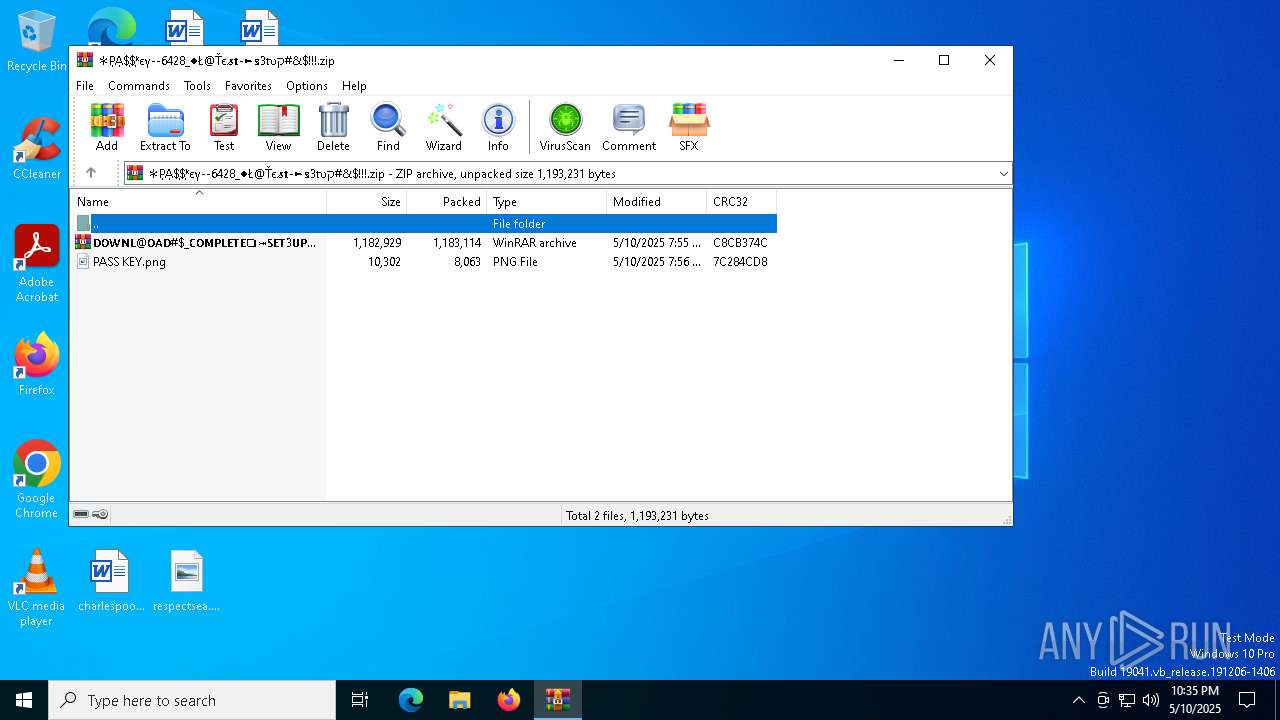
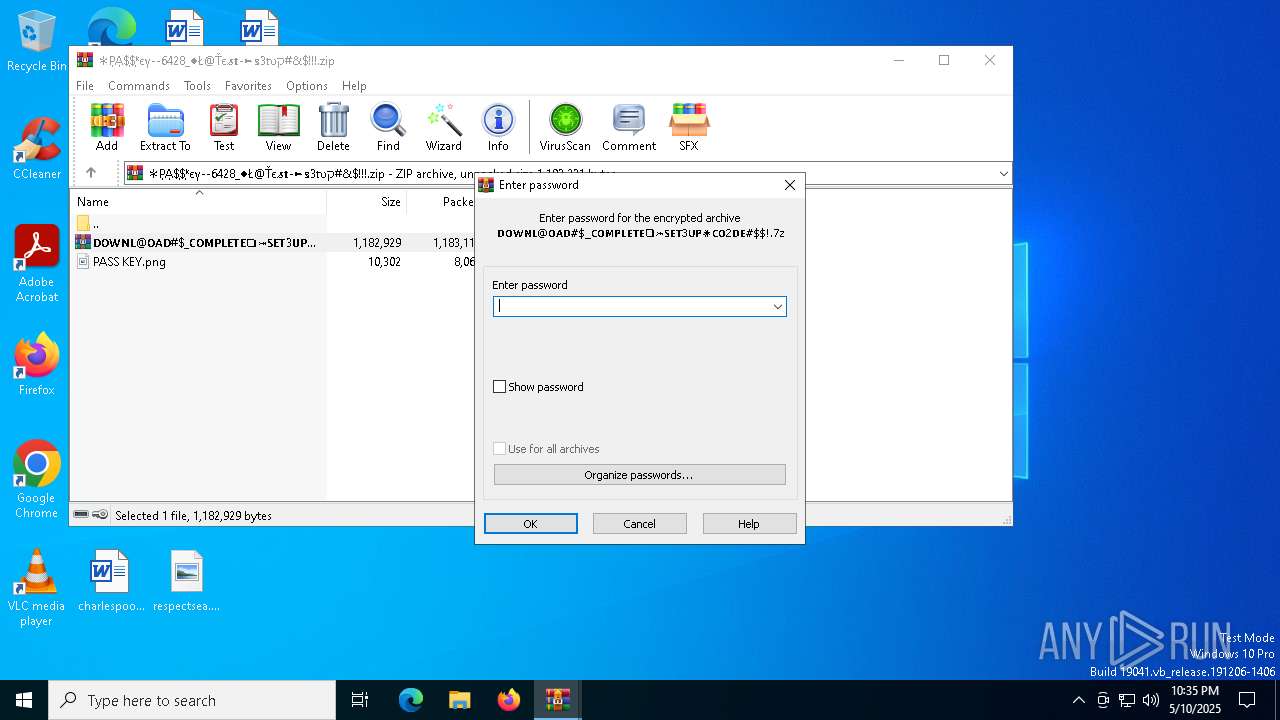
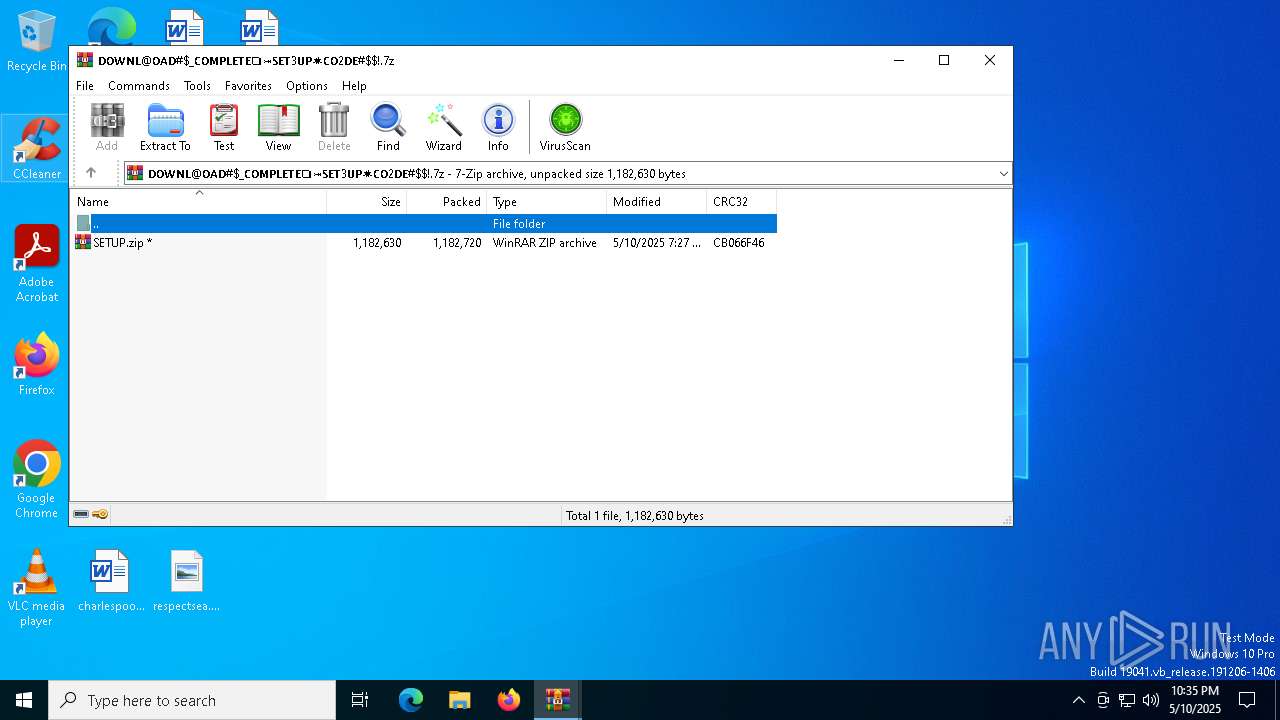
| File name: | ✻P͎A͎$͎$͎ᵏєү--6428_♦Ł@Ťє𝓼𝐭-►𝕤3𝔱υק#&$!!!.zip |
| Full analysis: | https://app.any.run/tasks/6a626eca-0383-4932-989a-5302da155da5 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 10, 2025, 22:35:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2FF5CE06C306B5502BB90E003AA868D2 |
| SHA1: | 8407E95A0F4D049B38AA92C91404BCFEFE5AFAEB |
| SHA256: | 082A8CAB941D512AB282DFCF44F8783F0866E14264F0E9CD1939CF93FC54255C |
| SSDEEP: | 49152:VJna0sw47VleWlHRDad0uWjlxaYagpsKVDi5oLyifSExGSz2eFjNLNYuTP+A+TDm:VJnhsr7VlJHxad0uSx3a7U0A5S6XSgZB |
MALICIOUS
Executing a file with an untrusted certificate
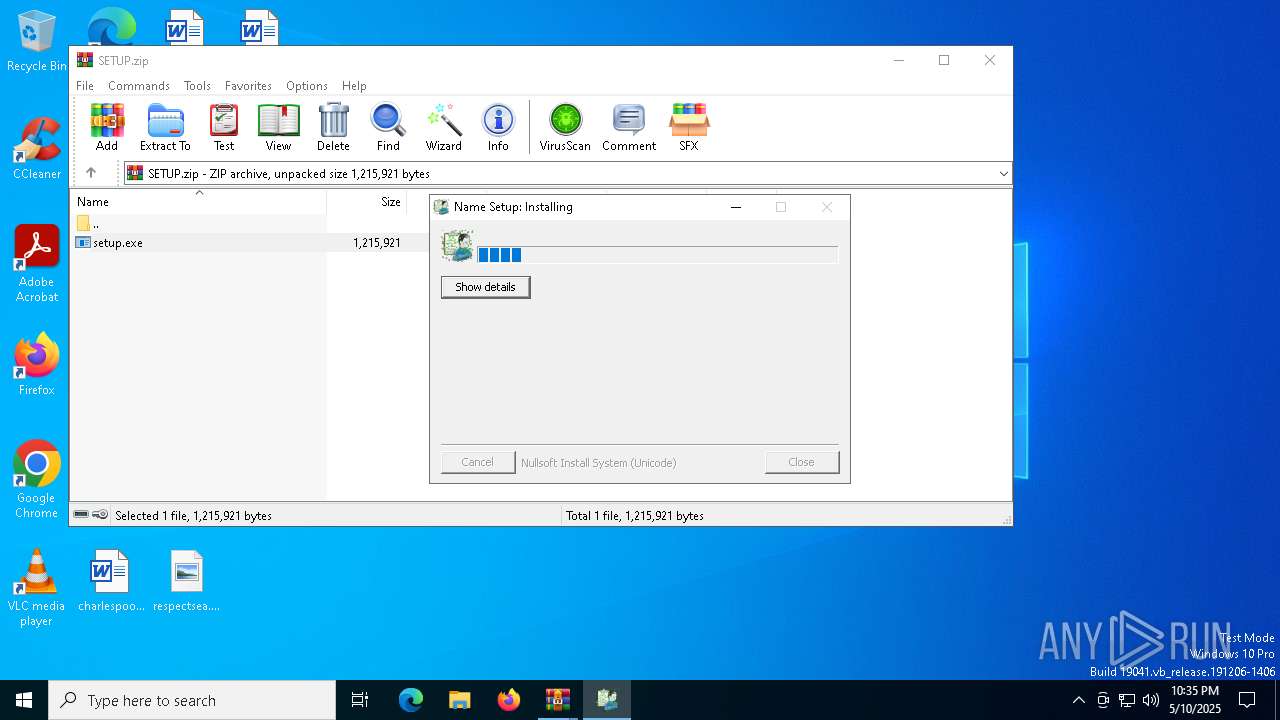
- setup.exe (PID: 7880)
LUMMA mutex has been found
- Warriors.com (PID: 6712)
Actions looks like stealing of personal data
- Warriors.com (PID: 6712)
Steals credentials from Web Browsers
- Warriors.com (PID: 6712)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 7148)
- WinRAR.exe (PID: 7416)
- cmd.exe (PID: 7932)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7148)
- WinRAR.exe (PID: 7416)
- WinRAR.exe (PID: 7816)
- setup.exe (PID: 7880)
Executing commands from a ".bat" file
- setup.exe (PID: 7880)
Get information on the list of running processes
- cmd.exe (PID: 7932)
Starts CMD.EXE for commands execution
- setup.exe (PID: 7880)
- cmd.exe (PID: 7932)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7932)
The executable file from the user directory is run by the CMD process
- Warriors.com (PID: 6712)
Starts application with an unusual extension
- cmd.exe (PID: 7932)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7932)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 7880)
Searches for installed software
- Warriors.com (PID: 6712)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7816)
Reads the computer name
- setup.exe (PID: 7880)
- extrac32.exe (PID: 6728)
- Warriors.com (PID: 6712)
Create files in a temporary directory
- setup.exe (PID: 7880)
- extrac32.exe (PID: 6728)
Checks supported languages
- setup.exe (PID: 7880)
- extrac32.exe (PID: 6728)
- Warriors.com (PID: 6712)
Process checks computer location settings
- setup.exe (PID: 7880)
Creates a new folder
- cmd.exe (PID: 8176)
Reads mouse settings
- Warriors.com (PID: 6712)
Reads the software policy settings
- Warriors.com (PID: 6712)
- slui.exe (PID: 7360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:11 00:55:32 |
| ZipCRC: | 0xc8cb374c |
| ZipCompressedSize: | 1183114 |
| ZipUncompressedSize: | 1182929 |
| ZipFileName: | 𝗗𝗢𝗪𝗡𝗟@𝗢𝗔𝗗#$_𝗖𝗢𝗠𝗣𝗟𝗘𝗧𝗘❏⤖𝗦𝗘𝗧3𝗨𝗣✷𝗖𝗢2𝗗𝗘#$!.7z |
Total processes
147
Monitored processes
20
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | cmd /c copy /b 215815\Warriors.com + Animals + Terry + Facility + Detect + Thermal + Studies + Joke + Deutsche + Concerns 215815\Warriors.com | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | findstr /V "dj" Pushed | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6048 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | cmd /c copy /b ..\Productions.vsdx + ..\English.vsdx + ..\Gis.vsdx + ..\Ability.vsdx + ..\Cats.vsdx + ..\Thru.vsdx + ..\Portland.vsdx + ..\Fiction.vsdx g | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6712 | Warriors.com g | C:\Users\admin\AppData\Local\Temp\215815\Warriors.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 6728 | extrac32 /Y /E Enclosed.vsdx | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7148 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\✻P͎A͎$͎$͎ᵏєү--6428_♦Ł@Ťє𝓼𝐭-►𝕤3𝔱υק#&$!!!.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7328 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7360 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 086
Read events
7 061
Write events
25
Delete events
0
Modification events
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\✻P͎A͎$͎$͎ᵏєү--6428_♦Ł@Ťє𝓼𝐭-►𝕤3𝔱υק#&$!!!.zip | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7416) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
Executable files
1
Suspicious files
22
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7880 | setup.exe | C:\Users\admin\AppData\Local\Temp\Cats.vsdx | binary | |
MD5:5948B3381C0A1EB046D09DF606891F19 | SHA256:0613D4732430C71C98910C04E94EA2D97173CBB9A1FBEB8197116B614876B111 | |||
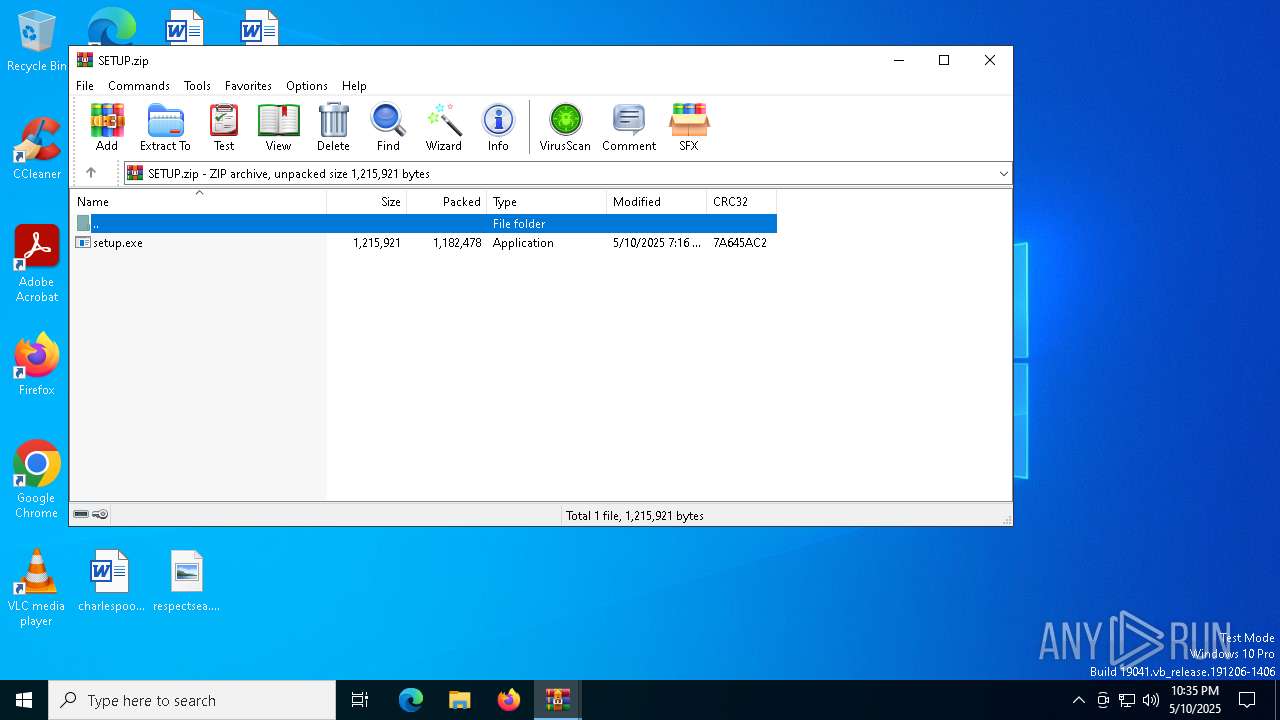
| 7416 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb7416.36325\SETUP.zip | compressed | |
MD5:C28F8298B2D98937516B707324A05645 | SHA256:E9B4323C25E57FFCC40BDE2314A9939D7E20FA03F2AEE006AE435C7359937DF3 | |||
| 7816 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7816.36547\setup.exe | executable | |
MD5:CA3E492EBD940233FFF9FC4E0E76A891 | SHA256:03B139C2D7EB566155C820059DD90FE815F813E5644BA8199BC4F01B4FA921AC | |||
| 7148 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7148.35229\𝗗𝗢𝗪𝗡𝗟@𝗢𝗔𝗗#$_𝗖𝗢𝗠𝗣𝗟𝗘𝗧𝗘❏⤖𝗦𝗘𝗧3𝗨𝗣✷𝗖𝗢2𝗗𝗘#$!.7z | compressed | |
MD5:BBA670858BBBB21FCFB3B7DBD3F5CF8E | SHA256:EF771658CE8AD2E300F62E3812E469937223B98BEE6DFF13663045073DB6BCE0 | |||
| 7880 | setup.exe | C:\Users\admin\AppData\Local\Temp\Ul.vsdx | text | |
MD5:77CDF4B521683D0917BD9B78D9AF7DD9 | SHA256:EAB32B59C501FA143A93E166B23185ABF6EA952E5F390354B3D4002D1FE1947B | |||
| 7880 | setup.exe | C:\Users\admin\AppData\Local\Temp\Ability.vsdx | binary | |
MD5:F63E79DAC28BBEB0EE41082B7CC58F09 | SHA256:E557C93BF020A2C31C159489E30453B5560955D46A13144B2746A6FEB5180279 | |||
| 6728 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Terry | binary | |
MD5:2EA7C072710F41D6523AC7CF17682DA3 | SHA256:88245217319DD58F7EB2296562DF97F3E592E52C94F88C1DA58C88931D9F9639 | |||
| 6728 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Concerns | binary | |
MD5:78168E40CB1452CF834DD1137593025B | SHA256:1D7E086F1425BB5981B119B93545E28ADAA16D7F9C735654B272F2C7D87E06DB | |||
| 7880 | setup.exe | C:\Users\admin\AppData\Local\Temp\Enclosed.vsdx | compressed | |
MD5:62F5433E864A092382778DB50D695B24 | SHA256:1EEBA50572B8211F8D0093DDE7AD0B50212DFBADF25DACEB7155835BA5487846 | |||
| 6728 | extrac32.exe | C:\Users\admin\AppData\Local\Temp\Facility | binary | |
MD5:6F1211E99F2B43F77C3A45B305558E36 | SHA256:1EE4B5B0C738955633EBA86A1D970CA32E2FC3EC4F0660956F6A8D4D6B7AA861 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
25
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.150:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1660 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1660 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.150:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1660 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
kMocBwQIQuslkcFlACcjh.kMocBwQIQuslkcFlACcjh |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |