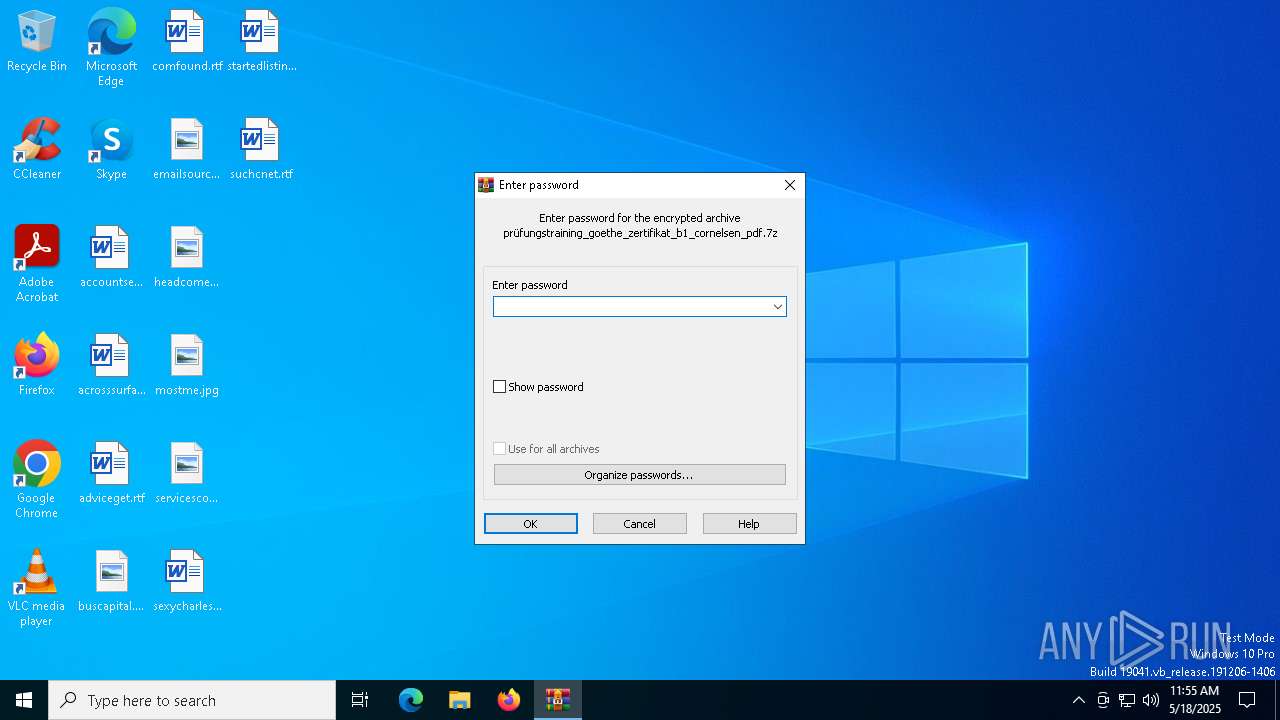
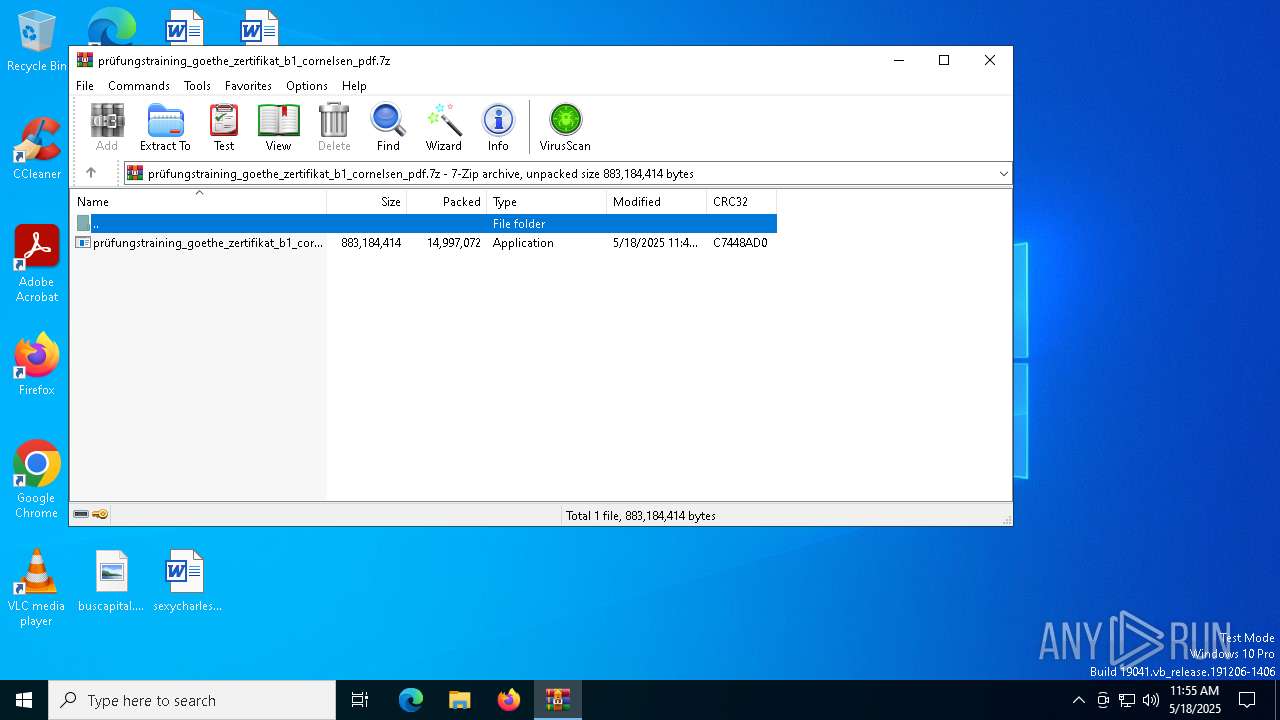
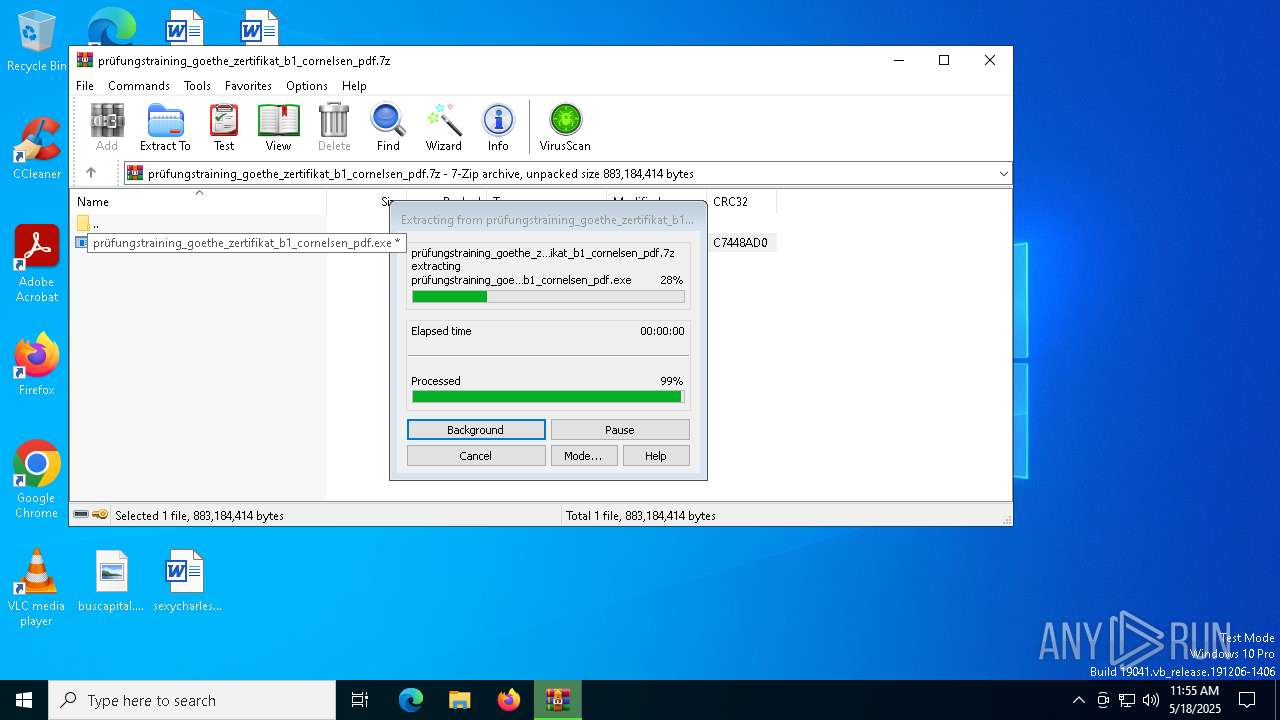
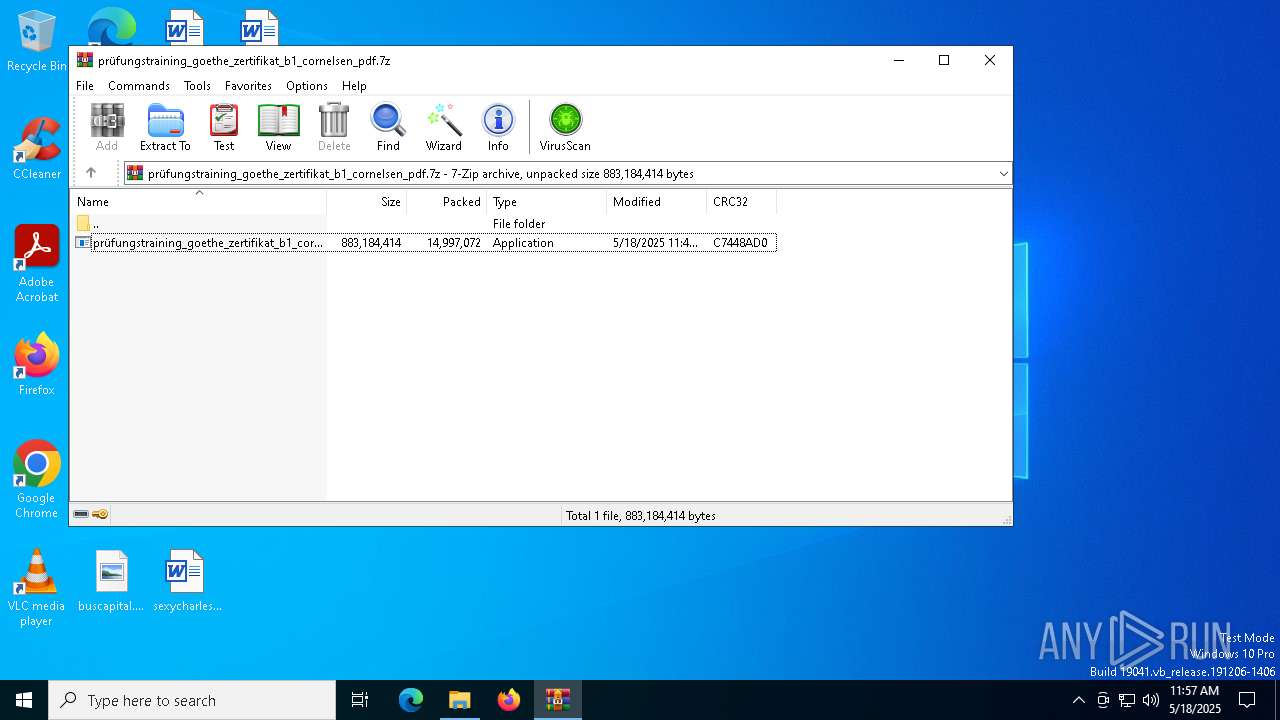
| File name: | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.7z |
| Full analysis: | https://app.any.run/tasks/906d20ab-4907-4ff0-98cc-bacbfb32c228 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 18, 2025, 11:54:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 174BA359E43464E18A57B85F07DA6BD8 |
| SHA1: | BFC9AA7F4342770FFA5DA4BC4397631AAC40C133 |
| SHA256: | 04EDCC26D24FA93CA05EB2C607E6D964A3F6505EBA5818A9637A9B02A755CAF7 |
| SSDEEP: | 98304:GiQiBHIjUZAtIfPzGch9jSaJsZoWJuoCXfC5xH5UQ0Ue6UW4N33bkYq7IS3YhXcx:FAagbvOQgkw5BiFAoOmV8xdMzEzUJv |
MALICIOUS
Actions looks like stealing of personal data
- Police.com (PID: 6620)
LUMMA mutex has been found
- Police.com (PID: 6620)
Steals credentials from Web Browsers
- Police.com (PID: 6620)
AutoIt loader has been detected (YARA)
- Police.com (PID: 680)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7592)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
Starts CMD.EXE for commands execution
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- cmd.exe (PID: 7952)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
- cmd.exe (PID: 4572)
Executing commands from a ".bat" file
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
Get information on the list of running processes
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4572)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4572)
Application launched itself
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4572)
Starts application with an unusual extension
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4572)
The executable file from the user directory is run by the CMD process
- Police.com (PID: 6620)
- Police.com (PID: 680)
Starts the AutoIt3 executable file
- cmd.exe (PID: 7952)
- cmd.exe (PID: 4572)
There is functionality for taking screenshot (YARA)
- Police.com (PID: 6620)
- Police.com (PID: 680)
Searches for installed software
- Police.com (PID: 6620)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Police.com (PID: 6620)
- Police.com (PID: 680)
INFO
Create files in a temporary directory
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- extrac32.exe (PID: 1532)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
Checks supported languages
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- extrac32.exe (PID: 1532)
- Police.com (PID: 6620)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
Reads the computer name
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- extrac32.exe (PID: 1532)
- Police.com (PID: 6620)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
Process checks computer location settings
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7892)
- prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe (PID: 7156)
Creates a new folder
- cmd.exe (PID: 6108)
- cmd.exe (PID: 8012)
Reads mouse settings
- Police.com (PID: 6620)
Application launched itself
- firefox.exe (PID: 2088)
- firefox.exe (PID: 1180)
Reads the software policy settings
- slui.exe (PID: 4424)
- Police.com (PID: 6620)
Manual execution by a user
- firefox.exe (PID: 2088)
Checks proxy server information
- slui.exe (PID: 4424)
Attempting to use instant messaging service
- Police.com (PID: 6620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
168
Monitored processes
39
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5264 -childID 4 -isForBrowser -prefsHandle 5188 -prefMapHandle 5192 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1244 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {4c1ed46f-8c18-4a65-880a-eba1b0603426} 1180 "\\.\pipe\gecko-crash-server-pipe.1180" 219e68e7f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 680 | Police.com T | C:\Users\admin\AppData\Local\Temp\497346\Police.com | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 5 Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1532 | extrac32 /Y /E Dishes.mpg | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2140 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3012 | findstr /V "checking" Realistic | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4424 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 416
Read events
18 404
Write events
12
Delete events
0
Modification events
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.7z | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7592) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
81
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7592 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7592.12553\prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | — | |
MD5:— | SHA256:— | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Statistics.mpg | binary | |
MD5:6C24A4930FC619BBAF4918D2E5ECE25F | SHA256:24EC87CF181235E79AAA88E7B203C443A5E33CF5D25E11BC00348A192F58FA04 | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Rec.mpg | binary | |
MD5:4DDDB17822C57B52816E74E67C694DE6 | SHA256:261D1CB857B6F80D506079FDC877C0EB586D8289AC2E3F097AC5CB7D4B646E5B | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Instructor.mpg | text | |
MD5:B38F98F2BCEC9278700CE565B176A18B | SHA256:BEFF1D83A5FB638B3CB8FB6F87AA96070E82E22447E6C8639E37B33A7EE1B3E1 | |||
| 7952 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Lithuania.mpg.bat | text | |
MD5:CFCF74C912478F52EEF5D109249AE0F2 | SHA256:2FD19D882075829554E6AF5C3454269320FD58F8E70279EB18FB0FF2928DC14A | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Pensions.mpg | binary | |
