| File name: | 5813bfc4da23ef6c272959821cf30c8f.exe |
| Full analysis: | https://app.any.run/tasks/16f238ff-8db6-48ff-a061-afc8cdf477ea |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 17, 2025, 14:48:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 7 sections |
| MD5: | 5813BFC4DA23EF6C272959821CF30C8F |
| SHA1: | 7C1FC969E10AAE2F7C5725611559EAB438C8CBFD |
| SHA256: | 059A0A5F8AB02FAAE85536A23A83F9224C4EC60055EC5A1067FA0A026F72A1B4 |
| SSDEEP: | 98304:qbv9tpRYHhTXTehyap+B/p4ov0nOpndRfHpwr43GGo1dPewH9xa+eKrntyZJvfP/:F5+wZq4 |
MALICIOUS
LUMMA has been detected (SURICATA)
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 4652)
- MSBuild.exe (PID: 1628)
Connects to the CnC server
- svchost.exe (PID: 2196)
- ramez.exe (PID: 4620)
LUMMA mutex has been found
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
- MSBuild.exe (PID: 1628)
Steals credentials from Web Browsers
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
- MSBuild.exe (PID: 1628)
Actions looks like stealing of personal data
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
- MSBuild.exe (PID: 1628)
LUMMA has been detected (YARA)
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
AMADEY mutex has been found
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- ramez.exe (PID: 5256)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 4620)
AMADEY has been detected (YARA)
- ramez.exe (PID: 4620)
Executing a file with an untrusted certificate
- ZGSI81i.exe (PID: 1240)
- BhEXzVm.exe (PID: 6384)
Known privilege escalation attack
- dllhost.exe (PID: 4056)
Registers / Runs the DLL via REGSVR32.EXE
- A2vn0Mb.tmp (PID: 776)
SUSPICIOUS
Reads the BIOS version
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- ramez.exe (PID: 4620)
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 5256)
- oxDU0MW.exe (PID: 3300)
Contacting a server suspected of hosting an CnC
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- svchost.exe (PID: 2196)
- ramez.exe (PID: 4620)
- MSBuild.exe (PID: 4652)
- MSBuild.exe (PID: 1628)
Process requests binary or script from the Internet
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- ramez.exe (PID: 4620)
Searches for installed software
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
Connects to the server without a host name
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- ramez.exe (PID: 4620)
Potential Corporate Privacy Violation
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- ramez.exe (PID: 4620)
Executable content was dropped or overwritten
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- oxDU0MW.exe (PID: 3300)
- A2vn0Mb.exe (PID: 5960)
- A2vn0Mb.tmp (PID: 5308)
- A2vn0Mb.exe (PID: 3992)
- A2vn0Mb.tmp (PID: 776)
Reads security settings of Internet Explorer
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- A2vn0Mb.tmp (PID: 5308)
Starts itself from another location
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 4620)
There is functionality for taking screenshot (YARA)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
The process executes via Task Scheduler
- ramez.exe (PID: 5256)
Executes application which crashes
- WinTemp-v4.exe (PID: 6808)
Reads the Windows owner or organization settings
- A2vn0Mb.tmp (PID: 776)
- A2vn0Mb.tmp (PID: 5308)
Process drops legitimate windows executable
- A2vn0Mb.tmp (PID: 776)
- A2vn0Mb.tmp (PID: 5308)
- ramez.exe (PID: 4620)
Starts POWERSHELL.EXE for commands execution
- regsvr32.exe (PID: 4464)
The process hide an interactive prompt from the user
- regsvr32.exe (PID: 4464)
The process checks if it is being run in the virtual environment
- FxefytI.exe (PID: 6744)
The process bypasses the loading of PowerShell profile settings
- regsvr32.exe (PID: 4464)
Starts a Microsoft application from unusual location
- BhEXzVm.exe (PID: 6384)
INFO
Checks supported languages
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- E759x7N.exe (PID: 6972)
- ramez.exe (PID: 5256)
- ZGSI81i.exe (PID: 1240)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
- 08IyOOF.exe (PID: 4724)
- oxDU0MW.exe (PID: 3300)
- A2vn0Mb.exe (PID: 5960)
- A2vn0Mb.tmp (PID: 5308)
- A2vn0Mb.exe (PID: 3992)
- A2vn0Mb.tmp (PID: 776)
- FxefytI.exe (PID: 6744)
- MSBuild.exe (PID: 1628)
- legedddd.exe (PID: 5452)
- BhEXzVm.exe (PID: 6384)
Reads the computer name
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
- oxDU0MW.exe (PID: 3300)
- A2vn0Mb.tmp (PID: 5308)
- A2vn0Mb.tmp (PID: 776)
- FxefytI.exe (PID: 6744)
- MSBuild.exe (PID: 1628)
Reads the software policy settings
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- E759x7N.exe (PID: 6972)
- MSBuild.exe (PID: 2692)
- MSBuild.exe (PID: 4652)
- slui.exe (PID: 744)
- ramez.exe (PID: 4620)
- MSBuild.exe (PID: 1628)
Themida protector has been detected
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- ramez.exe (PID: 4620)
Create files in a temporary directory
- 5813bfc4da23ef6c272959821cf30c8f.exe (PID: 2136)
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- oxDU0MW.exe (PID: 3300)
- A2vn0Mb.exe (PID: 5960)
- A2vn0Mb.tmp (PID: 5308)
- A2vn0Mb.exe (PID: 3992)
- A2vn0Mb.tmp (PID: 776)
Process checks computer location settings
- VOLP5W0YAT6B9P0B5RGX.exe (PID: 2692)
- ramez.exe (PID: 4620)
- A2vn0Mb.tmp (PID: 5308)
Checks proxy server information
- ramez.exe (PID: 4620)
Creates files or folders in the user directory
- ramez.exe (PID: 4620)
- WerFault.exe (PID: 6516)
- A2vn0Mb.tmp (PID: 776)
Checks transactions between databases Windows and Oracle
- oxDU0MW.exe (PID: 3300)
Reads the machine GUID from the registry
- oxDU0MW.exe (PID: 3300)
- FxefytI.exe (PID: 6744)
- ramez.exe (PID: 4620)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 4056)
The sample compiled with english language support
- A2vn0Mb.tmp (PID: 776)
- A2vn0Mb.tmp (PID: 5308)
- ramez.exe (PID: 4620)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1040)
- powershell.exe (PID: 4724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2136) 5813bfc4da23ef6c272959821cf30c8f.exe
C2 (9)onehunqpom.life/zpxd
narrathfpt.top/tekq
featurlyin.top/pdal
overcovtcg.top/juhd
laminaflbx.shop/twoq
cornerdurv.top/adwq
posseswsnc.top/akds
jackthyfuc.run/xpas
blackswmxc.top/bgry
(PID) Process(6972) E759x7N.exe
C2 (11)onehunqpom.life/zpxd
featurlyin.top/pdal
overcovtcg.top/juhd
blackswmxc.top/bgry
laminaflbx.shop/twoq
racxilb.digital/ozi
posseswsnc.top/akds
https://t.me/kz_prokla1
chainsimbb.run/qgbb
jackthyfuc.run/xpas
narrathfpt.top/tekq
(PID) Process(2692) MSBuild.exe
C2 (10)emphatakpn.bet/ladk
featurlyin.top/pdal
overcovtcg.top/juhd
laminaflbx.shop/twoq
https://t.me/wermnjgk34
posseswsnc.top/akds
testcawepr.run/dsap
saxecocnak.live/manj
venaetdqfn.run/gjud
blackswmxc.top/bgry
(PID) Process(4652) MSBuild.exe
C2 (8)emphatakpn.bet/ladk
featurlyin.top/pdal
overcovtcg.top/juhd
laminaflbx.shop/twoq
testcawepr.run/dsap
saxecocnak.live/manj
posseswsnc.top/akds
blackswmxc.top/bgry
Amadey
(PID) Process(4620) ramez.exe
C2185.156.72.96
URLhttp://185.156.72.96/te4h2nus/index.php
Version5.34
Options
Drop directoryd610cf342e
Drop nameramez.exe
Strings (125)lv:
msi
Kaspersky Lab
av:
|
#
"
\App
00000422
dm:
Powershell.exe
ProgramData\
ps1
rundll32
http://
Content-Disposition: form-data; name="data"; filename="
SOFTWARE\Microsoft\Windows NT\CurrentVersion
dll
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
id:
VideoID
cred.dll|clip.dll|
0000043f
cmd
00000423
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
-executionpolicy remotesigned -File "
2022
------
2016
og:
\0000
CurrentBuild
2019
:::
S-%lu-
" && timeout 1 && del
ProductName
Panda Security
ESET
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/k
+++
?scr=1
Doctor Web
GET
SYSTEM\ControlSet001\Services\BasicDisplay\Video
/quiet
.jpg
d610cf342e
vs:
sd:
rundll32.exe
"taskkill /f /im "
pc:
random
=
360TotalSecurity
<d>
wb
Content-Type: multipart/form-data; boundary=----
Startup
Norton
&& Exit"
os:
https://
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
2025
Avira
%-lu
zip
POST
"
Content-Type: application/octet-stream
Rem
/te4h2nus/index.php
------
5.34
<c>
clip.dll
AVAST Software
\
shell32.dll
" && ren
e3
ramez.exe
kernel32.dll
DefaultSettings.XResolution
d1
DefaultSettings.YResolution
185.156.72.96
r=
cred.dll
--
GetNativeSystemInfo
-%lu
ComputerName
&unit=
Keyboard Layout\Preload
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
ar:
Sophos
%USERPROFILE%
exe
e1
e2
st=s
Programs
0123456789
un:
rb
bi:
abcdefghijklmnopqrstuvwxyz0123456789-_
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
cmd /C RMDIR /s/q
Bitdefender
-unicode-
AVG
WinDefender
&&
shutdown -s -t 0
Comodo
00000419
Content-Type: application/x-www-form-urlencoded
/Plugins/
Main
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:15 15:45:51+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 322560 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4a6000 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
167
Monitored processes
36
Malicious processes
15
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ZGSI81i.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Users\admin\AppData\Local\Temp\is-JG916.tmp\A2vn0Mb.tmp" /SL5="$1300BE,1190066,187904,C:\Users\admin\AppData\Local\Temp\10132350101\A2vn0Mb.exe" /VERYSILENT | C:\Users\admin\AppData\Local\Temp\is-JG916.tmp\A2vn0Mb.tmp | A2vn0Mb.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
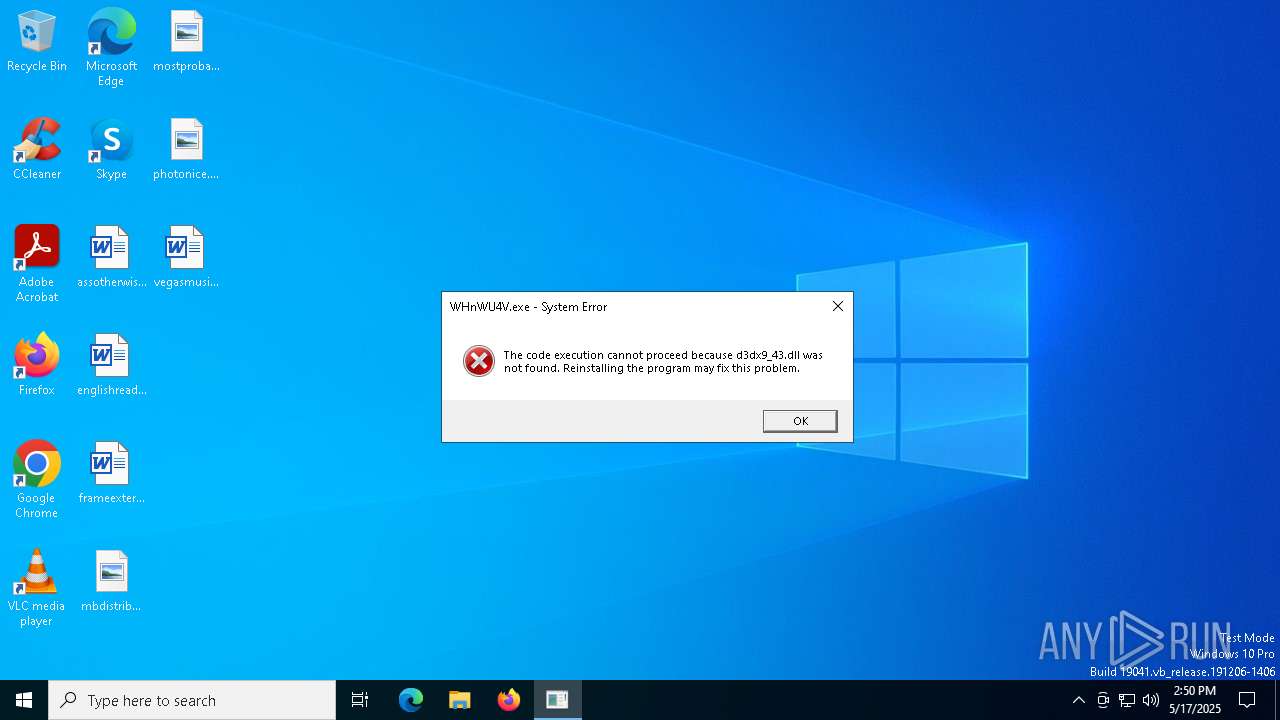
| 1040 | "C:\Users\admin\AppData\Local\Temp\10132310101\WHnWU4V.exe" | C:\Users\admin\AppData\Local\Temp\10132310101\WHnWU4V.exe | — | ramez.exe | |||||||||||
User: admin Company: xone.fun Integrity Level: MEDIUM Description: xone Exit code: 3221225781 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1040 | "powershell" -Command "if (Get-ScheduledTask | Where-Object { $_.Actions.Execute -eq 'regsvr32' -and $_.Actions.Arguments -eq '/s /i:INSTALL \"%APPDATA%\Microsoft\SystemCertificates\2XamlDiagnostics_3.pfx\"' }) { exit 0 } else { exit 1 }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1240 | "C:\Users\admin\AppData\Local\Temp\10132320101\ZGSI81i.exe" | C:\Users\admin\AppData\Local\Temp\10132320101\ZGSI81i.exe | — | ramez.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1628 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | legedddd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Local\Temp\5813bfc4da23ef6c272959821cf30c8f.exe" | C:\Users\admin\AppData\Local\Temp\5813bfc4da23ef6c272959821cf30c8f.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
Lumma(PID) Process(2136) 5813bfc4da23ef6c272959821cf30c8f.exe C2 (9)onehunqpom.life/zpxd narrathfpt.top/tekq featurlyin.top/pdal overcovtcg.top/juhd laminaflbx.shop/twoq cornerdurv.top/adwq posseswsnc.top/akds jackthyfuc.run/xpas blackswmxc.top/bgry | |||||||||||||||
Total events
22 107
Read events
22 078
Write events
26
Delete events
3
Modification events
| (PID) Process: | (4620) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4620) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4620) ramez.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4056) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6516) WerFault.exe | Key: | \REGISTRY\A\{0506477d-8304-03b5-5c5e-a200d86f4d0e}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (6516) WerFault.exe | Key: | \REGISTRY\A\{0506477d-8304-03b5-5c5e-a200d86f4d0e}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6516) WerFault.exe | Key: | \REGISTRY\A\{0506477d-8304-03b5-5c5e-a200d86f4d0e}\Root\InventoryApplicationFile\wintemp-v4.exe|f791608f285ab7b9 |
| Operation: | write | Name: | ProgramId |
Value: 00062d1790ba7edff789f6d1ea3b25fba79f0000ffff | |||
| (PID) Process: | (6516) WerFault.exe | Key: | \REGISTRY\A\{0506477d-8304-03b5-5c5e-a200d86f4d0e}\Root\InventoryApplicationFile\wintemp-v4.exe|f791608f285ab7b9 |
| Operation: | write | Name: | FileId |
Value: 0000c67d29b5890fd31ed5920d7a64a617562b73c005 | |||
| (PID) Process: | (6516) WerFault.exe | Key: | \REGISTRY\A\{0506477d-8304-03b5-5c5e-a200d86f4d0e}\Root\InventoryApplicationFile\wintemp-v4.exe|f791608f285ab7b9 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\users\admin\appdata\local\temp\wintemp-v4.exe | |||
| (PID) Process: | (6516) WerFault.exe | Key: | \REGISTRY\A\{0506477d-8304-03b5-5c5e-a200d86f4d0e}\Root\InventoryApplicationFile\wintemp-v4.exe|f791608f285ab7b9 |
| Operation: | write | Name: | LongPathHash |
Value: wintemp-v4.exe|f791608f285ab7b9 | |||
Executable files
29
Suspicious files
14
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6516 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_WinTemp-v4.exe_b94cb1a11794a5dd2f6fd7af9dc9a68a2cdb6d7_be18d7e5_1cdb8933-8942-4056-af00-c632ad0d00a3\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6516 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\WinTemp-v4.exe.6808.dmp | — | |
MD5:— | SHA256:— | |||
| 4620 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10132330101\08IyOOF.exe | executable | |
MD5:5BDF4F3AA32819EC9F05733DBACB15EA | SHA256:5125BDD56A603DCB3929A4BF2282467DED28CCFED837D908AD4EFF4246F43E94 | |||
| 2692 | VOLP5W0YAT6B9P0B5RGX.exe | C:\Users\admin\AppData\Local\Temp\d610cf342e\ramez.exe | executable | |
MD5:0AB91DB8E520412B94BACF7BC00406DC | SHA256:6764AFA6D68FA5C4773D6CCD61A7D5D1C723876A18DD3B15EDDBDF3036FCD5CE | |||
| 2692 | VOLP5W0YAT6B9P0B5RGX.exe | C:\Windows\Tasks\ramez.job | binary | |
MD5:A5482AB0DC9924BC7C2963C7AE281A2E | SHA256:597902FB67C82115D23C3D7128B24994140893E1E7A4ABC356241226B07463AF | |||
| 4620 | ramez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\WHnWU4V[1].exe | executable | |
MD5:9B5FD9A501F4AB5122B8F9249F08F976 | SHA256:FB4D9C11C501DFD623F3F5E37155A386F98794992B04F4555C5FBCBFC014E3C4 | |||
| 4620 | ramez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\08IyOOF[1].exe | executable | |
MD5:5BDF4F3AA32819EC9F05733DBACB15EA | SHA256:5125BDD56A603DCB3929A4BF2282467DED28CCFED837D908AD4EFF4246F43E94 | |||
| 4620 | ramez.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\E759x7N[1].exe | executable | |
MD5:D14A22031323C343623D6766BA80B1ED | SHA256:BBC04EE70F769D1D57EA46968ABDD2AD2B673BACD805FE1BCBAC9E7FE8C28AE4 | |||
| 4620 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10132300101\E759x7N.exe | executable | |
MD5:D14A22031323C343623D6766BA80B1ED | SHA256:BBC04EE70F769D1D57EA46968ABDD2AD2B673BACD805FE1BCBAC9E7FE8C28AE4 | |||
| 4620 | ramez.exe | C:\Users\admin\AppData\Local\Temp\10132340101\oxDU0MW.exe | executable | |
MD5:750999A63402695E1972E5FF52F68DFE | SHA256:8CC12056BF3A841E1BD61916033530AFAD5D3ABAB5512402121D24159423B67C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
61
DNS requests
35
Threats
46
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.96:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/mine/random.exe | unknown | — | — | unknown |
5384 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5384 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4620 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
4620 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
4620 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/files/5712371530/E759x7N.exe | unknown | — | — | unknown |
4620 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.164.96:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | 104.21.48.1:443 | cornerdurv.top | CLOUDFLARENET | — | unknown |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | 172.67.222.194:443 | narrathfpt.top | CLOUDFLARENET | US | unknown |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cornerdurv.top |
| unknown |
narrathfpt.top |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
jackthyfuc.run |
| unknown |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cornerdurv .top) |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cornerdurv .top) in TLS SNI |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (laminaflbx .shop) |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2136 | 5813bfc4da23ef6c272959821cf30c8f.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |