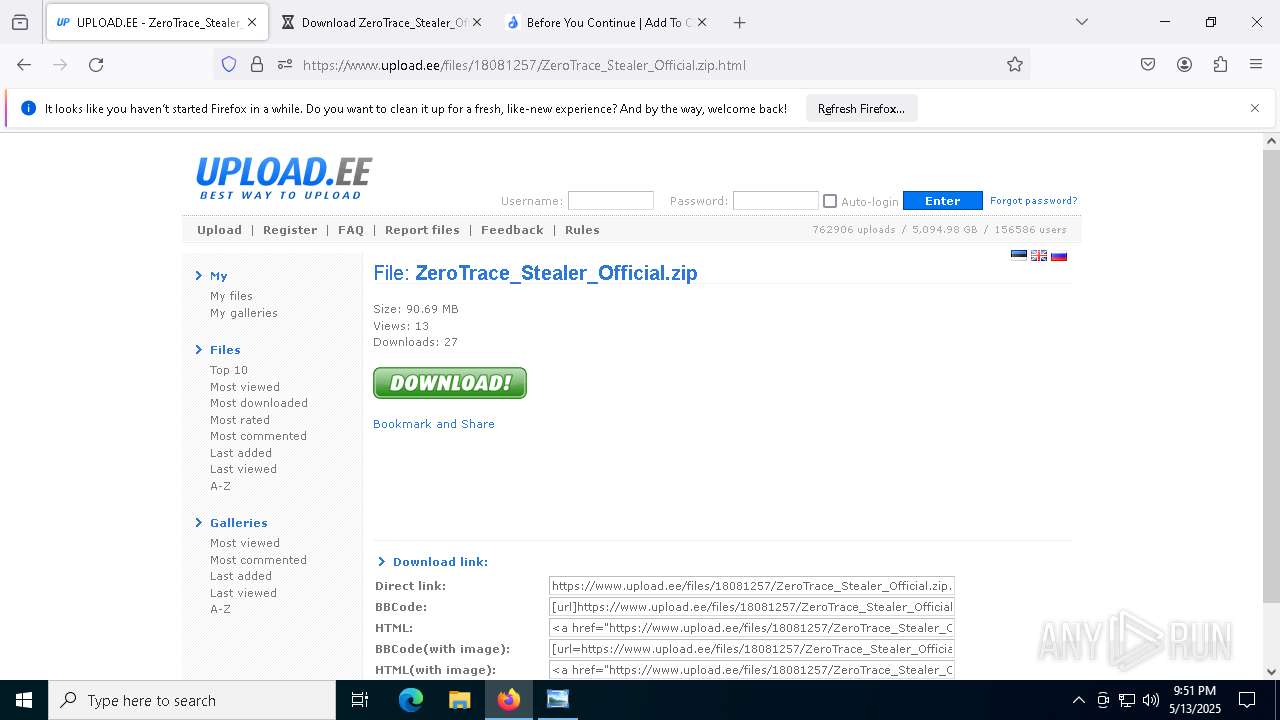
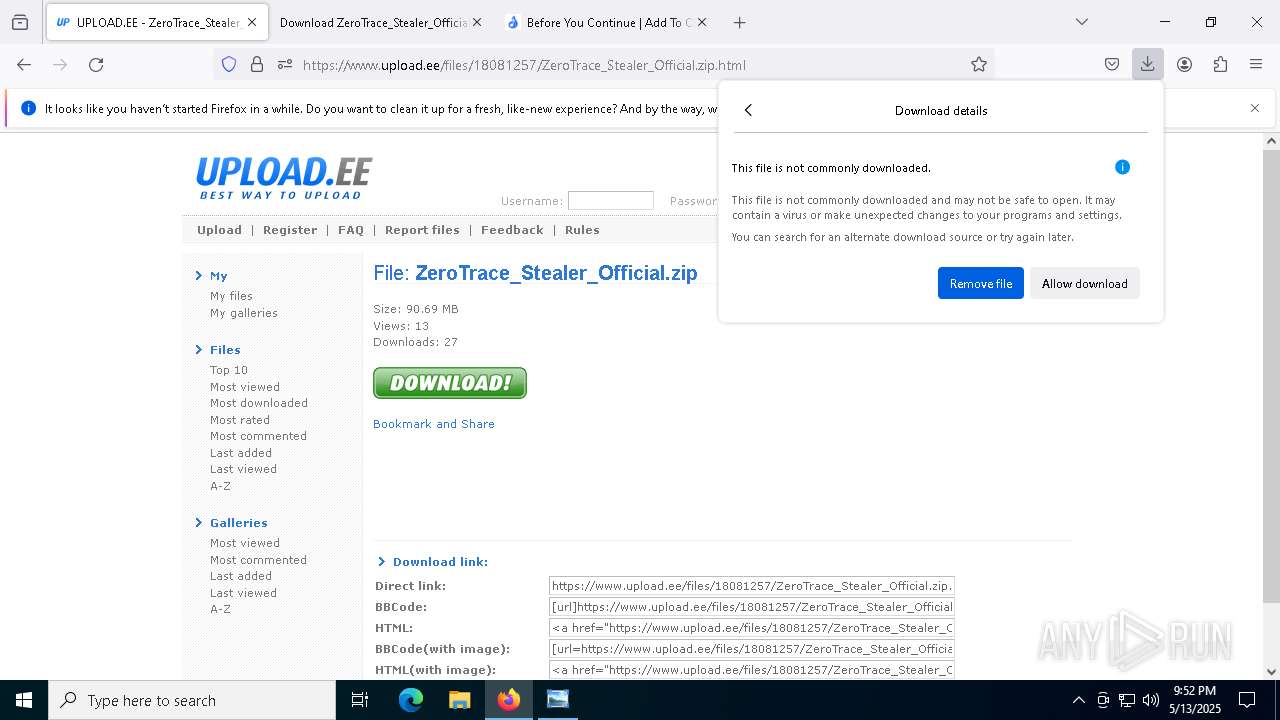
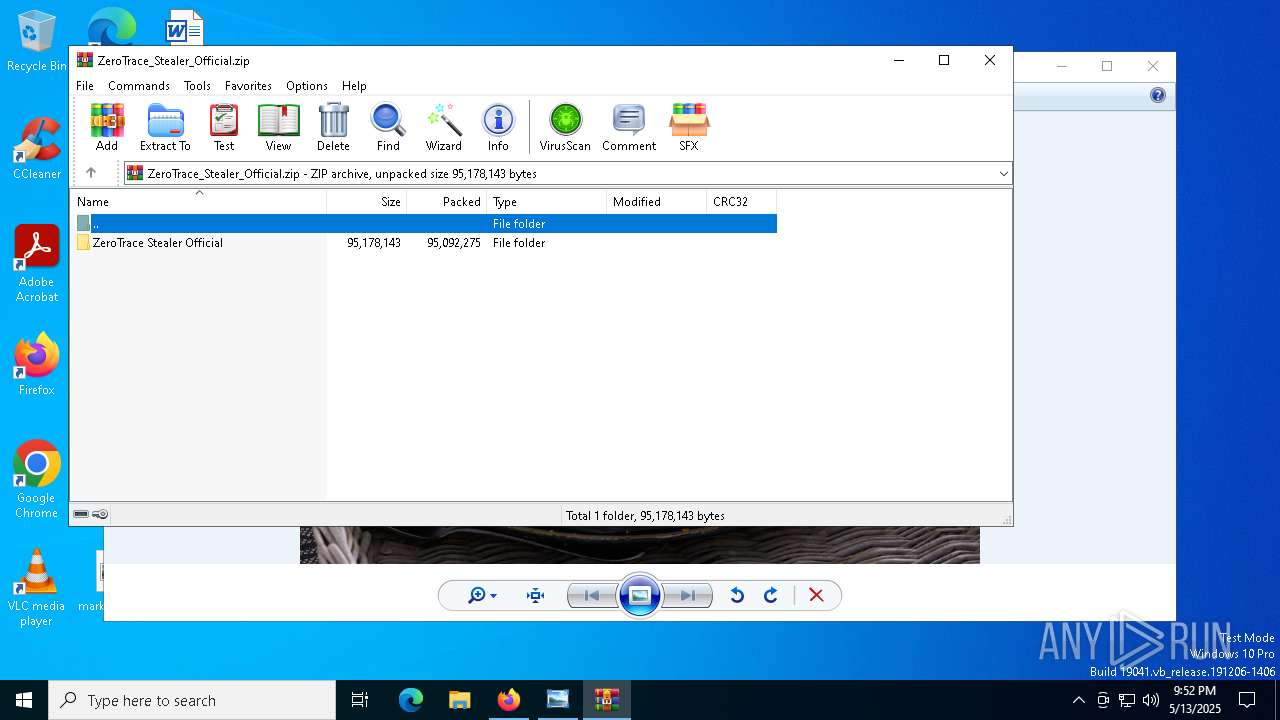
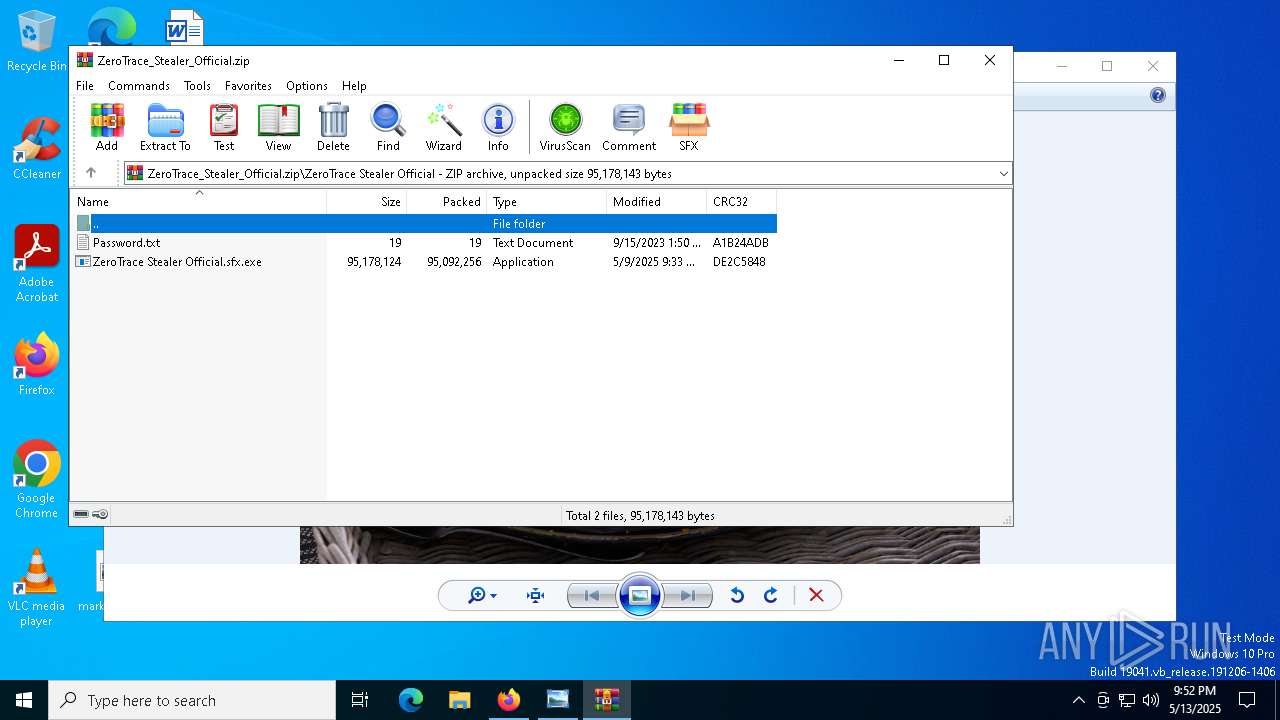
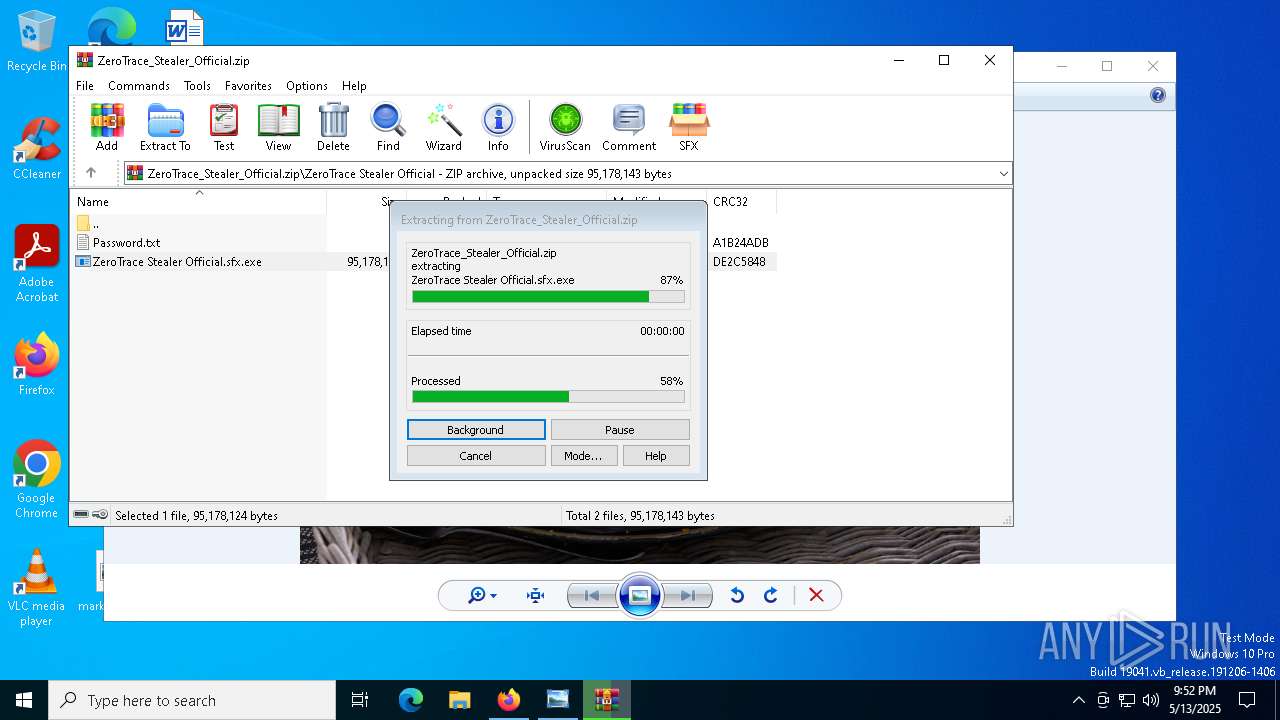
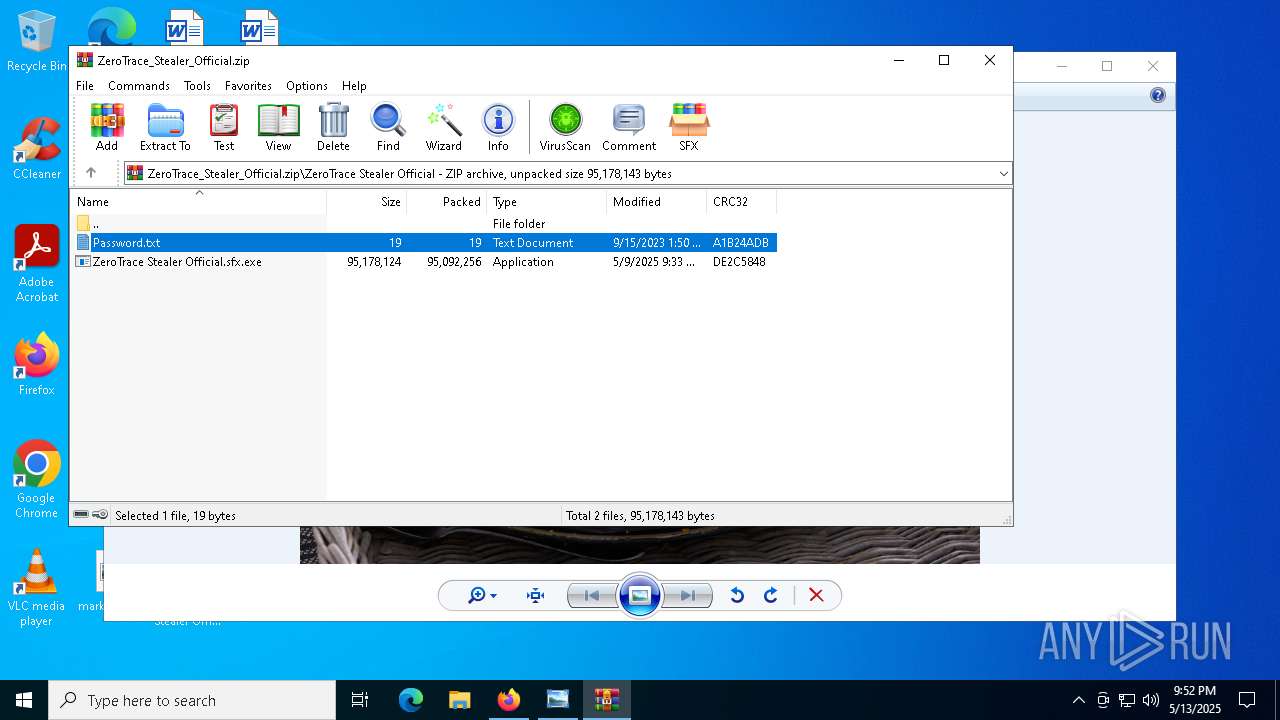
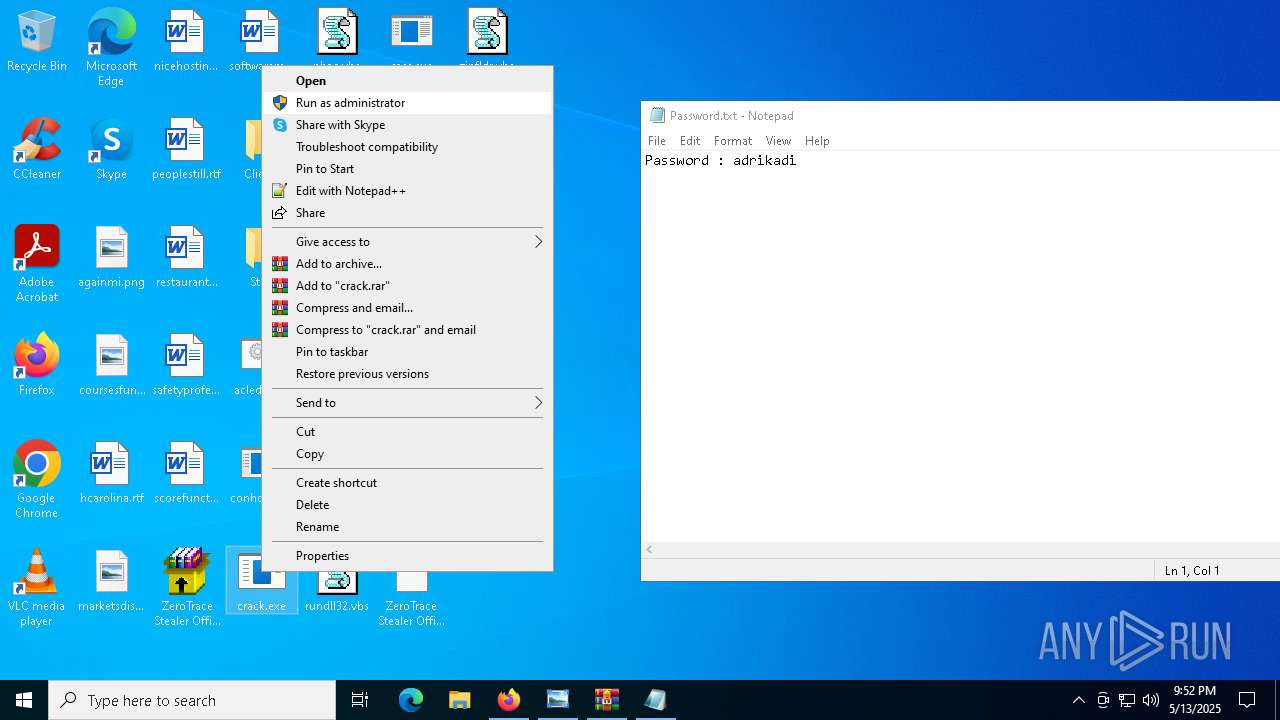
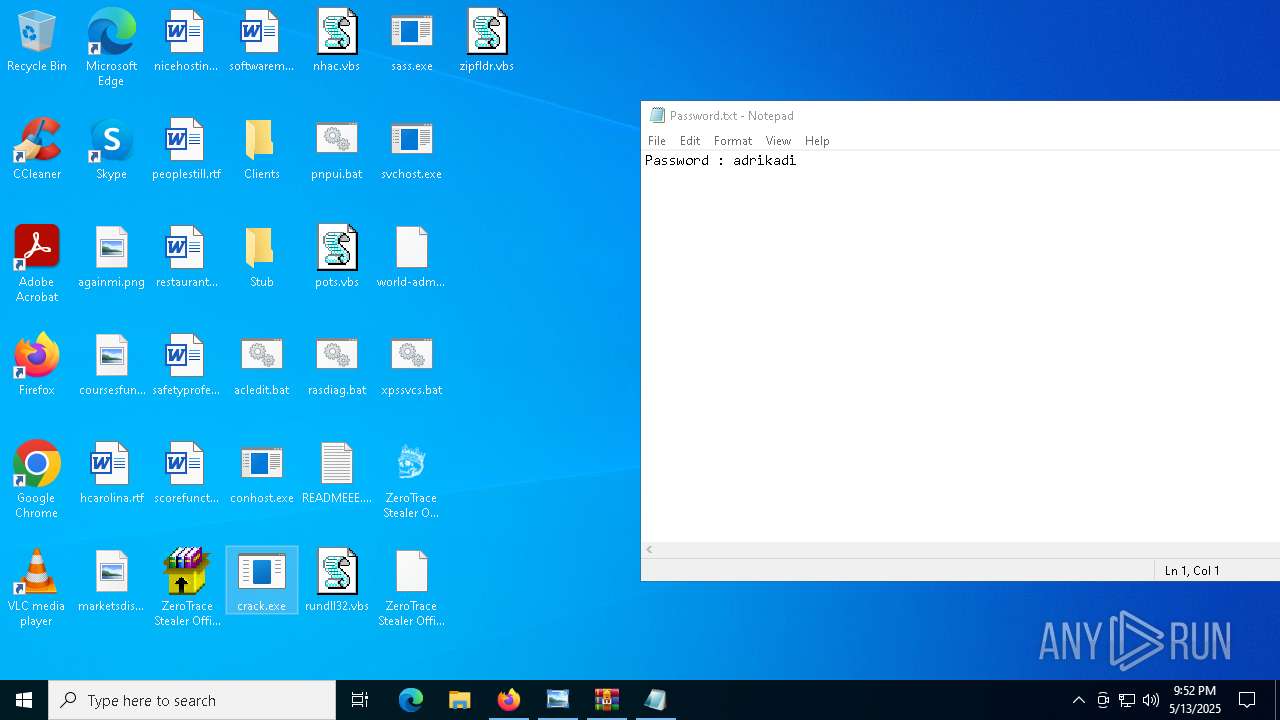
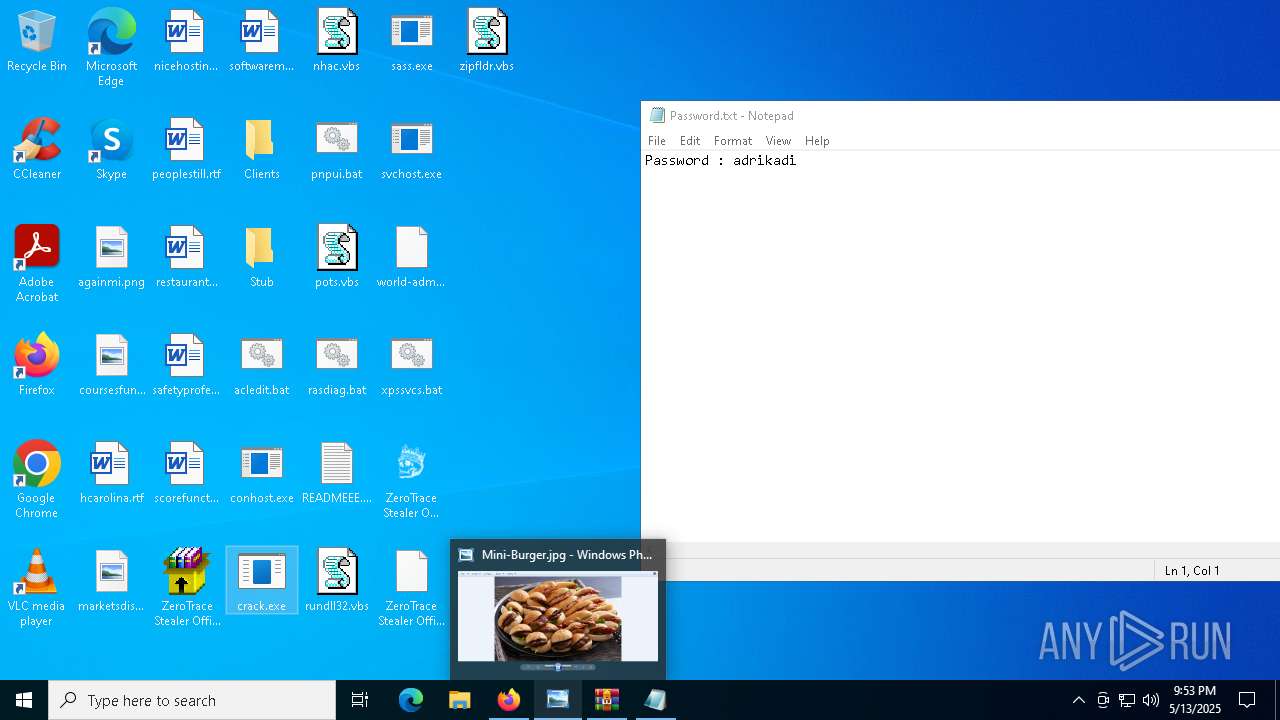
| File name: | Mini-Burger.jpg |
| Full analysis: | https://app.any.run/tasks/3fbcbddb-9fed-4511-b9c4-42e4d7c5b057 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | May 13, 2025, 21:50:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/jpeg |
| File info: | JPEG image data, JFIF standard 1.01, resolution (DPI), density 300x300, segment length 16, Exif Standard: [TIFF image data, little-endian, direntries=11, manufacturer=NIKON CORPORATION, model=NIKON D700, xresolution=176, yresolution=184, resolutionunit=2, software=Capture One 8 Windows, datetime=2018:02:26 09:07:58], comment: "Optimized by JPEGmini 3.13.3.8 0x4b7dfa98", comment: "Optimized by JPEGmini 3.13.3.8 0x717bd9f8", baseline, precision 8, 1920x1278, components 3 |
| MD5: | 2851EE06ED6A04BA81017863310784B4 |
| SHA1: | 29C466CC1B7F40565612D0C3F7C4ABCDD6883D8F |
| SHA256: | 0A392648CEB675F25D7430F9885096926532F42AAF69DA27691E218582287062 |
| SSDEEP: | 24576:raF4lOANMQWU+dXoTS8aFkM0Q3CUwzeihlElDlLBdPfxbUdPJWpIF/XVfAXNM13I:rM4lOANMQWU+dXou8aFkM0Q3CUwzeihs |
MALICIOUS
Vulnerable driver has been detected
- InstallUtil.exe (PID: 6676)
XMRig has been detected
- OmegaEngine.exe (PID: 6960)
MINER has been detected (SURICATA)
- svchost.exe (PID: 2196)
- OmegaEngine.exe (PID: 6960)
Connects to the CnC server
- OmegaEngine.exe (PID: 6960)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 9064)
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
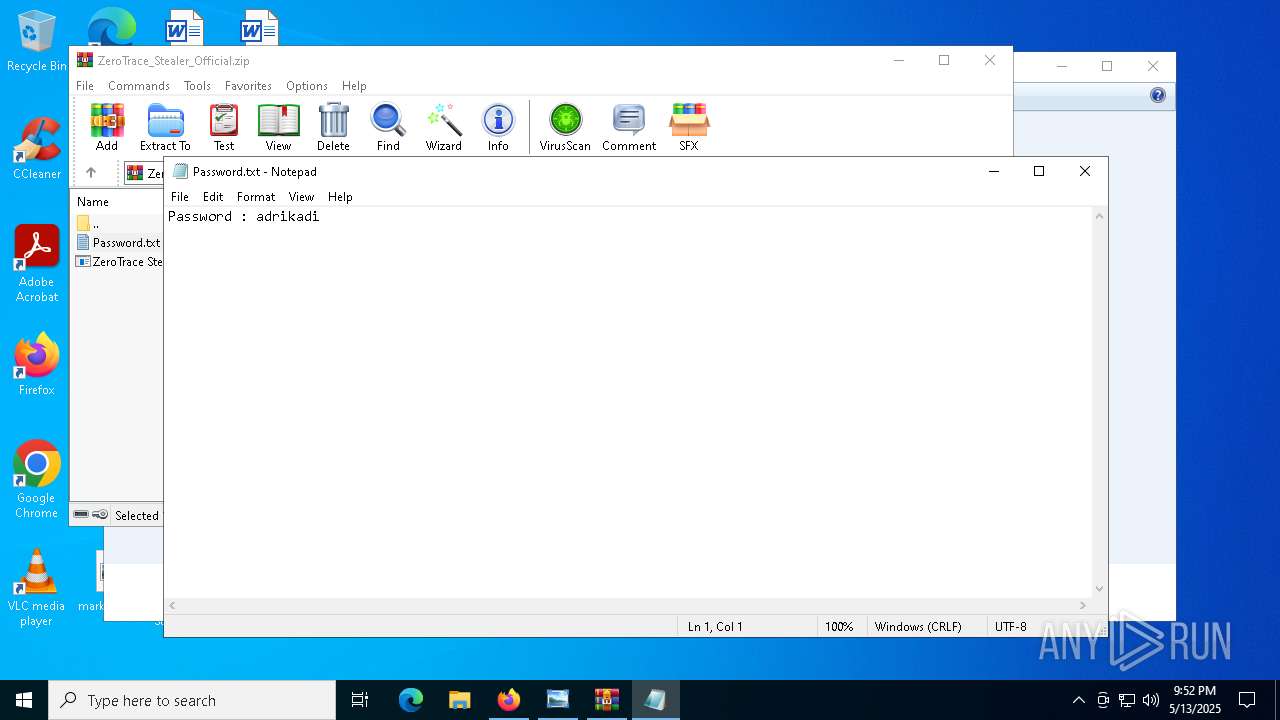
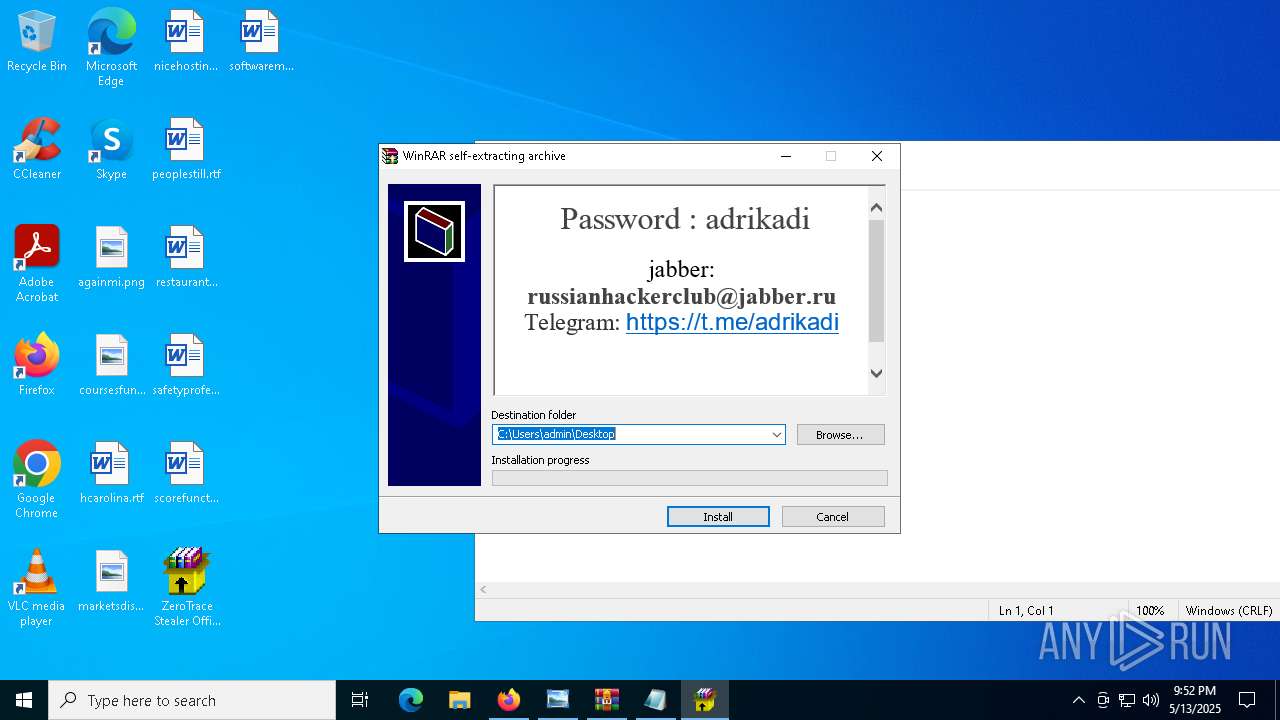
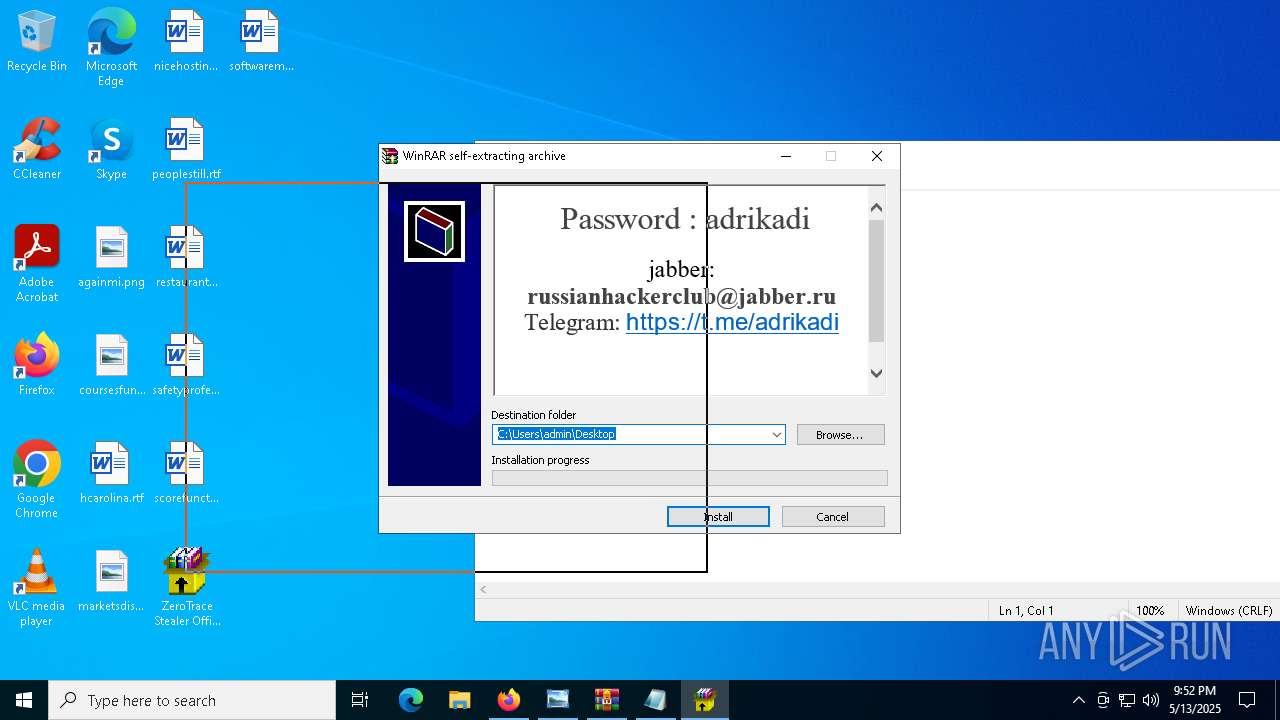
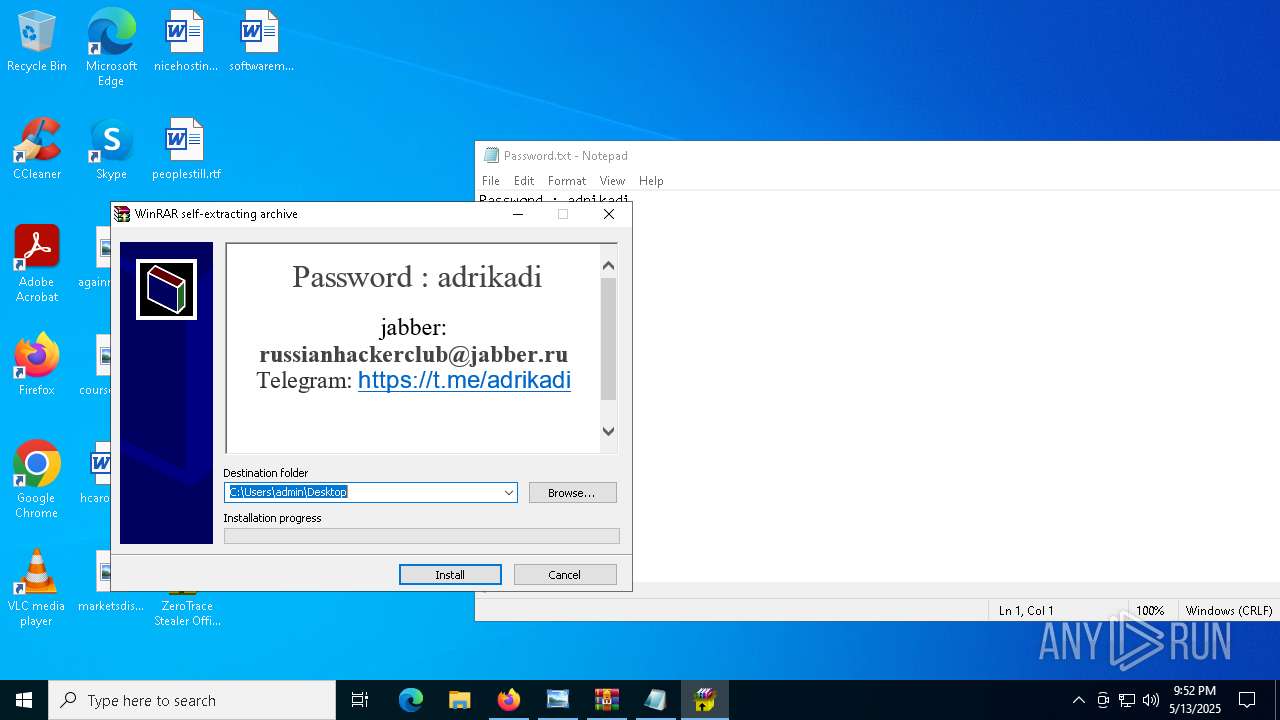
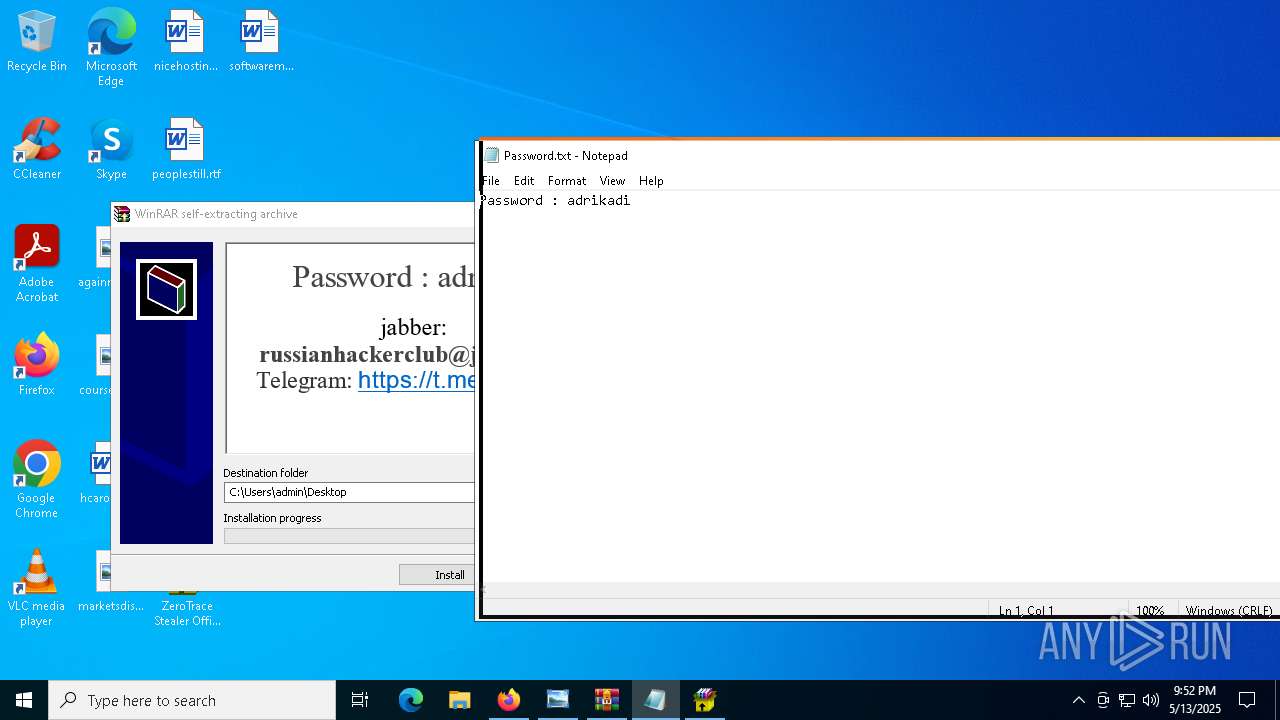
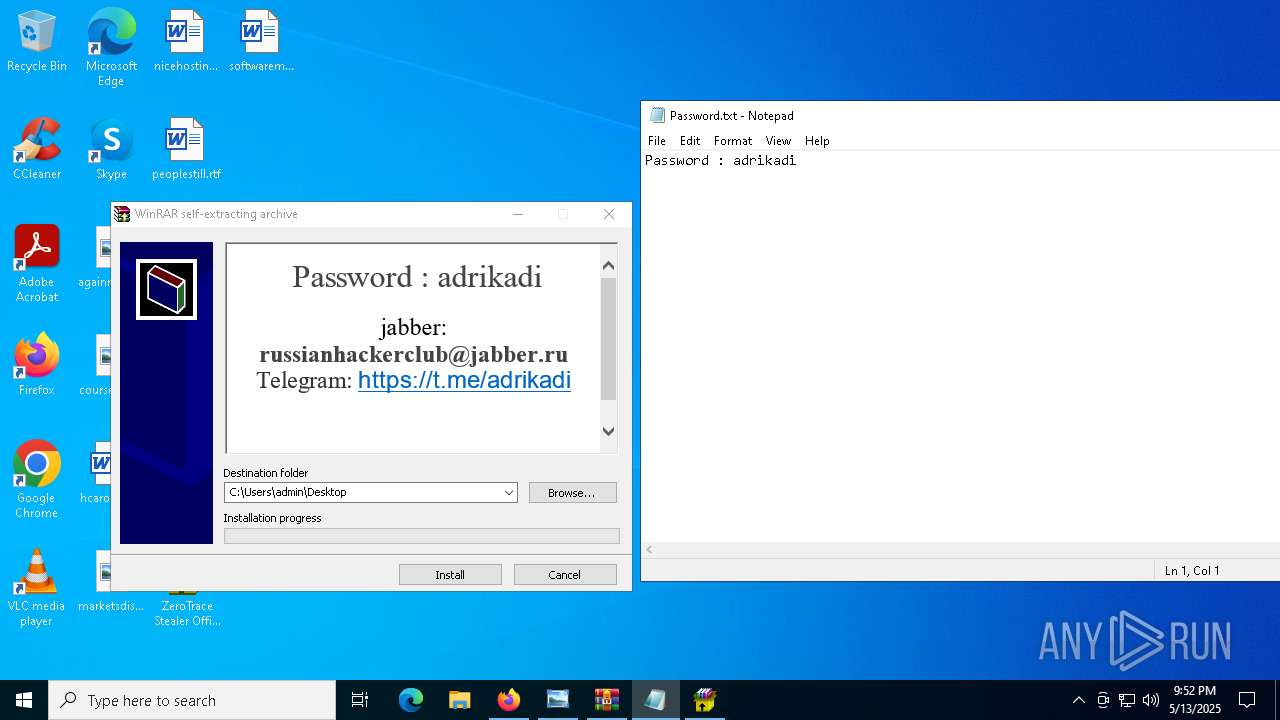
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 9064)
Reads Internet Explorer settings
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
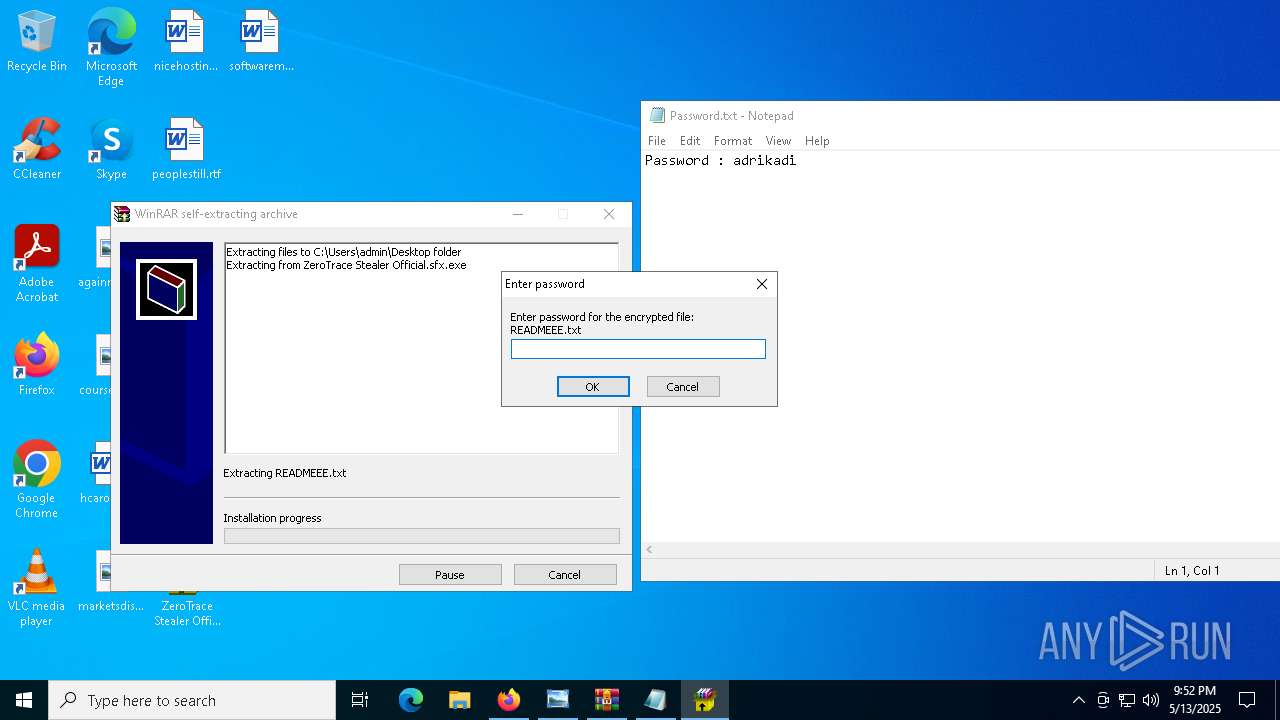
The process creates files with name similar to system file names
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
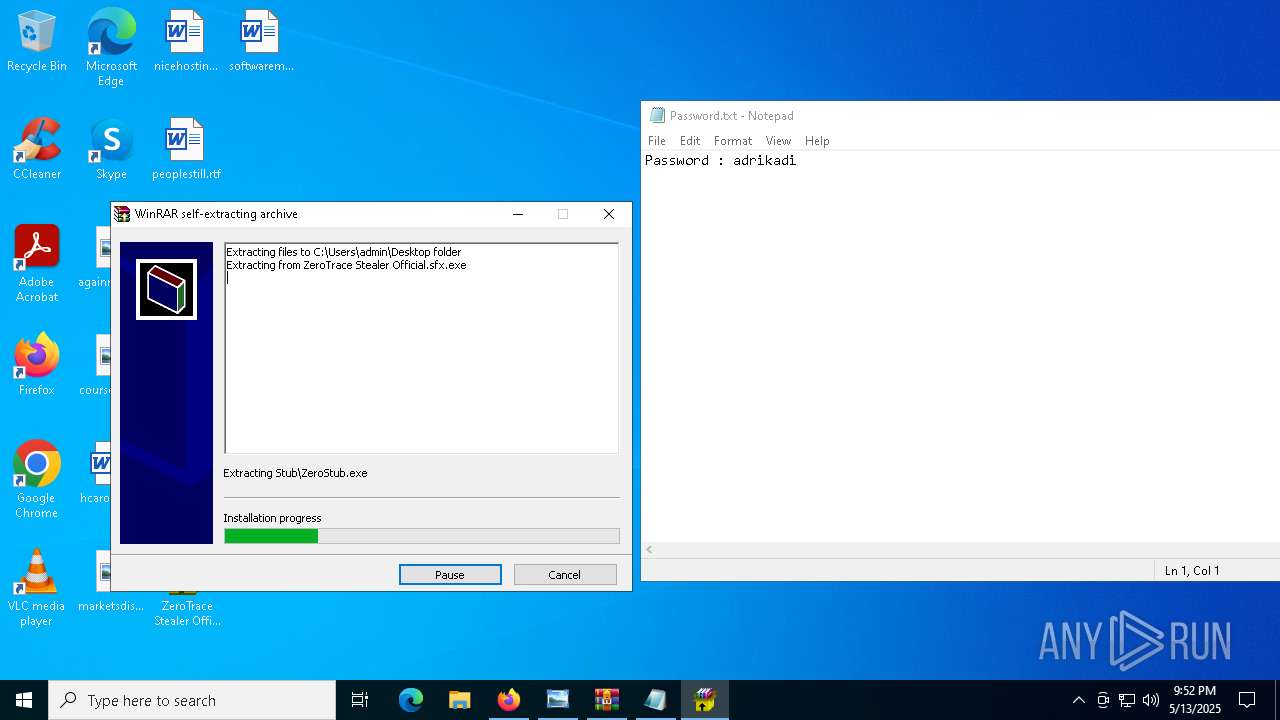
Executable content was dropped or overwritten
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
- crack.exe (PID: 7144)
- sass.exe (PID: 7156)
- svchost.exe (PID: 3364)
- conhost.exe (PID: 1280)
- InstallUtil.exe (PID: 6676)
- powershell.exe (PID: 8848)
- crack.exe (PID: 5384)
- powershell.exe (PID: 7700)
- crack.exe (PID: 10048)
Reads Microsoft Outlook installation path
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
There is functionality for taking screenshot (YARA)
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
- crack.exe (PID: 7144)
The process executes VB scripts
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
Process drops legitimate windows executable
- crack.exe (PID: 7144)
- InstallUtil.exe (PID: 6676)
- crack.exe (PID: 5384)
The process drops C-runtime libraries
- crack.exe (PID: 7144)
- crack.exe (PID: 5384)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5132)
- wscript.exe (PID: 4284)
- wscript.exe (PID: 2416)
- wscript.exe (PID: 8612)
- Update.exe (PID: 8236)
- svchost.exe (PID: 1240)
Process drops python dynamic module
- crack.exe (PID: 7144)
- crack.exe (PID: 5384)
Executing commands from a ".bat" file
- wscript.exe (PID: 5132)
- wscript.exe (PID: 4284)
- wscript.exe (PID: 2416)
- wscript.exe (PID: 8612)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 9124)
- cmd.exe (PID: 9116)
- cmd.exe (PID: 9128)
- cmd.exe (PID: 9172)
Downloads file from URI via Powershell
- powershell.exe (PID: 8848)
- powershell.exe (PID: 3124)
- powershell.exe (PID: 7700)
- powershell.exe (PID: 4012)
Drops a system driver (possible attempt to evade defenses)
- InstallUtil.exe (PID: 6676)
Crypto Currency Mining Activity Detected
- svchost.exe (PID: 2196)
Potential Corporate Privacy Violation
- OmegaEngine.exe (PID: 6960)
The executable file from the user directory is run by the CMD process
- clip.exe (PID: 9200)
- svchost.exe (PID: 1240)
Checks for external IP
- svchost.exe (PID: 2196)
- Update.exe (PID: 8236)
- svchost.exe (PID: 1240)
- crack.exe (PID: 10048)
- crack.exe (PID: 10144)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Update.exe (PID: 8236)
- svchost.exe (PID: 1240)
Found regular expressions for crypto-addresses (YARA)
- sass.exe (PID: 7156)
Starts application with an unusual extension
- cmd.exe (PID: 5352)
- cmd.exe (PID: 9616)
Starts itself from another location
- svchost.exe (PID: 3364)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 5352)
- cmd.exe (PID: 9616)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2288)
- cmd.exe (PID: 8064)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5352)
Application launched itself
- crack.exe (PID: 7144)
- crack.exe (PID: 5384)
The process connected to a server suspected of theft
- svchost.exe (PID: 1240)
INFO
Application launched itself
- firefox.exe (PID: 2100)
- firefox.exe (PID: 4980)
- chrome.exe (PID: 496)
Reads the software policy settings
- slui.exe (PID: 2140)
Manual execution by a user
- WinRAR.exe (PID: 9064)
- firefox.exe (PID: 2100)
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
- InstallUtil.exe (PID: 6676)
- crack.exe (PID: 5384)
Connects to unusual port
- firefox.exe (PID: 4980)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1272)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 9064)
Checks supported languages
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
Reads the computer name
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
Checks proxy server information
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
The sample compiled with english language support
- crack.exe (PID: 7144)
- InstallUtil.exe (PID: 6676)
- svchost.exe (PID: 3364)
- crack.exe (PID: 5384)
Process checks computer location settings
- ZeroTrace Stealer Official.sfx.exe (PID: 7632)
The sample compiled with japanese language support
- InstallUtil.exe (PID: 6676)
Changes the display of characters in the console
- cmd.exe (PID: 5352)
- cmd.exe (PID: 9616)
PyInstaller has been detected (YARA)
- crack.exe (PID: 7144)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF-EXIF JPEG Bitmap (38.4) |
|---|---|---|
| .jpg | | | JFIF JPEG bitmap (30.7) |
| .jpg | | | JPEG bitmap (23) |
| .mp3 | | | MP3 audio (7.6) |
EXIF
JFIF
| JFIFVersion: | 1.01 |
|---|---|
| ResolutionUnit: | inches |
| XResolution: | 300 |
| YResolution: | 300 |
EXIF
| Make: | NIKON CORPORATION |
|---|---|
| Model: | NIKON D700 |
| XResolution: | 300 |
| YResolution: | 300 |
| ResolutionUnit: | inches |
| Software: | Capture One 8 Windows |
| Artist: | - |
| Copyright: | - |
| ModifyDate: | 2018:02:26 09:07:58 |
| ExposureTime: | 1/160 |
| FNumber: | 9 |
| ExposureProgram: | Manual |
| ISO: | 400 |
| ExifVersion: | 0220 |
| DateTimeOriginal: | 2018:02:26 09:07:58 |
| CreateDate: | 2018:02:26 09:07:58 |
| ShutterSpeedValue: | 1/160 |
| ApertureValue: | 9 |
| ExposureCompensation: | +1/3 |
| MaxApertureValue: | 2.9 |
| MeteringMode: | Center-weighted average |
| LightSource: | Unknown |
| Flash: | No Flash |
| FocalLength: | 105.0 mm |
| UserComment: | - |
| ExifImageWidth: | 4256 |
| ExifImageHeight: | 2832 |
| SensingMethod: | One-chip color area |
| FileSource: | Digital Camera |
| SceneType: | Directly photographed |
| ExposureMode: | Manual |
| WhiteBalance: | Auto |
| Contrast: | Normal |
| Saturation: | Normal |
| Sharpness: | Normal |
| SubjectDistanceRange: | Unknown |
| GPSVersionID: | 2.2.0.0 |
| Compression: | JPEG (old-style) |
| ThumbnailOffset: | 932 |
| ThumbnailLength: | 2986 |
| ThumbnailImage: | (Binary data 2986 bytes, use -b option to extract) |
ICC_Profile
| ProfileCMMType: | Adobe Systems Inc. |
|---|---|
| ProfileVersion: | 2.1.0 |
| ProfileClass: | Display Device Profile |
| ColorSpaceData: | RGB |
| ProfileConnectionSpace: | XYZ |
| ProfileDateTime: | 2000:08:11 19:51:59 |
| ProfileFileSignature: | acsp |