MD5:6A68DDBBA1CD2B7EBFBC6A2228C9CC6E | SHA256:B173E91D091EC5F721FD9B64FC82CC06C1F53D6D13B449F0E007E83B8ED40FB7 | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Genius.mpg | binary | |
MD5:9883842A781BA15AF904654D31BD4832 | SHA256:9CE0BC2F009A71AA620B2835A36DADD3D09FA5A0683FB36D5B3103331B277E9F | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Lithuania.mpg | text | |
MD5:CFCF74C912478F52EEF5D109249AE0F2 | SHA256:2FD19D882075829554E6AF5C3454269320FD58F8E70279EB18FB0FF2928DC14A | |||
| 1180 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7892 | prüfungstraining_goethe_zertifikat_b1_cornelsen_pdf.exe | C:\Users\admin\AppData\Local\Temp\Dishes.mpg | compressed | |
MD5:2315EA1CFE6A661D27CF6BD1D8FF56A1 | SHA256:8D42625A02563B4B512DE1166888E69A4B4A3C55604EEA959DC9CCDAAB3D7E71 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
62
DNS requests
85
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1276 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1276 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1180 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
1180 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 216.58.206.35:80 | http://o.pki.goog/s/wr3/FIY | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 184.24.77.80:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 184.24.77.80:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
1180 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1512 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
KkohxloJqyIpvzOKGSXHiPhpSSuH.KkohxloJqyIpvzOKGSXHiPhpSSuH |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6620 | Police.com | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
680 | Police.com | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |