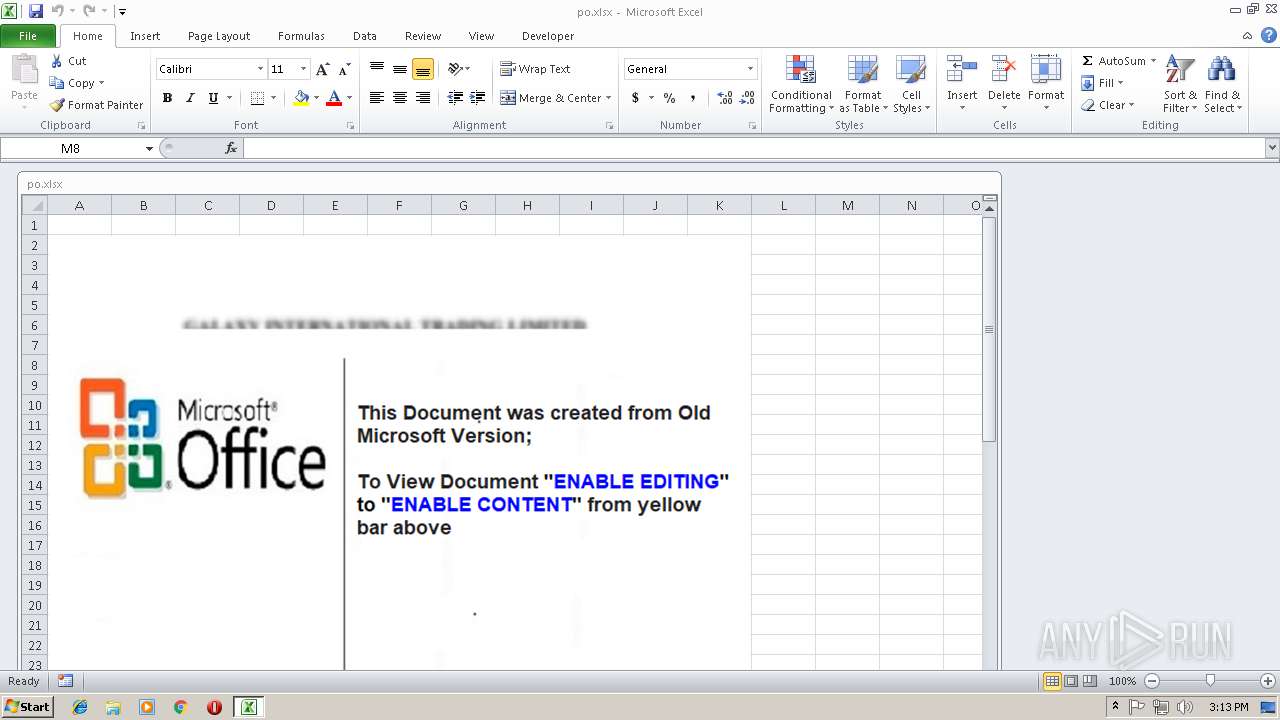
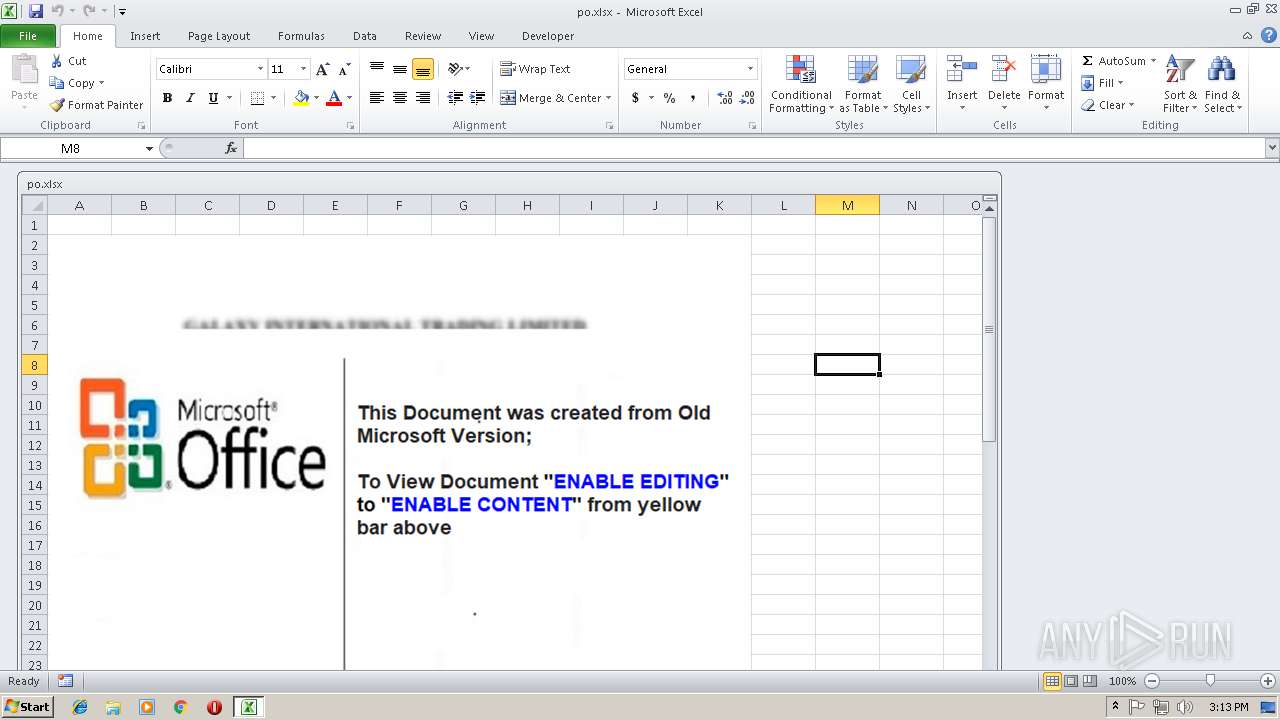
| File name: | po.xlsx |
| Full analysis: | https://app.any.run/tasks/34cf7b04-3c77-49e2-acee-a30d5ab1e60d |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | November 08, 2018, 15:12:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | 8162899574DD9BF113E7D5850B36903D |
| SHA1: | 79528E042C26EDCA9E535869318CC95588FDAFDE |
| SHA256: | 05806749C9C50F3A7559357C5DCBB3917783BE47706C6BEC8B74C9C50A84A7CE |
| SSDEEP: | 3072:7Wno3fi5NdQVRmuK+Cmk0wsoyqBemBazm7TqRF87mNnB0GDxXAUHw:s7QuuK+CR07oymBaEORF+cHXRw |
MALICIOUS
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 2936)
Application was dropped or rewritten from another process
- rns.exe (PID: 3436)
- rns.exe (PID: 1908)
- RegSvcs.exe (PID: 1904)
- vbc.exe (PID: 2340)
FORMBOOK was detected
- explorer.exe (PID: 1604)
Connects to CnC server
- explorer.exe (PID: 1604)
Downloads executable files from the Internet
- EQNEDT32.EXE (PID: 2936)
Downloads executable files from IP
- EQNEDT32.EXE (PID: 2936)
Formbook was detected
- rundll32.exe (PID: 2424)
- Firefox.exe (PID: 4064)
Changes the autorun value in the registry
- rundll32.exe (PID: 2424)
Actions looks like stealing of personal data
- rundll32.exe (PID: 2424)
Stealing of credential data
- rundll32.exe (PID: 2424)
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 2936)
SUSPICIOUS
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 2424)
Executable content was dropped or overwritten
- vbc.exe (PID: 2340)
- rns.exe (PID: 3436)
- EQNEDT32.EXE (PID: 2936)
Application launched itself
- rns.exe (PID: 1908)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 1604)
Loads DLL from Mozilla Firefox
- rundll32.exe (PID: 2424)
Creates files in the user directory
- rundll32.exe (PID: 2424)
Drop AutoIt3 executable file
- vbc.exe (PID: 2340)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3556)
Dropped object may contain Bitcoin addresses
- rns.exe (PID: 1908)
- vbc.exe (PID: 2340)
Creates files in the user directory
- Firefox.exe (PID: 4064)
Starts Microsoft Office Application
- explorer.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
10
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1604 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | "C:\Users\admin\AppData\Local\Temp\RegSvcs.exe" | C:\Users\admin\AppData\Local\Temp\RegSvcs.exe | — | rns.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 1908 | "C:\Users\admin\AppData\Local\Temp\90407336\rns.exe" qgx=vbw | C:\Users\admin\AppData\Local\Temp\90407336\rns.exe | — | vbc.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 2340 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2424 | "C:\Windows\System32\rundll32.exe" | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2936 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3112 | /c del "C:\Users\admin\AppData\Local\Temp\RegSvcs.exe" | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3436 | C:\Users\admin\AppData\Local\Temp\90407336\rns.exe C:\Users\admin\AppData\Local\Temp\90407336\UGFIR | C:\Users\admin\AppData\Local\Temp\90407336\rns.exe | rns.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 14, 5 Modules
| |||||||||||||||
| 3556 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4064 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\Firefox.exe | rundll32.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
Total events
1 004
Read events
944
Write events
53
Delete events
7
Modification events
| (PID) Process: | (1604) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000006821FD290F362A42A685E6961EA74BA800000000020000000000106600000001000020000000CE7EE1893B7BC0A023C01C954805F5BA662E1D1469B65F8C59D7F54E9F630B3E000000000E800000000200002000000085828C68936B7B5E6876AF7DB7B057DF6EBC2CC00000FE266FB8290890ECDD4730000000B9DEF93655EC723283738F42E0C5C1FAC971E5F738CB554A9DF98C4D73D8923D356DCB25DAB34BC0DB3E8115A7BB27A54000000001220A5F3FD7335490EC4840B64EBE3D82DBFB30F406F435787EF948C8D4E96F38A2C3B963B7A2A51CD691A628B7682C8A87788450477630104A2E4C7A8AB96F | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | !#a |
Value: 21236100E40D0000010000000000000000000000 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: E40D0000D49263817577D40100000000 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | !#a |
Value: 21236100E40D0000010000000000000000000000 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3556) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
74
Text files
48
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3556 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR9381.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2936 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\frank[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\igw.pdf | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\aaq.docx | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\bqd.xl | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\ocj.dat | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\hnq.mp3 | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\jpp.jpg | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\qgx=vbw | text | |
MD5:— | SHA256:— | |||
| 2340 | vbc.exe | C:\Users\admin\AppData\Local\Temp\90407336\uvd.xl | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
22
DNS requests
19
Threats
42
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1604 | explorer.exe | GET | — | 172.217.168.19:80 | http://www.xn--n9j7ff2irju61ovphy97i.com/aa8/?0puHwJ=1dSfG+6p2+XpdxKPE4MLxT/HXcyBkSgMzXVh47vwts/p9M1747zdxw2yoAxc37c8tq+Ewg==&00A=vDzpdxFPZdFhEjM&sql=1 | US | — | — | malicious |
1604 | explorer.exe | GET | — | 203.170.80.250:80 | http://www.misterpips.com/aa8/?0puHwJ=5j3zBjERkQZ9BrvBozWMVamVFVEOpyDcfugbGSmkUPL+Oe3M4hwR5L2pHLMlU/qxqvD4mg==&00A=vDzpdxFPZdFhEjM&sql=1 | AU | — | — | malicious |
1604 | explorer.exe | GET | — | 160.202.124.193:80 | http://www.boxilite.com/aa8/?0puHwJ=NabGGMvU0ukeEQLlh6+MgxSvMPLz7OWkzcoZHL5n5LWGphHkQNmcZkyqtkTQUFx+M7z4zw==&00A=vDzpdxFPZdFhEjM&sql=1 | US | — | — | malicious |
2936 | EQNEDT32.EXE | GET | 200 | 23.249.161.100:80 | http://23.249.161.100/frankm/frank.exe | US | executable | 822 Kb | malicious |
1604 | explorer.exe | POST | — | 172.217.168.19:80 | http://www.xn--n9j7ff2irju61ovphy97i.com/aa8/ | US | — | — | malicious |
1604 | explorer.exe | POST | — | 172.217.168.19:80 | http://www.xn--n9j7ff2irju61ovphy97i.com/aa8/ | US | — | — | malicious |
1604 | explorer.exe | POST | — | 47.52.142.209:80 | http://www.fluorysports.com/aa8/ | HK | — | — | malicious |
1604 | explorer.exe | POST | — | 47.52.142.209:80 | http://www.fluorysports.com/aa8/ | HK | — | — | malicious |
1604 | explorer.exe | POST | — | 47.52.142.209:80 | http://www.fluorysports.com/aa8/ | HK | — | — | malicious |
1604 | explorer.exe | POST | — | 160.202.124.193:80 | http://www.boxilite.com/aa8/ | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2936 | EQNEDT32.EXE | 23.249.161.100:80 | — | ColoCrossing | US | malicious |
1604 | explorer.exe | 74.208.236.237:80 | www.mtamstore.com | 1&1 Internet SE | US | malicious |
1604 | explorer.exe | 172.217.168.19:80 | www.xn--n9j7ff2irju61ovphy97i.com | Google Inc. | US | whitelisted |
1604 | explorer.exe | 47.52.142.209:80 | www.fluorysports.com | Alibaba (China) Technology Co., Ltd. | HK | malicious |
1604 | explorer.exe | 203.170.80.250:80 | www.misterpips.com | Dreamscape Networks Limited | AU | malicious |
1604 | explorer.exe | 160.202.124.193:80 | www.boxilite.com | QuickPacket, LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.lcdluq.info |
| unknown |
www.mtamstore.com |
| malicious |
www.misterpips.com |
| malicious |
www.recht-auf-loeschung.info |
| unknown |
www.xn--n9j7ff2irju61ovphy97i.com |
| malicious |
www.wisdommwakiwa.com |
| unknown |
www.fluorysports.com |
| malicious |
www.forgotumented.net |
| unknown |
www.yg6669.com |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2936 | EQNEDT32.EXE | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2936 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
2936 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2936 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
2936 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
1604 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1604 | explorer.exe | A Network Trojan was detected | SC SPYWARE Trojan-Spy.Win32.Noon |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] FormBook CnC Checkin (GET) |
1604 | explorer.exe | A Network Trojan was detected | MALWARE [PTsecurity] TrojanSpy:FormBook CnC Checkin (POST) |
13 ETPRO signatures available at the full report