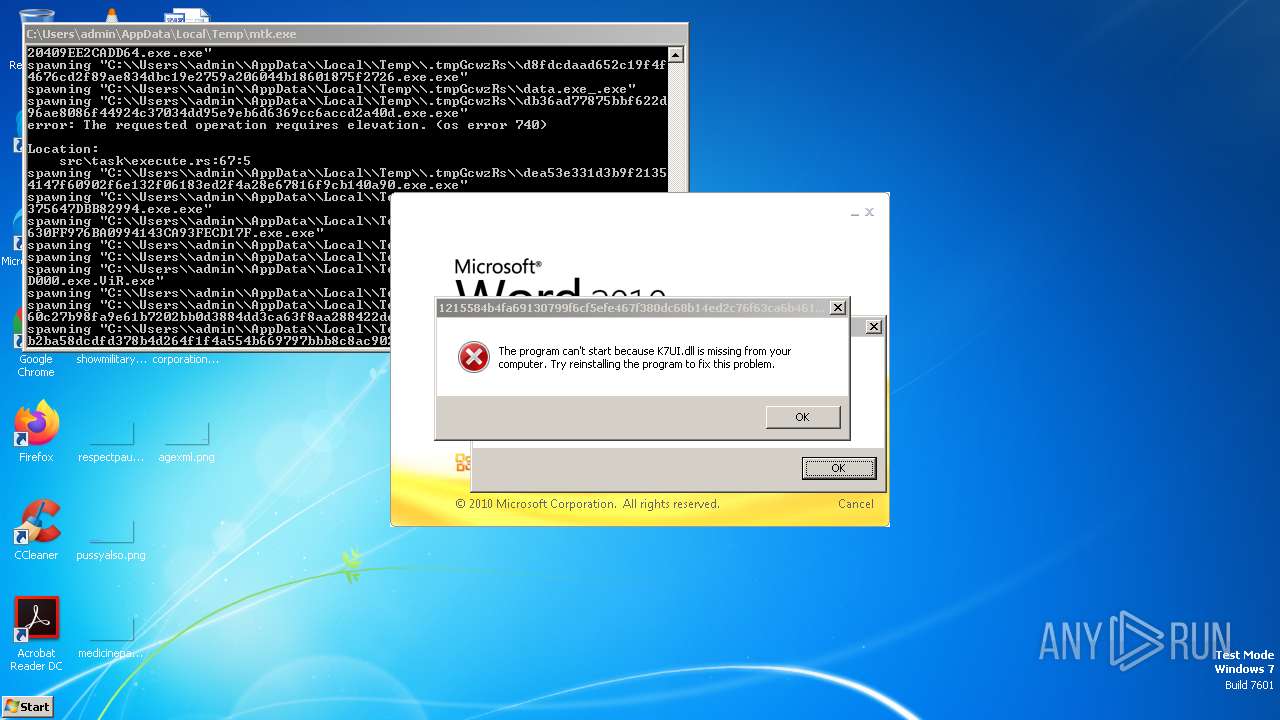
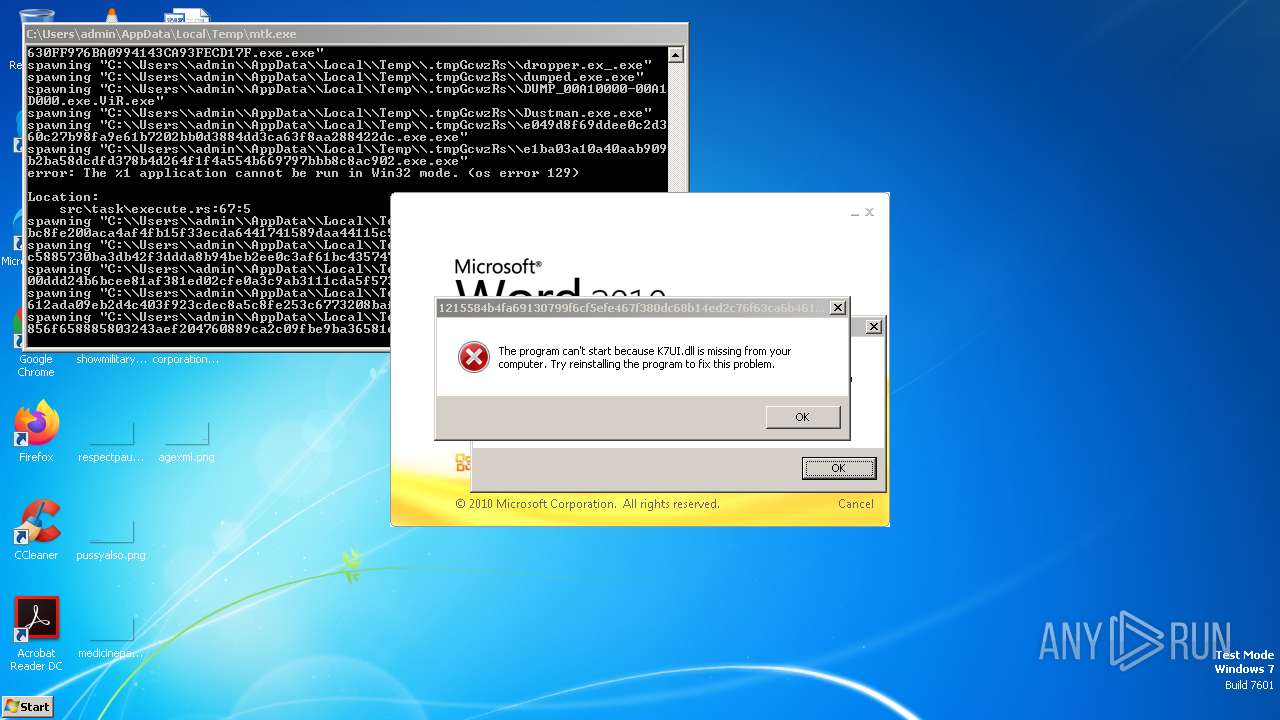
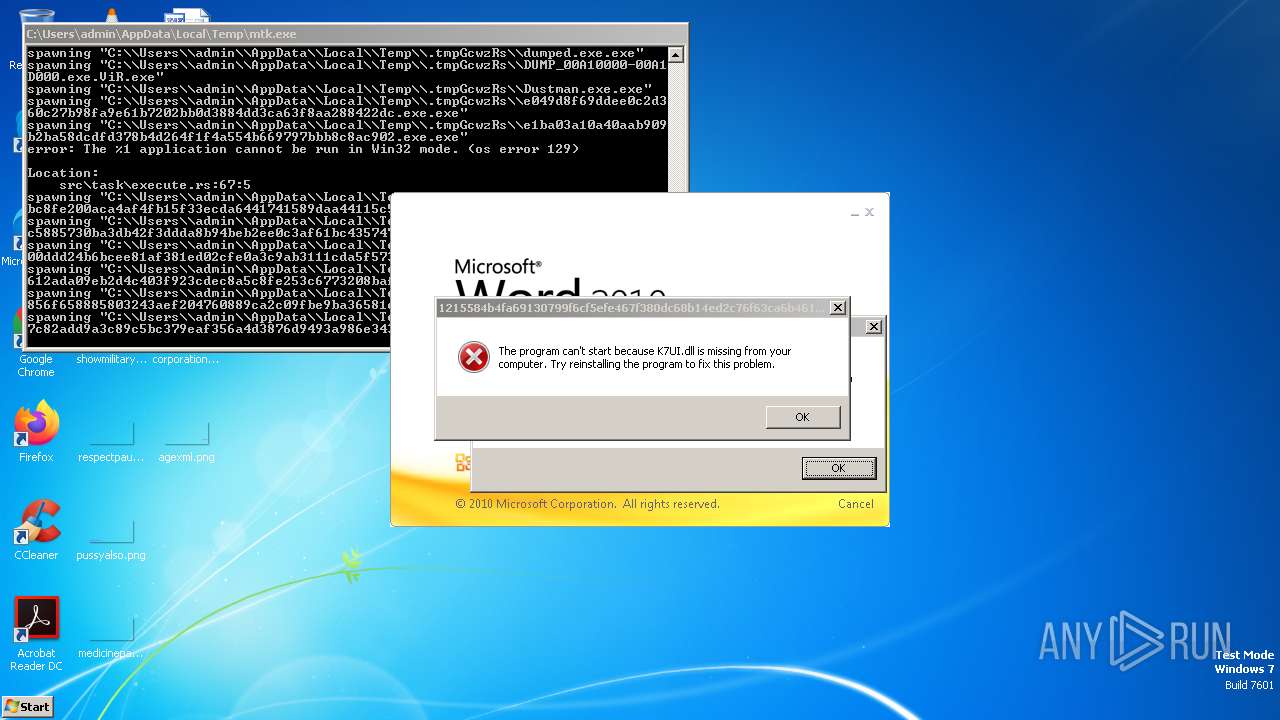
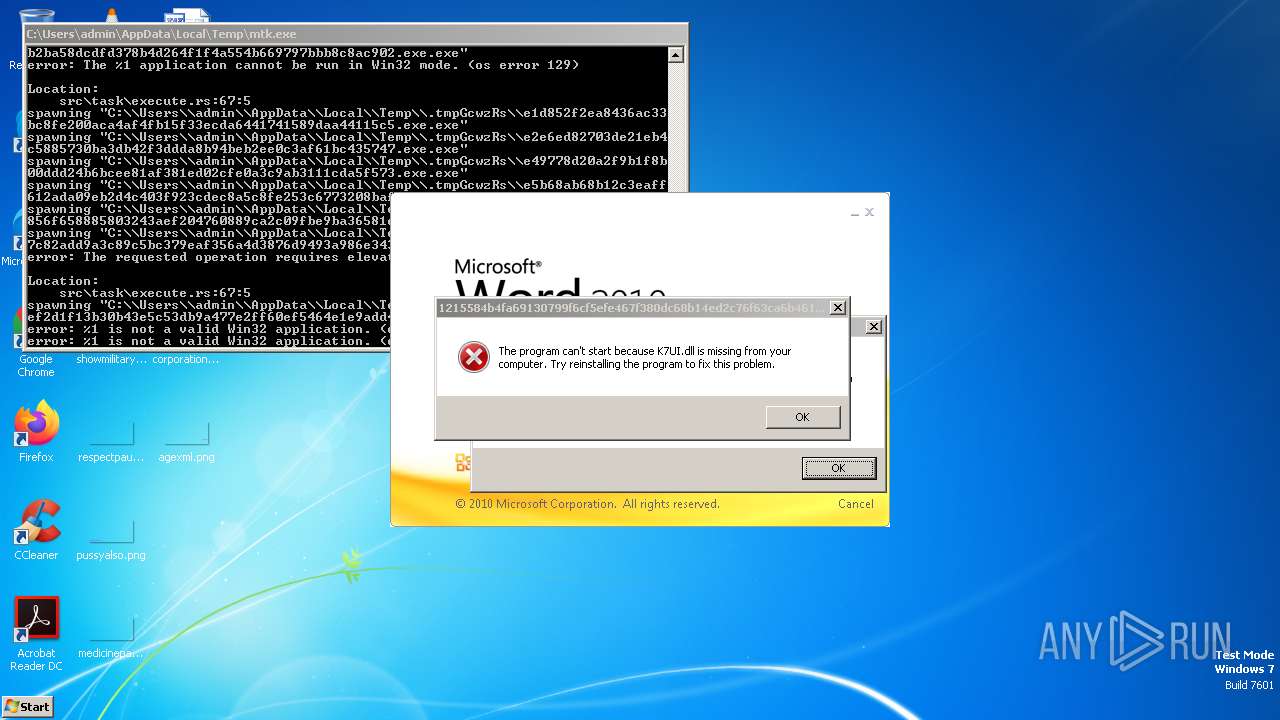
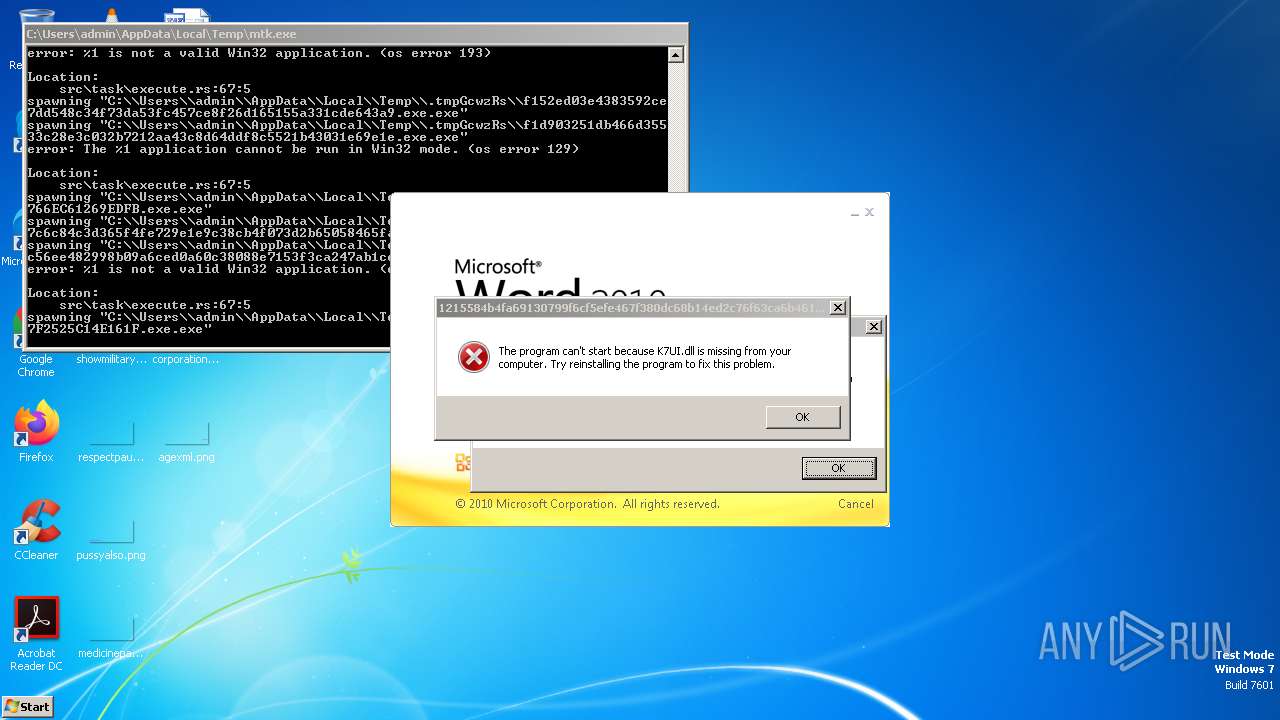
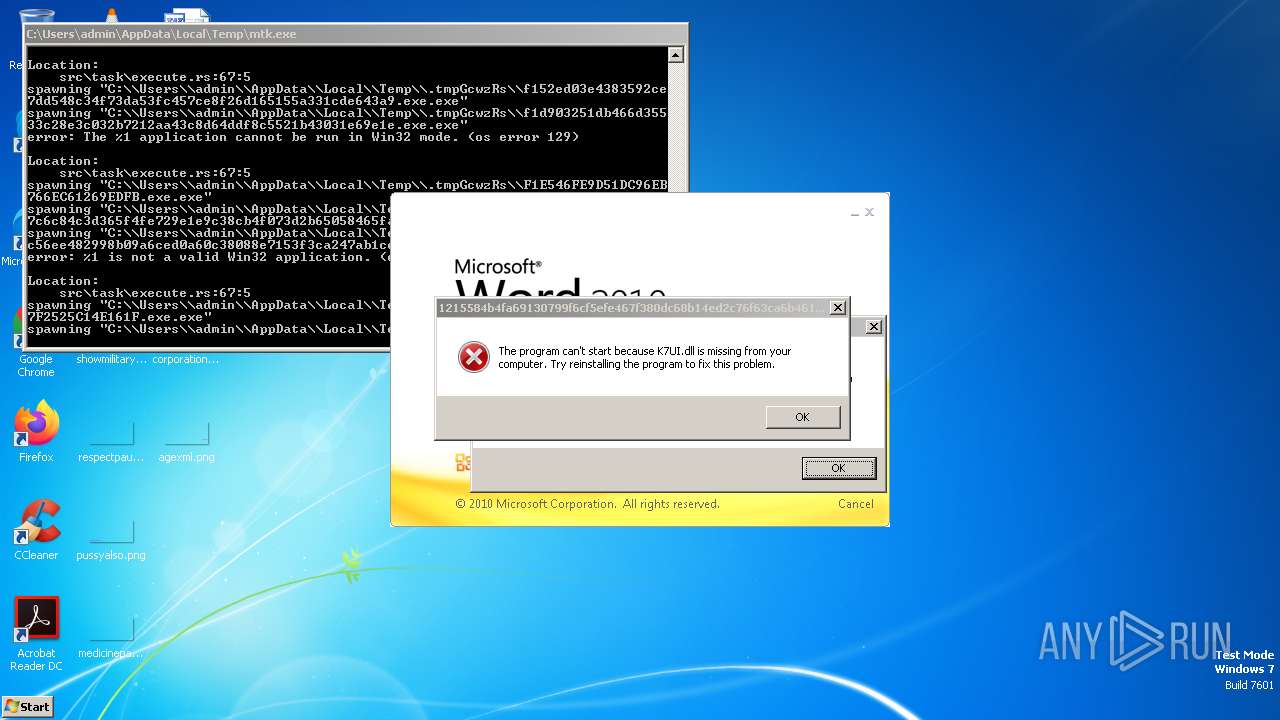
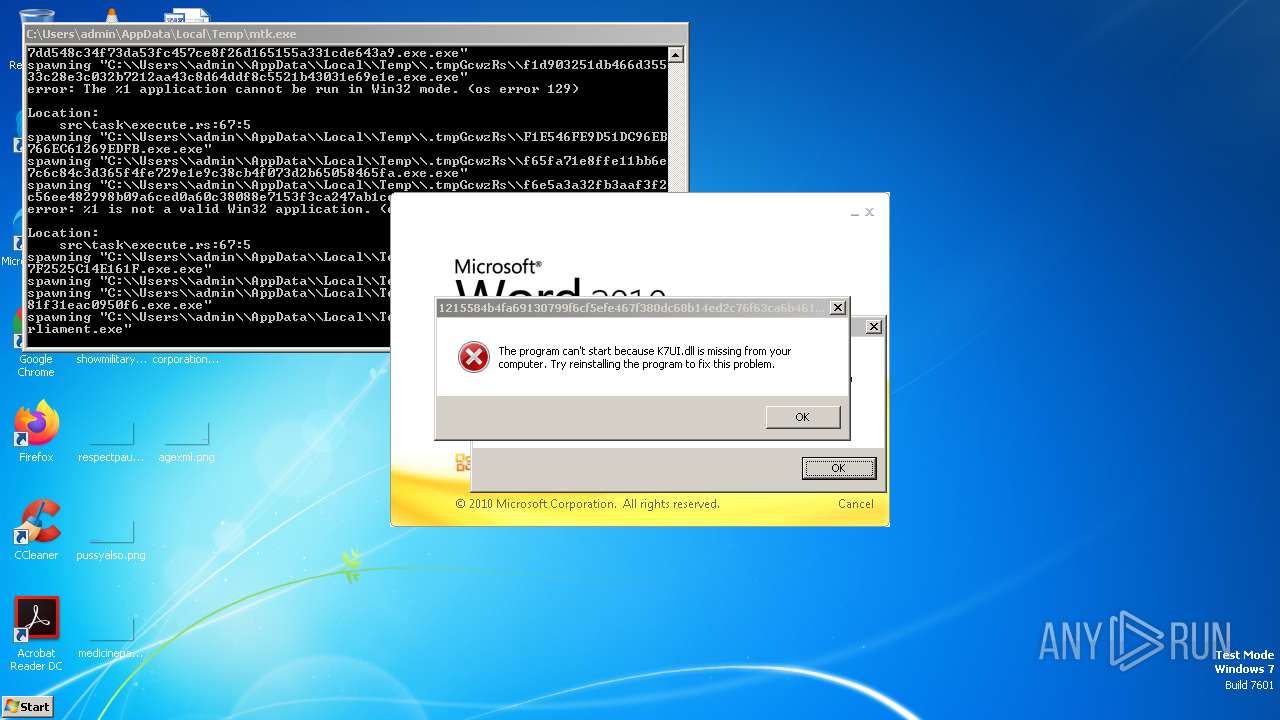
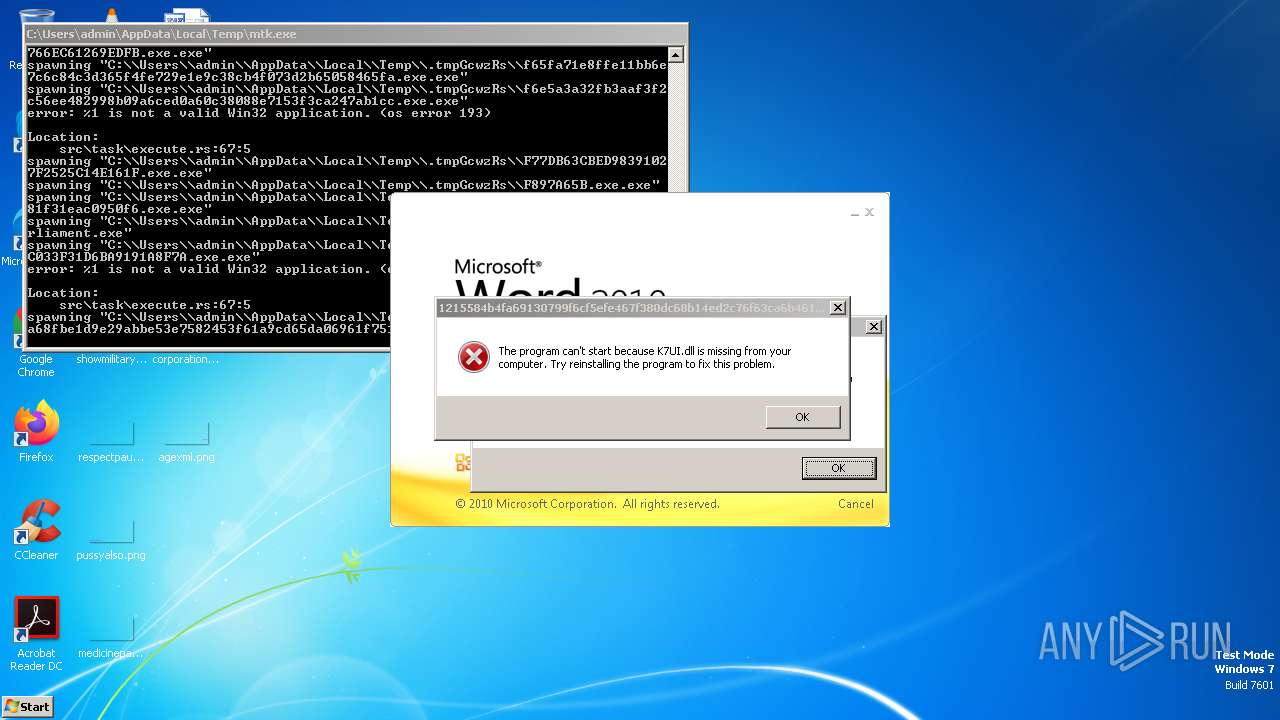
| File name: | mtk.exe |
| Full analysis: | https://app.any.run/tasks/4d56e33a-9ae5-42a1-9c42-e01674b85e09 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | October 24, 2023, 20:15:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 0DBAFF61A0D7EB35C23542FE980C8E30 |
| SHA1: | A65BCE229A1F0143C6F5C86A205DA15D74652335 |
| SHA256: | 0771DDC1515150CF7BB2EAED7CE17DB58BF1F3F963EC60B28E29266763C92594 |
| SSDEEP: | 49152:5hkVUncRtu1kPxXzEgDH/0nl0efk6e4Ath5+hY7hYKJ+NFK2Z0N/eEDNIGuWFlva:qxJDhlEF0N/e06Wrghxt |
MALICIOUS
Application was dropped or rewritten from another process
- 01259a104a0199b794b0c61fcfc657eb766b2caeae68d5c6b164a53a97874257.exe.exe (PID: 2748)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2004)
- 03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe (PID: 992)
- 0442cfabb3212644c4b894a7e4a7e84c00fd23489cc4f96490f9988e6074b6ab.exe.exe (PID: 2728)
- 0468127a19daf4c7bc41015c5640fe1f.exe.exe (PID: 3016)
- 05455efecab4a7931fa53a3c2008d04fc6b539c5e8f451f19b617bd9b3ebcd83.exe.exe (PID: 1968)
- 084a220ba90622cc223b93f32130e9f2d072679f66d1816775bf14832d492b8a.exe.exe (PID: 2144)
- 0dc2ab0ccf783fb39028326a7e8b0ba4eaa148020ec05fc26313ef2bf70f700f.exe.exe (PID: 1424)
- 07529fae9e74be81fd302d022603d9f0796b4b9120b0d6131f75d41b979bbca5.exe.exe (PID: 364)
- 0eb038e7e5edd6ac1b4eee8dd1c51b6d94da24d02ba705e7e7f10b41edf701c2.exe.exe (PID: 2684)
- 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe (PID: 2892)
- 08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe (PID: 2116)
- 0cfc34fa76228b1afc7ce63e284a23ce1cd2927e6159b9dea9702ad9cb2a6300.exe.exe (PID: 2620)
- 1001a8c7f33185217e6e1bdbb8dba9780d475da944684fb4bf1fc04809525887.exe.exe (PID: 2332)
- 1002.exe.exe (PID: 2036)
- 1003.exe.exe (PID: 2224)
- 131.exe.exe (PID: 2584)
- 1215584b4fa69130799f6cf5efe467f380dc68b14ed2c76f63ca6b461ad57246.exe.exe (PID: 1584)
- 17.exe.exe (PID: 2644)
- 15540D149889539308135FA12BEDBCBF.exe.exe (PID: 1088)
- 1952fa94b582e9af9dca596b5e51c585a78b8b1610639e3b878bbfa365e8e908.exe.exe (PID: 1124)
- 19e818d0da361c4feedd456fca63d68d4b024fbbd3d9265f606076c7ee72e8f8.ViR.exe (PID: 2748)
- 1b76fdbd4cd92c7349bc99291137637614f4fb9598ae29df0a39a422611b86f8.exe.exe (PID: 2952)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2888)
- 1D34D800AA3320DC17A5786F8EEC16EE.exe.exe (PID: 1296)
- 1ee894c0b91f3b2f836288c22ebeab44798f222f17c255f557af2260b8c6a32d.exe.exe (PID: 2284)
- 20240431d6eb6816453651b58b37f53950fcc3f0929813806525c5fd97cdc0e1.exe.exe (PID: 2804)
- 2094d105ec70aa98866a83b38a22614cff906b2cf0a08970ed59887383ee7b70.exe.exe (PID: 3040)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2880)
- 21.exe.exe (PID: 792)
- utilview.exe (PID: 1696)
- utilview.exe (PID: 2452)
- 260ebbf392498d00d767a5c5ba695e1a124057c1c01fff2ae76db7853fe4255b.exe.exe (PID: 3088)
- 2a3b92f6180367306d750e59c9b6446b.exe.exe (PID: 3240)
- 323CANON.EXE_WORM_VOBFUS.SM01.exe (PID: 3800)
- gbudn.exe (PID: 4000)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2692)
- KB00653670.exe (PID: 2564)
- gbudn.exe (PID: 7568)
Drops the executable file immediately after the start
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2004)
- mtk.exe (PID: 2612)
- 05455efecab4a7931fa53a3c2008d04fc6b539c5e8f451f19b617bd9b3ebcd83.exe.exe (PID: 1968)
- 08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe (PID: 2116)
- 0eb038e7e5edd6ac1b4eee8dd1c51b6d94da24d02ba705e7e7f10b41edf701c2.exe.exe (PID: 2684)
- 19e818d0da361c4feedd456fca63d68d4b024fbbd3d9265f606076c7ee72e8f8.ViR.exe (PID: 2748)
- 17.exe.exe (PID: 2644)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2692)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2880)
- 2a3b92f6180367306d750e59c9b6446b.exe.exe (PID: 3240)
- 3372c1edab46837f1e973164fa2d726c5c5e17bcb888828ccd7c4dfcc234a370.exe.exe (PID: 2556)
- 23f12c28515e7b9d8b2dd60ef660290ae32434bb50d56a8c8259df4881800971.exe.exe (PID: 2516)
- 0442cfabb3212644c4b894a7e4a7e84c00fd23489cc4f96490f9988e6074b6ab.exe.exe (PID: 2728)
- 3f2781d44c71a2c0509173118dd97e5196db510a65c9f659dc2366fa315fe5e5.exe.exe (PID: 4008)
- frame.exe (PID: 4080)
- 6b91fdb0992ca029c913092db7b4fd94c917c1473953d1ec77c74d030776fe9a.exe.exe (PID: 2880)
- 75b30164a31d305f47f2c3c2121432e6d7b316cfb3deb6b39f78180168bc9472.exe.exe (PID: 4364)
- ggjsona.exe (PID: 3020)
- 73ebf8c9571f00c9923c87e7442f3d9132627163c5a64e40ad4eb1a1f2266de9.exe.exe (PID: 4408)
- 6072a303039b032f1b3b0e596a3eb9a35568cef830a18404c18bb4fffef86fba.exe.exe (PID: 3576)
- 773635768e738bec776dfd7504164b3596e5eee344757dd1ac9a1ad19b452c86.exe.exe (PID: 4720)
- 9b3c6fd39b2809e388255c5651953251920c5c7d5e77da1070ab3c127e8bdc11.exe.exe (PID: 5916)
- 9c17f267f79597ee01515f5ef925375d8a19844830cc46917a3d1b5bcb0ba4c3.exe.exe (PID: 4820)
- a3667153a6322fb8d4cf8869c094a05e995e2954fda833fe14304837ed4fd0bd.exe.exe (PID: 4092)
- 8a0c95be8a40ae5419f7d97bb3e91b2b.exe.exe (PID: 6040)
- 3_4.exe.exe (PID: 1968)
- ArdamaxKeylogger_E33AF9E602CBB7AC3634C2608150DD18.exe.exe (PID: 5628)
- blanca de nieve.scr.exe (PID: 7436)
- b81b10bdf4f29347979ea8a1715cbfc560e3452ba9fffcc33cd19a3dc47083a4.exe.exe (PID: 6752)
- C116CD083284CC599C024C3479CA9B70_2.tmp_.exe (PID: 7904)
- AAA._xe.exe (PID: 5840)
- c7128e2772b4f8c59943028e205d1b23c07f36206c1c61a05645c7bf143b24ee.exe.exe (PID: 6072)
- Gadget.exe (PID: 8096)
- c0cf40b8830d666a24bdd4febdc162e95aa30ed968fa3675e26ad97b2e88e03a.exe.exe (PID: 7544)
- bea95bebec95e0893a845f62e832d7cf.exe.ViR.exe (PID: 6912)
- cf65cc6e4b2b0c3f602b16398c8c30c277b8cfaed689fe7cb61b92560d4e5b1b.exe.exe (PID: 6216)
- e1d852f2ea8436ac33bc8fe200aca4af4fb15f33ecda6441741589daa44115c5.exe.exe (PID: 10420)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
- Dustman.exe.exe (PID: 11844)
- e49778d20a2f9b1f8b00ddd24b6bcee81af381ed02cfe0a3c9ab3111cda5f573.exe.exe (PID: 13136)
- FLASH829.EXE.exe (PID: 24736)
- 3b4497c7f8c89bf22c984854ac7603573a53b95ed147e80c0f19e549e2b65693.exe.exe (PID: 3172)
Application was injected by another process
- WerFault.exe (PID: 4004)
- WerFault.exe (PID: 4012)
- WerFault.exe (PID: 1176)
Runs injected code in another process
- KB00653670.exe (PID: 2564)
Uses Task Scheduler to run other applications
- gbudn.exe (PID: 4000)
Deletes shadow copies
- ggjsona.exe (PID: 3020)
- 5d40615701c48a122e44f831e7c8643d07765629a83b15d090587f469c77693d.exe.exe (PID: 3320)
Starts NET.EXE for service management
- 5d40615701c48a122e44f831e7c8643d07765629a83b15d090587f469c77693d.exe.exe (PID: 3320)
- net.exe (PID: 3552)
- net.exe (PID: 2288)
- net.exe (PID: 3512)
- net.exe (PID: 4704)
- net.exe (PID: 4304)
- net.exe (PID: 4496)
- net.exe (PID: 3560)
- net.exe (PID: 984)
- net.exe (PID: 4320)
- net.exe (PID: 4432)
- net.exe (PID: 2880)
- net.exe (PID: 4688)
- net.exe (PID: 4736)
- net.exe (PID: 2688)
- net.exe (PID: 3728)
- net.exe (PID: 3876)
- net.exe (PID: 4536)
- net.exe (PID: 4904)
- net.exe (PID: 3192)
- net.exe (PID: 3140)
- net.exe (PID: 5016)
- net.exe (PID: 3144)
- net.exe (PID: 5348)
- net.exe (PID: 3796)
- net.exe (PID: 752)
- net.exe (PID: 5700)
Starts CMD.EXE for self-deleting
- 5a765351046fea1490d20f25.exe.exe (PID: 2464)
SUSPICIOUS
Reads settings of System Certificates
- mtk.exe (PID: 2612)
Reads the Internet Settings
- mtk.exe (PID: 2612)
- 0468127a19daf4c7bc41015c5640fe1f.exe.exe (PID: 3016)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2004)
- 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe (PID: 2892)
- cmd.exe (PID: 2468)
- utilview.exe (PID: 2452)
Process drops legitimate windows executable
- mtk.exe (PID: 2612)
- 19e818d0da361c4feedd456fca63d68d4b024fbbd3d9265f606076c7ee72e8f8.ViR.exe (PID: 2748)
- svchost.exe (PID: 3440)
- blanca de nieve.scr.exe (PID: 7436)
- AAA._xe.exe (PID: 5840)
- svchost.exe (PID: 5284)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
- FLASH829.EXE.exe (PID: 24736)
The process creates files with name similar to system file names
- mtk.exe (PID: 2612)
Creates executable files that already exist in Windows
- mtk.exe (PID: 2612)
Executing commands from a ".bat" file
- 08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe (PID: 2116)
- 17.exe.exe (PID: 2644)
- 9c17f267f79597ee01515f5ef925375d8a19844830cc46917a3d1b5bcb0ba4c3.exe.exe (PID: 4820)
- 9b3c6fd39b2809e388255c5651953251920c5c7d5e77da1070ab3c127e8bdc11.exe.exe (PID: 5916)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
Starts CMD.EXE for commands execution
- 08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe (PID: 2116)
- 0eb038e7e5edd6ac1b4eee8dd1c51b6d94da24d02ba705e7e7f10b41edf701c2.exe.exe (PID: 2684)
- 17.exe.exe (PID: 2644)
- 3372c1edab46837f1e973164fa2d726c5c5e17bcb888828ccd7c4dfcc234a370.exe.exe (PID: 2556)
- 07529fae9e74be81fd302d022603d9f0796b4b9120b0d6131f75d41b979bbca5.exe.exe (PID: 364)
- 03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe (PID: 992)
- 1952fa94b582e9af9dca596b5e51c585a78b8b1610639e3b878bbfa365e8e908.exe.exe (PID: 1124)
- 30196c83a1f857d36fde160d55bd4e5b5d50fbb082bd846db295cbe0f9d35cfb.exe.exe (PID: 3448)
- 3bedb4bdb17718fda1edd1a8fa4289dc61fdda598474b5648414e4565e88ecd5.exe.exe (PID: 3156)
- 388f5bc2f088769b361dfe8a45f0d5237c4580b287612422a03babe6994339ff.exe.exe (PID: 4040)
- 6b91fdb0992ca029c913092db7b4fd94c917c1473953d1ec77c74d030776fe9a.exe.exe (PID: 2880)
- 50414f60d7e24d25f9ebb68f99d67a46e8b12458474ac503b6e0d0562075a985.exe.exe (PID: 3404)
- 5663b2d4a4aec55d5d6fb507e3fdcb92ffc978d411de68b084c37f86af6d2e19.exe.exe (PID: 3104)
- 52cb02da0462fdd08d537b2c949e2e252f7a7a88354d596e9f5c9f1498d1c68f.exe.exe (PID: 3584)
- 773635768e738bec776dfd7504164b3596e5eee344757dd1ac9a1ad19b452c86.exe.exe (PID: 4720)
- 5d491ea5705e90c817cf0f5211c9edbcd5291fe8bd4cc69cdb58e8d0e6b6d1fe.exe.exe (PID: 3396)
- 9b3c6fd39b2809e388255c5651953251920c5c7d5e77da1070ab3c127e8bdc11.exe.exe (PID: 5916)
- 9c17f267f79597ee01515f5ef925375d8a19844830cc46917a3d1b5bcb0ba4c3.exe.exe (PID: 4820)
- a3667153a6322fb8d4cf8869c094a05e995e2954fda833fe14304837ed4fd0bd.exe.exe (PID: 4092)
- 5a765351046fea1490d20f25.exe.exe (PID: 2464)
- bc12d7052e6cfce8f16625ca8b88803cd4e58356eb32fe62667336d4dee708a3.exe.exe (PID: 3824)
- bdef2ddcd8d4d66a42c9cbafd5cf7d86c4c0e3ed8c45cc734742c5da2fb573f7.exe.exe (PID: 5012)
- e1d852f2ea8436ac33bc8fe200aca4af4fb15f33ecda6441741589daa44115c5.exe.exe (PID: 10420)
- a98099541168c7f36b107e24e9c80c9125fefb787ae720799b03bb4425aba1a9.exe.exe (PID: 4588)
- Dustman.exe.exe (PID: 11844)
- dea53e331d3b9f21354147f60902f6e132f06183ed2f4a28e67816f9cb140a90.exe.exe (PID: 11752)
- e2e6ed82703de21eb4c5885730ba3db42f3ddda8b94beb2ee0c3af61bc435747.exe.exe (PID: 11868)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
- d8fdcdaad652c19f4f4676cd2f89ae834dbc19e2759a206044b18601875f2726.exe.exe (PID: 10108)
Application launched itself
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2888)