| PrimaryPlatform: | Apple Computer Inc. |
| CMMFlags: | Not Embedded, Independent |
| DeviceManufacturer: | none |
| DeviceModel: | - |
| DeviceAttributes: | Reflective, Glossy, Positive, Color |
| RenderingIntent: | Perceptual |
| ConnectionSpaceIlluminant: | 0.9642 1 0.82491 |
| ProfileCreator: | Adobe Systems Inc. |
| ProfileID: | - |
| ProfileCopyright: | Copyright 2000 Adobe Systems Incorporated |
| ProfileDescription: | Adobe RGB (1998) |
| MediaWhitePoint: | 0.95045 1 1.08905 |
| MediaBlackPoint: | 0 0 0 |
| RedTRC: | (Binary data 14 bytes, use -b option to extract) |
| GreenTRC: | (Binary data 14 bytes, use -b option to extract) |
| BlueTRC: | (Binary data 14 bytes, use -b option to extract) |
| RedMatrixColumn: | 0.60974 0.31111 0.01947 |
| GreenMatrixColumn: | 0.20528 0.62567 0.06087 |
| BlueMatrixColumn: | 0.14919 0.06322 0.74457 |
IPTC
| CodedCharacterSet: | UTF8 |
|---|---|
| ApplicationRecordVersion: | 4 |
| Urgency: | 0 (reserved) |
| DateCreated: | 2018:02:26 |
| TimeCreated: | 09:07:58 |
| By-line: | |
| CopyrightNotice: |
XMP
| XMPToolkit: | XMP Core 4.4.0 |
|---|---|
| GPSVersionID: | 2.2.0.0 |
| ExifVersion: | 0221 |
| Urgency: | 0 (reserved) |
| DateCreated: | 2018:02:26 09:07:58 |
| LegacyIPTCDigest: | DC31EA5809B3825BE57C3B6B5323D279 |
| Rating: | - |
| Label: | None |
| SerialNumber: | 2029519 |
| LensInfo: | 105mm f/2.7999999153933 |
| Lens: | 105.0 mm f/2.8 |
| FlashCompensation: | - |
| Creator: | |
| Rights: |
Composite
| Aperture: | 9 |
|---|---|
| ImageSize: | 1920x1278 |
| Megapixels: | 2.5 |
| ShutterSpeed: | 1/160 |
| DateTimeCreated: | 2018:02:26 09:07:58 |
| FocalLength35efl: | 105.0 mm |
| LightValue: | 11.7 |
| LensID: | 105.0mm f/2.8 |
Total processes
209
Monitored processes
78
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --remote-debugging-port=9222 --user-data-dir="C:\Users\admin\AppData\Local\Google\Chrome\User Data" --profile-directory="Default" --headless --disable-gpu | C:\Program Files\Google\Chrome\Application\chrome.exe | — | Update.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1900 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1820 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {a3e98a2d-8833-4470-b115-84840b5fb22c} 4980 "\\.\pipe\gecko-crash-server-pipe.4980" 219a57ed010 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6004 -childID 8 -isForBrowser -prefsHandle 4816 -prefMapHandle 5300 -prefsLen 31324 -prefMapSize 244583 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {27af454f-aeac-44bc-9b38-5a542b1ccd1d} 4980 "\\.\pipe\gecko-crash-server-pipe.4980" 219ac4e0850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\AppData\Local\Temp\svchost.exe" | C:\Users\admin\AppData\Local\Temp\svchost.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ZeroTrace Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
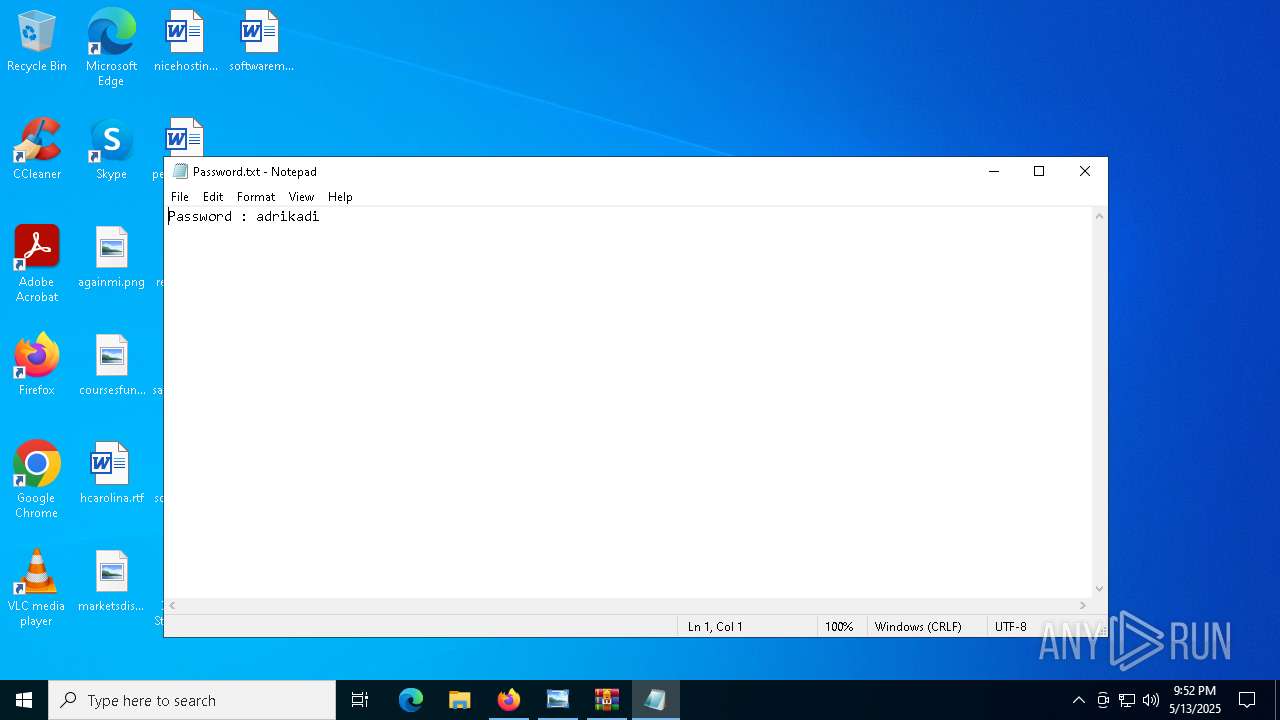
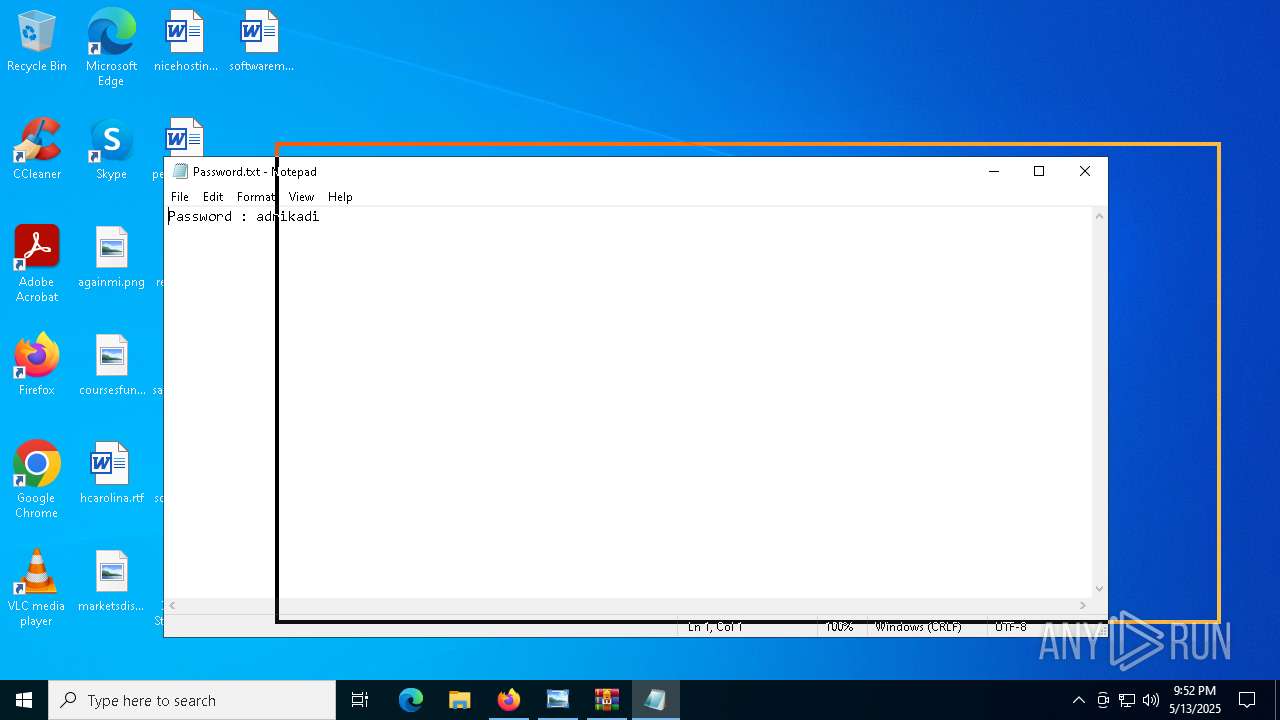
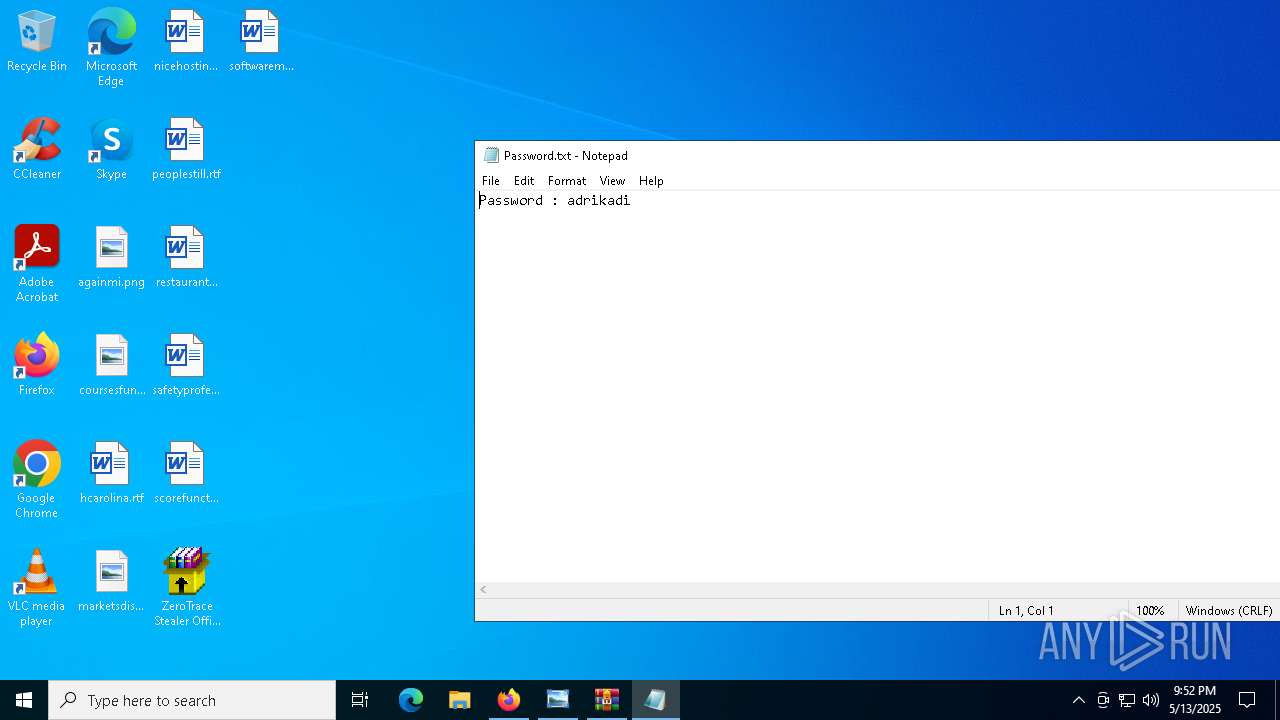
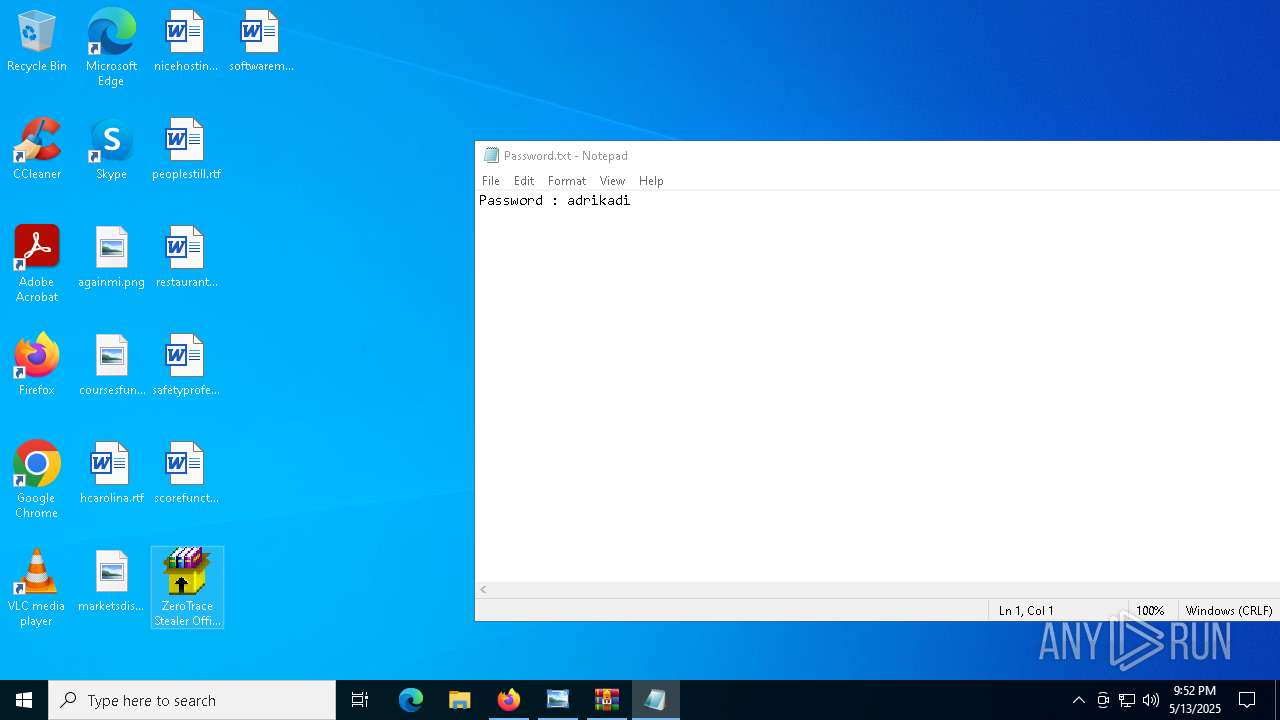
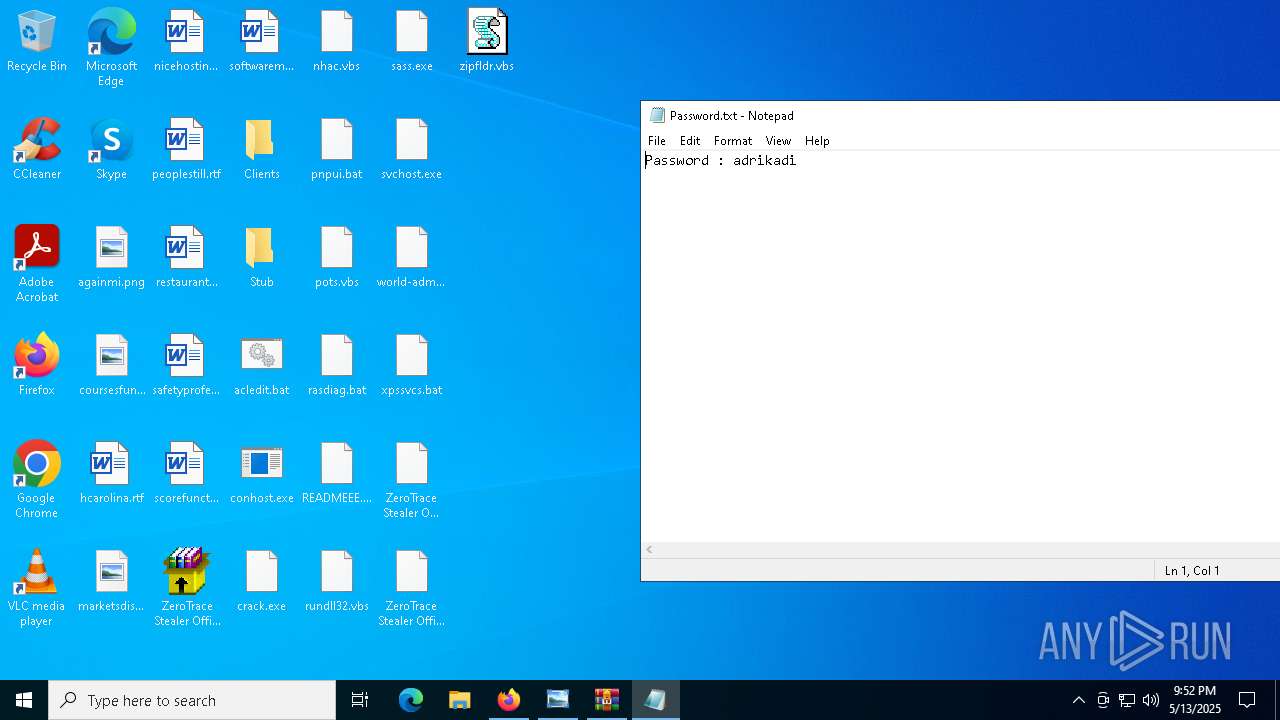
| 1272 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa9064.44182\Password.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\Users\admin\Desktop\conhost.exe" | C:\Users\admin\Desktop\conhost.exe | ZeroTrace Stealer Official.sfx.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: bilal Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1672 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2152 -parentBuildID 20240213221259 -prefsHandle 2136 -prefMapHandle 2132 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b0d2eec8-e2a0-4f60-b996-a186bd885765} 4980 "\\.\pipe\gecko-crash-server-pipe.4980" 2199877f310 socket | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2140 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
66 560
Read events
66 493
Write events
64
Delete events
3
Modification events
| (PID) Process: | (4980) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\ZeroTrace_Stealer_Official.zip | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (9064) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
Executable files
132
Suspicious files
229
Text files
1 918
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4980 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:A4191B41190530A651AC6B9A4D37A0AB | SHA256:ADC21BFE1746DC86AFDE30F310313F6A57D62E882C2095F3D35CAE10A07BA3E2 | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4980 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
57
TCP/UDP connections
177
DNS requests
226
Threats
33
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4980 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4980 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4980 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
4980 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
4980 | firefox.exe | POST | 200 | 2.22.242.121:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |