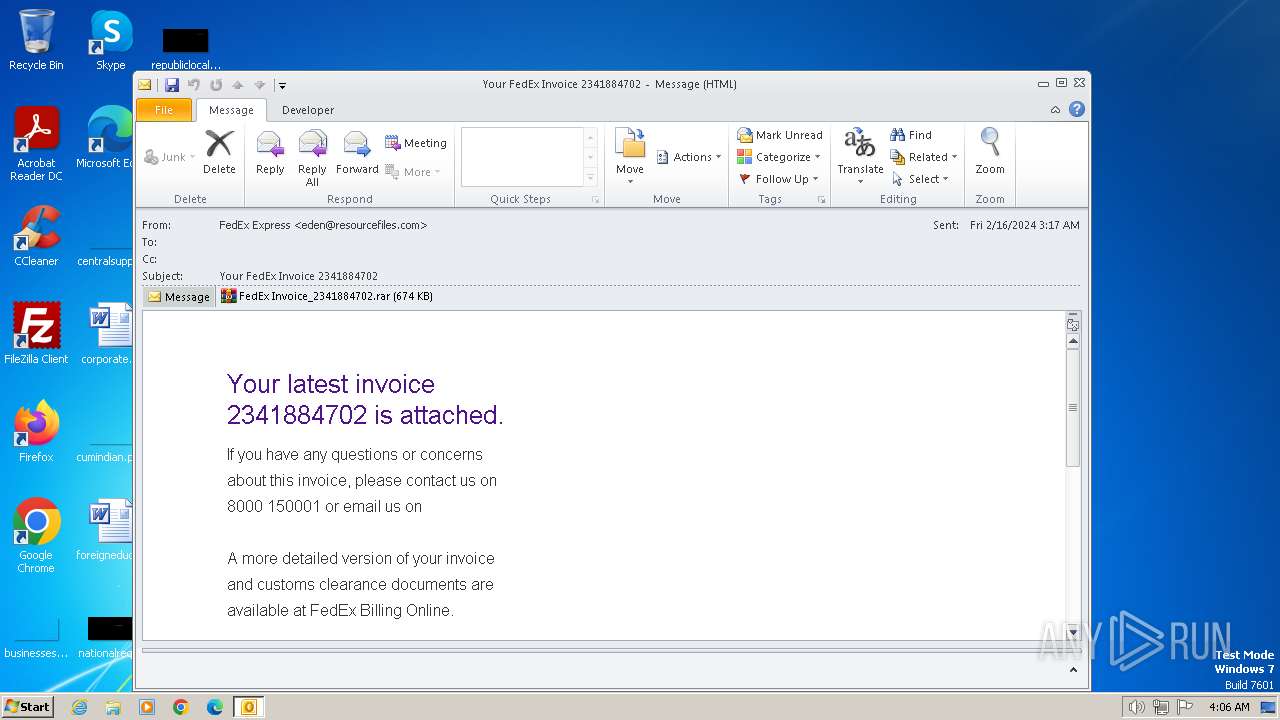
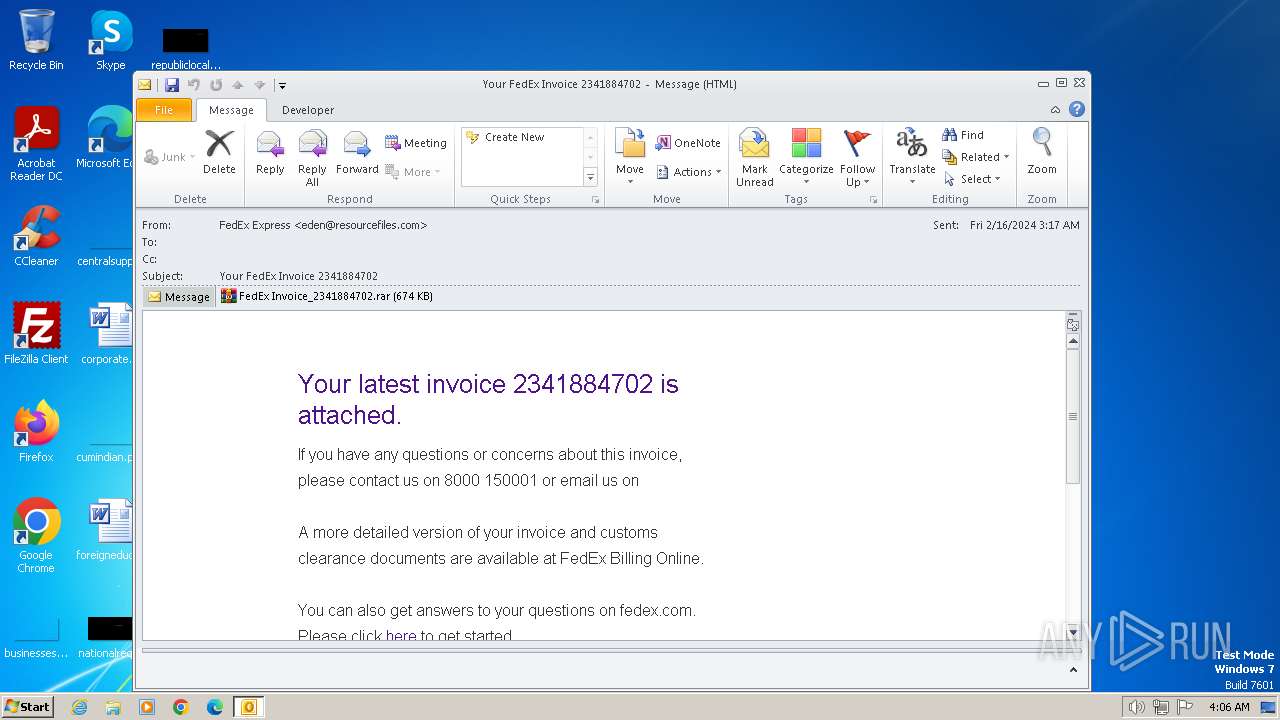
| File name: | Your FedEx Invoice 2341884702.eml |
| Full analysis: | https://app.any.run/tasks/27649b9e-3f2a-4f03-b5ed-79fa980e28a4 |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | February 16, 2024, 04:06:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | SMTP mail, ASCII text, with CRLF line terminators |
| MD5: | 17544D9CD687725A9C98054DC1529B63 |
| SHA1: | 2D3707884A9011FE5F168F415327AB959318B365 |
| SHA256: | 09C3E5BAD51D26A57EE79F5C072404EC58F4AA9742FA69A09927749B0B2A4D42 |
| SSDEEP: | 24576:7hx0JfH7XhTGItRAITBRffcW1KR+H5Miwkbz9/Oxf1bcnQE:+oI9RffcWH+UzFO/E |
MALICIOUS
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 3700)
FORMBOOK has been detected (YARA)
- proquota.exe (PID: 2148)
Steals credentials
- proquota.exe (PID: 2148)
FORMBOOK has been detected (SURICATA)
- explorer.exe (PID: 1164)
Actions looks like stealing of personal data
- proquota.exe (PID: 2148)
SUSPICIOUS
Process drops legitimate windows executable
- OUTLOOK.EXE (PID: 3700)
- WinRAR.exe (PID: 4000)
- explorer.exe (PID: 1164)
Reads Microsoft Outlook installation path
- explorer.exe (PID: 1164)
Starts a Microsoft application from unusual location
- FedEx Invoice_2341884702.exe (PID: 2364)
- FedEx Invoice_2341884702.exe (PID: 2168)
Application launched itself
- FedEx Invoice_2341884702.exe (PID: 2364)
Reads the Internet Settings
- proquota.exe (PID: 2148)
Loads DLL from Mozilla Firefox
- proquota.exe (PID: 2148)
Executable content was dropped or overwritten
- proquota.exe (PID: 2148)
Process drops SQLite DLL files
- proquota.exe (PID: 2148)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 1164)
- proquota.exe (PID: 2148)
Reads the Internet Settings
- explorer.exe (PID: 1164)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4000)
- explorer.exe (PID: 1164)
- proquota.exe (PID: 2148)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3700)
Manual execution by a user
- WinRAR.exe (PID: 4000)
- FedEx Invoice_2341884702.exe (PID: 2364)
- proquota.exe (PID: 2148)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4000)
Checks supported languages
- FedEx Invoice_2341884702.exe (PID: 2364)
- FedEx Invoice_2341884702.exe (PID: 2168)
Reads the machine GUID from the registry
- FedEx Invoice_2341884702.exe (PID: 2364)
Reads the computer name
- FedEx Invoice_2341884702.exe (PID: 2364)
Create files in a temporary directory
- proquota.exe (PID: 2148)
Checks proxy server information
- proquota.exe (PID: 2148)
Creates files or folders in the user directory
- proquota.exe (PID: 2148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 1) (100) |
|---|
Total processes
45
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1308 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | proquota.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 2148 | "C:\Windows\System32\proquota.exe" | C:\Windows\System32\proquota.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ProQuota Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\Desktop\FedEx Invoice_2341884702.exe" | C:\Users\admin\Desktop\FedEx Invoice_2341884702.exe | — | FedEx Invoice_2341884702.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .Netframwork Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 2364 | "C:\Users\admin\Desktop\FedEx Invoice_2341884702.exe" | C:\Users\admin\Desktop\FedEx Invoice_2341884702.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: .Netframwork Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 3700 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Your FedEx Invoice 2341884702.eml" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 4000 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\FedEx Invoice_2341884702.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
18 531
Read events
18 301
Write events
191
Delete events
39
Modification events
| (PID) Process: | (1164) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C47000000000200000000001066000000010000200000008ED9A1005EF4B952223AFF6842F43155FEF321F115A52192490F5580741942E6000000000E80000000020000200000008C49FB323AB369A23C0759A68E34BF298189611F5676B4328B8B309D70404C53300000008BB5AEDCE2B223DA441B4F5C0704498F36EEFB403A69215D06CD299C9C2950A7B7F4D2124F63C8C61B753103C3C3947B40000000C8978C004960C9EE6733254763FDE1DC473B238B3EADF44710EEC003753698BBAE5F64BE5BB2EBFF17AD885DE5C2B05CCB3033E4859E7477B1888118CF304F91 | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3700) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
13
Text files
4
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR376.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3700 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF0FD701DFB431E924.TMP | binary | |
MD5:72F5C05B7EA8DD6059BF59F50B22DF33 | SHA256:1DC0C8D7304C177AD0E74D3D2F1002EB773F4B180685A7DF6BBE75CCC24B0164 | |||
| 3700 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\NormalEmail.dotm | document | |
MD5:162384EF7EE6B25BFFD74083E98F9100 | SHA256:DD2C9808F4563F8D3E070B69A28B34246A4EDC4CE521CEC13C52DE89FD05A086 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\FedEx Invoice_2341884702.exe | executable | |
MD5:CAE74512F661579FC340B2203B159AF4 | SHA256:986B0BD9617FE3F2A0956754996C45298CDC3CDD2703EC837FA2D966028F5C8C | |||
| 3700 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\2CA65QMF\FedEx Invoice_2341884702.rar | compressed | |
MD5:E8C4664BBB11E2498AF51C485C1D42D7 | SHA256:557502A203D1F91B1AB609BB793B045DFC2067D64FEDEA60E8A3C0547AB817CB | |||
| 1164 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms | automaticdestinations-ms | |
MD5:44096159114E51AD87929D848691D703 | SHA256:C9742A8C5C5E576B6F243EAC955DB4B2D6D04C5AAE05231815E4D6FB341FF071 | |||
| 1164 | explorer.exe | C:\Users\admin\Desktop\FedEx Invoice_2341884702.rar | compressed | |
MD5:E8C4664BBB11E2498AF51C485C1D42D7 | SHA256:557502A203D1F91B1AB609BB793B045DFC2067D64FEDEA60E8A3C0547AB817CB | |||
| 3700 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~WRD0000.tmp | document | |
MD5:162384EF7EE6B25BFFD74083E98F9100 | SHA256:DD2C9808F4563F8D3E070B69A28B34246A4EDC4CE521CEC13C52DE89FD05A086 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
58
TCP/UDP connections
62
DNS requests
13
Threats
49
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1164 | explorer.exe | GET | — | 91.195.240.117:80 | http://www.chameleonboysclub.com/g3h4/?Ipf0rV=EzVemOi9F5PrbqjSpYgh2o3emqccsRGcNSzh5/VVBzkrCXFmlgzCOpgVwfN+WOTPdNatfdcL3ND0D5Oqnp7ifF/EtsRXIj+En/wIaK6ZfiOWmeYZPu2z+LNHtxTR&76yX=LbT0ClNp7r4xK4n0 | unknown | — | — | unknown |
2148 | proquota.exe | GET | 200 | 45.33.6.223:80 | http://www.sqlite.org/2019/sqlite-dll-win32-x86-3280000.zip | unknown | compressed | 472 Kb | unknown |
1164 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://www.barrettdigitalart.com/g3h4/ | unknown | html | 7.22 Kb | unknown |
1164 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://www.barrettdigitalart.com/g3h4/ | unknown | html | 7.23 Kb | unknown |
1164 | explorer.exe | POST | 200 | 206.233.249.197:80 | http://www.click-advertising.net/g3h4/ | unknown | html | 165 b | unknown |
1164 | explorer.exe | POST | — | 188.114.97.3:80 | http://www.barrettdigitalart.com/g3h4/ | unknown | — | — | unknown |
1164 | explorer.exe | GET | 301 | 188.114.97.3:80 | http://www.barrettdigitalart.com/g3h4/?Ipf0rV=XbLJlNGEtKCVcgAr+z1a4JWOLcBeMbPS0sz5DT5hAXrZxmNu3mZ/EdNlE8mf2m9oShAc/L1zcnw/QKhOWmb+aHwwvETZzrgBOqmw+wR53lSfmD8L7nu7vJbI/0by&76yX=LbT0ClNp7r4xK4n0 | unknown | — | — | unknown |
1164 | explorer.exe | POST | 200 | 206.233.249.197:80 | http://www.click-advertising.net/g3h4/ | unknown | html | 165 b | unknown |
1164 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://www.barrettdigitalart.com/g3h4/ | unknown | html | 7.22 Kb | unknown |
1164 | explorer.exe | POST | 404 | 188.114.97.3:80 | http://www.barrettdigitalart.com/g3h4/ | unknown | html | 7.22 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3700 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1164 | explorer.exe | 91.195.240.117:80 | www.chameleonboysclub.com | SEDO GmbH | DE | unknown |
2148 | proquota.exe | 45.33.6.223:80 | www.sqlite.org | Linode, LLC | US | unknown |
1164 | explorer.exe | 188.114.97.3:80 | www.barrettdigitalart.com | CLOUDFLARENET | NL | unknown |
1164 | explorer.exe | 206.233.249.197:80 | www.click-advertising.net | HONG KONG Megalayer Technology Co.,Limited | US | unknown |
1164 | explorer.exe | 37.9.175.196:80 | www.terazinvestment.com | WebSupport s.r.o. | SK | unknown |
1164 | explorer.exe | 15.235.86.83:80 | www.angelasboutiquesc.com | OVH SAS | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
www.justgoodsin.com |
| unknown |
www.chameleonboysclub.com |
| unknown |
www.sqlite.org |
| whitelisted |
www.barrettdigitalart.com |
| unknown |
www.click-advertising.net |
| unknown |
www.terazinvestment.com |
| unknown |
www.angelasboutiquesc.com |
| unknown |
www.severnii-port.pro |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |
1164 | explorer.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP header |