| File name: | 7zS.sfx.exe |
| Full analysis: | https://app.any.run/tasks/9ebfad5c-9293-40ec-b486-06e0a1defdfb |
| Verdict: | Malicious activity |
| Threats: | GCleaner is a type of malware loader that has the capability to deliver numerous malicious software programs, which differ based on the location of the targeted victim. This malware is commonly spread through fraudulent websites that advertise free PC optimization tools |
| Analysis date: | January 05, 2024, 21:08:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | BA081B0E14F236799AC98B4704B299D2 |
| SHA1: | B4A15A7359431171610EF629BE5C5E9F18C9C6DB |
| SHA256: | 048C51CDDD7226942B94B0B406E6134FB17766EDA673F1DD713FEE7C845F4514 |
| SSDEEP: | 98304:owUSQ8X4lkznjwiC1RjqNuf64su9XqozngBs9a02Ot3oyte5UHvKgYpkUZU3KMqL:jB8YpyPvawQ5rH |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 1632)
- setup_install.exe (PID: 784)
Starts CMD.EXE for self-deleting
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
GCLEANER has been detected (YARA)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
SUSPICIOUS
The process hide an interactive prompt from the user
- cmd.exe (PID: 1632)
Starts CMD.EXE for commands execution
- setup_install.exe (PID: 784)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1632)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 1632)
Reads the Internet Settings
- 7zS.sfx.exe (PID: 2064)
- 62a4bad8262f6_79a499f590.exe (PID: 1264)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- powershell.exe (PID: 1772)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- control.exe (PID: 3220)
- 62a4badb7af85_623761ba41.exe (PID: 1820)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
- rundll32.exe (PID: 3208)
Starts application with an unusual extension
- 62a4bae1cd5ec_f0e751fd26.exe (PID: 2628)
- JKiHEG (PID: 1924)
Reads the Windows owner or organization settings
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1772)
Checks Windows Trust Settings
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
Reads security settings of Internet Explorer
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
Reads settings of System Certificates
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
Adds/modifies Windows certificates
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2988)
Uses RUNDLL32.EXE to load library
- control.exe (PID: 3220)
INFO
Checks supported languages
- 7zS.sfx.exe (PID: 2064)
- setup_install.exe (PID: 784)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
- 62a4bad8262f6_79a499f590.exe (PID: 1264)
- 62a4bad771e8f_923347.exe (PID: 1112)
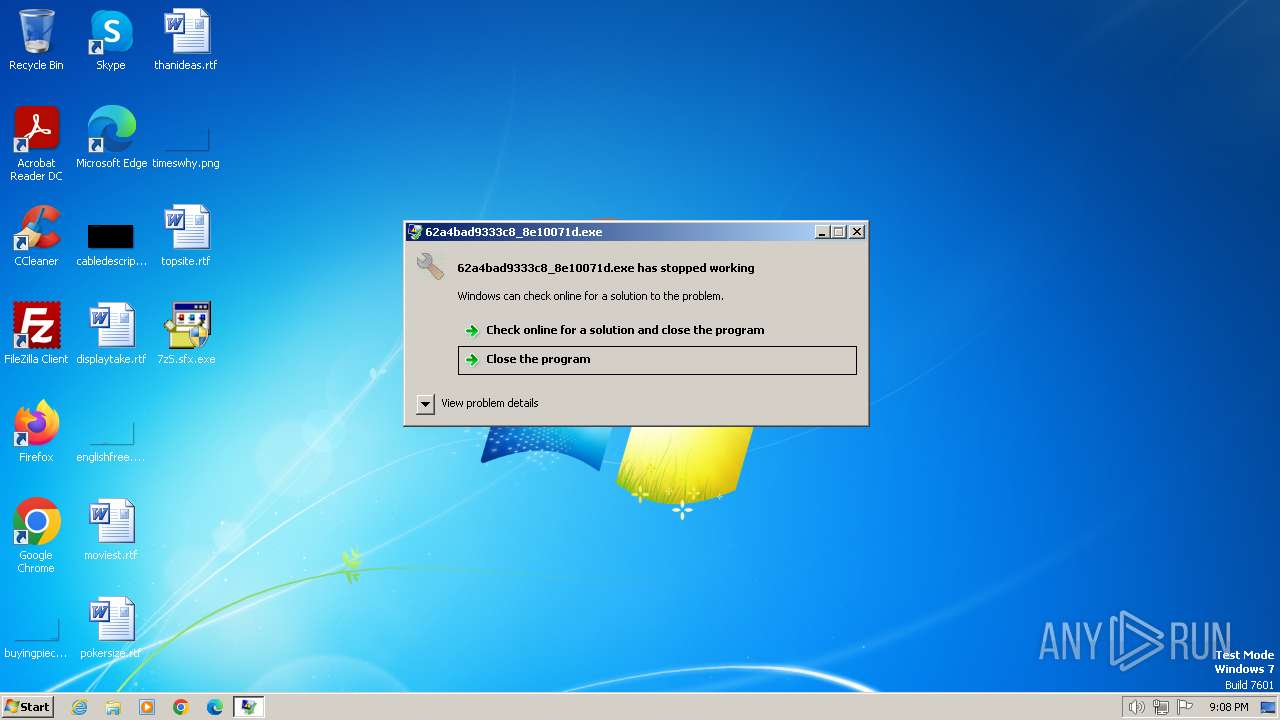
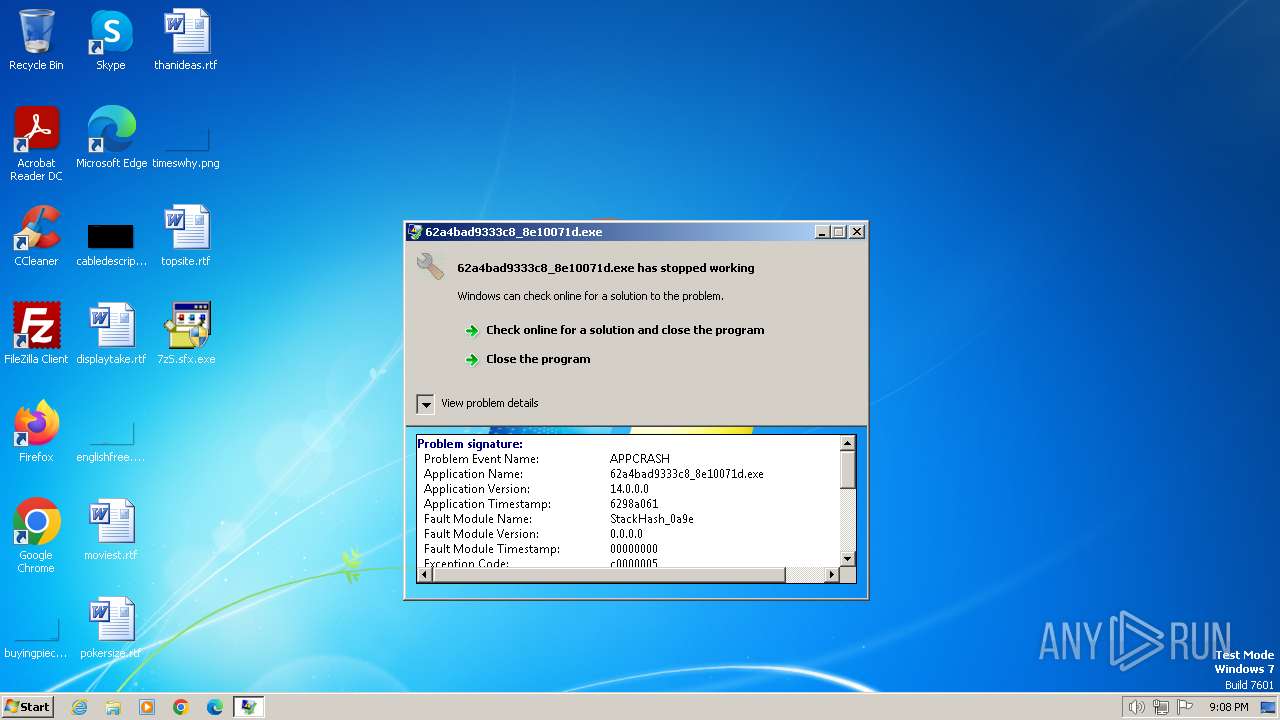
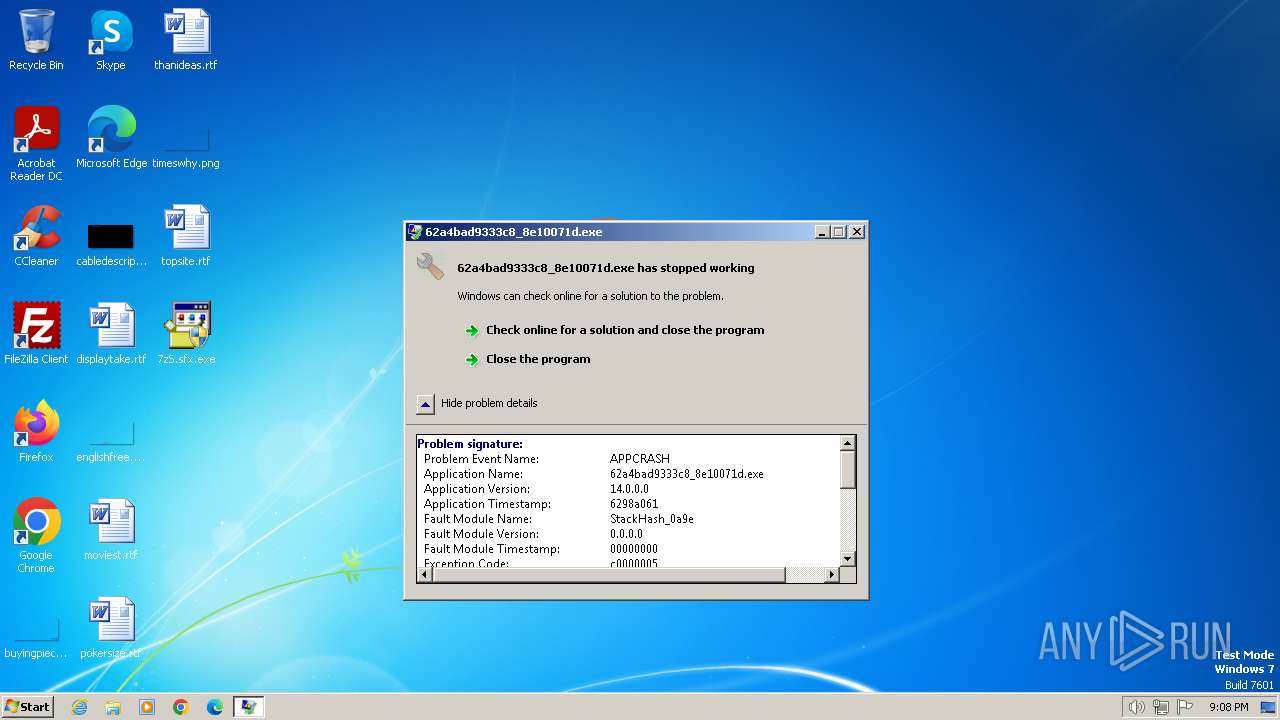
- 62a4bad9333c8_8e10071d.exe (PID: 2172)
- 62a4badb7af85_623761ba41.exe (PID: 1820)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
- 62a4bae1cd5ec_f0e751fd26.exe (PID: 2628)
- 62a4bae2a134b_4fa915d.exe (PID: 796)
- 62a4bae132fe9_b10406e779.exe (PID: 2300)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- 62a4bad8262f6_79a499f590.exe (PID: 1844)
- 62a4badf31e77_62aa4e13bb.exe (PID: 1636)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- JKiHEG (PID: 1924)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- CmvDgs (PID: 996)
- 62a4badf31e77_62aa4e13bb.exe (PID: 3036)
- f6009.exe (PID: 3580)
Drops 7-zip archiver for unpacking
- 7zS.sfx.exe (PID: 2064)
Reads the computer name
- 7zS.sfx.exe (PID: 2064)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
- 62a4bad771e8f_923347.exe (PID: 1112)
- 62a4bad8262f6_79a499f590.exe (PID: 1264)
- 62a4bad8262f6_79a499f590.exe (PID: 1844)
- 62a4badb7af85_623761ba41.exe (PID: 1820)
- 62a4bae2a134b_4fa915d.exe (PID: 796)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- f6009.exe (PID: 3580)
The executable file from the user directory is run by the CMD process
- 62a4bad9333c8_8e10071d.exe (PID: 2172)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
- 62a4badf31e77_62aa4e13bb.exe (PID: 1636)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
- 62a4bad8262f6_79a499f590.exe (PID: 1264)
- 62a4bad771e8f_923347.exe (PID: 1112)
- 62a4badb7af85_623761ba41.exe (PID: 1820)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- 62a4bae132fe9_b10406e779.exe (PID: 2300)
- 62a4bae2a134b_4fa915d.exe (PID: 796)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bae1cd5ec_f0e751fd26.exe (PID: 2628)
Drops the executable file immediately after the start
- 7zS.sfx.exe (PID: 2064)
- 62a4bae132fe9_b10406e779.exe (PID: 2300)
- 62a4bae1cd5ec_f0e751fd26.exe (PID: 2628)
- JKiHEG (PID: 1924)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- rundll32.exe (PID: 3208)
Create files in a temporary directory
- 7zS.sfx.exe (PID: 2064)
- 62a4bae132fe9_b10406e779.exe (PID: 2300)
- 62a4bae1cd5ec_f0e751fd26.exe (PID: 2628)
- 62a4badb7af85_623761ba41.exe (PID: 1820)
- JKiHEG (PID: 1924)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- rundll32.exe (PID: 3208)
Application launched itself
- 62a4bad8262f6_79a499f590.exe (PID: 1264)
- 62a4badf31e77_62aa4e13bb.exe (PID: 1636)
Reads the machine GUID from the registry
- 62a4bad771e8f_923347.exe (PID: 1112)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
Checks proxy server information
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
- 62a4bae02cdda_a09bb3e.exe (PID: 1900)
- 62a4badcb43a3_a6c0e514.exe (PID: 848)
- rundll32.exe (PID: 3208)
Process drops legitimate windows executable
- 62a4bae132fe9_b10406e779.tmp (PID: 2636)
Reads Environment values
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
Starts itself from another location
- JKiHEG (PID: 1924)
Creates files or folders in the user directory
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bae89fe45_b5ccf628.exe (PID: 2624)
Checks for external IP
- 62a4bae4d2a9c_cc09b024e.exe (PID: 2640)
- 62a4bad6b95e3_be16fe.exe (PID: 1584)
Unusual connection from system programs
- rundll32.exe (PID: 3208)
Connects to unusual port
- 62a4bad771e8f_923347.exe (PID: 1112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
GCleaner
(PID) Process(848) 62a4badcb43a3_a6c0e514.exe
C2 (1)203.159.80.49
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:02:21 17:00:00+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 104448 |
| InitializedDataSize: | 28160 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1910c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 19.0.0.0 |
| ProductVersionNumber: | 19.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z Setup SFX |
| FileVersion: | 19 |
| InternalName: | 7zS.sfx |
| LegalCopyright: | Copyright (c) 1999-2018 Igor Pavlov |
| OriginalFileName: | 7zS.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 19 |
Total processes
92
Monitored processes
44
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | C:\Windows\system32\cmd.exe /c 62a4bad771e8f_923347.exe | C:\Windows\System32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 604 | taskkill /im "62a4bae02cdda_a09bb3e.exe" /f | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 784 | "C:\Users\admin\AppData\Local\Temp\7zS0180632E\setup_install.exe" | C:\Users\admin\AppData\Local\Temp\7zS0180632E\setup_install.exe | — | 7zS.sfx.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 796 | 62a4bae2a134b_4fa915d.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bae2a134b_4fa915d.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 848 | 62a4badcb43a3_a6c0e514.exe /mixtwo | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4badcb43a3_a6c0e514.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
GCleaner(PID) Process(848) 62a4badcb43a3_a6c0e514.exe C2 (1)203.159.80.49 | |||||||||||||||
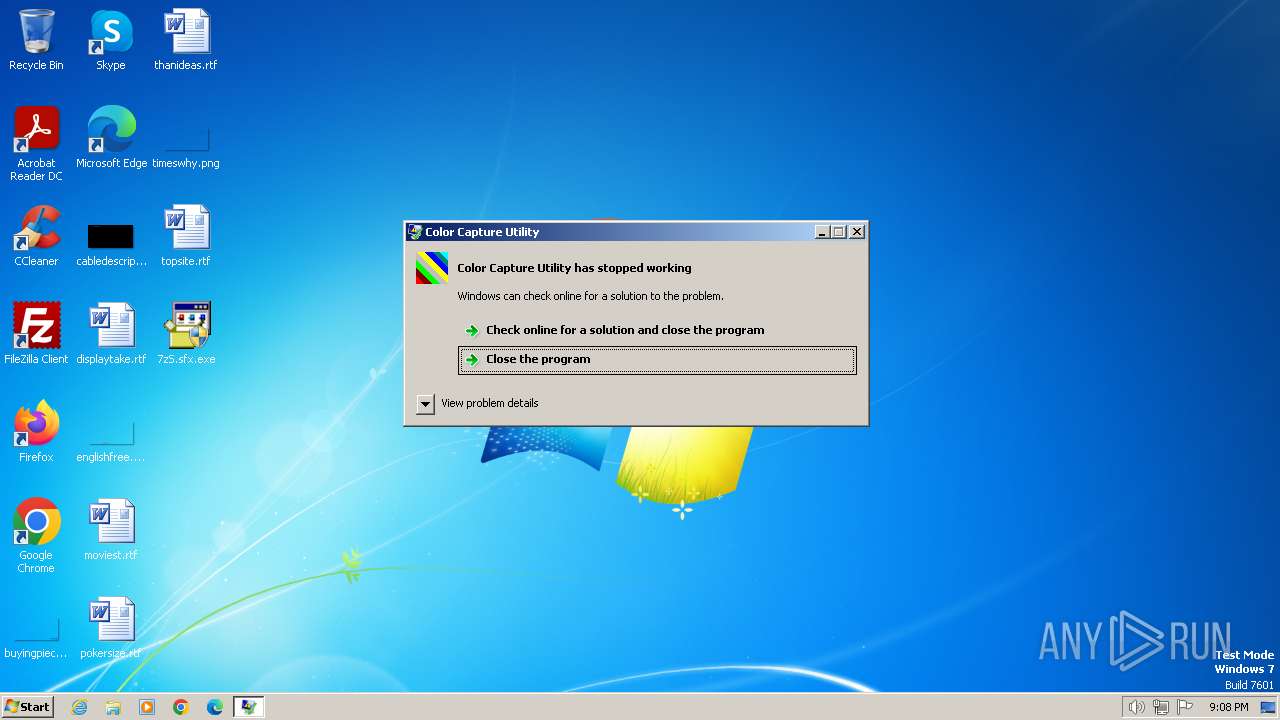
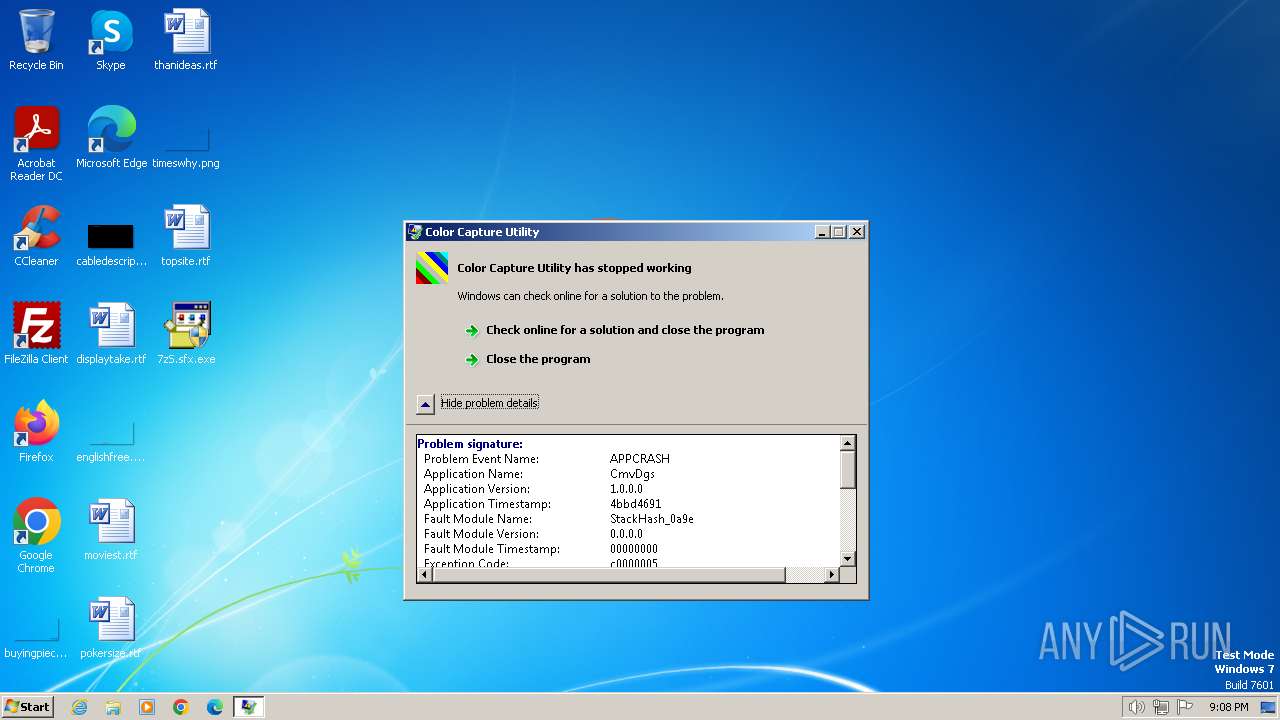
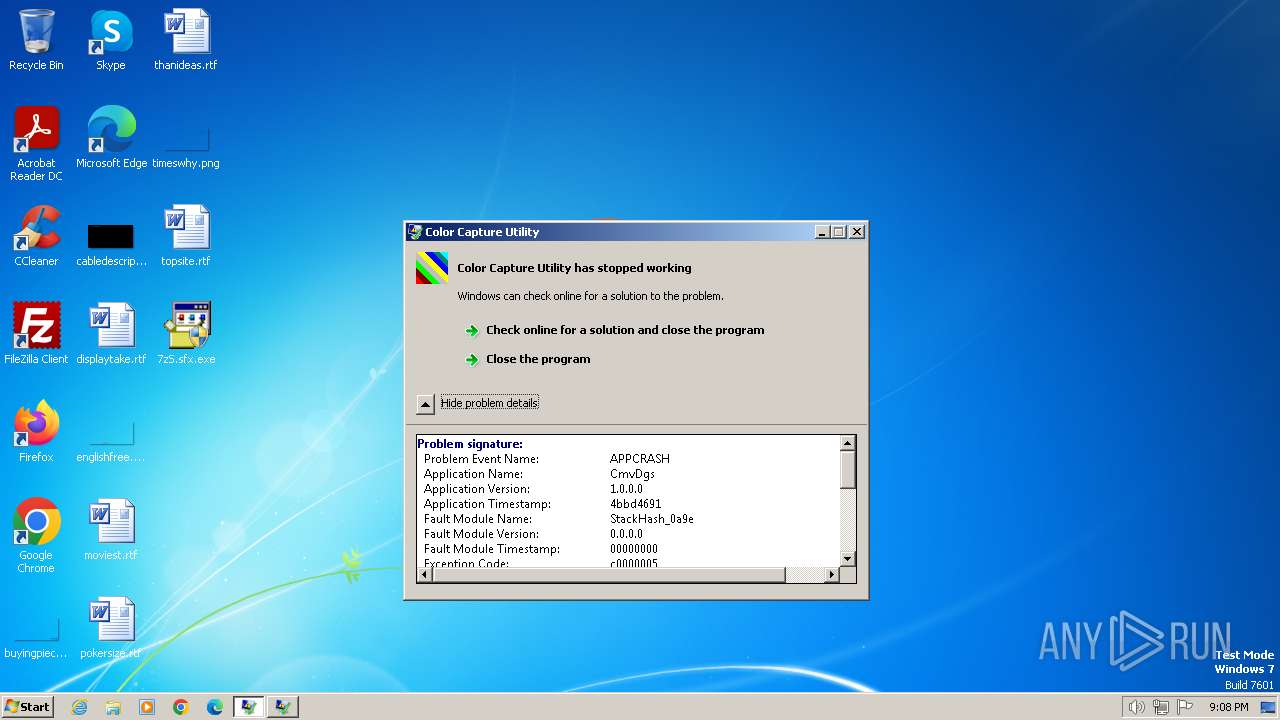
| 996 | C:\Users\admin\AppData\Local\Temp\oYqDcONISRSwFEnLnc\CmvDgs | C:\Users\admin\AppData\Local\Temp\oYqDcONISRSwFEnLnc\CmvDgs | JKiHEG | ||||||||||||
User: admin Company: MASM32 SDK Integrity Level: HIGH Description: Color Capture Utility Exit code: 3221225477 Version: 1.0 Modules
| |||||||||||||||
| 1112 | 62a4bad771e8f_923347.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bad771e8f_923347.exe | cmd.exe | ||||||||||||
User: admin Company: Installer Project Integrity Level: HIGH Description: Installer Project Exit code: 0 Version: 3, 48, 1, 0 Modules
| |||||||||||||||
| 1264 | 62a4bad8262f6_79a499f590.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bad8262f6_79a499f590.exe | — | cmd.exe | |||||||||||
User: admin Company: TODO: <Company name> Integrity Level: HIGH Description: TODO: <File description> Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1576 | C:\Windows\system32\cmd.exe /c 62a4bade488e6_dadba0.exe | C:\Windows\System32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1584 | 62a4bad6b95e3_be16fe.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bad6b95e3_be16fe.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 4294967295 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
20 222
Read events
19 982
Write events
236
Delete events
4
Modification events
| (PID) Process: | (2064) 7zS.sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2064) 7zS.sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2064) 7zS.sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2064) 7zS.sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1264) 62a4bad8262f6_79a499f590.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1264) 62a4bad8262f6_79a499f590.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1264) 62a4bad8262f6_79a499f590.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1264) 62a4bad8262f6_79a499f590.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2624) 62a4bae89fe45_b5ccf628.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2624) 62a4bae89fe45_b5ccf628.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
26
Suspicious files
17
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bad9333c8_8e10071d.exe | executable | |
MD5:10F718551CE15CE0C355B32669B51D2F | SHA256:74328B4664781C7C6D58BF597A0BE968F198FBB199BD0C3425FF575A3F52D688 | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\libstdc++-6.dll | executable | |
MD5:5E279950775BAAE5FEA04D2CC4526BCC | SHA256:97DE47068327BB822B33C7106F9CBB489480901A6749513EF5C31D229DCACA87 | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bae132fe9_b10406e779.exe | executable | |
MD5:E57B3F11829F7F85D0E482043F8A6BD4 | SHA256:7195EDBA387EE58556E027F17BC09F4B43DB205AB89485E90863AF84F2252517 | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\setup_install.exe | executable | |
MD5:57CE0037AFBF6D9C2B519127DF0D6E68 | SHA256:22A5982C64B0F2FBBFADFC2DFE2387FBBBCC7985552AAC146B74AE9E49FBDB5C | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bae4d2a9c_cc09b024e.exe | executable | |
MD5:C8CC1B2DC76454583C3968D96AF6D095 | SHA256:03BC61C86383045EC0D07802596D98EC5B869144FB9F41330332058D340183F3 | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\libgcc_s_dw2-1.dll | executable | |
MD5:9AEC524B616618B0D3D00B27B6F51DA1 | SHA256:59A466F77584438FC3ABC0F43EDC0FC99D41851726827A008841F05CFE12DA7E | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\libwinpthread-1.dll | executable | |
MD5:1E0D62C34FF2E649EBC5C372065732EE | SHA256:509CB1D1443B623A02562AC760BCED540E327C65157FFA938A22F75E38155723 | |||
| 2628 | 62a4bae1cd5ec_f0e751fd26.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bae1cd5ec_f0e751fd26.exe:y | executable | |
MD5:8595EB1A87C49B9B940B46524E1FDF87 | SHA256:77596040B690AF4836406A17C20A69CD5093FD0C470B89DF209A26694141BD4C | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4badb7af85_623761ba41.exe | executable | |
MD5:687970EE527C342266C4D3BA85EB31FE | SHA256:55A3D8C8E10550FCF0CB0A04282661333791D9646B0BC47DB3CEC8A82FD96F6A | |||
| 2064 | 7zS.sfx.exe | C:\Users\admin\AppData\Local\Temp\7zS0180632E\62a4bad8262f6_79a499f590.exe | executable | |
MD5:0CAD21764FE956F3028096FF3FF37549 | SHA256:F65A68DCC63BD141E3A6619ED81B9C0FF3A5492EBD73034F8C794681F1875E3E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
35
DNS requests
17
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2636 | 62a4bae132fe9_b10406e779.tmp | HEAD | 404 | 151.115.10.1:80 | http://pierpont.s3.pl-waw.scw.cloud/cul-pub/poweroff.exe | unknown | — | — | unknown |
2636 | 62a4bae132fe9_b10406e779.tmp | HEAD | 404 | 151.115.10.1:80 | http://nikola.s3.pl-waw.scw.cloud/adv-spec/poweroff.exe | unknown | — | — | unknown |
2636 | 62a4bae132fe9_b10406e779.tmp | GET | 404 | 151.115.10.1:80 | http://pierpont.s3.pl-waw.scw.cloud/cul-pub/poweroff.exe | unknown | xml | 224 b | unknown |
2624 | 62a4bae89fe45_b5ccf628.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0f8b9cb74b2995b5 | unknown | compressed | 4.66 Kb | unknown |
2640 | 62a4bae4d2a9c_cc09b024e.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?789a5713bc875667 | unknown | compressed | 65.2 Kb | unknown |
2636 | 62a4bae132fe9_b10406e779.tmp | GET | 404 | 151.115.10.1:80 | http://nikola.s3.pl-waw.scw.cloud/adv-spec/poweroff.exe | unknown | xml | 222 b | unknown |
2640 | 62a4bae4d2a9c_cc09b024e.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33e02552bdc6c8f0 | unknown | compressed | 4.66 Kb | unknown |
2624 | 62a4bae89fe45_b5ccf628.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEA3teJZTSbNo1B9%2B4%2BHu0es%3D | unknown | binary | 313 b | unknown |
2640 | 62a4bae4d2a9c_cc09b024e.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2624 | 62a4bae89fe45_b5ccf628.exe | GET | 200 | 192.229.221.95:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTwhx4whLWmoMiOrOHBDr230kVlzwQUQd9N8GGTx%2Fy1q818kgKdD3ycCpACEAaqQBqJGZ3PSb1X5c3H%2F0I%3D | unknown | binary | 280 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
796 | 62a4bae2a134b_4fa915d.exe | 46.23.109.174:80 | — | Serverius Holding B.V. | NL | unknown |
2636 | 62a4bae132fe9_b10406e779.tmp | 151.115.10.1:80 | pierpont.s3.pl-waw.scw.cloud | Online S.a.s. | PL | unknown |
2624 | 62a4bae89fe45_b5ccf628.exe | 164.138.208.141:443 | www.telellevo.es | Cyberneticos Hosting SL | ES | unknown |
2640 | 62a4bae4d2a9c_cc09b024e.exe | 104.21.4.208:443 | iplogger.org | CLOUDFLARENET | — | unknown |
2624 | 62a4bae89fe45_b5ccf628.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2640 | 62a4bae4d2a9c_cc09b024e.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2624 | 62a4bae89fe45_b5ccf628.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
v.xyzgamev.com |
| unknown |
udninfofree.shop |
| unknown |
www.icodeps.com |
| unknown |
buyinvestment24.com |
| unknown |
pierpont.s3.pl-waw.scw.cloud |
| unknown |
www.telellevo.es |
| unknown |
best-boutique-clu2.xyz |
| unknown |
best-atel1er.com |
| unknown |
nikola.s3.pl-waw.scw.cloud |
| unknown |
iplogger.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in DNS Lookup) |
2640 | 62a4bae4d2a9c_cc09b024e.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
1584 | 62a4bad6b95e3_be16fe.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
4 ETPRO signatures available at the full report