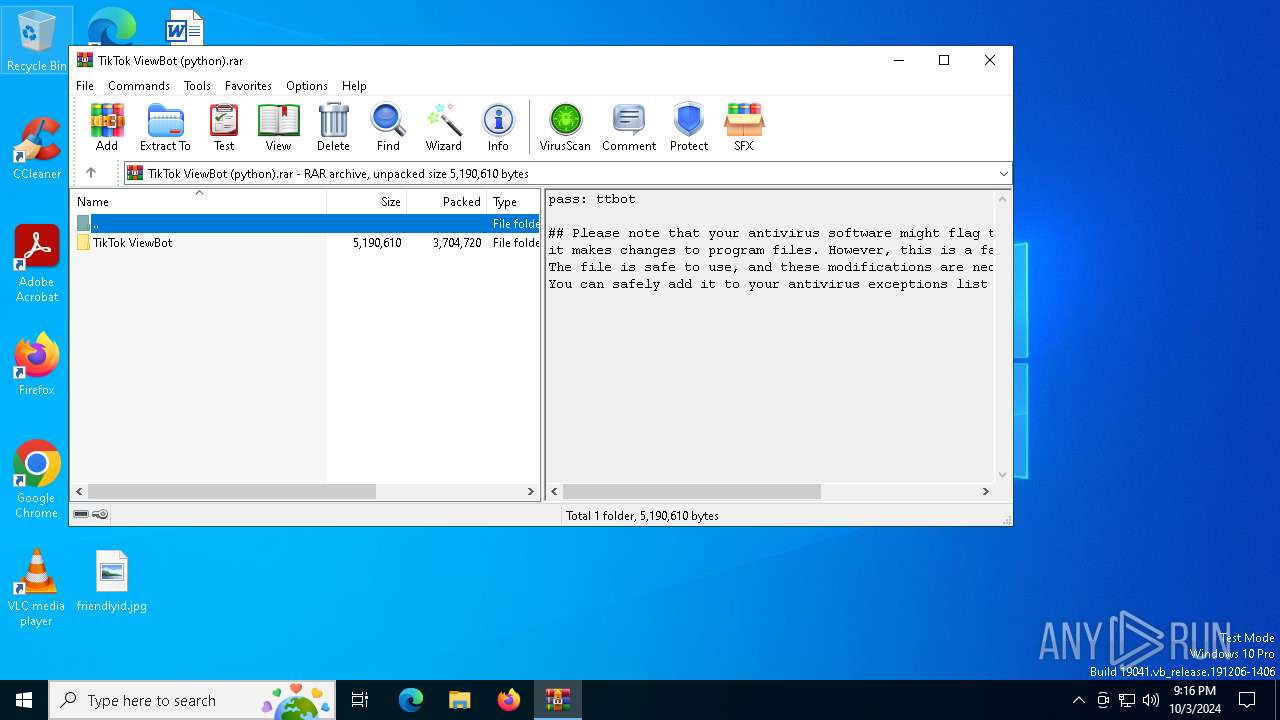
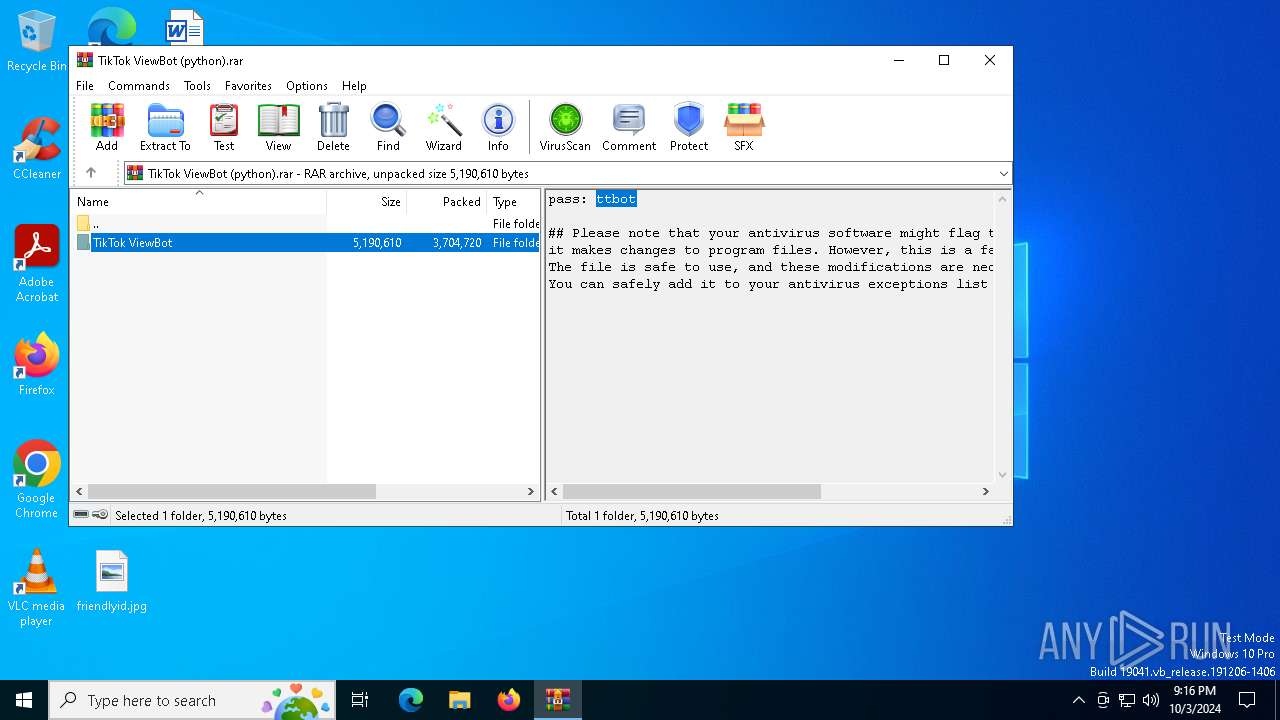
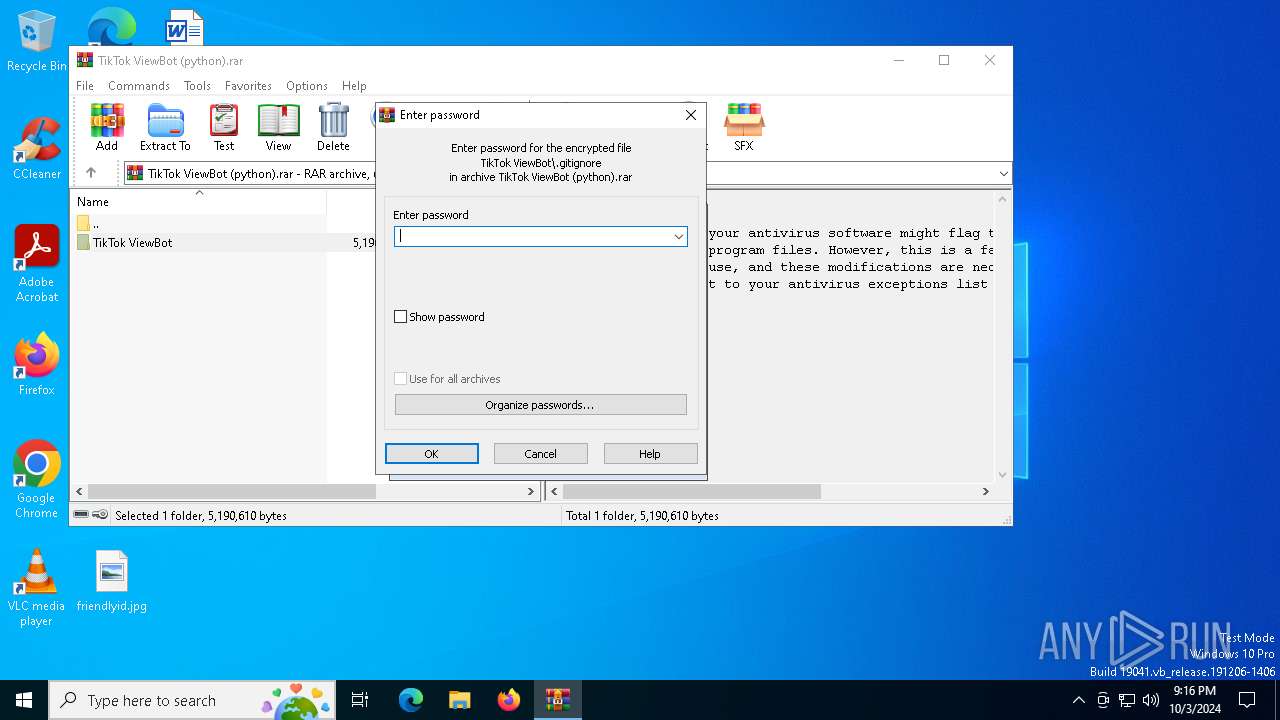
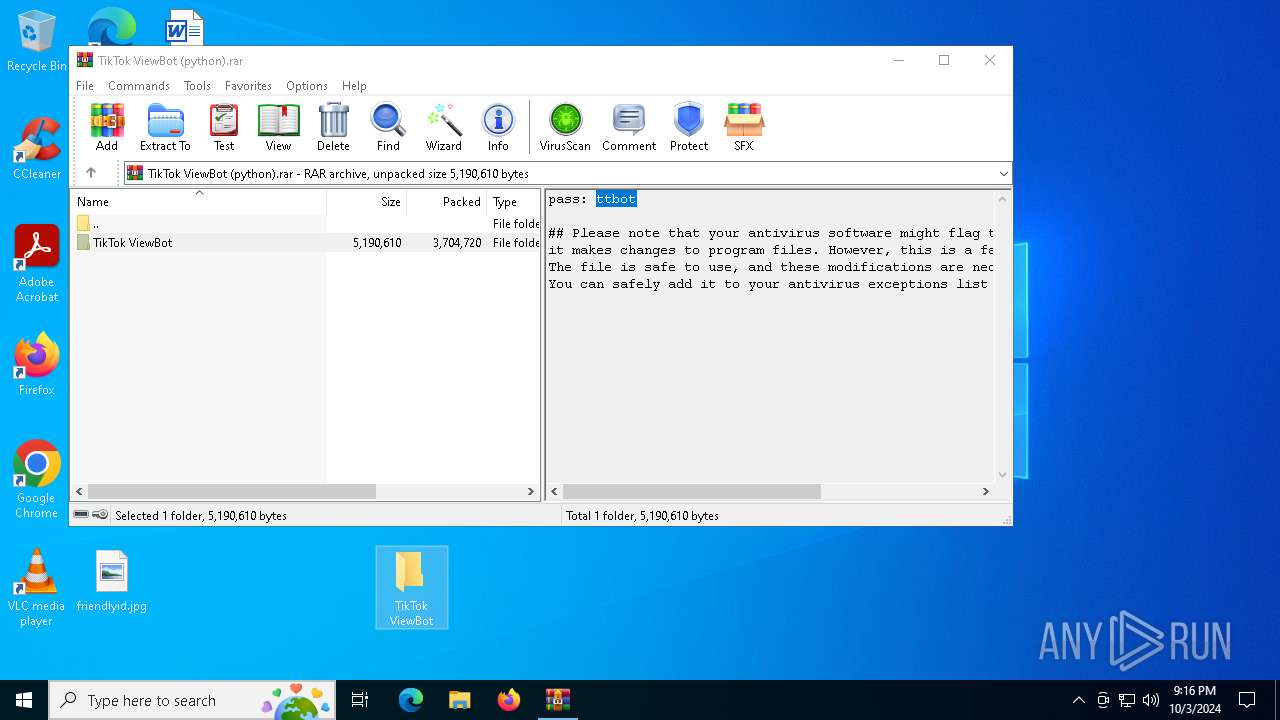
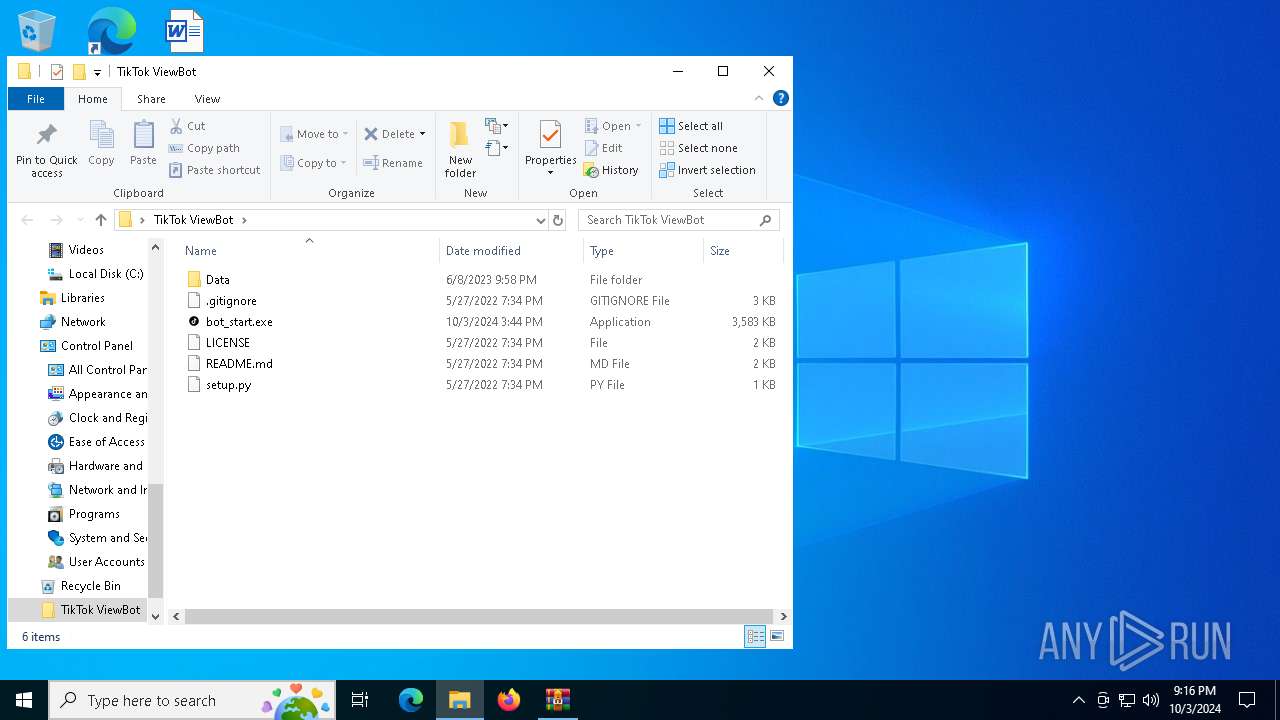
| File name: | TikTok ViewBot (python).rar |
| Full analysis: | https://app.any.run/tasks/9db60724-20db-43cc-873d-fc8aee21e585 |
| Verdict: | Malicious activity |
| Threats: | Stealc is a stealer malware that targets victims’ sensitive data, which it exfiltrates from browsers, messaging apps, and other software. The malware is equipped with advanced features, including fingerprinting, control panel, evasion mechanisms, string obfuscation, etc. Stealc establishes persistence and communicates with its C2 server through HTTP POST requests. |
| Analysis date: | October 03, 2024, 21:16:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C363B2BE8BC5164B9A05210D57BA1C0E |
| SHA1: | 5D74725B4F0A8B8E473DFF1D10097D31304F0335 |
| SHA256: | 03594E7F921AEA6CBCF8F7F83E39D5947E18ED66574B5F821EB90B9524B5F81A |
| SSDEEP: | 98304:8OWQKujdZV4/SVnhXH8IcOnpdQwTtXhS6QtS/vlUuU3T2SWSZtbCDh7thSMnIGIM:0mCKQAB/U8 |
MALICIOUS
Stealers network behavior
- sWsmPty.exe (PID: 4920)
Connects to the CnC server
- sWsmPty.exe (PID: 4920)
STEALC has been detected (SURICATA)
- sWsmPty.exe (PID: 4920)
ONLINECLIPPER has been detected (YARA)
- VC_redistx64.exe (PID: 3180)
SUSPICIOUS
Executable content was dropped or overwritten
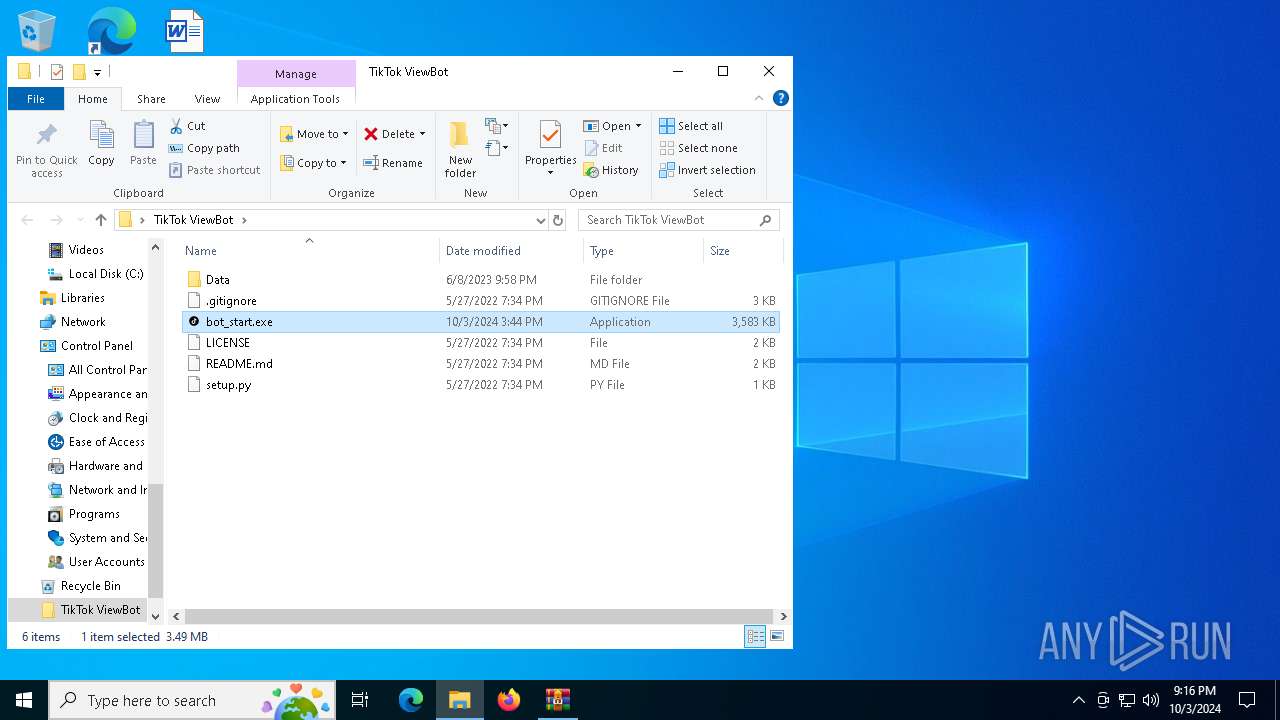
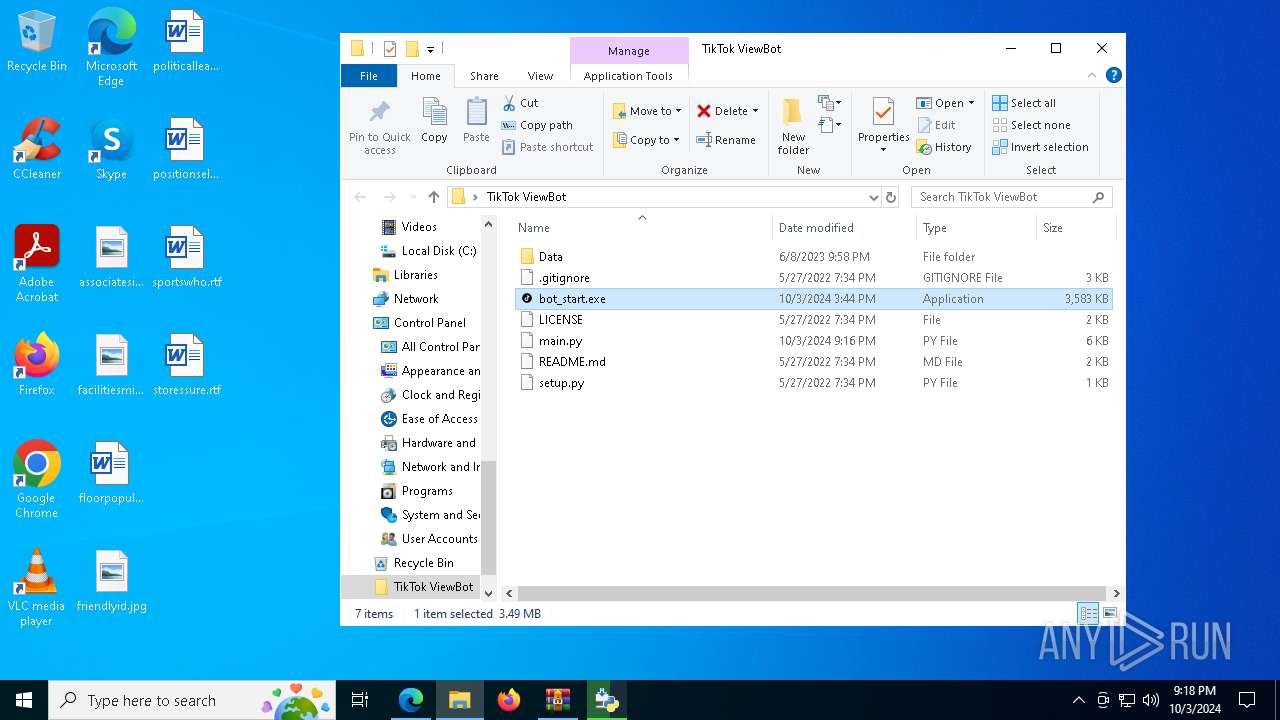
- bot_start.exe (PID: 5588)
- VC_redistx64.exe (PID: 3180)
- python-3.7.0-amd64.exe (PID: 7648)
- python-3.7.0-amd64.exe (PID: 7572)
- python-3.7.0-amd64.exe (PID: 7812)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- sWsmPty.exe (PID: 4920)
- VC_redistx64.exe (PID: 3180)
Connects to the server without a host name
- sWsmPty.exe (PID: 4920)
Starts itself from another location
- python-3.7.0-amd64.exe (PID: 7572)
The process drops C-runtime libraries
- python-3.7.0-amd64.exe (PID: 7572)
- msiexec.exe (PID: 5704)
Process drops legitimate windows executable
- python-3.7.0-amd64.exe (PID: 7572)
- msiexec.exe (PID: 5704)
Contacting a server suspected of hosting an CnC
- sWsmPty.exe (PID: 4920)
Possible usage of Discord/Telegram API has been detected (YARA)
- VC_redistx64.exe (PID: 3180)
Executes as Windows Service
- VSSVC.exe (PID: 2648)
Process drops python dynamic module
- msiexec.exe (PID: 5704)
INFO
Manual execution by a user
- bot_start.exe (PID: 5588)
- msedge.exe (PID: 4932)
- notepad++.exe (PID: 7192)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3824)
- msedge.exe (PID: 4932)
- msedge.exe (PID: 3300)
- msiexec.exe (PID: 5704)
- msedge.exe (PID: 1312)
Attempting to use instant messaging service
- VC_redistx64.exe (PID: 3180)
- sWsmPty.exe (PID: 4920)
Manages system restore points
- SrTasks.exe (PID: 4108)
Themida protector has been detected
- VC_redistx64.exe (PID: 3180)
Application launched itself
- msedge.exe (PID: 4932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(3180) VC_redistx64.exe
Telegram-Tokens (1)7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE
Telegram-Info-Links
7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE
Get info about bothttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/getMe
Get incoming updateshttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/getUpdates
Get webhookhttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/deleteWebhook?drop_pending_updates=true
Telegram-Tokens (1)7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE
Telegram-Info-Links
7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE
Get info about bothttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/getMe
Get incoming updateshttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/getUpdates
Get webhookhttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7308213044:AAFm9yNR1WX2-QnC_ZcUdYHkkJGg7179JYE
End-PointsendMessage
Args
Telegram-Responses
oktrue
result
message_id172833
from
id7308213044
is_bottrue
first_namecry
usernamecrystaker_bot
chat
id1886849305
first_nameSir
last_nameShant
usernamesirshant
typeprivate
date1727990207
text🚀Clipper is online!!!
#3e21ac9cc7f9036e191b6a498aa05c2166112969c1e32c6515325e78c275fac6
entities
offset24
length65
typehashtag
TRiD
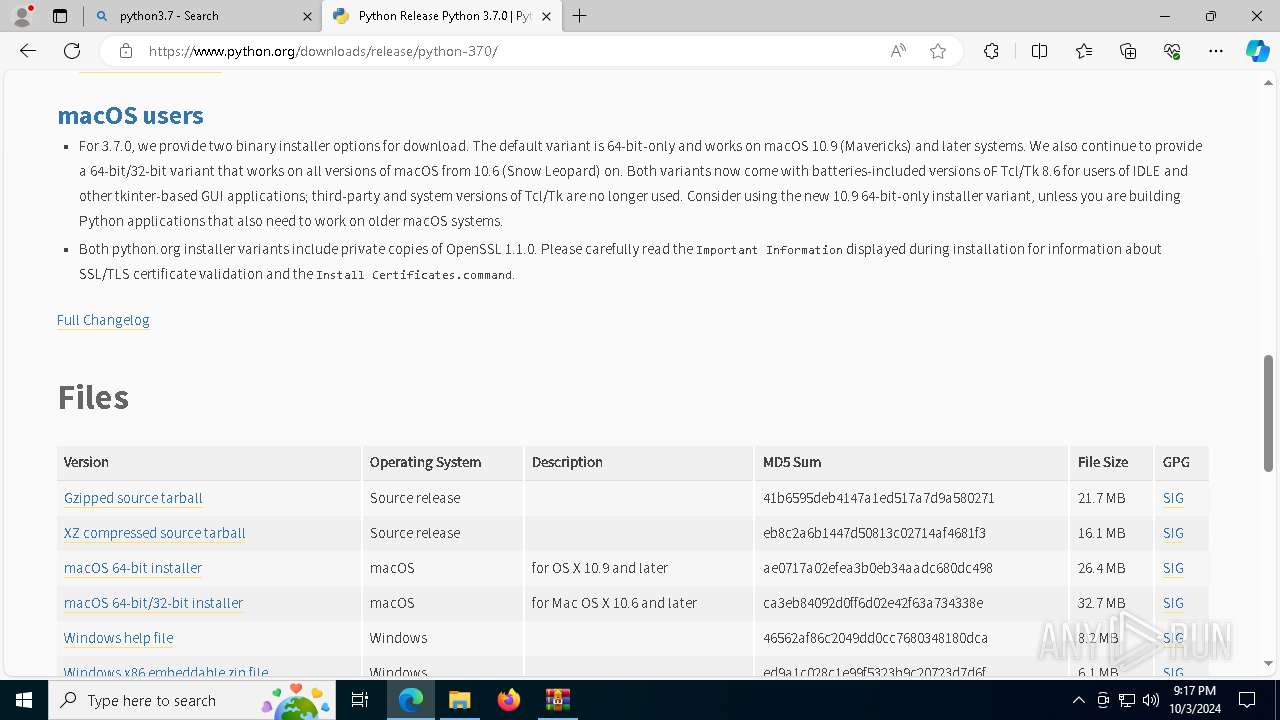
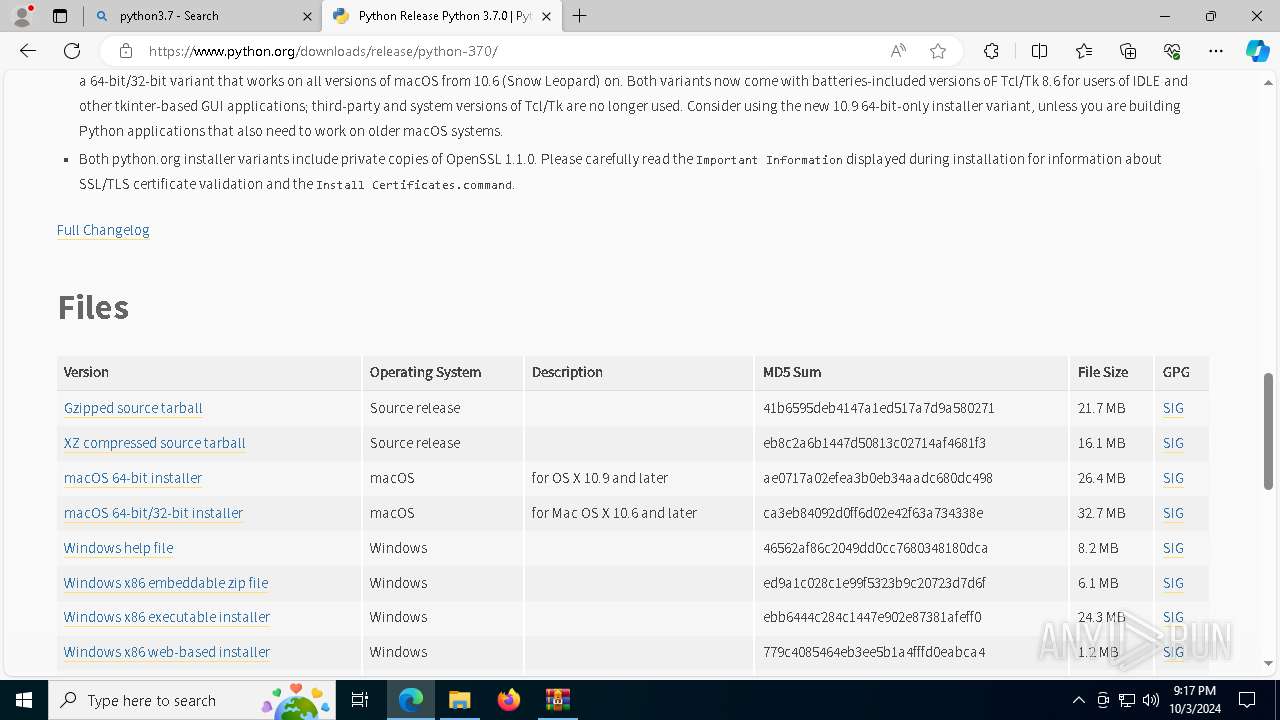
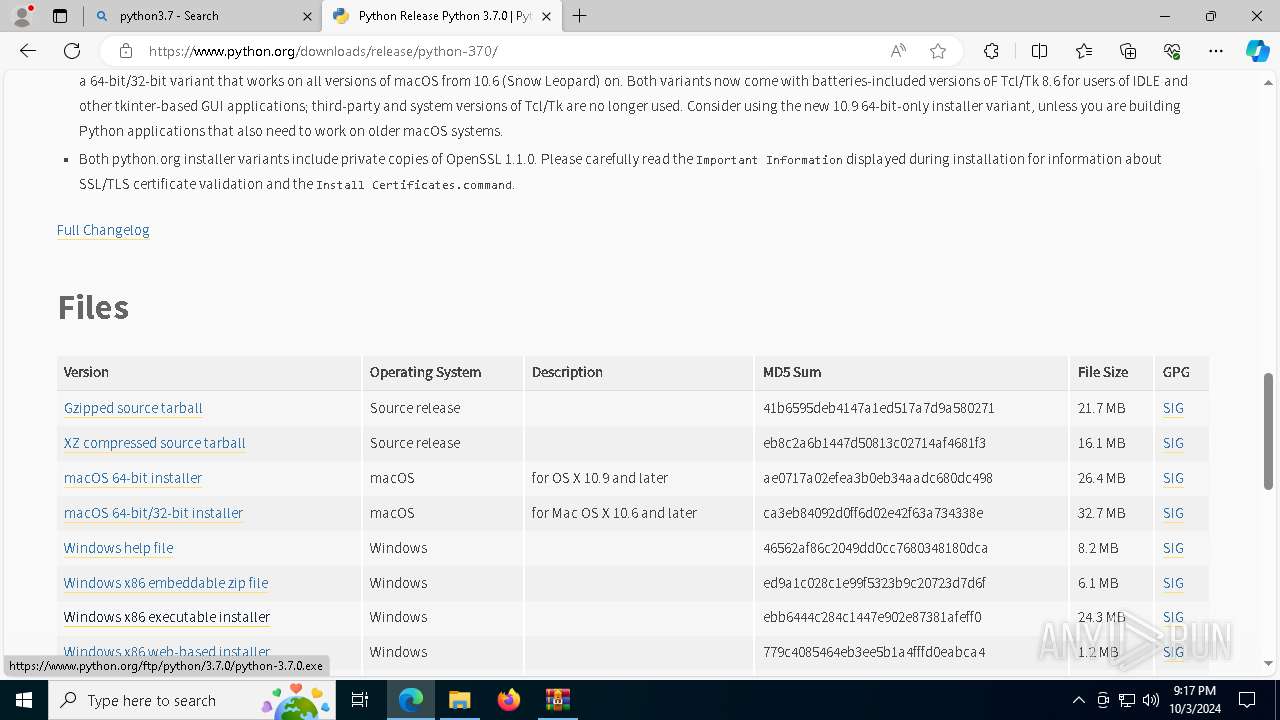
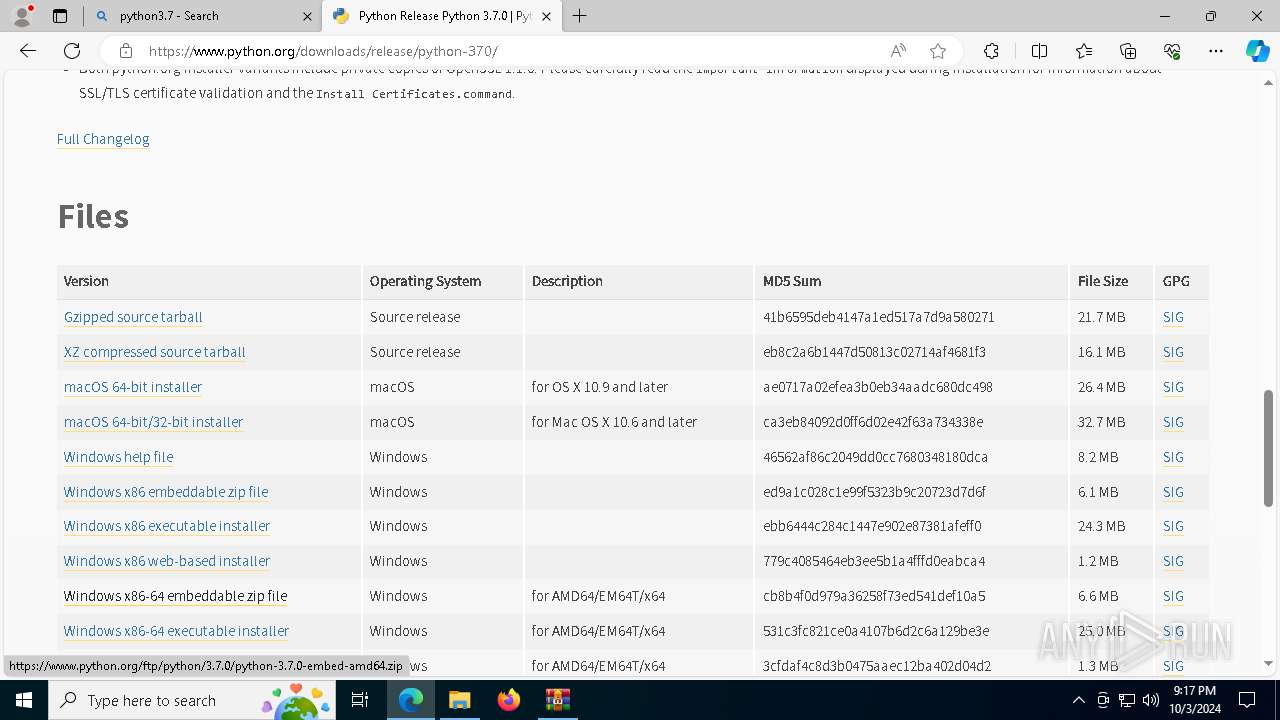
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
217
Monitored processes
76
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4384 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1164 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8660 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6504 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1312 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7856 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2208 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2252 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --no-appcompat-clear --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=2372 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2356 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7856 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7900 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2648 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2772 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3508 --field-trial-handle=2376,i,13089581456406030620,4250563549354934433,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
50 668
Read events
45 911
Write events
4 663
Delete events
94
Modification events
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TikTok ViewBot (python).rar | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3824) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4920) sWsmPty.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4920) sWsmPty.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4920) sWsmPty.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
101
Suspicious files
887
Text files
3 241
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\Data\UserAgent.py | text | |
MD5:0C9B29E6B8291144A8A1C7B190ACCBE5 | SHA256:8EC04B593BBF03B344809EBCA690DCEC7BC082BCCD0E28D3B4931B371AB044C9 | |||
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\Data\Proxies.txt | text | |
MD5:479410925B7FCA43CFD87C5867CC65F2 | SHA256:23725E00D9DACEC4E1FDC3C2A2FB7D20743873A1F9CF9D66D0CD0069E70CB0B3 | |||
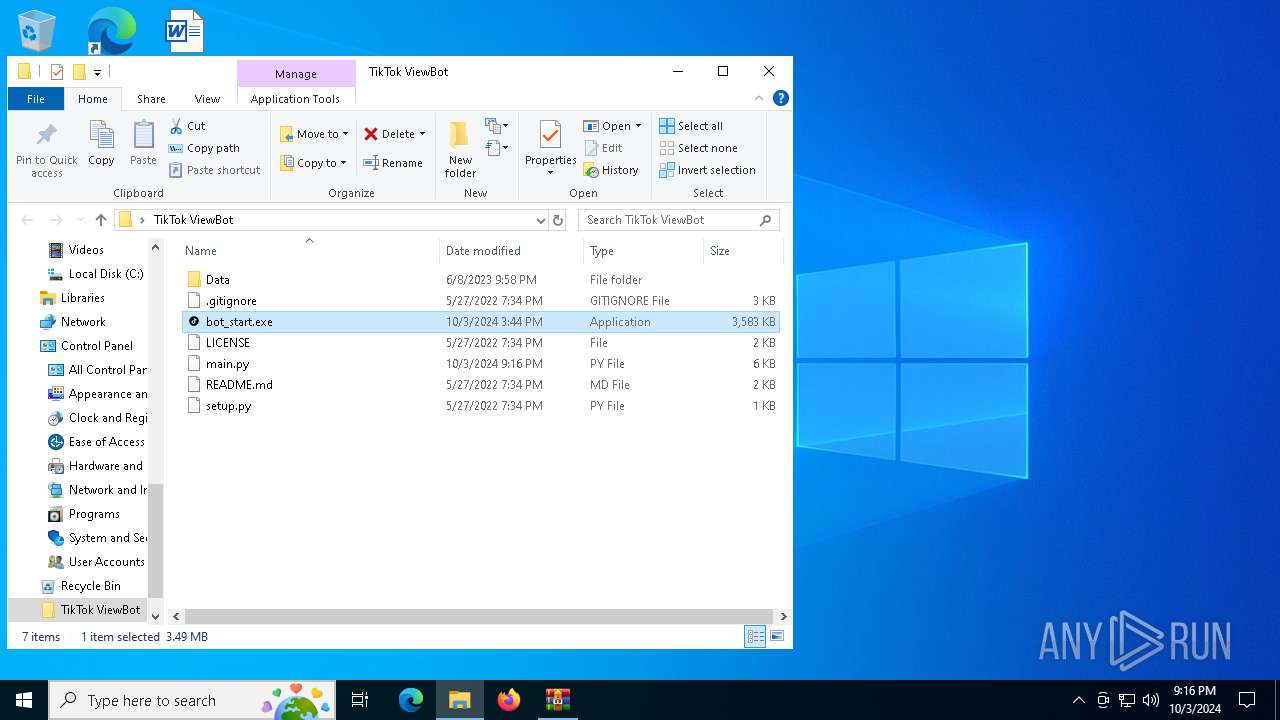
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\bot_start.exe | executable | |
MD5:75BED36AA66CB6D80FDB60D0B152FBEB | SHA256:EB4081440D3455D5403C1D460475DAB513F2595A5078260F3B9C93E4FAB9A913 | |||
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\Data\ScrapProxie.py | text | |
MD5:005E6B6CD75E6FD6040731C64494E537 | SHA256:8FD6AFC4C92B8C65EB96A7493E559C83449578FCF178E20D9D126B411EEAD5E5 | |||
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\.gitignore | text | |
MD5:DA211C7C93BF4E8861AF1DC2616C9548 | SHA256:FCC9443AE95FC4CFD56AED31937D8060E03212A92707615FED5EE59E0B38DEF6 | |||
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\Data\Lists.py | text | |
MD5:58B844082767DD40B291276087B6323B | SHA256:B21702251CF0E88C166088D4E08294B2B0C2F961DA8056AC48C735243D554279 | |||
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\LICENSE | text | |
MD5:92CD1AA46AF18DB848C738B5381D5776 | SHA256:98DC91FE998ED0C083E5F54BD7B4B86455DB81CBE0F90833D6EB1C029F4C49B8 | |||
| 3824 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3824.345\TikTok ViewBot\README.md | text | |
MD5:A7A864F27133423E30394AF410CB4782 | SHA256:04AC4EFD3BBA8AC958CD3A73FEF70715703C62F8DEB962D12B13249C7B2AE3F6 | |||
| 4920 | sWsmPty.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\156887258BBD6E1FEF562837733EA04E_5BBC02CEDFD3F7AC9E268D830CF231EE | der | |
MD5:931FF6913D57F05F2B8F4B76AF05D993 | SHA256:FAE982414A46ECEDE90D2A24A1AD5EE330F3FC4424AAF51FC939A678F6630C3B | |||
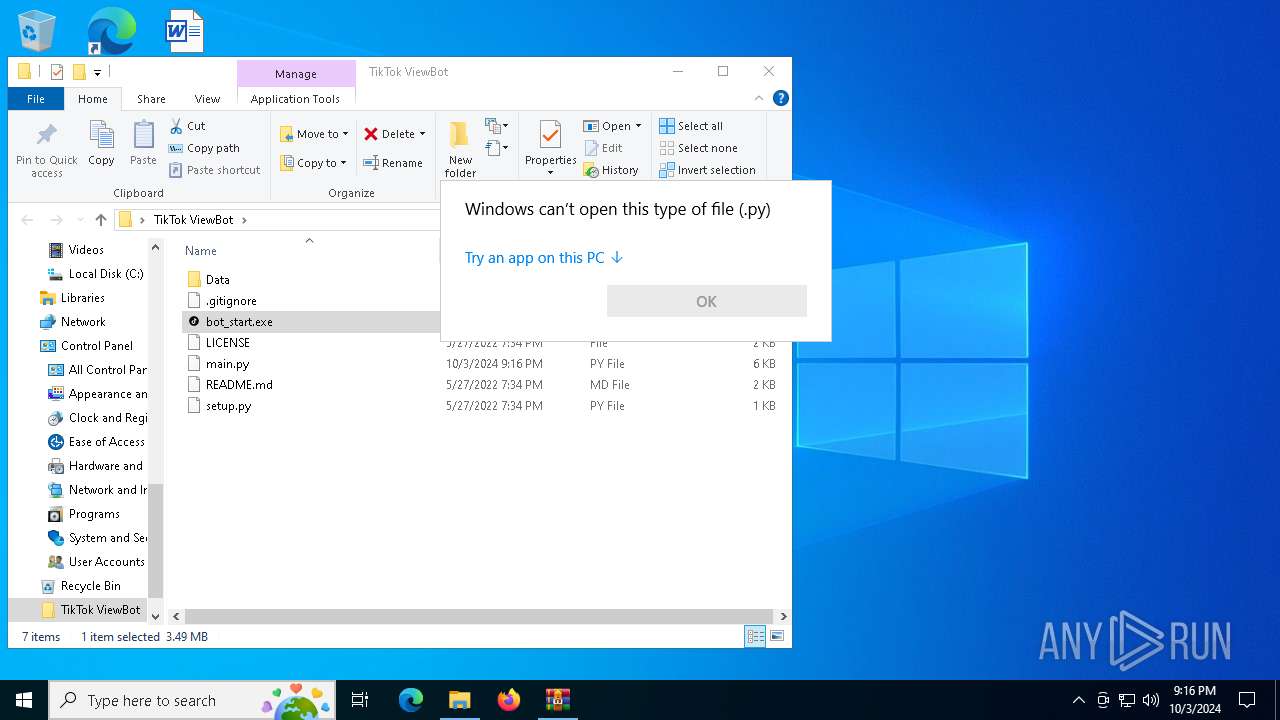
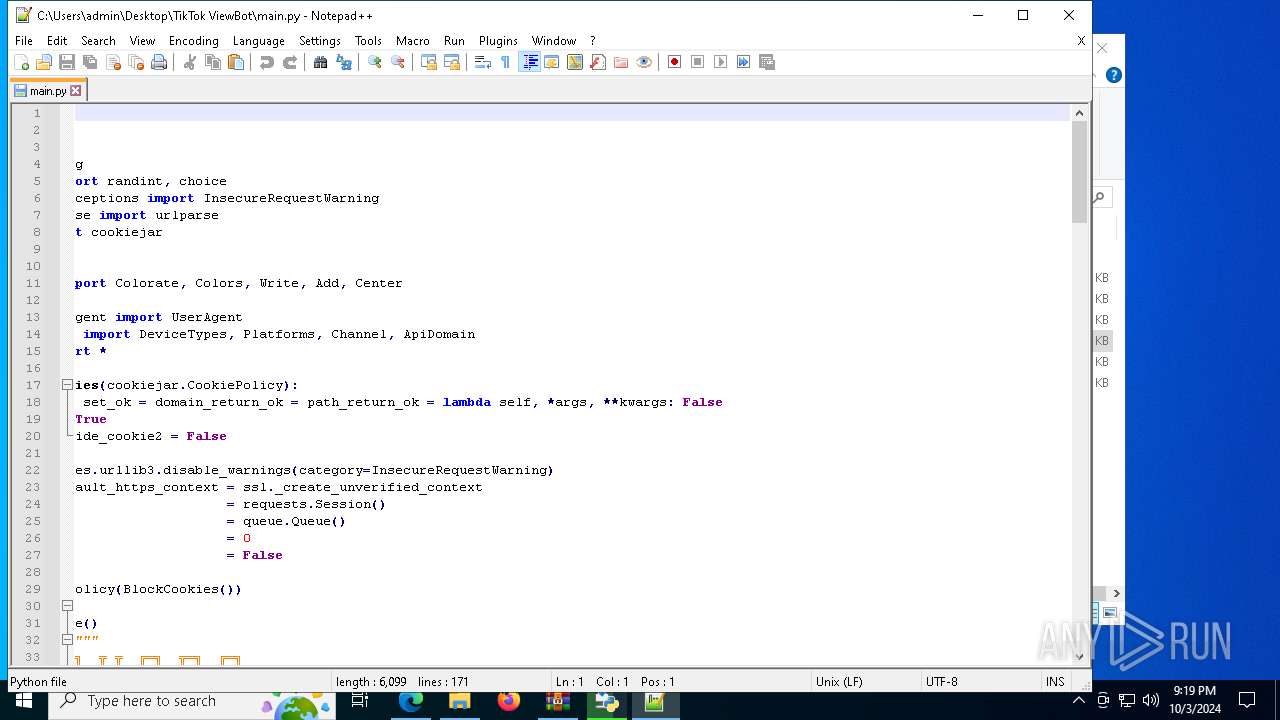
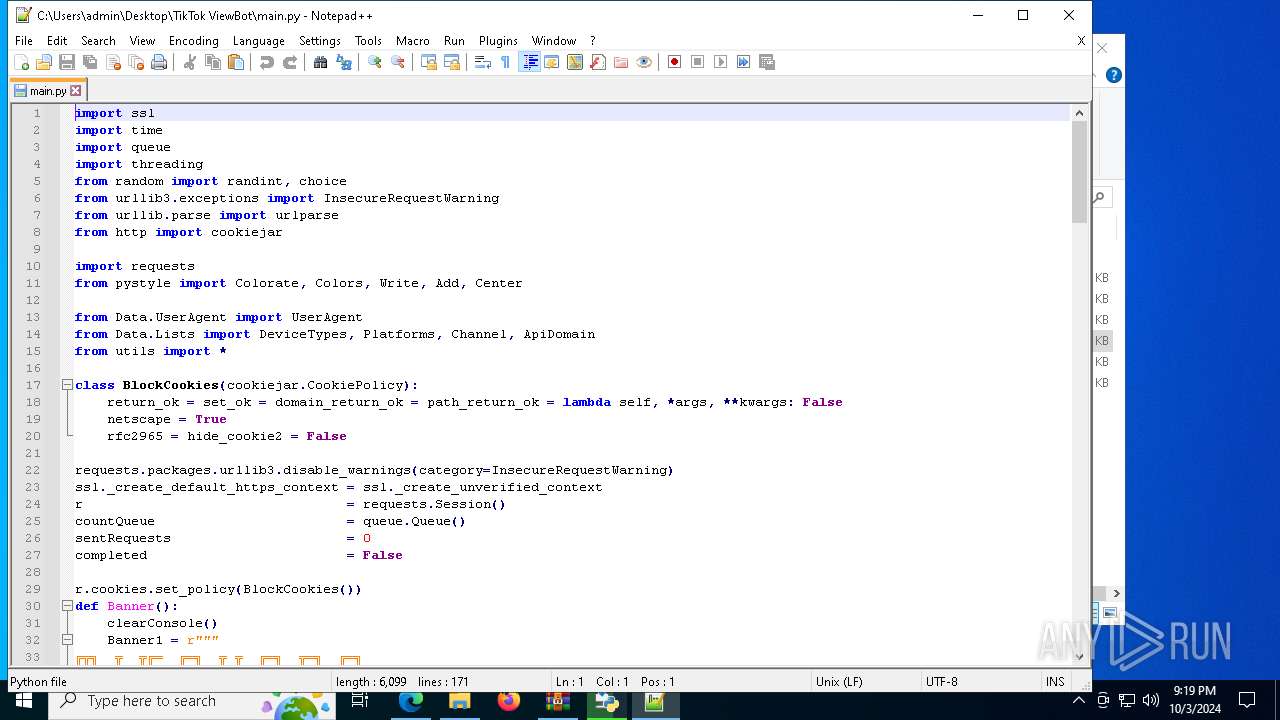
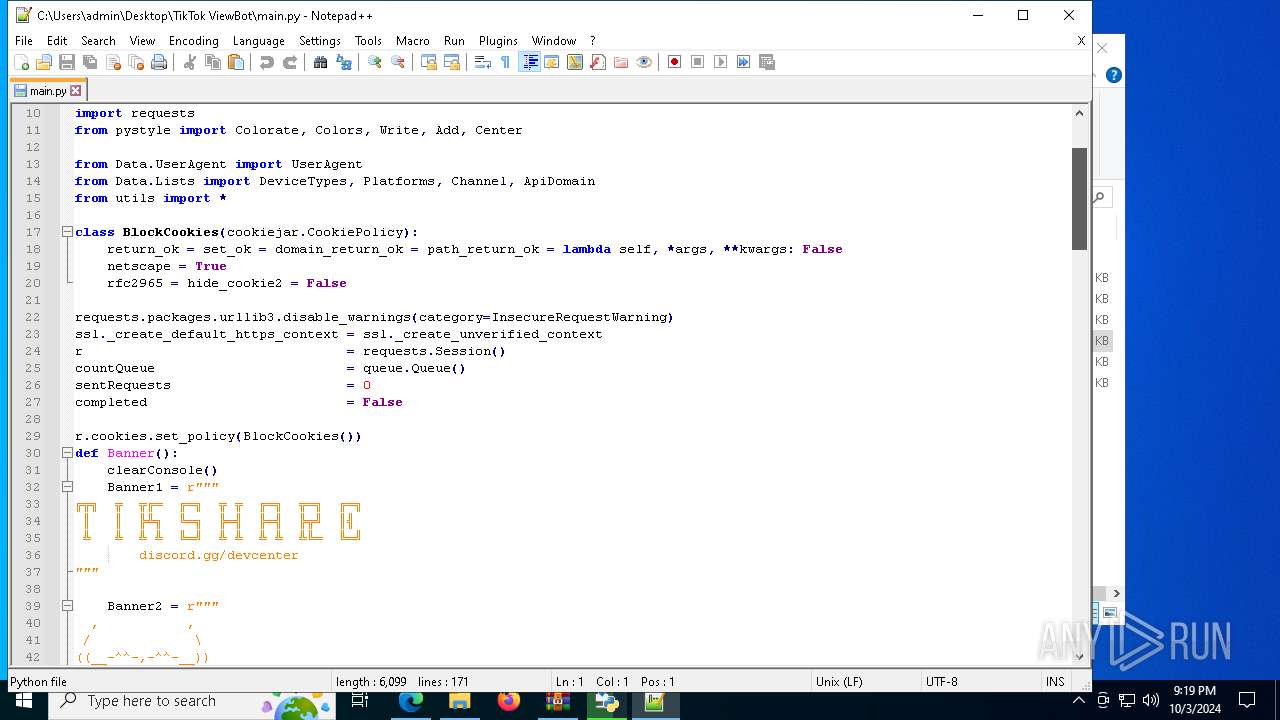
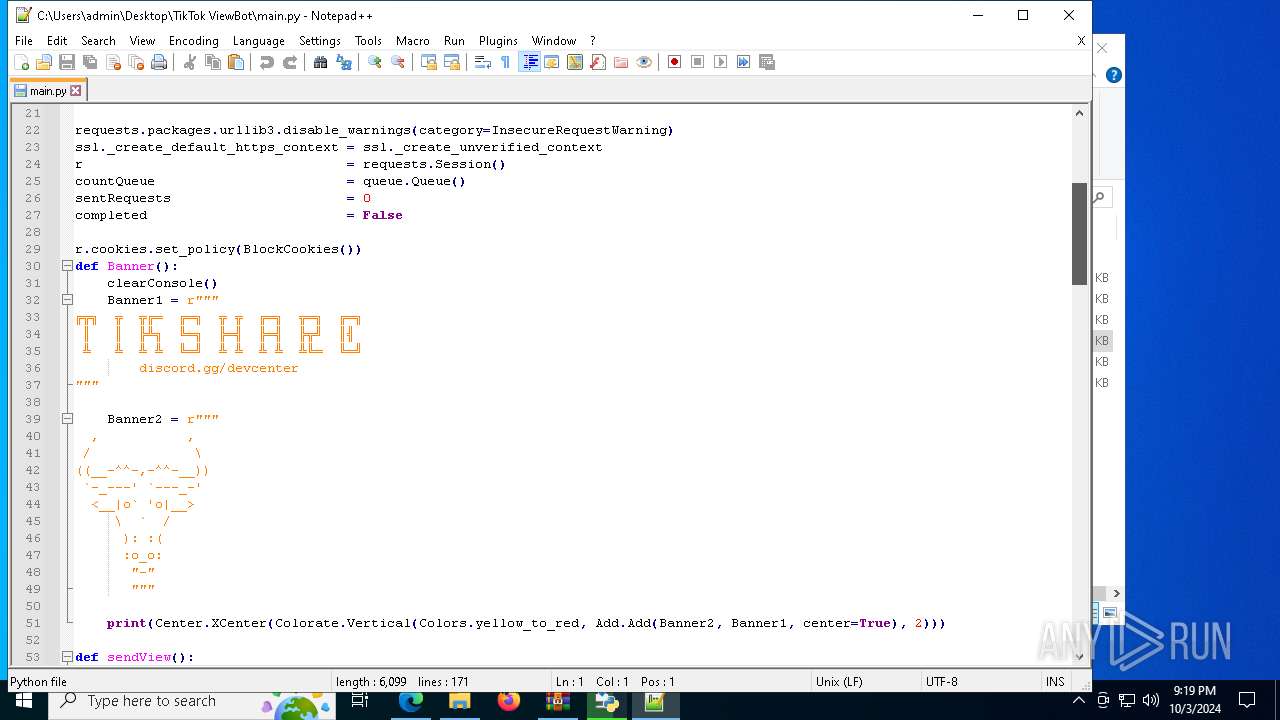
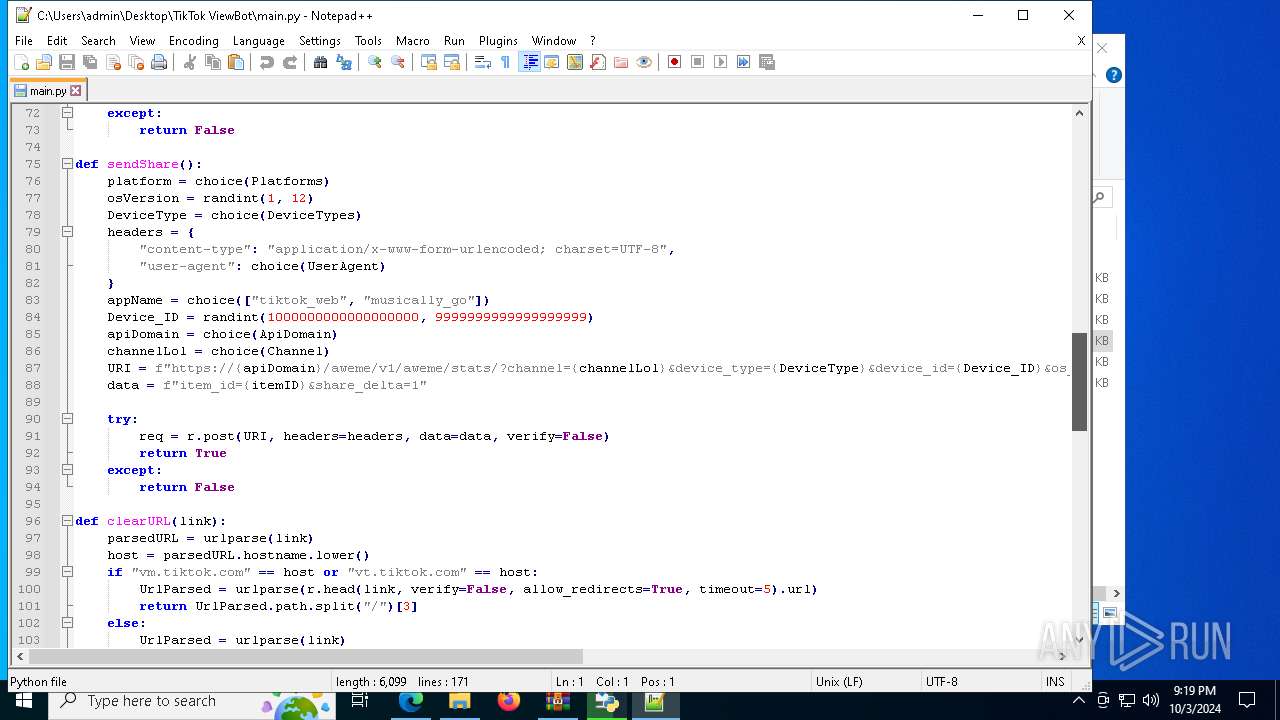
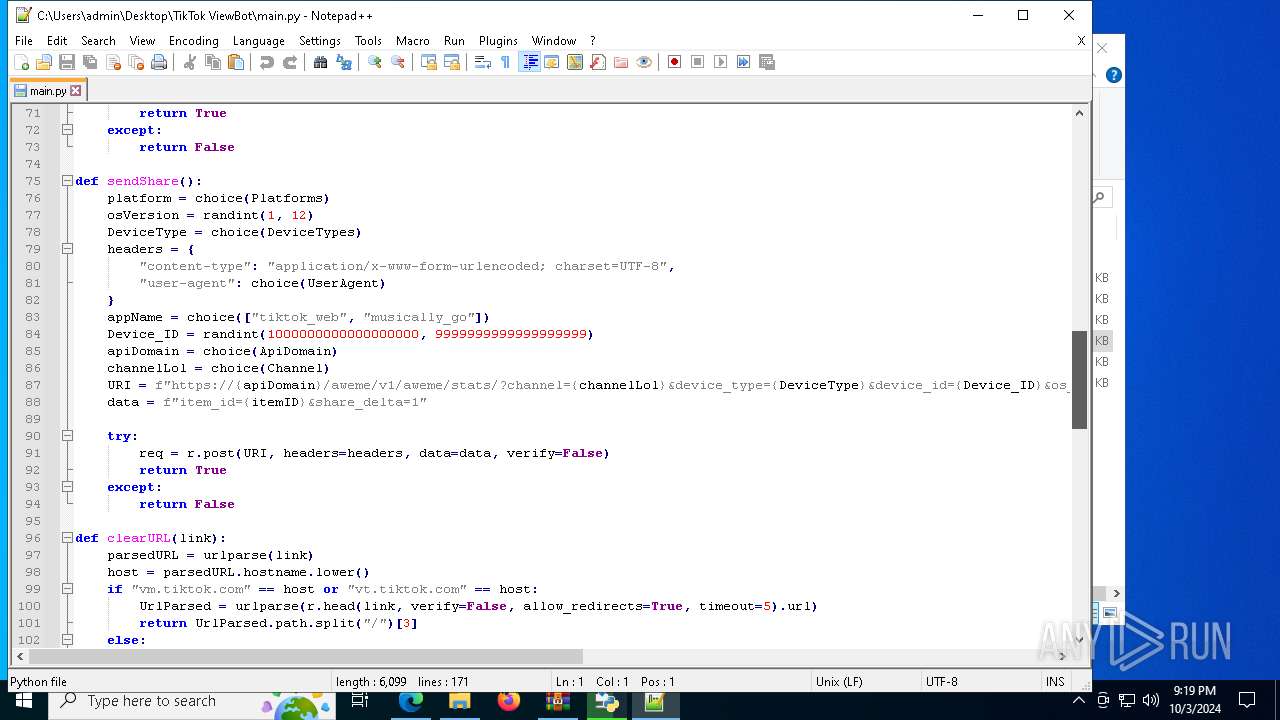
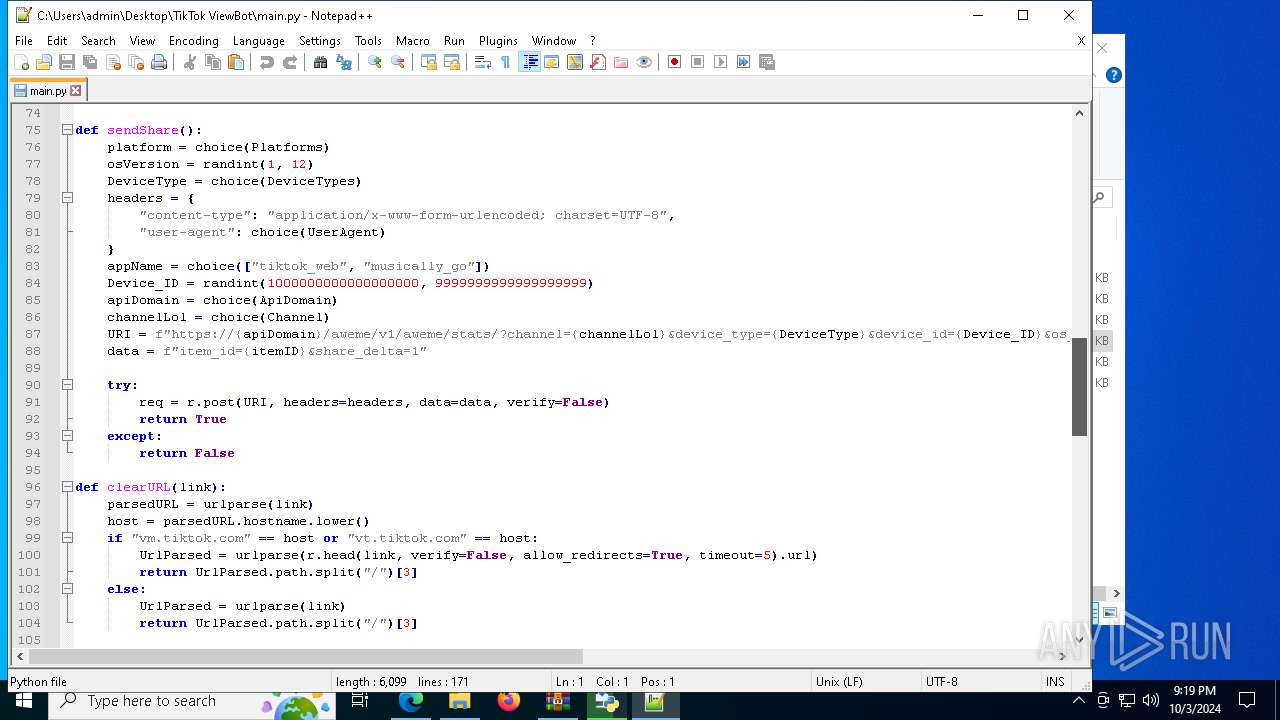
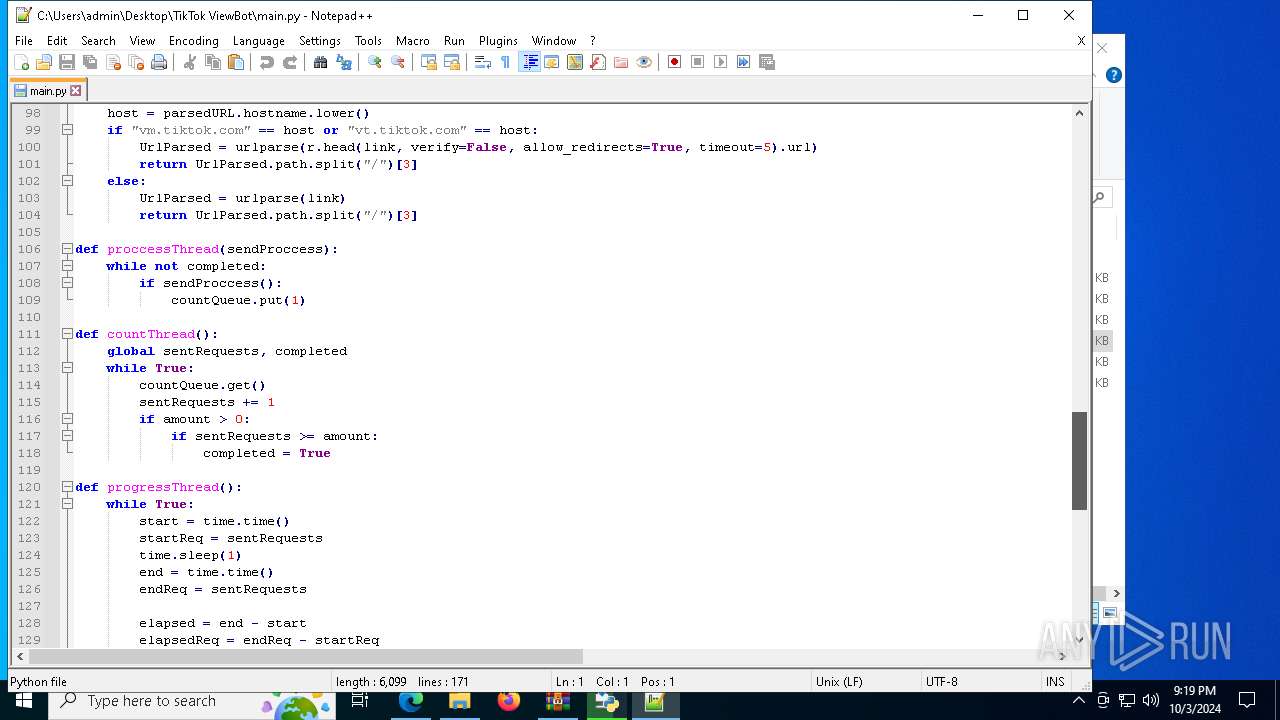
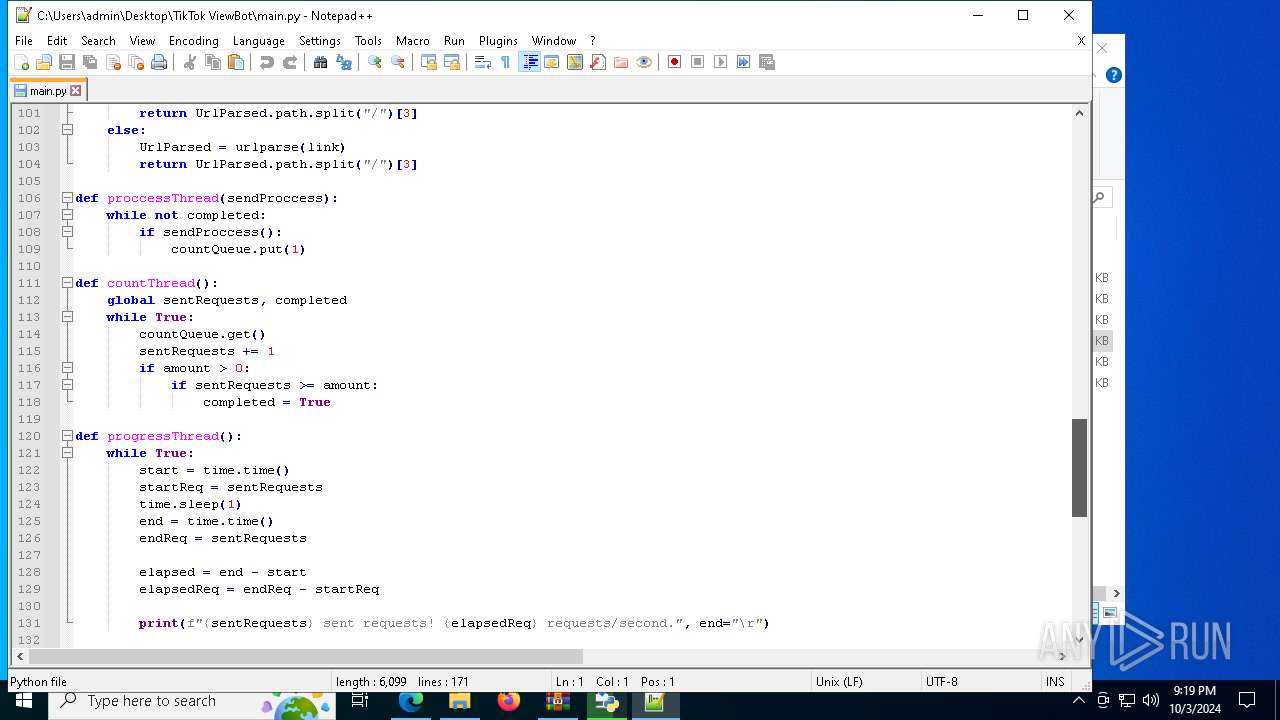
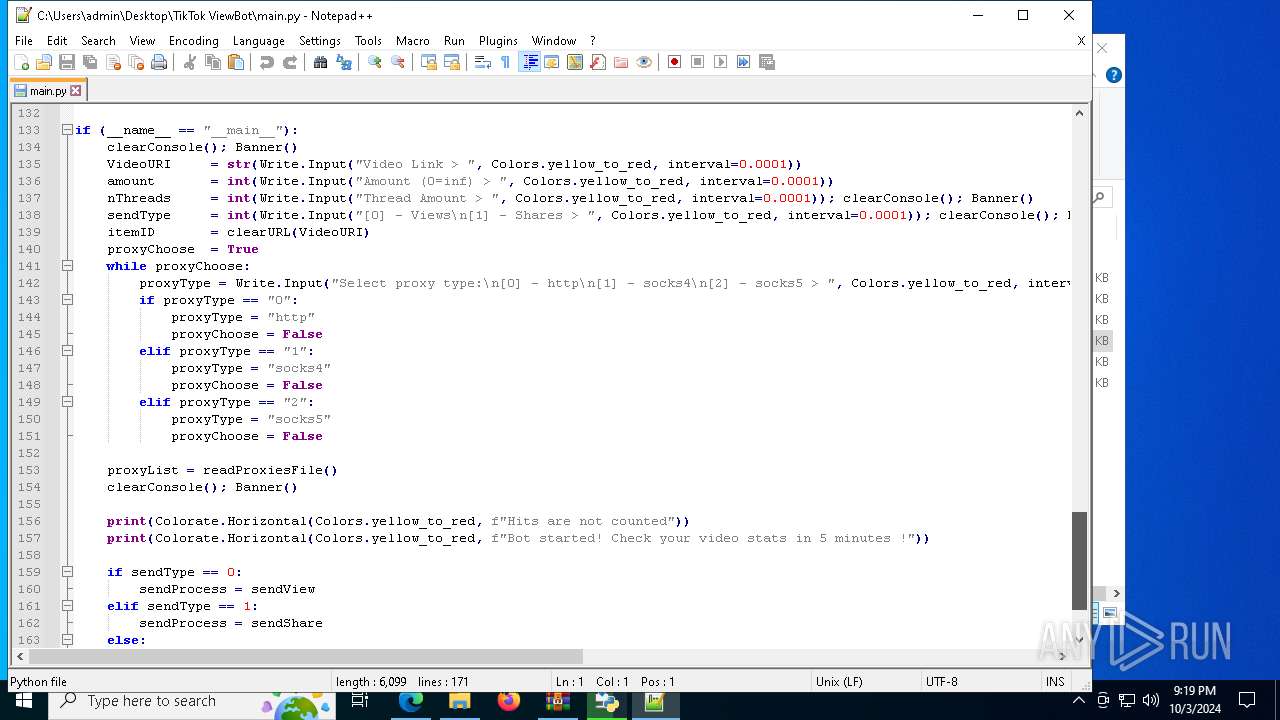
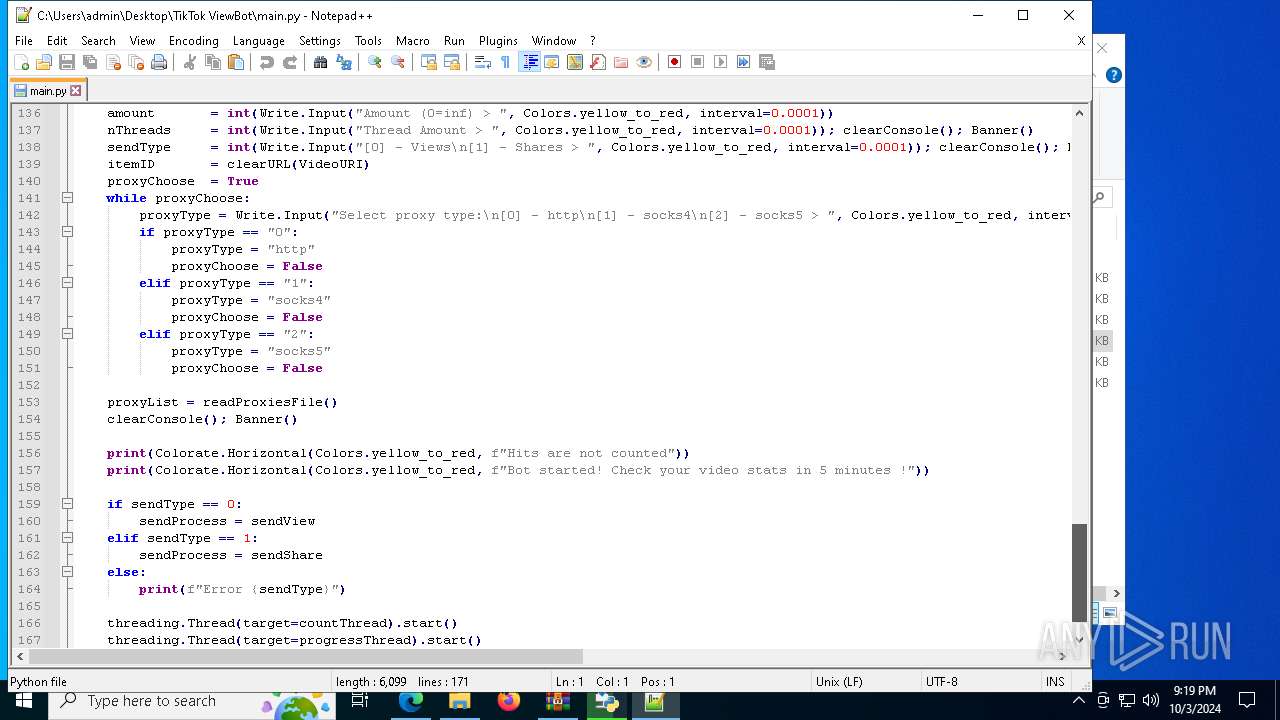
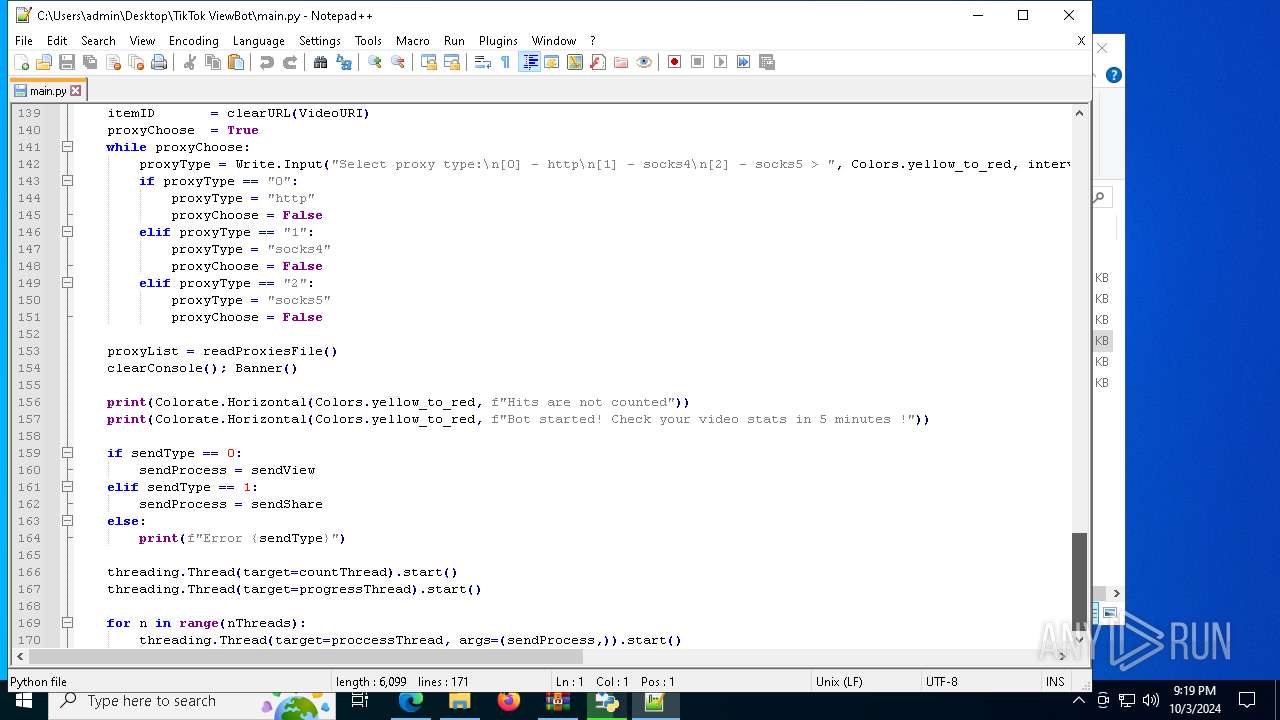
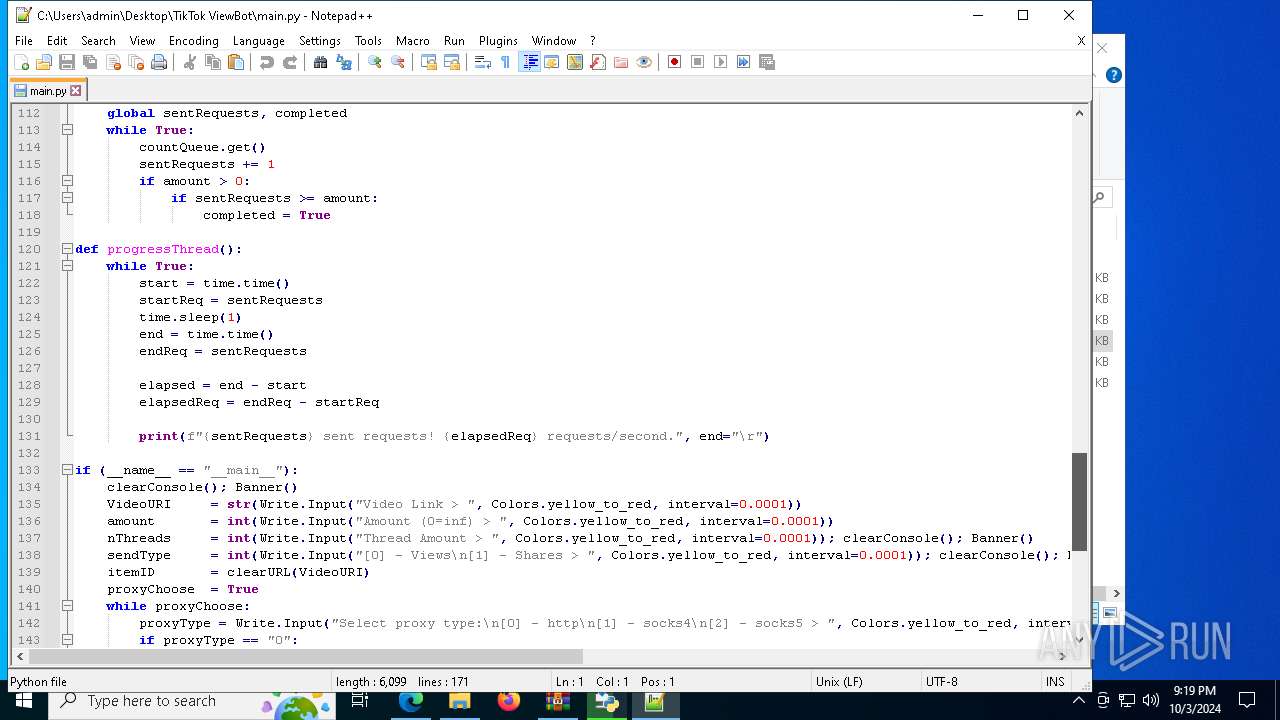
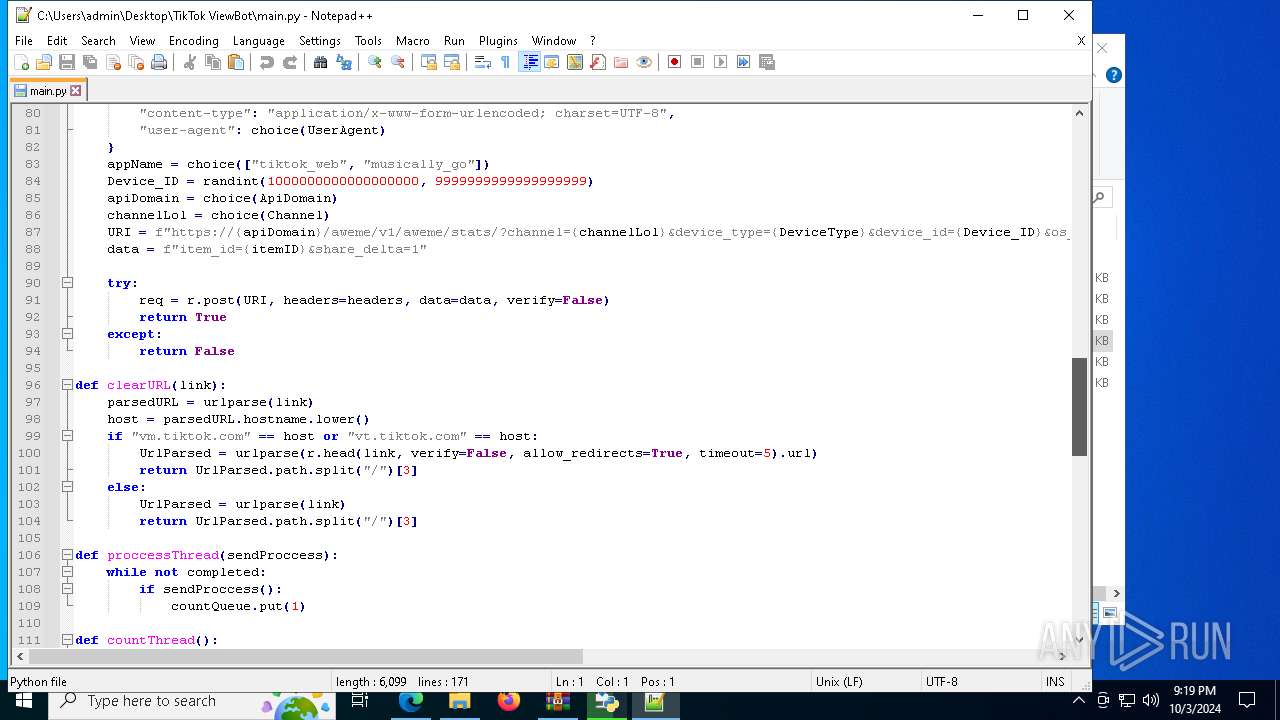
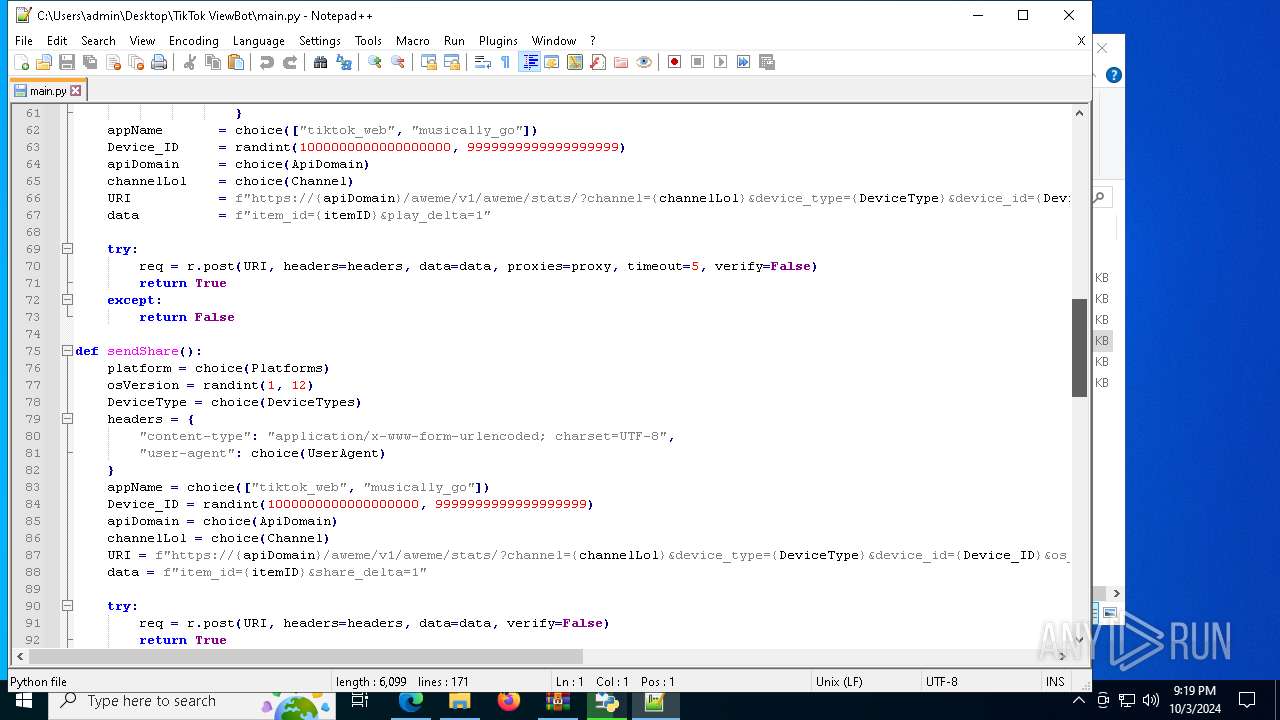
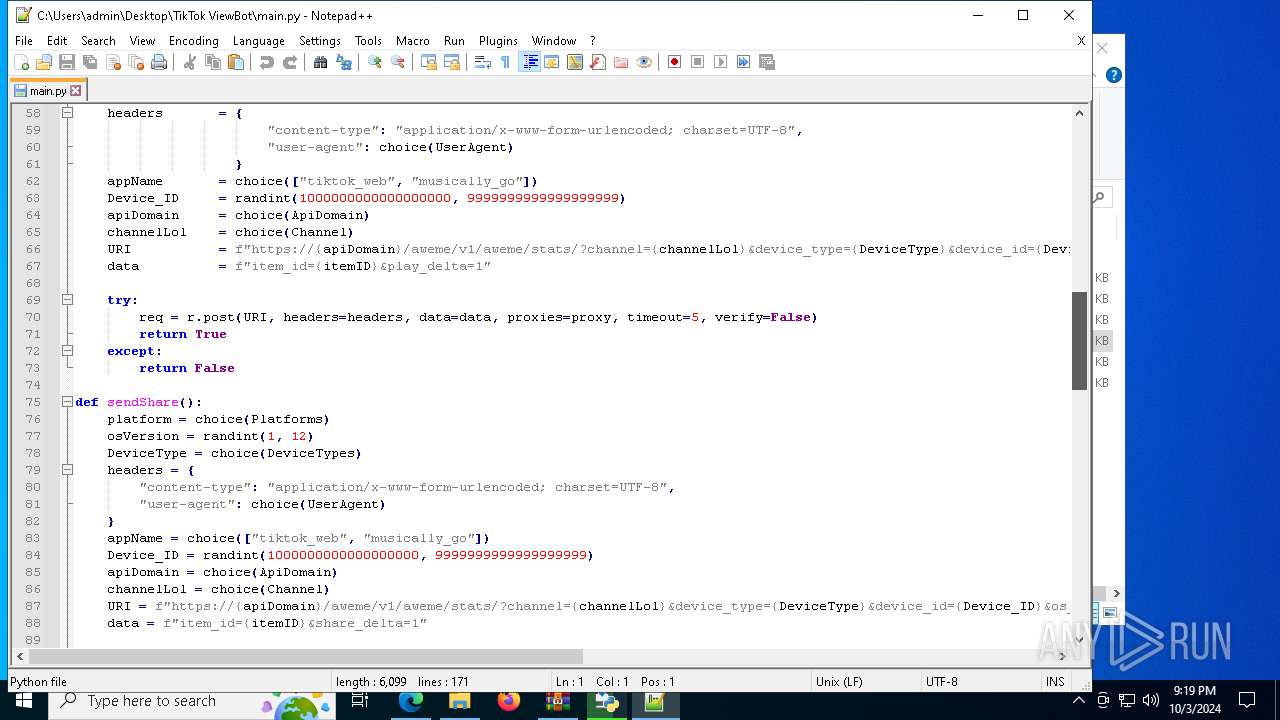
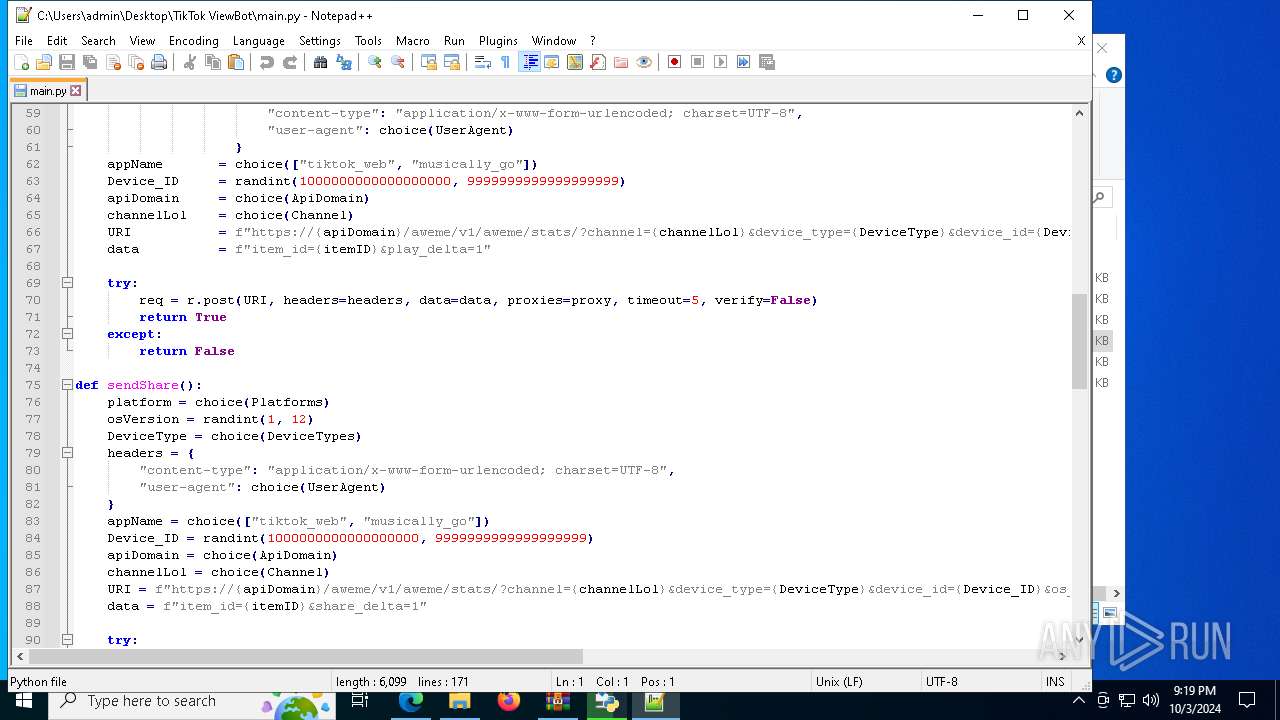
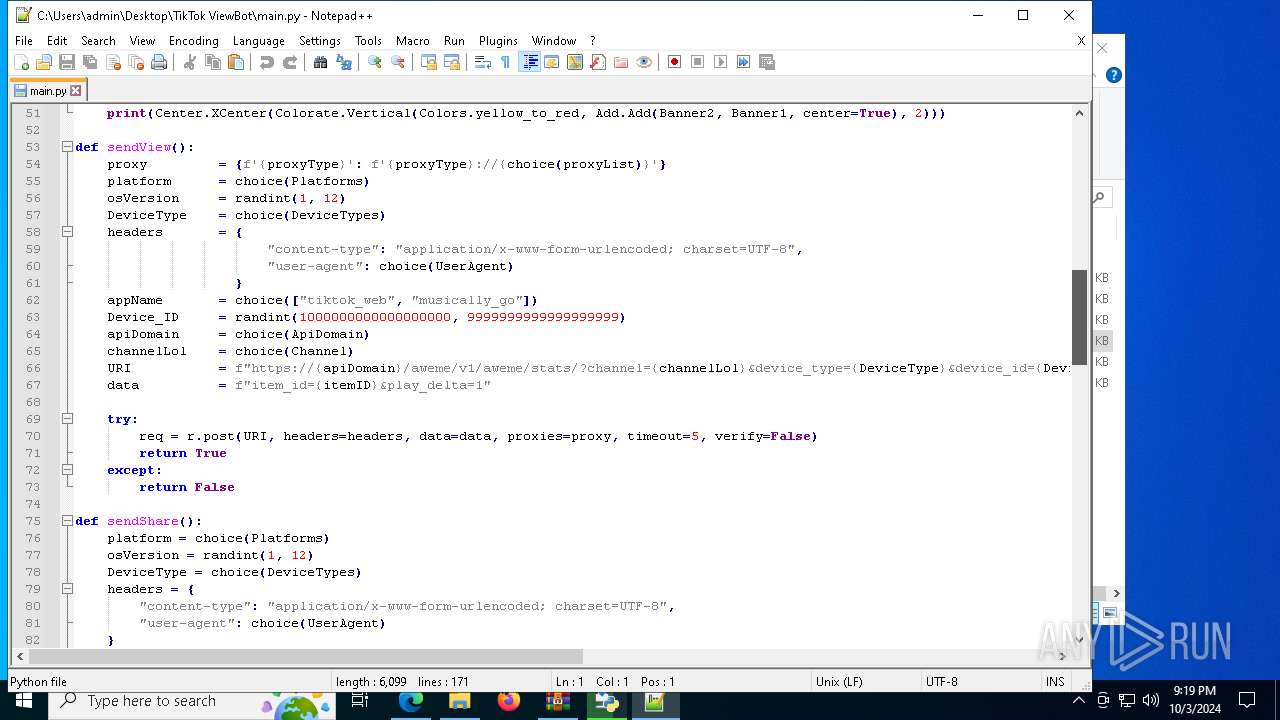
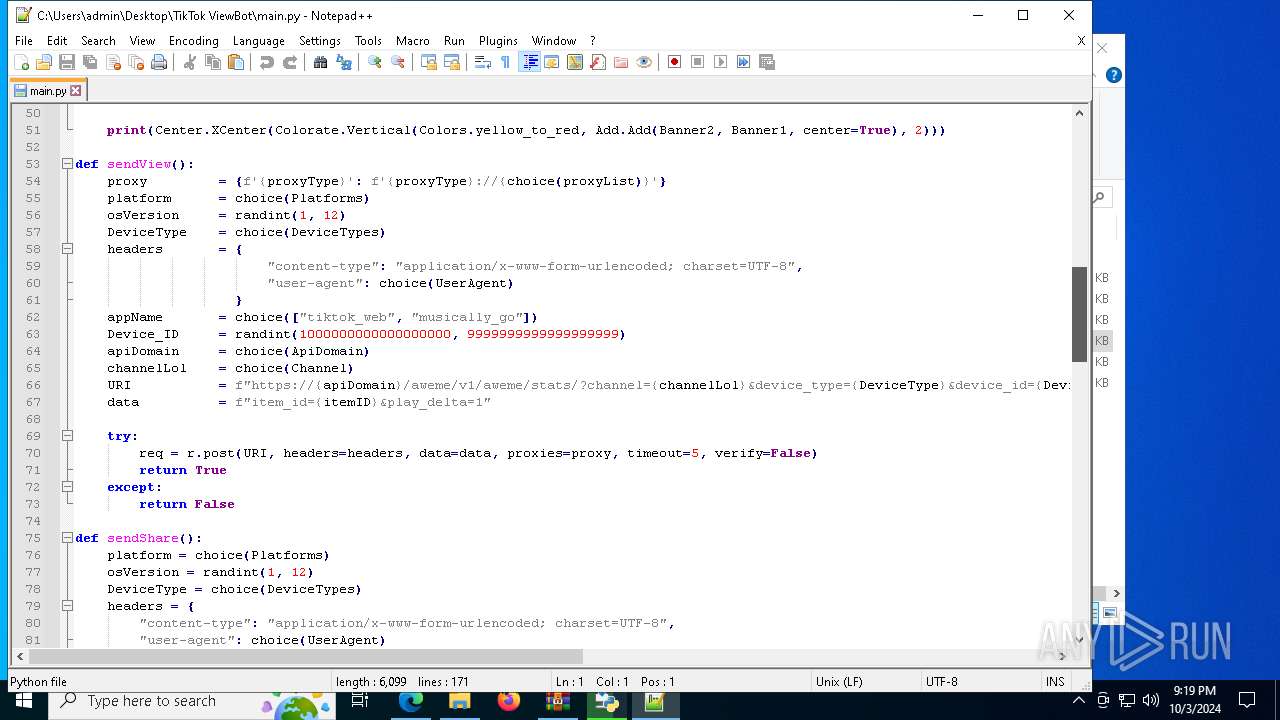
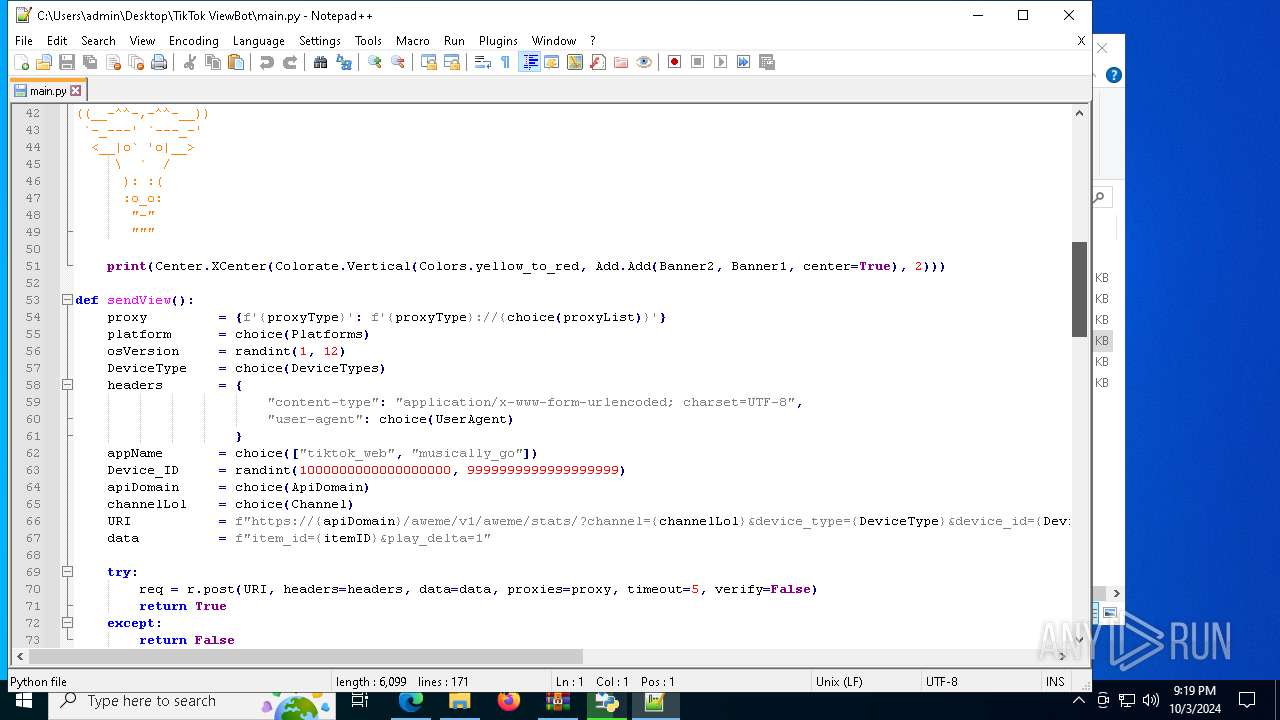
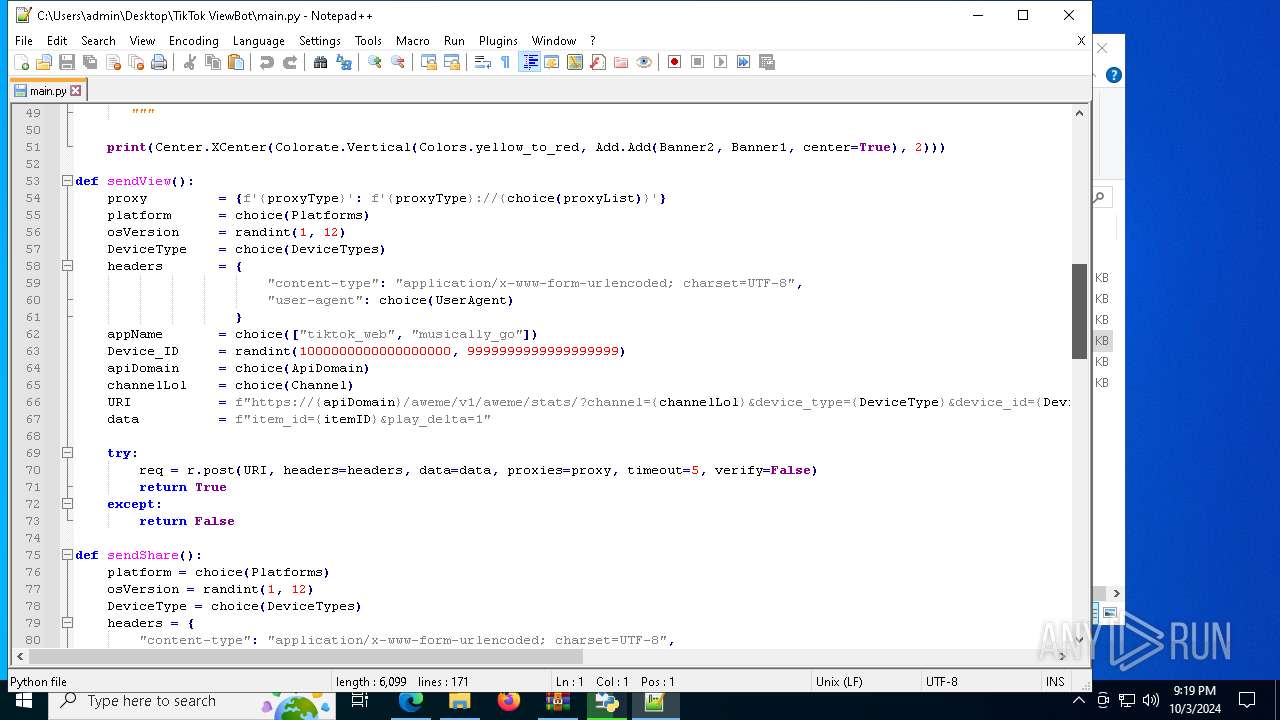
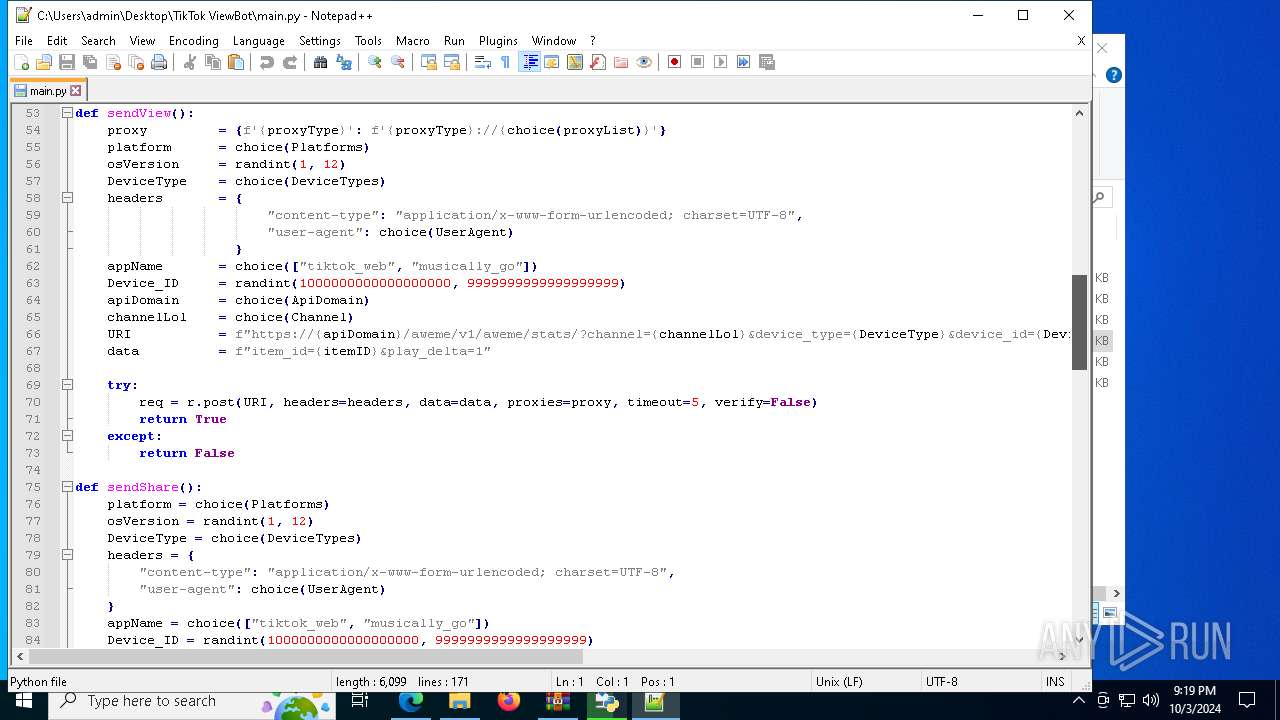
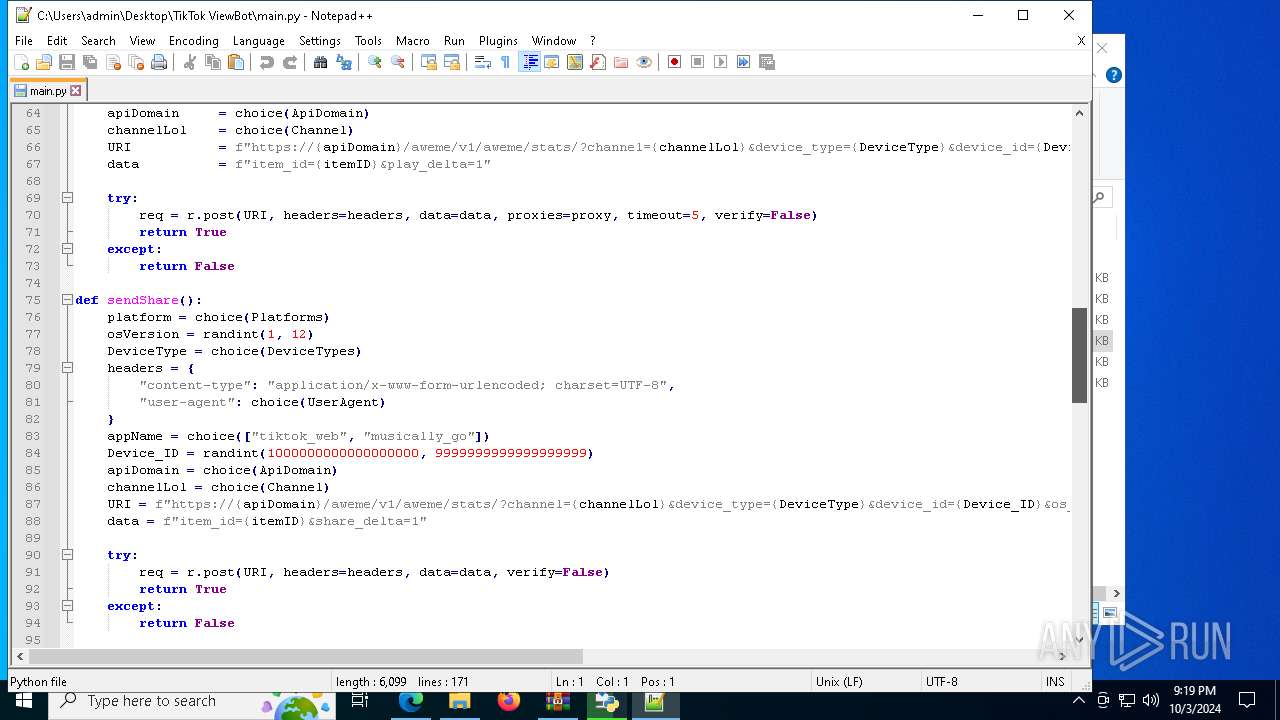
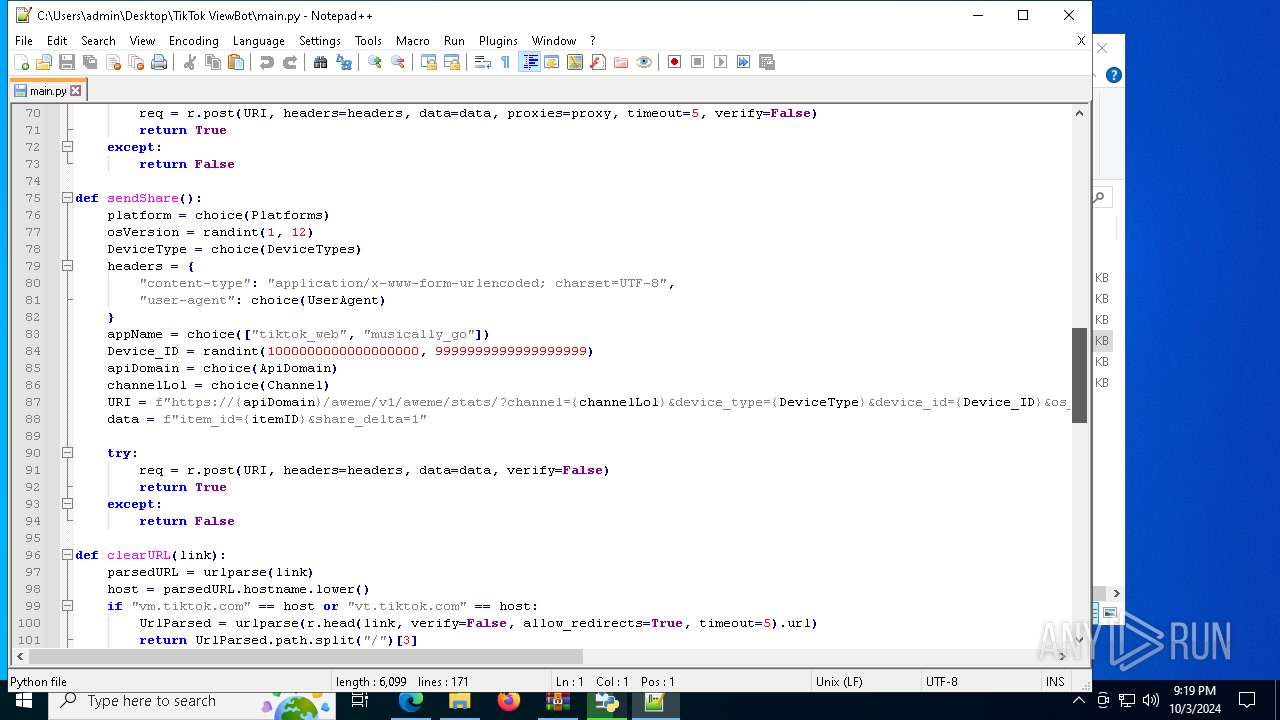
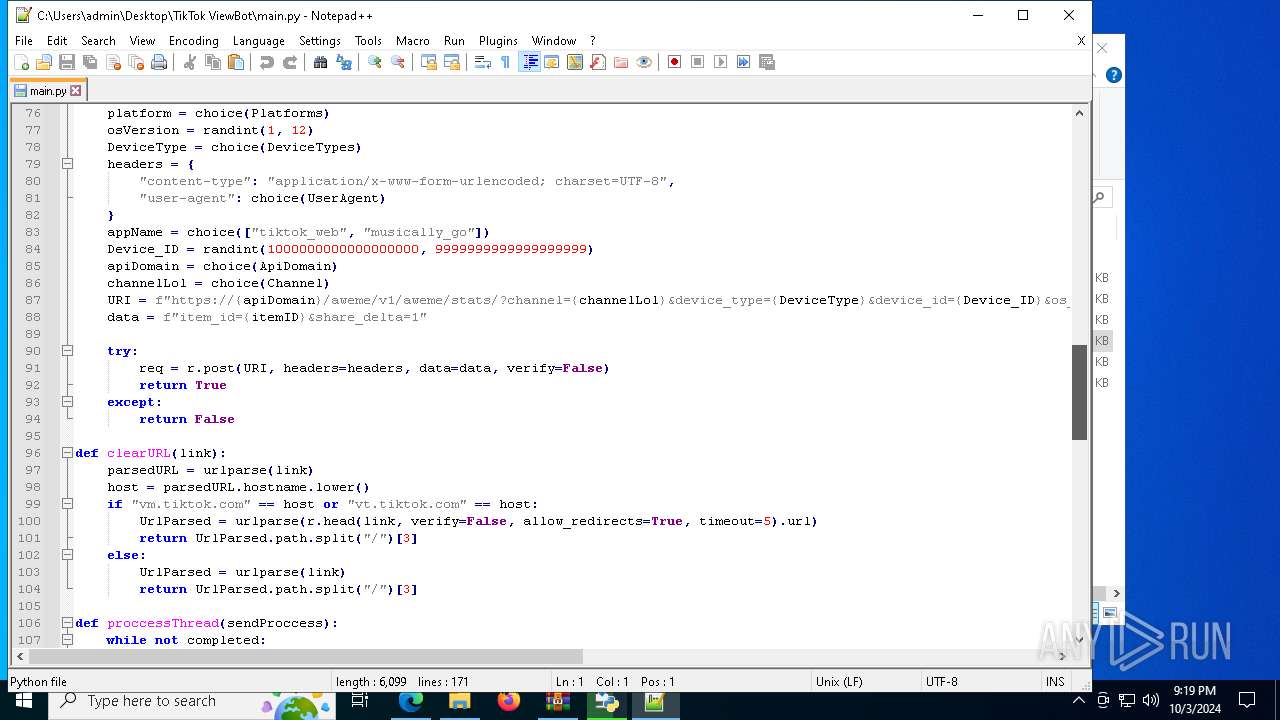
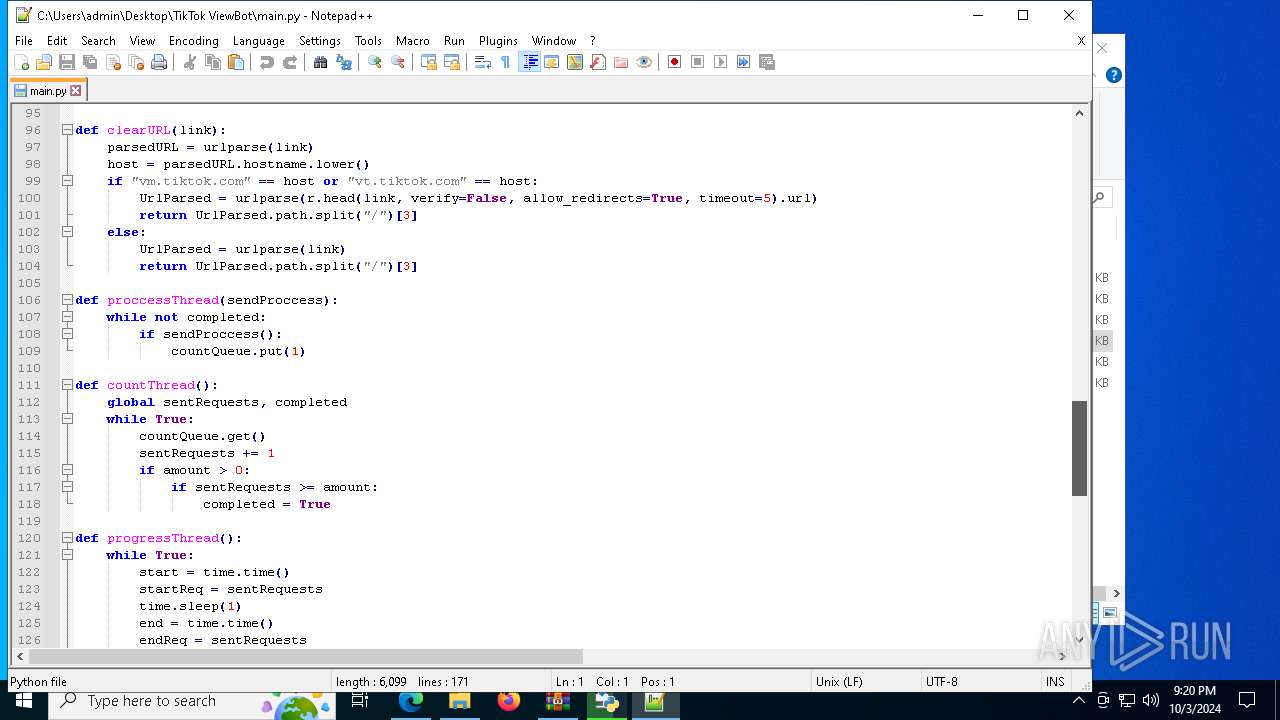
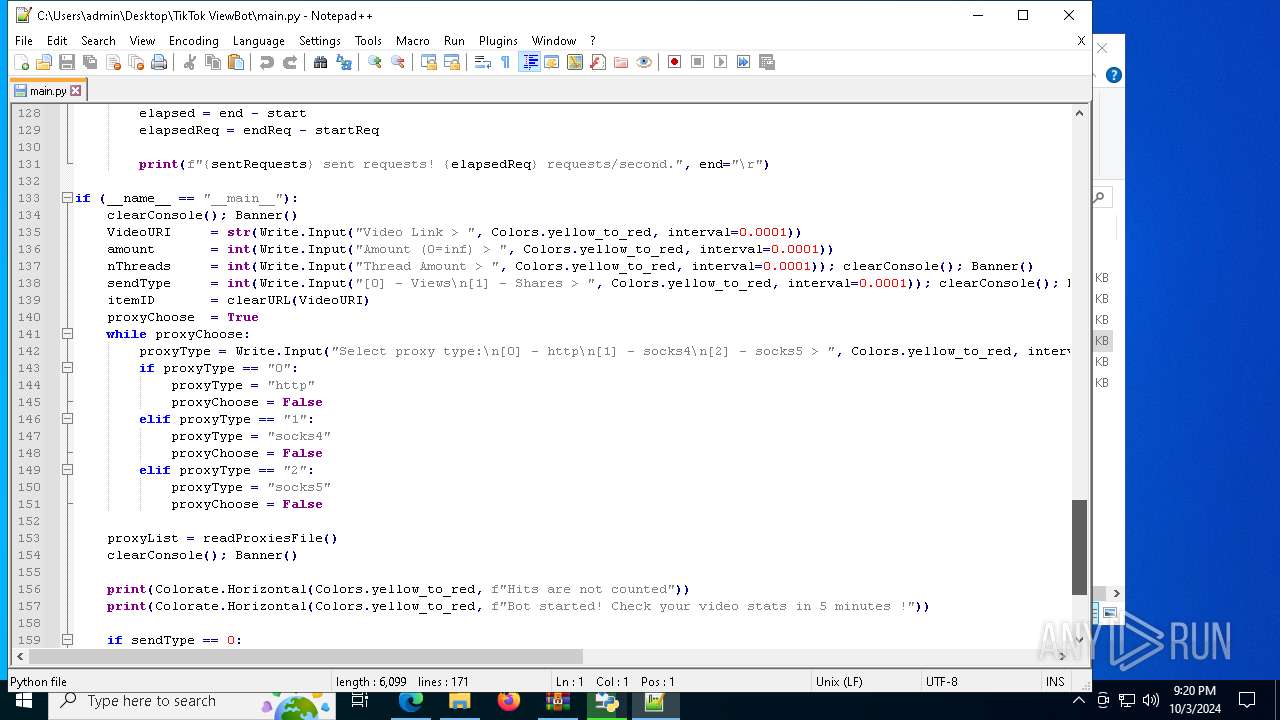
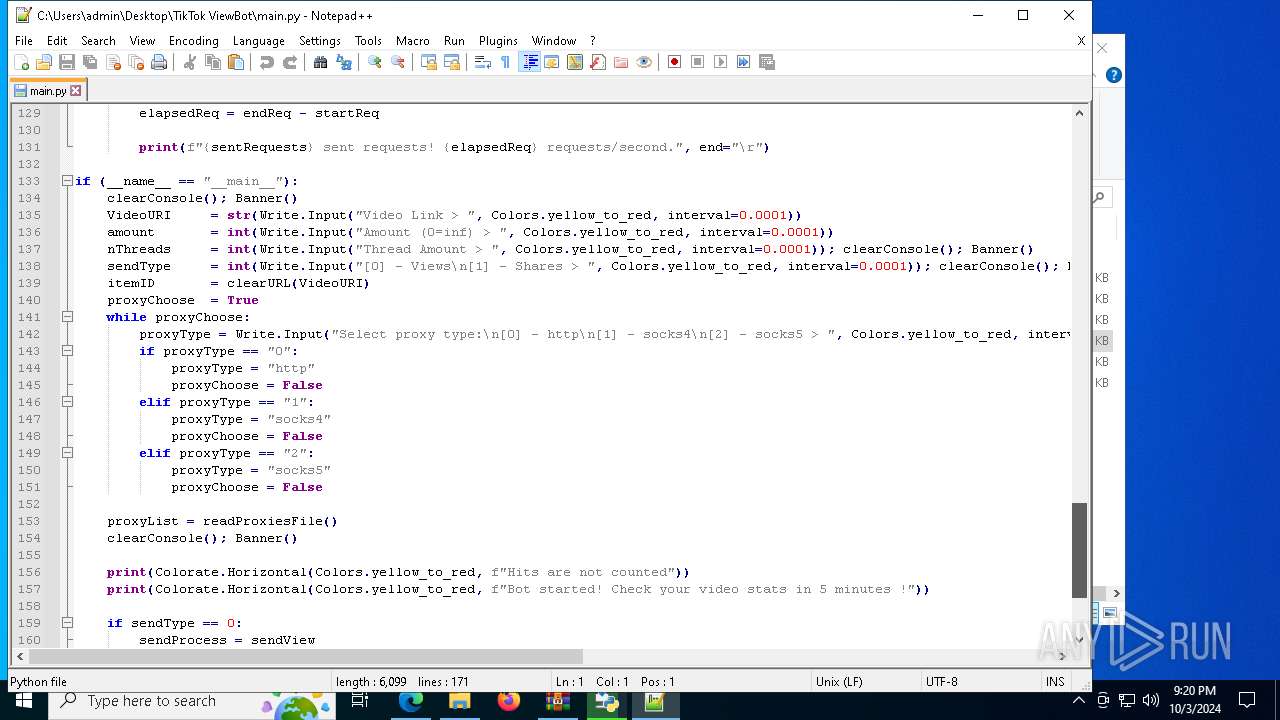
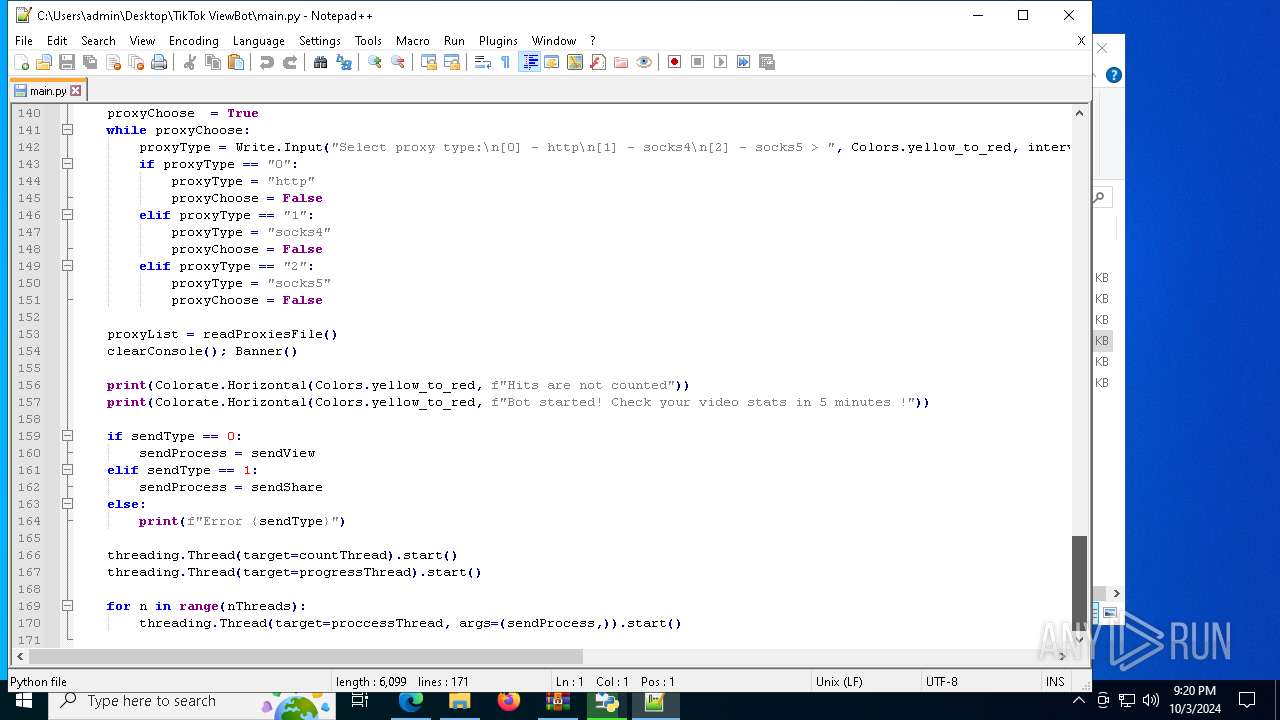
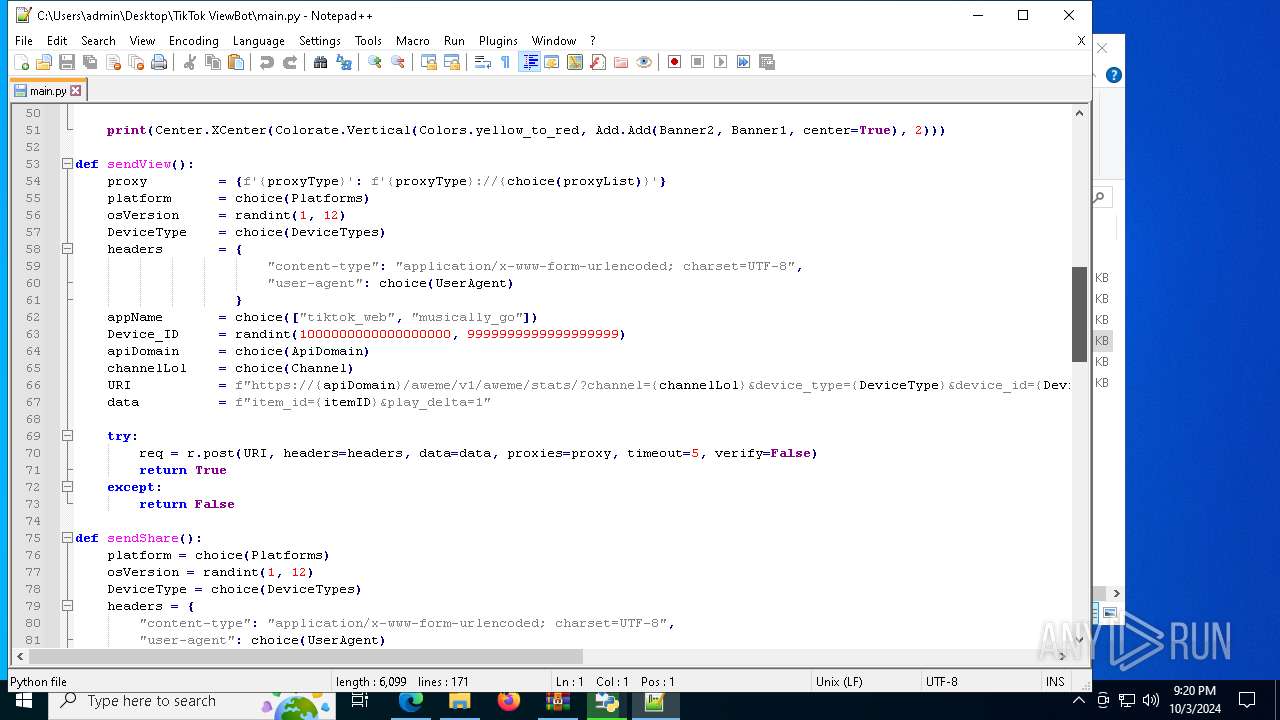
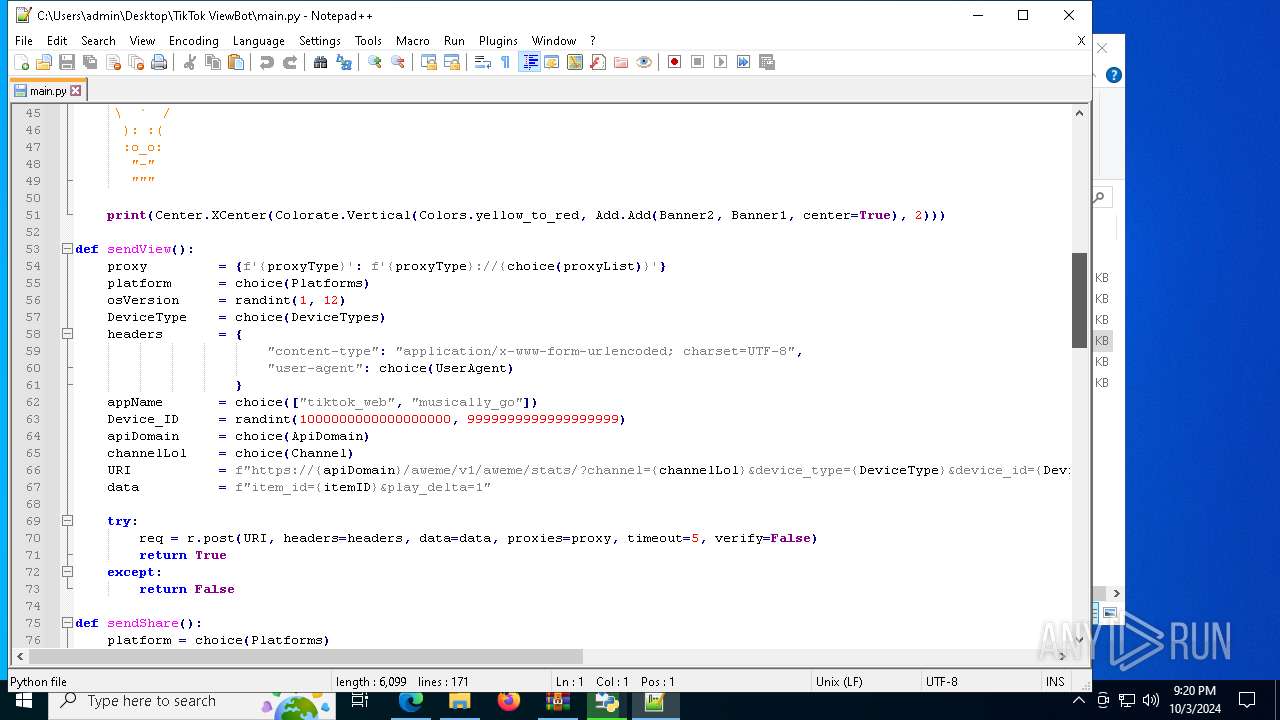
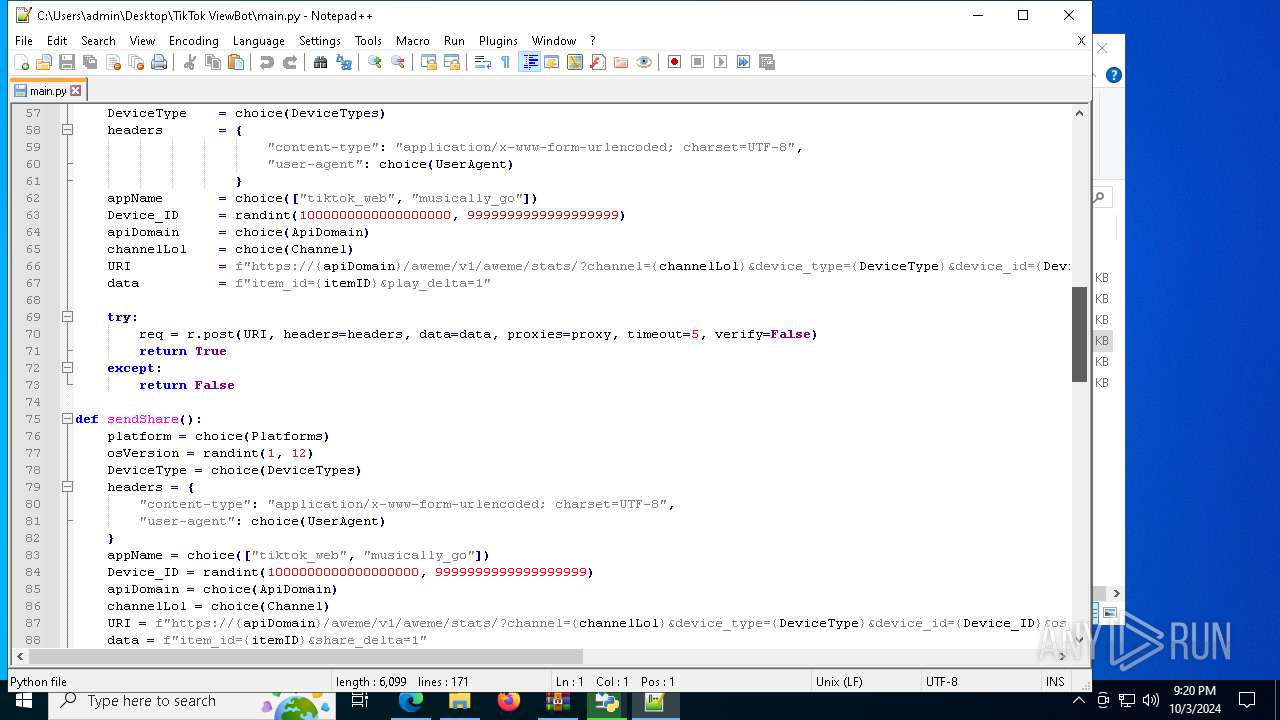
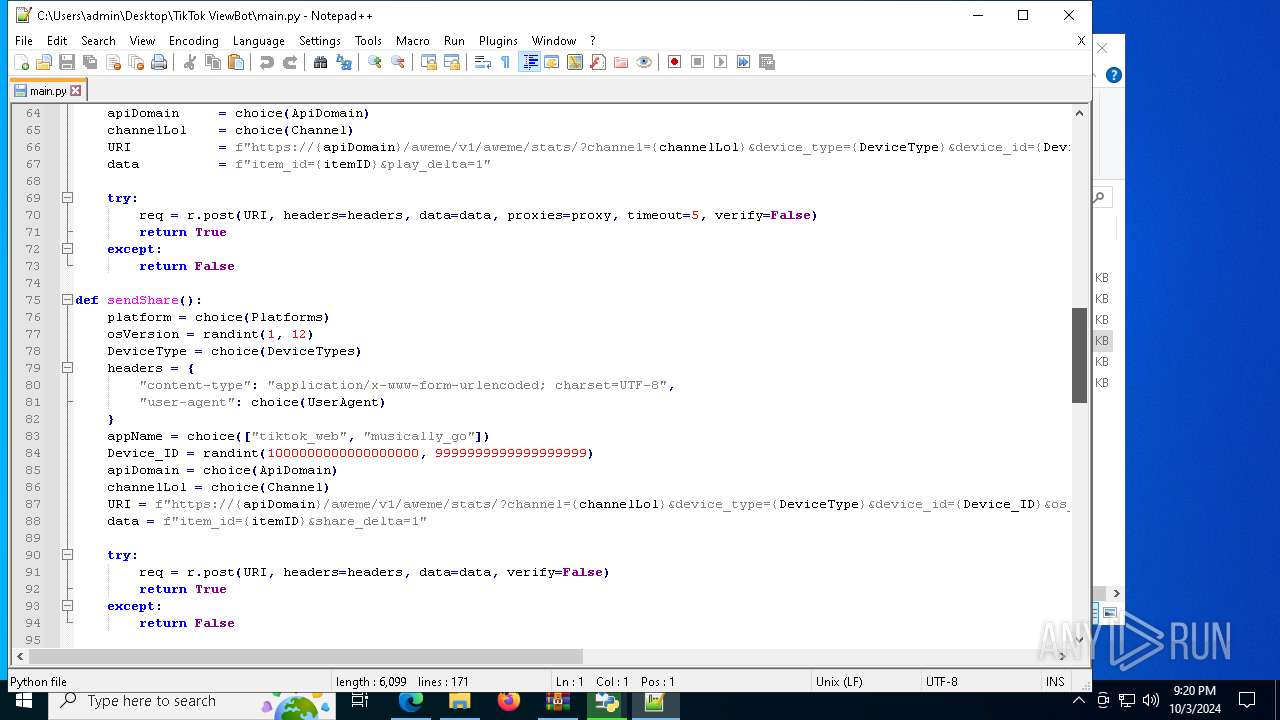
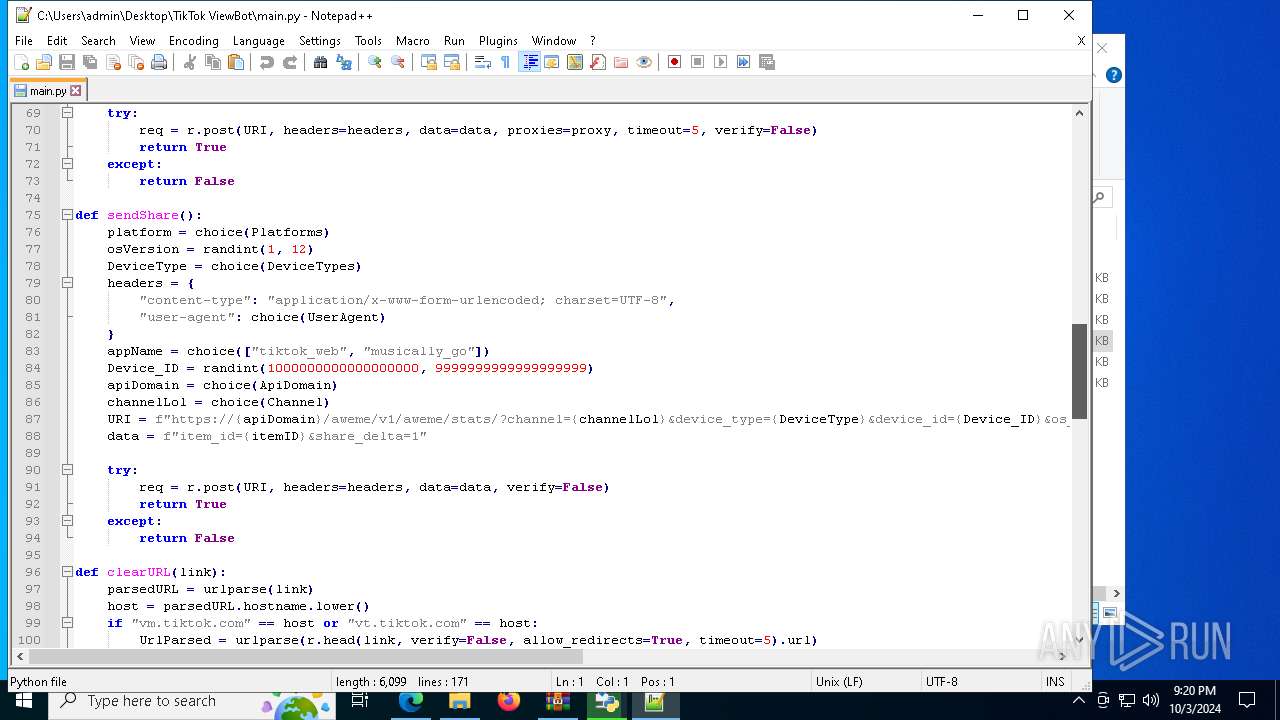
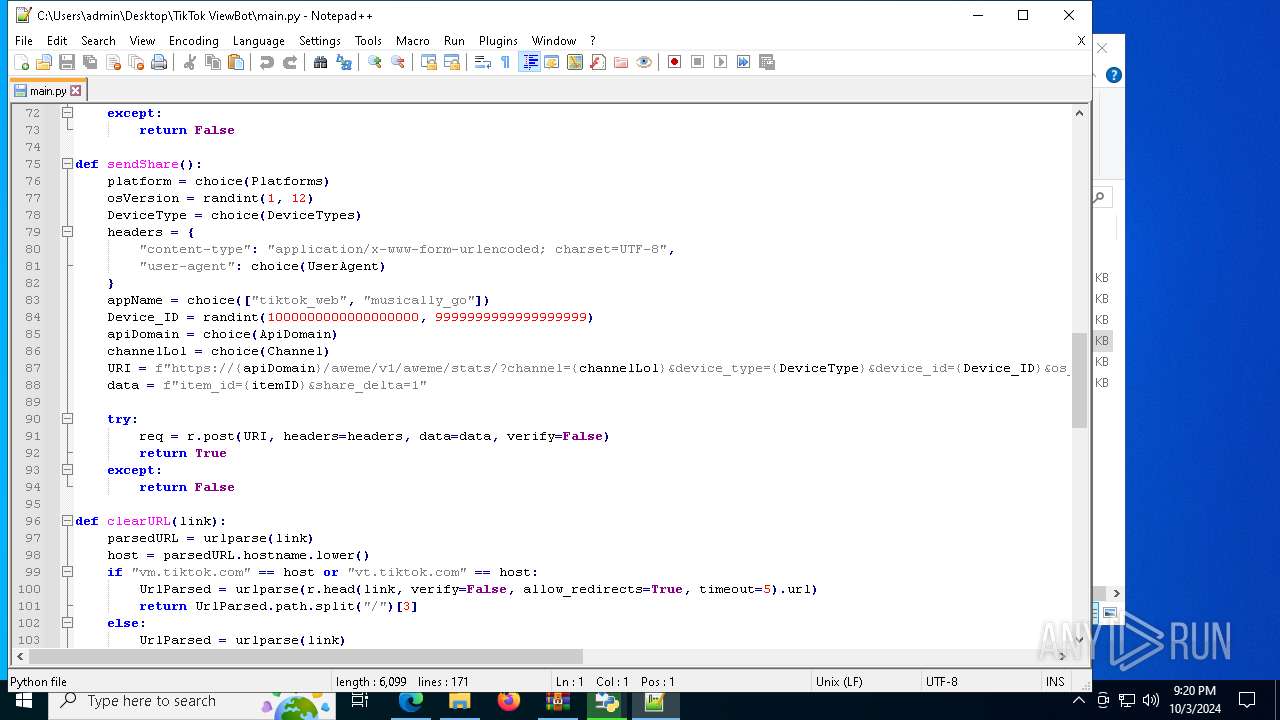
| 5588 | bot_start.exe | C:\Users\admin\Desktop\TikTok ViewBot\main.py | text | |
MD5:AA214E7B8696382BDC34B4122F001CFC | SHA256:484EFFF3A213DE2098B2943B80B4520F459BC74B253F78BE03C3B6C32A22B747 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
155
DNS requests
148
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2100 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1984 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4920 | sWsmPty.exe | GET | 200 | 193.233.112.44:80 | http://193.233.112.44/ | unknown | — | — | unknown |
4920 | sWsmPty.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEIwQDA%2BMDwwOjAJBgUrDgMCGgUABBQdI2%2BOBkuXH93foRUj4a7lAr4rGwQUOpqFBxBnKLbv9r0FQW4gwZTaD94CAQc%3D | unknown | — | — | whitelisted |
4920 | sWsmPty.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEQwQjBAMD4wPDAJBgUrDgMCGgUABBTkIInKBAzXkF0Qh0pel3lfHJ9GPAQU0sSw0pHUTBFxs2HLPaH%2B3ahq1OMCAxvnFQ%3D%3D | unknown | — | — | whitelisted |
3180 | VC_redistx64.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEowSDBGMEQwQjAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCQDflMUbWnbjyw%3D%3D | unknown | — | — | whitelisted |
4920 | sWsmPty.exe | GET | 200 | 192.124.249.36:80 | http://ocsp.godaddy.com//MEkwRzBFMEMwQTAJBgUrDgMCGgUABBS2CA1fbGt26xPkOKX4ZguoUjM0TgQUQMK9J47MNIMwojPX%2B2yz8LQsgM4CCDxp2lE7ehLK | unknown | — | — | whitelisted |
68 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
68 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3916 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2100 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2100 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4920 | sWsmPty.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
2256 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
3180 | VC_redistx64.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
3180 | VC_redistx64.exe | Misc activity | ET HUNTING Telegram API Certificate Observed |
4920 | sWsmPty.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |
4920 | sWsmPty.exe | Malware Command and Control Activity Detected | ET MALWARE [SEKOIA.IO] Win32/Stealc C2 Check-in |
3300 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
3300 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
3300 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
3300 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|