- utilview.exe (PID: 1696)
- 3f2781d44c71a2c0509173118dd97e5196db510a65c9f659dc2366fa315fe5e5.exe.exe (PID: 3460)
- 40accff9b9d71053d4d6f95e6efd7eca1bb1ef5af77c319fe5a4b429eb373990.exe.exe (PID: 3204)
- 51B4EF5DC9D26B7A26E214CEE90598631E2EAA67.exe.exe (PID: 2800)
- 5a765351046fea1490d20f25.exe.exe (PID: 3440)
- syhonay.exe (PID: 2880)
- 73ebf8c9571f00c9923c87e7442f3d9132627163c5a64e40ad4eb1a1f2266de9.exe.exe (PID: 4368)
- wovoletir.exe (PID: 5424)
- a98099541168c7f36b107e24e9c80c9125fefb787ae720799b03bb4425aba1a9.exe.exe (PID: 4588)
Starts itself from another location
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2880)
- 17.exe.exe (PID: 2644)
- 2a3b92f6180367306d750e59c9b6446b.exe.exe (PID: 3240)
- 3372c1edab46837f1e973164fa2d726c5c5e17bcb888828ccd7c4dfcc234a370.exe.exe (PID: 2556)
- 23f12c28515e7b9d8b2dd60ef660290ae32434bb50d56a8c8259df4881800971.exe.exe (PID: 2516)
- 3f2781d44c71a2c0509173118dd97e5196db510a65c9f659dc2366fa315fe5e5.exe.exe (PID: 4008)
- 0442cfabb3212644c4b894a7e4a7e84c00fd23489cc4f96490f9988e6074b6ab.exe.exe (PID: 2728)
- 73ebf8c9571f00c9923c87e7442f3d9132627163c5a64e40ad4eb1a1f2266de9.exe.exe (PID: 4408)
- 8a0c95be8a40ae5419f7d97bb3e91b2b.exe.exe (PID: 6040)
- 3_4.exe.exe (PID: 1968)
- Gadget.exe (PID: 8096)
- c0cf40b8830d666a24bdd4febdc162e95aa30ed968fa3675e26ad97b2e88e03a.exe.exe (PID: 7544)
- e49778d20a2f9b1f8b00ddd24b6bcee81af381ed02cfe0a3c9ab3111cda5f573.exe.exe (PID: 13136)
Uses TASKKILL.EXE to kill process
- 5d40615701c48a122e44f831e7c8643d07765629a83b15d090587f469c77693d.exe.exe (PID: 3320)
The process executes via Task Scheduler
- FlashUpdate.exe (PID: 5744)
- gbudn.exe (PID: 7568)
- 4cc343.exe (PID: 13728)
The process executes JS scripts
- afa8d185de2f357082ed4042fc057a6d7300f603d3bfdbe7e6c351868e45e477.exe.exe (PID: 4548)
Writes files like Keylogger logs
- ArdamaxKeylogger_E33AF9E602CBB7AC3634C2608150DD18.exe.exe (PID: 5628)
Drops a system driver (possible attempt to evade defenses)
- Dustman.exe.exe (PID: 11844)
Uses ICACLS.EXE to modify access control lists
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
Uses ATTRIB.EXE to modify file attributes
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
INFO
Checks proxy server information
- mtk.exe (PID: 2612)
- 0468127a19daf4c7bc41015c5640fe1f.exe.exe (PID: 3016)
- utilview.exe (PID: 2452)
Checks supported languages
- mtk.exe (PID: 2612)
- 01259a104a0199b794b0c61fcfc657eb766b2caeae68d5c6b164a53a97874257.exe.exe (PID: 2748)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2004)
- 0468127a19daf4c7bc41015c5640fe1f.exe.exe (PID: 3016)
- 0442cfabb3212644c4b894a7e4a7e84c00fd23489cc4f96490f9988e6074b6ab.exe.exe (PID: 2728)
- 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe (PID: 2892)
- 07529fae9e74be81fd302d022603d9f0796b4b9120b0d6131f75d41b979bbca5.exe.exe (PID: 364)
- 05455efecab4a7931fa53a3c2008d04fc6b539c5e8f451f19b617bd9b3ebcd83.exe.exe (PID: 1968)
- 08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe (PID: 2116)
- 0cfc34fa76228b1afc7ce63e284a23ce1cd2927e6159b9dea9702ad9cb2a6300.exe.exe (PID: 2620)
- 084a220ba90622cc223b93f32130e9f2d072679f66d1816775bf14832d492b8a.exe.exe (PID: 2144)
- 03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe (PID: 992)
- 0dc2ab0ccf783fb39028326a7e8b0ba4eaa148020ec05fc26313ef2bf70f700f.exe.exe (PID: 1424)
- 0eb038e7e5edd6ac1b4eee8dd1c51b6d94da24d02ba705e7e7f10b41edf701c2.exe.exe (PID: 2684)
- 1002.exe.exe (PID: 2036)
- 1003.exe.exe (PID: 2224)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2692)
- 1952fa94b582e9af9dca596b5e51c585a78b8b1610639e3b878bbfa365e8e908.exe.exe (PID: 1124)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2888)
- 17.exe.exe (PID: 2644)
- 1b76fdbd4cd92c7349bc99291137637614f4fb9598ae29df0a39a422611b86f8.exe.exe (PID: 2952)
- 1D34D800AA3320DC17A5786F8EEC16EE.exe.exe (PID: 1296)
- 1ee894c0b91f3b2f836288c22ebeab44798f222f17c255f557af2260b8c6a32d.exe.exe (PID: 2284)
- 19e818d0da361c4feedd456fca63d68d4b024fbbd3d9265f606076c7ee72e8f8.ViR.exe (PID: 2748)
- 20240431d6eb6816453651b58b37f53950fcc3f0929813806525c5fd97cdc0e1.exe.exe (PID: 2804)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2880)
- 2094d105ec70aa98866a83b38a22614cff906b2cf0a08970ed59887383ee7b70.exe.exe (PID: 3040)
- KB00653670.exe (PID: 2564)
- 23eeb35780faf868a7b17b8e8da364d71bae0e46c1ababddddddecbdbd2c2c64.exe.exe (PID: 2336)
- utilview.exe (PID: 2452)
- 2a3b92f6180367306d750e59c9b6446b.exe.exe (PID: 3240)
- 30196c83a1f857d36fde160d55bd4e5b5d50fbb082bd846db295cbe0f9d35cfb.exe.exe (PID: 3448)
- 323CANON.EXE_WORM_VOBFUS.SM01.exe (PID: 3800)
- 301210D5557D9BA34F401D3EF7A7276F.exe.exe (PID: 3264)
- utilview.exe (PID: 1696)
Reads the machine GUID from the registry
- mtk.exe (PID: 2612)
- 01259a104a0199b794b0c61fcfc657eb766b2caeae68d5c6b164a53a97874257.exe.exe (PID: 2748)
- 0cfc34fa76228b1afc7ce63e284a23ce1cd2927e6159b9dea9702ad9cb2a6300.exe.exe (PID: 2620)
- 0dc2ab0ccf783fb39028326a7e8b0ba4eaa148020ec05fc26313ef2bf70f700f.exe.exe (PID: 1424)
- 084a220ba90622cc223b93f32130e9f2d072679f66d1816775bf14832d492b8a.exe.exe (PID: 2144)
- 1002.exe.exe (PID: 2036)
- 1003.exe.exe (PID: 2224)
- 0468127a19daf4c7bc41015c5640fe1f.exe.exe (PID: 3016)
Reads the computer name
- mtk.exe (PID: 2612)
- 01259a104a0199b794b0c61fcfc657eb766b2caeae68d5c6b164a53a97874257.exe.exe (PID: 2748)
- 0468127a19daf4c7bc41015c5640fe1f.exe.exe (PID: 3016)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2004)
- 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe (PID: 2892)
- 0cfc34fa76228b1afc7ce63e284a23ce1cd2927e6159b9dea9702ad9cb2a6300.exe.exe (PID: 2620)
- 084a220ba90622cc223b93f32130e9f2d072679f66d1816775bf14832d492b8a.exe.exe (PID: 2144)
- 0dc2ab0ccf783fb39028326a7e8b0ba4eaa148020ec05fc26313ef2bf70f700f.exe.exe (PID: 1424)
- 17.exe.exe (PID: 2644)
- 1b76fdbd4cd92c7349bc99291137637614f4fb9598ae29df0a39a422611b86f8.exe.exe (PID: 2952)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2880)
- KB00653670.exe (PID: 2564)
- utilview.exe (PID: 2452)
- 0442cfabb3212644c4b894a7e4a7e84c00fd23489cc4f96490f9988e6074b6ab.exe.exe (PID: 2728)
- 07529fae9e74be81fd302d022603d9f0796b4b9120b0d6131f75d41b979bbca5.exe.exe (PID: 364)
- 0eb038e7e5edd6ac1b4eee8dd1c51b6d94da24d02ba705e7e7f10b41edf701c2.exe.exe (PID: 2684)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2692)
- 1D34D800AA3320DC17A5786F8EEC16EE.exe.exe (PID: 1296)
- 1952fa94b582e9af9dca596b5e51c585a78b8b1610639e3b878bbfa365e8e908.exe.exe (PID: 1124)
- 23eeb35780faf868a7b17b8e8da364d71bae0e46c1ababddddddecbdbd2c2c64.exe.exe (PID: 2336)
- 2094d105ec70aa98866a83b38a22614cff906b2cf0a08970ed59887383ee7b70.exe.exe (PID: 3040)
- 323CANON.EXE_WORM_VOBFUS.SM01.exe (PID: 3800)
- 20240431d6eb6816453651b58b37f53950fcc3f0929813806525c5fd97cdc0e1.exe.exe (PID: 2804)
- 30196c83a1f857d36fde160d55bd4e5b5d50fbb082bd846db295cbe0f9d35cfb.exe.exe (PID: 3448)
- 301210D5557D9BA34F401D3EF7A7276F.exe.exe (PID: 3264)
- 2a3b92f6180367306d750e59c9b6446b.exe.exe (PID: 3240)
- 03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe (PID: 992)
- 1003.exe.exe (PID: 2224)
- 1002.exe.exe (PID: 2036)
- 1ee894c0b91f3b2f836288c22ebeab44798f222f17c255f557af2260b8c6a32d.exe.exe (PID: 2284)
Create files in a temporary directory
- mtk.exe (PID: 2612)
- 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe (PID: 2004)
- 0442cfabb3212644c4b894a7e4a7e84c00fd23489cc4f96490f9988e6074b6ab.exe.exe (PID: 2728)
- 05455efecab4a7931fa53a3c2008d04fc6b539c5e8f451f19b617bd9b3ebcd83.exe.exe (PID: 1968)
- 08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe (PID: 2116)
- 1b76fdbd4cd92c7349bc99291137637614f4fb9598ae29df0a39a422611b86f8.exe.exe (PID: 2952)
- 0eb038e7e5edd6ac1b4eee8dd1c51b6d94da24d02ba705e7e7f10b41edf701c2.exe.exe (PID: 2684)
- 1b893ca3b782679b1e5d1afecb75be7bcc145b5da21a30f6c18dbddc9c6de4e7.exe.exe (PID: 2880)
- 17.exe.exe (PID: 2644)
Dropped object may contain TOR URL's
- mtk.exe (PID: 2612)
- 3372c1edab46837f1e973164fa2d726c5c5e17bcb888828ccd7c4dfcc234a370.exe.exe (PID: 2556)
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
- cerber.exe.exe (PID: 7496)
Reads Environment values
- 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe (PID: 2892)
- 1b76fdbd4cd92c7349bc99291137637614f4fb9598ae29df0a39a422611b86f8.exe.exe (PID: 2952)
Creates files or folders in the user directory
- 19e818d0da361c4feedd456fca63d68d4b024fbbd3d9265f606076c7ee72e8f8.ViR.exe (PID: 2748)
- 17.exe.exe (PID: 2644)
Reads product name
- 1b76fdbd4cd92c7349bc99291137637614f4fb9598ae29df0a39a422611b86f8.exe.exe (PID: 2952)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2280)
- svchost.exe (PID: 3440)
- svchost.exe (PID: 5284)
- svchost.exe (PID: 7272)
Application launched itself
- iexplore.exe (PID: 2280)
The dropped object may contain a URL to Tor Browser
- ed01ebfbc9eb5bbea545af4d01bf5f1071661840480439c6e5babe8e080e41aa.exe.exe (PID: 17128)
- cerber.exe.exe (PID: 7496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| Subsystem: | Windows command line |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x28032c |
| UninitializedDataSize: | - |
| InitializedDataSize: | 1511936 |
| CodeSize: | 2664960 |
| LinkerVersion: | 14.37 |
| PEType: | PE32+ |
| ImageFileCharacteristics: | Executable, Large address aware |
| TimeStamp: | 2023:10:24 19:43:43+00:00 |
| MachineType: | AMD AMD64 |
Total processes
505
Monitored processes
365
Malicious processes
37
Suspicious processes
22
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\64442cceb7d618e70c62d461cfaafdb8e653b8d98ac4765a6b3d8fd1ea3bce15.exe.exe" | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\64442cceb7d618e70c62d461cfaafdb8e653b8d98ac4765a6b3d8fd1ea3bce15.exe.exe | — | mtk.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 0 Version: 1.00 | |||||||||||||||
| 364 | "C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\07529fae9e74be81fd302d022603d9f0796b4b9120b0d6131f75d41b979bbca5.exe.exe" | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\07529fae9e74be81fd302d022603d9f0796b4b9120b0d6131f75d41b979bbca5.exe.exe | — | mtk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Help Service Exit code: 0 Version: 2, 0, 0, 2 Modules
| |||||||||||||||
| 416 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\Public\Video\movie.mp4" | C:\Program Files\VideoLAN\VLC\vlc.exe | — | 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 2.2.6 | |||||||||||||||
| 588 | "C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\8c213b3707b0b042d769fdf543c6e8bd7c127cea6a9bc989eaf241a1505d1ed9.exe.exe" | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\8c213b3707b0b042d769fdf543c6e8bd7c127cea6a9bc989eaf241a1505d1ed9.exe.exe | — | mtk.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 600 | C:\Windows\system32\net1 stop BackupExecJobEngine /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 752 | "net.exe" stop CASAD2DWebSvc /y | C:\Windows\SysWOW64\net.exe | — | 5d40615701c48a122e44f831e7c8643d07765629a83b15d090587f469c77693d.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 792 | "C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\21.exe.exe" | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\21.exe.exe | — | mtk.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 984 | "net.exe" stop ccSetMgr /y | C:\Windows\SysWOW64\net.exe | — | 5d40615701c48a122e44f831e7c8643d07765629a83b15d090587f469c77693d.exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 984 | C:\Windows\system32\net1 stop PDVFSService /y | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 992 | "C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe" | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe | — | mtk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Help Service Exit code: 0 Version: 2, 0, 0, 2 Modules
| |||||||||||||||
Total events
4 866
Read events
4 786
Write events
80
Delete events
0
Modification events
| (PID) Process: | (2612) mtk.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\156\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2004) 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2004) 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2004) 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2004) 0283c0f02307adc4ee46c0382df4b5d7b4eb80114fbaf5cb7fe5412f027d165e.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3016) 0468127a19daf4c7bc41015c5640fe1f.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3016) 0468127a19daf4c7bc41015c5640fe1f.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000C1000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3016) 0468127a19daf4c7bc41015c5640fe1f.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3016) 0468127a19daf4c7bc41015c5640fe1f.exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2468) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
584
Suspicious files
926
Text files
147
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2612 | mtk.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:26B8C301554A9D8BCCCF4DD93016E383 | SHA256:AA84904EB011D4EA7CC847AB1E70617FB2654B6CD491876D49F67931E7364225 | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\TarCD00.tmp | binary | |
MD5:9441737383D21192400ECA82FDA910EC | SHA256:BC3A6E84E41FAEB57E7C21AA3B60C2A64777107009727C5B7C0ED8FE658909E5 | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\01259a104a0199b794b0c61fcfc657eb766b2caeae68d5c6b164a53a97874257.exe.exe | executable | |
MD5:460B288A581CDEB5F831D102CB6D198B | SHA256:01259A104A0199B794B0C61FCFC657EB766B2CAEAE68D5C6B164A53A97874257 | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\0dc2ab0ccf783fb39028326a7e8b0ba4eaa148020ec05fc26313ef2bf70f700f.exe.exe | executable | |
MD5:77B645EF1C599F289F3D462A09048C49 | SHA256:0DC2AB0CCF783FB39028326A7E8B0BA4EAA148020EC05FC26313EF2BF70F700F | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\0cfc34fa76228b1afc7ce63e284a23ce1cd2927e6159b9dea9702ad9cb2a6300.exe.exe | executable | |
MD5:34409ABA1F76045AA0255E49DE16D586 | SHA256:0CFC34FA76228B1AFC7CE63E284A23CE1CD2927E6159B9DEA9702AD9CB2A6300 | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\03641e5632673615f23b2a8325d7355c4499a40f47b6ae094606a73c56e24ad0.exe.exe | executable | |
MD5:2B9106E8DF3AA98C3654A4E0733D83E7 | SHA256:03641E5632673615F23B2A8325D7355C4499A40F47B6AE094606A73C56E24AD0 | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe | executable | |
MD5:60D083B7C74CC84F38074A5D02A2C07C | SHA256:0D7D4DC173C88C4F72C8F9F419AE8473D044F4B3E8F32E4A0F34FE4BBC698776 | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\CabCCFF.tmp | compressed | |
MD5:F3441B8572AAE8801C04F3060B550443 | SHA256:6720349E7D82EE0A8E73920D3C2B7CB2912D9FCF2EDB6FD98F2F12820158B0BF | |||
| 2612 | mtk.exe | C:\Users\admin\AppData\Local\Temp\.tmpGcwzRs\08fd696873ed9df967a991fb397fe11e54a4367c81c6660575e1413b440c3af2.exe.exe | executable | |
MD5:C4DE3FEA790F8FF6452016DB5D7AA33F | SHA256:08FD696873ED9DF967A991FB397FE11E54A4367C81C6660575E1413B440C3AF2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
1 142
DNS requests
68
Threats
107
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 404 | 188.40.187.155:80 | http://mynexa.io/hfv23svj2/plugins/scr.dll | unknown | — | — | unknown |
— | — | GET | 404 | 123.57.60.215:80 | http://123.57.60.215/DotNetLoader40.exe | unknown | text | 19 b | unknown |
— | — | GET | 404 | 123.57.60.215:80 | http://123.57.60.215/beacon.txt | unknown | text | 19 b | unknown |
— | — | GET | 404 | 123.57.60.215:80 | http://123.57.60.215/beacon.txt | unknown | text | 19 b | unknown |
2612 | mtk.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e5937c9360690284 | unknown | compressed | 61.6 Kb | unknown |
— | — | GET | 404 | 123.57.60.215:80 | http://123.57.60.215/DotNetLoader40.exe | unknown | text | 19 b | unknown |
— | — | GET | 200 | 13.248.169.48:80 | http://yumproject.com/wp-content/uploads/2014/11/questd.pdf | unknown | html | 12.1 Kb | unknown |
— | — | GET | 404 | 58.158.177.102:80 | http://flash-update.buyonebuy.top/flach.php | unknown | html | 207 b | unknown |
— | — | GET | 200 | 13.248.169.48:80 | http://yumproject.com/wp-content/uploads/2014/11/questd.pdf | unknown | html | 12.1 Kb | unknown |
— | — | GET | 200 | 132.226.8.169:80 | http://checkip.dyndns.org/ | unknown | html | 106 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2612 | mtk.exe | 45.67.85.72:443 | m.crep.vip | — | US | unknown |
2612 | mtk.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2892 | 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe | 58.158.177.102:443 | flash-update.buyonebuy.top | ARTERIA Networks Corporation | JP | unknown |
3016 | 0468127a19daf4c7bc41015c5640fe1f.exe.exe | 193.135.12.107:80 | — | LLC Baxet | RU | malicious |
2452 | utilview.exe | 132.226.8.169:80 | checkip.dyndns.org | ORACLE-BMC-31898 | JP | unknown |
— | — | 95.181.46.38:14307 | — | E-Light-Telecom Ltd. | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
m.crep.vip |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
flash-update.buyonebuy.top |
| unknown |
checkip.dyndns.org |
| shared |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
exusin.ru |
| unknown |
imagisp.ru |
| unknown |
cudgewit.ru |
| unknown |
mynexa.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
324 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
324 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Query (checkip .dyndns .org) |
324 | svchost.exe | Misc activity | AV INFO Query to checkip.dyndns. Domain |
— | — | A Network Trojan was detected | ET MALWARE Common Upatre Header Structure 2 |
— | — | Device Retrieving External IP Address Detected | ET MALWARE Upatre External IP Check |
— | — | A Network Trojan was detected | ET MALWARE Mazilla Suspicious User-Agent Jan 15 2015 |
— | — | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup - checkip.dyndns.org |
2892 | 0d7d4dc173c88c4f72c8f9f419ae8473d044f4b3e8f32e4a0f34fe4bbc698776.exe.exe | Domain Observed Used for C2 Detected | ET MALWARE Malicious SSL certificate detected (Possible Sinkhole) |
— | — | A Network Trojan was detected | ET MALWARE Common Upatre Header Structure 2 |
— | — | A Network Trojan was detected | ET MALWARE Mazilla Suspicious User-Agent Jan 15 2015 |
29 ETPRO signatures available at the full report
Process | Message |
|---|---|
vlc.exe | core libvlc: one instance mode ENABLED
|
7249b1a5082c9d9654d9fac3bb5e965ea23e395554d3351b77dd4f29677426fe.exe.exe | Script Error |
7249b1a5082c9d9654d9fac3bb5e965ea23e395554d3351b77dd4f29677426fe.exe.exe | Run OK |