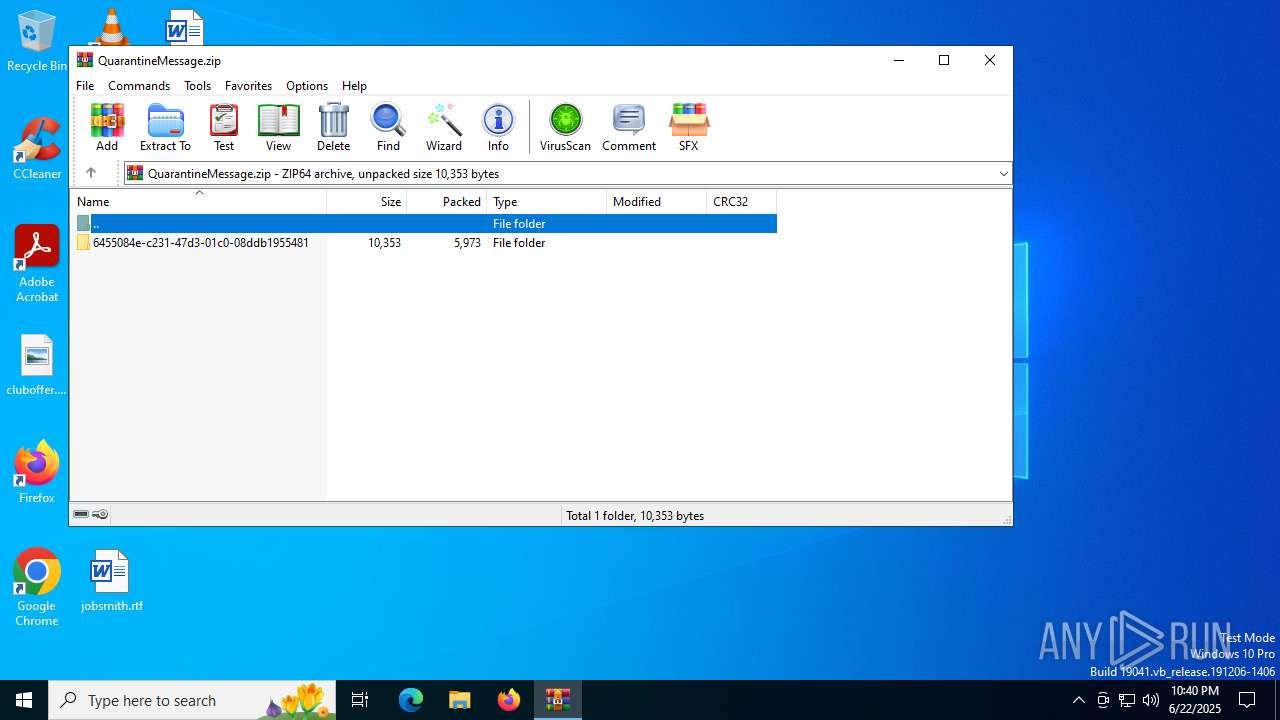
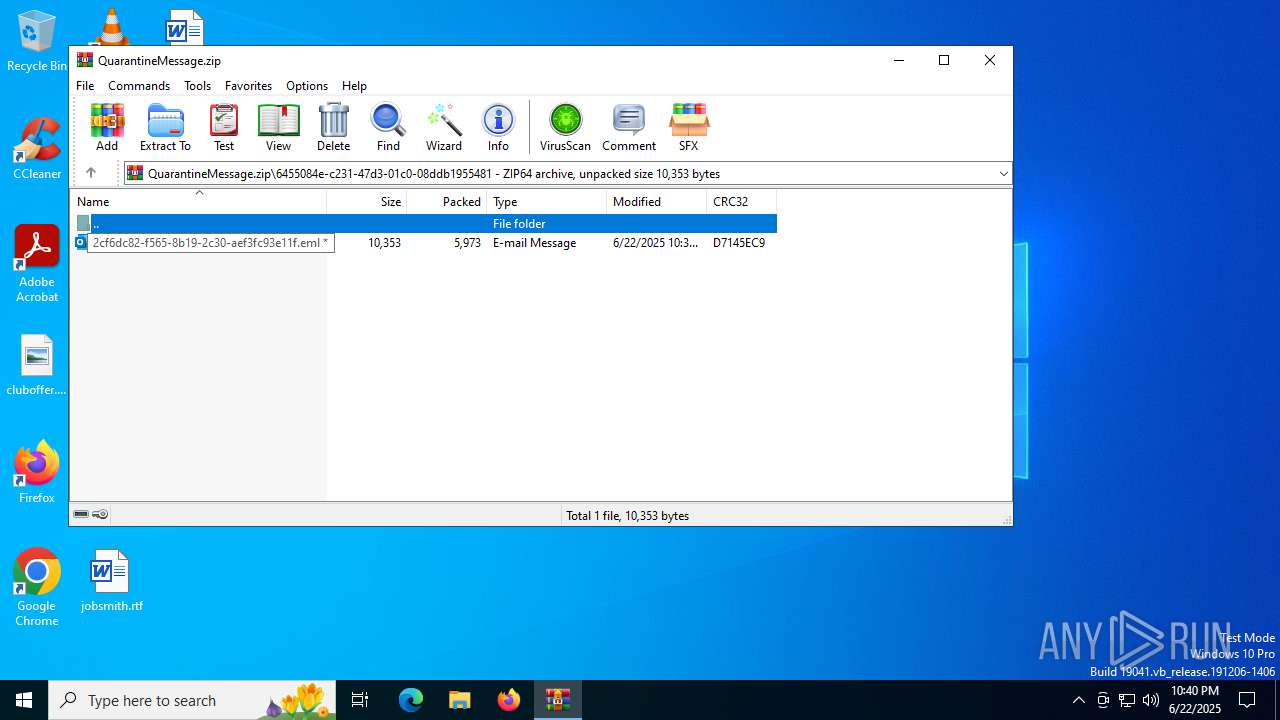
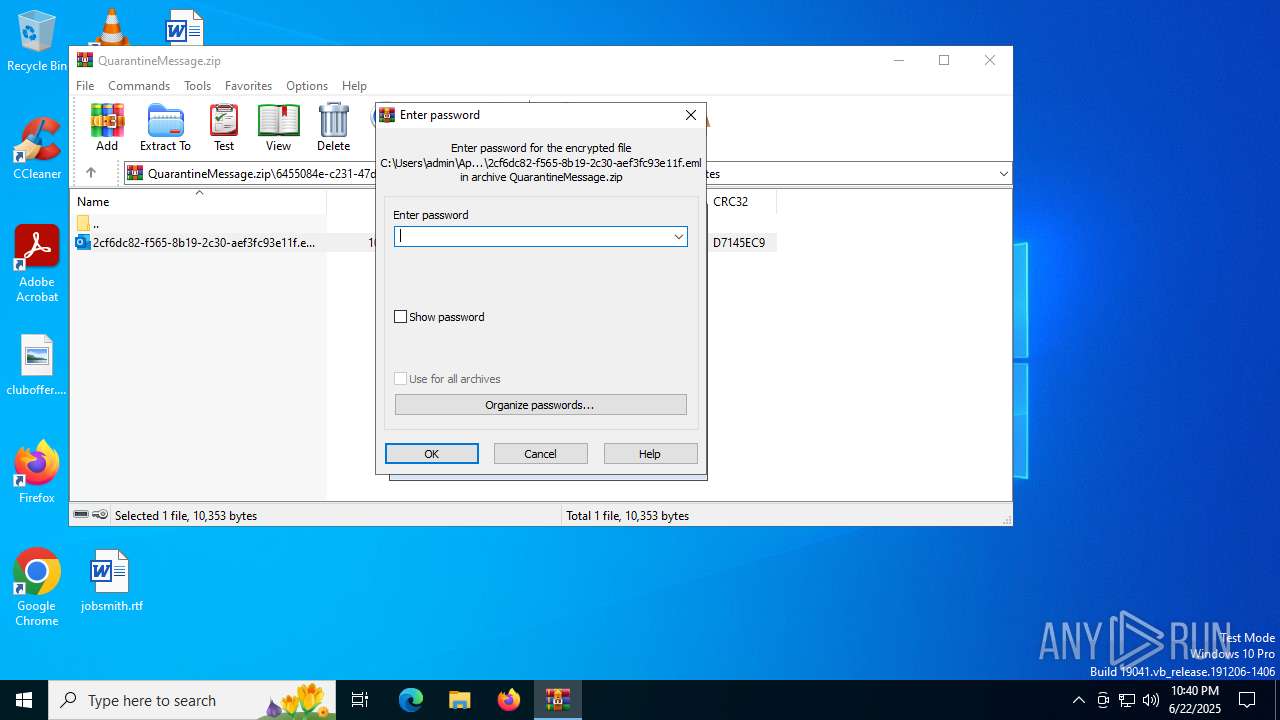
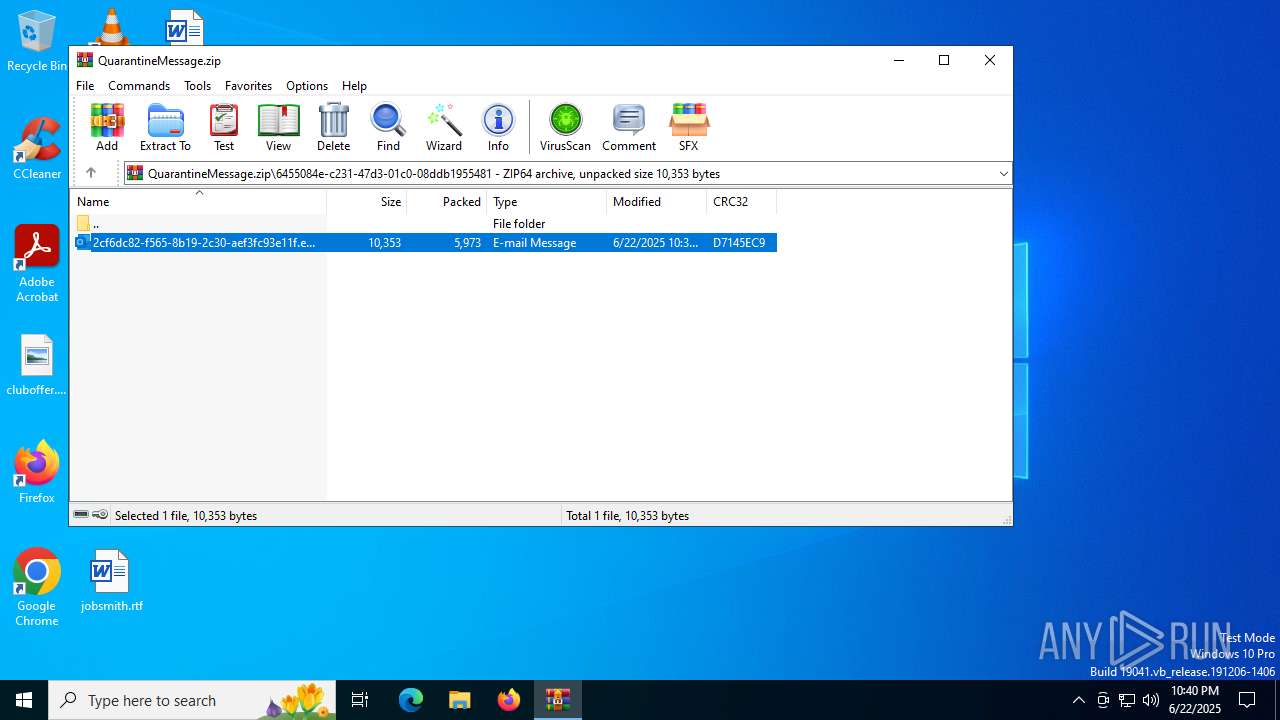
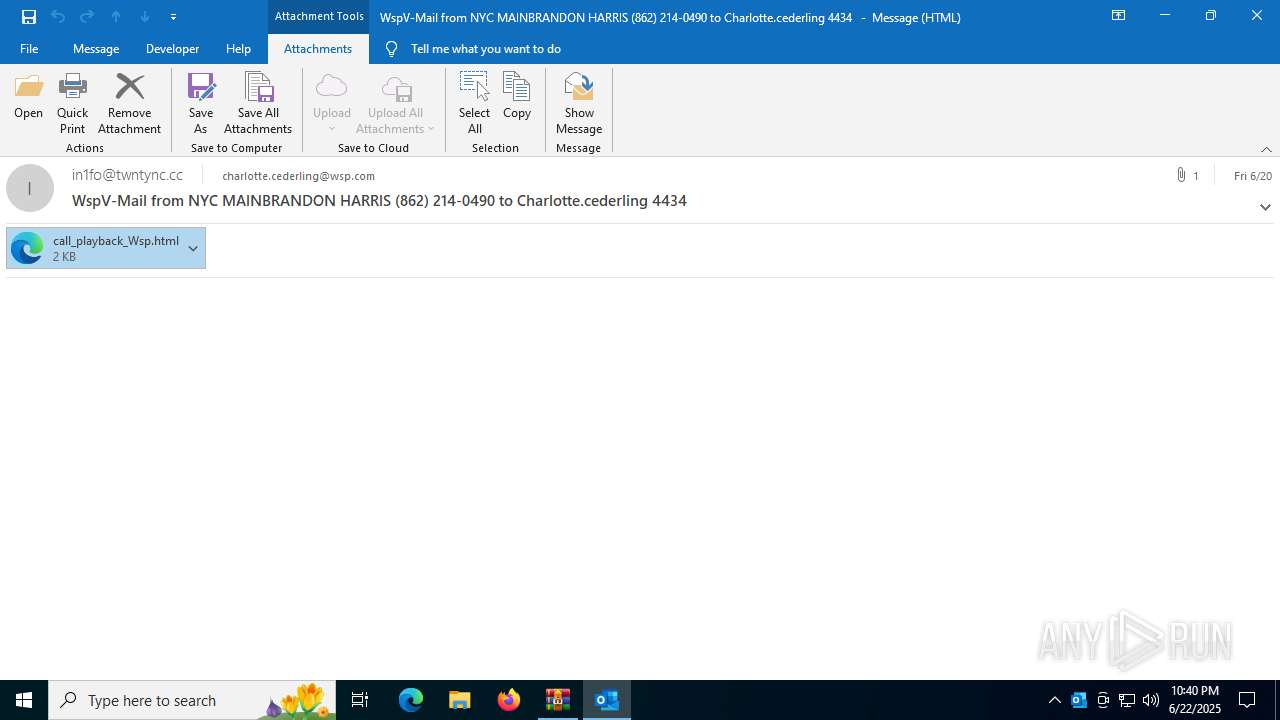
| File name: | QuarantineMessage.zip |
| Full analysis: | https://app.any.run/tasks/99a8ea87-51f5-4b7f-91b8-1ee551db1265 |
| Verdict: | Malicious activity |
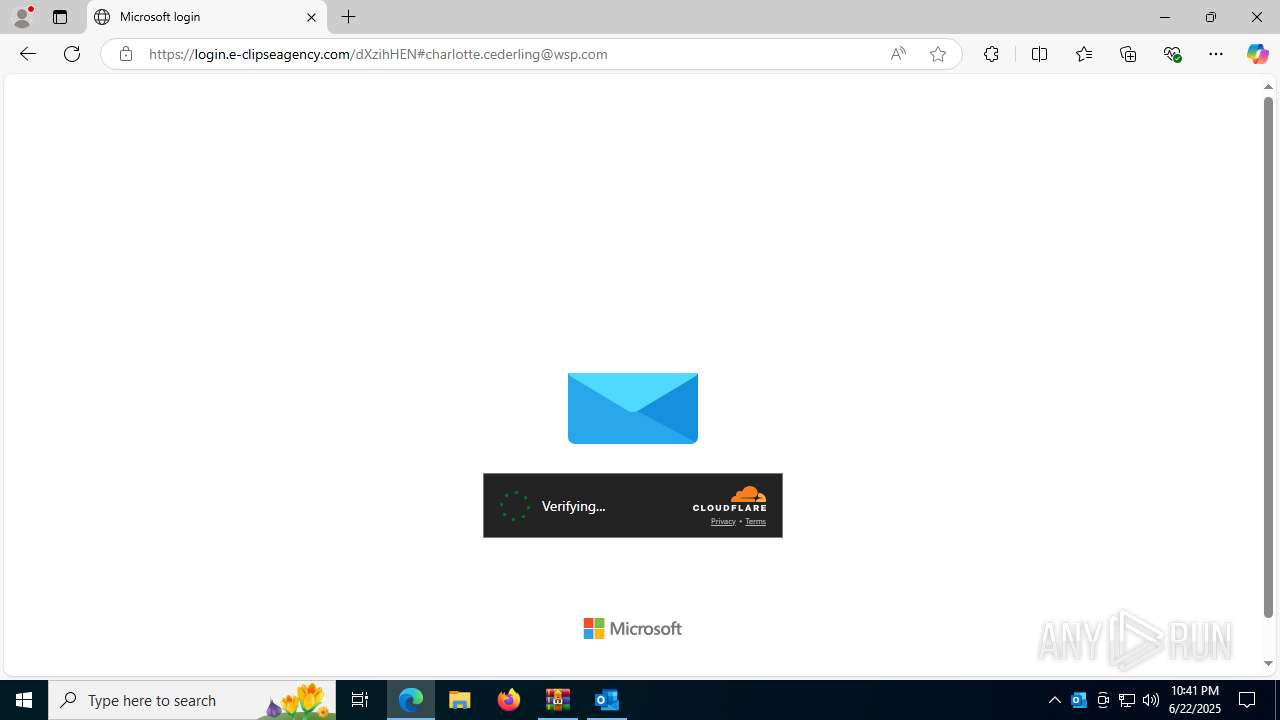
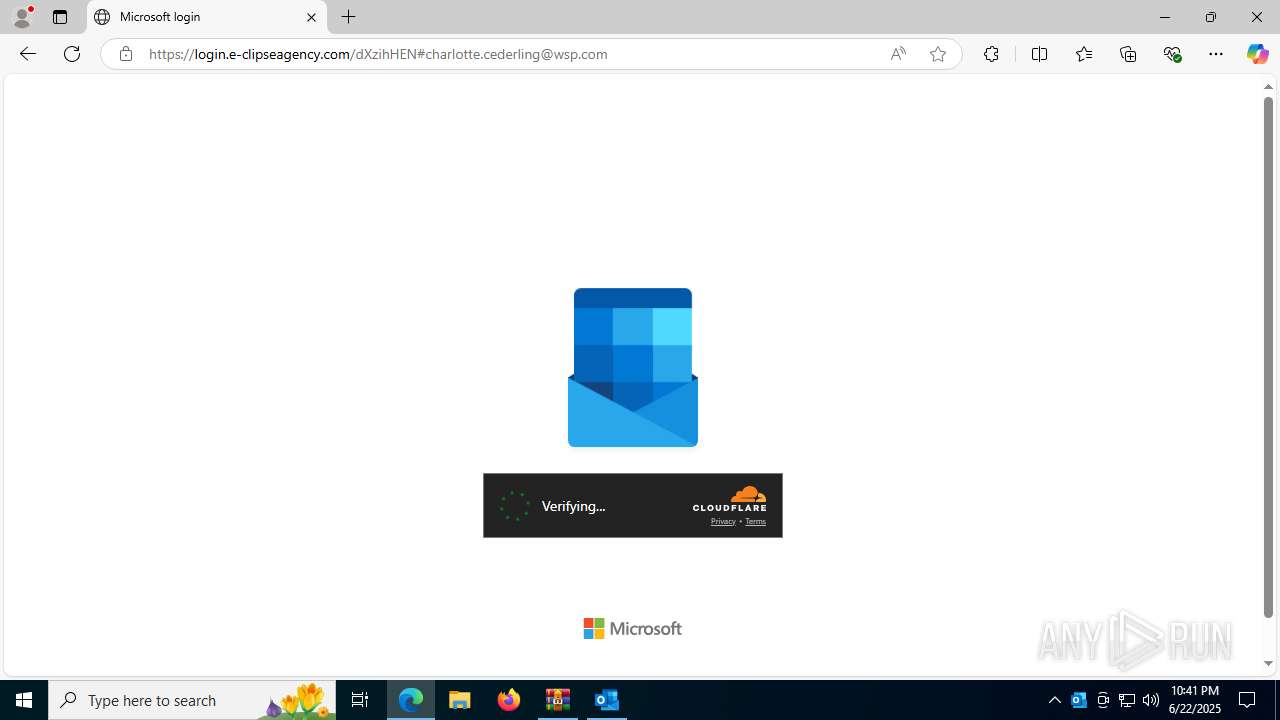
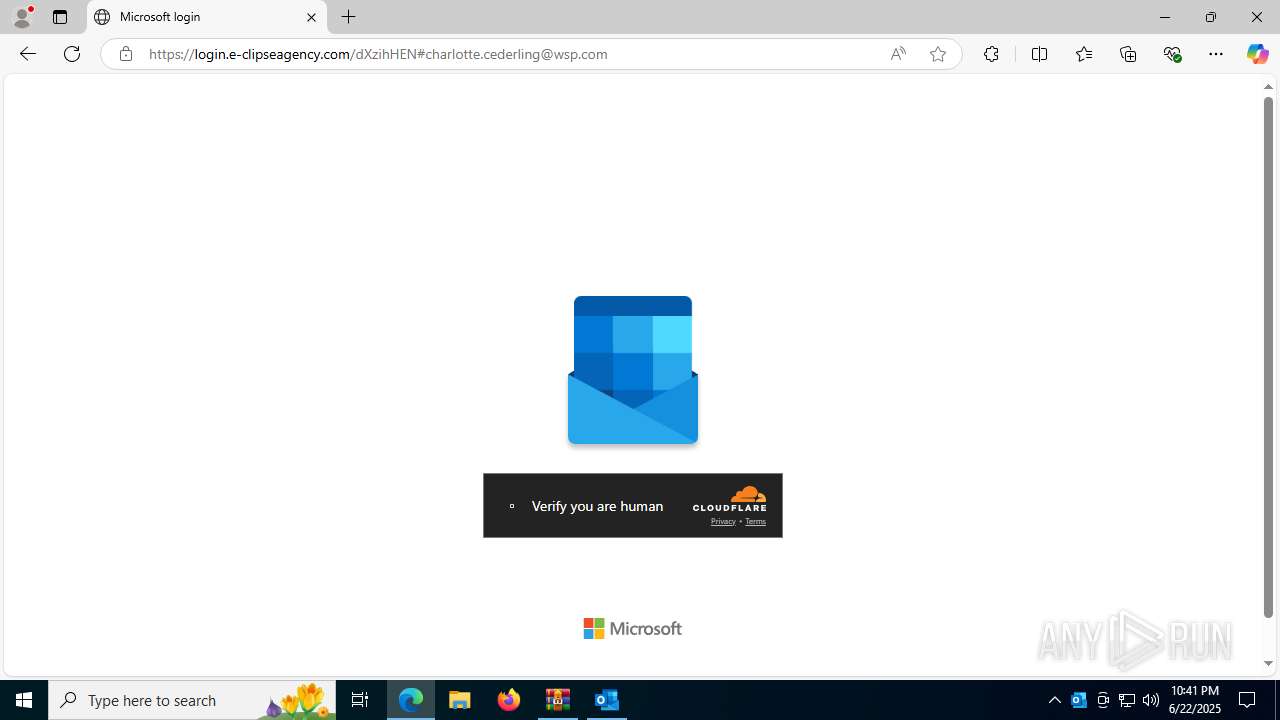
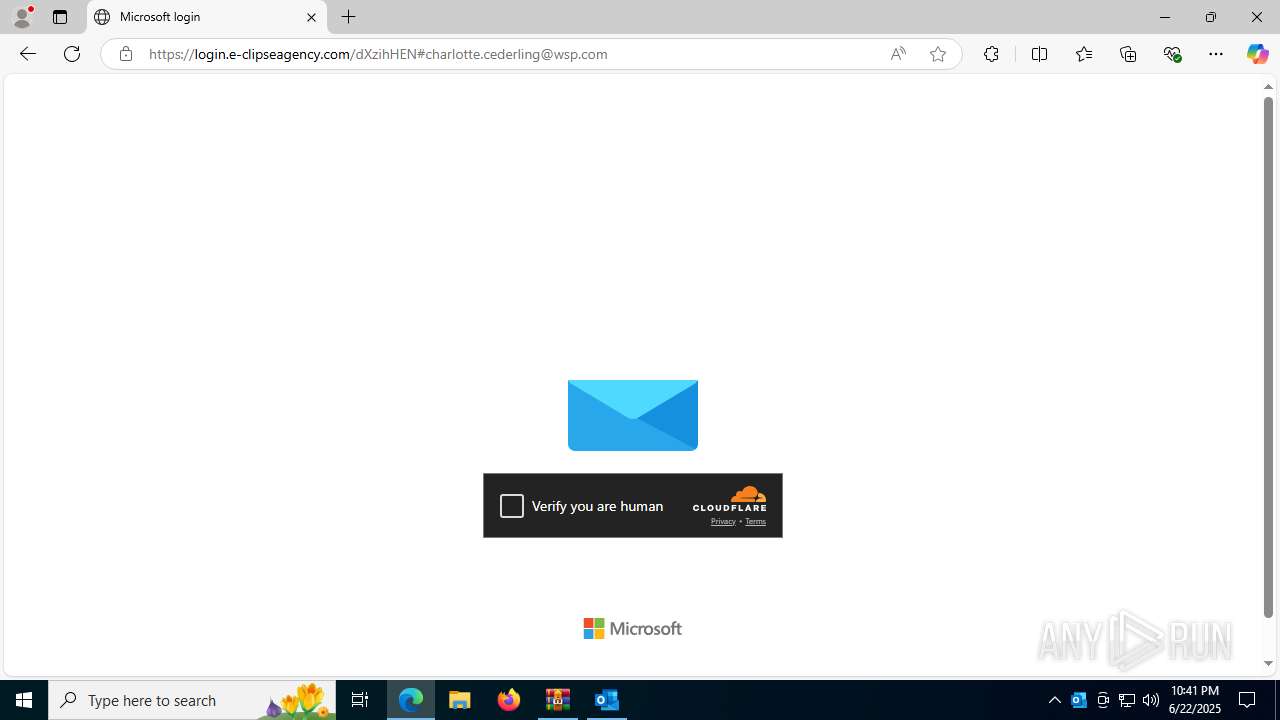
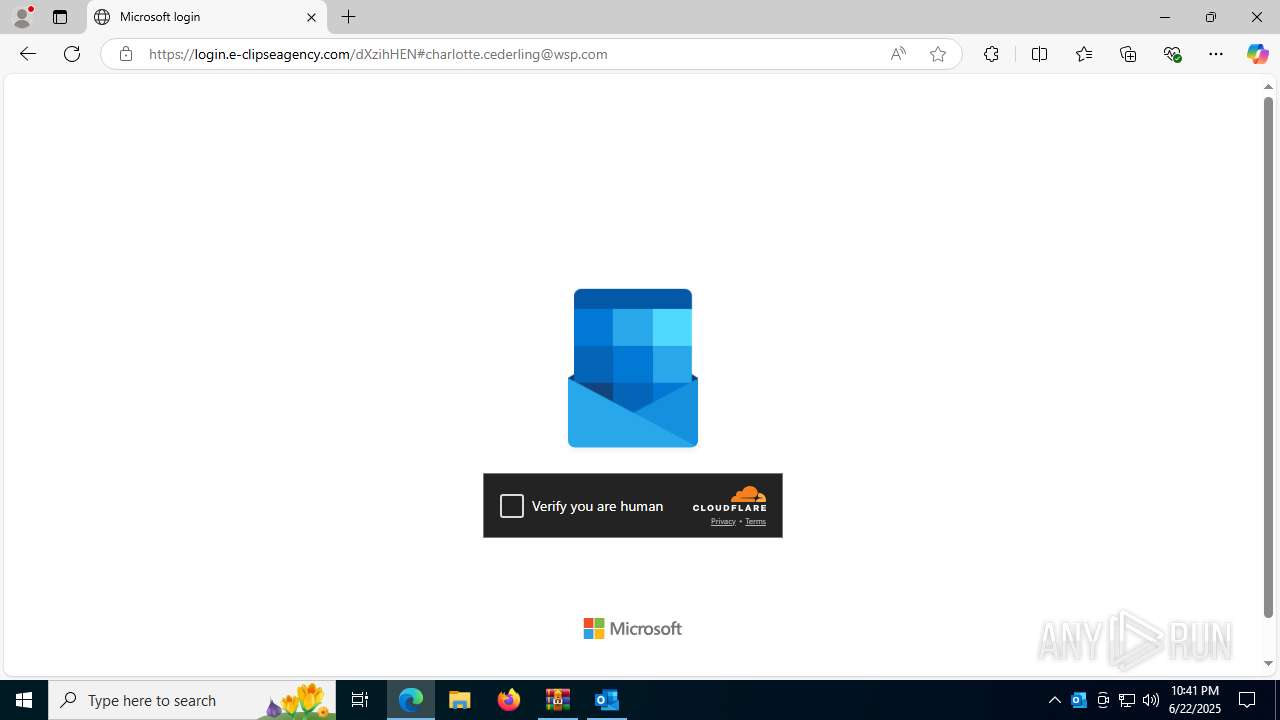
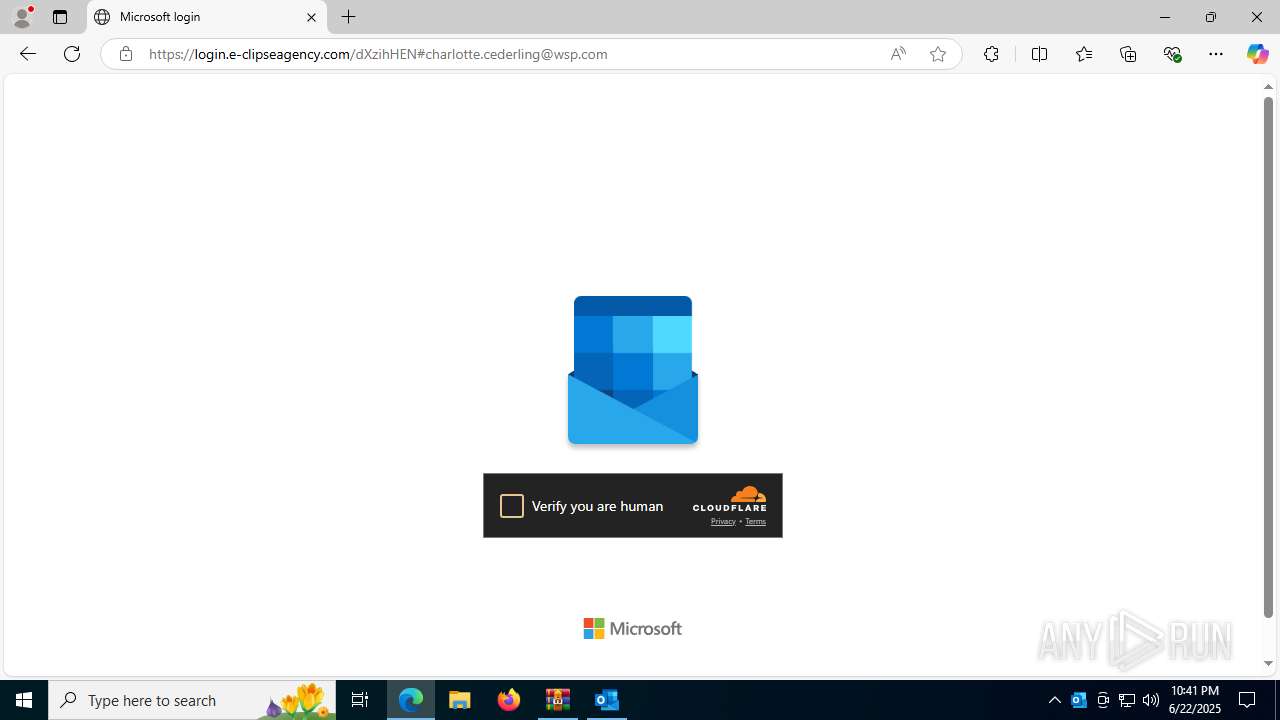
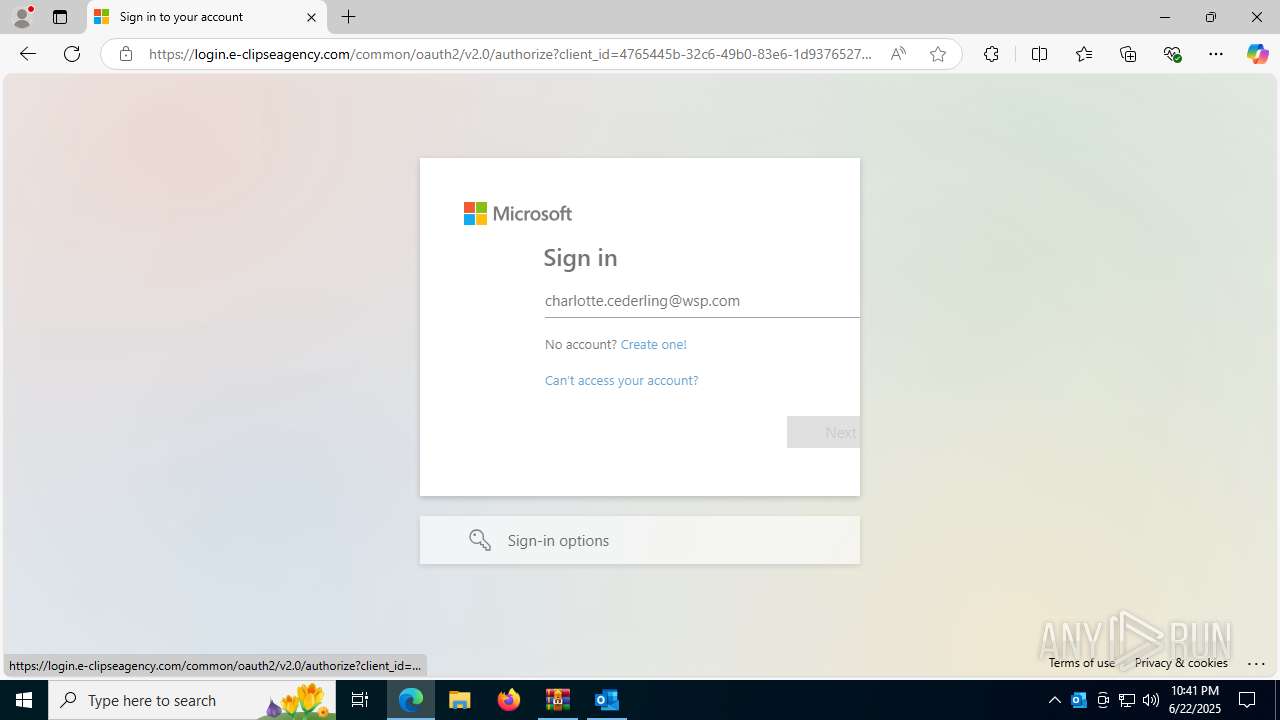
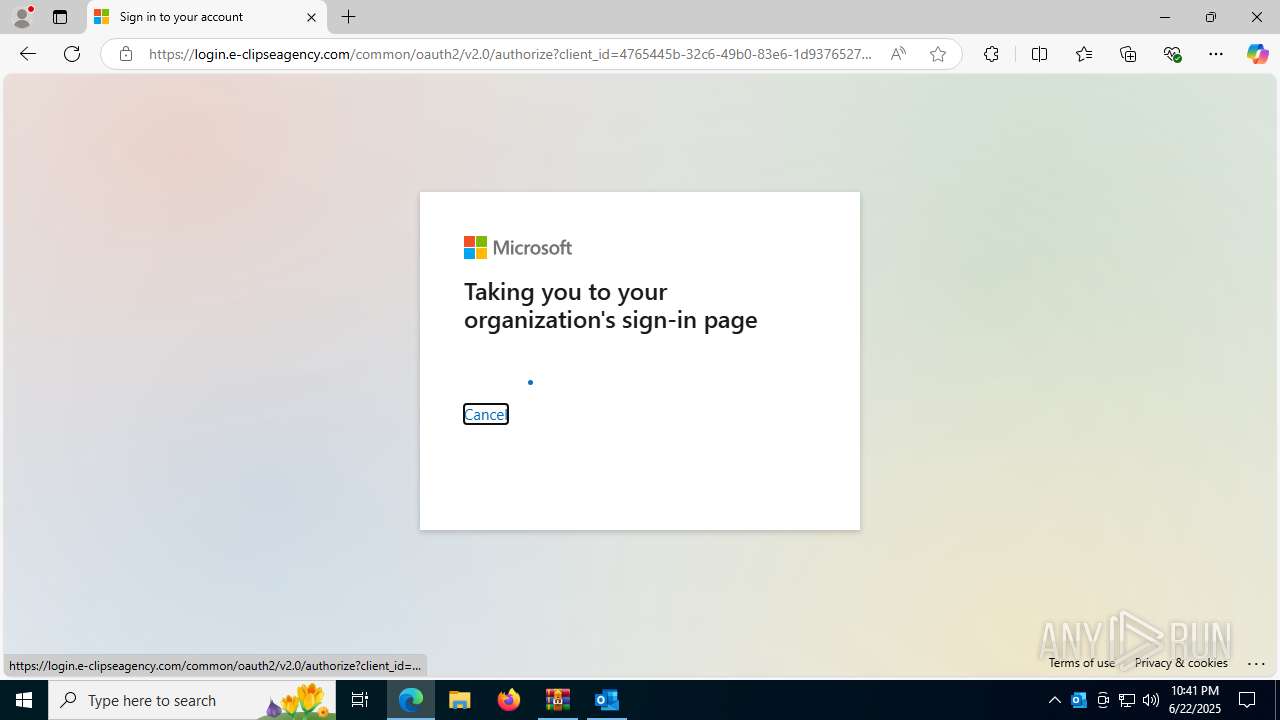
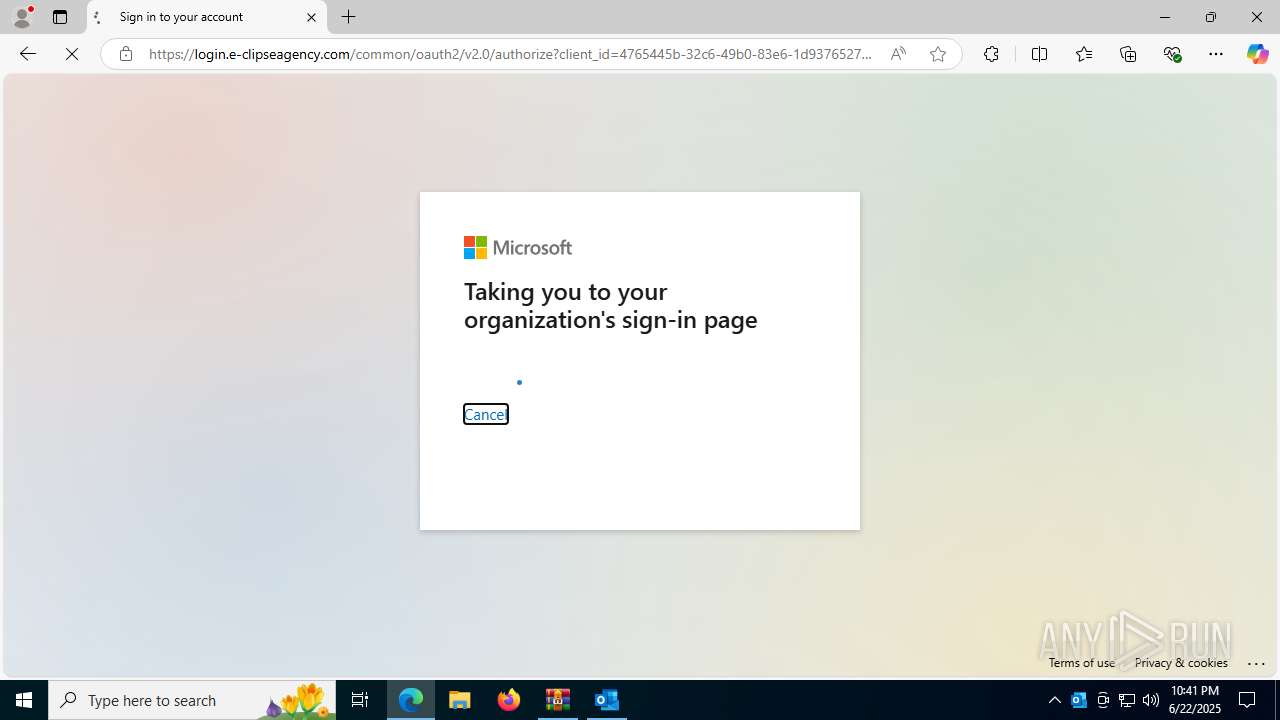
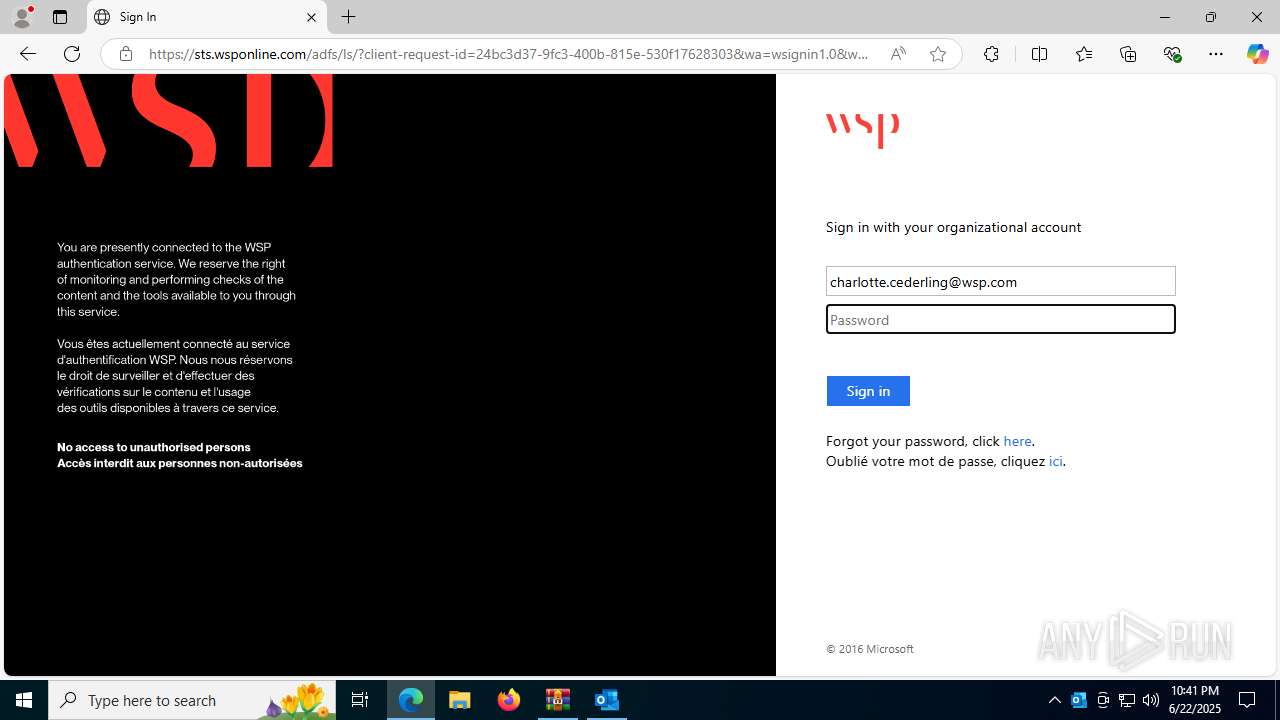
| Threats: | EvilProxy is a phishing-as-a-service (PhaaS) platform that enables cybercriminals to bypass multi-factor authentication (MFA) and hijack user sessions. It leverages reverse proxy techniques to harvest credentials and session cookies, posing a serious threat to both individuals and enterprises. |
| Analysis date: | June 22, 2025, 22:40:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | F3C0E123D5110C7B25771012734ABE0F |
| SHA1: | 533CAA69D349E16A166FE0EB30DDCD75BDBFB787 |
| SHA256: | 0928108178F09748EF9F042E3BB7B3617A2F58E97A414D559A0C976AF88C7FDA |
| SSDEEP: | 192:IgG7PbH37sFLUg3C0RsAprImScNU4FapG8KyT2iSoVjy:IggPzYlRC0Rsq8mScGlSsjy |
MALICIOUS
PHISHING has been detected (SURICATA)
- msedge.exe (PID: 724)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4192)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 4192)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 4192)
Application launched itself
- msedge.exe (PID: 2220)
Checks supported languages
- identity_helper.exe (PID: 7772)
Reads the computer name
- identity_helper.exe (PID: 7772)
Reads Environment values
- identity_helper.exe (PID: 7772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:22 22:30:42 |
| ZipCRC: | 0xd7145ec9 |
| ZipCompressedSize: | 4294967295 |
| ZipUncompressedSize: | 4294967295 |
| ZipFileName: | 6455084e-c231-47d3-01c0-08ddb1955481/2cf6dc82-f565-8b19-2c30-aef3fc93e11f.eml |
Total processes
165
Monitored processes
26
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 724 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2280,i,13619647299912752865,5981471775954370788,262144 --variations-seed-version --mojo-platform-channel-handle=2512 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2120 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2456,i,13619647299912752865,5981471775954370788,262144 --variations-seed-version --mojo-platform-channel-handle=2452 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
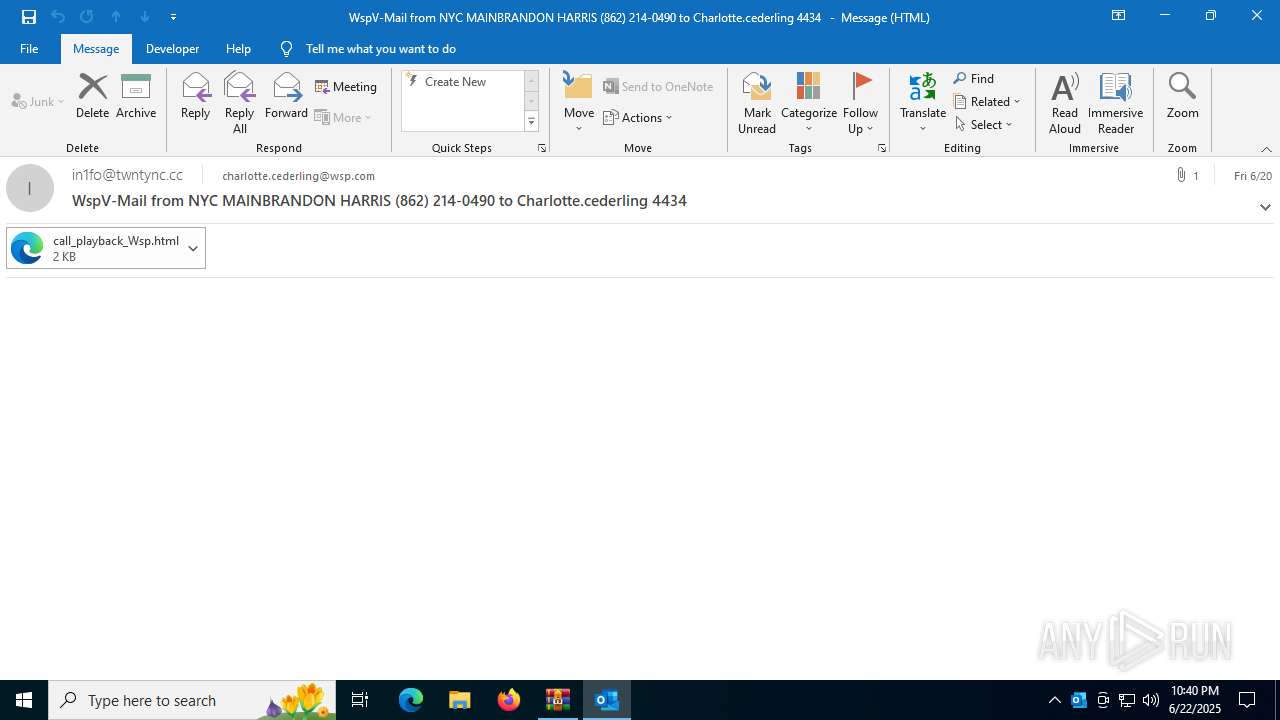
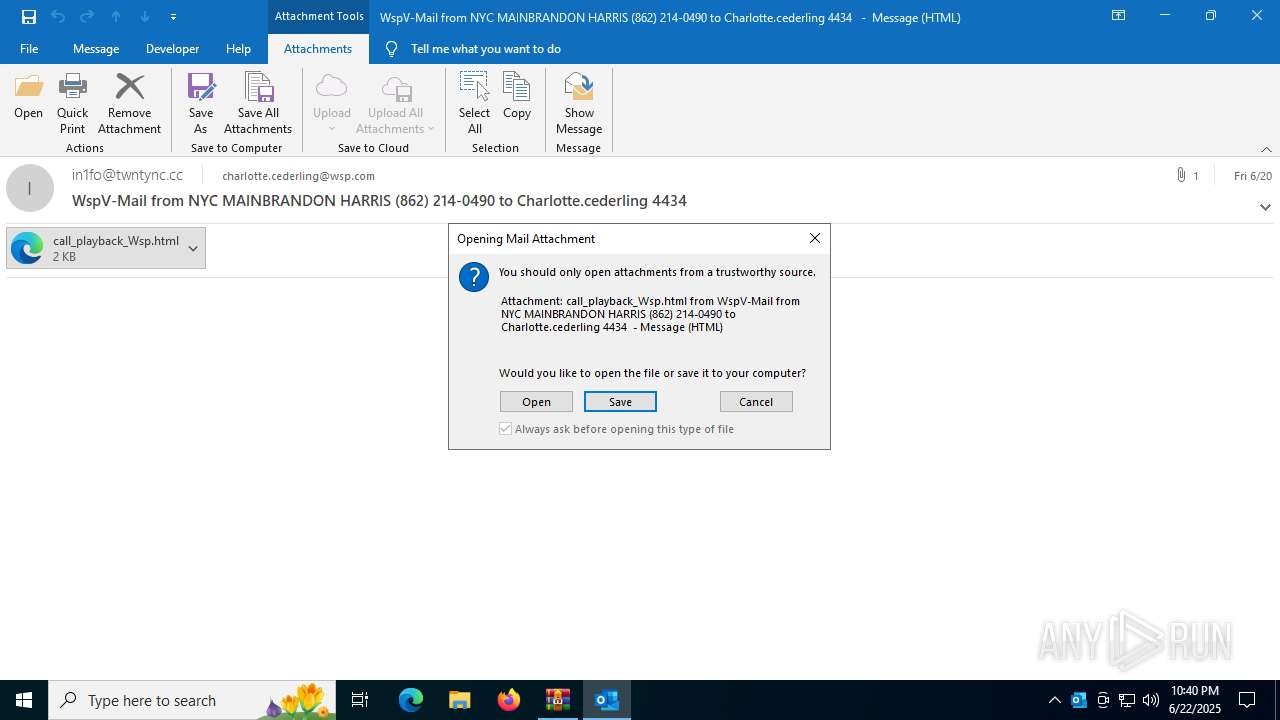
| 2220 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\WN1DLTCJ\call_playback_Wsp.html | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2464 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc3606f208,0x7ffc3606f214,0x7ffc3606f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3752 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Rar$DIb4192.34779\2cf6dc82-f565-8b19-2c30-aef3fc93e11f.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4192 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\QuarantineMessage.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4752 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3608,i,13619647299912752865,5981471775954370788,262144 --variations-seed-version --mojo-platform-channel-handle=3672 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 5620 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "FFAED861-5518-4C35-85FB-8514741ED8FF" "58712E98-5C31-4157-BC95-445CBAC0C6A8" "3752" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 5960 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4260,i,13619647299912752865,5981471775954370788,262144 --variations-seed-version --mojo-platform-channel-handle=4216 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
16 283
Read events
15 118
Write events
1 044
Delete events
121
Modification events
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\QuarantineMessage.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
5
Suspicious files
78
Text files
35
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3752 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:42F338C2562D9D70FA0412C682EC4654 | SHA256:CD9EF7A97FD0272BF03E95AE529A00C58C52FC6DD82EE32652B3E4443C154FD6 | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:F584E02E941F2D43B5994D88307441C2 | SHA256:264BC64B3CA8E9DA9D459E508472B94CDBEF331C4FF9AF49C5EB4448FCBFB7DC | |||
| 3752 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:B21658C36146E52260507791512E9C19 | SHA256:7A23CD44FBFDEE3399FF9C0CE8535AD47FA28207F3697EFC8382D218F8A1DDE3 | |||
| 2220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF17d929.TMP | — | |
MD5:— | SHA256:— | |||
| 2220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF17d939.TMP | — | |
MD5:— | SHA256:— | |||
| 2220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF17d939.TMP | — | |
MD5:— | SHA256:— | |||
| 2220 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
76
DNS requests
77
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3752 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
724 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:xG6Bs9u59yytsb4BWwCENpGNlnK1hnRPNNRWE_-oHZA&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
436 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4880 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4648 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3752 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3752 | OUTLOOK.EXE | 23.200.86.240:443 | omex.cdn.office.net | Akamai International B.V. | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
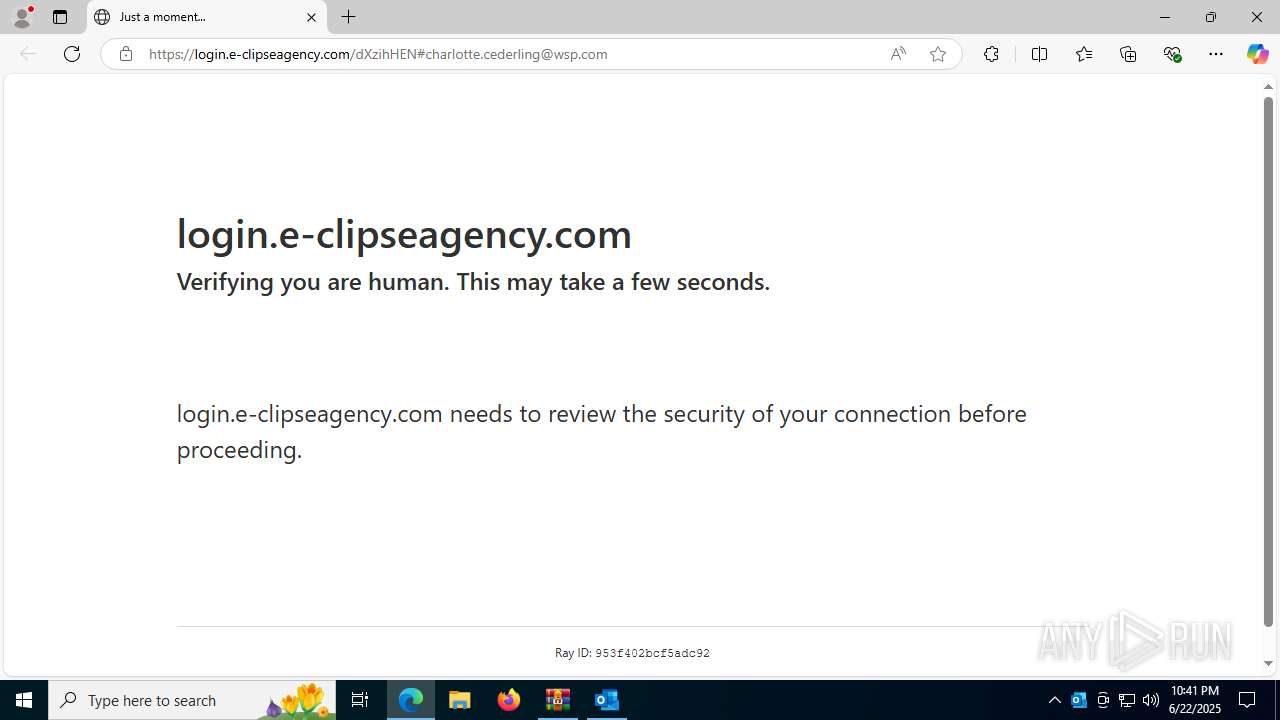
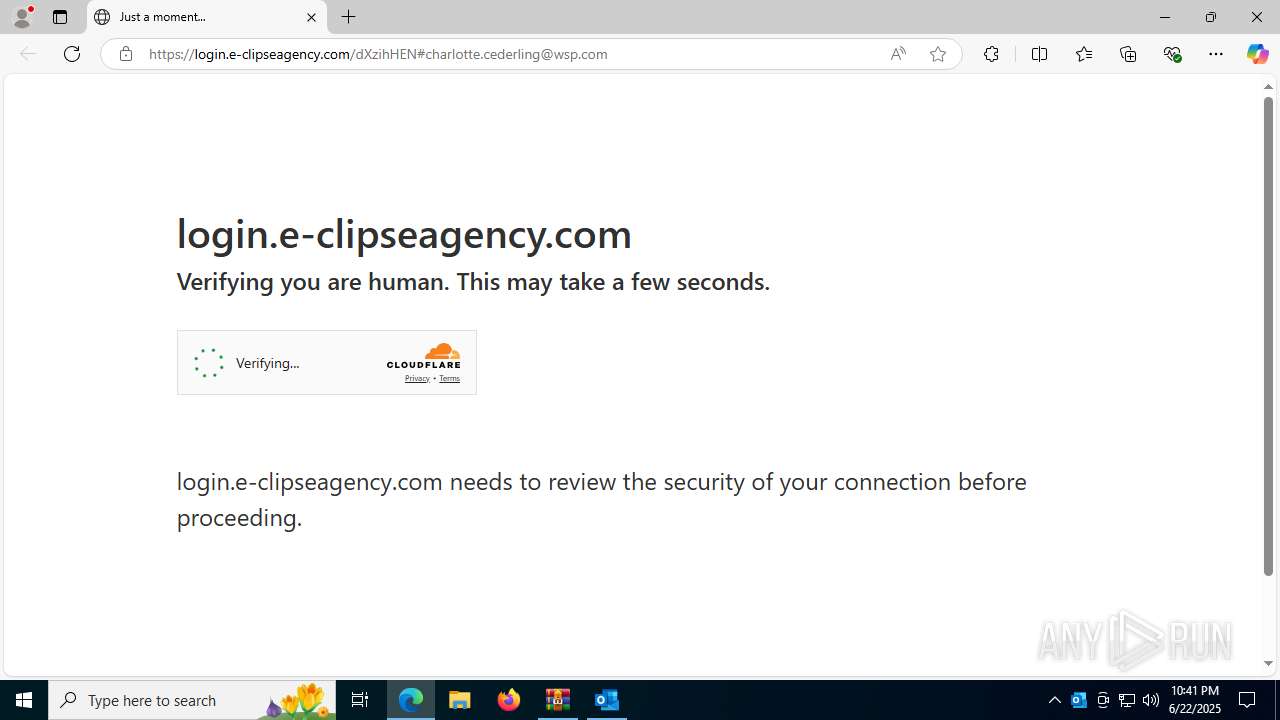
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
724 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
724 | msedge.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Possible Domain chain identified as Phishing (authisnotlogin) |