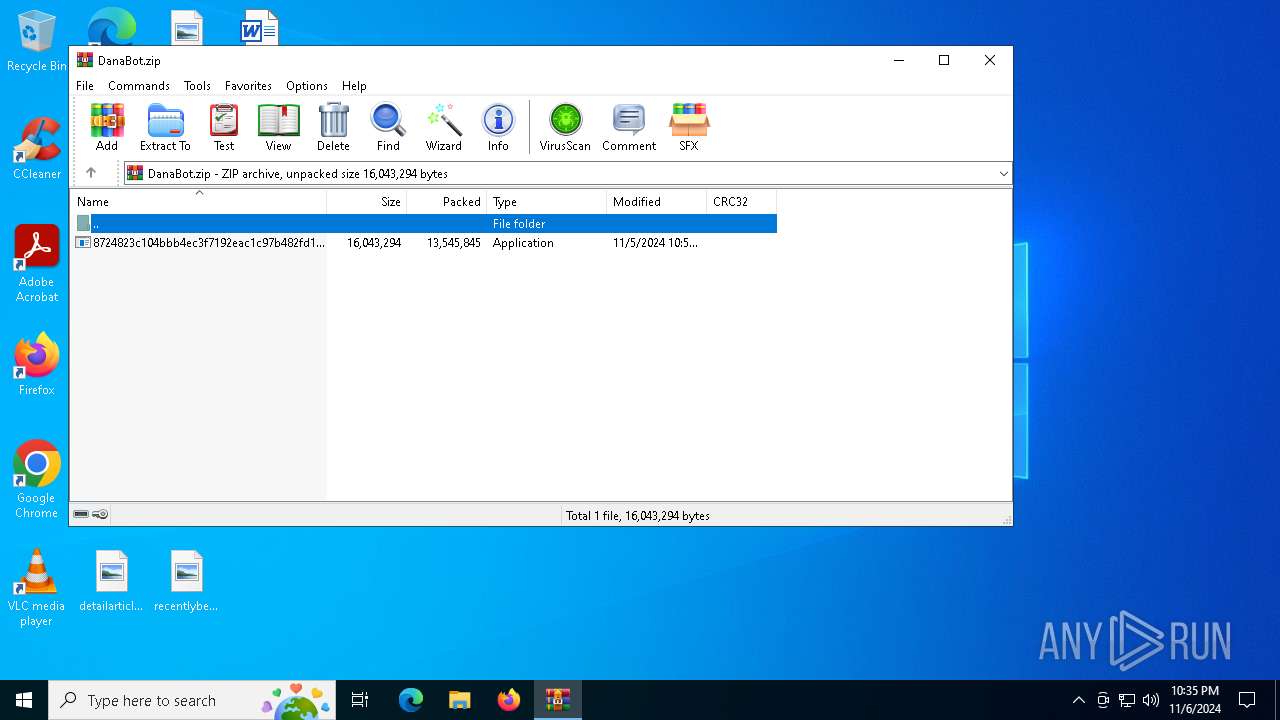
| File name: | DanaBot.zip |
| Full analysis: | https://app.any.run/tasks/28b6f968-e9c5-4d6e-b95f-ffa5a0522c3b |
| Verdict: | Malicious activity |
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | November 06, 2024, 22:35:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
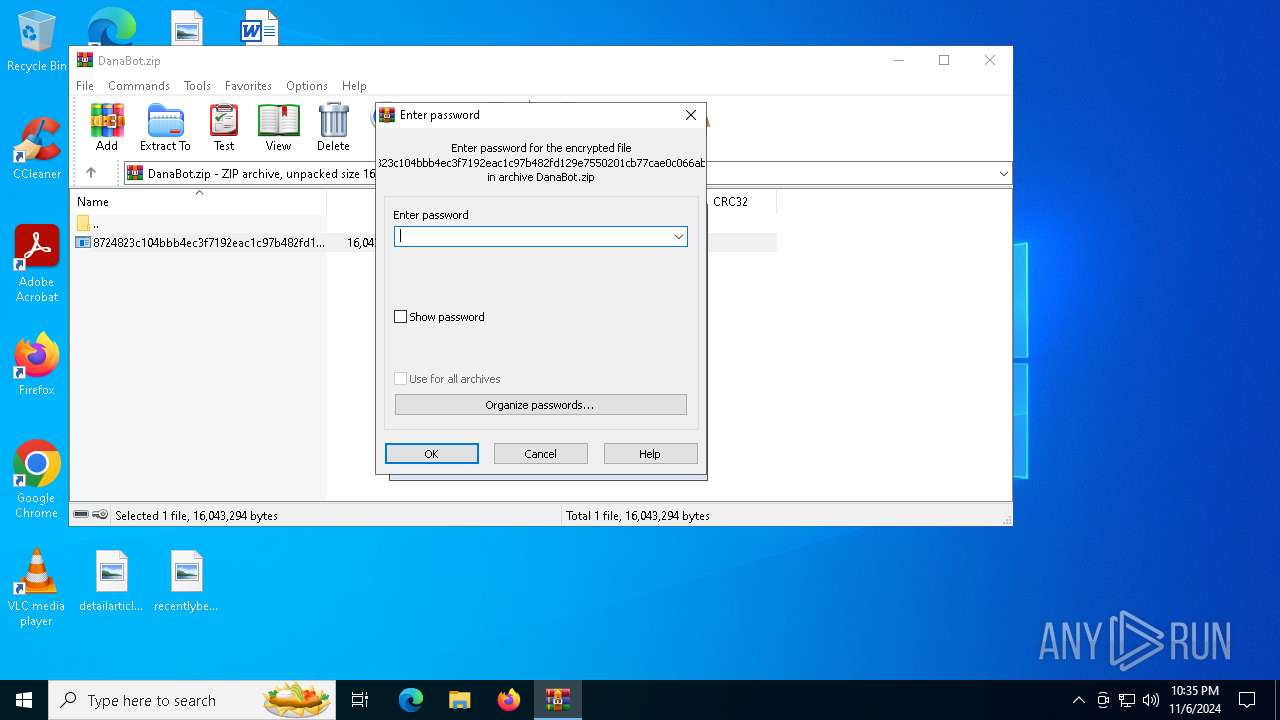
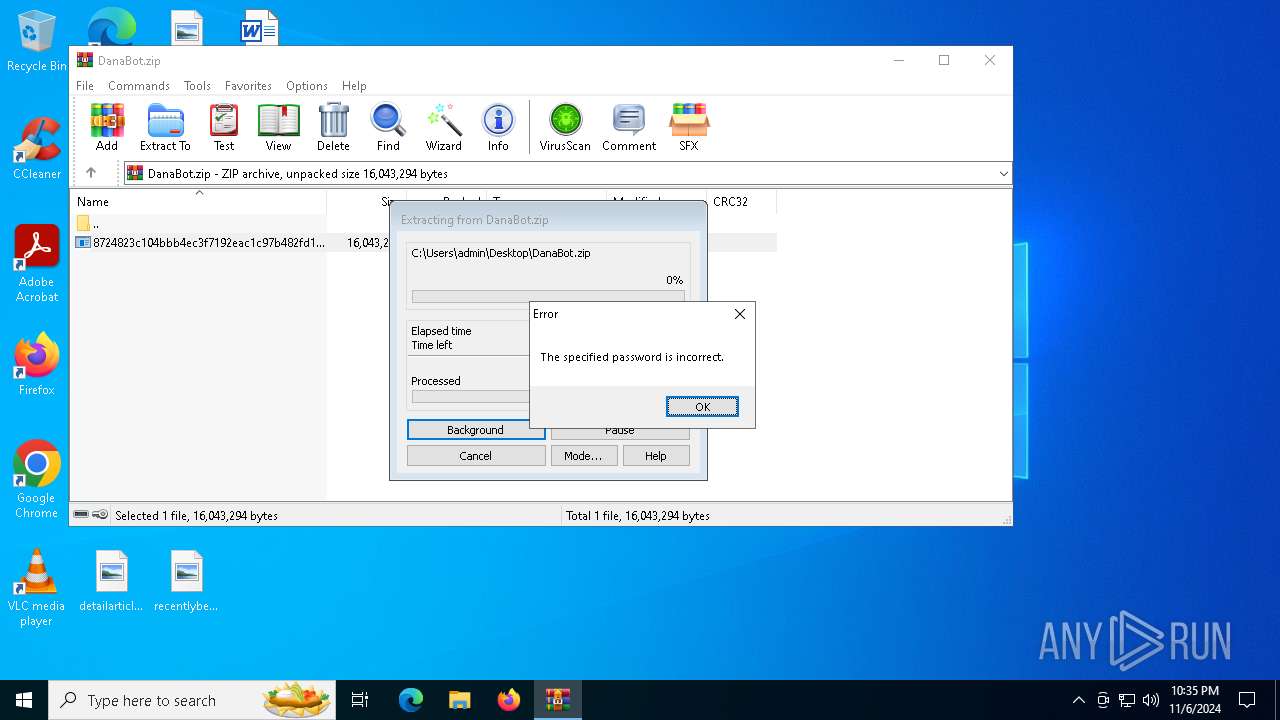
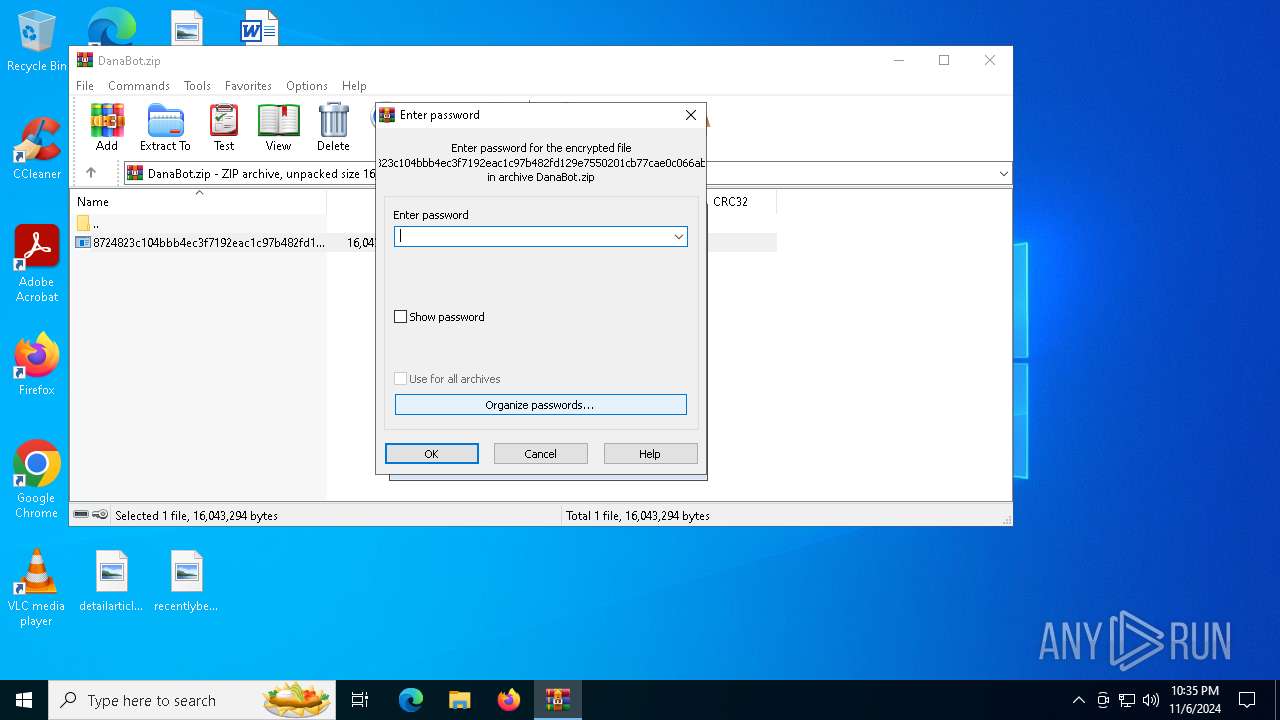
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 9279E7EF1039CF81206E051A90BD9F8A |
| SHA1: | 921C9ED9291919B4C40EA892F3B9500AB29FD753 |
| SHA256: | 0967D24212F64D4A5E5496E942E214A361D7077D3624489557EA6BDE78CEC89C |
| SSDEEP: | 98304:nzUekhfvrpceiovb8ll5hBwxrx1qSuSdmfCIgovMVJp179BrRAxOm6a01ApX8R3F:/LWYWvj6+y6itahFBkk742TFdz |
MALICIOUS
DANABOT has been detected (YARA)
- EasePaint.exe (PID: 1500)
DANABOT has been detected (SURICATA)
- EasePaint.exe (PID: 1500)
- EasePaint.exe (PID: 6460)
SUSPICIOUS
Process drops legitimate windows executable
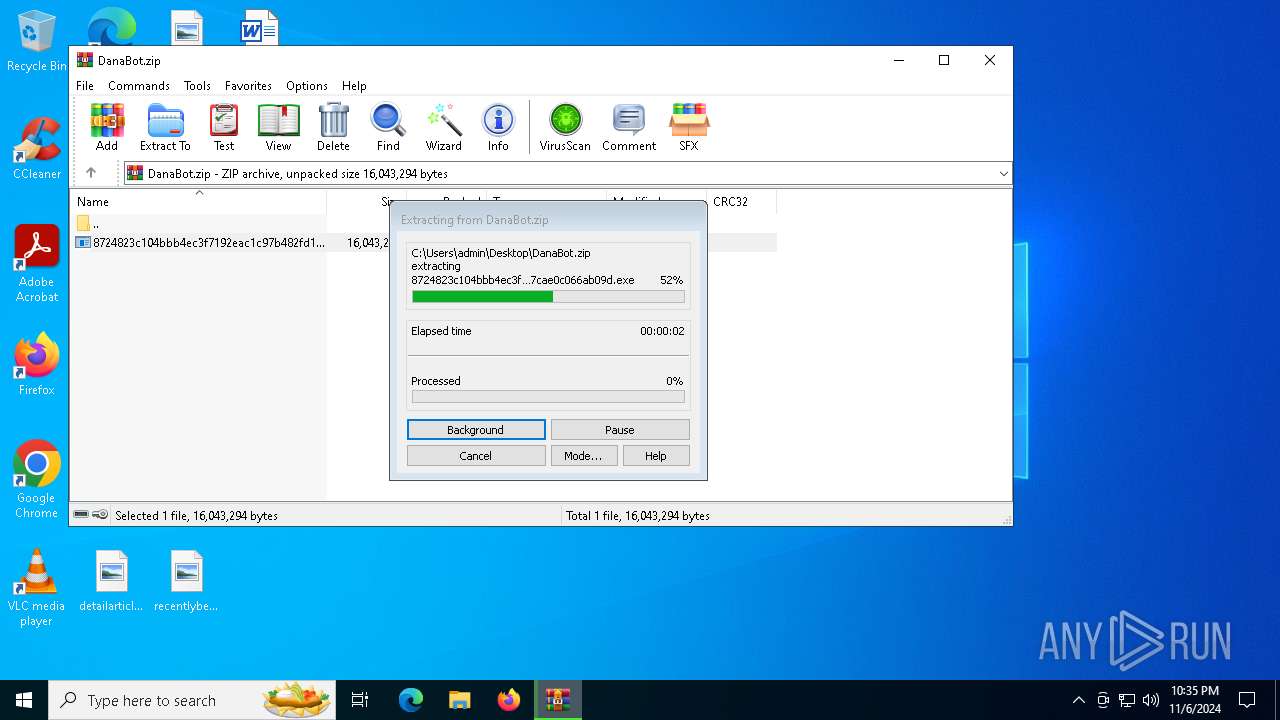
- 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe (PID: 6964)
- 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe (PID: 6184)
Executable content was dropped or overwritten
- 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe (PID: 6184)
