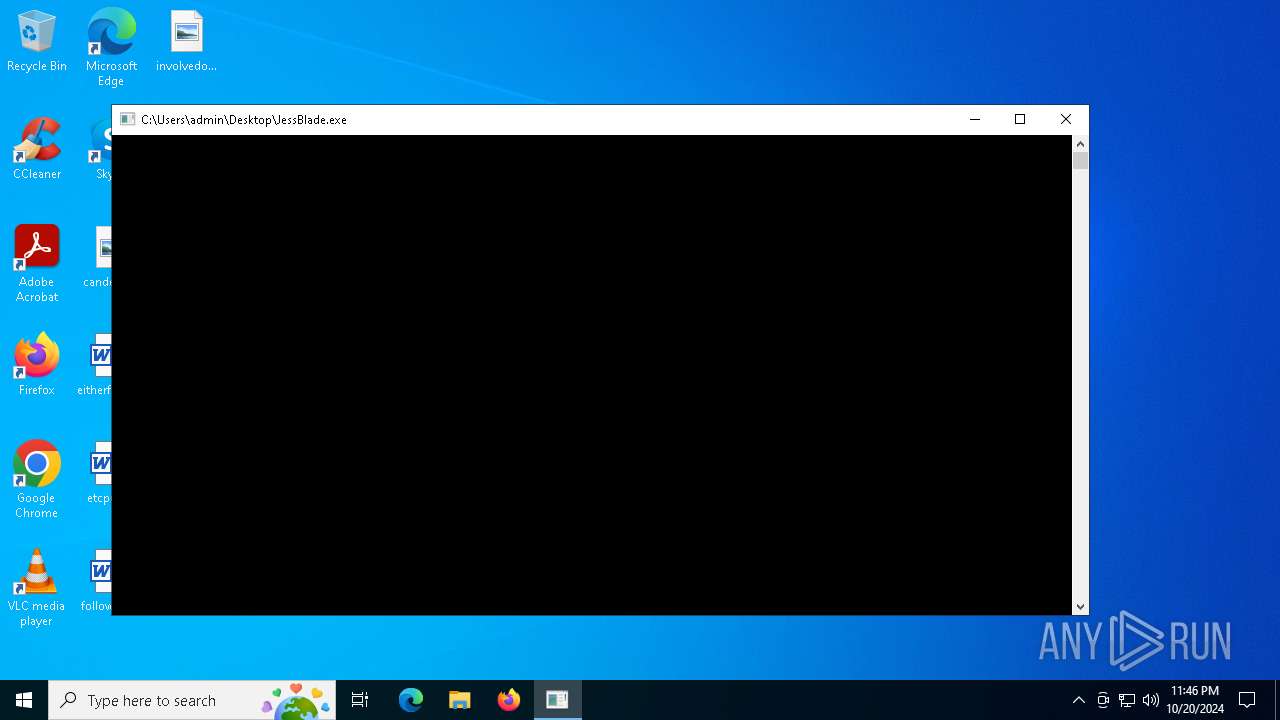
| File name: | JessBlade.exe |
| Full analysis: | https://app.any.run/tasks/398b8177-2819-4318-9e77-3d3e7109bdf2 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | October 20, 2024, 23:46:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 61FEC8102978A11D3F4D2CCA07F18695 |
| SHA1: | 4FC63BF4413D069E86074FAB878F1150C337FA3A |
| SHA256: | 02A9796CCD1895E1C1B3449A587C206BB5AA0566681960F6ADF07C1A883667BE |
| SSDEEP: | 12288:BfBoDaAiJ4GFBYA6xLzpAkdlnoHXADUq7DDdyzq64EOOKBT9Wr:BSDaAiGGFmA0XukdRoHXADUq7DDdyzL |
MALICIOUS
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2172)
- aspnet_regiis.exe (PID: 2708)
Connects to the CnC server
- svchost.exe (PID: 2172)
Actions looks like stealing of personal data
- aspnet_regiis.exe (PID: 2708)
SUSPICIOUS
Executable content was dropped or overwritten
- JessBlade.exe (PID: 5516)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2172)
- aspnet_regiis.exe (PID: 2708)
INFO
Checks supported languages
- aspnet_regiis.exe (PID: 2708)
- JessBlade.exe (PID: 5516)
Reads the computer name
- JessBlade.exe (PID: 5516)
- aspnet_regiis.exe (PID: 2708)
Creates files or folders in the user directory
- JessBlade.exe (PID: 5516)
Reads the machine GUID from the registry
- aspnet_regiis.exe (PID: 2708)
Reads the software policy settings
- aspnet_regiis.exe (PID: 2708)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:20 20:59:54+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 41472 |
| InitializedDataSize: | 364032 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a00a |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 9.8.7.7 |
| ProductVersionNumber: | 9.8.7.7 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | jump banana i he black vision me lazy it connect |
| CompanyName: | produce organize blue |
| FileDescription: | banana manage large |
| FileVersion: | 9.8.7.7 |
| InternalName: | HarveyDavid.HDutA |
| LegalCopyright: | support it it they destroy (c) 2024 |
| LegalTrademarks: | energy learn understand it you |
| OriginalFileName: | HarveyDavid.HDutA |
| ProductName: | universe understand fast |
| ProductVersion: | 9.8.7.7 |
| AssemblyVersion: | 9.8.7.7 |
Total processes
125
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis.exe | JessBlade.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: aspnet_regiis.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5516 | "C:\Users\admin\Desktop\JessBlade.exe" | C:\Users\admin\Desktop\JessBlade.exe | explorer.exe | ||||||||||||
User: admin Company: produce organize blue Integrity Level: MEDIUM Description: banana manage large Exit code: 0 Version: 9.8.7.7 Modules
| |||||||||||||||
| 6268 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | JessBlade.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 524
Read events
3 524
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5516 | JessBlade.exe | C:\Users\admin\AppData\Roaming\msvcp110.dll | executable | |
MD5:3F90EB9A022B7234636C4BC1C4F14013 | SHA256:584813A16E7C4F66F6B5B1B16333D798F0A706DFF357C14E32CA48FCC87F23C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
17
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2000 | RUXIMICS.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2000 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.212.216.106:443 | https://steamcommunity.com/profiles/76561199724331900 | unknown | html | 33.7 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2000 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2000 | RUXIMICS.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2000 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
passimovrt.cfd |
| malicious |
monstourtu.sbs |
| malicious |
heroicmint.sbs |
| malicious |
sidercotay.sbs |
| malicious |
captaitwik.sbs |
| malicious |
wrigglesight.sbs |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (passimovrt .cfd) |
2708 | aspnet_regiis.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (passimovrt .cfd in TLS SNI) |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer Related Activity |
— | — | A Network Trojan was detected | ET MALWARE Lumma Stealer CnC Host Checkin |
2 ETPRO signatures available at the full report