| File name: | CompPkgSrv.exe |
| Full analysis: | https://app.any.run/tasks/3cdd70e5-448c-4db8-86b7-21b095491ff4 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | October 25, 2023, 17:29:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 8429F941D3578C91936046063FC5C689 |
| SHA1: | 8D1AAC21C4955528D73F4B593F54B2BFFFADD3AC |
| SHA256: | 09E8EF80ADA96003239A1A10768ED3E09282AEA53BF21945F254B16261CDDA32 |
| SSDEEP: | 768:FcwtM6NqDuiP/tkiP9JqYcX5Pd1mswQk1+CSCv7mqb2n/pwH1oraTgbTWSG4V8Gj:F1iDBlGpPdhk0Gbbkwt8XHaG7p6VclN |
MALICIOUS
Drops the executable file immediately after the start
- CompPkgSrv.exe (PID: 556)
ASYNCRAT was detected
- Component Package Support Server.exe (PID: 3408)
ASYNCRAT has been detected (YARA)
- Component Package Support Server.exe (PID: 3408)
SUSPICIOUS
Executing commands from a ".bat" file
- CompPkgSrv.exe (PID: 556)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1040)
Starts CMD.EXE for commands execution
- CompPkgSrv.exe (PID: 556)
Reads settings of System Certificates
- Component Package Support Server.exe (PID: 3408)
Reads the Internet Settings
- Component Package Support Server.exe (PID: 3408)
Connects to unusual port
- Component Package Support Server.exe (PID: 3408)
INFO
Reads the computer name
- CompPkgSrv.exe (PID: 556)
- Component Package Support Server.exe (PID: 3408)
- wmpnscfg.exe (PID: 1560)
Checks supported languages
- CompPkgSrv.exe (PID: 556)
- Component Package Support Server.exe (PID: 3408)
- wmpnscfg.exe (PID: 1560)
Reads the machine GUID from the registry
- CompPkgSrv.exe (PID: 556)
- Component Package Support Server.exe (PID: 3408)
- wmpnscfg.exe (PID: 1560)
Create files in a temporary directory
- CompPkgSrv.exe (PID: 556)
- Component Package Support Server.exe (PID: 3408)
The executable file from the user directory is run by the CMD process
- Component Package Support Server.exe (PID: 3408)
Reads Environment values
- Component Package Support Server.exe (PID: 3408)
Manual execution by a user
- taskmgr.exe (PID: 2820)
- taskmgr.exe (PID: 3168)
- wmpnscfg.exe (PID: 1560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3408) Component Package Support Server.exe
BotnetDefault
Version1.0.7
Options
AutoRuntrue
MutexgaijinentertaimentMutex_qwqdanchun
InstallFolder%Temp%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIICMDCCAZmgAwIBAgIVAIE1Nn7FqVyzW277aZ10vNvIqqZPMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIzMDExMzE3MjQwMloXDTMzMTAyMjE3MjQwMlowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignatureaGIN1IOWT8iIVvQlEyKW3366A/CCqHMa2M3u7pkc+yR4AU7vl5j+Wf0ak44O4NZYfsfRhdxOrj8+Q2R0uro+uPARG0Rx3U7WMQ/pswsL3/192muAOL7Z4hZhlpTTDJmaqbS4S5wwGj9lZI702RjU150xPgJpVw17f/OecU1YkSE=
Keys
AES2dead4ca5a7ee020672535b3a394d3c7a6925588d5f9f03a54e3fbefcbf6db61
SaltDcRatByqwqdanchun
Credentials
Protocolpastebin
URLhttps://pastebin.com/raw/PWQ2PBCw
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| AssemblyVersion: | 4.25.4.0 |
|---|---|
| ProductVersion: | 4.25.4.0 |
| ProductName: | - |
| OriginalFileName: | - |
| LegalTrademarks: | - |
| LegalCopyright: | - |
| InternalName: | - |
| FileVersion: | 4.25.4.0 |
| FileDescription: | - |
| CompanyName: | - |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 4.25.4.0 |
| FileVersionNumber: | 4.25.4.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x10a0e |
| UninitializedDataSize: | - |
| InitializedDataSize: | 4096 |
| CodeSize: | 60416 |
| LinkerVersion: | 8 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable |
| TimeStamp: | 2022:01:12 03:47:42+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
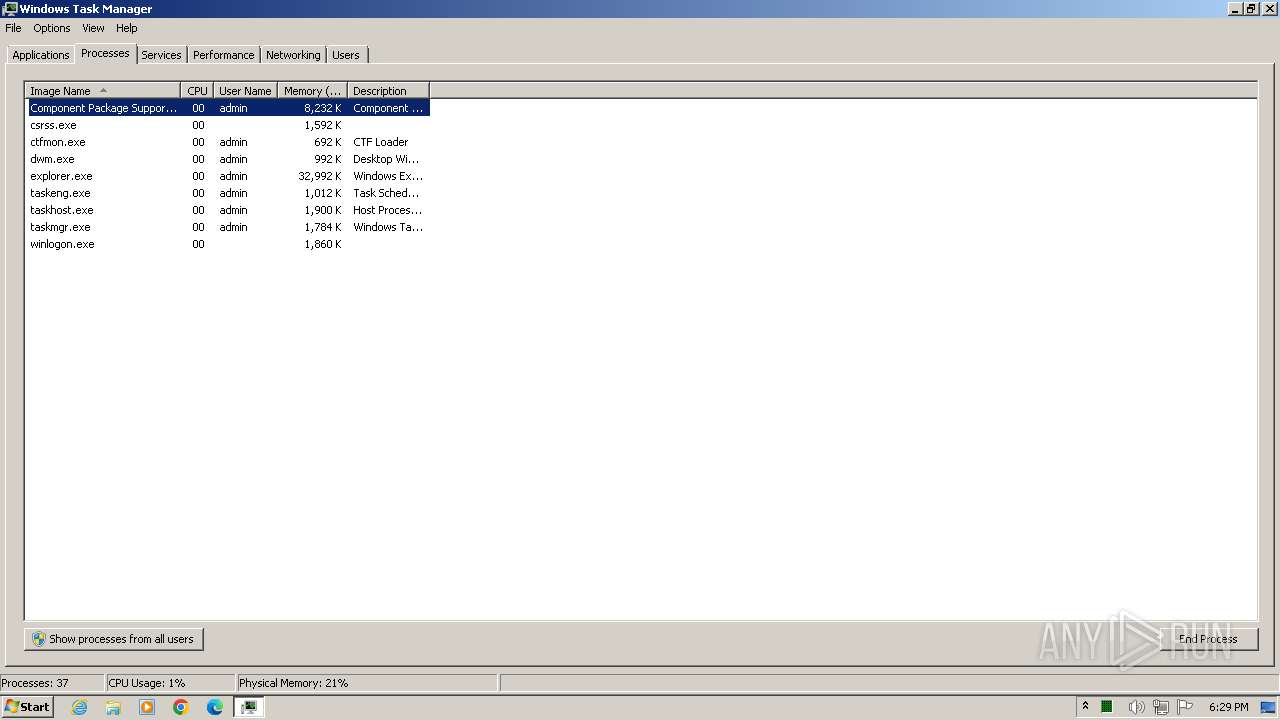
Total processes
44
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | "C:\Users\admin\AppData\Local\Temp\CompPkgSrv.exe" | C:\Users\admin\AppData\Local\Temp\CompPkgSrv.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 4.25.4.0 Modules
| |||||||||||||||
| 1040 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\tmpD59D.tmp.bat"" | C:\Windows\System32\cmd.exe | — | CompPkgSrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2820 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3168 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3408 | "C:\Users\admin\AppData\Local\Temp\Component Package Support Server.exe" | C:\Users\admin\AppData\Local\Temp\Component Package Support Server.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 4.25.4.0 Modules
AsyncRat(PID) Process(3408) Component Package Support Server.exe BotnetDefault Version1.0.7 Options AutoRuntrue MutexgaijinentertaimentMutex_qwqdanchun InstallFolder%Temp% BSoDfalse AntiVMfalse Certificates Cert1MIICMDCCAZmgAwIBAgIVAIE1Nn7FqVyzW277aZ10vNvIqqZPMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIzMDExMzE3MjQwMloXDTMzMTAyMjE3MjQwMlowEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A... Server_SignatureaGIN1IOWT8iIVvQlEyKW3366A/CCqHMa2M3u7pkc+yR4AU7vl5j+Wf0ak44O4NZYfsfRhdxOrj8+Q2R0uro+uPARG0Rx3U7WMQ/pswsL3/192muAOL7Z4hZhlpTTDJmaqbS4S5wwGj9lZI702RjU150xPgJpVw17f/OecU1YkSE= Keys AES2dead4ca5a7ee020672535b3a394d3c7a6925588d5f9f03a54e3fbefcbf6db61 SaltDcRatByqwqdanchun Credentials Protocolpastebin URLhttps://pastebin.com/raw/PWQ2PBCw | |||||||||||||||
| 4060 | timeout 3 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 118
Read events
5 087
Write events
28
Delete events
3
Modification events
| (PID) Process: | (556) CompPkgSrv.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3408) Component Package Support Server.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2820) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
| (PID) Process: | (2820) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E803000001000000010000004401000076000000DC0200005C0200000300000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000009C00000040000000210000004600000052000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000002000000010000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF00000000FFFFFFFF4F00000028000000500000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
| (PID) Process: | (1560) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{62FF88C3-1FED-4512-8EDD-4C83342E3BDD}\{35C103F6-2134-4DEC-A1F1-9020AE6CF1A0} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1560) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{62FF88C3-1FED-4512-8EDD-4C83342E3BDD} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1560) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{729C16D2-A791-4AC3-8C28-A143BD9BC8D7} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3168) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | UsrColumnSettings |
Value: 1C0C0000340400000000000050000000010000001D0C0000350400000000000023000000010000001E0C000036040000000000003C000000010000001F0C000039040000000000004E00000001000000200C000037040000000000004E00000001000000 | |||
| (PID) Process: | (3168) taskmgr.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 30030000E80300000100000001000000440100007600000058040000900200000000000001000000000000000000000001000000000000000100000000000000000000000200000004000000090000001D000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000009C00000040000000210000004600000052000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0000000002000000010000000300000004000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0500000000000000FFFFFFFF00000000020000000300000004000000FFFFFFFF00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000630060003C005A00FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF000000000000010000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF0400000000000000FFFFFFFF00000000FFFFFFFF4F00000028000000500000003400000050000000000000000100000002000000030000000400000000000000FFFFFFFF43000000000000000000000001000000 | |||
Executable files
1
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3408 | Component Package Support Server.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 556 | CompPkgSrv.exe | C:\Users\admin\AppData\Local\Temp\tmpD59D.tmp.bat | text | |
MD5:6DD3FCDC13959D4BA9160FED8A165EAF | SHA256:DC12432CCD296488CF1218A7BAADA1BD22FAC93BFE5CD379AA33D1A88CF2E670 | |||
| 556 | CompPkgSrv.exe | C:\Users\admin\AppData\Local\Temp\Component Package Support Server.exe | executable | |
MD5:8429F941D3578C91936046063FC5C689 | SHA256:09E8EF80ADA96003239A1A10768ED3E09282AEA53BF21945F254B16261CDDA32 | |||
| 3408 | Component Package Support Server.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:5FD137EF30A9A49D91AD77AB4A5E890C | SHA256:8CE4E293386DEC284C59013EAEDA211D5154609FCA20906D27EBDE0141A51500 | |||
| 3408 | Component Package Support Server.exe | C:\Users\admin\AppData\Local\Temp\CabF088.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 3408 | Component Package Support Server.exe | C:\Users\admin\AppData\Local\Temp\TarF089.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
3
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3408 | Component Package Support Server.exe | GET | 200 | 184.24.77.194:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?9dba6c8ec4d90c93 | unknown | compressed | 61.6 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3408 | Component Package Support Server.exe | 172.67.34.170:443 | pastebin.com | CLOUDFLARENET | US | unknown |
3408 | Component Package Support Server.exe | 3.124.67.191:12835 | 7.tcp.eu.ngrok.io | AMAZON-02 | DE | malicious |
3408 | Component Package Support Server.exe | 184.24.77.194:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| shared |
7.tcp.eu.ngrok.io |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Misc activity | ET INFO DNS Query to a *.ngrok domain (ngrok.io) |
3408 | Component Package Support Server.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
3408 | Component Package Support Server.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT) |
3408 | Component Package Support Server.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |