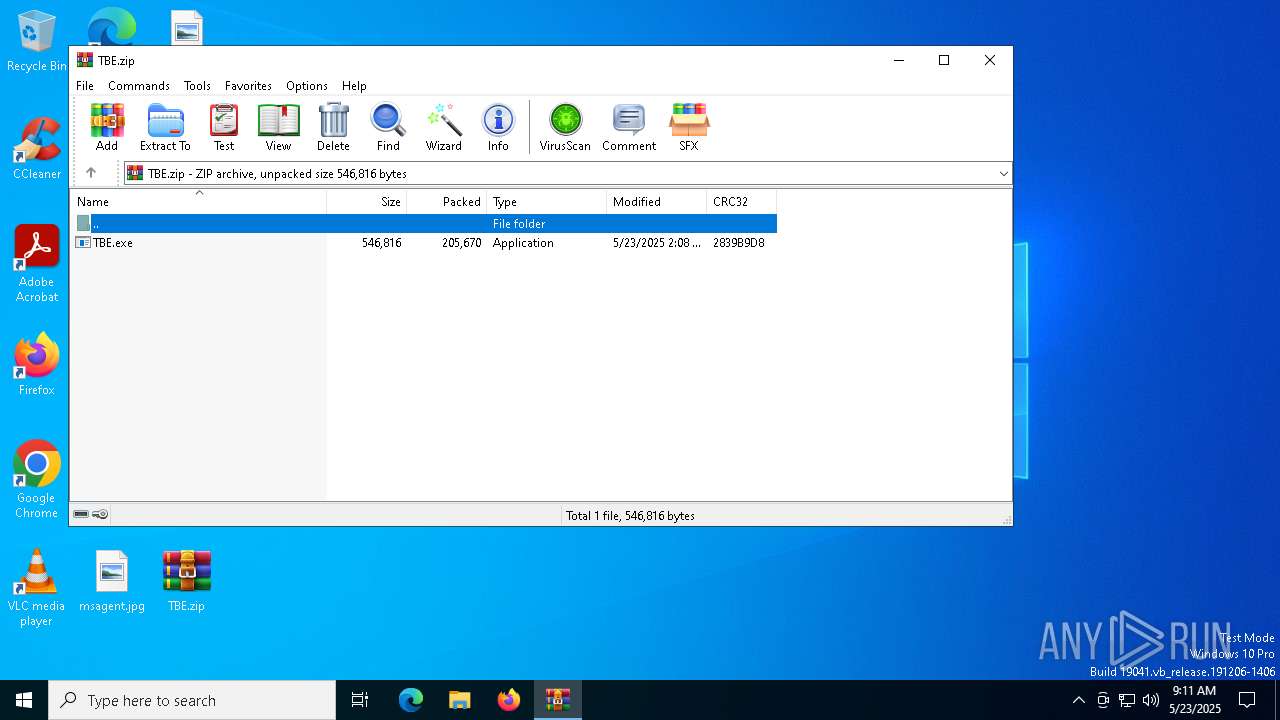
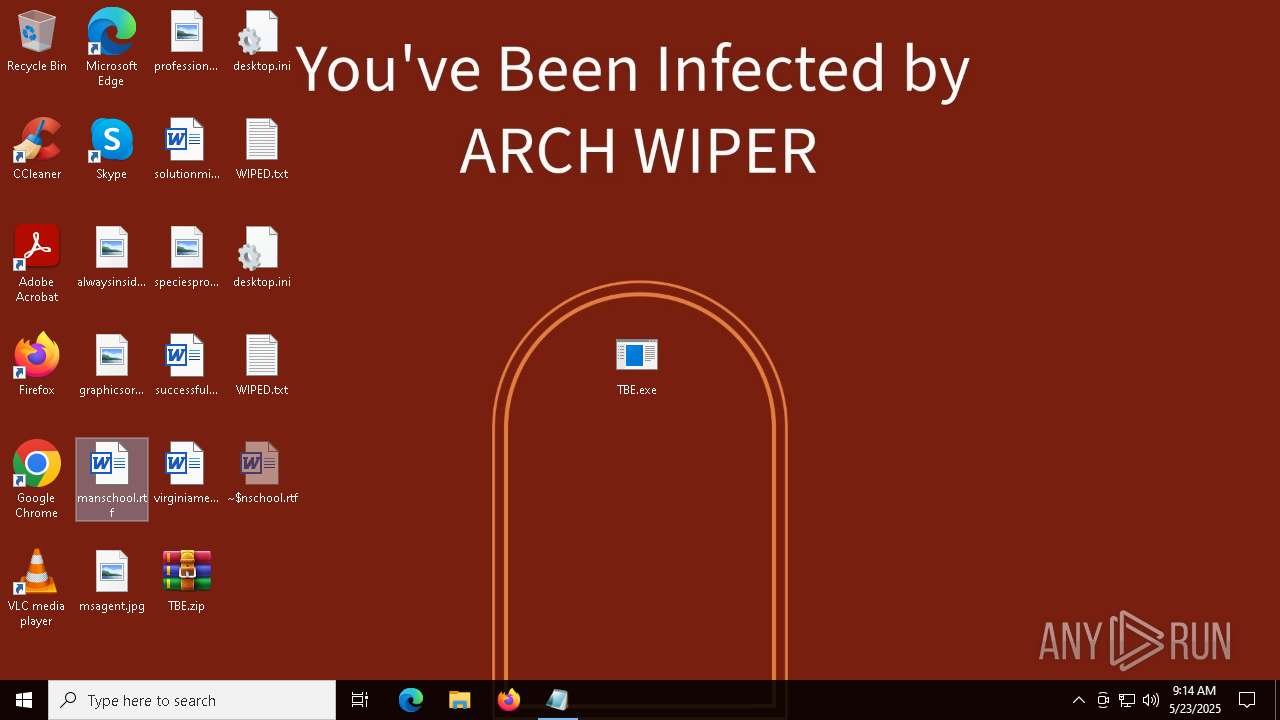
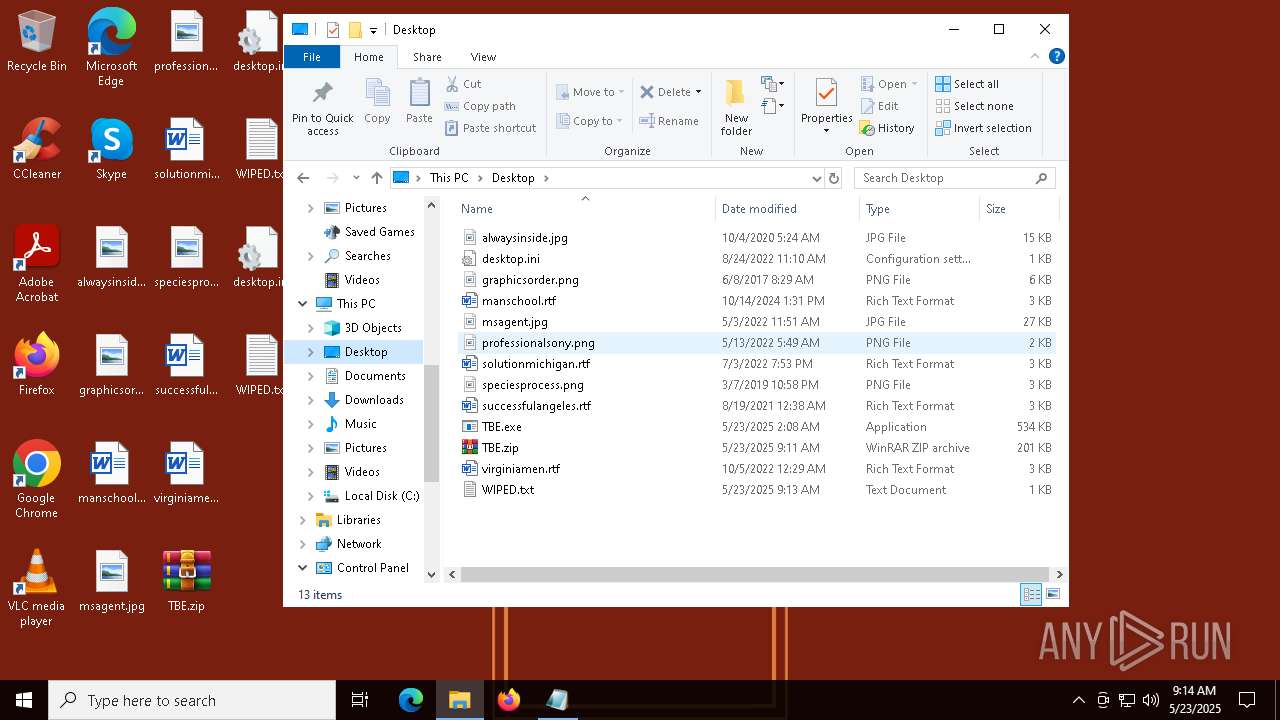
| File name: | TBE.zip |
| Full analysis: | https://app.any.run/tasks/5e3fa860-c8e1-483a-b377-dfb66bff14fb |
| Verdict: | Malicious activity |
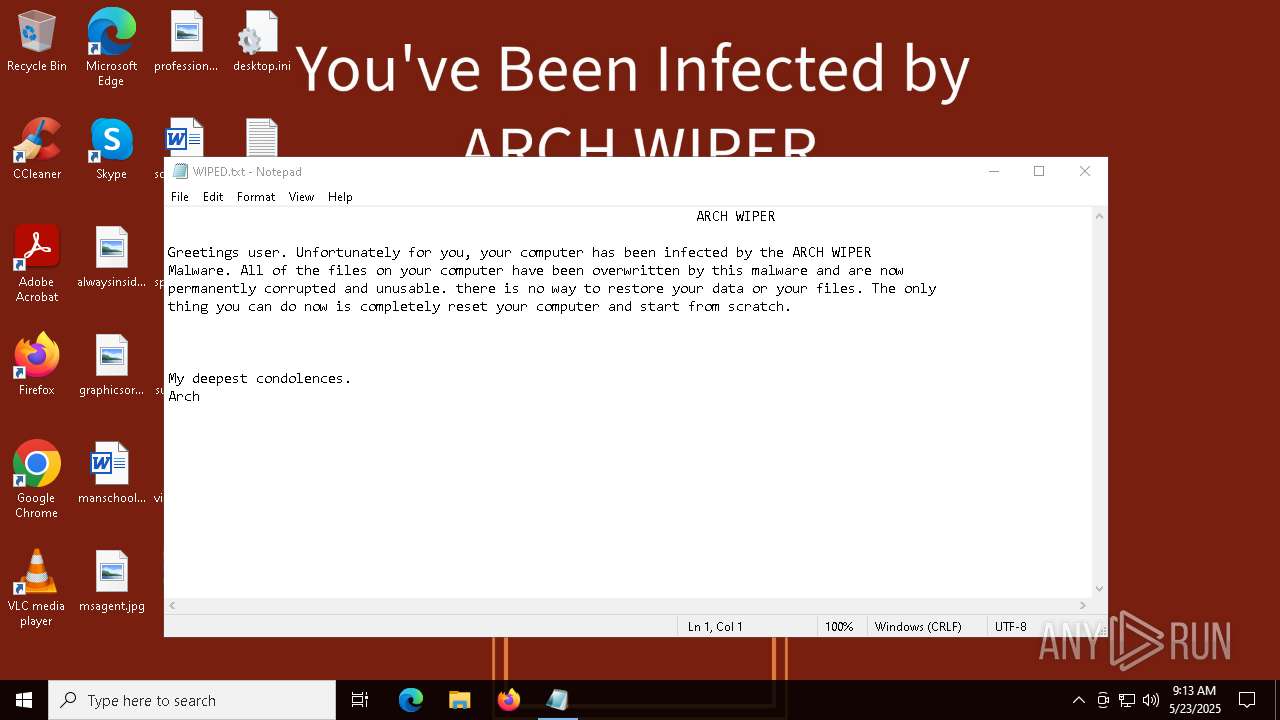
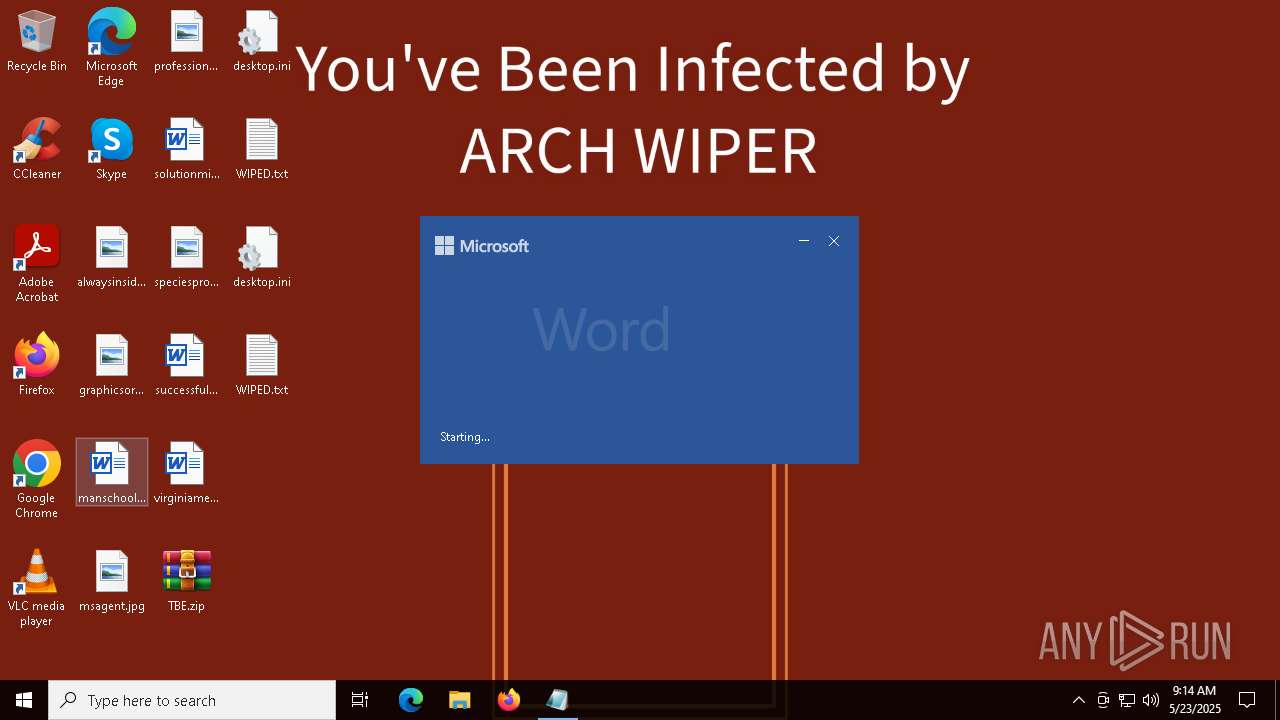
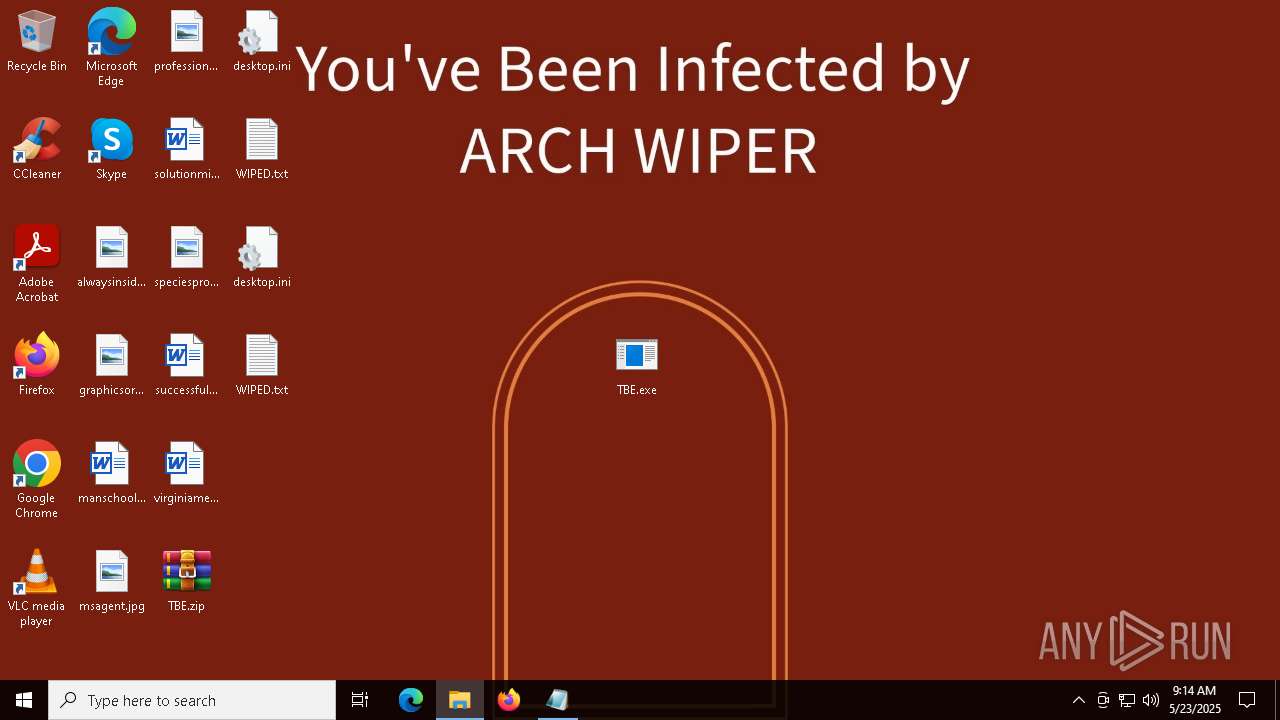
| Threats: | Chaos ransomware is a malware family known for its destructive capabilities and diverse variants. It first appeared in 2021 as a ransomware builder and later acted as a wiper. Unlike most ransomware strains that encrypt data to extort payment, early Chaos variants permanently corrupted files, while later versions adopted more conventional encryption techniques. |
| Analysis date: | May 23, 2025, 09:11:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 91B383CCB951FDF64C2297471B56957D |
| SHA1: | DF9FB2F9B426C1873FEAD3C12274481277B1B978 |
| SHA256: | 030F32751EA70720842C20F903143A7A1E6D3BAEB51A4803E0EC84ED84D10AB7 |
| SSDEEP: | 6144:YX/dZV31ubP2oWbkk7/Xd/hCUZ/rSuZ0f3J:YjWjhWbka/t/rrF05 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5576)
CHAOS has been detected (YARA)
- TBE.exe (PID: 8024)
- TheBrokenEnd.exe (PID: 6808)
RANSOMWARE has been detected
- TheBrokenEnd.exe (PID: 6808)
Create files in the Startup directory
- TheBrokenEnd.exe (PID: 6808)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 7352)
Deletes shadow copies
- cmd.exe (PID: 7520)
- cmd.exe (PID: 2088)
SUSPICIOUS
Reads the date of Windows installation
- TheBrokenEnd.exe (PID: 6808)
- TBE.exe (PID: 8024)
Found regular expressions for crypto-addresses (YARA)
- TBE.exe (PID: 8024)
- TheBrokenEnd.exe (PID: 6808)
Starts itself from another location
- TBE.exe (PID: 8024)
Reads security settings of Internet Explorer
- TBE.exe (PID: 8024)
- TheBrokenEnd.exe (PID: 6808)
Executable content was dropped or overwritten
- TBE.exe (PID: 8024)
Executes as Windows Service
- vds.exe (PID: 5984)
- VSSVC.exe (PID: 6272)
- wbengine.exe (PID: 7576)
Start notepad (likely ransomware note)
- TheBrokenEnd.exe (PID: 6808)
Starts CMD.EXE for commands execution
- TheBrokenEnd.exe (PID: 6808)
INFO
Checks supported languages
- TBE.exe (PID: 8024)
- TheBrokenEnd.exe (PID: 6808)
Reads the computer name
- TBE.exe (PID: 8024)
- TheBrokenEnd.exe (PID: 6808)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5576)
Reads the software policy settings
- slui.exe (PID: 7240)
- slui.exe (PID: 8076)
Manual execution by a user
- TBE.exe (PID: 8024)
- WINWORD.EXE (PID: 2244)
- mspaint.exe (PID: 7100)
- mspaint.exe (PID: 4648)
Process checks computer location settings
- TheBrokenEnd.exe (PID: 6808)
- TBE.exe (PID: 8024)
Creates files or folders in the user directory
- TBE.exe (PID: 8024)
- TheBrokenEnd.exe (PID: 6808)
Reads Microsoft Office registry keys
- TheBrokenEnd.exe (PID: 6808)
Create files in a temporary directory
- TheBrokenEnd.exe (PID: 6808)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6080)
- WMIC.exe (PID: 5116)
Reads the machine GUID from the registry
- TheBrokenEnd.exe (PID: 6808)
Checks proxy server information
- slui.exe (PID: 8076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:23 02:08:58 |
| ZipCRC: | 0x2839b9d8 |
| ZipCompressedSize: | 205670 |
| ZipUncompressedSize: | 546816 |
| ZipFileName: | TBE.exe |
Total processes
169
Monitored processes
27
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "19CFDD2B-F270-4648-99AD-06563DAC2521" "373EEF7A-631C-4E57-9F11-582E9055845D" "2244" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 2088 | "C:\Windows\System32\cmd.exe" /C vssadmin delete shadows /all /quiet & wmic shadowcopy delete | C:\Windows\System32\cmd.exe | — | TheBrokenEnd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\manschool.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
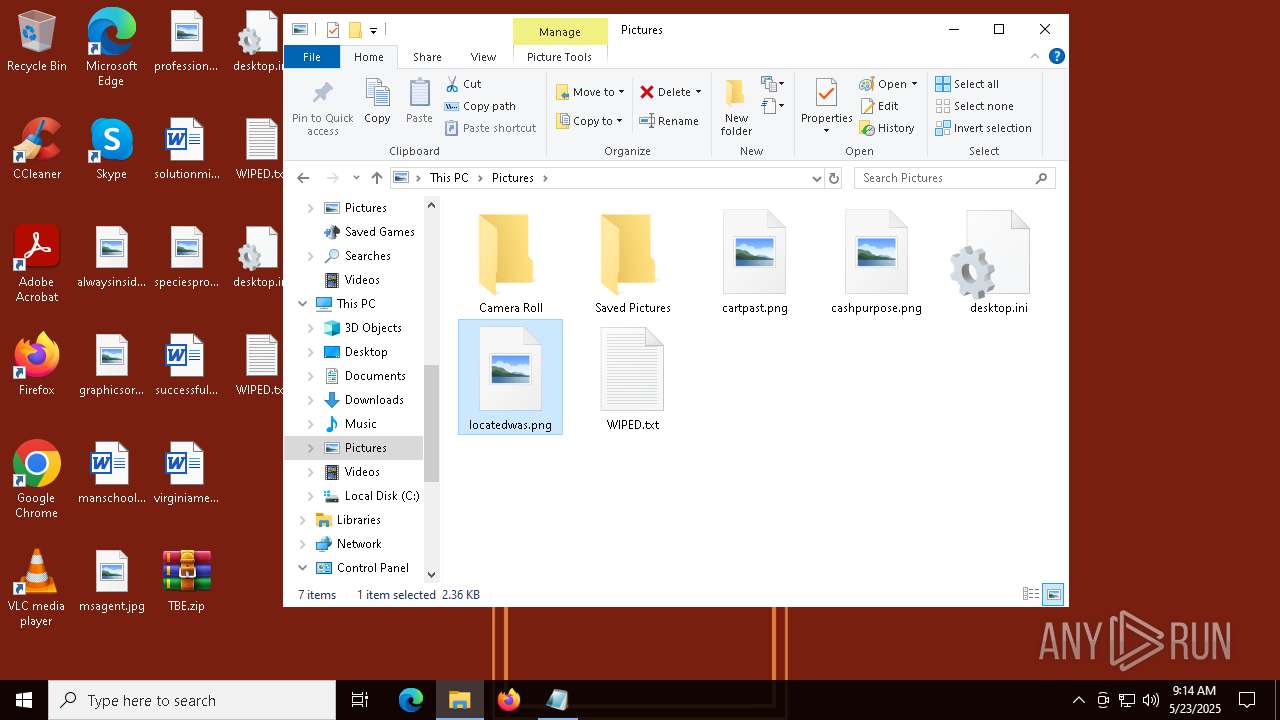
| 4648 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Pictures\locatedwas.png" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | bcdedit /set {default} recoveryenabled no | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5384 | C:\WINDOWS\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\TBE.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
13 905
Read events
13 521
Write events
340
Delete events
44
Modification events
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\TBE.zip | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
3
Suspicious files
29
Text files
102
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
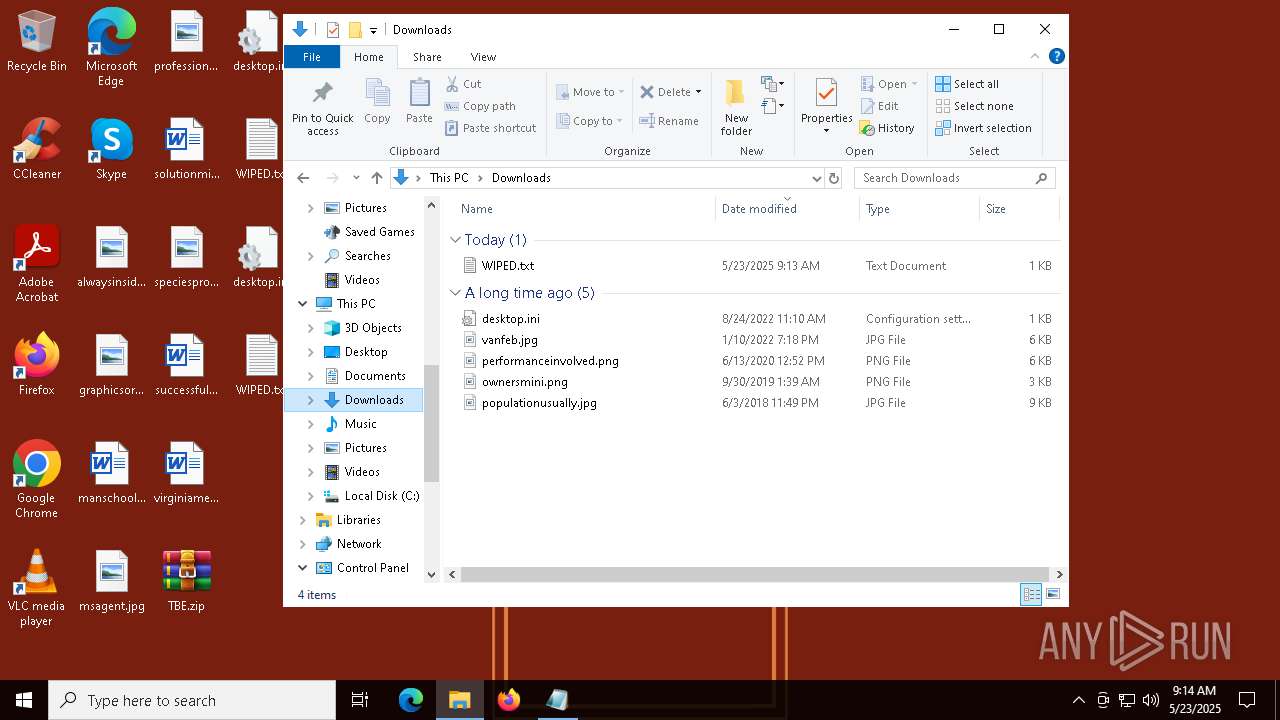
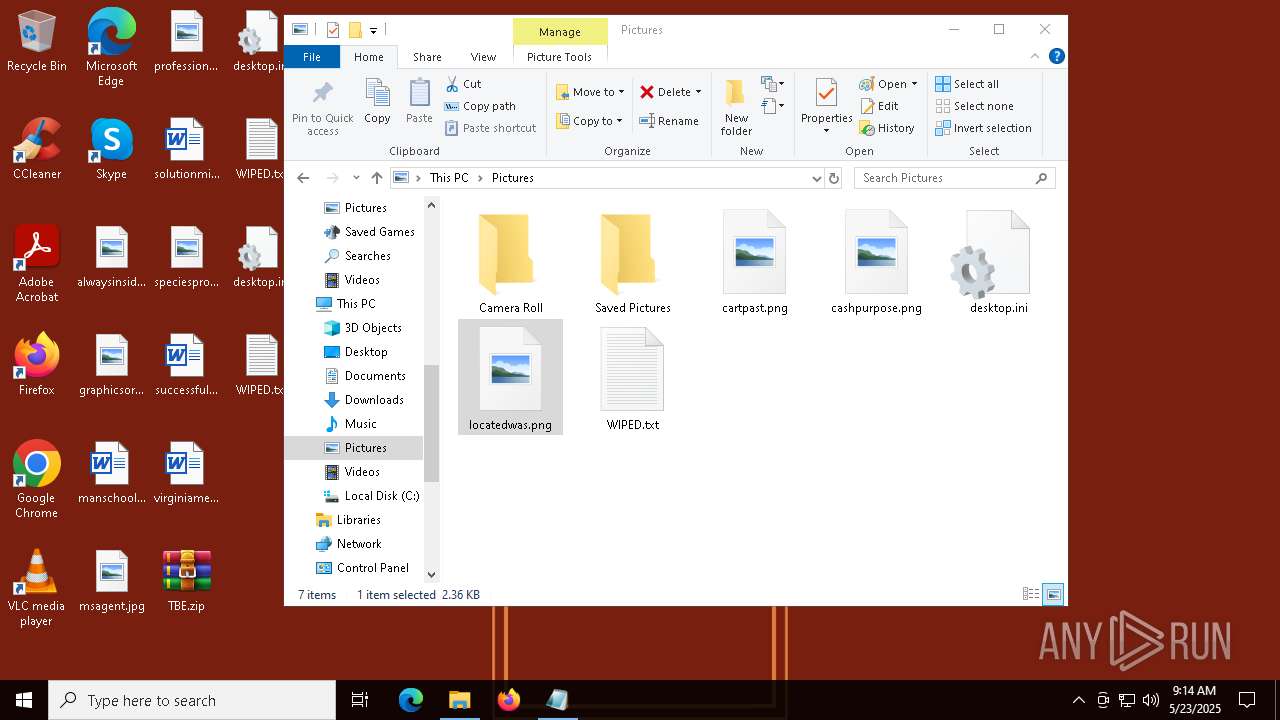
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\core\linux-x64\WIPED.txt | text | |
MD5:EFD4EA1425BABFBB77E887B44342EEAC | SHA256:5E664BA67074B709DBDAA1FDB2D36745F691661C725D27AE1E31238E7636E51F | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Documents\Outlook Files\WIPED.txt | text | |
MD5:EFD4EA1425BABFBB77E887B44342EEAC | SHA256:5E664BA67074B709DBDAA1FDB2D36745F691661C725D27AE1E31238E7636E51F | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Documents\OneNote Notebooks\My Notebook\WIPED.txt | text | |
MD5:EFD4EA1425BABFBB77E887B44342EEAC | SHA256:5E664BA67074B709DBDAA1FDB2D36745F691661C725D27AE1E31238E7636E51F | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Links\WIPED.txt | text | |
MD5:EFD4EA1425BABFBB77E887B44342EEAC | SHA256:5E664BA67074B709DBDAA1FDB2D36745F691661C725D27AE1E31238E7636E51F | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Desktop\WIPED.txt | text | |
MD5:EFD4EA1425BABFBB77E887B44342EEAC | SHA256:5E664BA67074B709DBDAA1FDB2D36745F691661C725D27AE1E31238E7636E51F | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Contacts\WIPED.txt | text | |
MD5:EFD4EA1425BABFBB77E887B44342EEAC | SHA256:5E664BA67074B709DBDAA1FDB2D36745F691661C725D27AE1E31238E7636E51F | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\TheBrokenEnd.url | binary | |
MD5:1BF9F5C5B57DE985F9AD31B29B377BAC | SHA256:50B49E79FE9F3C69FDB7A66A9A46DF0BA59DF24C0C0C7D88EFEE51B932C7956B | |||
| 8024 | TBE.exe | C:\Users\admin\AppData\Roaming\TheBrokenEnd.exe | executable | |
MD5:9BBFA1FA31B5922CCB85596B048398CF | SHA256:53C229B50576223794765AF3EFBFEACB7A72E544AE6384C88E5B5B3853918541 | |||
| 5576 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5576.32222\TBE.exe | executable | |
MD5:9BBFA1FA31B5922CCB85596B048398CF | SHA256:53C229B50576223794765AF3EFBFEACB7A72E544AE6384C88E5B5B3853918541 | |||
| 6808 | TheBrokenEnd.exe | C:\Users\admin\Documents\PowerShell\Modules\PSSQLite\1.1.0\core\linux-x64\SQLite.Interop.dll.Arch | text | |
MD5:69BD9EB68CBDB12393731F11EA4FE1D7 | SHA256:BCB00C3CD9F7316B4DAA035F10C9D3C7480CA4AB13DFA1AD6F417D9FDAF1C34D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7788 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2244 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7788 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |