| File name: | Preview.exe |
| Full analysis: | https://app.any.run/tasks/fb9ec9ac-fe41-4e4a-ac55-3af04938258e |
| Verdict: | Malicious activity |
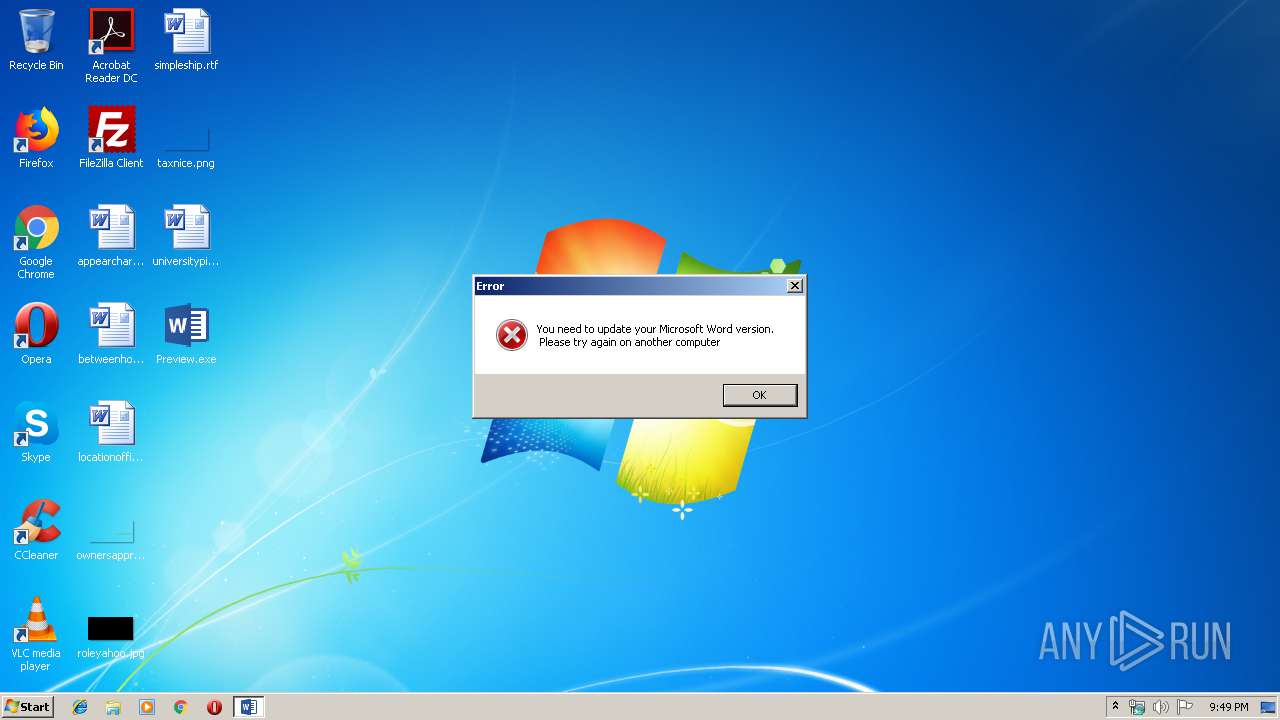
| Threats: | TrickBot is an advanced banking trojan that attackers can use to steal payment credentials from the victims. It can redirect the victim to a fake banking cabinet and retrieve credentials typed in on the webpage. |
| Analysis date: | October 23, 2019, 20:48:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 334E0D9F02077E9383778B80E4264491 |
| SHA1: | B718E3103BE3076EA0C53CA703C073FA08EB1E6C |
| SHA256: | 03944D9CD1AD0759158E31FE8FFA3A575DDE491AD7472ACDA15D3D18F8B59954 |
| SSDEEP: | 12288:Ar9srWN1kQqD/BtSYxaontLIQ8IdDuipVHbsq/IE5xLC9U49ZFWC7PhKvU:ArvN4LByotLIXaVwEPWCjC7PovU |
MALICIOUS
Loads the Task Scheduler COM API
- ввсасоаасасаштултт.exe (PID: 2588)
- ввсасоаасасаштултт.exe (PID: 2840)
Known privilege escalation attack
- DllHost.exe (PID: 600)
TRICKBOT was detected
- ввсасоаасасаштултт.exe (PID: 2588)
Connects to CnC server
- ввсасоаасасаштултт.exe (PID: 2588)
SUSPICIOUS
Executable content was dropped or overwritten
- Preview.exe (PID: 2740)
- ввсасоаасасаштултт.exe (PID: 2840)
Creates files in the program directory
- Preview.exe (PID: 2740)
Starts itself from another location
- Preview.exe (PID: 2740)
Executed via COM
- DllHost.exe (PID: 600)
Creates files in the user directory
- ввсасоаасасаштултт.exe (PID: 2840)
- ввсасоаасасаштултт.exe (PID: 2588)
Executed via Task Scheduler
- ввсасоаасасаштултт.exe (PID: 2588)
Removes files from Windows directory
- ввсасоаасасаштултт.exe (PID: 2588)
Creates files in the Windows directory
- ввсасоаасасаштултт.exe (PID: 2588)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:10:23 08:38:41+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 352256 |
| InitializedDataSize: | 466944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3ec93 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 23-Oct-2019 06:38:41 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 23-Oct-2019 06:38:41 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00055F8A | 0x00056000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.59335 |
.rdata | 0x00057000 | 0x00053173 | 0x00054000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.17607 |
.data | 0x000AB000 | 0x00006CDC | 0x00004000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.55886 |
.rsrc | 0x000B2000 | 0x000196B6 | 0x0001A000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.00155 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.65542 | 86 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 2.974 | 112 | Latin 1 / Western European | English - United States | RT_ACCELERATOR |
3 | 2 | 8 | Latin 1 / Western European | English - United States | RT_ACCELERATOR |
4 | 3.10887 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 2.12655 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 3.41173 | 38056 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 2.84409 | 178 | Latin 1 / Western European | English - United States | RT_STRING |
8 | 3.91484 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
9 | 4.08609 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
10 | 4.21943 | 1720 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
ADVAPI32.dll |
CRYPT32.dll |
GDI32.dll |
KERNEL32.dll |
OLEACC.dll (delay-loaded) |
OLEAUT32.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
WINSPOOL.DRV |
Exports
Title | Ordinal | Address |
|---|---|---|
Func | 1 | 0x000020B0 |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | C:\Windows\system32\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2588 | C:\Users\admin\AppData\Roaming\HttpService\ввсасоаасасаштултт.exe | C:\Users\admin\AppData\Roaming\HttpService\ввсасоаасасаштултт.exe | taskeng.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Modules
| |||||||||||||||
| 2740 | "C:\Users\admin\Desktop\Preview.exe" | C:\Users\admin\Desktop\Preview.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2840 | "C:\ProgramData\ввсасоаасасаштултт.exe" | C:\ProgramData\ввсасоаасасаштултт.exe | DllHost.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2928 | "C:\ProgramData\ввсасоаасасаштултт.exe" | C:\ProgramData\ввсасоаасасаштултт.exe | — | Preview.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
116
Read events
98
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2740) Preview.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2740) Preview.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (600) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (600) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2588) ввсасоаасасаштултт.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
2
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\TEMP\Cab2357.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\TEMP\Tar2368.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\TEMP\Cab2379.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\TEMP\Tar237A.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\TEMP\Cab385A.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\TEMP\Tar385B.tmp | — | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94308059B57B3142E455B38A6EB92015 | binary | |
MD5:— | SHA256:— | |||
| 2740 | Preview.exe | C:\ProgramData\ввсасоаасасаштултт.exe | executable | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Users\admin\AppData\Roaming\HttpService\settings.ini | text | |
MD5:— | SHA256:— | |||
| 2588 | ввсасоаасасаштултт.exe | C:\Windows\system32\config\systemprofile\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94308059B57B3142E455B38A6EB92015 | compressed | |
MD5:93871E1433144C58CAB0DEDDD1D46925 | SHA256:3193F3035A4F457D66BAB3048880AAC2EB8557027F6373E606D4621609AF1068 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
1
Threats
17
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2588 | ввсасоаасасаштултт.exe | GET | 200 | 92.122.213.201:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 57.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2588 | ввсасоаасасаштултт.exe | 185.68.93.43:443 | — | Relink LTD | RU | malicious |
2588 | ввсасоаасасаштултт.exe | 92.122.213.201:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex/Trickbot CnC) |
2588 | ввсасоаасасаштултт.exe | A Network Trojan was detected | MALWARE [PTsecurity] Blacklist SSL certificate detected (Trickbot) |
8 ETPRO signatures available at the full report