| URL: | https://google.com |
| Full analysis: | https://app.any.run/tasks/ff3b9034-dcaf-4747-b1c8-e0c850e22ba5 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 27, 2025, 09:51:35 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 99999EBCFDB78DF077AD2727FD00969F |
| SHA1: | 72FE95C5576EC634E214814A32AB785568EDA76A |
| SHA256: | 05046F26C83E8C88B3DDAB2EAB63D0D16224AC1E564535FC75CDCEEE47A0938D |
| SSDEEP: | 3:N8r3uK:2LuK |
MALICIOUS
AMADEY mutex has been found
- random.exe (PID: 5720)
- ramez.exe (PID: 7624)
- TempJFKETFLNTSPLUMUNLRXPRTYLSPTYXTGN.EXE (PID: 7404)
AMADEY has been detected (SURICATA)
- ramez.exe (PID: 7624)
Connects to the CnC server
- ramez.exe (PID: 7624)
- svchost.exe (PID: 2196)
- cmd.exe (PID: 6840)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 760)
Run PowerShell with an invisible window
- powershell.exe (PID: 1180)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 1180)
Request from PowerShell that ran from MSHTA.EXE
- powershell.exe (PID: 1180)
AMADEY has been detected (YARA)
- ramez.exe (PID: 7624)
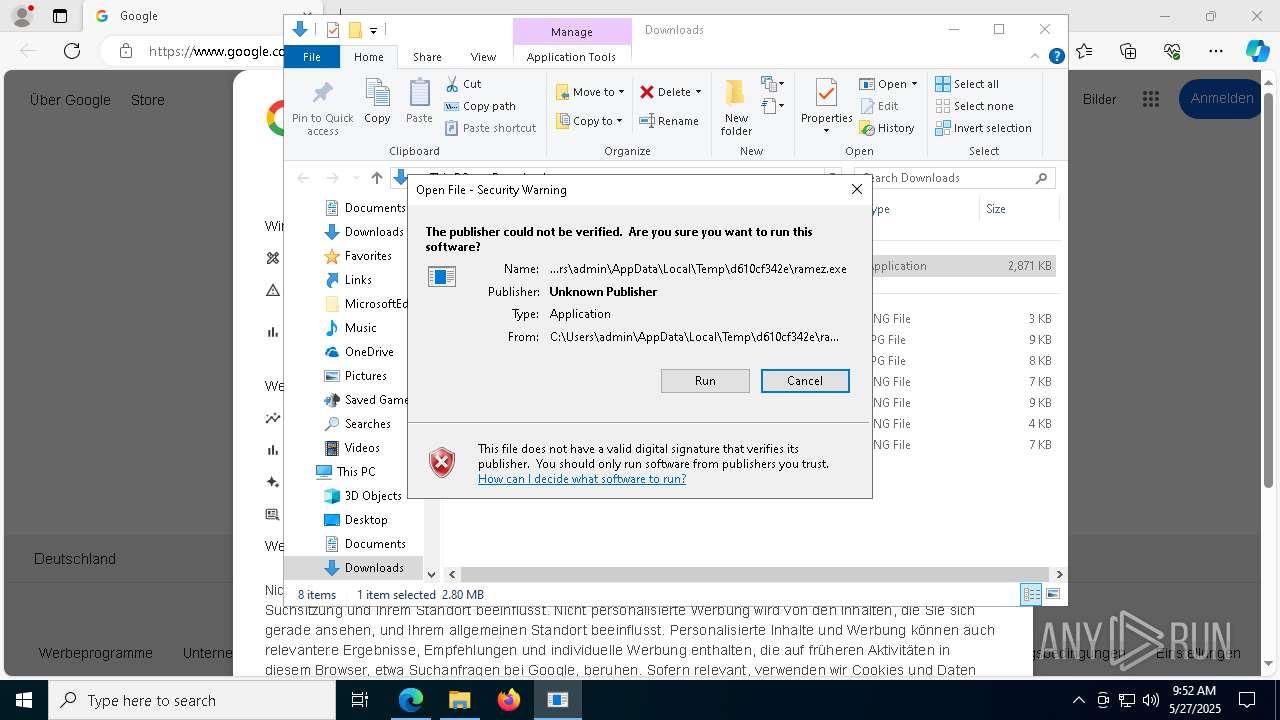
Executing a file with an untrusted certificate
- m9wPaPW.exe (PID: 1184)
- m9wPaPW.exe (PID: 4896)
- m9wPaPW.exe (PID: 8080)
- m9wPaPW.exe (PID: 8016)
- 10731ddb90.exe (PID: 8288)
- sGe7ljJ.exe (PID: 11160)
- sGe7ljJ.exe (PID: 10356)
Registers / Runs the DLL via REGSVR32.EXE
- m9wPaPW.tmp (PID: 2552)
- m9wPaPW.tmp (PID: 7000)
- rundll32.exe (PID: 1040)
HIJACKLOADER has been detected (YARA)
- USilv.exe (PID: 1120)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 1512)
Adds process to the Windows Defender exclusion list
- oxDU0MW.exe (PID: 4336)
Changes Windows Defender settings
- oxDU0MW.exe (PID: 4336)
- NSudoLG.exe (PID: 4608)
- NSudoLG.exe (PID: 9588)
Uses Task Scheduler to autorun other applications
- oxDU0MW.exe (PID: 4336)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 5892)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 3028)
- NSudoLG.exe (PID: 4608)
- cmd.exe (PID: 8948)
- NSudoLG.exe (PID: 9588)
MINER has been detected (SURICATA)
- cmd.exe (PID: 6840)
Starts SC.EXE for service management
- cmd.exe (PID: 3028)
GCLEANER has been detected (SURICATA)
- 10731ddb90.exe (PID: 8288)
ASYNCRAT has been detected (SURICATA)
- rundll32.exe (PID: 9248)
GENERIC has been found (auto)
- 10731ddb90.exe (PID: 8288)
SUSPICIOUS
Potential Corporate Privacy Violation
- msedge.exe (PID: 7340)
- ramez.exe (PID: 7624)
- powershell.exe (PID: 1180)
- ab29c609bc.exe (PID: 3676)
- cmd.exe (PID: 6840)
- 10731ddb90.exe (PID: 8288)
Reads the BIOS version
- random.exe (PID: 5720)
- ramez.exe (PID: 7624)
Reads security settings of Internet Explorer
- random.exe (PID: 5720)
- ramez.exe (PID: 7624)
- xegYmPC.exe (PID: 8040)
- m9wPaPW.tmp (PID: 4404)
Starts itself from another location
- random.exe (PID: 5720)
- USilv.exe (PID: 1616)
- USilv.exe (PID: 8008)
Executable content was dropped or overwritten
- random.exe (PID: 5720)
- ramez.exe (PID: 7624)
- powershell.exe (PID: 1180)
- USilv.exe (PID: 1616)
- xegYmPC.exe (PID: 8040)
- USilv.exe (PID: 1120)
- m9wPaPW.exe (PID: 1184)
- m9wPaPW.tmp (PID: 4404)
- m9wPaPW.exe (PID: 4896)
- m9wPaPW.tmp (PID: 2552)
- m9wPaPW.exe (PID: 8080)
- m9wPaPW.tmp (PID: 3176)
- m9wPaPW.exe (PID: 8016)
- m9wPaPW.tmp (PID: 7000)
- xegYmPC.exe (PID: 2560)
- oxDU0MW.exe (PID: 4336)
- release.exe (PID: 4700)
- BetaContro.exe (PID: 6436)
- jRE9kd1BncC299.exe (PID: 5364)
- Infra-Co.exe (PID: 760)
- df0c0c211d.exe (PID: 5720)
- 7z.exe (PID: 8584)
- Unlocker.exe (PID: 8084)
- cmd.exe (PID: 3028)
- 10731ddb90.exe (PID: 8288)
Connects to the server without a host name
- ramez.exe (PID: 7624)
- powershell.exe (PID: 1180)
- ab29c609bc.exe (PID: 3676)
- 10731ddb90.exe (PID: 8288)
Contacting a server suspected of hosting an CnC
- ramez.exe (PID: 7624)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 1512)
- rundll32.exe (PID: 3884)
- rundll32.exe (PID: 9248)
Starts CMD.EXE for commands execution
- f718e4cb38.exe (PID: 3676)
- release.exe (PID: 4700)
- oxDU0MW.exe (PID: 4336)
- df0c0c211d.exe (PID: 5720)
- cmd.exe (PID: 5868)
- NSudoLG.exe (PID: 5172)
- cmd.exe (PID: 1696)
- cmd.exe (PID: 3028)
- Unlocker.exe (PID: 8648)
- ff6072db20.exe (PID: 8796)
- NSudoLG.exe (PID: 4212)
- cmd.exe (PID: 9028)
- Unlocker.exe (PID: 8084)
- cmd.exe (PID: 8948)
- cmd.exe (PID: 8744)
- Unlocker.exe (PID: 9768)
- Unlocker.exe (PID: 9740)
Found IP address in command line
- powershell.exe (PID: 1180)
Manipulates environment variables
- powershell.exe (PID: 1180)
Starts process via Powershell
- powershell.exe (PID: 1180)
Probably download files using WebClient
- mshta.exe (PID: 5216)
Process requests binary or script from the Internet
- ramez.exe (PID: 7624)
- powershell.exe (PID: 1180)
- ab29c609bc.exe (PID: 3676)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 5216)
- m9wPaPW.tmp (PID: 2552)
- regsvr32.exe (PID: 656)
- m9wPaPW.tmp (PID: 7000)
- regsvr32.exe (PID: 7216)
- rundll32.exe (PID: 1040)
- regsvr32.exe (PID: 4120)
- oxDU0MW.exe (PID: 4336)
- NSudoLG.exe (PID: 4608)
- cmd.exe (PID: 8356)
- NSudoLG.exe (PID: 9588)
There is functionality for enable RDP (YARA)
- ramez.exe (PID: 7624)
Reads the Windows owner or organization settings
- m9wPaPW.tmp (PID: 4404)
- m9wPaPW.tmp (PID: 2552)
PowerShell delay command usage (probably sleep evasion)
- powershell.exe (PID: 5868)
- powershell.exe (PID: 1128)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 9612)
Get information on the list of running processes
- regsvr32.exe (PID: 656)
- regsvr32.exe (PID: 7216)
- rundll32.exe (PID: 1040)
- regsvr32.exe (PID: 4120)
- cmd.exe (PID: 3900)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3888)
- cmd.exe (PID: 8948)
There is functionality for taking screenshot (YARA)
- USilv.exe (PID: 1120)
- jRE9kd1BncC299.exe (PID: 5364)
- USilv.exe (PID: 4000)
Hides errors and continues executing the command without stopping
- powershell.exe (PID: 6208)
Filtering the input of cmdlet (POWERSHELL)
- powershell.exe (PID: 6208)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 5576)
- rundll32.exe (PID: 3796)
- rundll32.exe (PID: 1040)
Executes as Windows Service
- rundll32.exe (PID: 1040)
- cmd.exe (PID: 8356)
Script adds exclusion path to Windows Defender
- oxDU0MW.exe (PID: 4336)
- NSudoLG.exe (PID: 4608)
- NSudoLG.exe (PID: 9588)
The process executes via Task Scheduler
- ramez.exe (PID: 4376)
- ramez.exe (PID: 10828)
- ramez.exe (PID: 8816)
- ramez.exe (PID: 8644)
Application launched itself
- rundll32.exe (PID: 1040)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 1696)
- cmd.exe (PID: 9028)
- cmd.exe (PID: 8744)
- cmd.exe (PID: 8948)
Script adds exclusion process to Windows Defender
- oxDU0MW.exe (PID: 4336)
Drops a system driver (possible attempt to evade defenses)
- release.exe (PID: 4700)
- Unlocker.exe (PID: 8084)
Hides command output
- cmd.exe (PID: 4892)
- cmd.exe (PID: 4452)
- cmd.exe (PID: 8084)
- cmd.exe (PID: 8048)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 1756)
- cmd.exe (PID: 5176)
- cmd.exe (PID: 5224)
- cmd.exe (PID: 6832)
Stops a currently running service
- sc.exe (PID: 1532)
- sc.exe (PID: 6352)
- sc.exe (PID: 8360)
- sc.exe (PID: 9696)
- sc.exe (PID: 9880)
- sc.exe (PID: 10004)
- sc.exe (PID: 5236)
- sc.exe (PID: 9312)
- sc.exe (PID: 9488)
- sc.exe (PID: 9836)
- sc.exe (PID: 10064)
- sc.exe (PID: 10212)
- sc.exe (PID: 4556)
- sc.exe (PID: 3140)
- sc.exe (PID: 9496)
- sc.exe (PID: 10036)
- sc.exe (PID: 9244)
- sc.exe (PID: 9448)
- sc.exe (PID: 9904)
Starts SC.EXE for service management
- cmd.exe (PID: 4892)
- cmd.exe (PID: 4452)
- cmd.exe (PID: 8048)
- cmd.exe (PID: 8084)
- cmd.exe (PID: 8828)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 1756)
- cmd.exe (PID: 5176)
- cmd.exe (PID: 5224)
- cmd.exe (PID: 5640)
- cmd.exe (PID: 6832)
- cmd.exe (PID: 10192)
- cmd.exe (PID: 10244)
Windows service management via SC.EXE
- sc.exe (PID: 7212)
- sc.exe (PID: 3016)
- sc.exe (PID: 5756)
- sc.exe (PID: 8840)
- sc.exe (PID: 9104)
- sc.exe (PID: 9192)
- sc.exe (PID: 8844)
- sc.exe (PID: 9016)
- sc.exe (PID: 4192)
- sc.exe (PID: 6480)
- sc.exe (PID: 9660)
- sc.exe (PID: 9776)
- sc.exe (PID: 9848)
- sc.exe (PID: 9912)
- sc.exe (PID: 9972)
- sc.exe (PID: 10112)
- sc.exe (PID: 10216)
- sc.exe (PID: 8088)
- sc.exe (PID: 9468)
- sc.exe (PID: 9560)
- sc.exe (PID: 9332)
- sc.exe (PID: 2616)
- sc.exe (PID: 9808)
- sc.exe (PID: 9876)
- sc.exe (PID: 9944)
- sc.exe (PID: 10072)
- sc.exe (PID: 10176)
- sc.exe (PID: 10220)
- sc.exe (PID: 8164)
- sc.exe (PID: 9884)
- sc.exe (PID: 9536)
- sc.exe (PID: 9788)
- sc.exe (PID: 7104)
- sc.exe (PID: 9268)
- sc.exe (PID: 9968)
- sc.exe (PID: 10172)
- sc.exe (PID: 10228)
- sc.exe (PID: 9844)
- sc.exe (PID: 8136)
- sc.exe (PID: 9516)
- sc.exe (PID: 6512)
- sc.exe (PID: 9932)
- sc.exe (PID: 9372)
- sc.exe (PID: 10392)
- sc.exe (PID: 10556)
- sc.exe (PID: 10584)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 5216)
Process drops legitimate windows executable
- jRE9kd1BncC299.exe (PID: 5364)
- cmd.exe (PID: 3028)
Starts a Microsoft application from unusual location
- Infra-Co.exe (PID: 760)
Connects to unusual port
- oxDU0MW.exe (PID: 4336)
- rundll32.exe (PID: 3884)
- cmd.exe (PID: 6840)
- rundll32.exe (PID: 9248)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 7976)
- cmd.exe (PID: 4428)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 5548)
Uses powercfg.exe to modify the power settings
- oxDU0MW.exe (PID: 4336)
Checks for external IP
- svchost.exe (PID: 2196)
- oxDU0MW.exe (PID: 4336)
Creates a new Windows service
- sc.exe (PID: 7000)
- sc.exe (PID: 976)
Drops 7-zip archiver for unpacking
- df0c0c211d.exe (PID: 5720)
Executing commands from a ".bat" file
- df0c0c211d.exe (PID: 5720)
- cmd.exe (PID: 5868)
- NSudoLG.exe (PID: 5172)
- cmd.exe (PID: 1696)
- cmd.exe (PID: 9028)
- NSudoLG.exe (PID: 4212)
- cmd.exe (PID: 8744)
- ff6072db20.exe (PID: 8796)
Starts application with an unusual extension
- cmd.exe (PID: 5232)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 8948)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 5232)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 8948)
The executable file from the user directory is run by the CMD process
- NSudoLG.exe (PID: 5172)
- NSudoLG.exe (PID: 4608)
- 7z.exe (PID: 8584)
- Unlocker.exe (PID: 8648)
- NSudoLG.exe (PID: 4212)
- Unlocker.exe (PID: 8084)
- NSudoLG.exe (PID: 9588)
- 7z.exe (PID: 8128)
- Unlocker.exe (PID: 9768)
- Unlocker.exe (PID: 9740)
Executes application which crashes
- ab29c609bc.exe (PID: 3676)
- Win-v41.exe (PID: 8876)
- ramez.exe (PID: 8816)
There is functionality for VM detection VirtualBox (YARA)
- oxDU0MW.exe (PID: 4336)
There is functionality for VM detection VMWare (YARA)
- oxDU0MW.exe (PID: 4336)
Invokes assembly entry point (POWERSHELL)
- powershell.exe (PID: 8372)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 8356)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3028)
- cmd.exe (PID: 8948)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2088)
- cmd.exe (PID: 8608)
- cmd.exe (PID: 9640)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 10200)
- schtasks.exe (PID: 10108)
- schtasks.exe (PID: 8992)
- schtasks.exe (PID: 1244)
- schtasks.exe (PID: 9340)
INFO
Checks supported languages
- identity_helper.exe (PID: 5428)
- random.exe (PID: 5720)
- f718e4cb38.exe (PID: 3676)
- ramez.exe (PID: 7624)
- TempJFKETFLNTSPLUMUNLRXPRTYLSPTYXTGN.EXE (PID: 7404)
- USilv.exe (PID: 1616)
- USilv.exe (PID: 1120)
- xegYmPC.exe (PID: 8040)
- m9wPaPW.tmp (PID: 4404)
- m9wPaPW.exe (PID: 4896)
- m9wPaPW.exe (PID: 1184)
- m9wPaPW.tmp (PID: 2552)
Application launched itself
- msedge.exe (PID: 208)
Reads Environment values
- identity_helper.exe (PID: 5428)
Reads the computer name
- identity_helper.exe (PID: 5428)
- random.exe (PID: 5720)
- f718e4cb38.exe (PID: 3676)
- ramez.exe (PID: 7624)
- xegYmPC.exe (PID: 8040)
- USilv.exe (PID: 1616)
- m9wPaPW.exe (PID: 1184)
- m9wPaPW.tmp (PID: 4404)
- m9wPaPW.exe (PID: 4896)
- USilv.exe (PID: 1120)
- m9wPaPW.tmp (PID: 2552)
Executable content was dropped or overwritten
- msedge.exe (PID: 208)
- msedge.exe (PID: 7340)
- msedge.exe (PID: 2088)
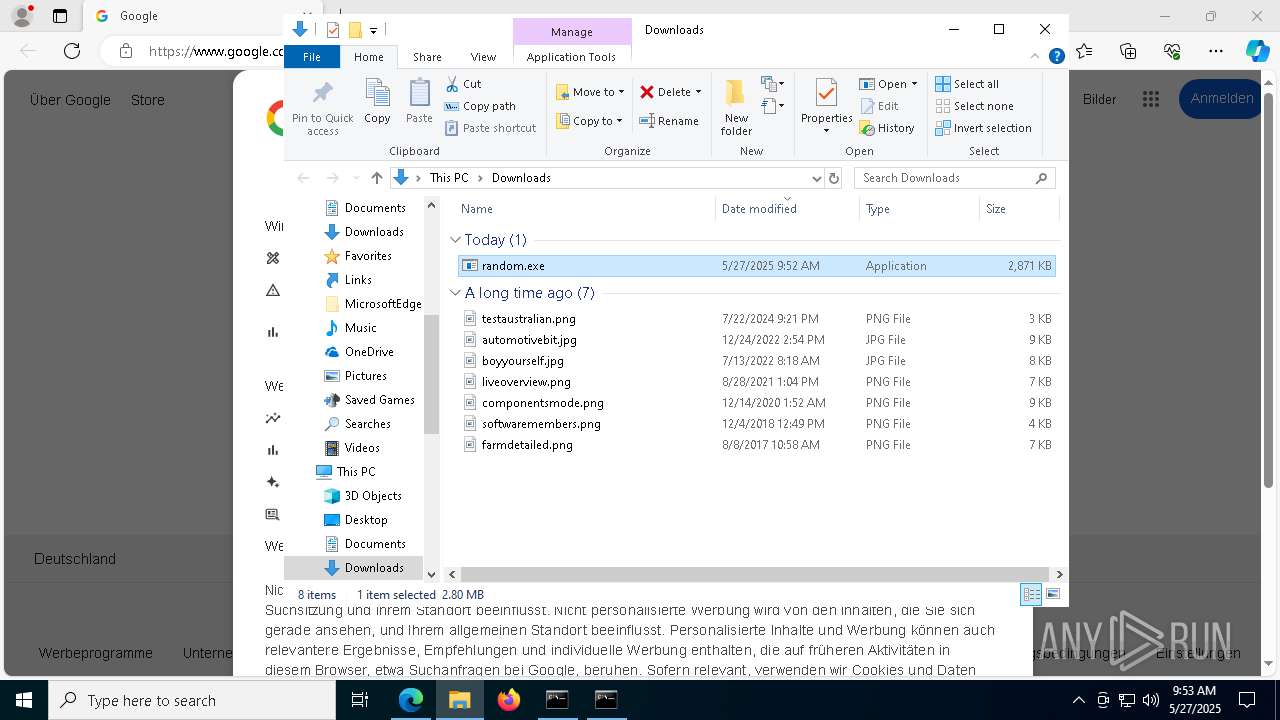
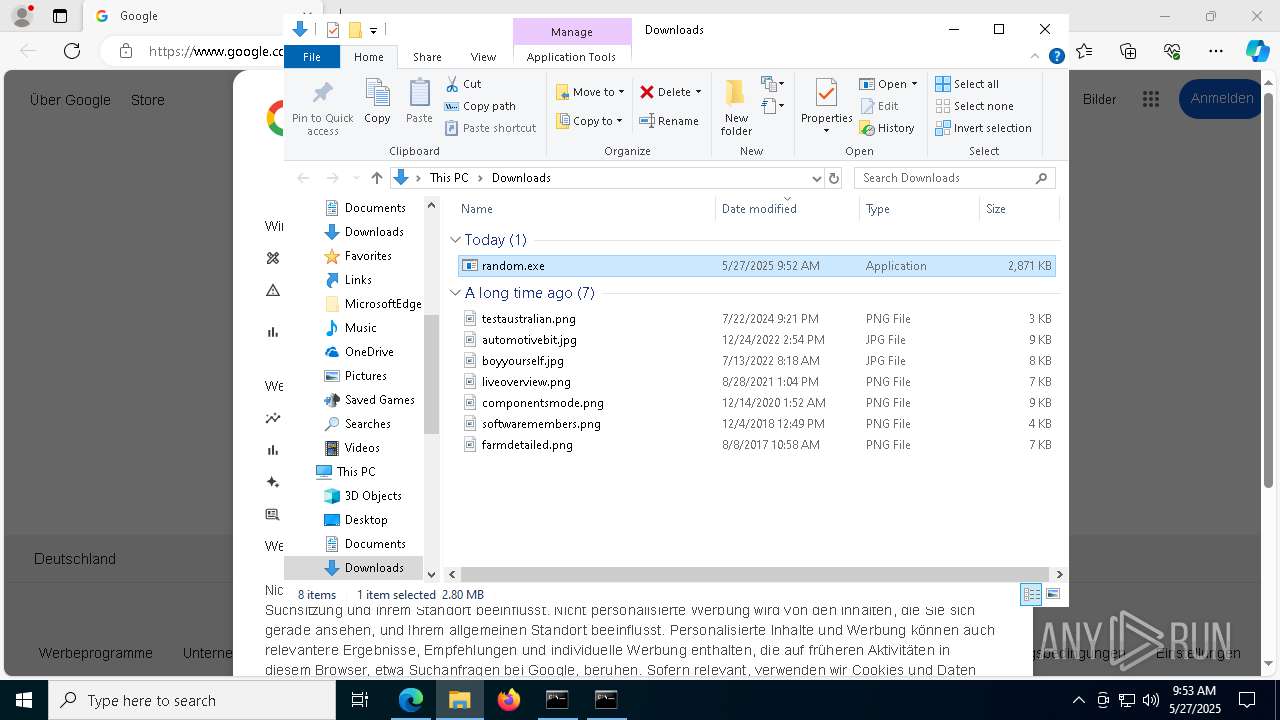
Launch of the file from Downloads directory
- msedge.exe (PID: 1328)
- msedge.exe (PID: 208)
Manual execution by a user
- random.exe (PID: 5720)
Create files in a temporary directory
- random.exe (PID: 5720)
- ramez.exe (PID: 7624)
- f718e4cb38.exe (PID: 3676)
- xegYmPC.exe (PID: 8040)
- USilv.exe (PID: 1120)
- m9wPaPW.exe (PID: 1184)
- m9wPaPW.tmp (PID: 4404)
- m9wPaPW.exe (PID: 4896)
Reads the machine GUID from the registry
- random.exe (PID: 5720)
Process checks computer location settings
- random.exe (PID: 5720)
- xegYmPC.exe (PID: 8040)
- ramez.exe (PID: 7624)
- m9wPaPW.tmp (PID: 4404)
Checks proxy server information
- ramez.exe (PID: 7624)
- powershell.exe (PID: 1180)
Creates files or folders in the user directory
- ramez.exe (PID: 7624)
- m9wPaPW.tmp (PID: 2552)
- USilv.exe (PID: 1120)
The sample compiled with english language support
- ramez.exe (PID: 7624)
- xegYmPC.exe (PID: 8040)
- USilv.exe (PID: 1616)
- USilv.exe (PID: 1120)
- xegYmPC.exe (PID: 2560)
- release.exe (PID: 4700)
- jRE9kd1BncC299.exe (PID: 5364)
- Infra-Co.exe (PID: 760)
- df0c0c211d.exe (PID: 5720)
- msedge.exe (PID: 2088)
- Unlocker.exe (PID: 8084)
- cmd.exe (PID: 3028)
Reads mouse settings
- f718e4cb38.exe (PID: 3676)
Reads Internet Explorer settings
- mshta.exe (PID: 5216)
Launch of the file from Task Scheduler
- cmd.exe (PID: 760)
Disables trace logs
- powershell.exe (PID: 1180)
The executable file from the user directory is run by the Powershell process
- TempJFKETFLNTSPLUMUNLRXPRTYLSPTYXTGN.EXE (PID: 7404)
Themida protector has been detected
- ramez.exe (PID: 7624)
Creates files in the program directory
- USilv.exe (PID: 1616)
- USilv.exe (PID: 1120)
- m9wPaPW.tmp (PID: 2552)
The sample compiled with chinese language support
- m9wPaPW.tmp (PID: 2552)
- USilv.exe (PID: 1120)
Creates a software uninstall entry
- m9wPaPW.tmp (PID: 2552)
Changes the display of characters in the console
- cmd.exe (PID: 5232)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 8948)
Starts MODE.COM to configure console settings
- mode.com (PID: 5156)
- mode.com (PID: 8744)
Checks operating system version
- cmd.exe (PID: 3028)
- cmd.exe (PID: 8948)
Application based on Rust
- rundll32.exe (PID: 1040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
595
Monitored processes
438
Malicious processes
39
Suspicious processes
21
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://google.com" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7124 --field-trial-handle=2256,i,1704193125331948162,8468997954746332124,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 496 | "C:\Users\admin\AppData\Roaming\Monmon5\tcpvcon.exe" "C:\Users\admin\AppData\Roaming\Monmon5\tcpvcon.exe" /accepteula | C:\Users\admin\AppData\Roaming\Monmon5\tcpvcon.exe | — | USilv.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: HIGH Description: Sysinternals TcpVcon Version: 4.18 Modules
| |||||||||||||||
| 632 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=5328 --field-trial-handle=2256,i,1704193125331948162,8468997954746332124,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 656 | /s /i:SERVICE "C:\ProgramData\738\sechost-7704b00a.p12" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --no-appcompat-clear --mojo-platform-channel-handle=5008 --field-trial-handle=2256,i,1704193125331948162,8468997954746332124,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 680 | "powershell" -Command "Get-Process | Select-Object -ExpandProperty ProcessName" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | reg query "HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System" /v "EnableLUA" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | C:\WINDOWS\system32\cmd.exe /c schtasks /create /tn qL6hsmaq1ZA /tr "mshta C:\Users\admin\AppData\Local\Temp\barseTUen.hta" /sc minute /mo 25 /ru "admin" /f | C:\Windows\SysWOW64\cmd.exe | — | f718e4cb38.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 760 | "C:\Users\admin\AppData\Local\Temp\Infra-Co.exe" | C:\Users\admin\AppData\Local\Temp\Infra-Co.exe | jRE9kd1BncC299.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Test Authoring and Execution Framework [v10.88] Version: 10.88.2411.08001 Modules
| |||||||||||||||
Total events
125 160
Read events
124 632
Write events
322
Delete events
206
Modification events
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8BB6654BB1942F00 | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: B6C46A4BB1942F00 | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262990 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CDA2E37B-E7A1-458A-A45D-34EC879758DC} | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262990 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D759EA58-A7A3-4194-8CD1-CB7D077008E6} | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262990 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5A98ADAF-4E11-4FA7-B44C-B85640C992FB} | |||
| (PID) Process: | (208) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 1DD39F4BB1942F00 | |||
Executable files
95
Suspicious files
261
Text files
304
Unknown types
52
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10a809.TMP | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10a809.TMP | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10a819.TMP | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10a829.TMP | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10a867.TMP | — | |
MD5:— | SHA256:— | |||
| 208 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
112
TCP/UDP connections
149
DNS requests
104
Threats
80
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7624 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7340 | msedge.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/mine/random.exe | unknown | — | — | malicious |
7624 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7624 | ramez.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/test/exe/random.exe | unknown | — | — | malicious |
7624 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
7624 | ramez.exe | POST | 200 | 185.156.72.96:80 | http://185.156.72.96/te4h2nus/index.php | unknown | — | — | unknown |
1180 | powershell.exe | GET | 200 | 185.156.72.2:80 | http://185.156.72.2/testmine/random.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1284 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5796 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
7340 | msedge.exe | 142.250.186.132:443 | www.google.com | — | — | whitelisted |
7340 | msedge.exe | 142.250.185.110:443 | google.com | — | — | whitelisted |
208 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7340 | msedge.exe | 2.16.241.205:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
www.google.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7340 | msedge.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 35 |
7340 | msedge.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7340 | msedge.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7340 | msedge.exe | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |
7624 | ramez.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 35 |
7624 | ramez.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey HTTP POST Request (st=s) |
7624 | ramez.exe | Malware Command and Control Activity Detected | ET MALWARE Amadey CnC Response |
7624 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
7624 | ramez.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
7624 | ramez.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |