| URL: | https://google.com |
| Full analysis: | https://app.any.run/tasks/b92835d7-08db-4ba0-8190-2e696fa1c416 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | August 12, 2022, 23:00:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 99999EBCFDB78DF077AD2727FD00969F |
| SHA1: | 72FE95C5576EC634E214814A32AB785568EDA76A |
| SHA256: | 05046F26C83E8C88B3DDAB2EAB63D0D16224AC1E564535FC75CDCEEE47A0938D |
| SSDEEP: | 3:N8r3uK:2LuK |
MALICIOUS
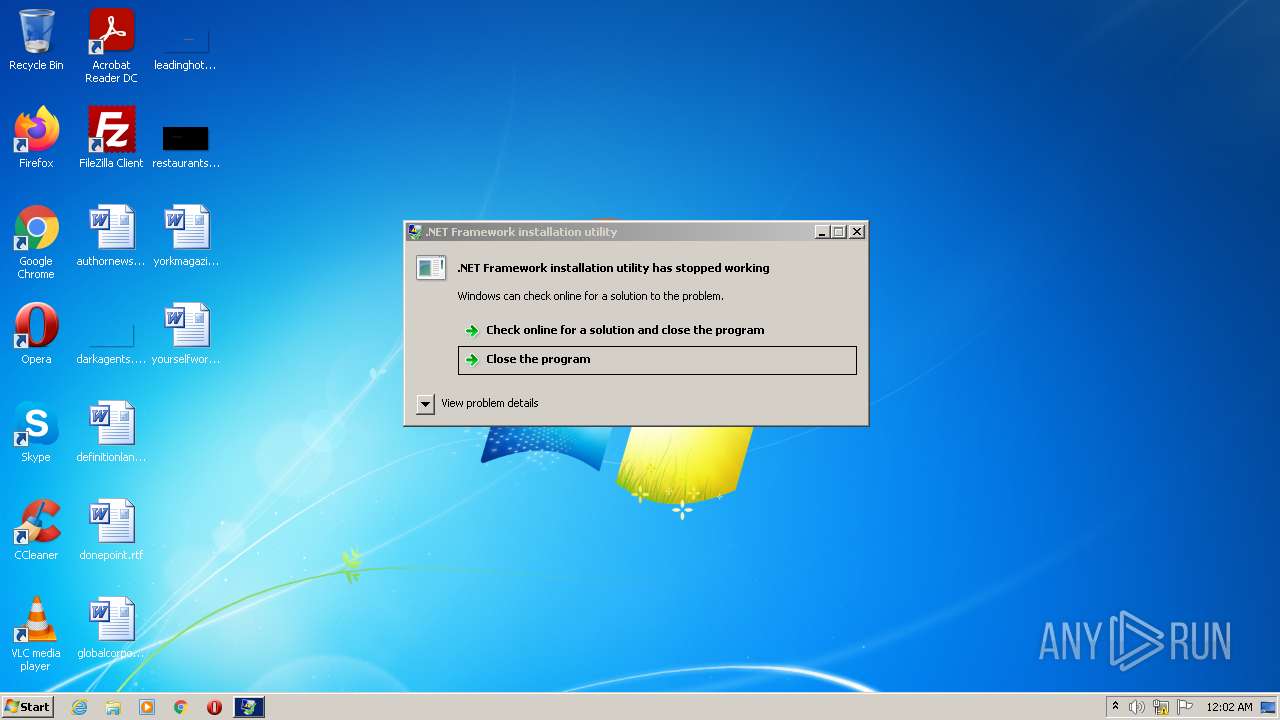
Drops executable file immediately after starts
- chrome.exe (PID: 3448)
- WindowsSystemGuardRuntime.exe (PID: 2408)
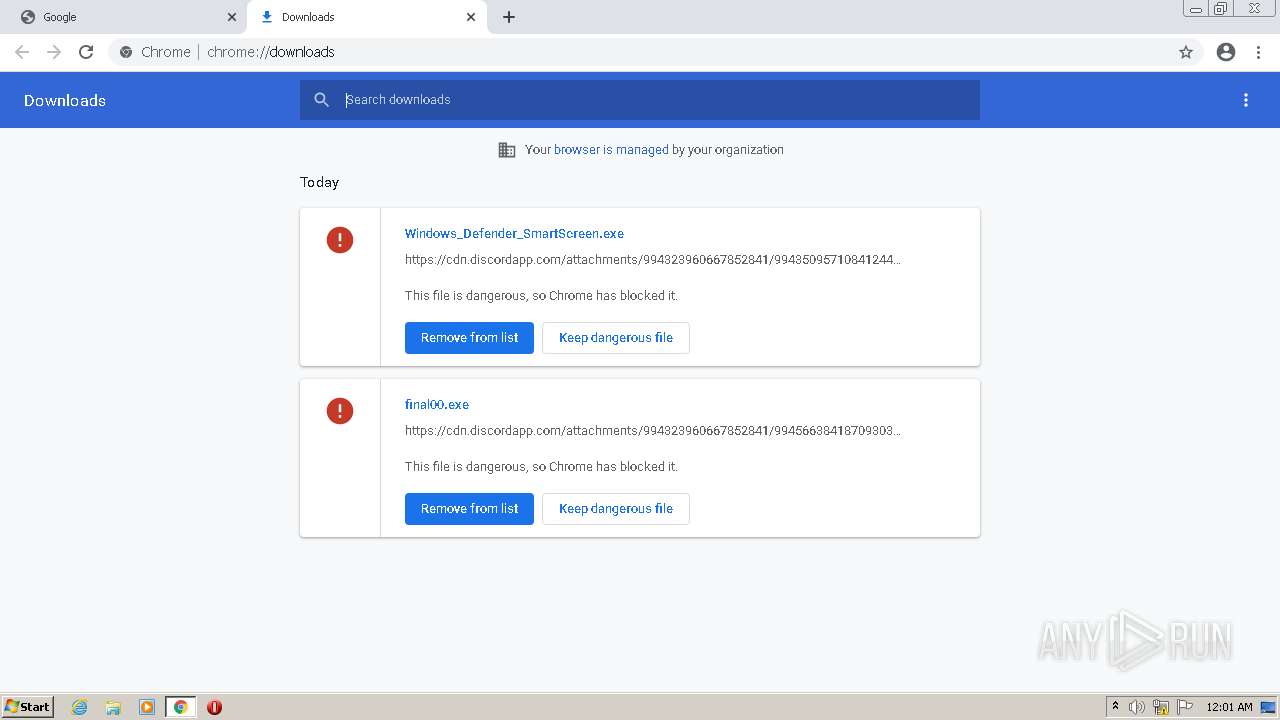
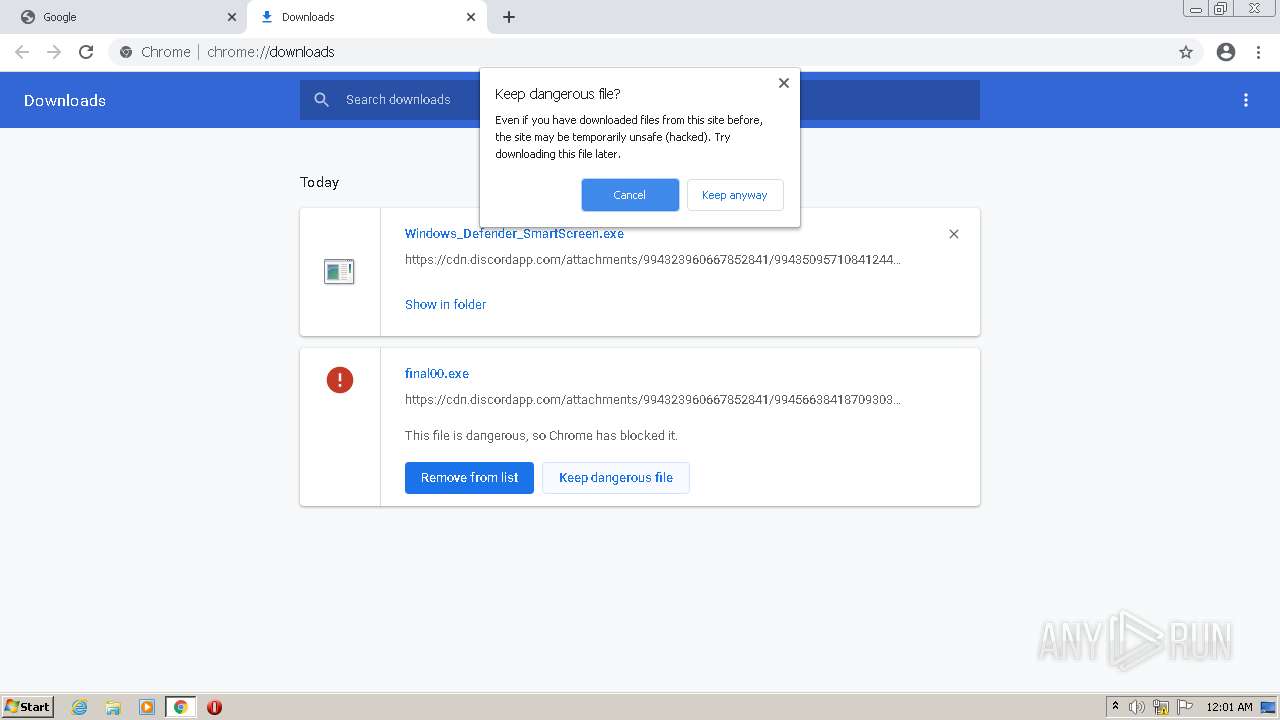
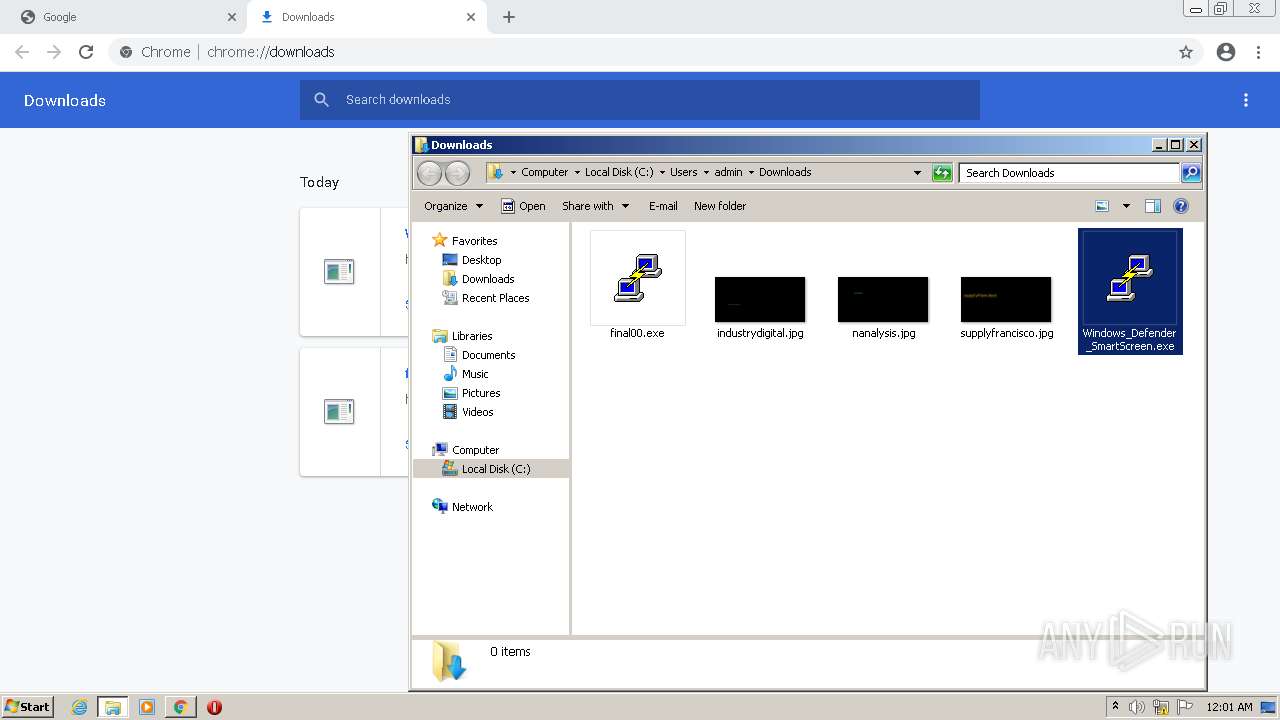
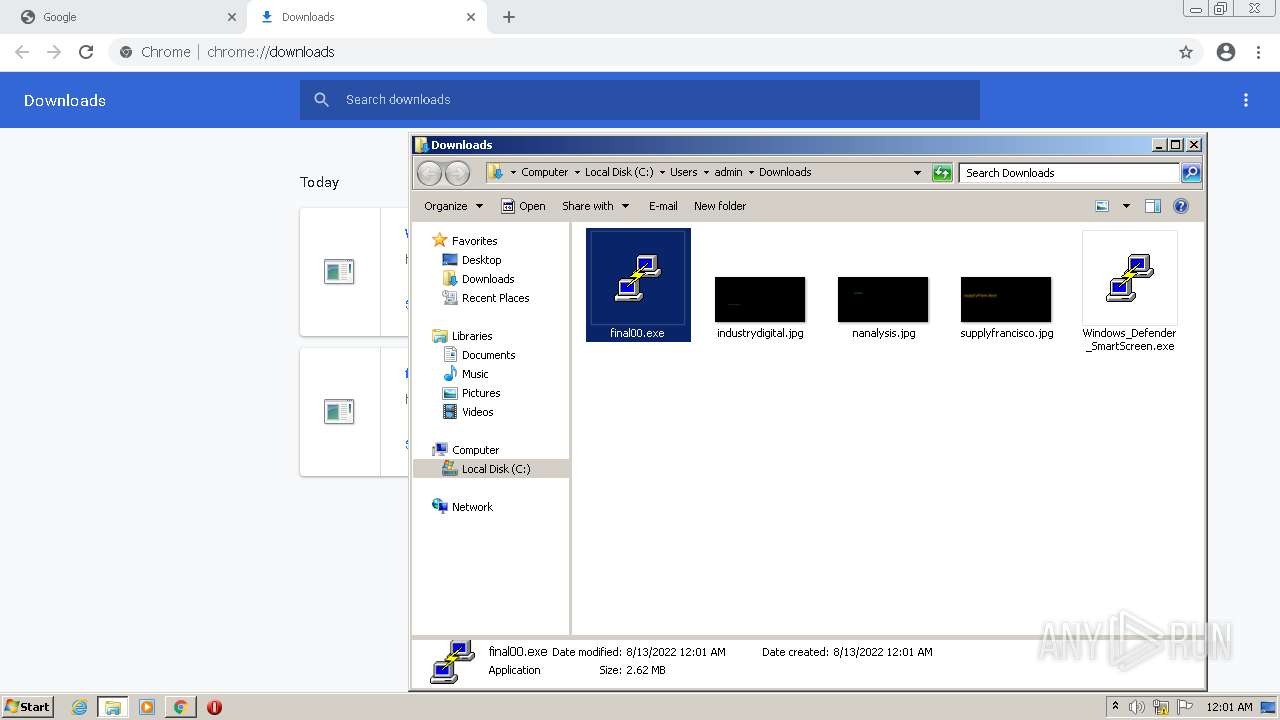
- final00.exe (PID: 968)
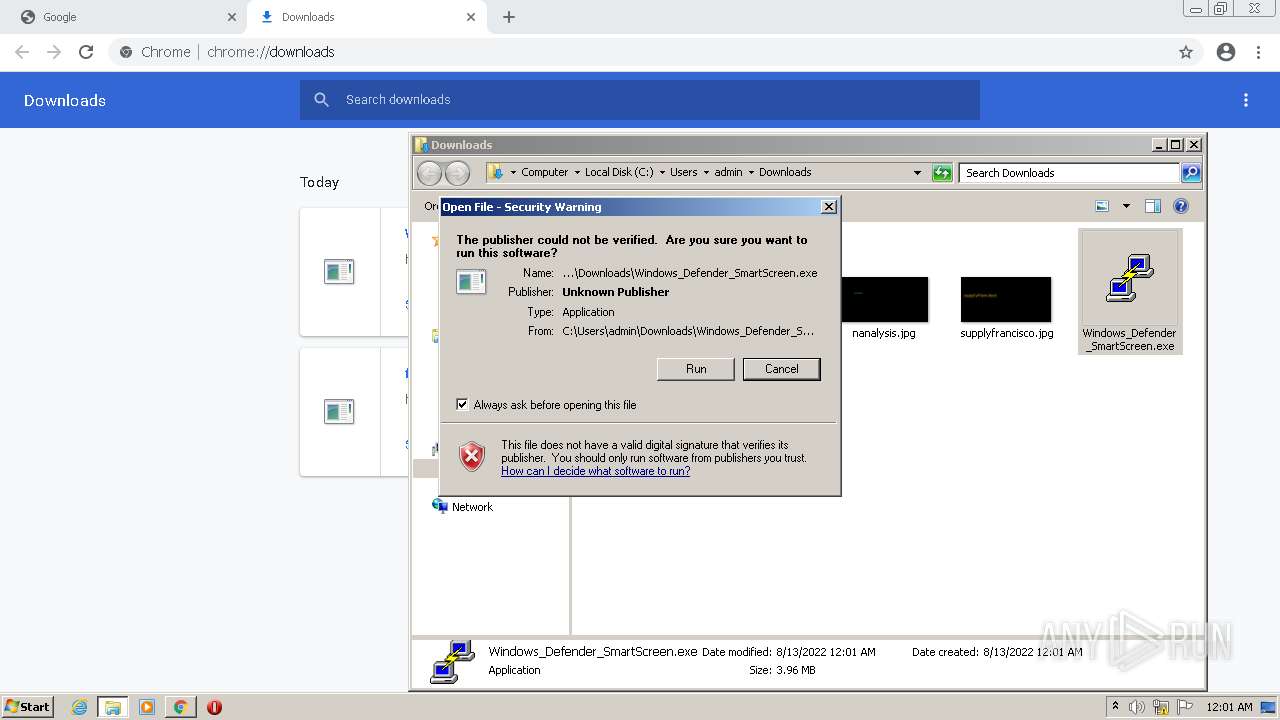
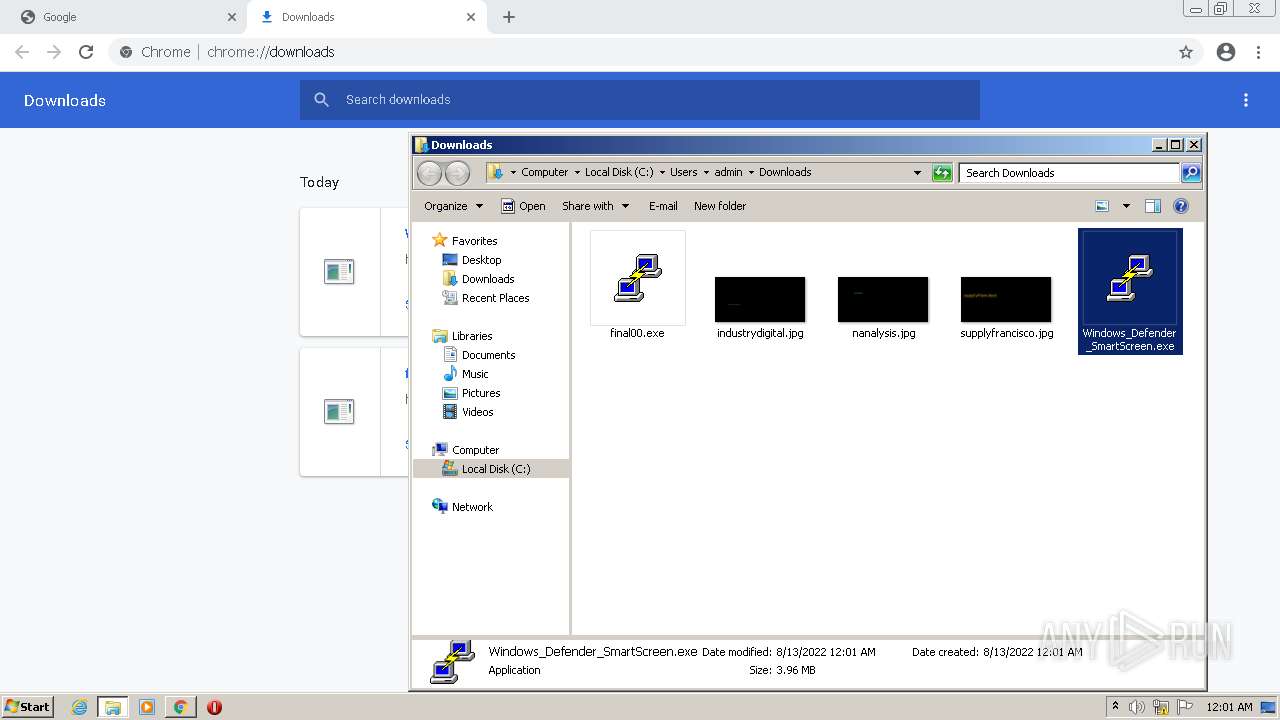
- Windows_Defender_SmartScreen.exe (PID: 3584)
- msiexec2.exe (PID: 3092)
- cmd.exe (PID: 3744)
Application was dropped or rewritten from another process
- final00.exe (PID: 968)
- Windows_Defender_SmartScreen.exe (PID: 3584)
- WindowsSystemGuardRuntime.exe (PID: 2408)
- dataencod.exe (PID: 3496)
- msiexec2.exe (PID: 3092)
- SecurityHealthService.exe (PID: 2332)
- tmpA2D.tmp.exe (PID: 3488)
Changes the autorun value in the registry
- powershell.exe (PID: 2604)
- Windows_Defender_SmartScreen.exe (PID: 3584)
- reg.exe (PID: 3820)
ASYNCRAT detected by memory dumps
- Windows_Defender_SmartScreen.exe (PID: 3584)
- RegAsm.exe (PID: 3148)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 3448)
- WindowsSystemGuardRuntime.exe (PID: 2408)
- final00.exe (PID: 968)
- Windows_Defender_SmartScreen.exe (PID: 3584)
- msiexec2.exe (PID: 3092)
- cmd.exe (PID: 3744)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3448)
Drops a file with a compile date too recent
- chrome.exe (PID: 3448)
- WindowsSystemGuardRuntime.exe (PID: 2408)
- final00.exe (PID: 968)
- Windows_Defender_SmartScreen.exe (PID: 3584)
- msiexec2.exe (PID: 3092)
- cmd.exe (PID: 3744)
Reads the computer name
- final00.exe (PID: 968)
- Windows_Defender_SmartScreen.exe (PID: 3584)
- WindowsSystemGuardRuntime.exe (PID: 2408)
- SecurityHealthService.exe (PID: 2332)
- dataencod.exe (PID: 3496)
- RegAsm.exe (PID: 3148)
- msiexec2.exe (PID: 3092)
- powershell.exe (PID: 2604)
- InstallUtil.exe (PID: 2456)
- tmpA2D.tmp.exe (PID: 3488)
Checks supported languages
- final00.exe (PID: 968)
- Windows_Defender_SmartScreen.exe (PID: 3584)
- WindowsSystemGuardRuntime.exe (PID: 2408)
- SecurityHealthService.exe (PID: 2332)
- msiexec2.exe (PID: 3092)
- dataencod.exe (PID: 3496)
- powershell.exe (PID: 2604)
- cmd.exe (PID: 2788)
- RegAsm.exe (PID: 3148)
- cmd.exe (PID: 3744)
- InstallUtil.exe (PID: 2456)
- cmd.exe (PID: 3476)
- tmpA2D.tmp.exe (PID: 3488)
Reads Environment values
- final00.exe (PID: 968)
- dataencod.exe (PID: 3496)
- msiexec2.exe (PID: 3092)
INFO
Checks supported languages
- chrome.exe (PID: 3448)
- chrome.exe (PID: 2064)
- chrome.exe (PID: 1032)
- chrome.exe (PID: 2748)
- chrome.exe (PID: 2156)
- chrome.exe (PID: 2460)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 1204)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 504)
- chrome.exe (PID: 3088)
- chrome.exe (PID: 2436)
- chrome.exe (PID: 2668)
- chrome.exe (PID: 3464)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 2412)
- chrome.exe (PID: 1020)
- chrome.exe (PID: 2740)
- chrome.exe (PID: 3400)
- chrome.exe (PID: 2728)
- chrome.exe (PID: 3188)
- chrome.exe (PID: 2724)
- chrome.exe (PID: 2688)
- chrome.exe (PID: 468)
- schtasks.exe (PID: 2072)
- PING.EXE (PID: 1980)
- PING.EXE (PID: 1144)
- PING.EXE (PID: 2380)
- reg.exe (PID: 3820)
Reads the computer name
- chrome.exe (PID: 3448)
- chrome.exe (PID: 2064)
- chrome.exe (PID: 2156)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 2668)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 3188)
- chrome.exe (PID: 3400)
- chrome.exe (PID: 468)
- PING.EXE (PID: 1980)
- PING.EXE (PID: 1144)
- PING.EXE (PID: 2380)
Application launched itself
- chrome.exe (PID: 3448)
Reads settings of System Certificates
- chrome.exe (PID: 2156)
- final00.exe (PID: 968)
- dataencod.exe (PID: 3496)
- powershell.exe (PID: 2604)
- msiexec2.exe (PID: 3092)
Checks Windows Trust Settings
- chrome.exe (PID: 3448)
- powershell.exe (PID: 2604)
Reads the date of Windows installation
- chrome.exe (PID: 468)
Manual execution by user
- final00.exe (PID: 968)
- Windows_Defender_SmartScreen.exe (PID: 3584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(3584) Windows_Defender_SmartScreen.exe
C2 (1)217.64.31.3
Ports (1)9742
Version1.0.7
Autorunfalse
MutexWindows Defender SmartScreen
CertificateMIICMDCCAZmgAwIBAgIVAMFTrb8Q6GSd0JjxO7QkGLiOdkWDMA0GCSqGSIb3DQEBDQUAMGQxFTATBgNVBAMMDERjUmF0IFNlcnZlcjETMBEGA1UECwwKcXdxZGFuY2h1bjEcMBoGA1UECgwTRGNSYXQgQnkgcXdxZGFuY2h1bjELMAkGA1UEBwwCU0gxCzAJBgNVBAYTAkNOMB4XDTIxMDYxOTEwMTgyM1oXDTMyMDMyODEwMTgyM1owEDEOMAwGA1UEAwwFRGNSYXQwgZ8wDQYJKoZIhvcNAQEBBQADgY0A...
Server_SignaturemDlyf+9cSmVoQIqJow5k5sfHGNGtAkGK5cg4CHsxiXUVgkPSHs5q9p4+GmX7ELrZ/PP1aYTsxwW3LwP7xJ+AV2B+W7LhbVb19j39rfrcFcR+xehbv/MGGuRuGIARZih+NX9qE9QQuyDE6/2u/YvDq78cjdn+y6a15f0ZNzoAisU=
AntiVMfalse
PasteBinnull
bdosfalse
Botnetwindows defender smartscreen
Aes_Keycab077b6fe23443344120eed605a7cc1ebc1c00f3fb99f900dc72615a2e73c60
SaltDcRatByqwqdanchun
Install_Folder%AppData%
(PID) Process(3148) RegAsm.exe
C2 (1)217.64.31.3
Ports (1)8437
Version0.5.7B
Autorunfalse
MutexWindows System Guard Runtime
CertificateMIIE4jCCAsqgAwIBAgIQAJmupDKFEn4QYTi6VNAu5zANBgkqhkiG9w0BAQ0FADASMRAwDgYDVQQDDAd3YXJyaW9yMCAXDTIyMDEzMDE3MzkzNFoYDzk5OTkxMjMxMjM1OTU5WjASMRAwDgYDVQQDDAd3YXJyaW9yMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA1p1heFXbFVfmtOd5Qw+jVCq6buTiUXzCHJ9ogNwGpJyyNyN70miKC4VIi30fCZ1IXcc8rAM4ODRzPV6HEPOKw29lKaG6kXtr...
Server_SignatureCdU9lYO+Koks/ooZPxCaIlyD1WjzrqKI89/8+bcbG1K2UJtehFNz4cSy2lbrJpp6/ogVAPJ+2mSy/CS6m0GjGVHT07mGU+LeBKx8o7rBrP7Kr0dZDjVOymu3jMayQKI/j6/PO6ZDe/kGjN0G3lVTGQo2z/6fFKB+6eaPIZDmsfatxkipqg7sItTszB2qr8nEgDi4iwc6tY65ctsabbmZqhK0s7fdqVFbMmrXV2QsByt7fPUn/3MySsIQHmAXp01FGZLf1n7pACkmyhQ3L/B2D9n9+8dT7tkkYuR7MaWWIAiv...
AntiVMfalse
PasteBinnull
bdosfalse
BotnetWindows System Guard Runtime
Aes_Key7ed0449feb1ee5da6fc31fb09299337401f1ec0ad1f8b058ce5c02896c516ebb
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Install_Folder%AppData%
Total processes
86
Monitored processes
42
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,8441996594364777422,15746612635049036747,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3028 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8441996594364777422,15746612635049036747,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1812 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
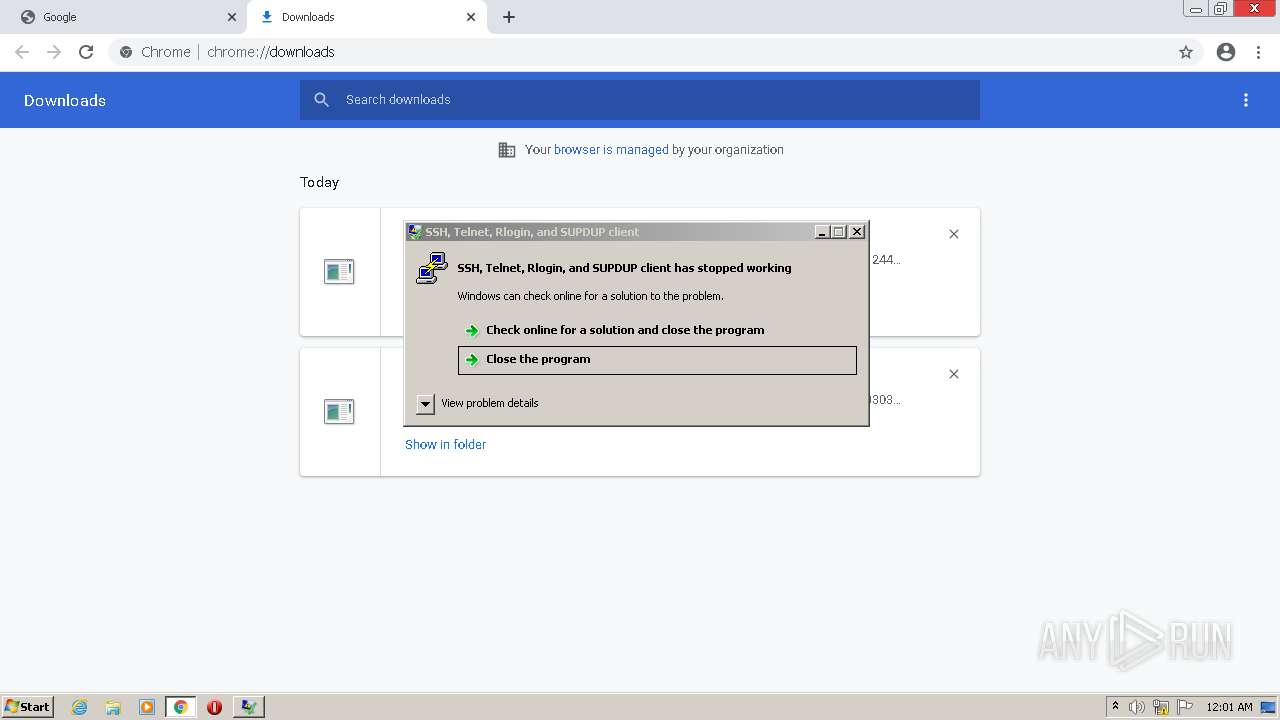
| 968 | "C:\Users\admin\Downloads\final00.exe" | C:\Users\admin\Downloads\final00.exe | Explorer.EXE | ||||||||||||
User: admin Company: Simon Tatham Integrity Level: MEDIUM Description: SSH, Telnet, Rlogin, and SUPDUP client Exit code: 0 Version: Release 0.77 (with embedded help) Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1048,8441996594364777422,15746612635049036747,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3292 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6ec6d988,0x6ec6d998,0x6ec6d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1144 | ping 127.0.0.1 -n 48 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1048,8441996594364777422,15746612635049036747,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=2308 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1980 | ping 127.0.0.1 -n 38 | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,8441996594364777422,15746612635049036747,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgACAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1060 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2072 | schtasks /create /tn \Windows System Guard Runtime /tr "C:\Users\admin\AppData\Roaming\Windows System Guard Runtime\Windows System Guard Runtime.exe" /st 00:00 /du 9999:59 /sc once /ri 60 /f | C:\Windows\system32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 2147500037 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
26 358
Read events
26 095
Write events
263
Delete events
0
Modification events
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3448) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
14
Suspicious files
37
Text files
102
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62F6DBA8-D78.pma | — | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RFcd816.TMP | text | |
MD5:64AD8ED3E666540337BA541C549F72F7 | SHA256:BECBDB08B5B37D203A85F2E974407334053BB1D2270F0B3C9A4DB963896F2206 | |||
| 1032 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RFcd816.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\355323f0-6822-4691-b965-3083cd64ec5d.tmp | text | |
MD5:— | SHA256:— | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 3448 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old~RFcdcf8.TMP | text | |
MD5:D0BA19096D6C8F8DE58312E8D938E893 | SHA256:AADE90A7B0984F3C719D528E4E6FAE3854E28B30363BDD4DF65037E69784A078 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
36
DNS requests
15
Threats
5
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2156 | chrome.exe | 142.250.184.206:443 | — | Google Inc. | US | whitelisted |
2156 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
2156 | chrome.exe | 142.250.185.68:443 | www.google.com | Google Inc. | US | whitelisted |
2156 | chrome.exe | 142.250.185.77:443 | accounts.google.com | Google Inc. | US | suspicious |
2156 | chrome.exe | 142.250.185.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2156 | chrome.exe | 142.250.186.106:443 | content-autofill.googleapis.com | Google Inc. | US | whitelisted |
2156 | chrome.exe | 142.250.186.97:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2156 | chrome.exe | 142.250.185.110:443 | apis.google.com | Google Inc. | US | whitelisted |
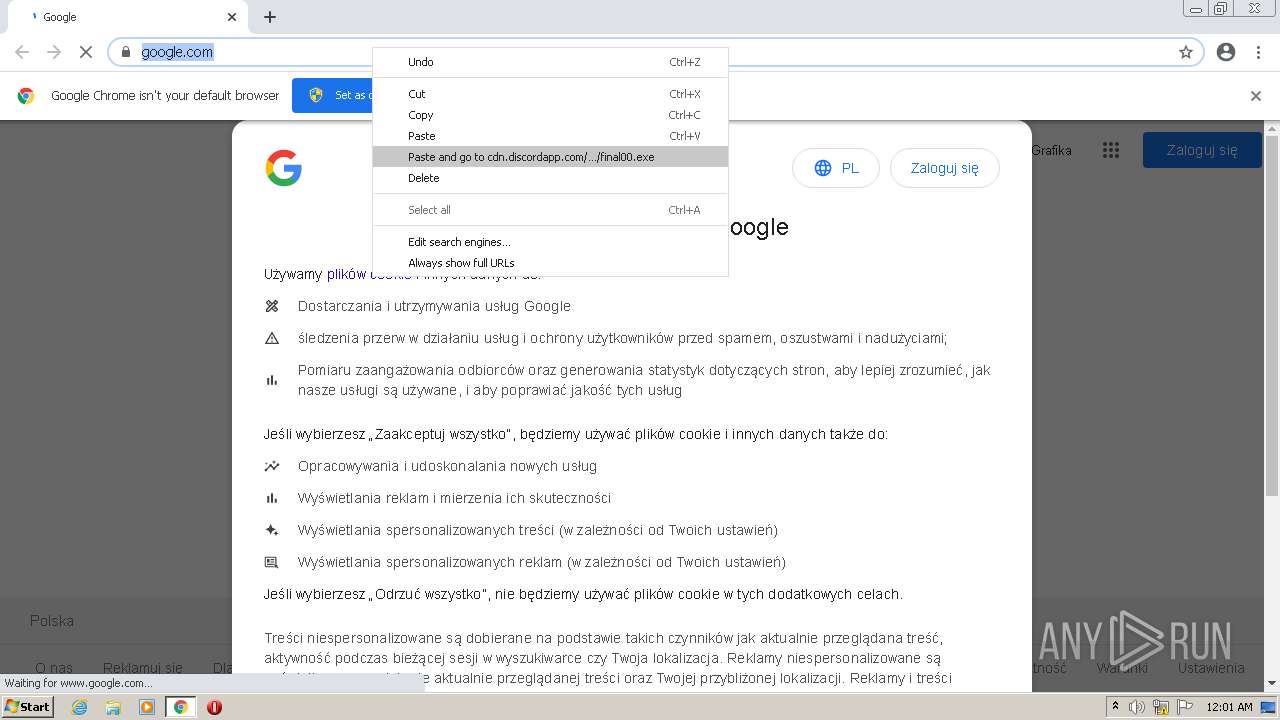
2156 | chrome.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
— | — | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
apis.google.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
cdn.discordapp.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2156 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2156 | chrome.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
3092 | msiexec2.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |