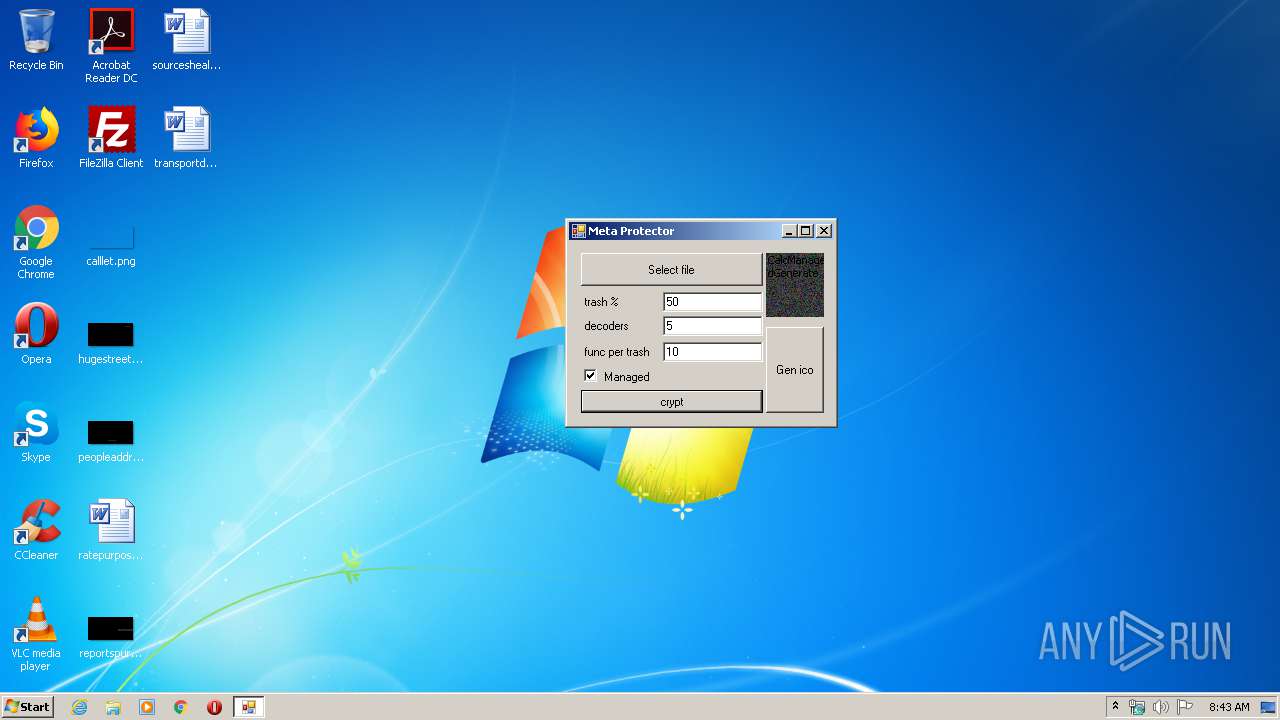
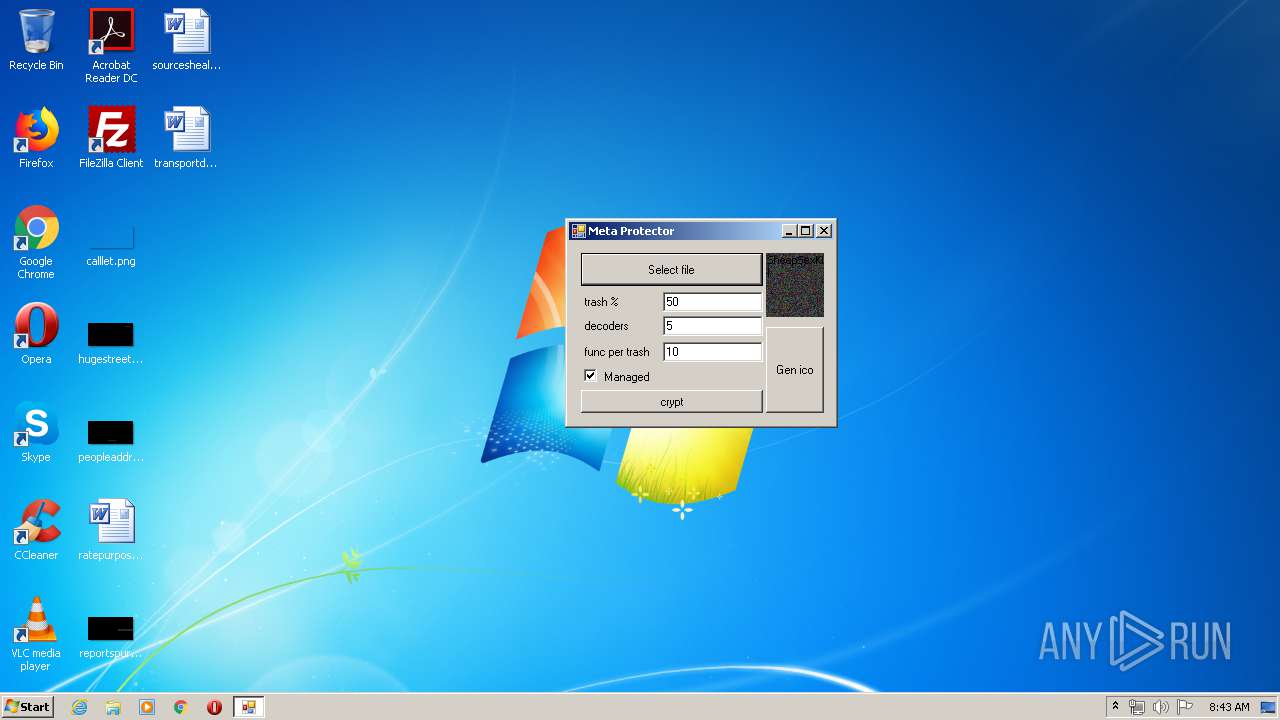
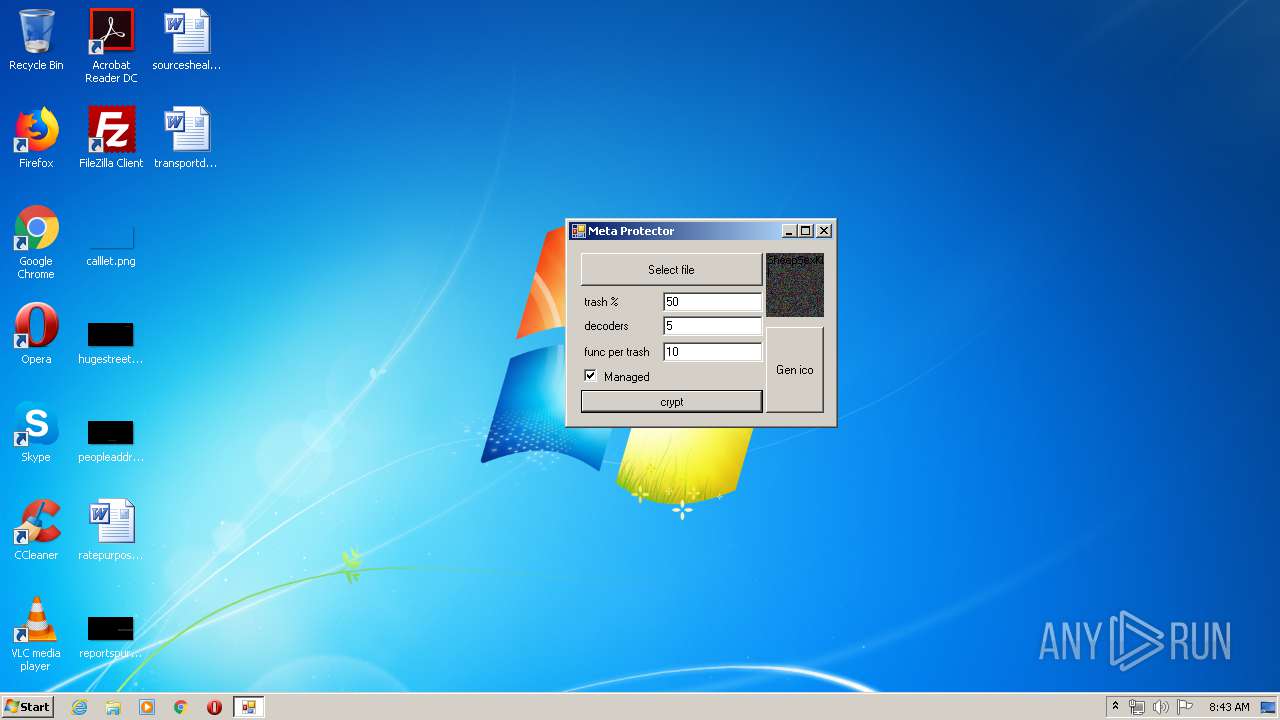
| File name: | by Julia.exe |
| Full analysis: | https://app.any.run/tasks/4002974c-f1af-428a-83f3-123e501d8689 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | March 01, 2020, 08:41:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E0019BE054E913D5768C56FAFC000C16 |
| SHA1: | 9A4CF7945D96AB0319FF95766C3CAAC1423856A7 |
| SHA256: | 04729F72BAB4A2EBEB2C19D00721CD15171EA4A1CBD35117BD20179C91A0F0FE |
| SSDEEP: | 393216:sK/9VOHmyX1GhRMEpq60l+i3Vk7FKw8OZh3fiW:n+HmElt+6WFKw8OZdft |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 3456)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2844)
Application was dropped or rewritten from another process
- MetaCrypt.exe (PID: 2392)
- coded by Julia.exe (PID: 4040)
- joined#.exe (PID: 3436)
- CL_Debug_Log.txt (PID: 3176)
- Helper.exe (PID: 3892)
- Helper.exe (PID: 3984)
- Helper.exe (PID: 1516)
- tor.exe (PID: 2648)
- Helper.exe (PID: 3316)
- Helper.exe (PID: 1780)
- Helper.exe (PID: 3940)
- Helper.exe (PID: 3388)
- Helper.exe (PID: 3996)
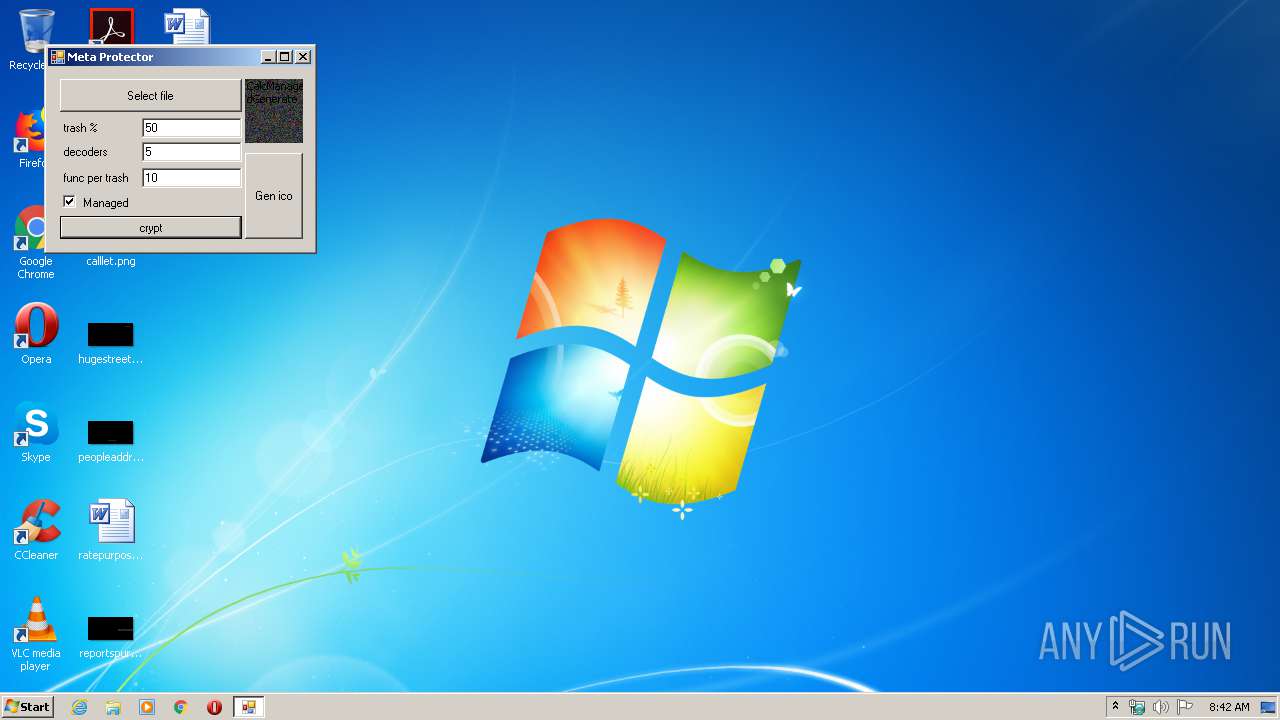
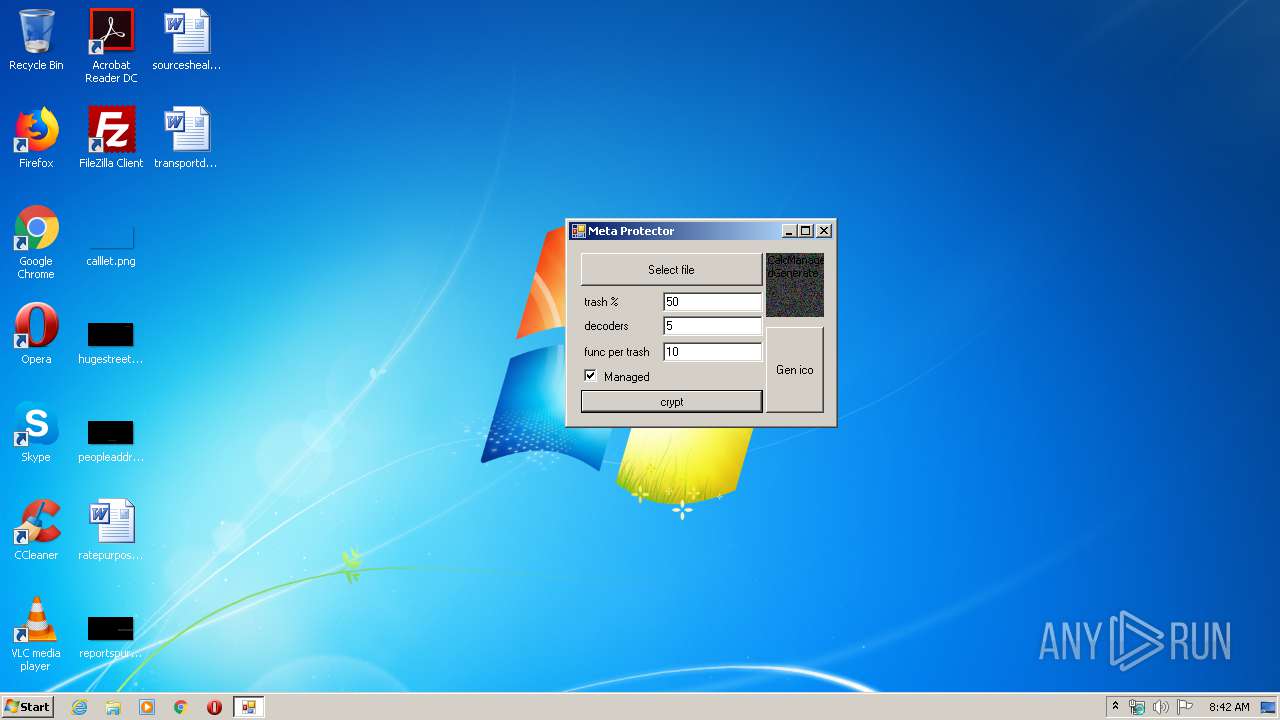
Starts Visual C# compiler
- MetaCrypt.exe (PID: 2392)
Loads dropped or rewritten executable
- tor.exe (PID: 2648)
- MetaCrypt.exe (PID: 2392)
Looks like application has launched a miner
- Helper.exe (PID: 3892)
MINER was detected
- attrib.exe (PID: 1412)
Connects to CnC server
- attrib.exe (PID: 1412)
SUSPICIOUS
Executable content was dropped or overwritten
- CL_Debug_Log.txt (PID: 3176)
- joined#.exe (PID: 3436)
- by Julia.exe (PID: 2168)
- cmd.exe (PID: 3456)
- coded by Julia.exe (PID: 4040)
- Helper.exe (PID: 1516)
- Helper.exe (PID: 3892)
- csc.exe (PID: 3108)
- csc.exe (PID: 2696)
- csc.exe (PID: 3952)
- csc.exe (PID: 2852)
- csc.exe (PID: 4064)
- csc.exe (PID: 2456)
- csc.exe (PID: 952)
Starts CMD.EXE for commands execution
- coded by Julia.exe (PID: 4040)
Starts application with an unusual extension
- coded by Julia.exe (PID: 4040)
Creates files in the user directory
- cmd.exe (PID: 3456)
- Helper.exe (PID: 3892)
- Helper.exe (PID: 1516)
- tor.exe (PID: 2648)
- Helper.exe (PID: 3940)
Executed via Task Scheduler
- Helper.exe (PID: 3892)
- Helper.exe (PID: 3984)
- Helper.exe (PID: 1780)
- Helper.exe (PID: 3996)
- Helper.exe (PID: 3388)
- Helper.exe (PID: 3316)
Application launched itself
- Helper.exe (PID: 3892)
Connects to unusual port
- tor.exe (PID: 2648)
- attrib.exe (PID: 1412)
Uses ATTRIB.EXE to modify file attributes
- Helper.exe (PID: 3892)
INFO
Reads settings of System Certificates
- coded by Julia.exe (PID: 4040)
- Helper.exe (PID: 3892)
Dropped object may contain Bitcoin addresses
- tor.exe (PID: 2648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 4.x (75) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (15.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.6) |
| .exe | | | Win32 Executable (generic) (2.5) |
| .exe | | | Win16/32 Executable Delphi generic (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:06:15 18:44:28+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | 3584 |
| InitializedDataSize: | 14533120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ae1 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 15-Jun-2013 16:44:28 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 15-Jun-2013 16:44:28 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00000C26 | 0x00000E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.14633 |
.rdata | 0x00002000 | 0x000004C0 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.21236 |
.data | 0x00003000 | 0x0000D6F0 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.72555 |
.rsrc | 0x00011000 | 0x00DDB518 | 0x00DDB600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99979 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 7.9998 | 14495282 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
2 | 7.97053 | 34034 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
2000 | 1.32958 | 66 | Latin 1 / Western European | English - United States | IMAGE |
4097 | 5.69939 | 157 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
kernel32.dll |
shlwapi.dll |
user32.dll |
Total processes
83
Monitored processes
34
Malicious processes
8
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES90AA.tmp" "c:\Users\admin\AppData\Local\Temp\CSC4EDCCE1B8B2F4442B4A0F6D11D6420F1.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 952 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\1fo04vss.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | MetaCrypt.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 1256 | -o stratum+tcp://xmr.pool.minergate.com:45700 -u daniilkomelyagin@mail.ru -p x -t 2 | C:\Windows\System32\attrib.exe | — | Helper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1412 | -o stratum+tcp://xmr.pool.minergate.com:45700 -u daniilkomelyagin@mail.ru -p x -t 2 | C:\Windows\System32\attrib.exe | Helper.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES96A6.tmp" "c:\Users\admin\AppData\Local\Temp\CSC3400FEB1E1D74921BE69D48F6BD986C.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 1516 | 7z e -p"DxSqsNKKOxqPrM4Y3xeK" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Tor.tmp" -o"C:\Users\admin\AppData\Roaming\Microsoft\Windows\Tor\" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | Helper.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1780 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1828 | -o stratum+tcp://xmr.pool.minergate.com:45700 -u daniilkomelyagin@mail.ru -p x -t 2 | C:\Windows\System32\attrib.exe | — | Helper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\AppData\Local\Temp\by Julia.exe" | C:\Users\admin\AppData\Local\Temp\by Julia.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2388 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES9212.tmp" "c:\Users\admin\AppData\Local\Temp\CSCC75A84BCA29E45F79FD1E22153C7D2A.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
Total events
1 863
Read events
1 704
Write events
154
Delete events
5
Modification events
| (PID) Process: | (2168) by Julia.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2168) by Julia.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3436) joined#.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3436) joined#.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4040) coded by Julia.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3892) Helper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3892) Helper.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2392) MetaCrypt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C004D00650074006100430072007900700074002E00650078006500000043003A005C00550073006500720073000000 | |||
| (PID) Process: | (2392) MetaCrypt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (2392) MetaCrypt.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
26
Suspicious files
3
Text files
145
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4040 | coded by Julia.exe | C:\Users\admin\AppData\Local\Temp\aut8267.tmp | — | |
MD5:— | SHA256:— | |||
| 4040 | coded by Julia.exe | C:\Users\admin\AppData\Local\Temp\asacpiex.dll | — | |
MD5:— | SHA256:— | |||
| 4040 | coded by Julia.exe | C:\Users\admin\AppData\Local\Temp\CR_Debug_Log.txt | — | |
MD5:— | SHA256:— | |||
| 4040 | coded by Julia.exe | C:\Users\admin\AppData\Local\Temp\aut898C.tmp | — | |
MD5:— | SHA256:— | |||
| 3176 | CL_Debug_Log.txt | C:\Users\admin\AppData\Local\Temp\start.bat | text | |
MD5:— | SHA256:— | |||
| 3436 | joined#.exe | C:\Users\admin\AppData\Local\Temp\icon.ico | mpg | |
MD5:— | SHA256:— | |||
| 3436 | joined#.exe | C:\Users\admin\AppData\Local\Temp\MetaCrypt.exe | executable | |
MD5:— | SHA256:— | |||
| 2168 | by Julia.exe | C:\Users\admin\AppData\Local\Temp\joined#.exe | executable | |
MD5:— | SHA256:— | |||
| 3176 | CL_Debug_Log.txt | C:\Users\admin\AppData\Local\Temp\start2.bat | text | |
MD5:— | SHA256:— | |||
| 3176 | CL_Debug_Log.txt | C:\Users\admin\AppData\Local\Temp\SystemCheck.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
21
DNS requests
6
Threats
30
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3892 | Helper.exe | GET | 301 | 88.99.66.31:80 | http://ezstat.ru/1UQw37 | DE | html | 178 b | shared |
4040 | coded by Julia.exe | GET | 301 | 88.99.66.31:80 | http://ezstat.ru/1Umw37 | DE | html | 178 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4040 | coded by Julia.exe | 88.99.66.31:80 | ezstat.ru | Hetzner Online GmbH | DE | malicious |
4040 | coded by Julia.exe | 88.99.66.31:443 | ezstat.ru | Hetzner Online GmbH | DE | malicious |
2648 | tor.exe | 94.142.242.84:443 | — | Netwerkvereniging Coloclue | NL | suspicious |
2648 | tor.exe | 172.98.193.43:443 | — | Centrilogic, Inc. | US | suspicious |
2648 | tor.exe | 163.172.157.213:443 | — | Online S.a.s. | FR | suspicious |
2648 | tor.exe | 51.15.235.73:9100 | — | Online S.a.s. | FR | suspicious |
2648 | tor.exe | 85.25.210.168:8443 | — | Host Europe GmbH | DE | malicious |
3892 | Helper.exe | 88.99.66.31:80 | ezstat.ru | Hetzner Online GmbH | DE | malicious |
2648 | tor.exe | 51.15.203.26:9001 | — | Online S.a.s. | FR | suspicious |
3892 | Helper.exe | 88.99.66.31:443 | ezstat.ru | Hetzner Online GmbH | DE | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ezstat.ru |
| shared |
iplogger.org |
| shared |
xmr.pool.minergate.com |
| suspicious |
fee.ssl.xexi.xyz |
| suspicious |
fee.v2.xexi.xyz |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2648 | tor.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 18 |
2648 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 18 |
2648 | tor.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TOR SSL connection |
2648 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 198 |
2648 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 665 |
2648 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 526 |
2648 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 528 |
2648 | tor.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TOR SSL connection |
2648 | tor.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
2648 | tor.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
5 ETPRO signatures available at the full report