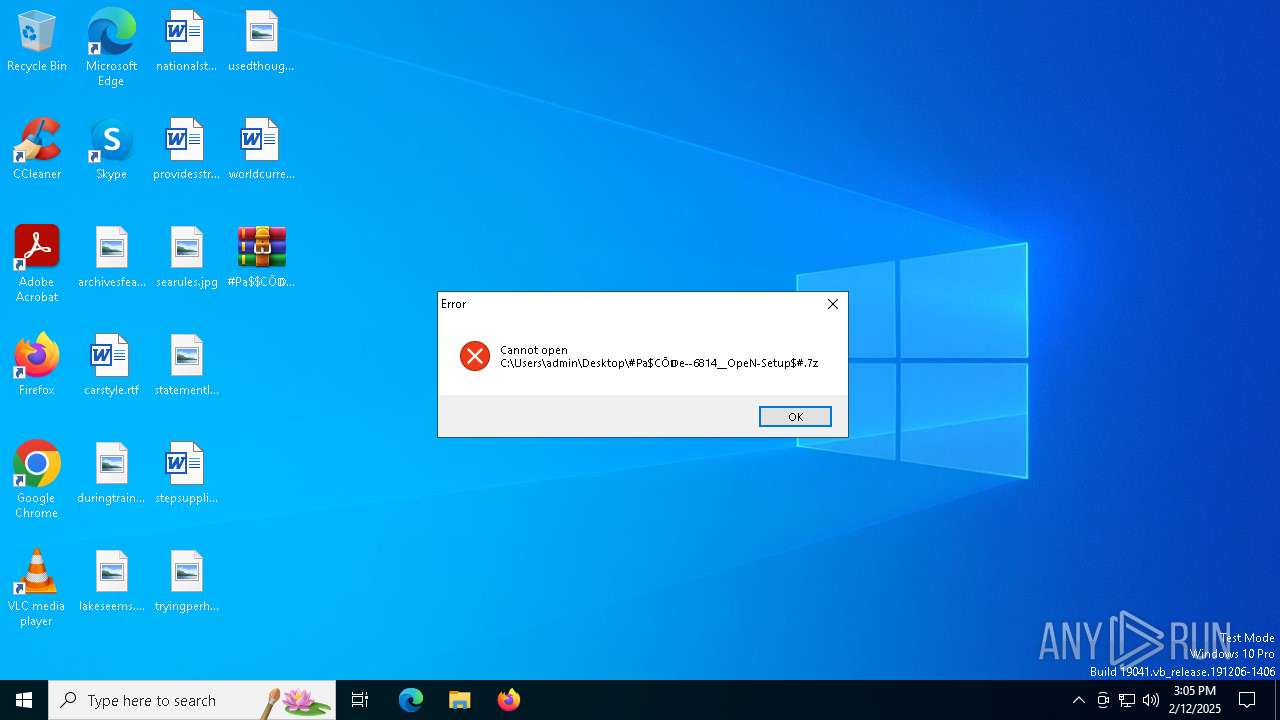
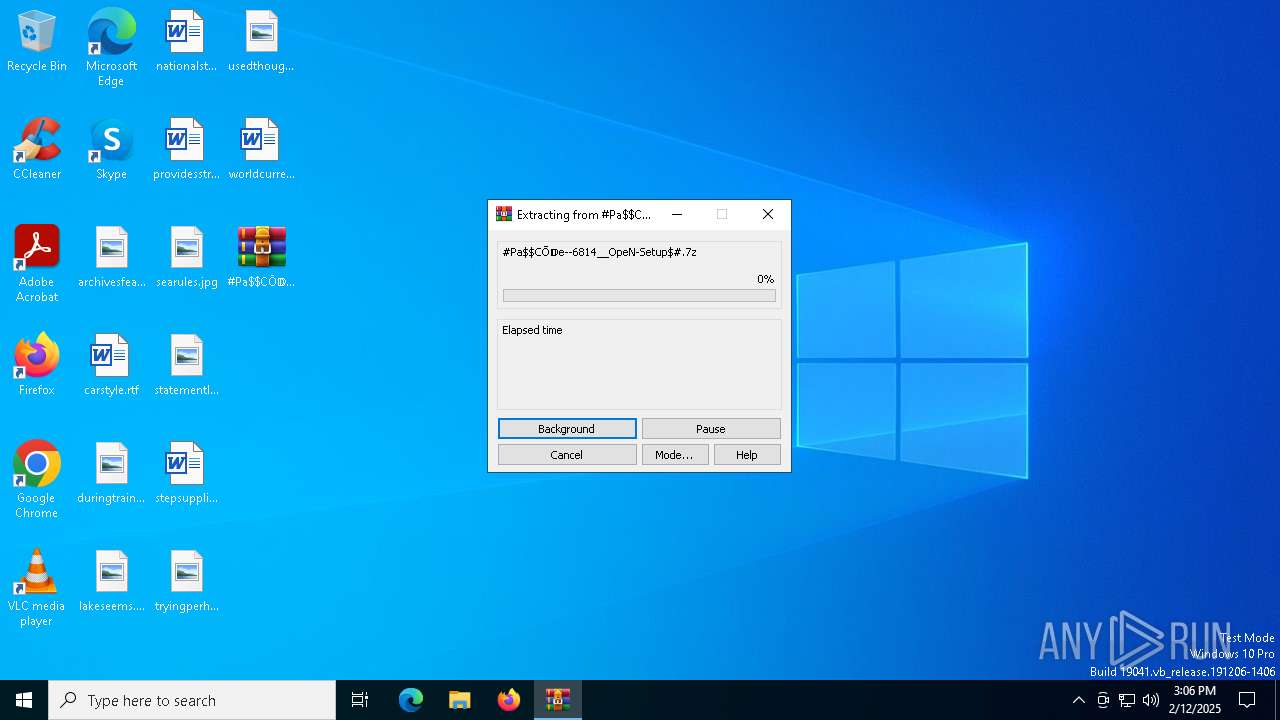
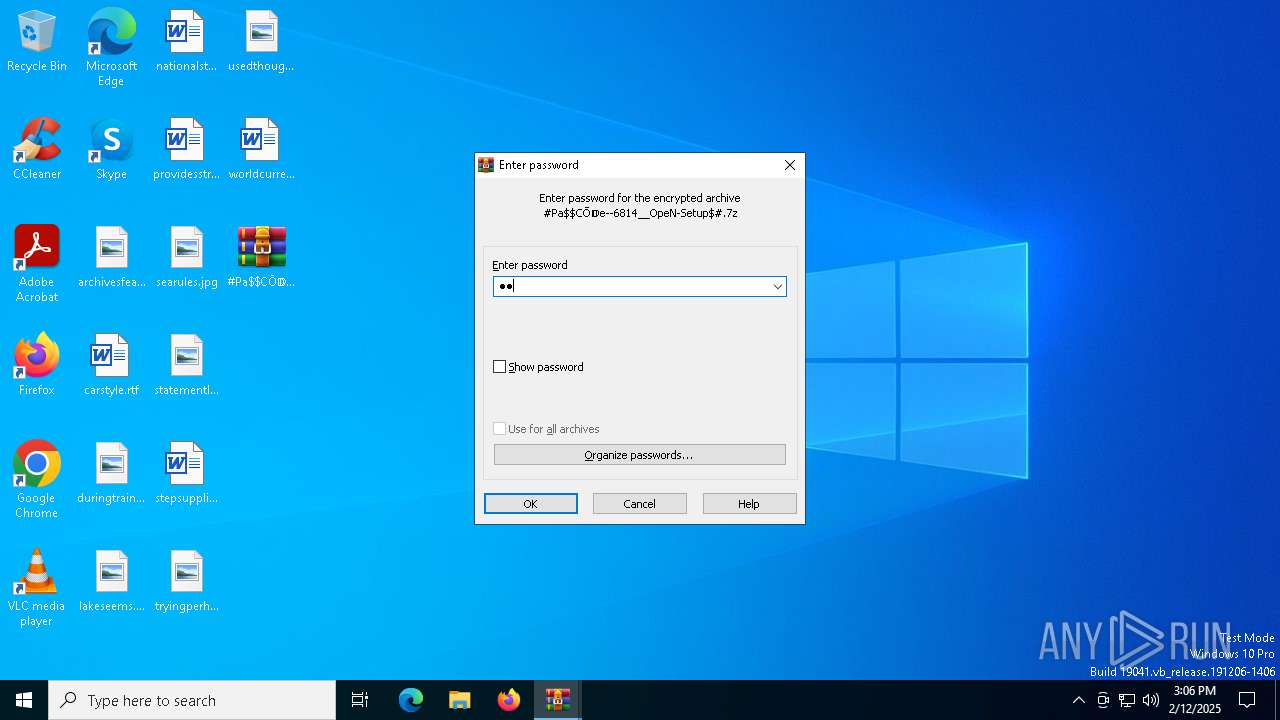
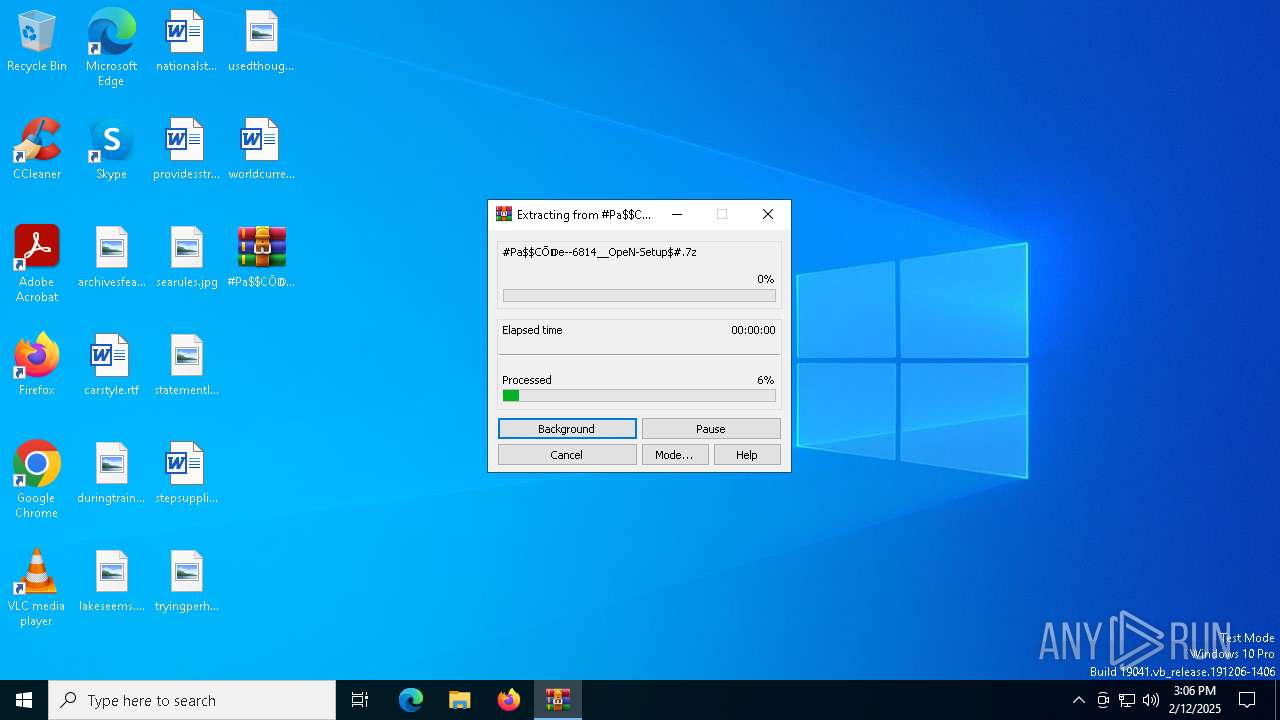
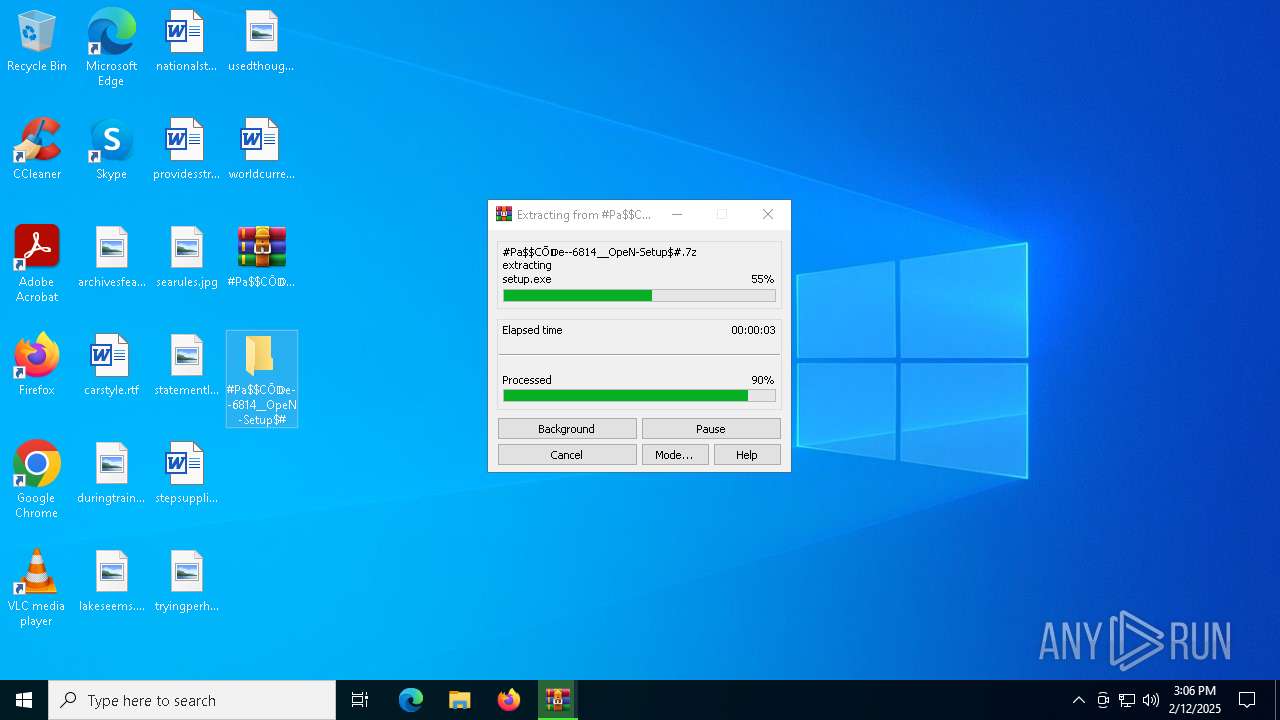
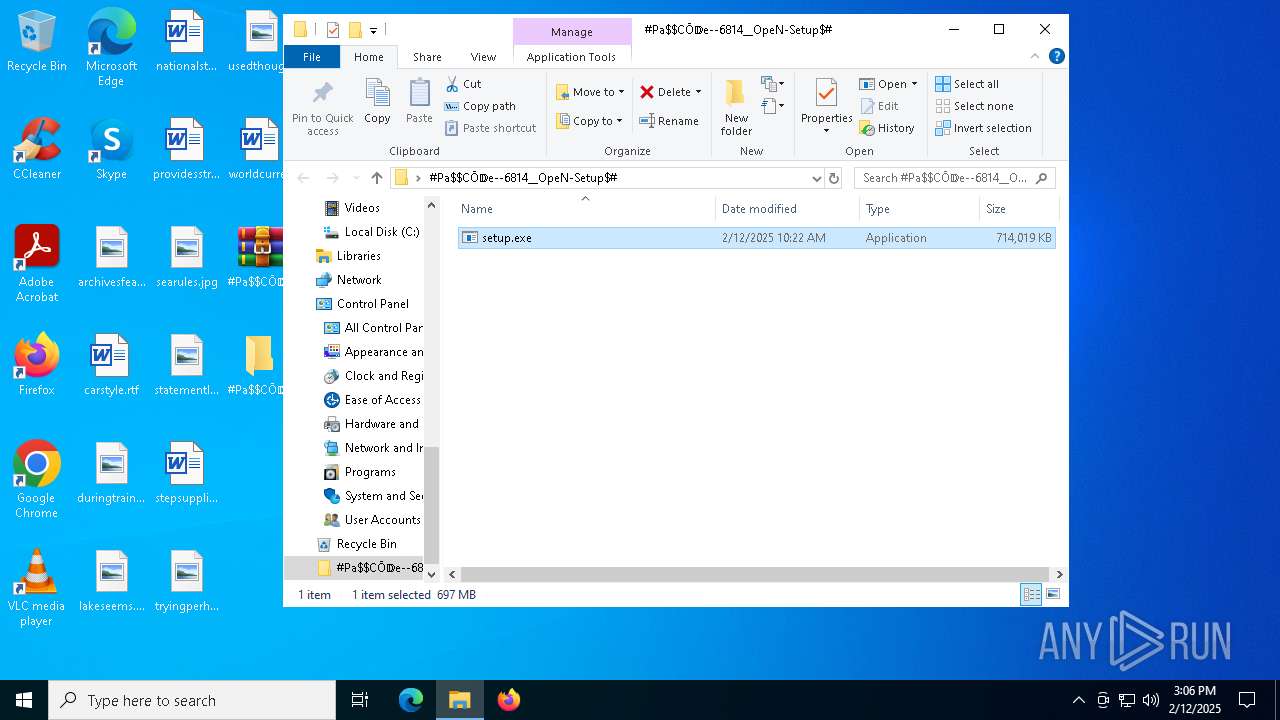
| File name: | #Pa$CŌ𝔻e--6814__OpeN-Setup$#.7z |
| Full analysis: | https://app.any.run/tasks/eca9466b-ccfb-4acb-9019-d90c1bfa9b35 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | February 12, 2025, 15:05:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7DD2B82801C77B3D607207533067F354 |
| SHA1: | FDA6C021200F5AF116C1F3591FAEE685C6851227 |
| SHA256: | 099E05C8887F9ED9F2A386680E74F70C88F84E27B1ABA24CC4076D462341E52F |
| SSDEEP: | 98304:KI/+W+X1oOvF3Ze5lWuuKkGJnHe2openTqcWxgdfupRpuQbXcfQYc9EkUjG29KVO:5WTHnoP |
MALICIOUS
Executing a file with an untrusted certificate
- setup.exe (PID: 2408)
LUMMA mutex has been found
- setup.exe (PID: 2408)
LUMMA has been detected (SURICATA)
- setup.exe (PID: 2408)
Steals credentials from Web Browsers
- setup.exe (PID: 2408)
Actions looks like stealing of personal data
- setup.exe (PID: 2408)
Known privilege escalation attack
- dllhost.exe (PID: 1904)
SUSPICIOUS
Searches for installed software
- setup.exe (PID: 2408)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 2408)
Process drops legitimate windows executable
- setup.exe (PID: 2408)
- vcpkgsrv.exe (PID: 2572)
Executable content was dropped or overwritten
- setup.exe (PID: 2408)
- vcpkgsrv.exe (PID: 2572)
Starts a Microsoft application from unusual location
- vcpkgsrv.exe (PID: 2572)
The process drops C-runtime libraries
- setup.exe (PID: 2408)
- vcpkgsrv.exe (PID: 2572)
Starts itself from another location
- vcpkgsrv.exe (PID: 2572)
INFO
Reads the computer name
- setup.exe (PID: 2408)
- vcpkgsrv.exe (PID: 2572)
- vcpkgsrv.exe (PID: 4952)
- vcpkgsrv.exe (PID: 6232)
Manual execution by a user
- setup.exe (PID: 2408)
- WinRAR.exe (PID: 6864)
Checks supported languages
- setup.exe (PID: 2408)
- vcpkgsrv.exe (PID: 2572)
- vcpkgsrv.exe (PID: 4952)
- vcpkgsrv.exe (PID: 6232)
Compiled with Borland Delphi (YARA)
- setup.exe (PID: 2408)
Reads the software policy settings
- setup.exe (PID: 2408)
- explorer.exe (PID: 6640)
The sample compiled with english language support
- setup.exe (PID: 2408)
- vcpkgsrv.exe (PID: 2572)
Creates files in the program directory
- vcpkgsrv.exe (PID: 2572)
Create files in a temporary directory
- vcpkgsrv.exe (PID: 4952)
- setup.exe (PID: 2408)
- choice.exe (PID: 488)
- vcpkgsrv.exe (PID: 6232)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 1904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
141
Monitored processes
13
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | C:\WINDOWS\SysWOW64\choice.exe | C:\Windows\SysWOW64\choice.exe | — | vcpkgsrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | C:\WINDOWS\SysWOW64\choice.exe | C:\Windows\SysWOW64\choice.exe | — | vcpkgsrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | choice.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1904 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2408 | "C:\Users\admin\Desktop\#Pa$CŌ𝔻e--6814__OpeN-Setup$#\setup.exe" | C:\Users\admin\Desktop\#Pa$CŌ𝔻e--6814__OpeN-Setup$#\setup.exe | explorer.exe | ||||||||||||
User: admin Company: Hagel Technologies Ltd. Integrity Level: MEDIUM Description: DU Meter Service Exit code: 0 Version: 8.10 Modules
| |||||||||||||||
| 2572 | "C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\vcpkgsrv.exe" | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\vcpkgsrv.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) Visual C++ Package Server Exit code: 0 Version: 17.0.34202.158 built by: D17.7 Modules
| |||||||||||||||
| 4952 | C:\ProgramData\FNPLicensingService\vcpkgsrv.exe | C:\ProgramData\FNPLicensingService\vcpkgsrv.exe | — | vcpkgsrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) Visual C++ Package Server Exit code: 1 Version: 17.0.34202.158 built by: D17.7 Modules
| |||||||||||||||
| 5488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | choice.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6232 | "C:\ProgramData\FNPLicensingService\vcpkgsrv.exe" | C:\ProgramData\FNPLicensingService\vcpkgsrv.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft (R) Visual C++ Package Server Exit code: 1 Version: 17.0.34202.158 built by: D17.7 Modules
| |||||||||||||||
| 6420 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\#Pa$CŌ𝔻e--6814__OpeN-Setup$#.7z | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1 Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 889
Read events
6 859
Write events
17
Delete events
13
Modification events
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F0000000000000000000000000000000000000000000AE02060000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F00000000000000000000000000000000000000000000C0304000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6420) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F00000000000000000000000000000000000000000001A0305000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
Executable files
23
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\airstrip.eps | — | |
MD5:— | SHA256:— | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\cpfe.dll | — | |
MD5:— | SHA256:— | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\dbxfb.dll | executable | |
MD5:FBE21C0E2FD44E82896F6274FE7ACAEC | SHA256:BD31280409672D3FE50F60421882CE69EDBDE8F6E47DB668BC6D55A3D0A74A73 | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\vcl290.bpl | executable | |
MD5:3E043A4959D3E68162B06DCDB758FAB0 | SHA256:92BA4C51E0F68158FCC6FE67CE587AC0C2B3E28DB5CA6E19C5A297E872EC1963 | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\dbxase.dll | executable | |
MD5:019F61F5BF96F5B80A846EFEF7FFE931 | SHA256:E136DB925A11447A2E0444D45866471A4BC54B03B403B912663054AA17BE469B | |||
| 2572 | vcpkgsrv.exe | C:\ProgramData\FNPLicensingService\cpfe.dll | — | |
MD5:— | SHA256:— | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\vclimg290.bpl | executable | |
MD5:8DA1CC2F7FEE2B1440CA4C2B48D7F991 | SHA256:68F84CCC92C047B8215713A97CA6E63BACD745D2A2636A46269D34F1F1F1CB8A | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\vcldbx290.bpl | executable | |
MD5:11B0604585D58DE18F7FD7A21C7CAE7D | SHA256:673889260535E326D342A7CED35E5F341A15544FBFEA13769D2F88816D2174BF | |||
| 2408 | setup.exe | C:\Users\admin\AppData\Local\Temp\GUPG6K52LI0NHPGTZT5WLX\dbxmss.dll | executable | |
MD5:9716A6A99A7FF149A94F8F10400E9D49 | SHA256:3BC85B74BA8B29AF22FAA6F66B1C33A5C3ED904868C9608A91AD079A1D6636FC | |||
| 2572 | vcpkgsrv.exe | C:\ProgramData\FNPLicensingService\airstrip.eps | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
42
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.18.244.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.20.102.93:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5892 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5892 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6748 | backgroundTaskHost.exe | GET | 200 | 2.16.38.4:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.18.244.211:80 | crl.microsoft.com | Akamai International B.V. | FR | whitelisted |
— | — | 95.101.136.201:443 | — | Akamai International B.V. | GB | unknown |
4712 | MoUsoCoreWorker.exe | 2.20.102.93:80 | www.microsoft.com | RCS & RDS | RO | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 95.101.136.201:443 | — | Akamai International B.V. | GB | unknown |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.16.38.4:80 | ocsp.digicert.com | AKAMAI-AS | ES | whitelisted |
1176 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2408 | setup.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |