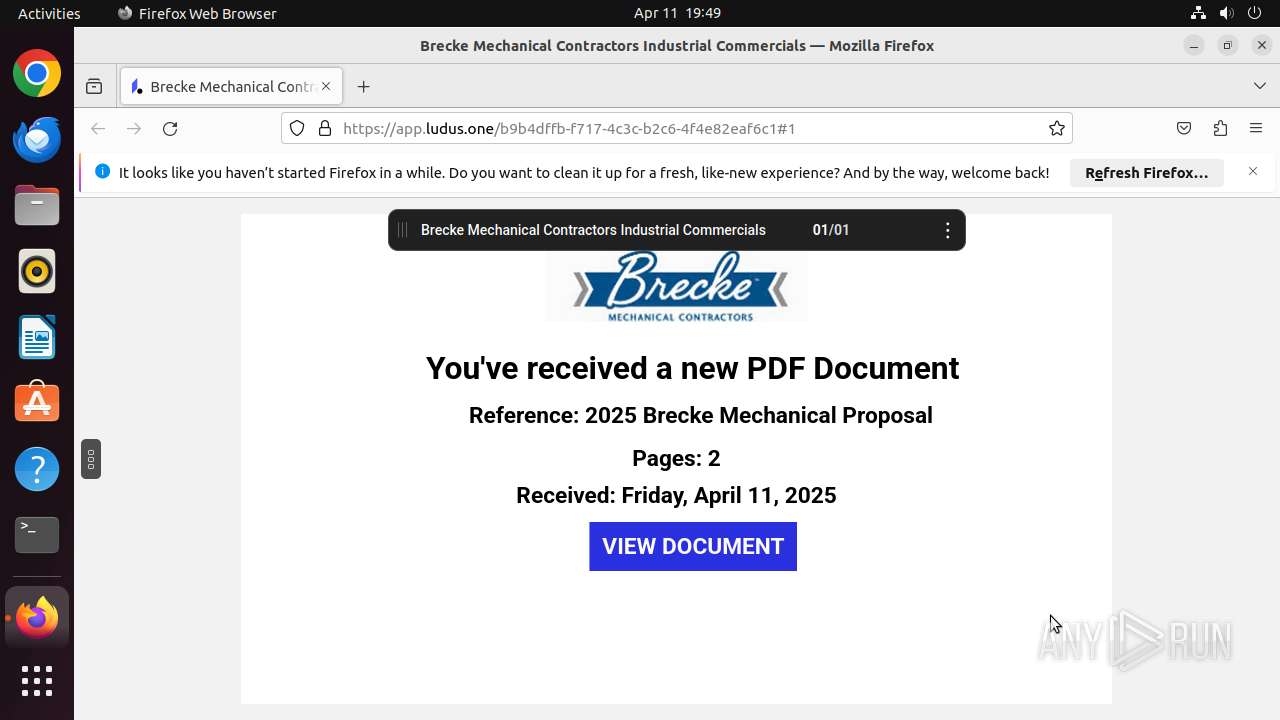
| URL: | https://url.us.m.mimecastprotect.com/s/kHMoC827DYSP89wolInfxcy0DjM?domain=click.securedvisit.com |
| Full analysis: | https://app.any.run/tasks/378b1170-47eb-478f-a903-97bf2580e388 |
| Verdict: | Malicious activity |
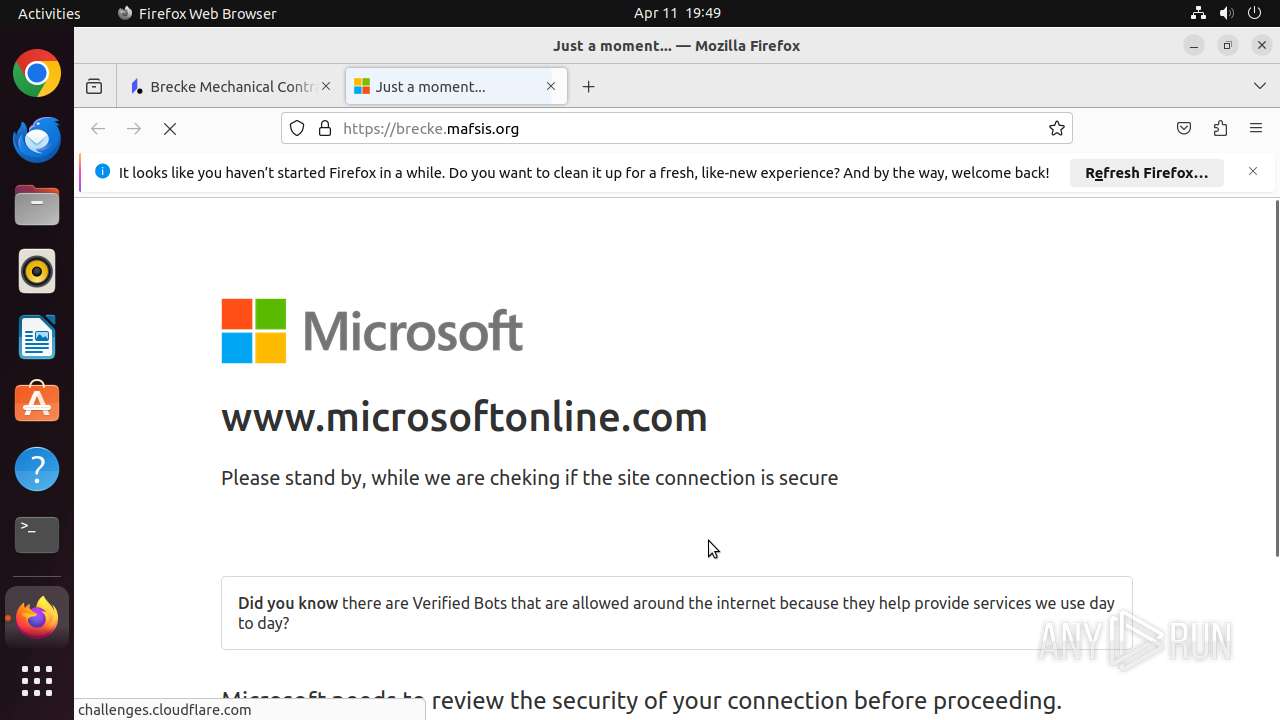
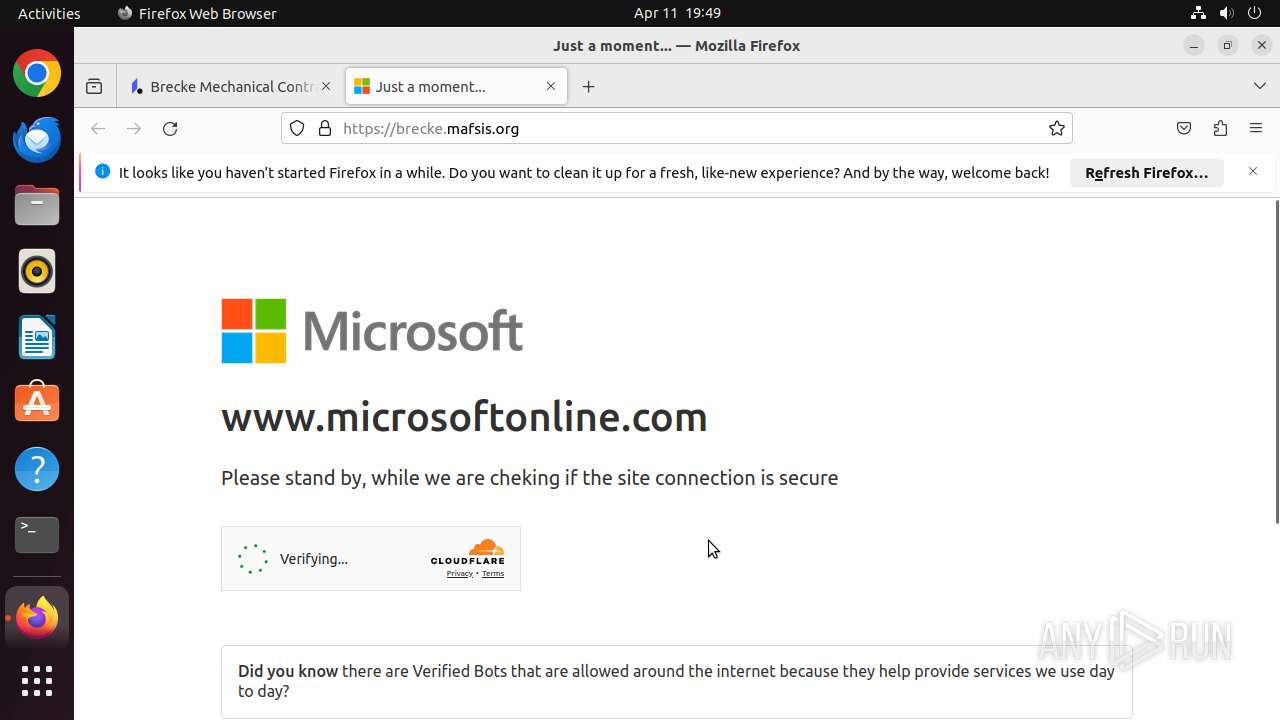
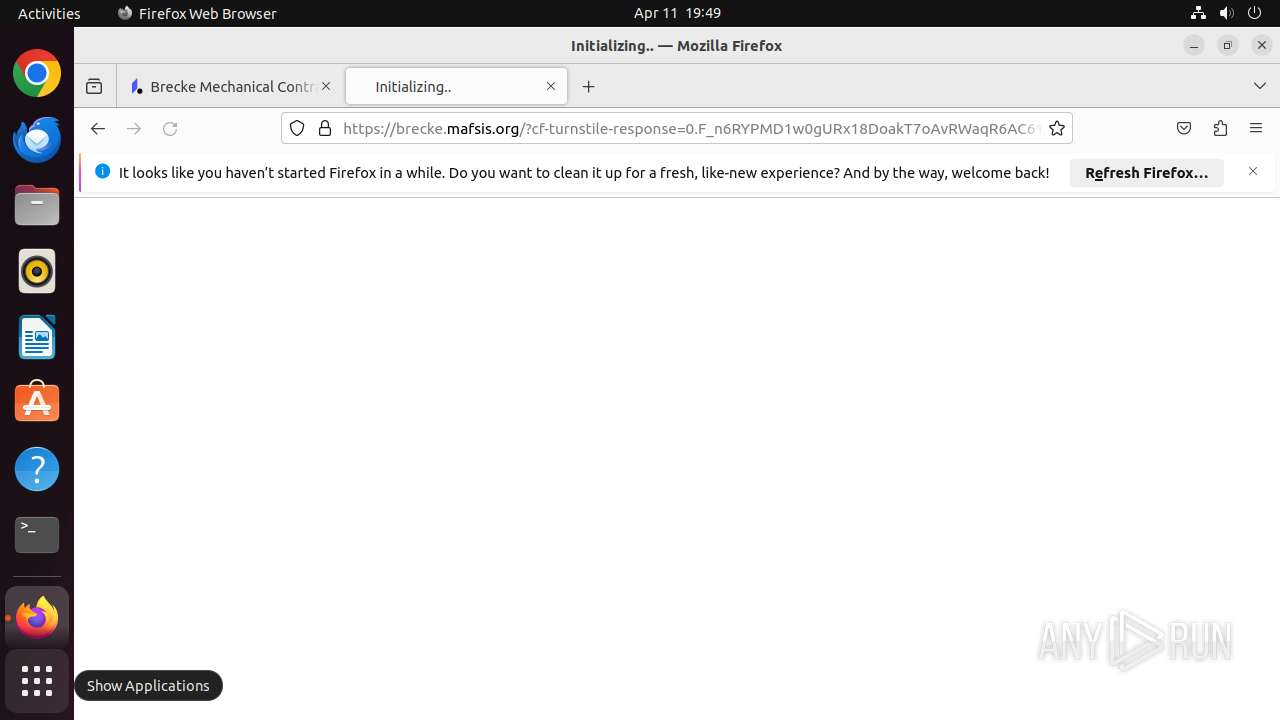
| Threats: | Sneaky 2FA is an Adversary-in-the-Middle (AiTM) phishing kit targeting Microsoft 365 accounts. Distributed as a Phishing-as-a-Service (PhaaS) through a Telegram bot, this malware bypasses two-factor authentication (2FA) to steal credentials and session cookies, posing a significant threat to individuals and organizations. |
| Analysis date: | April 11, 2025, 18:49:22 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| Indicators: | |
| MD5: | AF8187301C5D4B781BB3ABC9F5DC0AC3 |
| SHA1: | E01325808C3C7AEB0B86561D65FD3B97B699EC9E |
| SHA256: | 055158DB96D375DB4507EDC8BF3C560D95661D3B6017140168925D7D7413F814 |
| SSDEEP: | 3:N8UjmTSCeoKmdXaeSKi0cLPFOLWsUTXQLK:2Ujweo9dXaNKFcLPFOLUTOK |
MALICIOUS
PHISHING has been detected (SURICATA)
- systemd-resolved (PID: 445)
SUSPICIOUS
Executes commands using command-line interpreter
- sudo (PID: 39489)
- firefox (PID: 39490)
Reads passwd file
- dumpe2fs (PID: 39511)
- dumpe2fs (PID: 39518)
Check the Environment Variables Related to System Identification (os-release)
- firefox (PID: 39490)
- snapctl (PID: 39538)
- snapctl (PID: 39543)
- snapctl (PID: 39581)
- snapctl (PID: 39576)
INFO
Checks timezone
- dumpe2fs (PID: 39518)
- dumpe2fs (PID: 39511)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
400
Monitored processes
182
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 445 | /lib/systemd/systemd-resolved | /usr/lib/systemd/systemd-resolved | systemd | |
User: systemd-resolve Integrity Level: UNKNOWN | ||||
| 39488 | /bin/sh -c "DISPLAY=:0 sudo -iu user firefox https://url\.us\.m\.mimecastprotect\.com/s/kHMoC827DYSP89wolInfxcy0DjM?domain=click\.securedvisit\.com " | /usr/bin/dash | — | any-guest-agent |
User: root Integrity Level: UNKNOWN | ||||
| 39489 | sudo -iu user firefox https://url.us.m.mimecastprotect.com/s/kHMoC827DYSP89wolInfxcy0DjM?domain=click.securedvisit.com | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 39490 | /snap/firefox/3358/usr/lib/firefox/firefox https://url.us.m.mimecastprotect.com/s/kHMoC827DYSP89wolInfxcy0DjM?domain=click.securedvisit.com | /snap/firefox/3358/usr/lib/firefox/firefox | sudo | |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39491 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39502 | /snap/snapd/20290/usr/lib/snapd/snap-seccomp version-info | /snap/snapd/20290/usr/lib/snapd/snap-seccomp | — | firefox |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39510 | /snap/snapd/20290/usr/lib/snapd/snap-confine --base core22 snap.firefox.firefox /usr/lib/snapd/snap-exec firefox https://url.us.m.mimecastprotect.com/s/kHMoC827DYSP89wolInfxcy0DjM?domain=click.securedvisit.com | /snap/snapd/20290/usr/lib/snapd/snap-confine | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39511 | dumpe2fs -h /dev/sda3 | /usr/sbin/dumpe2fs | — | udisksd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39512 | snap-update-ns --from-snap-confine firefox | /snap/snapd/20290/usr/lib/snapd/snap-update-ns | — | firefox |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 39518 | dumpe2fs -h /dev/sda3 | /usr/sbin/dumpe2fs | — | udisksd |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
93
DNS requests
115
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 91.189.91.49:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
39490 | firefox | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
39490 | firefox | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 23.32.238.27:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 23.32.238.82:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 216.58.212.131:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
39490 | firefox | POST | 200 | 216.58.212.131:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.49:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
— | — | 37.19.194.81:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
1178 | snap-store | 37.19.194.81:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
512 | snapd | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
39490 | firefox | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
39490 | firefox | 205.139.111.12:443 | url.us.m.mimecastprotect.com | MIMECAST | US | whitelisted |
39490 | firefox | 34.36.137.203:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
39490 | firefox | 34.160.144.191:443 | content-signature-2.cdn.mozilla.net | GOOGLE | US | whitelisted |
39490 | firefox | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
url.us.m.mimecastprotect.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
39490 | firefox | Not Suspicious Traffic | INFO [ANY.RUN] Firebase Web App Development Platform (firebaseio .com) |
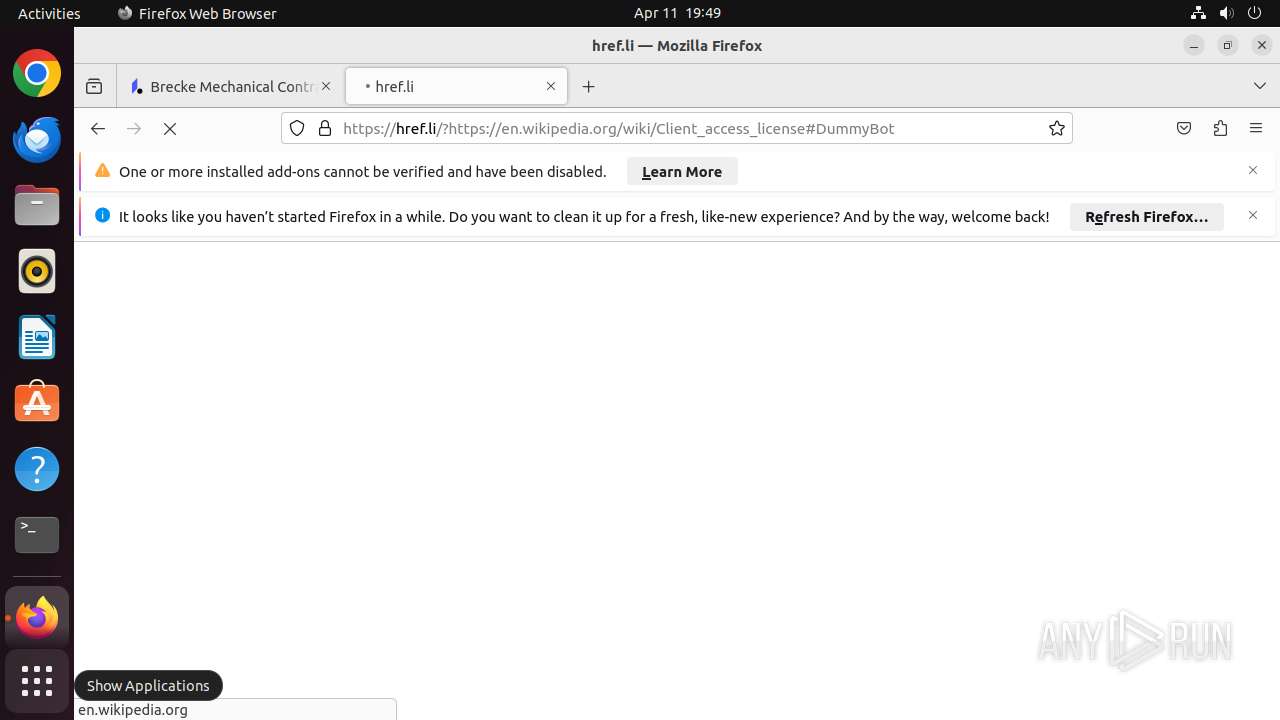
445 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious redirect to Wikipedia (hrefwiki) |
445 | systemd-resolved | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspicious redirect to Wikipedia (hrefwiki) |
2 ETPRO signatures available at the full report