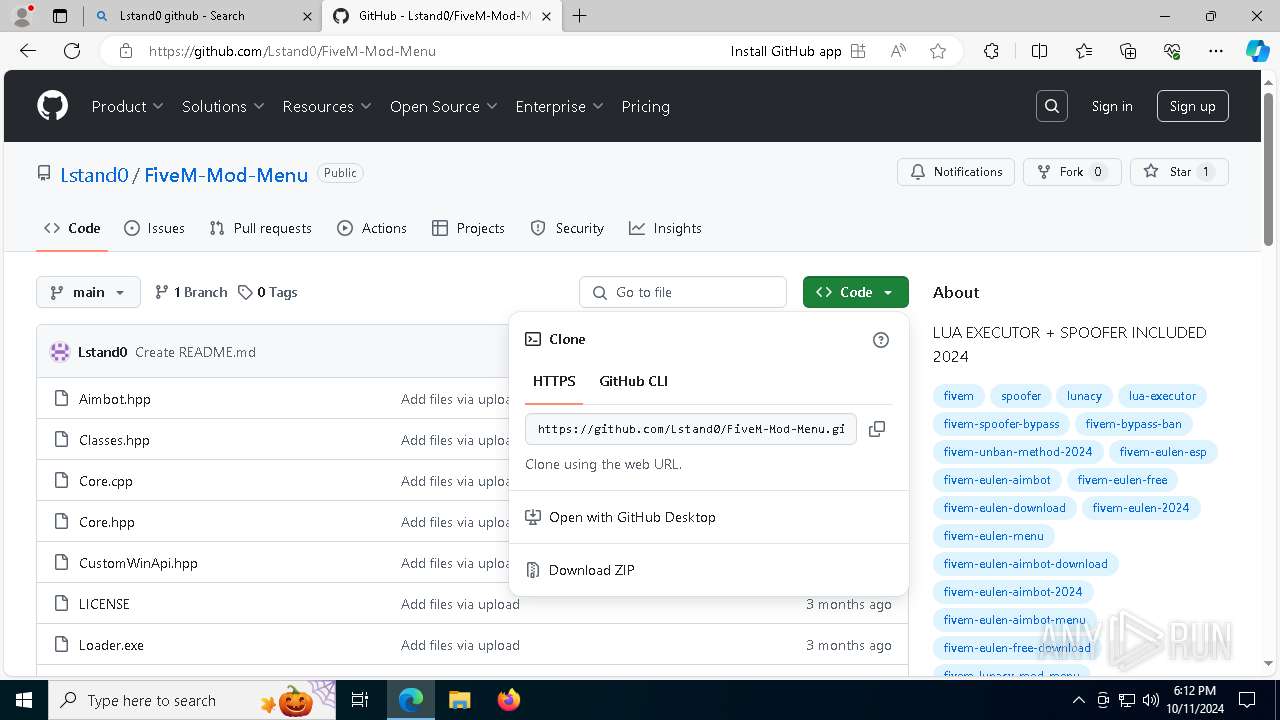
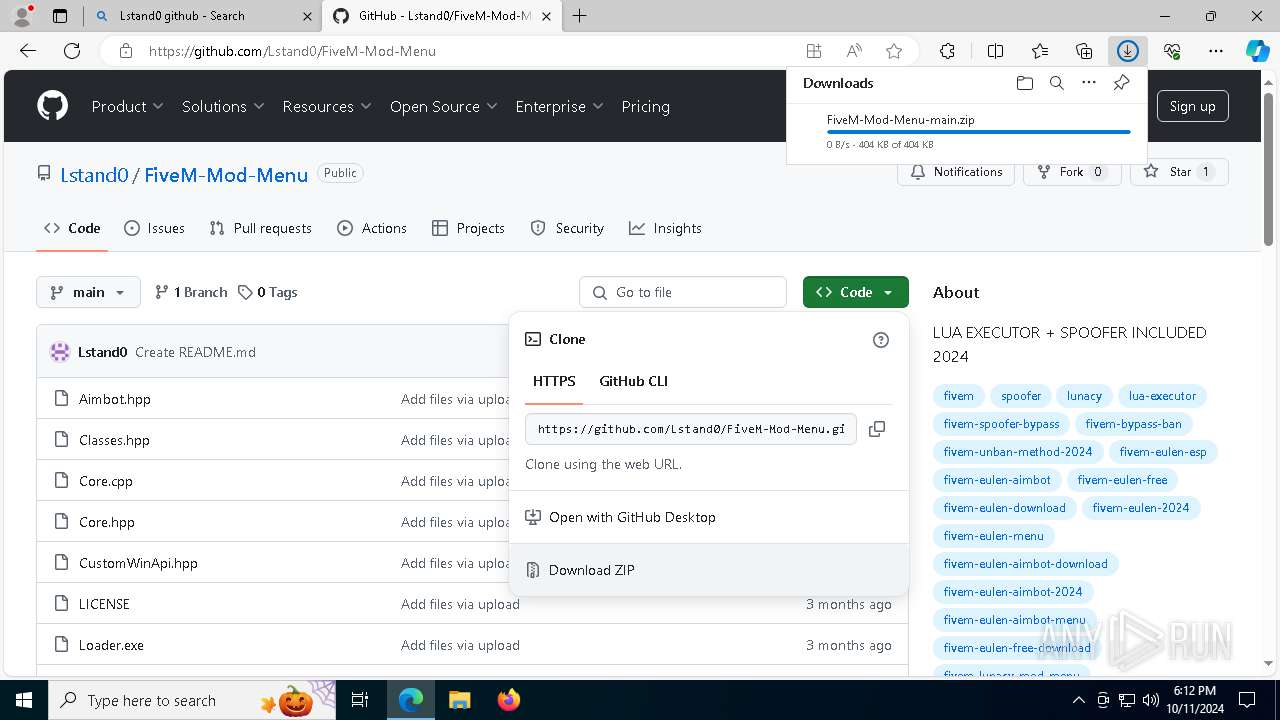
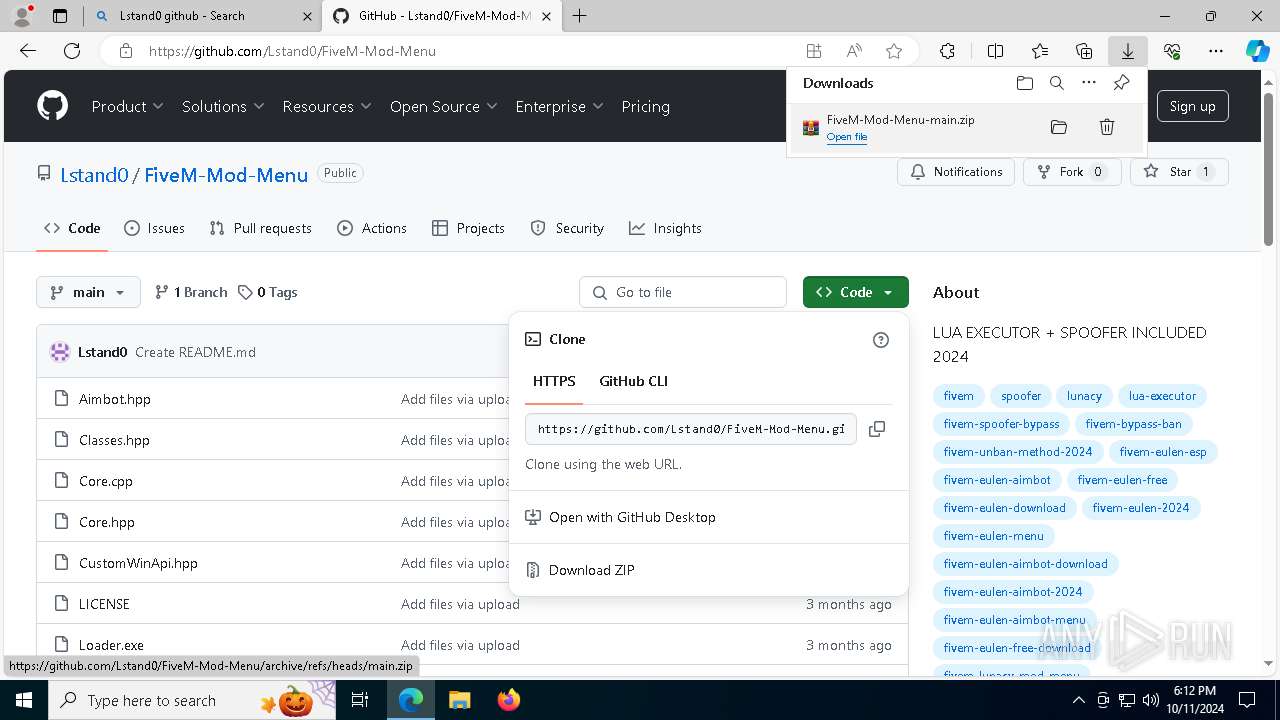
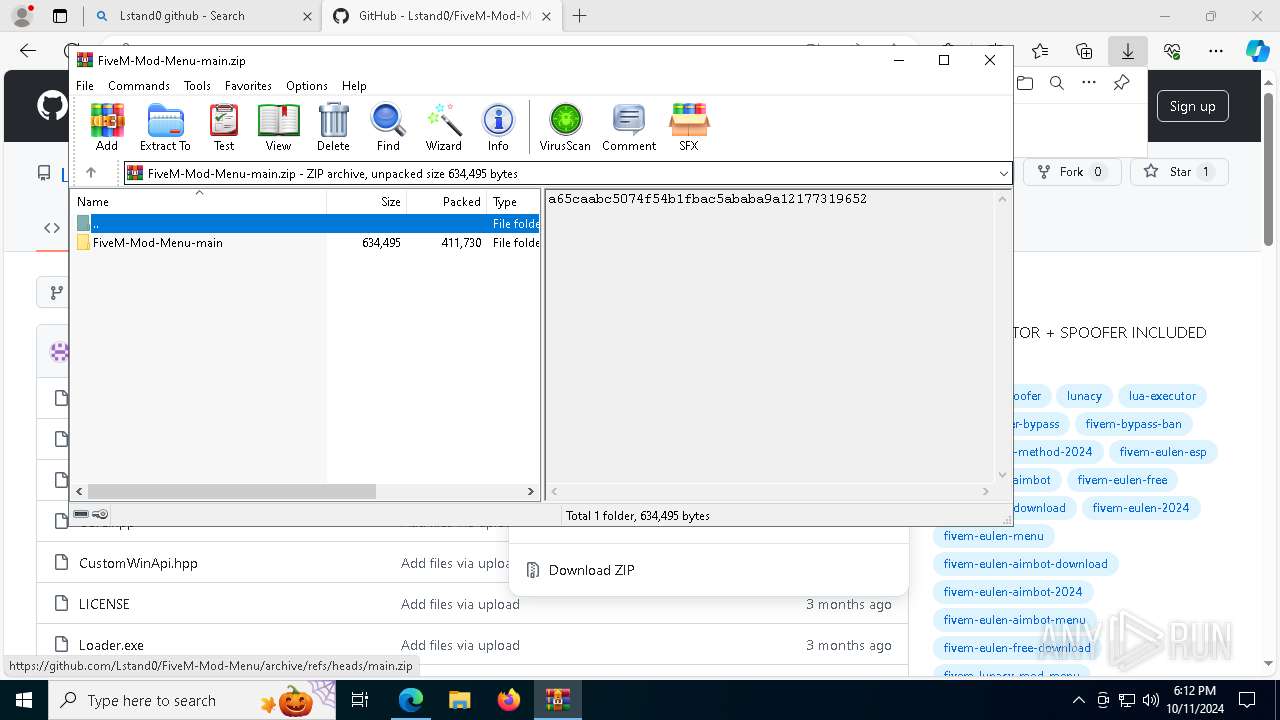
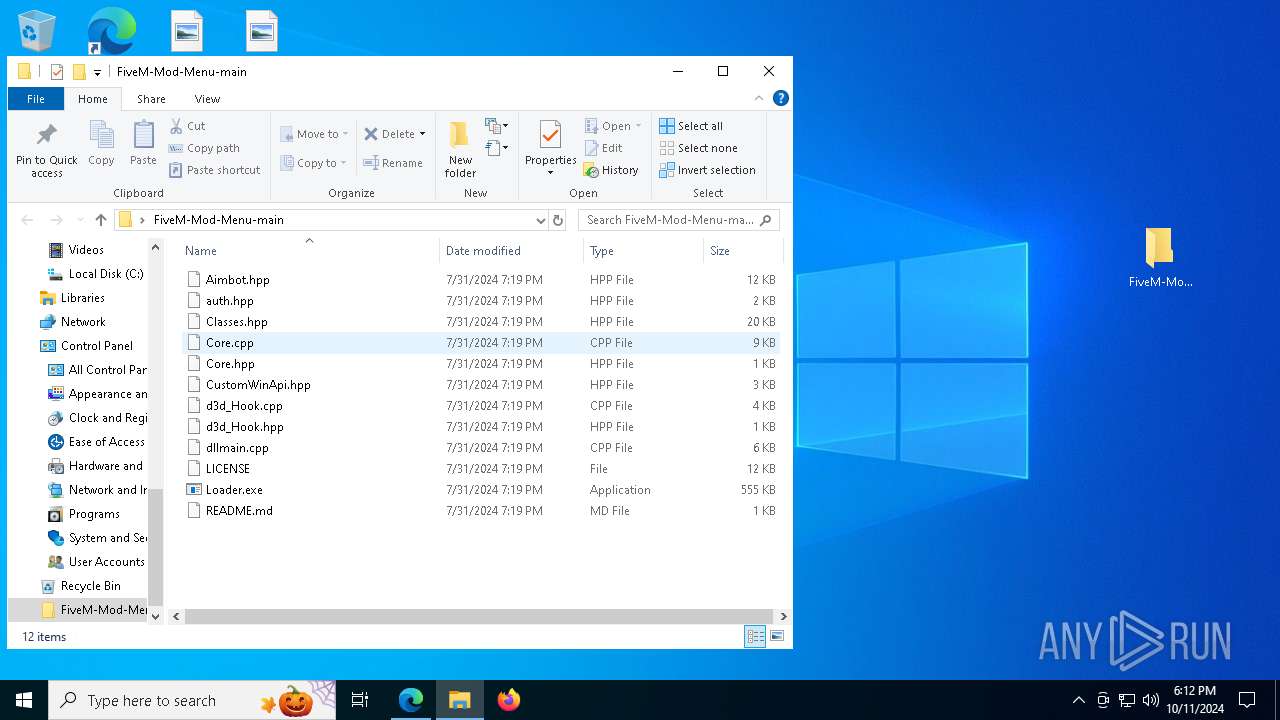
| download: | /Lstand0/FiveM-Mod-Menu |
| Full analysis: | https://app.any.run/tasks/a96941f6-c1cc-4e6b-921d-88e09524520c |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 11, 2024, 18:11:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines (1616) |
| MD5: | 5807281F04BCD20F31826064E781A796 |
| SHA1: | BC0E48F507450B2EDDFF2142733965DAB9FD58E8 |
| SHA256: | 036C3C510B1AD912A12B18A873C4F411D3CA9051DCF4F16A87AA688CD532098A |
| SSDEEP: | 6144:xPo/ipOL/saqkPV9FxLtcsDSsmwo9XvZJT3CqbMrhryf65NRPaCieMjAkvCJv1VS:xo/ipOL/saqkPV9FxLtcsDSsmwo9XvZX |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2172)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
SUSPICIOUS
Executable content was dropped or overwritten
- Loader.exe (PID: 1588)
- Loader.exe (PID: 7368)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7180)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6756)
Manual execution by a user
- msedge.exe (PID: 5508)
- Loader.exe (PID: 1588)
- Loader.exe (PID: 7368)
Application launched itself
- msedge.exe (PID: 5508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
HTML
| Title: | GitHub - Lstand0/FiveM-Mod-Menu: LUA EXECUTOR + SPOOFER INCLUDED 2024 |
|---|---|
| RoutePattern: | /:user_id/:repository |
| RouteController: | files |
| RouteAction: | disambiguate |
| CurrentCatalogServiceHash: | f3abb0cc802f3d7b95fc8762b94bdcb13bf39634c40c357301c4aa1d67a256fb |
| RequestId: | F73C:3FAF5A:C93C25:CCCE65:67096A44 |
| HtmlSafeNonce: | fcd8c3968c4fb0f5d9d7a309a1c5c5ebe521fcfff07535654467ce6b10b69598 |
| VisitorPayload: | eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJGNzNDOjNGQUY1QTpDOTNDMjU6Q0NDRTY1OjY3MDk2QTQ0IiwidmlzaXRvcl9pZCI6IjIxOTYwNjk0NTIwMzA1NTE3MiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9 |
| VisitorHmac: | b89f3ef4ae45cd310abef4ec2dabae90e0b36136a2b35d73d37685b9cedf8b97 |
| HovercardSubjectTag: | repository:836403385 |
| GithubKeyboardShortcuts: | repository,copilot |
| GoogleSiteVerification: | Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I |
| OctolyticsUrl: | https://collector.github.com/github/collect |
| AnalyticsLocation: | /<user-name>/<repo-name> |
| UserLogin: | - |
| Viewport: | width=device-width |
| Description: | LUA EXECUTOR + SPOOFER INCLUDED 2024. Contribute to Lstand0/FiveM-Mod-Menu development by creating an account on GitHub. |
| AppleItunesApp: | app-id=1477376905, app-argument=https://github.com/Lstand0/FiveM-Mod-Menu |
| TwitterImage: | https://opengraph.githubassets.com/d2e02119c3fff5eca80808d47cdc27c449e33136b599875944aae18f06a50452/Lstand0/FiveM-Mod-Menu |
| TwitterSite: | @github |
| TwitterCard: | summary_large_image |
| TwitterTitle: | GitHub - Lstand0/FiveM-Mod-Menu: LUA EXECUTOR + SPOOFER INCLUDED 2024 |
| TwitterDescription: | LUA EXECUTOR + SPOOFER INCLUDED 2024. Contribute to Lstand0/FiveM-Mod-Menu development by creating an account on GitHub. |
| Hostname: | github.com |
| ExpectedHostname: | github.com |
| HTTPEquivXPjaxVersion: | 2f493710ed608f49d92be962c899d07f5b52d37955a1e5ca6143379b85a6e506 |
| HTTPEquivXPjaxCspVersion: | ace39c3b6632770952207593607e6e0be0db363435a8b877b1f96abe6430f345 |
| HTTPEquivXPjaxCssVersion: | e9cc7e98b095db1b8c9b142a4deff85379758b12b581319e274e0c6025b9af7e |
| HTTPEquivXPjaxJsVersion: | b52778c5830024a35c966aaf150f98df6a35054007f7d0b70182b53b47c10eae |
| TurboCacheControl: | no-preview |
| GoImport: | github.com/Lstand0/FiveM-Mod-Menu git https://github.com/Lstand0/FiveM-Mod-Menu.git |
| OctolyticsDimensionUser_id: | 177158843 |
| OctolyticsDimensionUser_login: | Lstand0 |
| OctolyticsDimensionRepository_id: | 836403385 |
| OctolyticsDimensionRepository_nwo: | Lstand0/FiveM-Mod-Menu |
| OctolyticsDimensionRepository_public: | |
| OctolyticsDimensionRepository_is_fork: | - |
| OctolyticsDimensionRepository_network_root_id: | 836403385 |
| OctolyticsDimensionRepository_network_root_nwo: | Lstand0/FiveM-Mod-Menu |
| TurboBodyClasses: | logged-out env-production page-responsive |
| BrowserStatsUrl: | https://api.github.com/_private/browser/stats |
| BrowserErrorsUrl: | https://api.github.com/_private/browser/errors |
| ThemeColor: | #1e2327 |
| ColorScheme: | light dark |
Total processes
188
Monitored processes
56
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7400 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1332 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5508 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1452 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2400 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1500 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6120 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1588 | "C:\Users\admin\Desktop\FiveM-Mod-Menu-main\Loader.exe" | C:\Users\admin\Desktop\FiveM-Mod-Menu-main\Loader.exe | explorer.exe | ||||||||||||
User: admin Company: StellarTech Innovations Inc. Integrity Level: MEDIUM Description: StellarTech Solutions Exit code: 0 Version: 1.1.0.0 Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=7564 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6596 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2364 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3648 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2808 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3460 --field-trial-handle=2412,i,14472093559771346849,4917306714758682559,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
9 321
Read events
9 273
Write events
48
Delete events
0
Modification events
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: FD94D8B3CD822F00 | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0850DEB3CD822F00 | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328328 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A26ED851-CA7B-496A-8955-85626FC28E8F} | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328328 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F2E210A4-0D11-4F18-B191-FFA20D95A6C0} | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328328 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FE14C639-DE04-4AE6-A111-3E630B437DB0} | |||
| (PID) Process: | (5508) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328328 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E2D7FD70-DC1E-4324-84B3-C751801FE292} | |||
Executable files
28
Suspicious files
549
Text files
113
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF90265.TMP | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF90265.TMP | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF90275.TMP | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF90265.TMP | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF90275.TMP | — | |
MD5:— | SHA256:— | |||
| 5508 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
159
DNS requests
151
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4548 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1728986190&P2=404&P3=2&P4=YCWSRM21qdwbU9ifxG%2funAaTGfJqt8TxAwHs%2f52JI36kvaOvqKida3fmfQz9CeoU76eOhglfV6UVDAFSVT0DLQ%3d%3d | unknown | — | — | whitelisted |
4548 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6991b5bf-fbe9-4d69-9238-4b6fbbf4624d?P1=1729240172&P2=404&P3=2&P4=eFulAnTX1iHq9sf5kN9yFYpU72IaK4TL2TTRI%2b5NW6lL%2baGTGFldqvs924oieoP71EYMXiiSOCEELfVIo%2bdqZQ%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7568 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7568 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4548 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/181d62d0-8e71-4ab0-b6f0-62f746749689?P1=1728986190&P2=404&P3=2&P4=YCWSRM21qdwbU9ifxG%2funAaTGfJqt8TxAwHs%2f52JI36kvaOvqKida3fmfQz9CeoU76eOhglfV6UVDAFSVT0DLQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7060 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
816 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (extorteauhhwigw .shop) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (potterryisiw .shop) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (penetratedpoopp .xyz) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (swellfrrgwwos .xyz) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (towerxxuytwi .xyz) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (pedestriankodwu .xyz) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (ellaboratepwsz .xyz) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (contintnetksows .shop) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (foodypannyjsud .shop) |
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Lumma Stealer Related CnC Domain in DNS Lookup (foodypannyjsud .shop) |