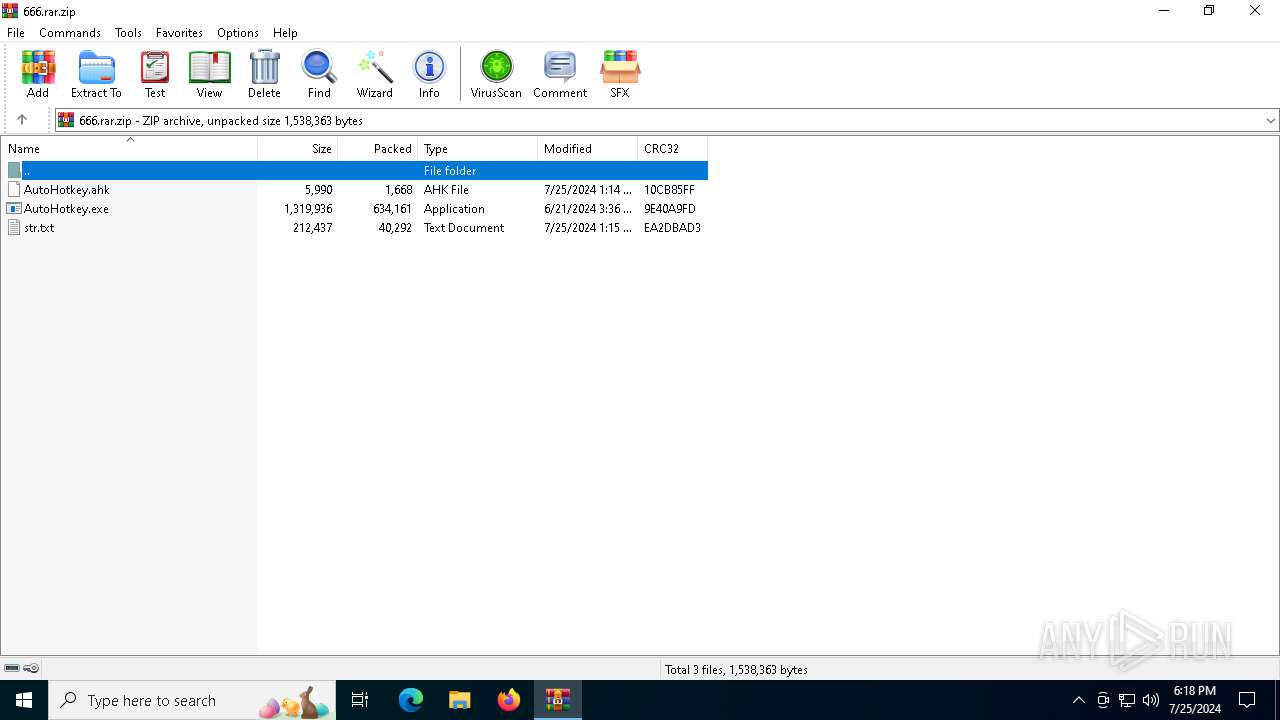
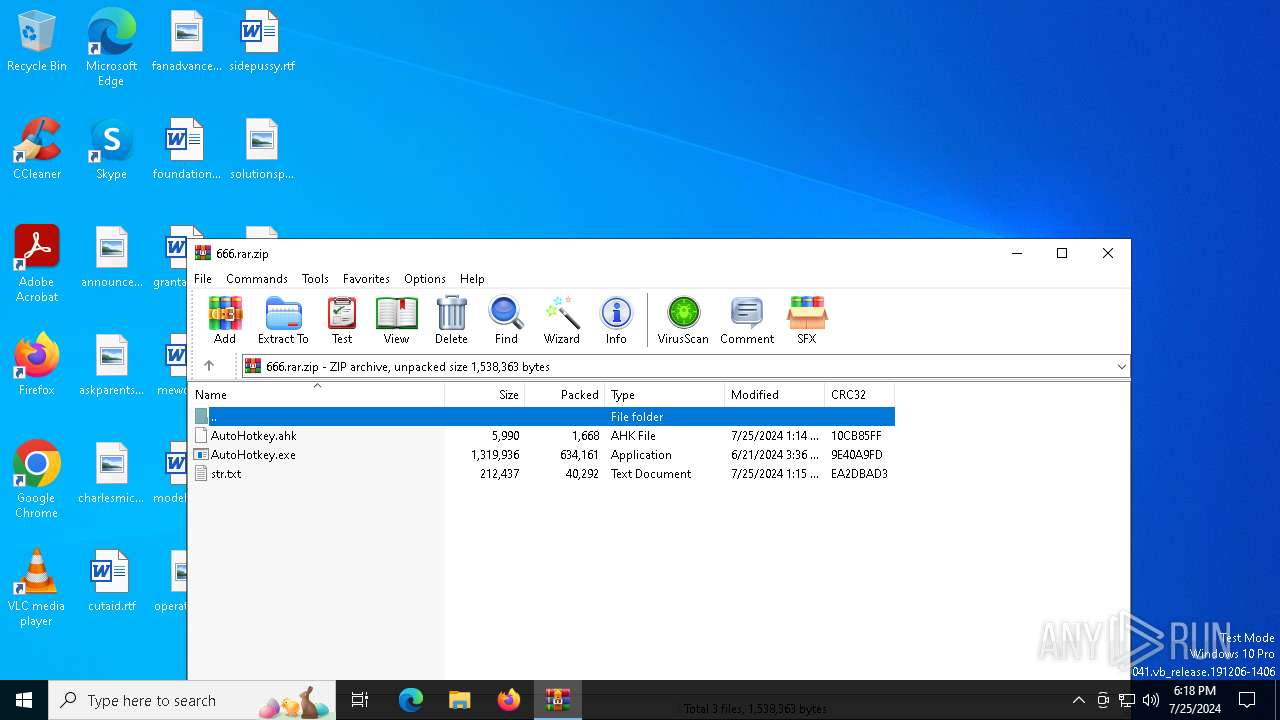
| File name: | 666.rar |
| Full analysis: | https://app.any.run/tasks/707d463f-dc15-475e-b024-cf0adfb99914 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 25, 2024, 18:18:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
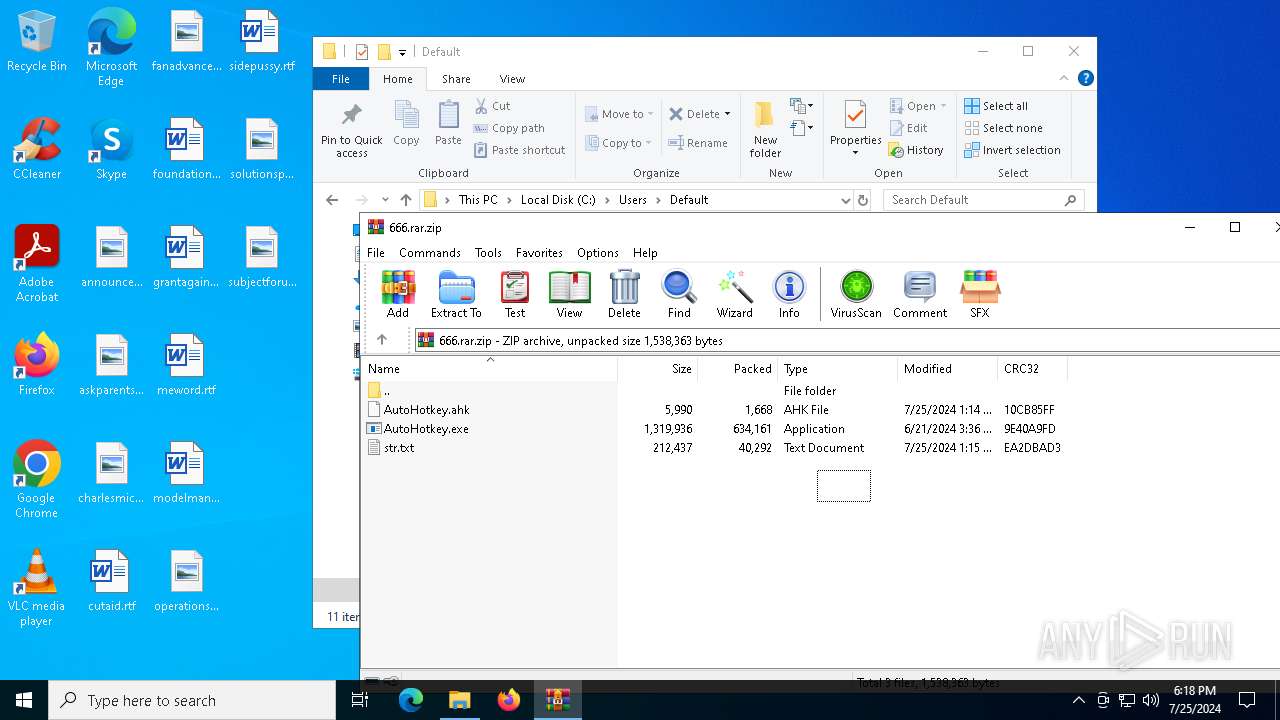
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | D25C6445CA8CF01AE430DAFBF19AD73B |
| SHA1: | BD49B5EB08864CB958F716E6532E2F156BE3296B |
| SHA256: | 05B539098D39D9B592534BA1B0BF5C277E9064ADCE2554910E7FB87F0C6CE69A |
| SSDEEP: | 24576:zgWdSdurcl26z3xGcGbLlmiEIoKpgwcJ7REslsBPvN4dSq4J6FTiTOxuqWj:zgWdSduol26z3xGcGbLlmiETKpgwcJVm |
MALICIOUS
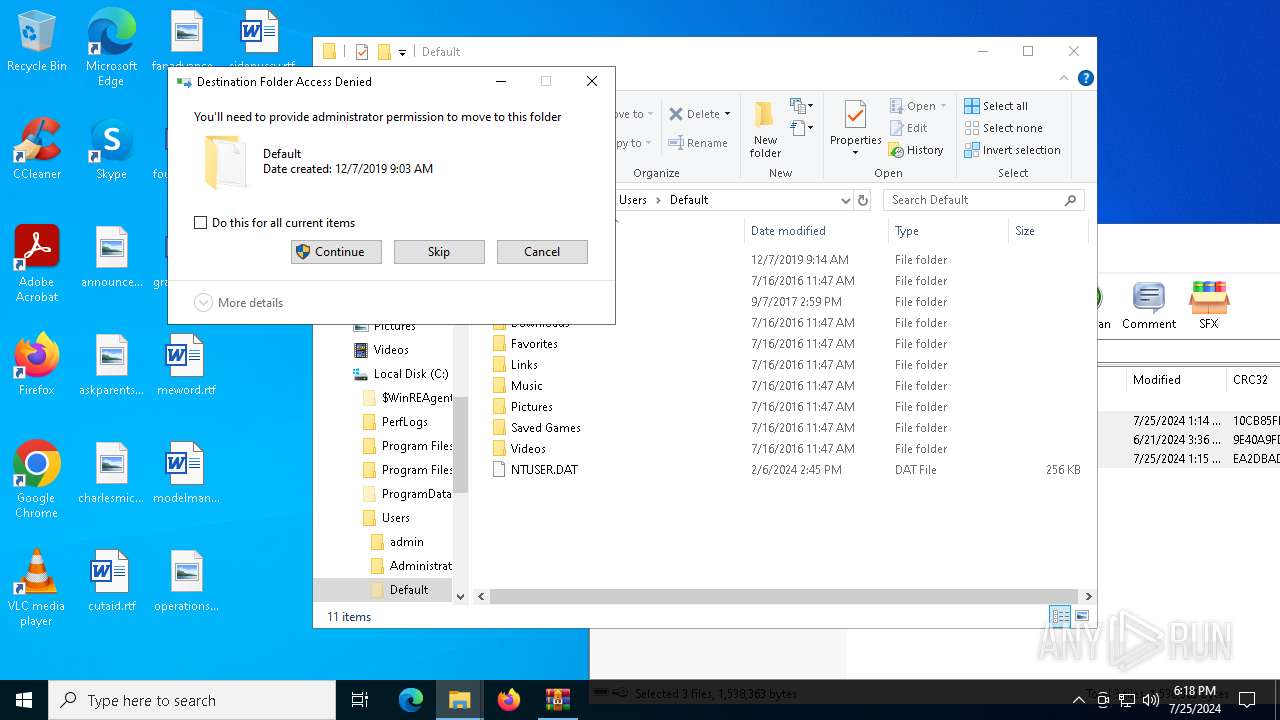
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4940)
ASYNCRAT has been detected (MUTEX)
- AppLaunch.exe (PID: 6804)
ASYNCRAT has been detected (SURICATA)
- AppLaunch.exe (PID: 6804)
ASYNCRAT has been detected (YARA)
- AppLaunch.exe (PID: 6804)
Actions looks like stealing of personal data
- AppLaunch.exe (PID: 6804)
SUSPICIOUS
Executable content was dropped or overwritten
- dllhost.exe (PID: 2332)
Creates file in the systems drive root
- OpenWith.exe (PID: 6468)
Executes application which crashes
- AppLaunch.exe (PID: 4404)
- AppLaunch.exe (PID: 6312)
Likely accesses (executes) a file from the Public directory
- AutoHotkey.exe (PID: 5792)
Connects to unusual port
- AppLaunch.exe (PID: 6804)
Contacting a server suspected of hosting an CnC
- AppLaunch.exe (PID: 6804)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4940)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 2332)
- OpenWith.exe (PID: 6468)
- notepad.exe (PID: 1320)
- OpenWith.exe (PID: 6792)
- notepad.exe (PID: 6616)
Drops the executable file immediately after the start
- dllhost.exe (PID: 2332)
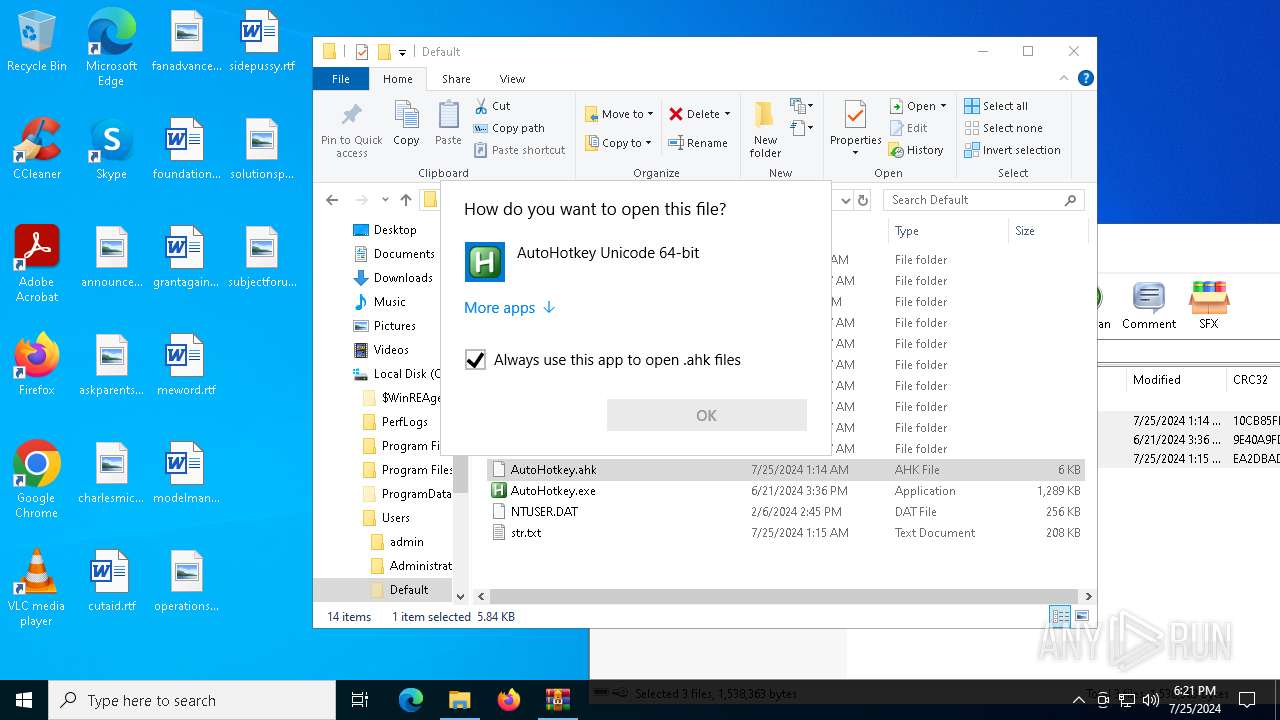
Manual execution by a user
- WINWORD.EXE (PID: 5304)
- notepad.exe (PID: 1320)
- AutoHotkey.exe (PID: 5792)
- AutoHotkey.exe (PID: 4884)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6468)
- OpenWith.exe (PID: 6792)
Checks supported languages
- AutoHotkey.exe (PID: 2136)
- AutoHotkey.exe (PID: 4884)
- AutoHotkey.exe (PID: 5792)
- AppLaunch.exe (PID: 6804)
- TextInputHost.exe (PID: 3380)
Reads the computer name
- TextInputHost.exe (PID: 3380)
- AppLaunch.exe (PID: 6804)
Checks proxy server information
- slui.exe (PID: 6860)
Reads the software policy settings
- slui.exe (PID: 6860)
- AppLaunch.exe (PID: 6804)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 6804)
Reads Environment values
- AppLaunch.exe (PID: 6804)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(6804) AppLaunch.exe
C2 (1)S95BCA55387D2A9BA0D7.webredirect.org
Ports (1)666
VersionXchallenger | 3Losh
Options
AutoRunfalse
MutexAsyncMutex_check
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAPeWQ4YJ3MvReCGwLzn7rTANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjIwNDI1MDA0MTA5WhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKT9nYYTjYTZhY+g1tekZ8/F29gsEIDgf/8odvCbCmYKGGZZi2yND9NjtBXEMANM9PAXCyMapGva...
Server_SignaturelhwMkmKuafMhOnoeZB+mL5RcdjQVpX/CmzprUS/VzF/AEruUkD2rbPvJUhFs+KGcpfGN67h0BdJ8lMjOrxGeS1U1RqUq5/Kc/xYB+scKbtpJ2c/uL7+v0TqX/O8P4Su+qbon+REcVomnVtj5YGFBmbKPmrQw+bZPHrfkgXALSMXbbi2DVZMaA2eqEldbubLj1FTNuHGcMDn6nDV81KnA5yqQtFlLK987+VJKBmxNyYjV/VbrvlTvrKy178i4bunUMX/85Yvvi0W/uOz9tBjnW5F+BI8VBEzEgJNwXCCEFSVN...
Keys
AES1223798329e91bb8a583095832a2fc82cb985d8f9e09bbb586cd2e8c9e236636
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:21 18:36:50 |
| ZipCRC: | 0x9e40a9fd |
| ZipCompressedSize: | 634161 |
| ZipUncompressedSize: | 1319936 |
| ZipFileName: | AutoHotkey.exe |
Total processes
170
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1320 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\Default\str.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\Default\AutoHotkey.exe" "C:\Users\Default\AutoHotkey.ahk" | C:\Users\Default\AutoHotkey.exe | — | OpenWith.exe | |||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey Unicode 64-bit Exit code: 0 Version: 1.1.37.02 Modules
| |||||||||||||||
| 2332 | C:\WINDOWS\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2668 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3280 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "C4B5AD1B-1C4C-4F86-A270-59E325D21B6C" "BDB939A5-8C30-402D-BA3B-1294ED575DE9" "5304" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 3380 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4088 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6312 -s 80 | C:\Windows\SysWOW64\WerFault.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4404 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | AutoHotkey.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET ClickOnce Launch Utility Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4548 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4404 -s 80 | C:\Windows\SysWOW64\WerFault.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4884 | "C:\Users\Default\AutoHotkey.exe" C:\Users\Default\AutoHotkey.ahk | C:\Users\Default\AutoHotkey.exe | — | explorer.exe | |||||||||||
User: admin Company: AutoHotkey Foundation LLC Integrity Level: MEDIUM Description: AutoHotkey Unicode 64-bit Exit code: 0 Version: 1.1.37.02 Modules
| |||||||||||||||
Total events
39 018
Read events
38 544
Write events
438
Delete events
36
Modification events
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\666.rar.zip | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4940) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6468) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\Office16\oregres.dll,-205 |
Value: Word | |||
| (PID) Process: | (6468) OpenWith.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @wmploc.dll,-102 |
Value: Windows Media Player | |||
Executable files
3
Suspicious files
29
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4940.33885\AutoHotkey.exe | executable | |
MD5:2D0600FE2B1B3BDC45D833CA32A37FDB | SHA256:EFFDEA83C6B7A1DC2CE9E9D40E91DFD59BED9FCBD580903423648B7CA97D9696 | |||
| 5304 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\sidepussy.rtf.LNK | binary | |
MD5:64ECC0ECF3B640FF614D60FFA66E8159 | SHA256:6D5C4B2C2890EAF23CCE5F6AD2A428370D2D7B80A632A1C9C802ECB6EBC87E64 | |||
| 4940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4940.33885\AutoHotkey.ahk | text | |
MD5:2F9DED57ADAEAB271FA81F56558CF051 | SHA256:8E199C8E3FC2462105A6D85C9DC2DF0BFC63107DC0F08354E1709C2CD958659D | |||
| 2332 | dllhost.exe | C:\Users\Default\AutoHotkey.exe | executable | |
MD5:2D0600FE2B1B3BDC45D833CA32A37FDB | SHA256:EFFDEA83C6B7A1DC2CE9E9D40E91DFD59BED9FCBD580903423648B7CA97D9696 | |||
| 2332 | dllhost.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:AEB8E12B95EA1F28553952033934D66F | SHA256:9EEED0ED0A2AF9870573227A657C3FC53558F524682D3CEA208A90BFAF368F18 | |||
| 5304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\09B59E90-364B-447C-985E-1C692F24A8B4 | xml | |
MD5:EBDFD3C8FB3372FF7E1C47B69997F3A5 | SHA256:32A9FB190E6FA81BFA132564E42C9800713716CE06A168FB9C3FFB4FB5DCD581 | |||
| 5304 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:38882679FFDBE75DE2BC6A230331E951 | SHA256:B2A24F85AEDBBC9D57613292528271AB1A62D2EED812F450948278A7DAA4E99F | |||
| 2332 | dllhost.exe | C:\Users\Default\str.txt | text | |
MD5:C6F85F5F29102D7424DF8E4902512599 | SHA256:BEE69FFA420819DA7CFCD92369C40A4ABD782A48BE53DF5AD86B1F202E0EDF3F | |||
| 5304 | WINWORD.EXE | C:\Users\admin\Desktop\~$depussy.rtf | binary | |
MD5:7839F5D5B9821283F99D995634C91A01 | SHA256:A0B0D426378E26550A2FD2449AB168D49E9B4BB5EA2C4316561608898F58BF19 | |||
| 5304 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\FontCache\4\PreviewFont\flat_officeFontsPreview_4_40.ttf | binary | |
MD5:4296A064B917926682E7EED650D4A745 | SHA256:E04E41C74D6C78213BA1588BACEE64B42C0EDECE85224C474A714F39960D8083 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
59
DNS requests
34
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6192 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4632 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5304 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3148 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6184 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4516 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.123.104.33:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4204 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6184 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4792 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2284 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webredirect .org Domain |
2284 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.webredirect .org Domain |
6804 | AppLaunch.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
6804 | AppLaunch.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
6804 | AppLaunch.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
6804 | AppLaunch.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|