- 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe (PID: 6964)
Application launched itself
- EasePaint.exe (PID: 1500)
- 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe (PID: 6184)
Executes application which crashes
- EasePaint.exe (PID: 1500)
Contacting a server suspected of hosting an CnC
- EasePaint.exe (PID: 1500)
- EasePaint.exe (PID: 6460)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5616)
- msiexec.exe (PID: 5372)
The process uses the downloaded file
- WinRAR.exe (PID: 5616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:11:05 22:56:22 |
| ZipCRC: | 0x72ffa84d |
| ZipCompressedSize: | 13545845 |
| ZipUncompressedSize: | 16043294 |
| ZipFileName: | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe |
Total processes
148
Monitored processes
13
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
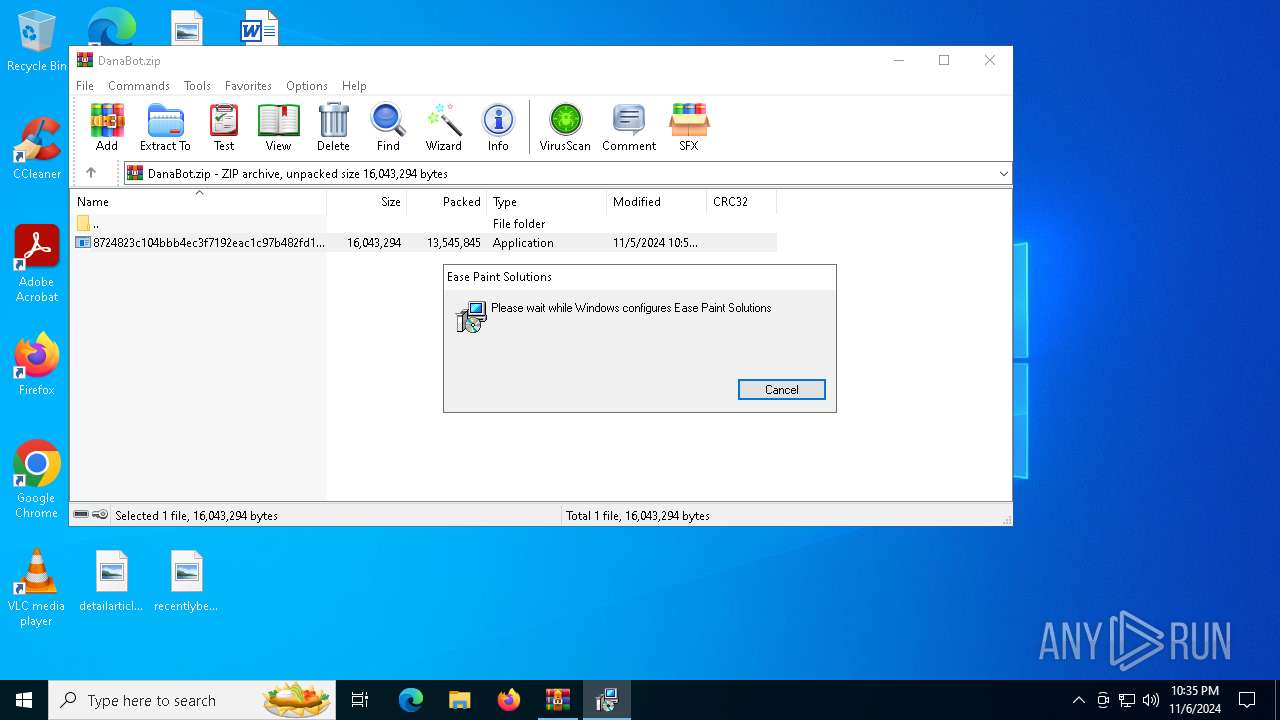
| 1500 | "C:\Users\admin\AppData\Local\Xiamen Baishengtong Software Technology Co. Ltd\Ease Paint Solutions\EasePaint.exe" | C:\Users\admin\AppData\Local\Xiamen Baishengtong Software Technology Co. Ltd\Ease Paint Solutions\EasePaint.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: EasePaint Exit code: 3221225477 Version: 2.2.0.0 Modules
| |||||||||||||||
| 1712 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1500 -s 2072 | C:\Windows\SysWOW64\WerFault.exe | — | EasePaint.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1952 | C:\Windows\syswow64\MsiExec.exe -Embedding 80E1647BC8765A8E4D77F1A83412B570 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | "C:\WINDOWS\system32\msiexec.exe" /i "C:\Users\admin\AppData\Roaming\Xiamen Baishengtong Software Technology Co. Ltd\Ease Paint Solutions 2.2.0.0\install\EB578B6\adv.msi" AI_SETUPEXEPATH=C:\Users\admin\AppData\Local\Temp\Rar$EXb5616.34773\8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe SETUPEXEDIR=C:\Users\admin\AppData\Local\Temp\Rar$EXb5616.34773\ EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1730931938 " CLIENTPROCESSID=6184 CHAINERUIPROCESSID=6184Chainer AI_EUIMSI="" | C:\Windows\SysWOW64\msiexec.exe | — | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5372 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5616 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\DanaBot.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5788 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5984 | C:\Windows\syswow64\MsiExec.exe -Embedding 5E7A11F034B3970C4CCF383E10871E14 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6184 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb5616.34773\8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb5616.34773\8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | WinRAR.exe | ||||||||||||
User: admin Company: Xiamen Baishengtong Software Technology Co. Ltd. Integrity Level: MEDIUM Description: Ease Paint Solutions Installer Exit code: 0 Version: 2.2.0.0 Modules
| |||||||||||||||
Total events
11 817
Read events
11 762
Write events
43
Delete events
12
Modification events
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\DanaBot.zip | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5372) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: FC14000002FBD93B9C30DB01 | |||
| (PID) Process: | (5372) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: B4493C4B959C289C41B5A948D7F782323AD5D0A8C8BE5D40E04E53A7BE6EEF00 | |||
| (PID) Process: | (5372) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
Executable files
28
Suspicious files
23
Text files
2
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6184 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | C:\Users\admin\AppData\Roaming\Xiamen Baishengtong Software Technology Co. Ltd\Ease Paint Solutions 2.2.0.0\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 5616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb5616.34773\8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | executable | |
MD5:9240ACA1F525F6E95CDA49F229C524A9 | SHA256:8724823C104BBB4EC3F7192EAC1C97B482FD129E7550201CB77CAE0C066AB09D | |||
| 6184 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | C:\Users\admin\AppData\Local\Temp\MSI5FCA.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 6184 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | C:\Users\admin\AppData\Local\Temp\MSI5EEE.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 5372 | msiexec.exe | C:\Windows\Installer\MSI645B.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 6184 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | C:\Users\admin\AppData\Roaming\Xiamen Baishengtong Software Technology Co. Ltd\Ease Paint Solutions 2.2.0.0\install\EB578B6\Patch.db | — | |
MD5:— | SHA256:— | |||
| 6964 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | C:\Users\admin\AppData\Local\Temp\shi61EA.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 5372 | msiexec.exe | C:\Windows\Installer\MSI6577.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 5372 | msiexec.exe | C:\Windows\Installer\MSI64D9.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
| 5372 | msiexec.exe | C:\Windows\Installer\MSI6538.tmp | executable | |
MD5:421643EE7BB89E6DF092BC4B18A40FF8 | SHA256:D6B89FD5A95071E7B144D8BEDCB09B694E9CD14BFBFAFB782B17CF8413EAC6DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
52
DNS requests
23
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6384 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6308 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6964 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6308 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5100 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6964 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6964 | 8724823c104bbb4ec3f7192eac1c97b482fd129e7550201cb77cae0c066ab09d.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAXvK8js53xlznpnfGmwHG8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5984 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6384 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6384 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1500 | EasePaint.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |
1500 | EasePaint.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |
6460 | EasePaint.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |
6460 | EasePaint.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Danabot TCP Packet |